Www Private Co

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
Everyone's sensitive data in the cloud is at risk! Quantum computers will have the processing power to break the classical encryption codes that now secure your files, healthcare and financial records, your corporate or personal confidential documents.
How it Works
We designed our revolutionary cybersecurity layer with an innovative patented approach
A process on the client-side that begins by applying AES 256-bit encryption to the user’s original data set and then performing All-or-Nothing transform. Finally, Private.me’s proprietary Information Dispersal Algorithm (IDA) is applied to the output to produce multiple slices of random data sets that is effectively hack-proof or “theoretically secure”.
Our Information Dispersal Algorithm (IDA) is the next-generation cryptosystem that is “theoretically secured” and extremely efficient. The output IDA data sets are indistinguishable from random data sets and therefore mathematically impossible to penetrate. Your data is fully protected when the three data sets are in transit separately and when they are at rest stored separately at three remote locations. Our IDA process is transparent and can be audited by third parties at any time.
In the event that a sliced data set is unavailable for retrieval or it has retrieved a corrupt payload, the original data remains safe. In order to re-create the original data set, a minimum threshold (2 out of 3 slices) is required to be reassembled to re-create the original data set. To protect each data set, the platform leverages Kerberos based authentication system in four “realms” or independent authentication authorities - Private.me central server plus the three storage nodes. To ensure none of the four services can retrieve a threshold of slices, a series of sophisticated cryptographic safeguards are kept in place. Please ask for our whitepaper for more information.
Our technology is ideal for scenarios wherein an organization has cloud storage needs but prefers not to extend full trust to a third-party remote data storage provider for safekeeping and access control enforcement. Our algorithm provides assurance against even a server system administrator compromising the data. This user protection extends to three areas: denial of legitimate access, tampering, and unauthorized decryption.
Building a cloud document or data storage product with the Private.me platform solves the problem of trust of remote servers, specifically by removing the need for blind trust. Private.me uses a secure in-depth, layered approach involving not only end-to-end data encryption but also cryptographic data dispersal adding significant security assurance to cloud storage. The system works by encrypting and securely slicing data on the client-side, then uploading the slices to separate cloud servers. Successful retrieval and decryption later require access to multiple servers to retrieve slices for decryption. Without the successful threshold, the data is immune even to brute force attempts to compromise it.
With email and other common messaging technologies are widely known to be subject to potential vulnerabilities, businesses need alternative channels to encourage best practices and safeguard restricted and sensitive information. With disparate systems, this is a difficult or impossible task to accomplish securely. However, a communication tool built on the Private.me platform uses the strong guarantees of end-to-end encryption and rigorous user authentication to safeguard data in transit. Even the intermediate cloud application hosts involved in transmitting messages are unable to decrypt a message - only intended recipients have access.
Key storage and management reflect a special case of the Private.me cloud approach that benefits from the secure data dispersal technique. By cryptographically splitting mission-critical keys for dispersal across multiple hosts, an organization can benefit from the same kind of distinct assurances used in the most critical national defense contexts, such as missile silo key protocols. In this case, the secret cryptographic keys are protected even in the event of a compromise of one of the storage servers due to the strong cryptographic slicing algorithm. Gaining access to only one slice does nothing for an attacker - a valid threshold is required to decrypt the key.
Documents and data stored in either workstations or servers on-premises are at risk from ransomware, which can spread rapidly through an organization and effectively destroy critical data. Documents and data stored in the Private.me cloud are insulated from any on-premises attacks. In addition, the use of the Private.me cloud's key escrow service protects in the event of a total loss of client-side data, which could otherwise be a loss due to end-to-end encryption.
Secure your cloud service for your customers! Build on our hackproof backend storage and cummunication platform. Our API makes it easy to preconnect to your existing application.
Secure your cloud service for your customers! Build on our hackproof backend storage and communication platform. Our API makes it easy to connect to your existing application.
Deploy it on your private cloud infrastructure with complete autonomy. This solution is ideal for Storing highly classified data.
A hybrid model by combining your private cloud infrastructure with a public cloud provider such as Amazon AWS. It achieves the same level of security as private cloud deployment but can be more economical upfront.
Build on our hackproof backend storage and communication platform. Our API makes it easy to connect your existing application to working with all top storage providers.
Case Study: VaultDrop
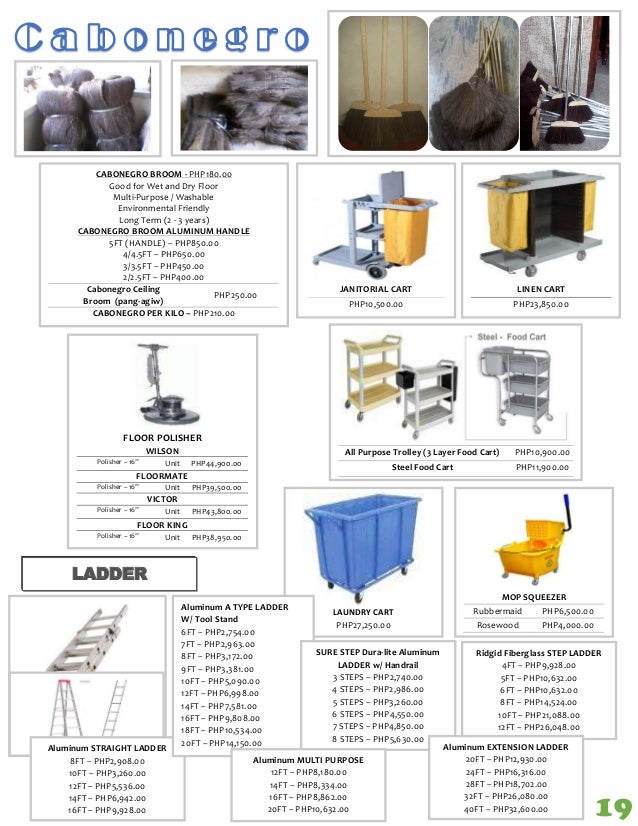
Powered by Private.me
VaultDrop leverages Private.me's full suite of developer solutions, including its patented data encryption and dispersal cloud storage services, as well as its identity management and single sign-on (SSO) service.
VaultDrop provides an ultra-secure cloud storage alternative to Dropbox, Google Drive, and Box.
Address:
5461 West Jefferson Blvd.
Los Angeles, CA 90016
USA
Open to Government Agencies
NAICS: 518210
©2021 Private.me. All Rights Reserved. Privacy Policy and Terms of Service.
AJ Esmailzadeh is founder and president of Private.Me and Private.Co, which create solutions that offer the most secure cloud storage in the world. He wanted to develop a solution where the end user is the only trusted party, not the cloud service providers, its employees, or worse yet, a hacker which under an unlikely circumstance, has gained control over the service provider’s system. The solutions are delivered via a revolutionary, patented cloud-based platform, which allows users to disperse data.
AJ is the Co-Founder & Vice President of EEMA Lighting Group, and President of Lumenton Lighting division. EEMA is based in Los Angeles, and serves North America. Since its inception, EEMA products have been installed in homes, public schools, universities and internationally-known hotels, including the Marriott, Hyatt, and City Center in Las Vegas.
AJ has many philanthropic interests, as well. He is the Chairman of the board for Angel Harvest, a non-profit organization based in Los Angeles feeding the needy. Since his involvement, the organization has delivered one million meals to the poor. He was also board member of Ohr Khaim Hashalom, a nonprofit organization that has provided 20+ housing to homeless families from the Rescue Mission. In addition, he serves as a board member of International Villas HOA, a Home Owners Association of 72 quadplex buildings.
Jacques Kempin is an innovator and entrepreneur that lived in France before he moved back to the USA in 2012.
While he was still a student at a French University, he developed and showcased the first interactive program gathering the collections of Louvre Museum for the inauguration of the Grand Louvre in 1989. In the early 90s, as the CTO of a subsidiary of the France Telecom Group, he also implemented the Louvre first CD-ROM, the first Virtual Reality tour of the museum, and the Museum’s educational website. He co-created a collection of cultural programs for the Orsay Museum, Picasso, Rodin, Flemish painters, Mythology and the Châteaux of the Loire Valley among others.
Jacques Co-Founded VeePee in 2000, a Telecommunications Infrastructure (IaaS) and Cloud Solutions Service (SaaS) Provider offering a wide range of services tailored to market demand, in all critical fields of Information System: security, storage, IP telephony, groupware, video conferencing, cloud computing, secure transmission. At VeePee, he created three secure file sharing applications: “Post”, one of the first web-based solutions, “Transfer”, an FTP based solution with simplified advanced web administration, and “Box”, a Peer to Peer environment integrated with the Workflow of the Press and Media industry.
While in France, Jacques was also a teacher for Product Design, Development & Distribution at ENSAD (Decorative Arts), ENSBA (Beaux-Arts) and University of Paris V (René Descartes).In the United States, he is the founder and CEO of Synaptiks, where he helped numerous companies with strategic planning and corporate development.
Jacques is also a Partner at Zeno Capital, a Venture Capital and Private Equity company based in New York.
Paul Hershenson is the Co-Founder of Art & Logic, Inc. a 23-year-old, Los Angeles-based custom software development firm. Paul has grown Art & Logic from a three person operation into a company with 75 developers working from home offices throughout North America. Art & Logic has served over 900 clients in a wide range of industries, from within the Fortune 500 to innovative startups. Art & Logic clients include Apple, Google, Motorola, HP, Disney, NBC Universal, The Discovery Channel, Space X, and many more. During the early years of his career, Paul pioneered the digital audio editing techniques that are used in all professional music software products today.
Dr. Stahl is a pioneer in the field of information security, having entered the field in 1980. He began his career securing teleconferencing at the White House, databases inside Cheyenne Mountain and the communications network controlling our nuclear weapons arsenal. As President of Citadel Information Group, he brings this experience to business, government, and the not-for-profit community.
Dr. Stahl excels at helping his clients develop and implement information security management strategies consistent with their unique information security responsibilities, their business realities and their cultural circumstances. This unusual management capability was developed through a career filled with growth, innovation and achievement in the management of technology and its strategic integration into the organization. Dr. Stahl has honed his craft not only through his extensive experience in the management of information security but also through his experiences as (i) COO of an online management education and training company, (ii) a strategic management consultant specializing in business performance, (iii) a software engineer, (iv) a research scientist and even (v) a mathematics professor.
Dr. Stahl earned his Ph.D. in mathematics from The University of Michigan and spent nearly 15 years teaching university mathematics. Once an active researcher, Dr. Stahl has published more than a dozen papers in advanced mathematics and computer science. He has taught courses in information security, software engineering, project management and computer programming at several universities and colleges. He recently served on the faculty at the University of Southern California in the School of Engineering’s Information Technology Program.
A few highlights from Dr. Stahl’s information security portfolio:
David Lam has 32 years of IT experience in positions of increasing responsibility, 27 of which include Information Security. David’s focus has been on securely managing information.
David is a Certified Information Systems Security Professional (CISSP), Certified Protection Professional (CPP), Certified Six Sigma Black Belt from ASQ and has also achieved ITIL Foundations, CNE, MCSE, CCNA, CCDA and Network+ certifications. As someone with experience in information technology, information security, and physical security, David works to bring these disparate disciplines together into coherent and efficient practices.
David holds a bachelor’s degree from UCLA and while there was elected to Phi Beta Kappa. He has taught multiple college extension classes and has presented at numerous conferences on technology, information security and physical security. Adding to David’s leadership expertise, David has written a Leadership Book called The New IQ: Innovative Questions and is also a Marshall Goldsmith Stakeholder Centered Coach.
David provides new perspectives to his teammates while helping them to achieve governance and optimal usage of their technologies. David is currently Chair of the ISSA Los Angeles CISO Forum.
David has also been published multiple times for security, including in the ISSA Journal and on Tom’s IT Pro. He has written the Information Security chapters for the ASIS Protection of Assets Manual with Dr. Stan Stahl.
Most recently, Rob has been CEO for two venture funded startups and before that, led startups in the mobile space and in enterprise software. He has worked at seven companies with four of them sold and three still operating. He has a broad domain of expertise, having held leadership positions in products, marketing, and operations in five other companies.
His academic credentials include a BA, BS, MS, and MBA degree and he is a Stanford alum. Rob is also an Executive in Residence at Quest Venture Partners.
In addition to his role as Chief Privacy Officer for Private.me, Timothy Toohey is also Partner and Head of Cyber, Privacy and Data Security Team at Morris Polich & Purdy LLP, which concentrates on data protection and privacy matters, complex litigation and intellectual property.
Tim is the author of Understanding Privacy & Data Protection – What You Need to Know which was published by Thomson Reuters/Aspatore in 2014. He handles a wide range of privacy and data breach matters, including advice regarding the Federal Credit Reporting Act, Computer Fraud and Abuse Act, Digital Millennium Copyright Act, Electronic Communications Privacy Act, and the US/EU Safe Harbor. He also deals with matters relating to cloud computing, and the privacy and security implications of “smart” devices and social media. Tim advises clients regarding California’s Song-Beverly Act, California Security Breach Notice requirements and international privacy and security issues, including compliance with European Union (E.U.) data protection and privacy directives.
With thousands of properties for sale on our site, we can help you find your space.
Find a rental space that you’ll love or advertise your rental property on our site FOR FREE!
Advertise with us and have your property seen by millions of people.
Get to know SA's best neighbourhoods.
Calculate your monthly repayment easily.
Whether you’re buying, selling, renting or investing, find useful information in our step by step guides.
Paint and wallpaper are not the only wall-covering options for your home. Which other options are available? Read more..
Bargains often seem attractive but there are pitfalls of buying what appears to be a bargain property. Read more..
The vetting process is critical in the process of approving new tenants. How should this be done? Read more..
You can design your small garden to look good while helping the environment. How can this be done? Read more..
The property industry has continued to record an increased number of female property buyers. What is the history behind this trend and what are the current prevailing conditions? Read more..
These are the alternatives to bricks and mortar that are attractive, eco-friendly, budget-friendly, and suitable for DIY enthusiasts. Read more..
Get the latest property news and advice delivered straight to your inbox.
Copyright © Private Property South Africa (Pty) Ltd. 1997 - 2021. All Rights Reserved.
Japan Film Xnxx
Primal Fetish Cum In Mouth
Porno Mature Picture Film
Nylon Footjob Mature
Young Daughter Porno Video
PrivCo | Private Company Financial Database
Private.me
Private Property - Property Portal South Africa | Your ...
Private Number Plates And DVLA Registrations
Private PC | PC Sales & Repairs
Private hospitals, surgery, treatment and services ...
Private GP Services
Private Accommodation
Home - RMB Private Bank - RMB
Www Private Co