Doxing and Anti Doxing By Imk
@its_me_kali
Doxing often involves hackers attempting to embarrass or shame individuals by publishing confidential information, images or videos obtained from their personal accounts. Initially, doxxing was used by hackers to "out" the identities of fellow bad actors/hackers. However, more recently, it has been used to attack users with opposing viewpoints.
In a doxing attack, hackers might publish someone's:
👀Real name
👀Telephone number
👀Social Security number
👀Home address
👀Employer
👀Credit card numbers
👀Bank account numbers
👀Personal photographs
👀Social media profiles
How does doxing work
Running a WHOIS search on a domain name
Tracking Usernames
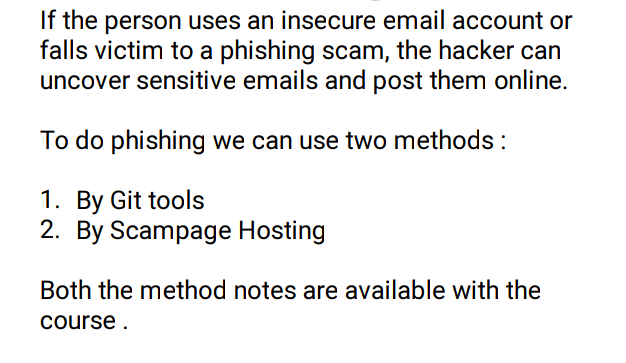
Phishing
Stalking Social Media
Checking Goverment Records
Google Dorking
Tracking IP address
Reverse Mobile phone lookup
Packet Sniffing
Data Brokers(Leaked Data)
Searching on Darkweb
Examples of Doxing
1. Celebrity Doxxing
It’s not uncommon for journalists to find out a celebrity’s personal life information and to publish such gossip on their media platforms. However, doxxing isn’t your regular entertainment news. Here, the hacker publishes the celebrity’s sensitive information such as their payment card info, email address, social security number or phone numbers.
2. Faulty Doxxing
Sometimes, doxxing is done by internet vigilantes who can’t be bothered to properly research or investigate their victims to ensure they have the right person. Instead, they wrongly link people to activities or situations that are unrelated to them. Due to such “faulty” doxing, hence the name, innocent people face:
- reputation loss,
- employment loss,
- harassment,
- physical harm, or
- loss of life.
3. Revenge Doxxing
Sometimes, people use doxing as a means of taking revenge. They publish their enemy’s some publicly identifying information online to cause them shame.
4. Swatting Doxxing
Another method of doxing is known as “swatting.” This occurs when a person wrongly accuses someone of a crime and sends police (or a SWAT team, hence “swatting”) to the victim’s address to cause them harassment. However, often such doxxing can prove fatal for the victim.
5. Crime Doxxing
While the swatting is done for fun, there are some people that use doxxing to execute serious crimes like murder. They reveal their enemies’ personal information online and provoke others to harm them. The motive can be personal revenge or showing disagreement or hatred towards any specific cause, religion, activity or race.
How you get doxxed?
🖤 Username Doxing
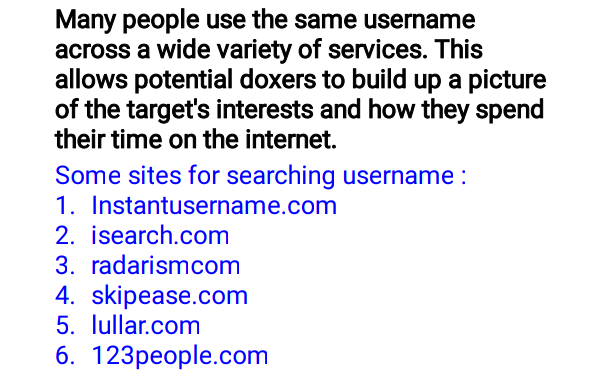
🖤Whois and Domain More
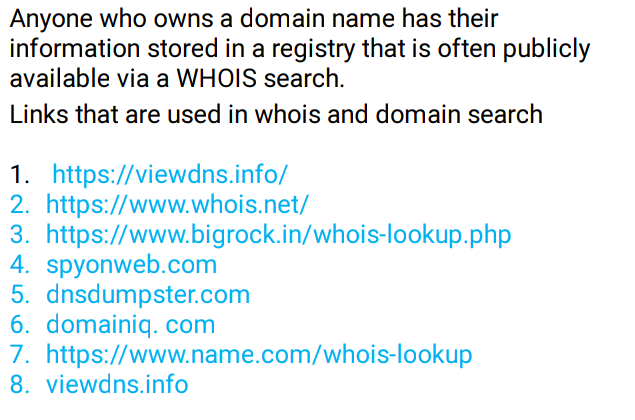
🖤Stalking Social Media
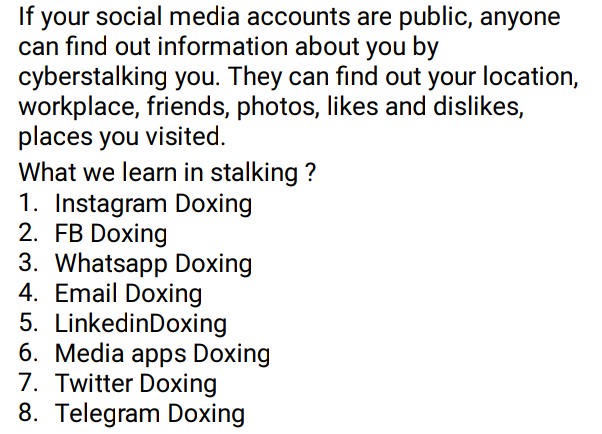
🖤Facebook Doxing
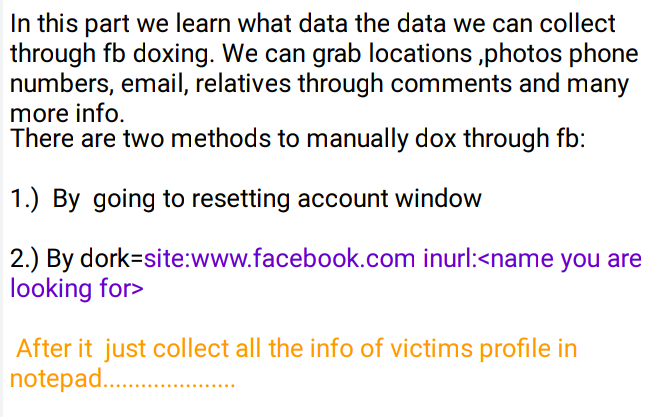
🖤Instagram Doxing
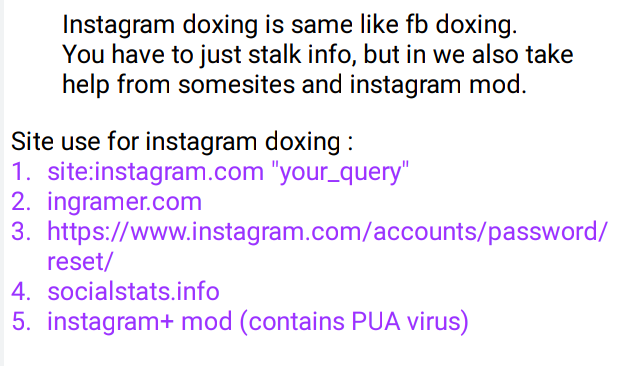
🖤Email Doxing
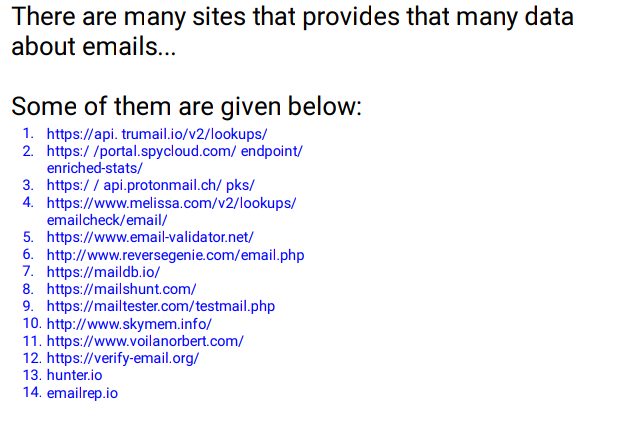
🖤Twitter Doxing
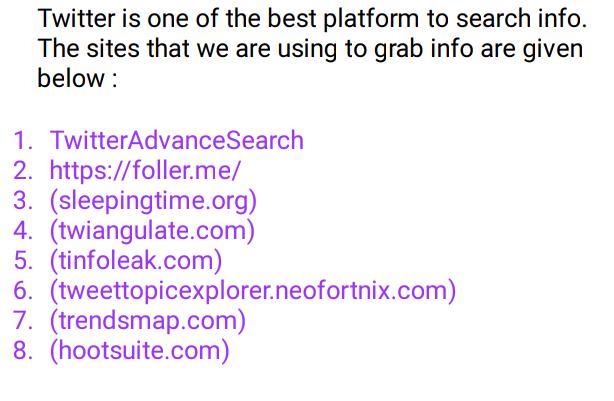
🖤Telegram Doxing

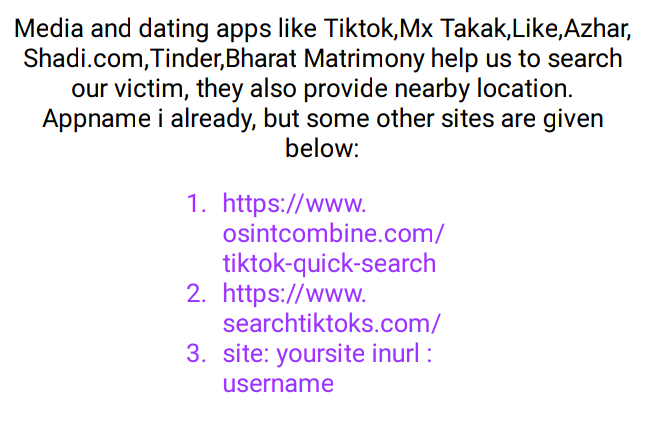
🖤Media And Dating Doxing
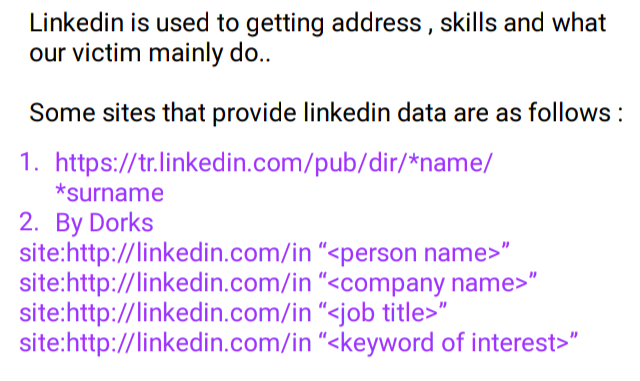
🖤LinkedIn Doxing
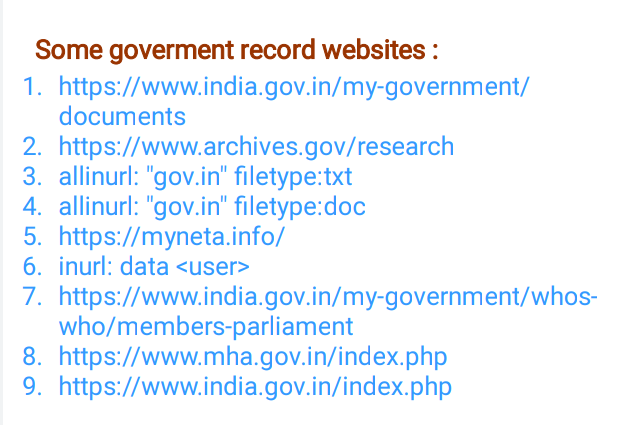
🖤Indian Goverment Data Doxing
🖤IP Locators
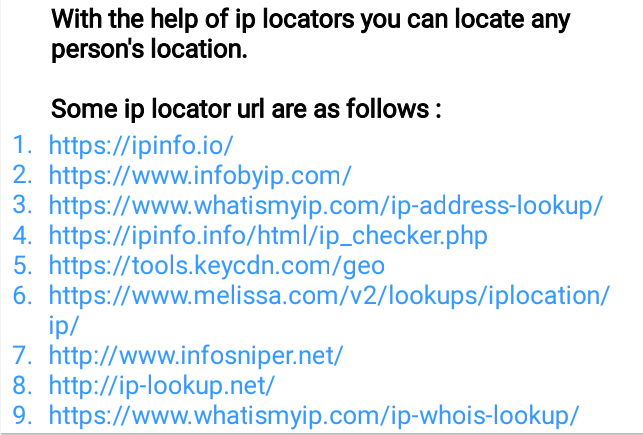
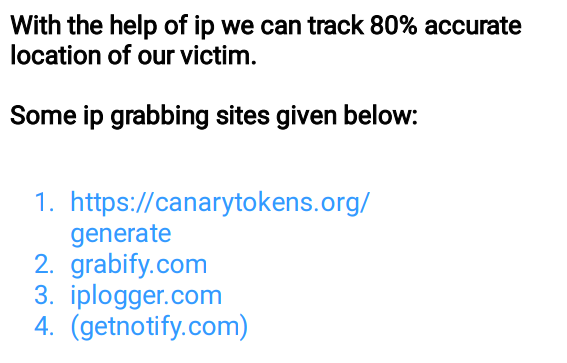
🖤Reverse Phone Lookup
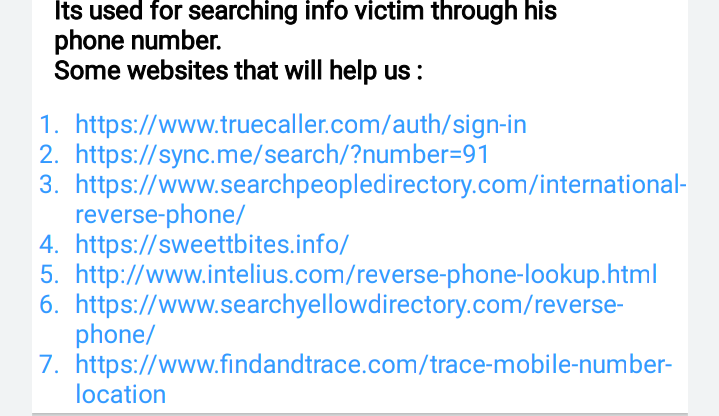
🖤Search Engine Doxing
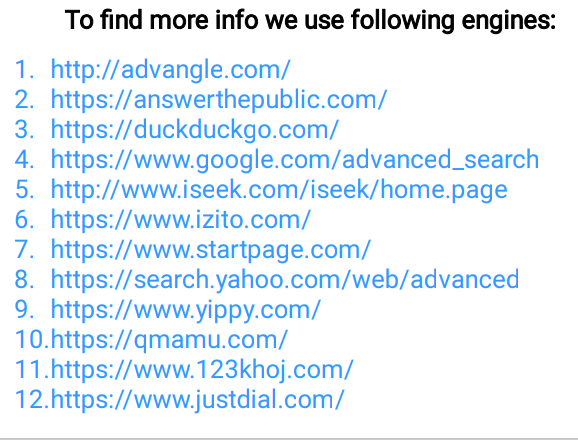
🖤Scientific Search Engine
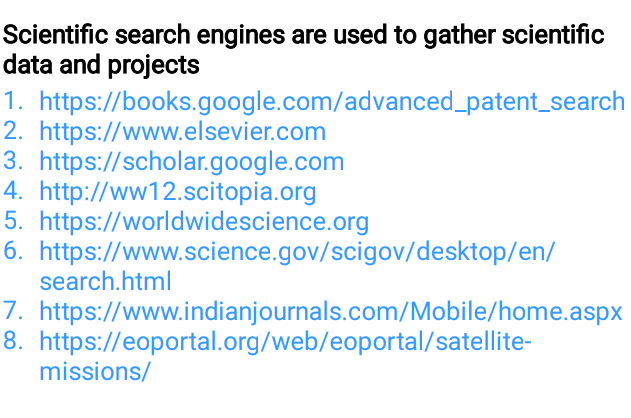
🖤Specific Search Engines
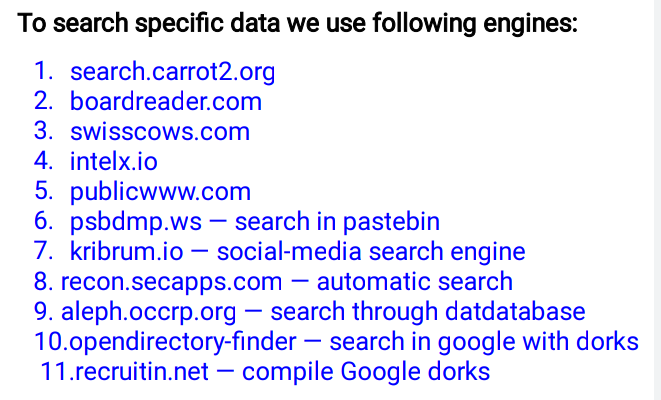
🖤Vehicles Search

🖤Archives Data
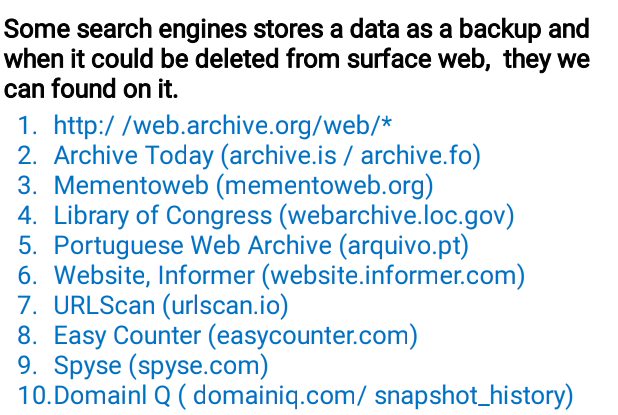
🖤Directories
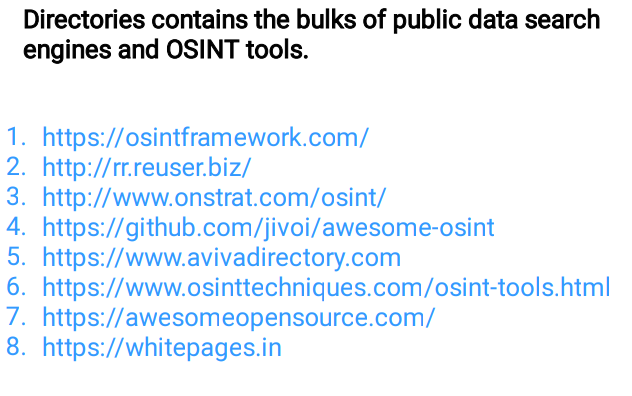
🖤Mac Address

🖤EXIF Data

🖤Company Search
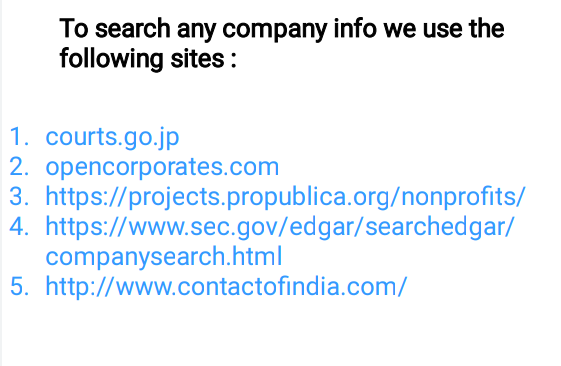
🖤PNG and JPEG Exif
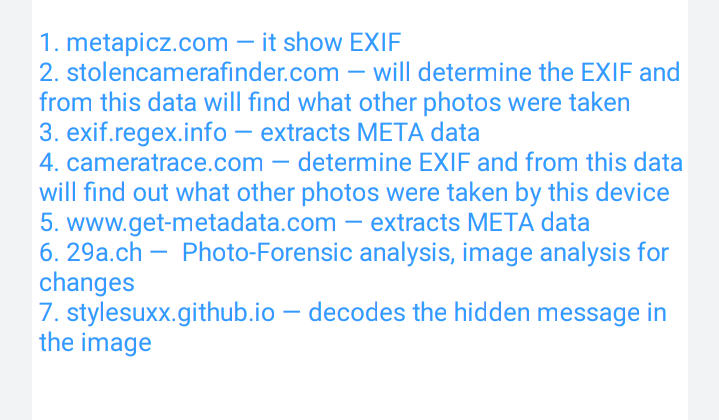
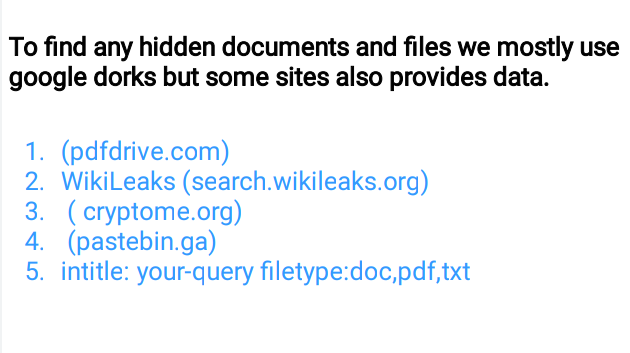
🖤Documents Doxing
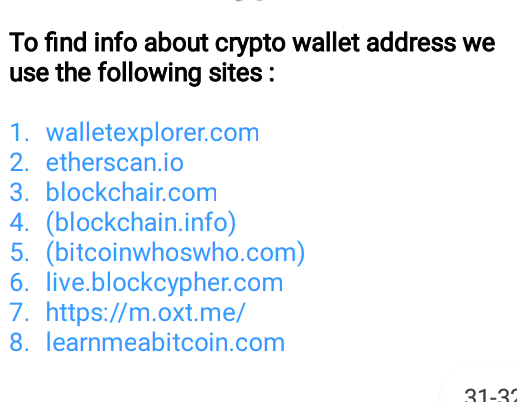
🖤Crypto Doxing
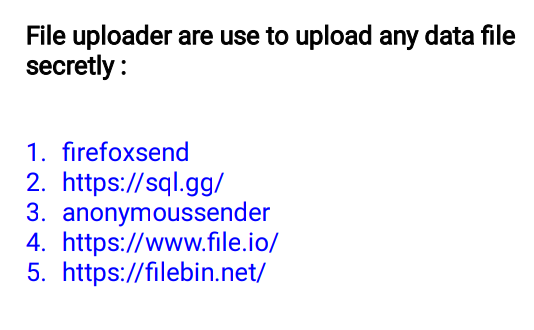
🖤File Uploader
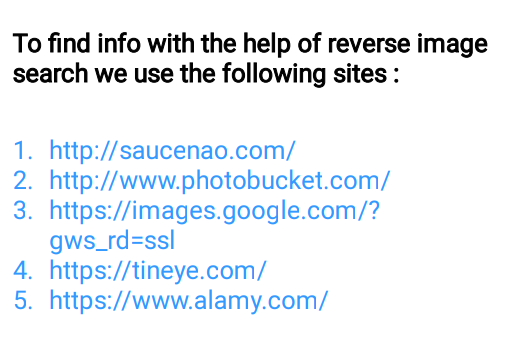
🖤Reverse Image Search
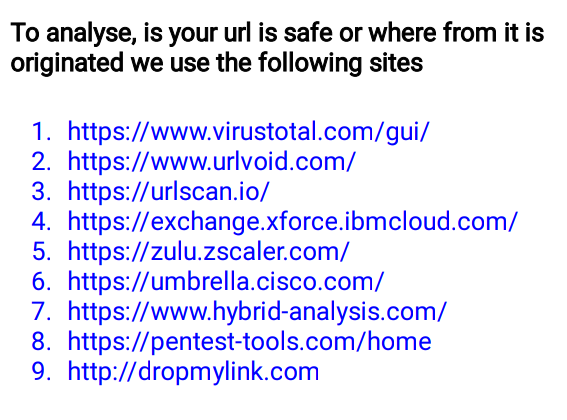
🖤URL Analysis
🖤Ebooks and PDFs

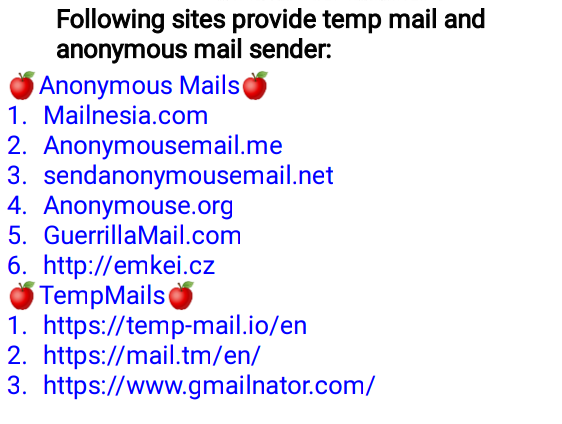
🖤Fake Mails
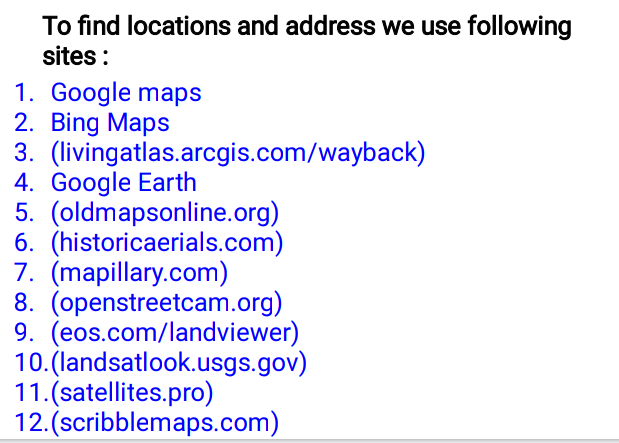
🖤Maps Data
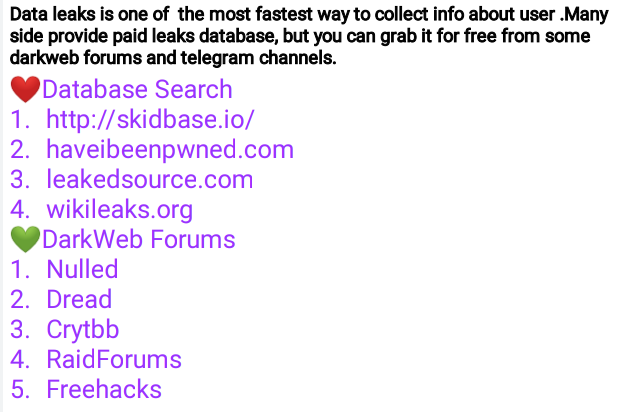
🖤Data Leaks
🖤IOT Search Engines

How to clear your tracks?
While doing doxing don't forget to use vpn,and proxies . Some tools that will help you remove your searches
❤️🔥 Data Destruction Tools
DBAN https://dban.org
The free version supports HDD only.
Eraser www.heidi.ie/eraser/ Open source; supports SSD.
CCleaner www.piriform.com/ccleaner Drive wiper and Windows trace cleaner.
SDelete https://technet.microsoft.com/
en-us/sysinternals/sdelete.aspx
Erases data according to DOD 5220.22-M.
❤️🔥 SSD Data-Erasing Tools
Tool URL
Intel Solid State Drive Toolbox https://downloadcenter.intel.com/download/26574?v=t
Corsair SSD Toolbox www.corsair.com/en-eu/support/downloads
Samsung Magician www.samsung.com/semiconductor/minisite/ssd/download/tools.html
SanDisk SSD https://kb.sandisk.com/app/answers/detail/a_id/16678/~/secure-erase-and-sanitize
How can I protect myself from Doxing?
- Adjust your social media settings:Ensure that your profiles, usernames/handles are kept private
- Remove any addresses, places of work, and specific locations from your accounts
- Set your posts to “friends only"
- Avoid discussing personal information that could be used against you, as well as anything that can identify your address, workplace or contact information
- Use a Virtual Private Network (VPN) and aIf you must use public wi-fi, turn off the public network sharing functionality on your device
- Use strong passwords
- Vary usernames and passwords across platforms
- Hide domain registration information from WHOIS (a database of all registered domain names on the web)
- Don't be afraid after getting doxed its your publicly shared information, so don't worry about it, otherwise attacker use you, don't pay money if you get doxed.
- Be Safe From Cat Phishing
Join CIDINT For More Knowledge
Is doxing is Illegal ?
Doxxing is immoral and illegal, and if you are discovered bothering individuals and disclosing their personal information, you could face serious legal consequences, including imprisonment. Detecting and prosecuting these types of crimes is often challenging for law enforcement.In India you get punishment under IT ACT 2000 for doxing or identity theft.
What is legal Way of Doxing ?
We can say that Open Source Intelligence is the legal way of Doxing.
Intelligence agencies use OSINT to track events, equipment such as weapons systems, and people. These are the 'targets of interest' (ToIs). But hackers use OSINT to identify technical vulnerabilities as well as human targets for phishing and social engineering attacks.Law Firms. Lawyers and private investigators can ethically and legally utilize OSINT techniques – especially information found on social media platforms – in legal and litigation intelligence to collect evidence and research about any suspect or potential juror.
Doxing Method
You will need the following things first before you use this method:
- A last name or first and last name
- A general location.
Social engineer and ask a few questions if you can, to figure out the name, age and general location of someone you are doxing. Ask the person if they are a registered voter also. If they are a registered voter, you can go to voterrecords.com and look them up. In 19 states, voter registration data is publicly searchable record. You can look up people’s voter information if they are a registered voter in these states to get their personal information. Even if the information is not current, it will give you some good information and also show you other people who are connected to that person.
If the person is in a state that is not included, you will probably have to look up the voter lookup sites from their state. You will need a VPN that will protect you from IPV6 leaks like NordVPN or PrivateInternetAccess that also doesn’t log. No IPVanish, HideMyAss, ExpressVPN, Cyberghost.
Once you have their name, date of birth and zip code or county, you can look up their information through that. Each state, county and city is different. Their sites for voter lookup may also be different, asking for different things, in order to access the site including driver’s license/ID number, house number, county, zip code, date of birth or some variation/combination of all. I don’t know how you can find such sites but a simple google search like “oregon voter lookup” or “texas voter lookup” may help you find it. Since those are government sites, it is illegal to access if you are not the person. Which is why you need a good VPN. Some of these sites may block you from access if they detect a VPN but it is unlikely.
If a person is not 18+ and is not a registered voter, you will have to try to get their parents/guardians names for doxing. Since they would be staying with their parents or guardians, you could dox the parents and it would be the same as doxing them.
Through mylife.com you can get birthdates.
Through Whitepages.com , you can get current information.
SearchPeopleFree and True People Search will provide all previous addresses and the general date of birth information (birth month and year). That’s pretty much it for doxing.
Extra Notes:
- You can paste their dox and archive it with web.archive.org/save
- You can paste their dox and archive it with archive.ph
Anti-Doxing Method
You will need to make a fake dox on yourself. If you have an alias, make the dox title your alias and then post the fake dox. React to the fake dox like you have just really been doxed. People will believe that the dox is real. This will keep people, mostly script kiddies, from doxing you in the future as most people are lazy and don’t want to go through the extra work if they don’t have to.
You can generate a fake identity from these websites:
- https://www.fakepersongenerator.com/fake-name-generator
- https://en.namefake.com/
- https://www.random-name-generator.com/
- https://www.fakenamegenerator.com/
You can use this website, to generate a fake photo: https://thispersondoesnotexist.com/ 1
Keep refreshing until you find a face that you like and that AI generated person will be “you”
You will need to go to https://www.ssn-verify.com/generate generate a fake SSN for yourself. This will go in your “dox.”
Once you are satisfied, you can begin making the fake dox on yourself. You can get on a VPN like NordVPN and make some bullshit accounts like a gmail or a fake instagram or twitter account.
Use a password generator for these fake burner accounts.
Put the password to these burner accounts in the fake dox, along with the username. Try to post a little on the accounts first for like a week and make it believable BUT not with any real information that could identify you. For your burner email, you could sign up for a few mailing lists under your generated fake name to make the email account believable.
The last step is to post the fake dox on you. The only real thing in it should be your real/actual alias in the dox title.
if you do it right, people who want to dox you will be easily misled and believe you have actually been doxed.
You should pretend like you were really doxed and that the fake dox is real to give it authenticity.
After that, go to sites like Whitepages, voterrecords.com , spokeo.com , etcetera.
Look up your real information, if it is out there.
Request that your information be removed from their website or concealed.