Web Penetration Testing

🛑 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE👈🏻👈🏻👈🏻
Headquarters: 5 Zarytskyh, Lviv, Ukraine
Copyright © 2021 Relevant Software LLC. All rights reserved. Terms and Conditions
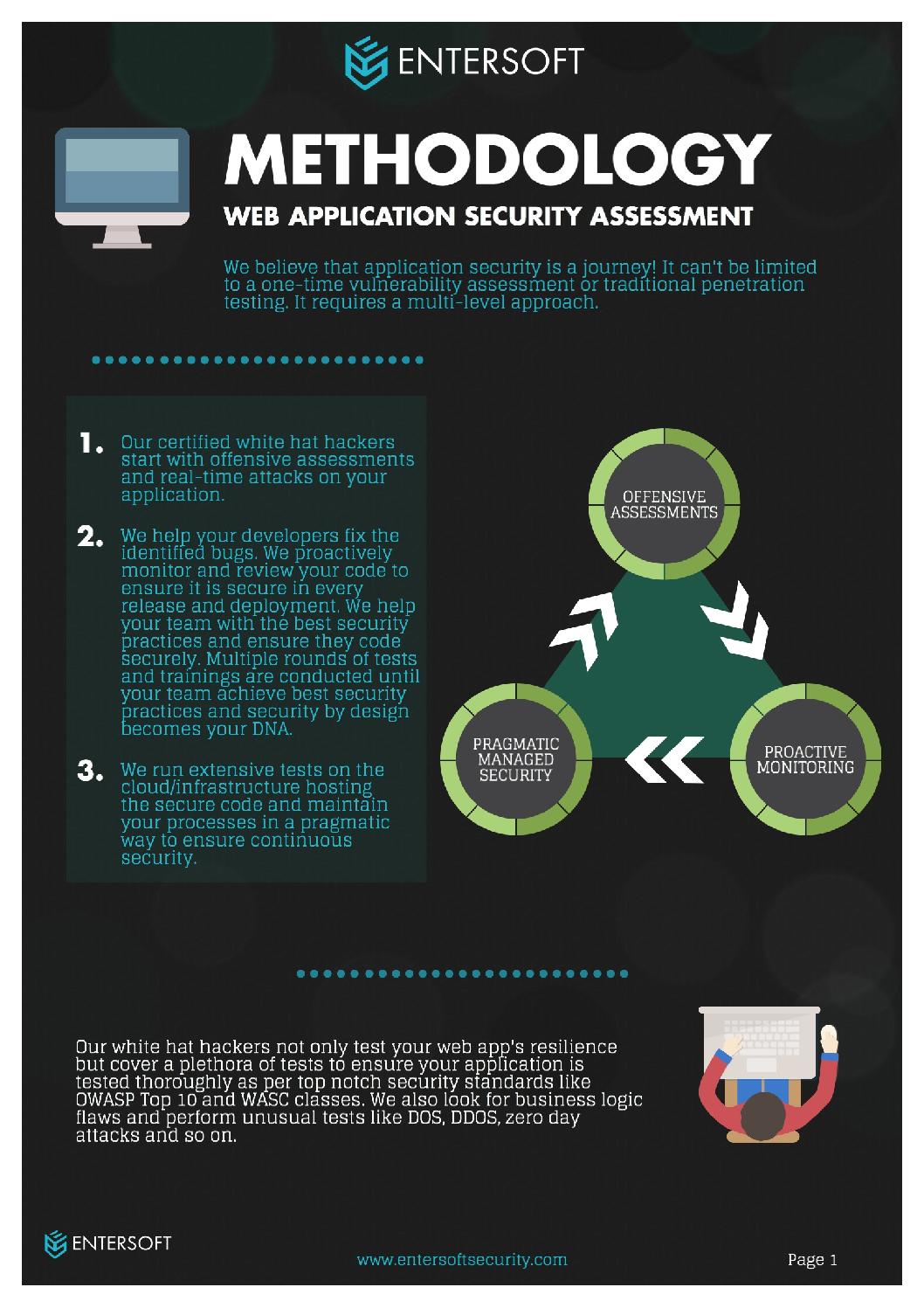
The best way to find flaws in your web application is by doing penetration testing, also known as Pen Test or Pen Testing. This is the most widely used security testing strategy for most web applications.
Web application penetration testing is carried out by initiating simulated attacks, both internally and externally, in order to get access to sensitive data.
Web penetration testing allows the end user to determine any security weakness of the entire web application and across its components, including the source code, database, and back-end network). This helps the developer in prioritizing the pinpointed vulnerabilities and threats, and come up with strategies to mitigate them.
Almost everything that we do is done through the internet. From shopping to banking to everyday transactions, most of them can be done digitally. And there are several web applications that can be used to complete these online activities.
The popularity of web applications has also introduced another vector of attack that malicious third parties can exploit for their personal gains. Since web applications usually store or send out sensitive data, it is crucial to keep these apps secure at all time, particularly those that are publicly exposed to the World Wide Web.
In a nutshell, web penetration testing is a preventive control measure that lets you analyze the overall status of the existing security layer of a system.
These are the common goals of doing pen testing for web apps:
When you look at the current internet usage, you’ll find out that there has been a sharp increase in mobile internet usage, which means a direct increase in the potential for mobile attacks. When users access websites or apps using mobile devices, they are more prone to attacks. Hence, pen testing plays a critical part in the software development lifecycle, helping build a secure system that users can use without having to worry about hacking or data theft.
For 7 years of building web and mobile applications, we have learned how to make them secure. Contact us to get a quote for penetration testing services from our cybersecurity experts.
Pen testing for web applications can be done in two ways: by simulating an inside or an outside attack. Let’s look at how these different types of attacks are designed and carried out:
As the name implies, the internal penetration testing is performed within the organization via LAN, including testing web applications that are hosted on the intranet.
This facilitates the identification of any vulnerabilities that may exist within the corporate firewall. One of the greatest misconceptions is that attacks can only occur externally so developers often overlook or do not give much importance to internal Pentesting.
Some of the internal attacks that can happen include:
The pentest is done by trying to access the environment without valid credentials and determining the possible route of attacks.
Unlike internal pentest, external pen testing focuses on attacks initiated from outside the organization to test web applications hosted on the internet.
Testers, also called ethical hackers, do not have information about the internal system and the security layers implemented by the organization. They are simply given the IP address of the target system to simulate external attacks. No other information is given and it is up to the testers to search public web pages to get more information about the target host, infiltrate it, and compromise it. External pen testing includes testing the organization’s firewalls, servers, and IDS.
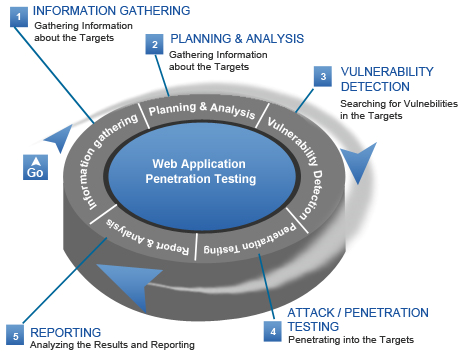
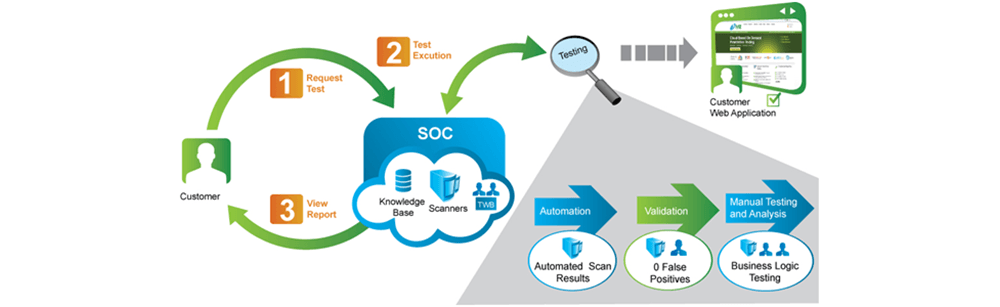
Pen testing for web apps focuses on the environment and the setup process, instead of the app itself to do this. This involves gathering information about the target web app, mapping out the network that hosts it, and investigating the possible points of injection or tampering attacks.
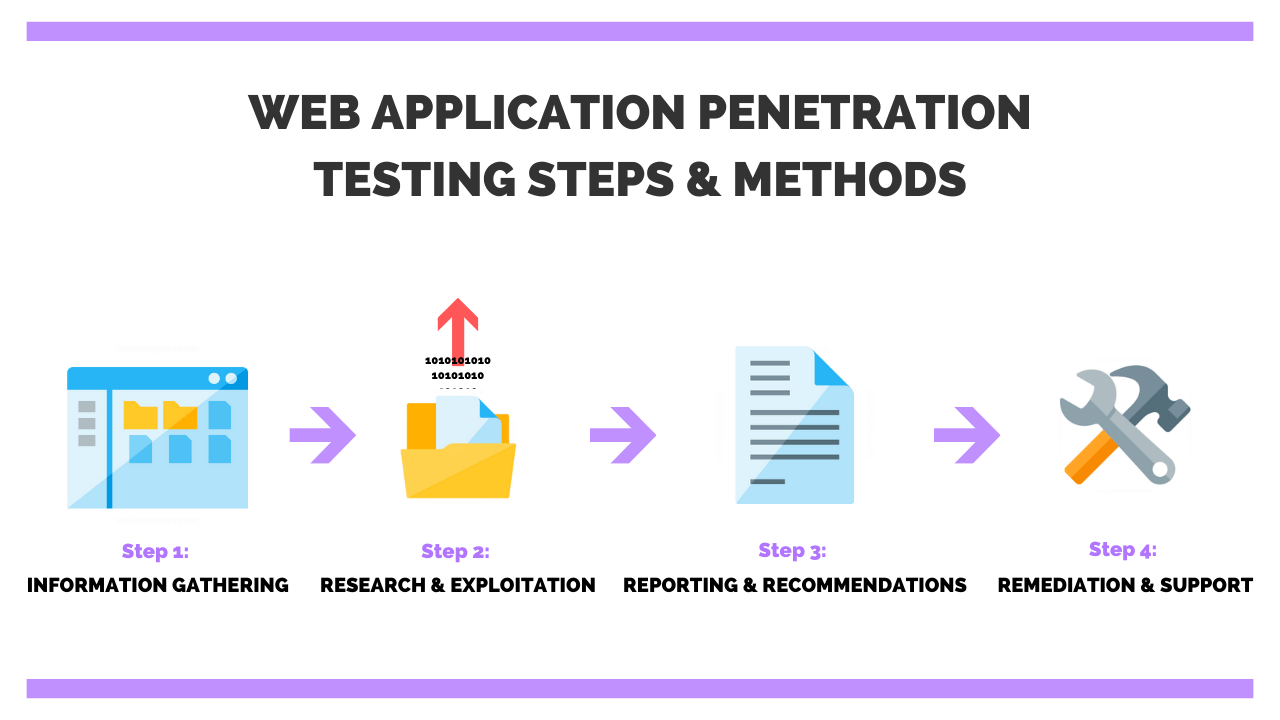
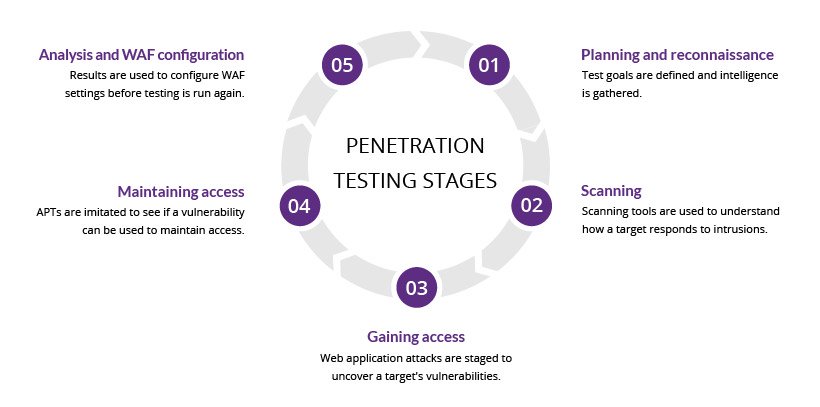
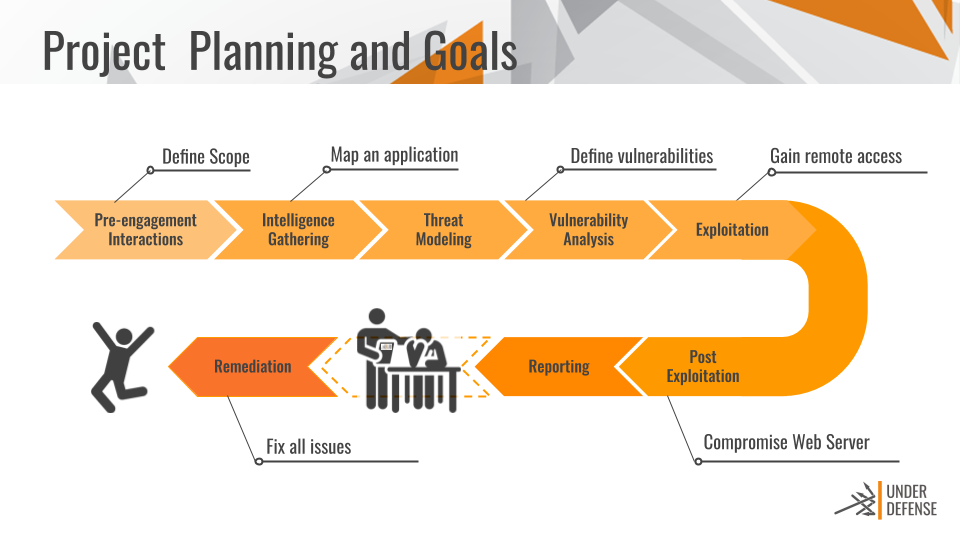
Here are the steps involved in web app penetration testing:
The first step in web app pen testing is the reconnaissance or information gathering phase. This step provides the tester with information that can be used to identify and exploit vulnerabilities in the web app.
Passive reconnaissance means collecting information that is readily available on the internet, without directly engaging with the target system. This is mostly done using Google, beginning with subdomains, links, previous versions, etc.
Active reconnaissance, on the other hand, means directly probing the target system to get an output. Here are some examples of methodologies used for active reconnaissance:
The next step is the actual exploitation step. In this phase, you implement the attacks based on the information you have gathered during the reconnaissance stage.
There are several tools you can use for the attacks, and this is where the data gathering plays an important role. The information you collected will help you narrow down the tools that you need according to the research you have previously conducted.
Let’s look at the top penetration tools used for web applications in the industry today:
Nmap or Network Mapper is more than a scanning and reconnaissance tool. It is used for both network discovery and security auditing purposes. Aside from providing basic information on the target website, it also includes a scripting module that can be used for vulnerability and backdoor detection, and execution of exploitations.
Wireshark is one of the most popular network protocol analyzers right now, facilitating deep inspection of protocols, as well as live-traffic capture and offline analysis of a captured file. The data can be exported using XML, PostScript, CSV, or plain text format for documentation and further analysis.
This pen testing tool is actually a framework, and not a specific application. You can use this to create custom tools for particular tasks. You can use Metasploit to:
Why these 200 tech companies & startups outsource to Ukraine
This vulnerability scanner helps testers identify vulnerabilities, configuration problems, and even the presence of malware on web applications. This tool, however, is not designed for executing exploitations, but offers great help when doing reconnaissance.
We’ve mentioned Burp Suite a couple of times earlier, and this is because this tool is an all-in-one platform for testing the security of web applications. It has several tools that can be used for every phase of the testing process, including Intercepting proxy, Application-aware spider, Advanced web application scanner, Intruder tool, Repeater tool, and Sequencer tool.
After the data gathering and exploitation processes, the next step is writing the web application pen testing report. Create a concise structure for your report and make sure that all findings are supported by data. Stick to what methods worked and describe the process in detail.
Aside from writing down the successful exploits, you need to categorize them according to their degree of criticality, to help the developers focus in dealing with the more serious exploits first.
Web applications offer a lot of convenience and value to the end users, but it comes with a cost. Most systems are publicly exposed to the internet and the data is readily available to those who are willing to do a bit of research. Because of the growing usage and evolving technologies, web applications are prone to vulnerabilities, in both design and configuration, that hackers might find and exploit. Because of this, web applications should be a priority when it comes to penetration testing, especially if they handle sensitive information.
Relevant is a 7-years old software development vendor that has expertise in web applications and cloud cybersecurity. Contact us now to get a quote of penetration testing for your web app. I was recently interviewed by Safety Detectives, where you can learn more about cybersecurity and our company.
I make sure our clients get the highest code quality and the best tech talent on the market. I am also a Software Engineering Advisor for startups. Let's connect.
Alleviate the pressure of a backlog without having to hire, train and maintain long-term salaries
Learn more
How OKRs Can Power Customer Experience and Product Improvements
ISO 20022 Overview: Migration and Adoption
Developing a Palm Scanner Solution for Payments Like Amazon One: Whys and Hows
How the IoT and AI Are Impacting Agriculture
Software Product Release Orchestration
By sending a message you agree with your information being stored by us in relation to dealing with your enquiry. Please have a look at our Privacy Policy.
Top-rated software
development company
of a team senior
and middle engineers
Relevant is a top-rated outsourcing company. We provide companies with senior tech talent and product development expertise to build world-class software.
Zarytskykh St, 5, L'viv, L'vivs'ka oblast,
79000, Ukraine.
Copyright © 2021 Relevant Software LLC. All rights reserved. Terms and Conditions
By sending a message you agree with your information being stored by us in relation to dealing with your enquiry. Please have a look at our Privacy Policy.
Top-rated software
development company
of a team senior
and middle engineers
We use cookies on our website. You can read more in our Privacy Policy. Agree
This website uses cookies to improve your experience while you navigate through the website. Out of these cookies, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities...
Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website. These cookies do not store any personal information.
Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. It is mandatory to procure user consent prior to running these cookies on your website.
We are looking forward to start working with you.
I’d like to sign an NDA with Relevant Software
I’d like to sign an NDA with Relevant Software
I’d like to sign an NDA with Relevant Software
I’d like to sign an NDA with Relevant Software
www.softwaretestinghelp.com/getting-starte…
How is penetration testing carried out for web applications?
How is penetration testing carried out for web applications?
Penetration testing for web applications is carried out by initiating simulated attacks, both internally and externally, in order to get access to sensitive data. A pen test allows the end user to determine any security weakness of the entire web application and across its components, including the source code, database, and back-end network).
relevant.software/blog/penetration-testing-f…
Web Penetration Testing is as the name suggestions, a penetration test that focuses solely on a web application rather than a network or company.
What do you need to know about sec542 penetration testing?
What do you need to know about sec542 penetration testing?
Anyone can learn to sling a few web hacks, but effective web application penetration testing requires something deeper. SEC542 enables students to assess a web application's security posture and convincingly demonstrate the business impact should attackers exploit the discovered vulnerabilities.
www.sans.org/cyber-security-courses/web …
What ' s The difference between penetration test and penetration testing?
What ' s The difference between penetration test and penetration testing?
In fact, a lot of the same tools and attack vectors are leveraged during the engagement. The key distinction is found in the methodology that web penetration testers use to footprint or map out a web applications functionality and then interrogate entry points (usually user supplied input fields).
www.pentestgeek.com/web-penetration-tes…
https://www.pentestgeek.com/web-penetration-testing
Перевести · Web Penetration Testing: Related Content Burp Suite Tutorial – Web Penetration Testing (Part 1) – An introduction to web application penetration testing with... How To Use Burpsuite – Web Penetration Testing (Part 2) – Expanding on the previous tutorial and offering deeper insight... Stealing The ...
https://relevant.software/blog/penetration-testing-for-web-applications
Перевести · 06.08.2020 · Web penetration testing allows the end user to determine any security weakness of the entire web application and across its components, including the source code, database, and back-end network). This helps the developer in prioritizing the pinpointed vulnerabilities and threats, and come up with strategies to mitigate them.
Web Application Ethical Hacking - Penetration Testing Course for Beginners
Ethical Hacking 101: Web App Penetration Testing - a full course for beginners
Modern Web Application Penetration Testing Part 1, XSS And XSRF Together
YouTube › SANS Offensive Operations
Web App Penetration Testing - #4 - Web Application Firewall Detection With WAFW00F
Hands-On Web Penetration Testing with Kali Linux: OWASP-ZAP|packtpub.com
Web App Penetration Testing - #2 - Spidering & DVWA
https://www.litres.ru/radhi-shatob/web-penetration-testing/chitat-onlayn
What is a Penetration Testing (Pen-test)? Penetration testing is the attack simulation on an IT system with the intention of finding security weaknesses to determine how the systems react to these attacks. …
https://www.apriorit.com/dev-blog/622-qa-web-application-pen-testing-owasp-checklist
Перевести · The major goal of penetration testing or pen testing is to find and fix security vulnerabilities, thus protecting the software from hacking. To do so, a QA specialist has to conduct simulated cyberattacks on the web application. Pen testing helps QA specialists to: identify previously unknown vulnerabilities
https://www.softwaretestinghelp.com/getting-started-with-web-application-penetration...
Перевести · Types of Web Penetration Testing #1) Internal Penetration Testing – As the name suggests, the internal pen testing is done within the organization over... #2) External …
https://resources.infosecinstitute.com/topic/top-7-web-application-penetration-testing...
Перевести · 01.03.2021 · Performing a web penetration test demands not only expertise, but also a significant amount of time. Cybercriminals may have all the time in the …
https://devcount.com/web-pentesting-tools
Перевести · 21.01.2021 · If you are completely new to web application penetration testing, here are the best penetration testing tutorials online to get you started. With the help of appropriate web app penetration testing tools, any professional pentester can identify web app security vulnerabilities, so that you can resolve them in time.
Перевести · “PentesterLab is an awesome resource to get hands-on, especially for newbies in web penetration testing or pentesting in general. It gives insights to possible web security flaws, their behavior and approaches that can be taken to exploit them. …
https://www.sans.org/cyber-security-courses/web-app-penetration-testing-ethical-hacking
Перевести · The GIAC Web Application Penetration Tester (GWAPT) certification validates a practitioner’s ability to better secure organizations through penetration testing and a thorough understanding of web application security issues.
SEC542.1: Introduction and Information Gathering
Overview Understanding the attacker's perspective is key to successful web application penetration testing. The course begins by thoroughly examini...
SEC542.2: Configuration, Identity, and Authorization Testing
Overview The second day begins with profiling the target(s) to understand the underlying configuration. The collected data is used to build a profi...
Overview After ending Day 2 with a successful authentication event, we begin by exploring how web applications track authenticated users and ways t...
Overview On day four, students continue exploring injection flaws. We cover methods to discover key vulnerabilities within web applications, such a...
SEC542.5: CSRF, Logic Flaws and Advanced Tools
Overview On the fifth day, we launch actual exploits against real-world applications, expanding our foothold within the application, and extending...
Overview On day six, students form teams and compete in a web application penetration testing tournament. This NetWars-powered Capture the Flag exe...
РекламаРеально низкие цены! 10 лет на рынке! Доставка и самовывоз! Более 5000 продуктов! · Москва · пн-пт 10:00-18:00, сб 12:00-15:00
Продавец: vitfit.ru. ОГРНИП: 309774633000300
Реклама150 000+ онлайн-курсов от экспертов. Программирование, бизнес, личностный рост! (EN)
Не удается получить доступ к вашему текущему расположению. Для получения лучших результатов предоставьте Bing доступ к данным о расположении или введите расположение.
Не удается получить доступ к расположению вашего устройства. Для получения лучших результатов введите расположение.
Redtube S
Dick Flash Video
Fast Fucking Sex
Man Fuck Cow Porn
Mature Tits Porn
Radhi Shatob, Web Penetration Testing – читать онлайн ...
Beginners Guide To Web Application Penetration Testing
PentesterLab: Learn Web Penetration Testing: The Right …
Web Application Penetration Testing Training | SANS SEC542
Web Penetration Testing