"Buckets" are containers for storing data in cloud storage
Cyber Detective • @cyb_detective"Buckets" are containers for storing data in cloud storage.
It often happens that, due to inattention of the owners, "buckets" that contain personal data end up in the public domain.
Examples, tools for finding "sensitive data" and security tips in this thread 🧵 [#1]

In March 2021 Daniel Niv published a study that Azure cloud servers hold millions of files with "sensitive data" that their owners made public by accident.
cyberark.com/resources/threat-resea…
The research team scanned 200 million storage accounts and found 100K, which contain sensitive data [#2]
In particular, they found:
2,5 millions records of Personally Identifiable Info
Personal Health Info (2,300 files)
Financial Data (2000 files)
Invoices (1 million)
Agreements, Contracts, and Assets Structure Plans (more than 1 million)
Log Files
Encryption Keys and Passwords [#3]
the above-mentioned article recommends using the #opensource tool github.com/securing/DumpsterDiver for search volumes of data from cloud storages to check if it includes secrets in it. [#4]
Also researches recommend use their own tool github.com/cyberark/BlobHunter for checking specifically Azure Cloud Storages. [#5]
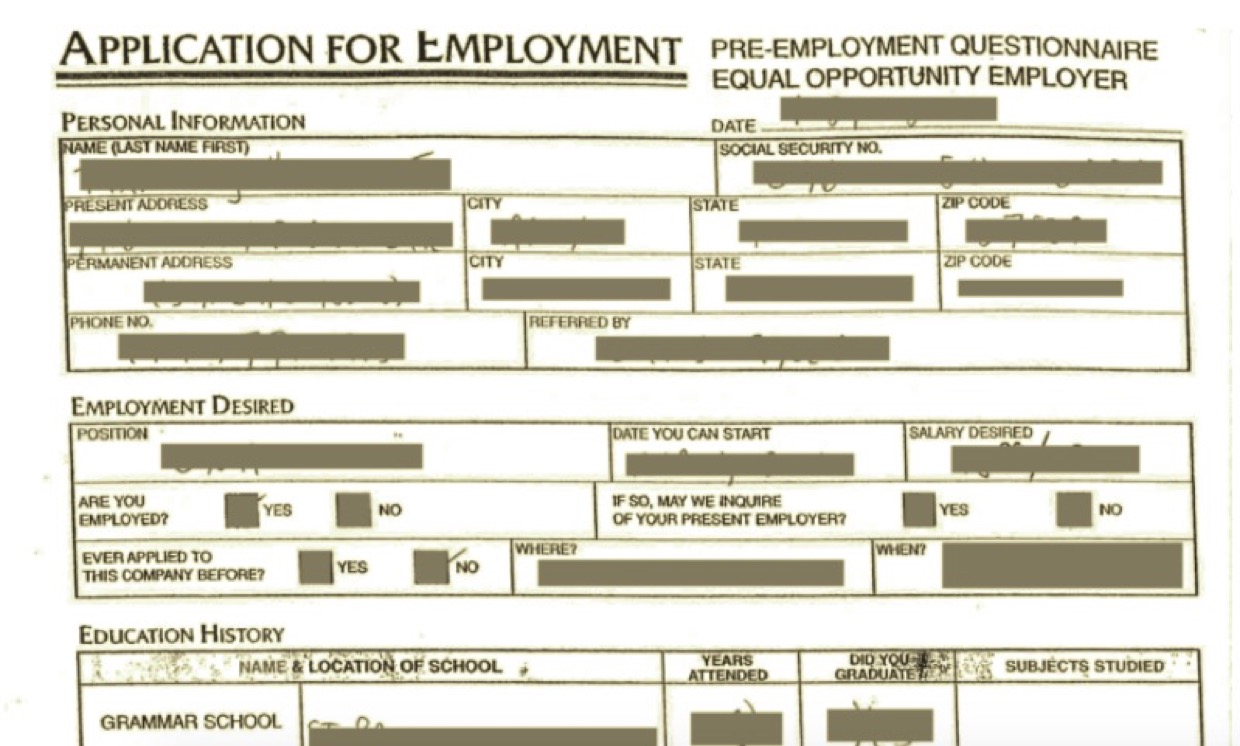
Online tools can also be used to search for sensitive data in the buckets. Here's a link for Amazon AWS:
buckets.grayhatwarfare.com (creator @grayhatwarfare)
the picture shows an example of private data found by the "invoice" query [#6]
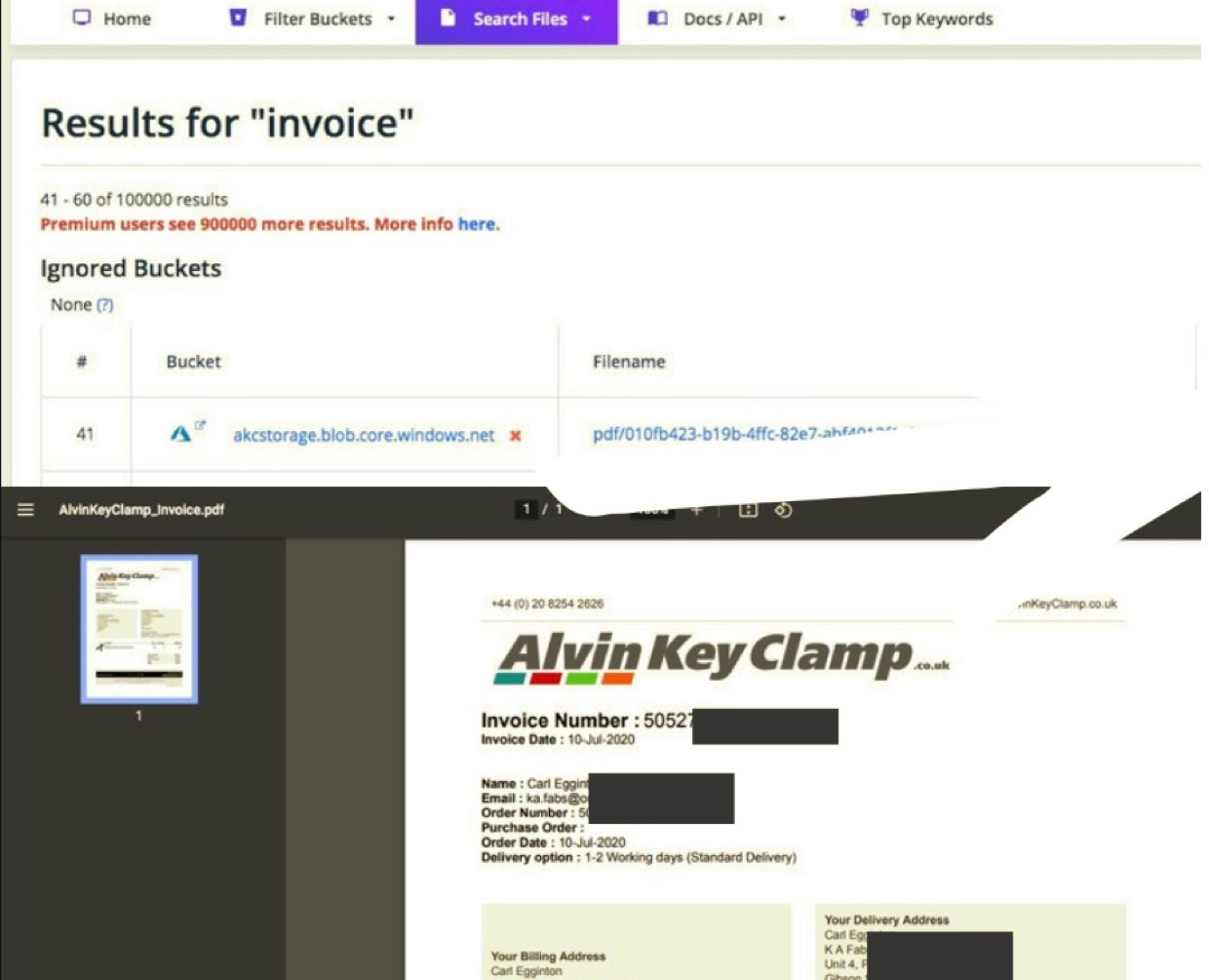
And here is a service for searching Microsoft Azure files:
osint.sh/buckets
The picture shows an example of the found list of users of the service by the query "users/csv" [#7]
There used to be a similar tool for Google buckets called DataDrifter.
But today it no longer works (perhaps temporarily)
(pics from andreafortuna.org) [#8]

For Google Storage research it's possible to reccomend GCPBucketBrute (script to enumerate buckets, determine what access you have to them, and determine if they can be privilege escalated).
github.com/RhinoSecurityLabs/GCPBuc… [#9]
Sensitive data in the bucket can also be searched using Google Dorks. For example:
"site:s3.amazonaws.com filetype:xls password"
This topic is covered in more detail in the article:
justhackerthings.com/post/hunting-f… [#10]
And finally, links to pages in the documentation where you can find out how to check if your cloud storage contain public buckets:
Amazon —docs.aws.amazon.com/AmazonS3/latest…
Azure — cloud.google.com/storage/docs/acces…
Google — docs.microsoft.com/en-us/azure/stor… [#11]
This thread is end.
You may use threadreaderapp.com (@threadreaderapp) for comfortable reading. [#12]