About Ripter 0.1
This program was created to test the security of personal systems.
Version 0.1 is the first version after beta testing. The program will be updated and supported.
Functional:
1) Remote CMD manager
2) Remote file manager (Upload, create, download and delete files)
3) Get PC information (IP address, local address, processor name, memory size, architecture OS, computer name, version OS, installed versions of the .NET Framework)
4) Process manager
5) Reverse proxy
6) Bypass UAC (x64 payload)
7) Dump the Lsass.exe process
8) Remote machine screenshot
9) Shellcode injection
10) Stealing system process tokens and elevating rights from administrator to system
11) Port scanner
12) Converting PE files to shellcode
13) Automating the launch of shellcodes on a remote machine
At the time of publication of this article, the tool is not detected by antivirus software.
This is accomplished through named pipes and function virtualization. Sandboxes rarely support named pipes and therefore don't see the big picture.
It’s not a bug, it’s a feature!
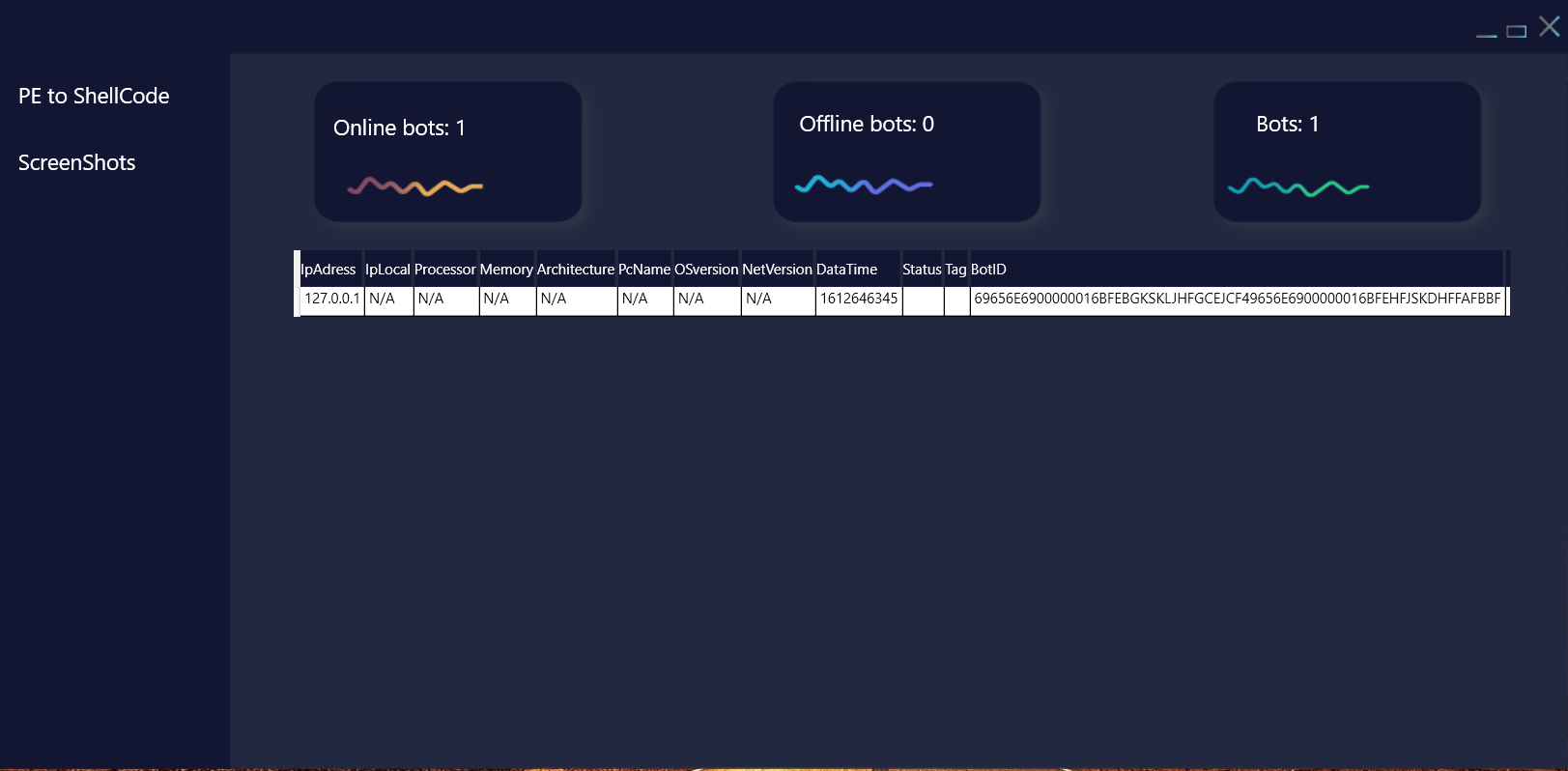
In fig. 2 data about the connected bot is not displayed. To get data (IP, processor, OS, etc.), you need to click on the bot.
The payload contains nothing but communication with other payloads, which are dynamically loaded into memory when needed and unloaded when not needed. This is done to bypass "runtime scan" and make the code short.
Self-Configuration
The program cannot independently communicate with the server. This is done to prevent data transfer protocols from getting into the databases of anti-virus programs. We did everything for you, but you need to connect to the server using any convenient protocol.
Scheme of work:
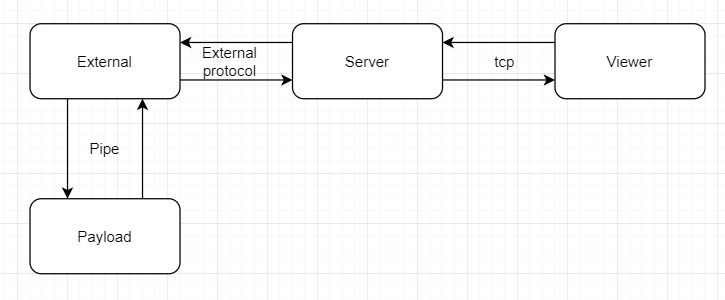
The control panel communicates with the server via the tcp protocol on the port you need. The payload and the server do not communicate directly. Your add-on (the outer block in Figure 3) interacts with the payload through the named pipes and sends information to the server using the protocol of your choice.
Additional material
Generating and running your ShellCode