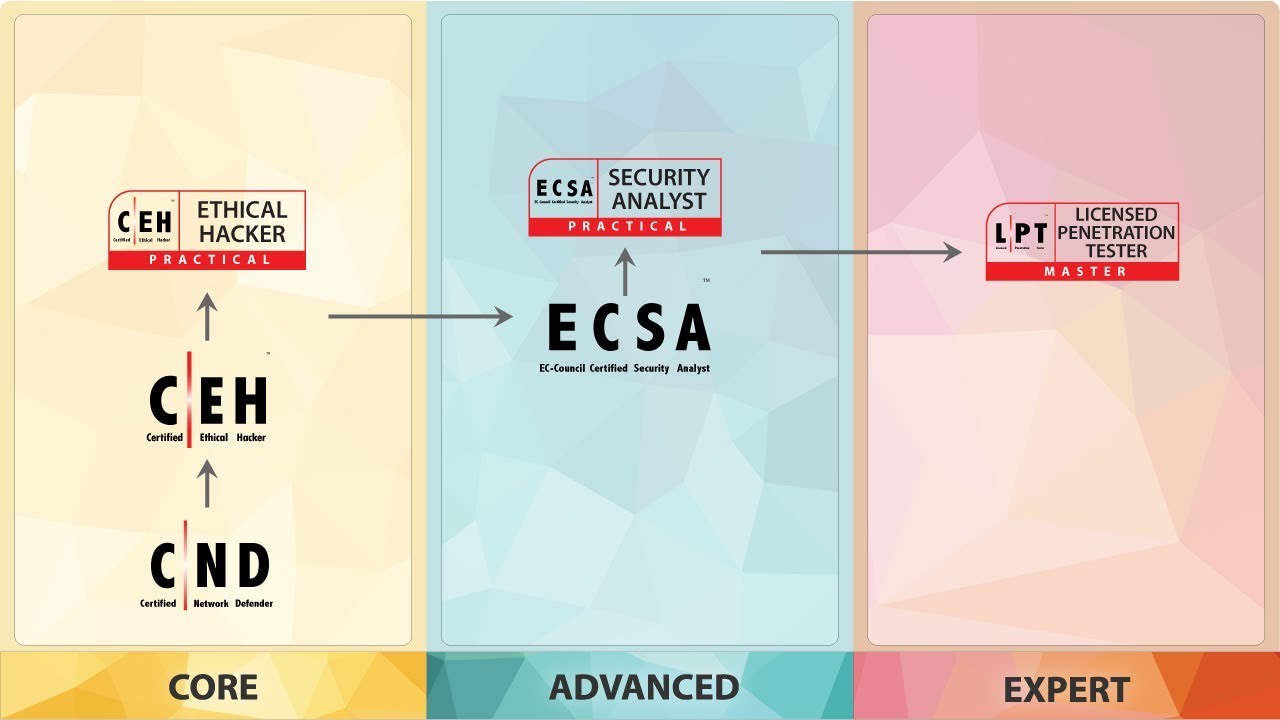
Licensed Penetration Tester Master

🛑 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Licensed Penetration Tester Master
EC-Council Advance Penetration Testing Course Licensed Penetration Tester (LPT)
Introducing the World’s Most Advanced Penetration Testing Program
About CHFI Training Program LPT (Masters)- Licensed Penetration Tester Certification
Certified Ethical Hacker CEH v11 LPT Course Modules
Get Satisfied Before enrollment Join Our Free Demo Session
Ethical Hacking Course Details LPT Program Details
Pick up your phone & register your seat for Cyber Security & Ethical Hacking Training & Certification courses . If you still have any kind of doubts feel free to contact our counselor.
TO KNOW MORE ABOUT Click The Buttons
Still Having Doubt Enquire With Us Now
LPT (Masters)- Licensed Penetration Tester course you will gain knowledge of proficient security and penetration testing skills. The course has been framed lucidly to demonstrate sophisticated notions like scanning against protections, spinning between networks, positioning proxy chains, and using web shells. EC-Council brings about a wide range of real-world obstacles that will not only able to test your Pen-testing skills but assure you and knowledge and expertise that is not built for the feeble persons. If you are interested in this course, you can enroll with us. This chief aim and objective of offering this courseware is to train you for resolving various multifaceted problems. In the true sense of the term, an actual penetration tester resolves the real-world problems and carries out a variety of tasks until it becomes a succeeding nature. This is the core underpinning of the program.
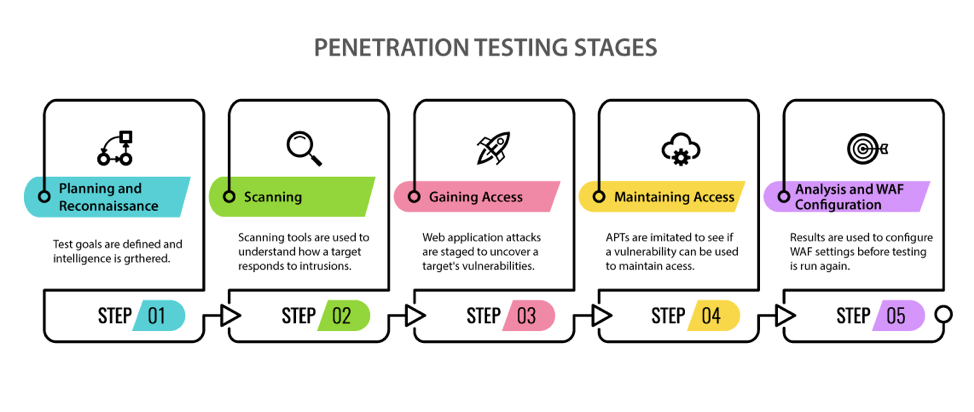
The Most Advanced Penetration Testing Range in the Planet
We Strongly Recommend You to Complete CND , CEH & ECSA Training & C ertification.
Module 01 Introduction to Vulnerability Assessment and Penetration Testing Module 02 Information Gathering Methodology Module 03 Scanning and Enumeration Module 04 Identify Vulnerabilities Module 05 Exploitation Module 06 Post Exploitation Module 07 Advanced Tips and Techniques Module 08 Preparing a Report Module 09 Practice Ranges
Give us a call or drop by anytime, we endeavor to answer all enquiries. We will be happy to answer your questions.
A leading brand in Cybersecurity & Digital Marketing Training & Certification with VAPT services.
Copyright © 2021 by ICSS. All Rights Reserved.
Licensed Penetration Tester | CERT
Licensed Penetration Tester LPT ( Masters ) Certification by Ec-Council
EC-Council Licensed Penetration Tester (LPT) Master
Демо-хак: на PenTest Show покажут, как легко взломать офисную... / Habr
List of computer security certifications - Wikipedia
Join our newsletter
Get the latest news, updates & offers straight to your inbox.
As more organizations turn to penetration testing for identifying gaps in their defense systems, the demand for skilled penetration testers has been growing. While other types of security practitioners can probe information systems and networks for their vulnerabilities, pentesters are highly specialized, trained to think like hackers when exploiting security weaknesses.
CyberSeek (a project of the National Initiative for Cybersecurity Education) included vulnerability analysts/penetration testers on its list of top nine most-in-demand cybersecurity job titles in 2019-2020 for the United States. According to CyberSeek, there were a total of 15,386 total job listings in this field between from June 2019 to May 2020 (out of a total of 507,924). For comparison, there were 33,432 openings for cybersecurity analysts — another mid-level security job that’s historically been one of the highest in demand.
While there’s a shortage of cybersecurity talent in general, penetration testing is one of the jobs that companies seem to have especially difficulty hiring. The (ISC) 2 2019 cybersecurity workforce study showed that penetration testing was one of eight areas where organizations with 500 or more employees were understaffed.
If you’re interested in a career path as a penetration tester , you will need a mix of technical hands-on skills and broad cybersecurity knowledge. Obtaining a specialized certification is one way to gain the technical skills while at the same time proving those skills to a potential employer. Here are some of the options for pursuing a pentesting certification.
The EC-Council (International Council of E-Commerce Consultants) bills itself as the “world’s largest cybersecurity technical certification body.” Their Certified Ethical Hacker cert is a comprehensive certification that is designed to teach you to think like a hacker. The cert is valid for three years.
To be eligible for the four-hour certification exam, candidates must either attend official training or be approved via an application process. You also need two years of experience in the information security field.
The official CEH training program includes 20 modules covering different security domains and more than 300 attack technologies. The program includes more than 140 labs that mimic real-time scenarios and access to more than 2,200 commonly used hacking tools.
The goals of program are to help you to:
Licensed Penetration Tester Master is an expert-level EC-Council certification (by comparison, CEH is considered core, or beginner). Unlike the CEH certification, LPT Master doesn’t have a predetermined eligibility criteria for candidates. Recertification is required every three years.
The purpose of LPT Master is, in the words of EC-Council, “to differentiate the experts from the novices in penetration testing.” Accordingly, the exam itself is 18 hours long. Here’s an overview of the exam:
The Information Assurance Certification Review Board (IACRB) is an industry standard organization that offers a variety of certifications. Certified Penetration Tester is a two-hour exam designed to demonstrate working knowledge and skills for pentesting.
Like other certs from the IACRB, CPT is valid for four years.
Another IACRB cert, Certified Expert Penetration Tester demonstrates expert knowledge in the pentesting field. The IACRB defines an expert pentester as “a person who is highly skilled in methods of evaluating the security of a computer systems, networks and software by simulating attacks by a malicious user.”
The definition goes on to say: “The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known or unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. An expert penetration tester should additionally possess the ability to discover and reliably exploit unknown vulnerabilities in targeted software and systems.”
Like the CPT, the two-hour CEPT exam includes nine domains. However, most of these domains are different from the CPT ones. The CEPT domains are:
Our most popular information security and hacking training goes in-depth into the techniques used by malicious, black-hat hackers with attention-getting lectures and hands-on labs.
Certified Mobile and Web Application Penetration Tester, offered by the IACRB, includes eight domains that are specific to mobile operating systems and web apps. The two-hour exam focuses on:
Red Teams are similar to pentesting, but typically require a larger-scale approach involving more people who are digging a lot deeper than typical pentesters. IACRB offers the Certified Red Team Operations Professional cert for those who want to demonstrate their skills at performing a comprehensive Red Team assessment.
The two-hour exam covers seven domains:
CompTIA’s PenTest+ is a relative newcomer to pentesting certs, but it’s well known in the industry for a host of other IT and security credentials. PenTest+ is designed to test “the latest penetration testing and vulnerability assessment and management skills that IT professionals need to run a successful, responsible penetration testing program,” according to CompTIA.
As with other CompTIA exams, PenTest+ is a combination of multiple-choice questions and hands-on, performance-based ones. The exam covers five basic areas:
The GIAC Penetration Tester (GPEN) credential is one of the pentesting certifications offered by GIAC. Part of SANS, GIAC is considered a leading authority for a variety of certs. GPEN focuses on pentesting methodologies and best practices, as well as legal issues around pentesting. The cert is valid for four years.
During the three-hour exam, candidates must demonstrate knowledge in the following areas:
A higher-level credential from GIAC when compared to GPEN, the GIAC Exploit Researcher and Advanced Penetration Tester doesn’t require specific training or practical knowledge to take the exam. You need to demonstrate that you can conduct advanced pentesting and can model advanced attackers in uncovering significant security flaws. Candidates also need to demonstrate how these security flaws translate into business risks.
The exam focuses on areas such as accessing the network, using advanced fuzzing techniques, exploiting clients and networks, identifying common crypto weaknesses, manipulating networks and using shellcode and Python scripts.
Offensive Security specializes in pentesting training and certifications. The Offensive Security Certified Professional Credential demonstrates a comprehensive mastery and practical understanding of pentesting.
Unlike most other certs, OSCP is 100 percent hands-on and can only be obtained by taking a course from Offensive Security, “Penetration Testing with Kali Linux.” After course completion, candidates take a 24-hour exam that simulates a real-world scenario. The exam consists of a virtual network with different targets that have various operating systems and configurations; candidates are expected to research the network, identify vulnerabilities, execute attacks and then present a pentesting report.
This is only a sample of the options available for pentesting credentials, rather than a comprehensive list. As with any security certifications, you should research all your choices carefully before deciding which one is the best for you. While your skill level may limit which programs you qualify for, other criteria you may want to consider (outside of costs) are recertification requirements, rigor and the industry validation of the credentialing body.
Our most popular information security and hacking training goes in-depth into the techniques used by malicious, black-hat hackers with attention-getting lectures and hands-on labs.
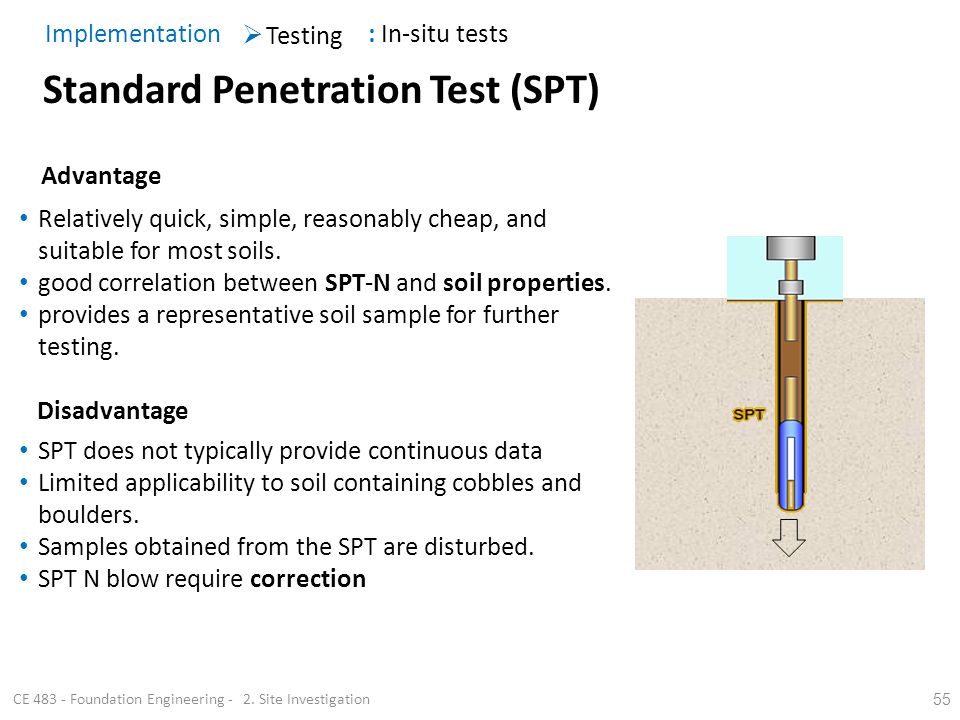
Rodika Tollefson splits her time between journalism and content strategy and creation for brands. She’s covered just about every industry over a two-decade career but is mostly interested in technology, cybersecurity and B2B topics. Tollefson has won various awards for her journalism and multimedia work. Her non-bylined content appears regularly on several top global brands’ blogs and other digital platforms. She can be reached at seattletechnologywriter.com.
Enroll in an Infosec boot camp and earn your next IT or security certification — guaranteed.
Get a first-hand look at the training content, phishing simulations and integrations that make Infosec IQ an industry leader .
Porno Double Penetration Wife
Outdoor Food Ration Calculator
Outdoor Group Anal
Chub Boys Kids Nudist
Porno Double Penetration Wife



















 f_auto" width="550" alt="Licensed Penetration Tester Master" title="Licensed Penetration Tester Master">fl_lossy/wordpress/2018/06/lpt.jpg" width="550" alt="Licensed Penetration Tester Master" title="Licensed Penetration Tester Master">
f_auto" width="550" alt="Licensed Penetration Tester Master" title="Licensed Penetration Tester Master">fl_lossy/wordpress/2018/06/lpt.jpg" width="550" alt="Licensed Penetration Tester Master" title="Licensed Penetration Tester Master">