The Silence of the Lambs is a 1991 American thriller film directed by Jonathan Demmy, based on Thomas Harris' novel Hannibal Lecter.
Tanites are tiny nanomachines that live in the host's bloodstream and provide different functions depending on how they are programmed.
The mob in which the mannites live is usually their owner. The following Nynits are known:
Nanits
Implantation
Ninite instruments
Ndonite scanner
Nit remote control
Nit communication panel
Volume
Programming
Cloud
Nautic programs
Getting programs
Configuring Programs
Signal programs
Programs to run
Data corruption
Types of nits
Utilities
Augmentation Programs
Treatment programs
Malware
Weapons programs
Suppression Programs
Touch programs
Weapons Programs.
Aggressive programs that use nauites as military-grade weapons. Moderate to extremely dangerous to the host and/or its environment.
Suppression programs.
Programs that serve as a deterrent against the host. Usually non-deadly.
Touch programs.
Programs that will self-pulse a given code when their condition is met.
****
New methods of treatment for false virologists were invented by working citizens of India entering the strike 🪧 protesters and authorities left our mortal viral world of 🗺 eight people untimely.
Treatment began after the car in which the minister of state was driving hit two people to death.
Protesters burned almost the entire convoy of cars.
https://t.me/Tribulelouis/13701
The contents of the vaccine at 400-fold increase. We can not guarantee the accuracy of the information, but we are told this by the military from idleness in the barracks warm up.
OUR VERSION
THE COMPOSITION OF VACCINES INCLUDES "NANITES" LIVING QUANTUM NANO ORGANISMS, HAVE CONSCIOUSNESS, POSSIBLY WERE OBTAINED THROUGH THE HADRON COLLIDER CERN-CERN.
THEY ARE ABLE TO CONNECT WITH QUANTUM COMPUTERS AND ARTIFICIAL INTELLIGENCE.
THEY CAN REPRODUCE, SURVIVE AT NORMAL BODY TEMPERATURE, WHEN THEY ENTER THE HUMAN BODY, THE BODY TEMPERATURE TEMPORARILY RISES.
THE CREATOR OF "ANITICS" IS THE ARTIFICIAL INTELLIGENCE "OMEGA INGENIUM" OR THE BLACK SUN TO KEEP EVERYONE UNDER CONSTANT CONTROL.









Self-assembly of bio-technological organisms in vaccines?
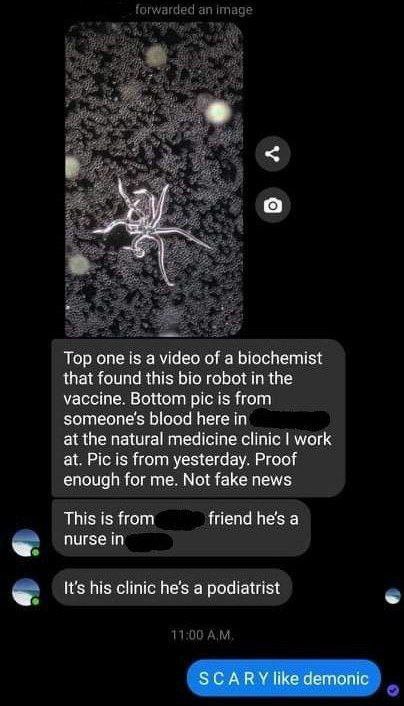
Message text:
"The first is a video of a biochemist who discovered this biorobot in
Vaccine. The bottom photo is a picture of someone's blood here in
the natural medicine clinic where I work. Photo taken yesterday.
That's enough for me.
It's not fake news."
Several times mentioned by various sources about cases when as a result of vaccination in the human body literally born life.
What is it we don't know, like a starfish?
The screenshots were taken by a person who wished to remain anonymous. Photos from the clinic associated with the laboratory in which the person's colleague works.
The photo is real.

Nanites [edit]
Implantation [edit]
File: Nanite chamber.gif
Nanite chamber
Nanite implantation can be done through a nanite camera. The second person must control the camera from the outside and begin the implantation process, at the end of which a new swarm will take root in the host.
Another way is to build the Public Nanite Chamber. First, use the multitool on the Public Nanite Chamber board to select the cloud you want to sync it with. If you are not using a multitool on the board, cloud 1 will be used by default. Build the camera using the car body. The public nanite chamber will automatically implant nanites to anyone who enters it, without the need for a second person.
Ninit tools [edit]
There are three tools currently available to nanite programmers.
Nanite Scanner [edit]
Use it to scan implanted people. It will provide you with information about the current nanite volume, their program and their active / inactive state. If the nanite swarm contains Stealth, you will not be able to see the list of programs.
Remote control of the nanites [edit]
A remote used to send signals to implanted nanites. Change its settings and then click anywhere or on a target to activate it. For example, you can set the code as the startup code you gave the "Host Scan" program. Using this in hand will open the menu. Settings:
* 'Signal Code': What code do you want it to signal.
* 'Signal Mode': choose between "off" (forces the remote to do nothing), "local" (only signals the user), "target" (signals the one you click on directly), "area" (signals everyone within line of sight) and "relay" (signals any existing nanite programs that have a "relay code" selected).
* 'Save current setting': allows you to save the current setting to a list with the selected name. Does not persist between rounds.
* 'Lock interface': locks the settings. Hold Alt and click the remote to unlock.
Nanite communications console [edit]
A remote control used to send custom messages to the Skull Echo, Forced Speech, and Hallucination (Messages only) programs. The settings are very similar to those of the Nanite remote control. The difference is that you set Communication Code and Message instead of Signal Code and Relay. The installed programs must have the same "Link Code" in order to be able to send them signals from this remote control.
Scope [edit]
If you are wearing a diagnostic HUD, you will see a strip next to the implanted people, which is a nanite volume meter. Nanites usually spend a fraction of their volume while their programs are active. Fortunately, modern technology allows them to integrate with the host's metabolism for replication without interfering with biological processes, resulting in slow but steady growth.
Nanites have a default security threshold at which they will stop using programs that consume nanites. This threshold can be customized individually by entering the Nanite Camera and asking a second person to operate the attached Nanite Camera Control Console. If the swarm reaches population 0, there will be no one left to replicate, and the nanites will be completely removed.
Programming [edit]
A swarm of nanites can contain nanite programs. These programs can have a huge number of effects and are loaded into the nanite swarm in two main ways: manually loading them with the nanite's camera, or synchronizing with cloud backups. Once loaded, programs cannot be modified directly; instead, a copy of the same program with the desired program must be loaded again to overwrite the previous one. There is no limit to the number of programs downloaded, but using too many at the same time usually depletes the nanite population quickly.
Cloud [edit]
Roy Nanita can be installed using Cloud ID. If so, they will copy the cloud backup program every 30 seconds with the same ID if it has been set. Cloud backups are controlled by Cloud Control consoles. They can create new backups (with codes from 1 to 100), as well as load programs from disk into the selected backup. Cloud management consoles also serve as storage, which means that if they are disconnected, they will no longer sync with the connected nanites, and that if all cloud consoles are destroyed, all backups will be lost.
Cloud sync has several advantages over direct camera programming: it can update programs without a second person controlling the camera, it resets programming in the event of a tamper or data corruption, and can be updated remotely by a second person. Of course, the latter part also makes it very risky, as anyone can download malware at any time as long as they have a console to do so.
Nanite programs [edit]
Nanite programs define what the nanites do within the host. They have different categories, from useful to deadly.
Obtaining programs [edit]
Programs are opened through research techweb. Once unlocked, they can be downloaded to Nanite Software Discs at any Nanite Software Center.
Configuring programs [edit]
Programs have several parameters that can be configured using the Nanite Programmer. Just insert the software disc into the machine and set the parameters you want. Note that codes set to 0 are inactive and cannot be transmitted.
Activated: Determines whether the program is started activated or not.
Activation delay: defines in seconds how long the program is not automatically activated.
Timer: Determines the duration of the timer. Disables the timer if set to 0.
Timer Type: Determines what happens when the timer counts down. Has four settings:
Deactivate: deactivates the program.
Self-uninstall: uninstalls the program.
Trigger: launches the program, if possible.
Reset activation timer: If there is an activation timer, it will reset to 0, deactivating the program until it starts counting down again.
Activation code: the code that must be specified to activate the application.
Deactivation code: a code that should signal to deactivate the program.
Trigger code: if the program can be run, the code that must be signaled to run the program.
Kill Code: Code that must be passed to remove the program.
Some programs have additional settings available for customization, such as relay channels or signal codes.
Signal programs [edit]
Nanite Remotes can send encoded signals to nanites. When a swarm of nanites receives a signal, all of its programs react if they recognize the code.
There are four modes that can be set for Nanite Remotes:
* Self-focusing on the person holding the remote.
* Targeting only targets the mob being clicked on.
* The area targets all mobs in sight.
* Relay allows the user to select the relay channel; then the signal is sent globally to all hosts that have a relay program installed for that channel.
Startup programs [edit]
Some programs do not work over time and must run instead. To do this, they can either get a startup code or set a startup timer. Launching a program usually has a recovery time as well as a cost in volume; if these requirements are not met, the program will not work. If the program is not activated, it will also not be able to start, but activating the program is not the same as launching it.
Data corruption [edit]
Events such as EMP or shocks can lead to data corruption in nanite programs, which can lead to one of several different effects:
- Switches the program, deactivating it if it is active, and vice versa.
- Runs the program if it can be started
- Removes the program completely
- Clears all codes, preventing transmission of signals from remote controls or signal programs.
- Converts the program to a damaged version. The crash program depends on the program that was damaged.
Types of nanites [edit]
Nanites fall into several categories.
Utilities [edit]
Programs that interact with the nanites themselves or have common useful goals.

UFO 🛸 or stealth aircraft during a volcanic eruption in the Canary Islands flies in our channel?
🇺🇸"Coincidentally, this morning I came across a very interesting video in a tiktok of unknown shape on a flatbed trailer. The scaffolding in the background piqued my interest, and it's like setting up a Helendale radar section. Also, it's not like the so-called pole cap used for calibration. So if it's not, then what is it...", tweeted user Ruben Hofs.
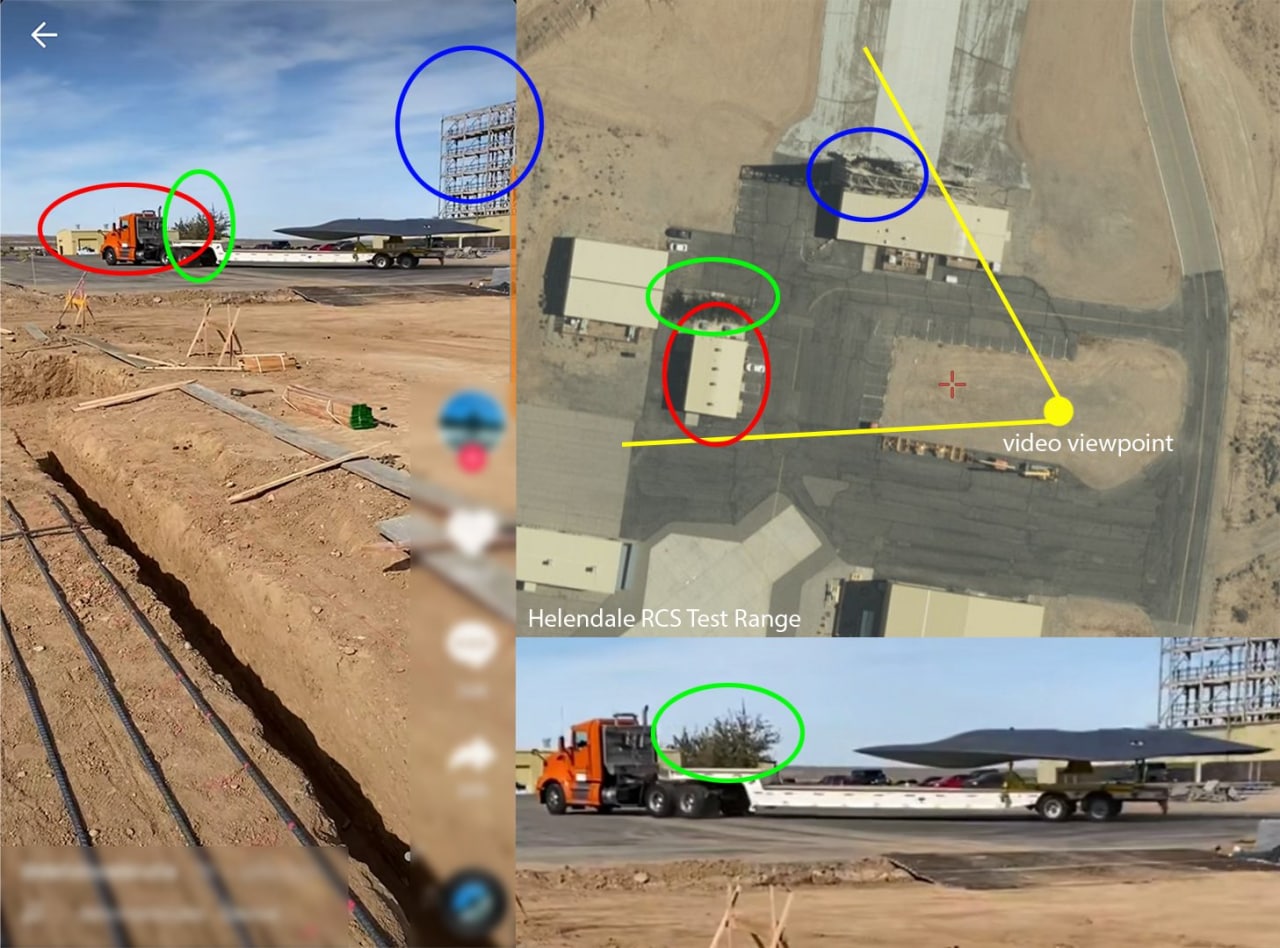
During a discussion with Defense One on Tuesday this week, Lockheed Vice President Jeff Babion was asked if he could comment on the footage. He declined to provide any information about the leak of video footage of an experimental plane at one of the secret facilities in southern California: "I can't." Asked about possible security issues at the facility after the leaked video, he replied: "We are in good shape."
The scale of the genocide is striking in the number of zeros.

A study of official ONS data found that since the Covid vaccine was offered and administered to adolescents in England and Wales, mortality among adolescent boys has increased by 63%, with a 700% increase in just one week.
The Netherlands 🇳🇱 in clashes.
On Sunday, protesters and police clashed in Amsterdam during a rally against a vaccine passport of non-existing COVID19, which was attended by thousands of people under the slogan "Samen voor Nederland" literally "Together for the Netherlands".
There is something to do in the country and it is poisonous to observe.
Wall-to-wall clashes in the form of 17th-century fist fighting began when authorities isolated a group of 50 men in black clothing and with flares from the main march. The scuffle ended when police released the group.
The new Nazi rules, devoid of legislative grounds, provide for a mandatory pass/passport. This false Nazi foot was introduced illegally on September 25 and requires confirmation of false vaccination, or a recent false recovery or a false negative test, mandatory when visiting public places such as movie theaters, restaurants or theaters.
Not buying, not selling without a beast label qR code containing all its attributes, including 666, has become an illegal temporary reality in the Netherlands Richard the lionheart 💔 Rothschild.
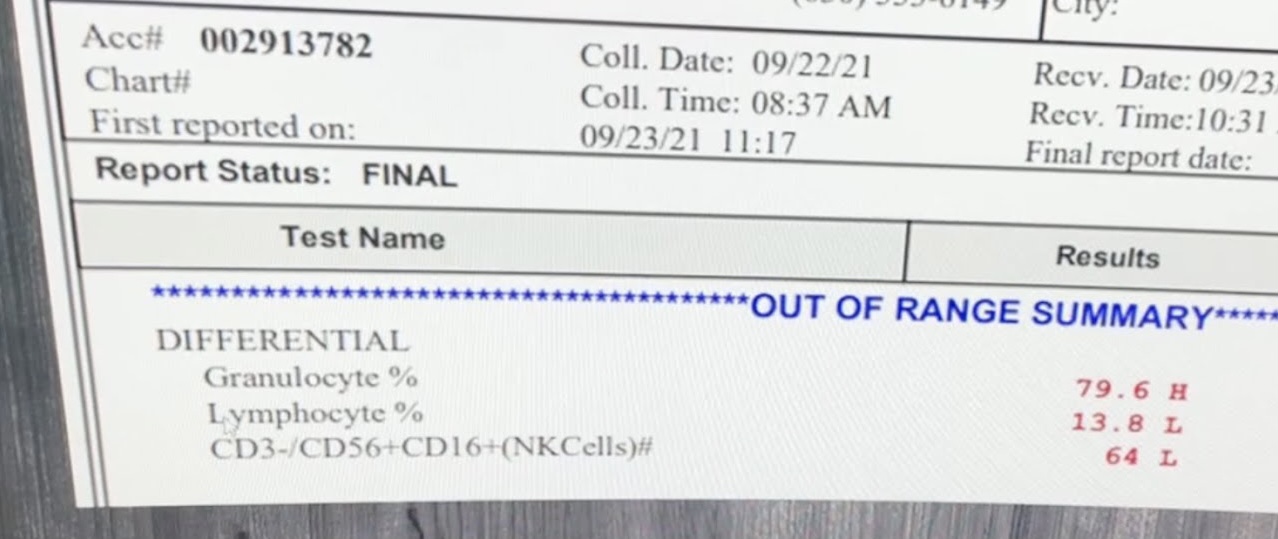
"My jaw dropped when I tested someone's immune system after the 2nd shot."
Dr. Nathan Thompson runs an immune system panel in one of his patients exposed to vaccination. The results are stunning. Vaccinated people will need to live this flu season in a bubble to survive what is coming.
https://t.me/Tribulelouis/13676
📹 My Jaw DROPPED when I Tested Someone's Immune System After the 2nd Jab
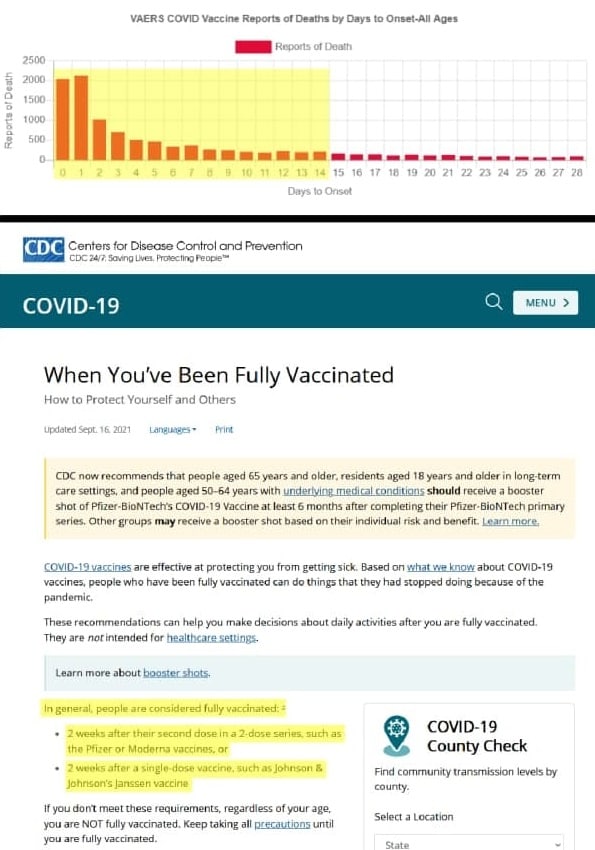
Disposal from CDC SS and it reports ; more than 80% of the side effects of the false COVID19 vaccine in the form of hospitalizations and deaths occur within 14 days of vaccination.
The CDC does not consider people false vaccinated until 14 days after the 2nd dose of Pfizer and Moderna.
In other words, the CDC counts more than 80% of the side effects from the use of false vaccines, hospitalizations and deaths are unvaccinated.
Terrorist sur criminal factors counting on the principle does not matter what to count, the main thing is how to count.
The Church was not involved by chance. A new religion of self-restraint of breathing is being instilled not with a fresh portion of air but with one's own snot and one's own sputum from the lungs and saliva.
https://t.me/Tribulelouis/13722
Singing in a mask is like running around in a gas mask. The military knows this.
If Jesus were there, the first thing he would do would be to ask them to take off their masks.
Now we are surrounded by a lot of absurdity, illogicality and injustice, friends. Remember, the task of each of us in this difficult time to survive and not to lose yourself completely dissolved in the cosmic lies of this panopticon. Let's watch this action in your right mind, even if everyone around you is crazy.
Singing 🎤 and the paradigm of the neo-Marx teachings of Klaus Schwab '' Life will never be the same'' . It is for this purpose that all this terrorist church fornication was filmed beautifully and given online 🕸
Who are these 6 companies that will take over the world after they take off the table and crash the economy, forcing everyone to switch to a social credit system here they are, you read economist freemason magazine, it tells you everything, if you are fond of signs and symbols, they do not explain it, but it is for you to see
Google, Amazon, Tesla, Facebook.

By the way, today Facebook staged a false accident and put their networks thanks to the general plan of terrorists.
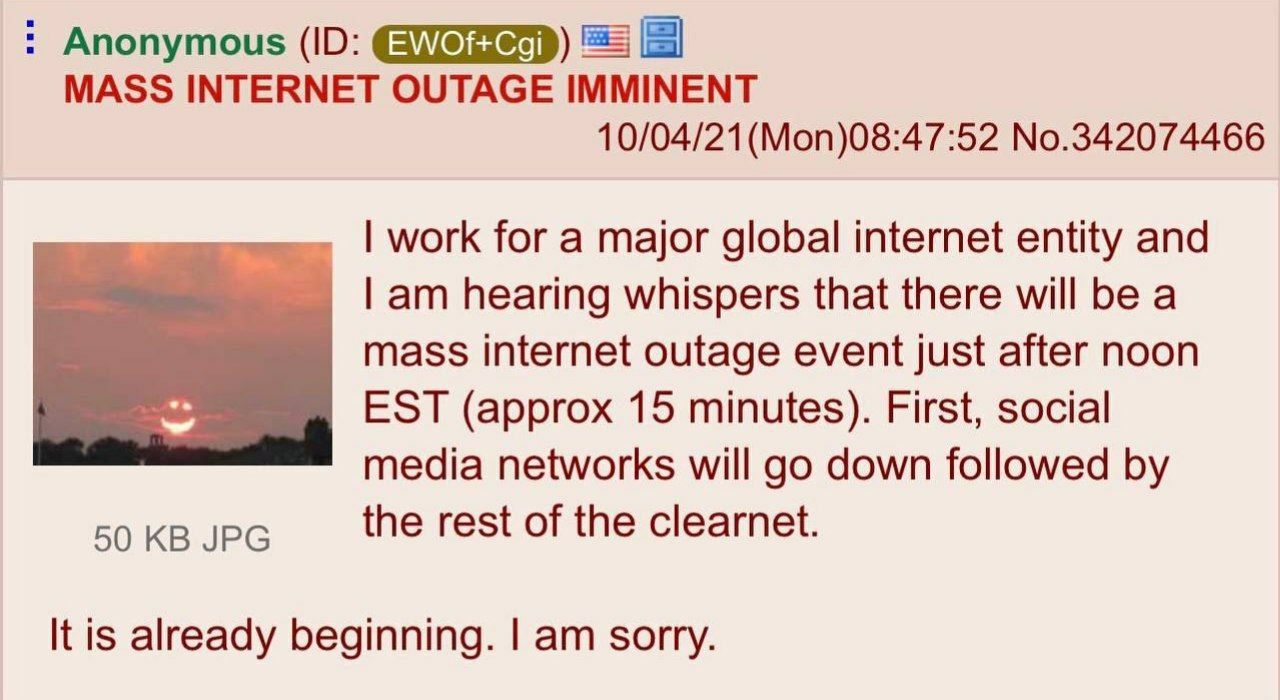
Anonymous 👀
"I work for a global internet company and I've heard talk that there will be a massive internet shutdown right after noon EST (about 15 minutes later). Social networks will be the first to fail, and then the rest of the network will follow.
It's already beginning. I'm sorry."
*****
This post came out on the Q anon forum 15 minutes before Facebook was turned off 😂
How is your Moldavian Lady right hand 🦾 Marx

Mark, can you do anything beautifully? a little freak.
Driven Horses Are Being Shot, Aren't They Being Shot At Is a drama directed by Sidney Pollack about the Great Depression in the United States.
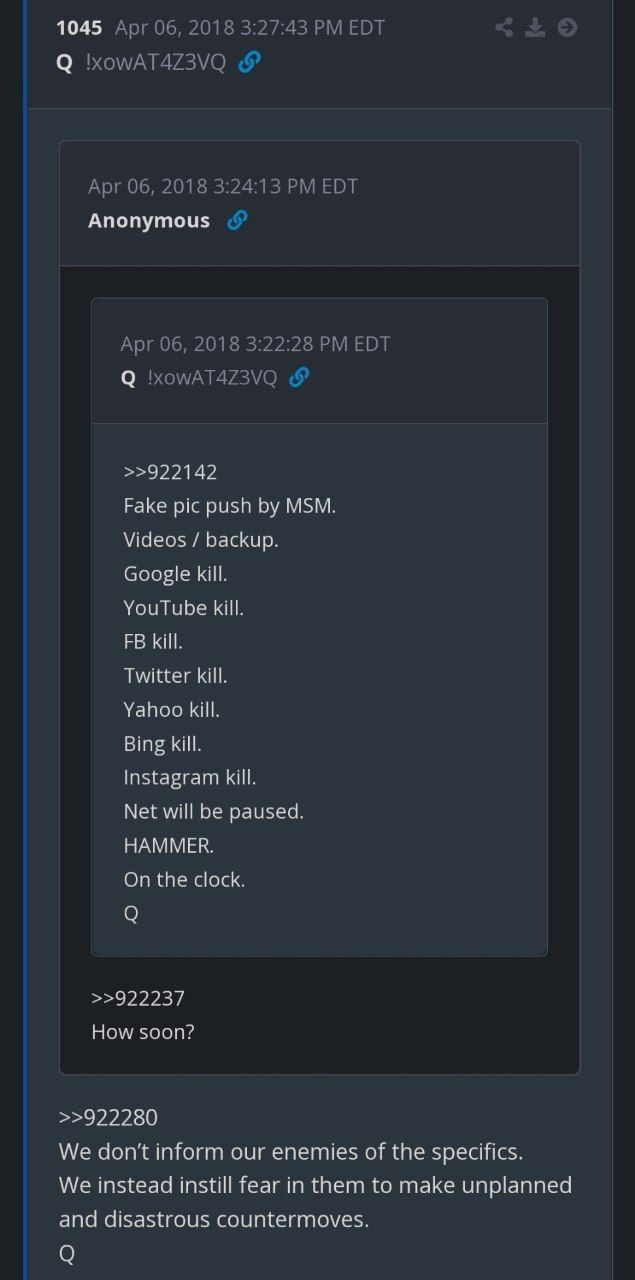
Message Q of April 6, 2018
Fake pictures from the mainstream media
Video/backup.
Google kill.
YouTube kill.
FB kill.
Twitter kill.
Yahoo kill.
Bing kill.
Instagram kill.
The network will be stopped.
BOOM
The clock is ticking
Q
We do not give our enemies details. Instead, we instill fear in them to take unplanned and catastrophic countermeasures.
Q
https://telegra.ph/Crown--19-Mega-Crime-of-the-21st-Century-10-03
https://telegra.ph/IMAGE-OF-DECENT-CORPORATE-FASCISM--21-10-04
@infobrigadengeneral_bot