how-does-passwordless-authentication-work
eregowkbmi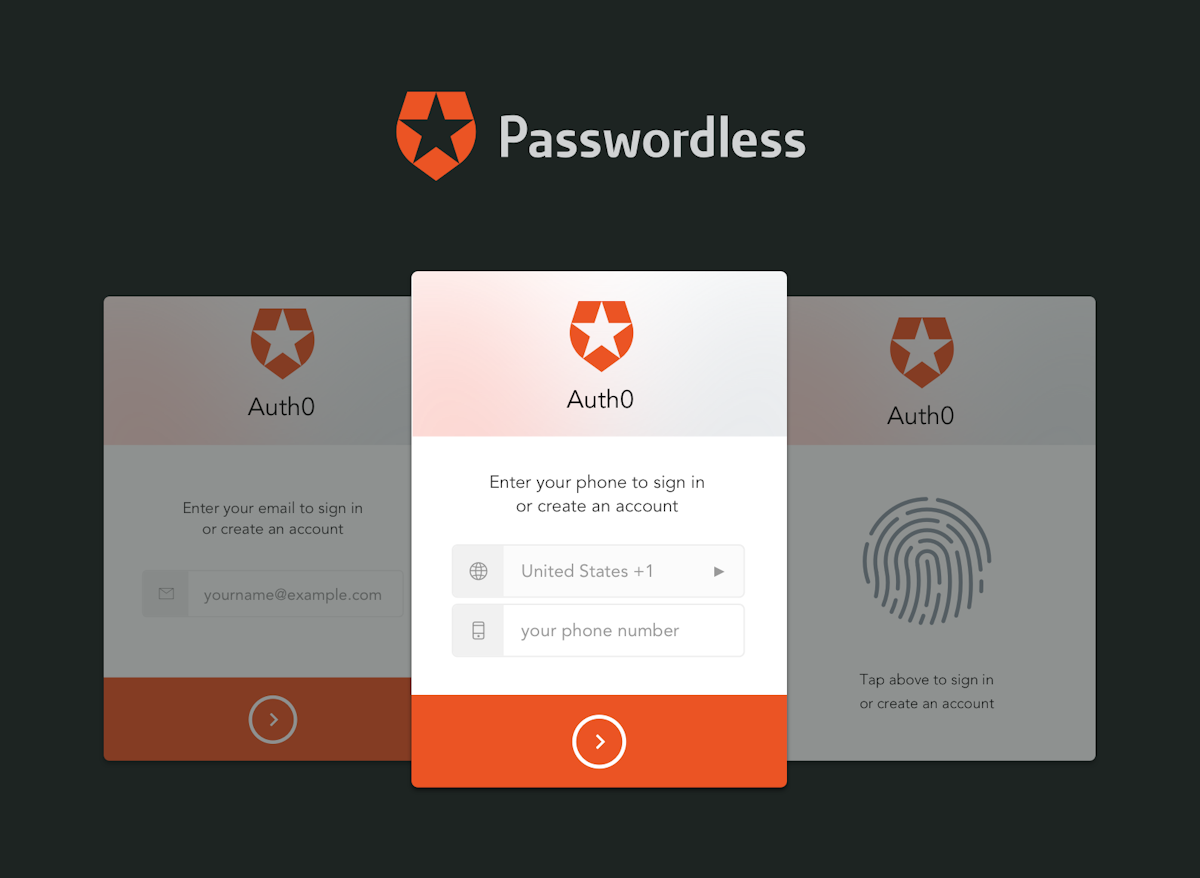
Passwordless authentication is the new buzzword in safe verification for identification and accessibility monitoring (IAM) options. Passwords stay a weakness for consumers and also those attempting to safeguard customer and corporate data. Actually, 81 percent of breaches entail weak or swiped passwords. As well as passwords are the top target of cyber criminals.
First, they need to save the passwords firmly. Failing to do so takes the chance of a violation, which can have a significant impact on the lower line, share worth, as well as the company's track record for several years ahead. Second, when you're the keeper of passwords, you're entrusted with sustaining them, too. That typically suggests taking care of password resets that flooding the helpdesk.
Is Passwordless Authentication Secure?Passwordless verification is a type of multi-factor authentication (MFA), yet one that replaces passwords with a much more secure authentication variable, such as a finger print or a PIN. With MFA, two or more aspects are needed for verification when visiting. Passwordless verification counts on the very same concepts as digital certificates: a cryptographic key couple with a personal and also a public trick.
There is only one secret for the padlock and only one lock for the secret. A private wishing to create a secure account makes use of a tool (a mobile app, a browser extension, etc.) to create a public-private crucial set. The personal trick is saved on the user's neighborhood tool and is tied to a verification variable, such as a fingerprint, PIN, or voice recognition.
Is Passwordless Authentication Secure?The general public key is given to the site, application, web browser, or various other online system for which the individual wishes to have an account. Today's passwordless verification depends on the FIDO2 standard (which incorporates the WebAuthn and the CTAP requirements). Utilizing this criterion, passwordless authentication frees IT from the problem of protecting passwords.
Like a padlock, if a cyberpunk gets the public trick, it's useless without the personal key that opens it. And also the private secret remains in the hands of the end-user or, within an organization, the staff member. One more advantage of passwordless authentication is that the user can select what tool he or she makes use of to produce the secrets and authenticate.
Best Passwordless Authentication Software In 2020
It may be a biometric or a physical device, such as YubiKey. The app or internet site to which the customer is verifying is agnostic. It doesn't care just how you produce your essential set and verify. As a matter of fact, passwordless authentication relies upon this. For instance, internet browsers implementing passwordless authentication may have JavaScript that is downloaded and install when you see a page which works on your maker, yet that script belongs to the web site and also does not keep your crucial information.
As a multi-factor verification approach, passwordless authentication will certainly proceed to evolve. A lot of organizations still utilize typical passwords as their core authentication technique. Yet the broad as well as well-known issues with passwords is anticipated to significantly drive businesses using IAM towards MFA and also towards passwordless verification.
Passwordless Authentication Guide
Passwordless authentication is an authentication approach in which a user can log in to a computer system without the going into (as well as remembering) a password or any various other knowledge-based secret. Passwordless authentication relies upon a cryptographic crucial set a personal and also a public secret. The general public secret is offered during enrollment to the confirming solution (remote web server, application or internet site) while the private trick is maintained on a user's gadget and also can only be accessed when a biometric signature, hardware token or various other passwordless aspect is presented.
Some layouts might additionally approve a mix of other variables such as geo-location, network address, behavior patterns as well as gestures, as so lengthy as no remembered passwords is included. Passwordless verification is sometimes confused with Multi-factor Authentication (MFA), because both use a wide range of authentication variables, however while MFA is used as an added layer of safety and security on top of password-based authentication, passwordless authentication does not call for a remembered secret as well as generally uses just one extremely secure aspect to verify identification, making it much faster and less complex for customers.
Use Passwordless Authentication To Improve Security
The notion that passwords need to lapse has actually been circling around in computer system scientific research since a minimum of 2004. Bill Gates, talking at the 2004 RSA Meeting anticipated the demise of passwords claiming "they simply do not satisfy the challenge for anything you really wish to secure." In 2011 IBM predicted that, within five years, "You will never need a password again." Matt Honan, a journalist at Wired, who was the target of a hacking case, in 2012 composed "The age of the password has actually pertained to an end." Heather Adkins, manager of Details Protection at Google, in 2013 claimed that "passwords are done at Google." Eric Grosse, VP of security design at Google, mentions that "passwords as well as easy holder tokens, such as cookies, are no longer enough to keep individuals secure." Christopher Mims, writing in the Wall Surface Street Journal claimed the password "is lastly dying" and also predicted their replacement by device-based verification.
Now they are a lot more than dead. The factors given often include recommendation to the usability in addition to security problems of passwords. Bonneau et al. methodically contrasted internet passwords to 35 contending verification systems in terms of their usability, deployability, as well as protection. (The technological record is an expanded version of the peer-reviewed paper by the exact same name.) Their evaluation reveals that many systems do far better than passwords on security, some schemes do much better and also some worse with regard to use, while every system does even worse than passwords on deployability.
What Is Passwordless Authentication?
Leading tech business (Microsoft, Google) and also industry large initiatives are creating far better architectures and also techniques to bring it to wider use, with several taking a cautious approach, maintaining passwords behind the scenes in some usage cases.