Watering Hole Attack

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Official websites use .gov
A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS
A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
Relevance (best match)
Term (A-Z)
Term (Z-A)
A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z
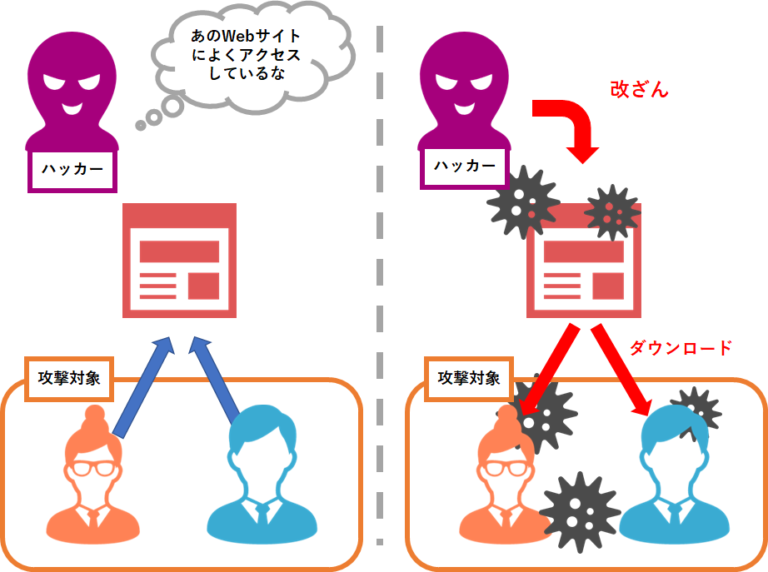
In a watering hole attack, the attacker compromises a site likely to be visited by a particular target group, rather than attacking the target group directly.
Source(s):
CNSSI 4009-2015
A security exploit where the attacker infects websites that are frequently visited by members of the group being attacked, with a goal of infecting a computer used by one of the targeted group when they visit the infected website.
Source(s):
NIST SP 800-150 under Watering Hole Attack
Comments about specific definitions should be sent to the authors of the linked Source publication. For NIST publications, an email is usually found within the document.
Comments about the glossary's presentation and functionality should be sent to secglossary@nist.gov.
See NISTIR 7298 Rev. 3 for additional details.
HEADQUARTERS
100 Bureau Drive
Gaithersburg, MD 20899
Want updates about CSRC and our publications? Subscribe
Contact CSRC Webmaster: webmaster-csrc@nist.gov
This article is about the computer hacking technique. For the place to obtain alcoholic drinks, see pub. For other uses, see Watering hole (disambiguation).
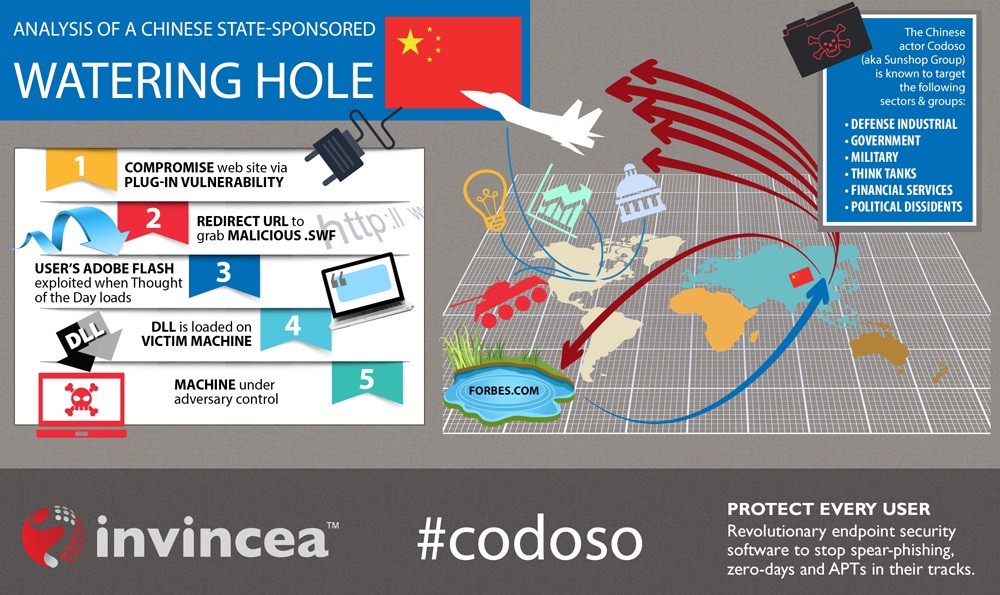
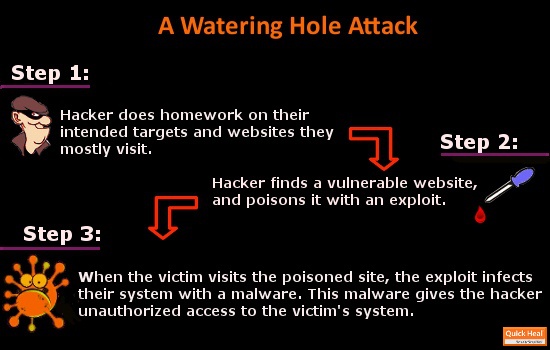
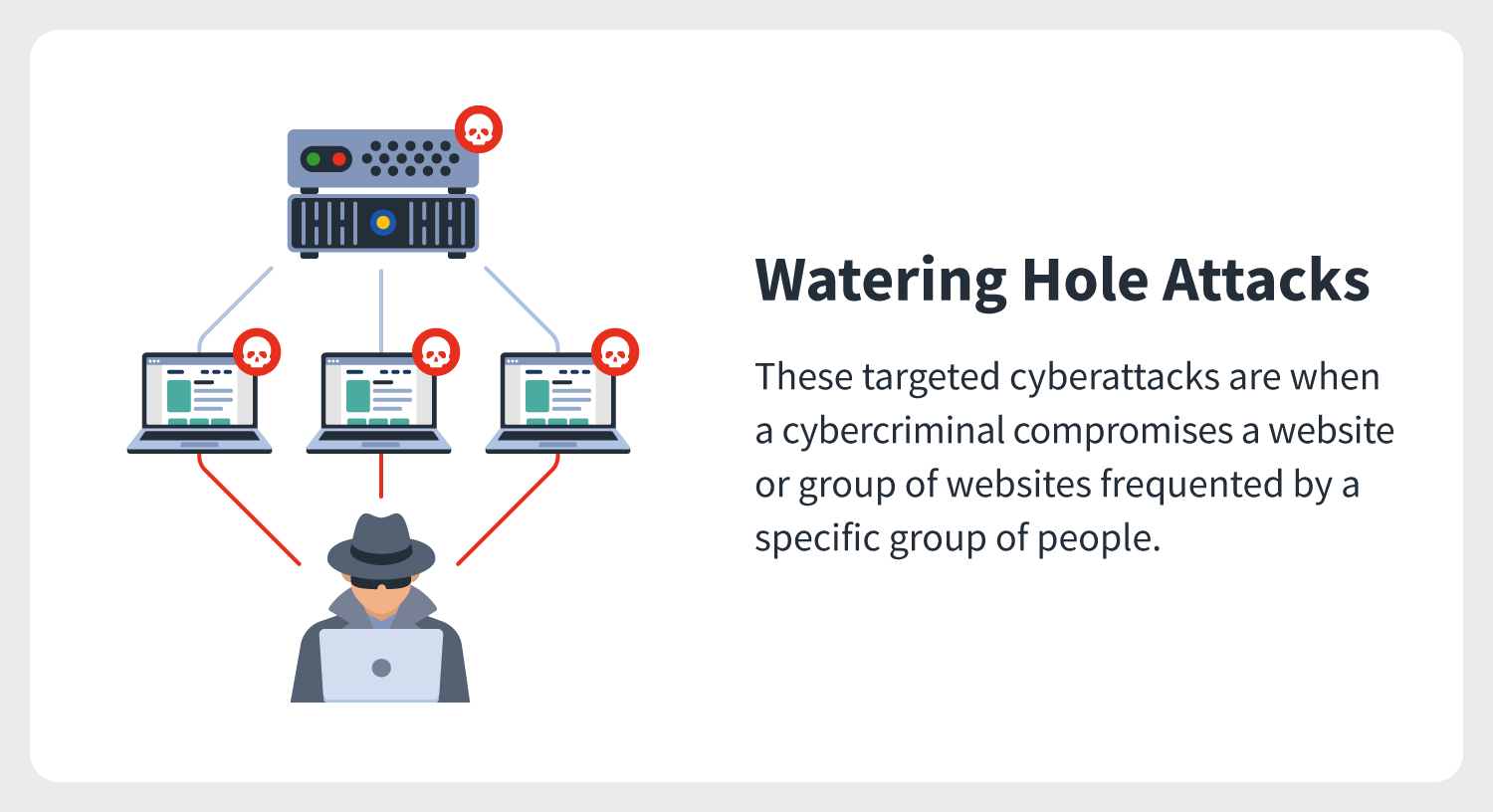
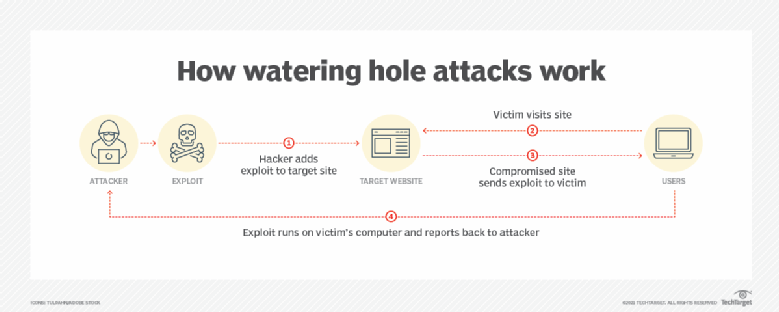
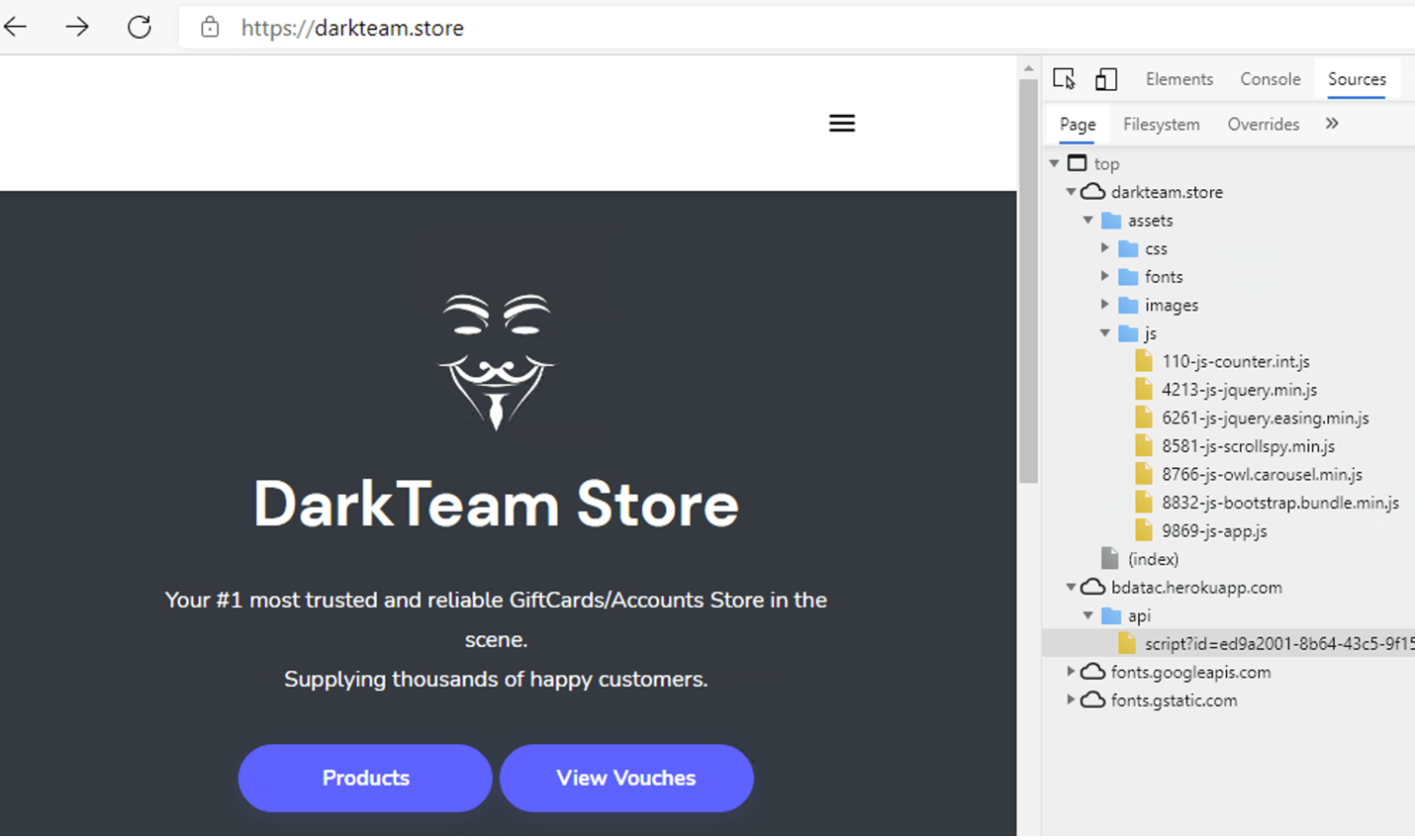
Watering hole is a computer attack strategy in which an attacker guesses or observes which websites an organization often uses and infects one or more of them with malware. Eventually, some member of the targeted group will become infected.[1][2][3] Hacks looking for specific information may only attack users coming from a specific IP address. This also makes the hacks harder to detect and research.[4] The name is derived from predators in the natural world, who wait for an opportunity to attack their prey near watering holes.[5]
Websites are often infected through zero-day vulnerabilities on browsers or other software.[4] A defense against known vulnerabilities is to apply the latest software patches to remove the vulnerability that allowed the site to be infected. This is assisted by users to ensure that all of their software is running the latest version. An additional defense is for companies to monitor their websites and networks and then block traffic if malicious content is detected.[6]
In December 2012, the Council on Foreign Relations website was found to be infected with malware through a zero-day vulnerability in Microsoft's Internet Explorer. In this attack, the malware was only deployed to users using Internet Explorer set to English, Chinese, Japanese, Korean and Russian.[7]
Havex was discovered in 2013 and is one of five known Industrial Control System (ICS) tailored malware developed in the past decade. Energetic Bear began utilizing Havex in a widespread espionage campaign targeting energy, aviation, pharmaceutical, defense, and petrochemical sectors. The campaign targeted victims primarily in the United States and Europe.[8]Havex exploited supply chain and watering-hole attacks on ICS vendor software in addition to spear phishing campaigns to gain access to victim systems.[9]
In early 2013, attackers used the United States Department of Labor website to gather information on users' information. This attack specifically targeted users visiting pages with nuclear-related content.[10]
In late 2016, a Polish bank discovered malware on computers belonging to the institution. It is believed that the source of this malware was the web server of the Polish Financial Supervision Authority.[11] There have been no reports on any financial losses as a result of this hack.[11]
There was an organization-level watering-hole attack in Montreal from 2016-2017 by an unknown entity causing a data breach.[12]
From August to September 2017, the installation binary of CCleaner distributed by the vendor's download servers included malware. CCleaner is a popular tool used to clean potentially unwanted files from Windows computers, widely used by security-minded users. The distributed installer binaries were signed with the developer's certificate making it likely that an attacker compromised the development or build environment and used this to insert malware.[13][14]
In June 2017, the NotPetya (also known as ExPetr) malware, believed to have originated in Ukraine, compromised a Ukrainian government website. The attack vector was from users of the site downloading it. The malware erases the contents of victims' hard drives.[15]
There was a country-level watering-hole attack in China from late 2017 into March 2018, by the group "LuckyMouse" also known as "Iron Tiger", "EmissaryPanda", "APT 27" and "Threat Group-3390."[16]
In 2019, a watering-hole attack, called Holy Water Campaign, targeted Asian religious and charity groups.[17] Victims were prompted to update Adobe Flash which triggered the attack. It was creative and distinct due to its fast evolution.[18] Motive remains unclear.[18]
Content is available under CC BY-SA 3.0 unless otherwise noted.
Granny Homemade Oral Video
Pov Slave Rus Sub
Shuft Tube 125 Xl
Romantic Porno Mom
Pussy Small Tits Teen Solo Home
watering hole attack - Glossary | CSRC
Watering hole attack - Wikipedia
What is a Watering Hole Attack? - ericom.com
What Is a Watering Hole Attack? | Fortinet
What is a watering hole attack?
Exploring Watering Hole Attacks: Tactics, Examples and ...
Phishing Variations: Watering Hole Attacks - Infosec Resources
What is a Watering Hole Attack? - Definition from Techopedia
Watering Hole Attack