W Penetration

🔞 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
W Penetration
You must be at least eighteen years old to view this content. Are you over eighteen and willing to see adult content?
Use of this site constitutes acceptance of our User Agreement and Privacy Policy . ©2021 reddit inc. All rights reserved. REDDIT and the ALIEN Logo are registered trademarks of reddit inc.
Doublepenetration | Videos and Pictures | Scrolller NSFW
A subreddit solely dedicated to girls taking 3 (or more) dicks at one time.
Penetration Testers
Search listening tool for market, customer & content... - AnswerThePublic
PENETRATION | Pronunciation in English (8 Video Examples)
Tools ▼
Information Gathering
Google Hacking - Free
Find Domains
Find Subdomains
Find Virtual Hosts
Website Recon
Web Application Testing
Website Scanner
URL Fuzzer
SQLi Scanner
XSS Scanner
CMS Tests
WordPress Scanner
Drupal Scanner
Joomla Scanner
SharePoint Scanner
Infrastructure Testing
Network Scan OpenVAS
Password Auditor
Subdomain Takeover
TCP Port Scan
UDP Port Scan
DNS Zone Transfer
SSL/TLS Scanner
Exploit Helpers
SQLi Exploiter
XSS Exploiter
HTTP Request Logger
Utils
ICMP Ping
Whois Lookup
All Tools
Countless
Vulnerabilities Found
What you can do with Pentest-Tools.com
Tools
Information Gathering
Web App Testing
Network Testing
Exploit Helpers
Developers
API Reference
Resources
Blog
Platform Tutorials
Platform Updates
Data Security
Support
Legal
Terms and Conditions
Privacy Policy
Company
About
Team
Jobs
Contact
©
2021 Pentest-Tools.com
Pentest-Tools.com allows you to quickly discover and report vulnerabilities in websites and network infrastructures. We provide a set of powerful and tightly integrated pentesting tools which enable you to perform easier, faster and more effective pentest engagements.
Quickly discover the attack surface of a target organization
Easily find low-hanging fruits by just using your browser
Bypass local network restrictions and scan from external IP addresses
Create credible proof-of-concepts to prove the real risk of vulnerabilities
Speed-up your pentesting engagements
Verify the security of your Internet facing servers using already installed and configured security tools
Present the results to management with easy to read reports
Show your customers the scan reports and increase their trust in your services
Periodically scan for vulnerabilities and get notified when new issues are discovered.
Check the security of your web applications by performing external security scans
Find SQL injection, Cross-Site Scripting, OS Command Injection and many other high risk vulnerabilities
Report the findings in a friendly format and present the results to management
Integrate the security scans (via API) into your current software development lifecycle
Obtain a quick overview of your company's security posture
Check if the IT team has done a good job in securing the perimeter
Discover the internet exposure of your company as an attacker sees it
Do a pre-audit to find and close the high risk issues before having a full security audit
Pentest robots combine our tools with your logic for massive productivity gains! We just launched them at Black Hat Europe 2020 and we can’t wait for you to see what they can do!
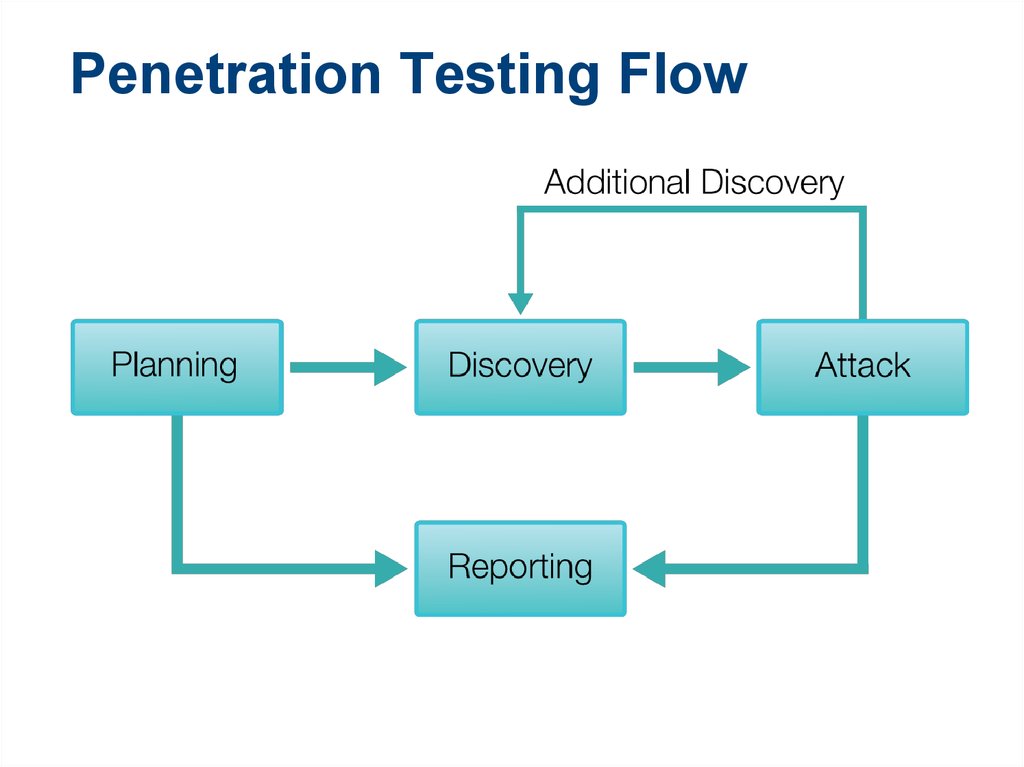
You get instant access to custom vulnerability scanners and innovative features that simplify the security assessment process and produce valuable results. The platform helps you cover all the phases of a penetration test, from information gathering, website scanning, network scanning to exploitation and reporting. Explore all Features
Don't waste your time installing, configuring and running complex security tools. We have them all setup for you, just say what is your target and press the Start button. You will receive a friendly report containing detailed vulnerability information, including risk description, evidence and recommendations for improvement.
All the scanners from our platform can be scheduled to periodically test your systems for vulnerabilities. Since our tools are regularly updated, you can be sure that you don't miss critical vulnerabilities. The scan reports are sent directly to your inbox so you can quickly react when issues are found.
Information gathering is crucial for planning a penetration test and for estimating the amount of work to be done. We have powerful reconnaissance tools which allow you to quickly discover the attack surface of an organization, passively scan for vulnerabilities and find the most promising targets.
Even if you have all the tools on your machine, the local firewall of your network might block you from scanning external hosts. The only way around this is to scan from an external server and Pentest-Tools.com was designed just for that. Our servers have a fast and direct Internet connection.
If you are a web development or an IT services company, you can easily use our platform to show your clients that you have correctly implemented all the necessary security measures. Our results are trusted by more than 50.000 clients in 40+ countries.
The API that we provide allows you to easily integrate the tools from our platform into your own systems and processes. This way you will benefit of the powerful scanning engines without having the trouble of running such scanners yourself.
Pentest-Tools.com was established in 2013 by a group of experienced penetration testers who needed a reliable online resource to perform security tests from.
The platform has quickly become a reference place for security professionals, system administrators, website developers and other IT specialists who wanted to verify the security of their websites and infrastructure.
“With several offices dotted around the world and 3 brands with multiple websites, I needed a solution that allowed me to monitor potential vulnerabilities across our business. We started with manual scans but now rely on the scheduling services for all our offices and websites to alert us of any issues. We’ve come to use the dashboard as a point of reference every day as part of our daily checks and we wouldn’t be without it. As long as Pentest-Tools.com continue to improve the scans and add new types of scans as the security landscape adapts, they’ll continue to have my business.”
IT & Network Supervisor at HBD Europe Ltd
“Pentest-Tools.com is my team's first go-to solution. Anytime we are preparing to deploy a new version of our software, we run many tools to monitor and secure our environment, but the simplicity and ease we have with Pentest-Tools.com to run network and web server scans to highlight issues is unmatched.”
“Qcast is keen on using Pentest-Tools.com because it provides a complete and easy to use in-depth analysis of our public web applications. With it we were able to check for vulnerabilities and stay secure.”
“NextWave has relied on Pentest-Tools.com for several years now. I’ve tried some of the other pentest systems, but none have the exceptional breadth of quality tools AND reasonable pricing we can afford. This makes Pentest-Tools.com a core part of our company’s network security offering. I highly recommend Pentest-Tools.com.”
President at NextWave Consulting, Inc.
Pentest-Tools.com is a Corporate Member of OWASP (The Open Web Application Security Project). We share their mission to use, strengthen, and advocate for secure coding standards into every piece of software we develop.
Anal Orgasmus
Anal Double Penetration Vk
Busty Teen Outdoor
Nerd And Jock Au
Nasty Beat