Vpn Virtual Private Network

🔞 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Vpn Virtual Private Network
A2 Hosting Shared hosting starts at $3.92/mo. Altus Hosting EU top hosting starts at $5.95/mo. BlueHost Shared hosting starts at $2.95/mo. GreenGeeks Eco-friendly hosting starts at $2.95/mo. Shopify Best online store builder ($29/mo). Sitejet Web builders for agency ($19/mo). ExpressVPN BVI-based VPN provider ($8.32/mo.)
Hostinger Shared hosting starts at $0.80/mo. HostPapa Canadian hosting starts at $3.95/mo. InMotion Hosting Shared hosting starts at $3.99/mo. InterServer Shared hosting at $5/mo for life. Wix Simple website builder ($12.50/mo). Zyro Cheap website builder for newbies ($1.99/mo.) SurfShark BVI-based VPN provider ($2.49/mo.)
ScalaHosting SPanel VPS hosting starts at $13.95/mo. SiteGround Shared hosting starts at $6.99/mo. TMDHosting Shared hosting starts at $2.95/mo. WP Engine Managed WP hosting at $29/mo. Weebly Popular site builders ($12/mo). IPVanish United States-based VPN provider ($6.49/mo.) NordVPN Panama-based VPN provider ($3.49/mo.) See All
HostScore Our automated web host performance tracking system. Website Valuation Tool Chat with A.I. and get a free valuation of your website. WHSR Blog Read latest industry news and articles.
Updated: Nov 17, 2020 / Article by: Jerry Low
* Heatmap of locations where the NSA collects data online using Boundless Informant, a big data analysis tool used by United States National Security Agency (NSA). Source: The Guardian
Example – Some of the devices supported by NordVPN – Note how each device supports its own set of protocols
Global VPN market value (billion, USD) – Source: Statista
Copyright © 2021 . WebRevenue Sdn Bhd (1359896-W)
Walkthrough tutorials and services you need to create your first website.
Home / Virtual Private Network (VPN): A Very Detailed Guide for Newbies
Virtual Private Network (VPN) services are somewhat of a hot topic nowadays since Internet privacy is coming under fire from many directions. Companies are trying to gather more data on their users to the extent that it is becoming overly intrusive (Want example? See this , this , this , and this ) while countries are divided on how to manage the situation.
For years we have been using major products such as Facebook, Google, Microsoft software and more but rapidly advancing technology has tempted these companies to squeeze users account of every bit of information they can for commercial purposes.
And while governments may struggle to control the situation, in some cases it is they themselves who are guilty of the same sins that the corporates are getting in trouble for – intrusion of privacy and illegal collection of private data .
So, what can we as individual do to protect our privacy online? The answer leads us back to our topic of VPNs.
FTC Disclosure: WHSR receives referral fees from some of the brands and companies mentioned in this article.
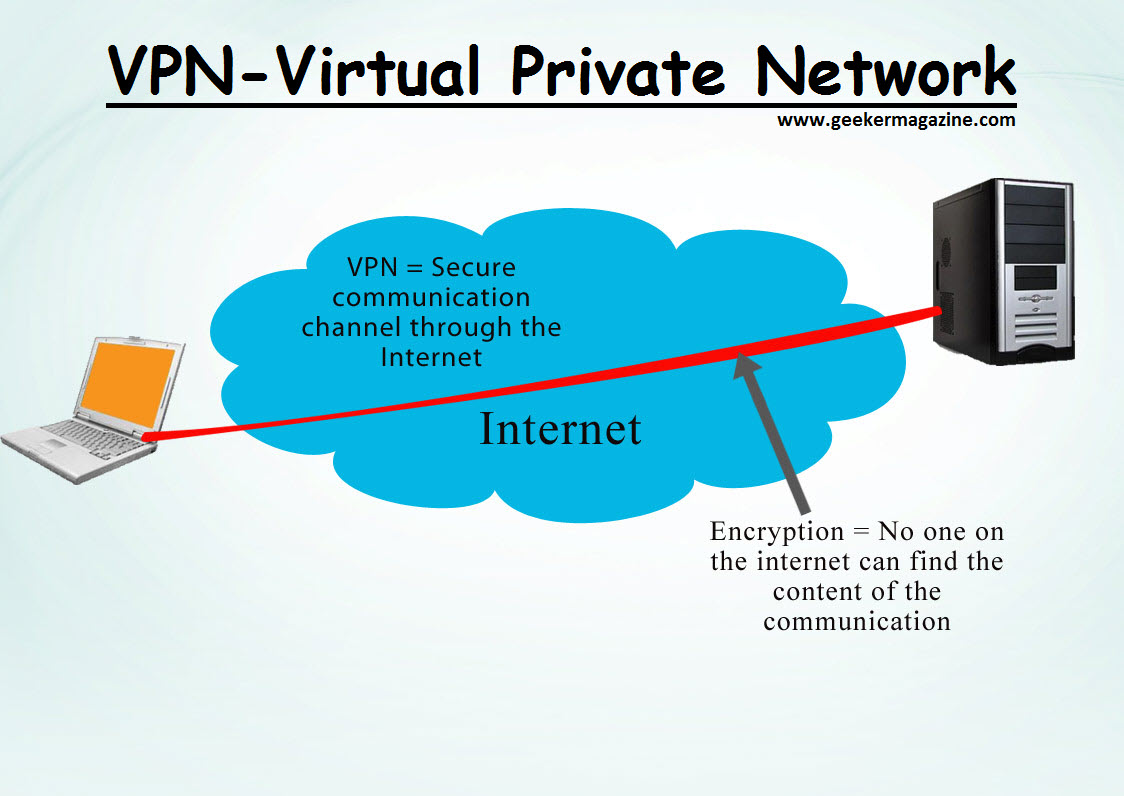
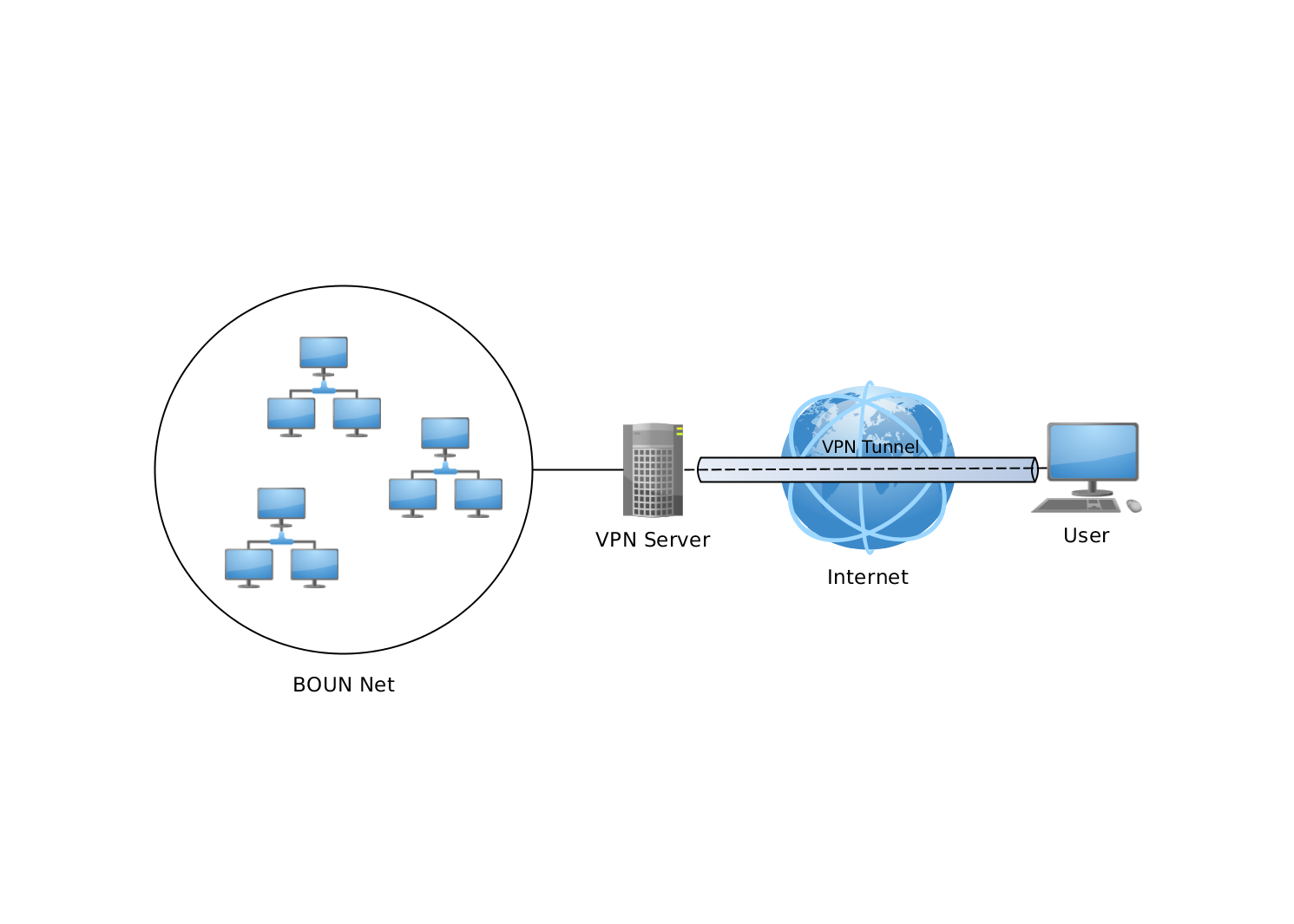
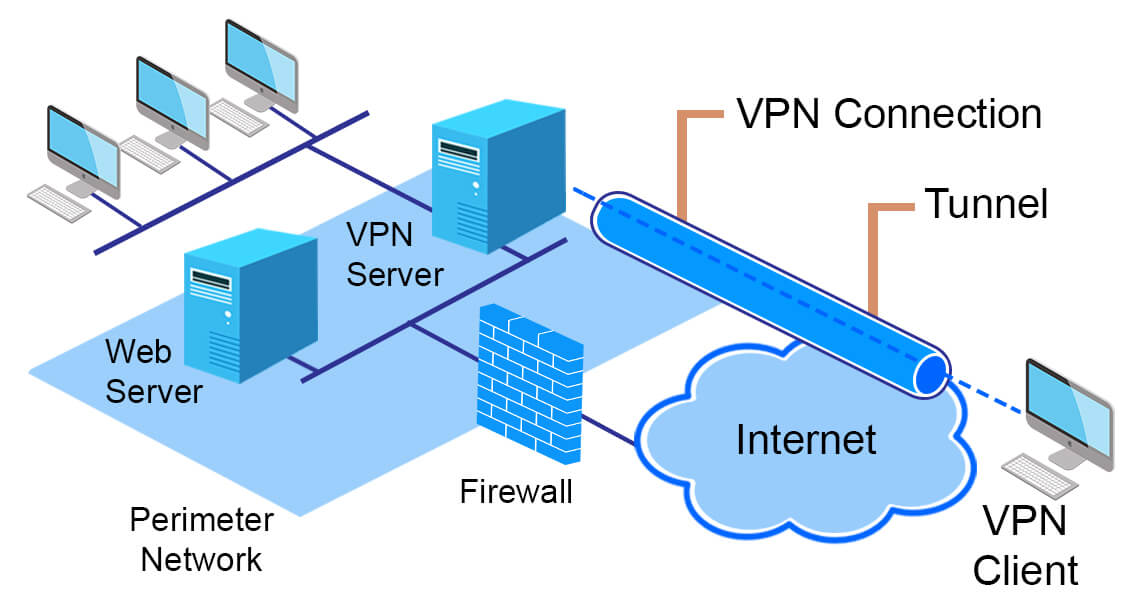
A VPN is a service that creates an encrypted connection from your device to a VPN server through your Internet connection. Think of it as a tunnel through a mountain, in which your Internet service provider (ISP) is the mountain, the tunnel is the VPN connection and the exit is to the world wide web.
There are some people who may mistake VPNs as alternatives to having an Internet connection, but this is incorrect.
Originally, VPNs were created to connect business networks together for more secure and convenient communications. Today, VPN service providers work hard to forward all your traffic to the Internet – bypassing government or ISP monitoring and even forced censorship in some cases.
In a nutshell, think of a VPN as a service that’s designed to help you gain full access to the Internet and protect you while doing it.
The primary purpose of a VPN is to create a secure tunnel for your data to travel through to its servers before passing on to the Internet. This however, has resulted in some other benefits, such as location spoofing.
While that might seem insignificant to you, there are many times when location spoofing has helped people overcome geo-location barriers. Take the Great Firewall of China for example. The Chinese government heavily censors the Internet and many things we take for granted online are blocked in China. Only by using a VPN can China-based users access sites like Google and Facebook.
(Here's a list of VPN services that still work in China by CompariTech).
For peer-to-peer (P2P) users, aside from the risk of identification, you also run the risk of having your port maps identified through Torrenting. VPNs help mask all of this so that your open ports can’t be easily exploited.
As I’ve mentioned, the first and foremost purpose of VPNs today is anonymity. By creating a secure tunnel from your device to their servers and encrypting the data that travels through that tunnel, VPNs effectively shield all your data activity.
This means that anyone trying to discover what you’re doing on the Internet, such as the sites you visit and so on won’t be able to find out much. VPNs are so much focused on anonymity that many of them today have taken to accepting payments that can’t be traced, such as crypto currency and gift certificates.
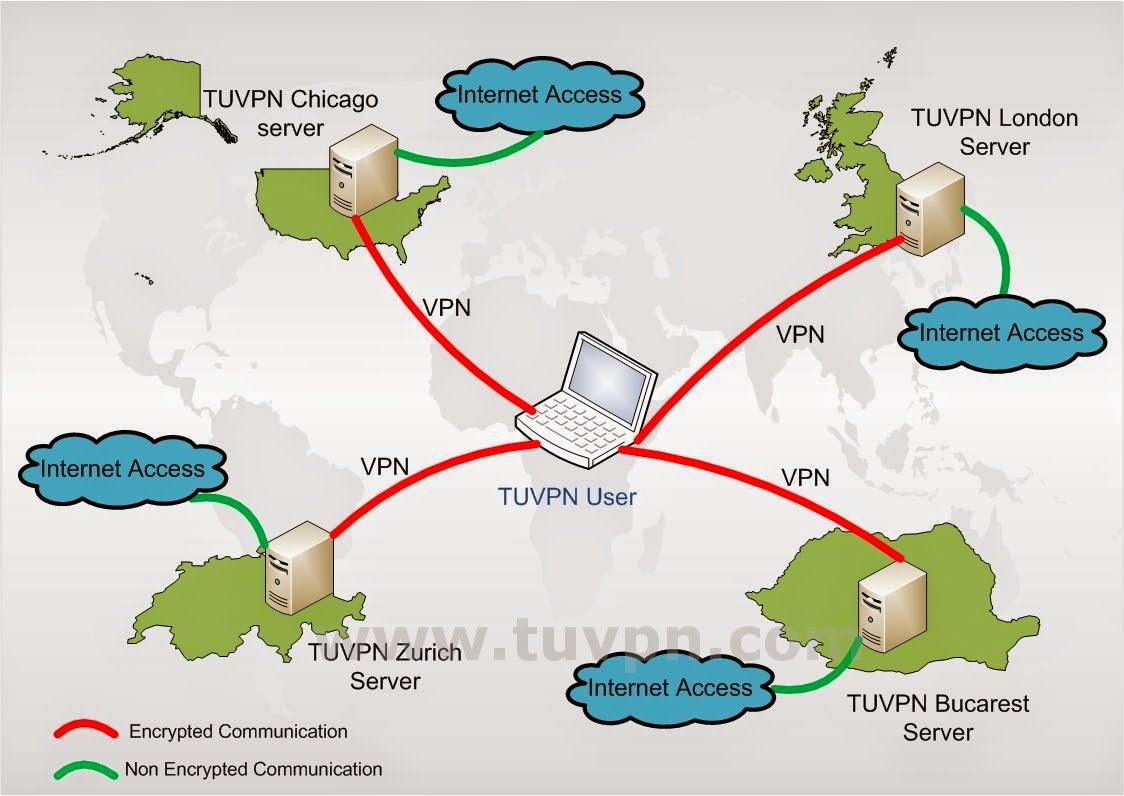
Location spoofing came about as a side benefit of VPN services. Because VPN services have servers in many locations around the world, by connecting to those servers you can ‘spoof’ your location as being the same as that of the VPN server.
Some providers in the marketplace might not be honest with their service offerings. They claim to offer physical servers in varied locations, but some of them are actually virtual. In other words, you may be connected to a server located in one country, but receive an IP address assigned to another country. For instance, a server in China could actually be from the US.
This is bad because this means your data passes through multiple servers in different parts of the world before reaching the final destination. There is no guarantee that cybercriminals, secret intelligence agencies, or copyright infringement hunters have their hand in one of these intermediate servers.
To avoid this issue, users should conduct proper testing to verify the true locations of a VPN. Here are four tools you can make use of –
Many VPN services today are also beginning to implement greater security measures to benefit their users. It started out mainly to help block online data collection and tracking but has now expanded to include ad-blocking and in some cases even anti-virus solutions.
It is a little difficult to describe how a VPN works unless a little technical detail is involved. However, for those who just want the basic concept, a VPN creates a secure tunnel from your device to the VPN server and then from there out to the world wide web.
In greater detail, the VPN first establishes a communication protocol from your device. This protocol will set the boundaries of how the data will travel from your device to the VPN server. There are a few main VPN protocols which are common, although each has their own advantages and disadvantage.
Although there are many communication protocols, there are some mainstream ones which are commonly supported irrespective of VPN service brand. Some are faster, some are slower, some more secure, others less so. The choice is yours depending on your requirements, so this might be a good section for you to pay attention to if you’re going to be using a VPN.
OpenVPN is an open source VPN protocol and that is both its strength as well as its possible weakness. Open source material can be accessed by anyone , which means that not only can legitimate users use and improve on it, but those with not so great intentions can also scrutinize it for weaknesses and exploit those.
Still, OpenVPN has become very much mainstream and remains one of the most secure protocols available. It supports very high encryption levels including what is considered to most as ‘unbreakable’ 256-bit key encryption requiring 2048-bit RSA authentication, and a 160-bit SHA1 hash algorithm.
Thanks to it being open source, it has also been adapted for use on almost all platforms today, from Windows and iOS to more exotic platforms such as routers and micro devices like the Raspberry Pi.
Unfortunately, high security has its downsides and OpenVPN is often seen as being very slow. This however is more of a trade-off, since it is normal that the higher the encryption rates being used, the more time it will take to process data streams.
Layer 2 Tunnel Protocol (L2TP) is the de facto successor of Point to Point Tunneling Protocol (PPTP) and Layer 2 Forwarding Protocol (L2F) . Unfortunately, since it didn’t come equipped to handle encryption it was often distributed together with the IPsec security protocol. To date, this combination has been seen as the most secure and having no vulnerabilities yet.
One thing to note is that this protocol uses UDP on port 500, which means that sites that do not allow VPN traffic can detect and block it easily.
Secure Socket Tunnelling Protocol (SSTP) is one that is lesser known among regular people, but it is very useful simply because it has been fully tried, tested and tied into every incarnation of Windows since the days of Vista SP1.
It is also very secure, using 256-bit SSL keys and 2048-bit SSL/TLS certificates. It is also unfortunately proprietary to Microsoft, so it’s not open to public scrutiny – again, both good and bad.
Internet Key Exchange version 2 (IKEv2) was co-developed by Microsoft and Cisco and was originally intended simply as a tunneling protocol. It therefore also makes use of IPSec for encryption. Its agility in reconnecting to lost connections has made it very popular among those who leverage on it for mobile deployment of VPNs.
Point-to-Point Tunnelling Protocol (PPTP) is one of dinosaurs amongst VPN protocols. the oldest VPN protocols. Although there are still some instances of use, this protocol has largely fallen by the wayside due to large, glaring gaps in its security.
It has several known vulnerabilities and has been exploited by both the good and bad guys long ago, making it no longer desirable. In fact, it’s only saving grace is its speed. As I mentioned earlier, the more secure a connection is, the more likely speed is to see a decline .
The simplest way to describe encryption that I can think of is perhaps messing up information so that only a person who has the guide to how you messed it up can translate it back to its original meaning.
Take for example a single word – Cat.
If I apply 256-bit encryption to that one word, it would be completely scrambled and undecipherable. Even the most powerful supercomputer on earth would take millions of years trying to decrypt that single word with 256-bit encryption applied to it.
Also, the levels of encryption are exponential, so 128-bit encryption doesn’t offer half the security of 256-bit encryption. Although still formidable, experts believe that 128-bit encryption will soon be broken .
These encryption methods and strengths are normally applied automatically, depending on which application we use, such as email, browsers, or other programs. VPNs on the other hand allow us to choose what types of encryption we want, since the type we choose will affect our VPN performance.
In this way we can ‘adjust’ the performance of our VPN service. For example, some may prefer extreme encryption and be willing to sacrifice speed. Others may prefer speed and so accept a lower level of encryption.
All of this is necessary and affected by encryption because when you’re logged in to a VPN service, the data you send when trying to browse the Internet goes through the encrypted VPN connection.
I have now been researching, testing and experimenting on VPNs for the better part of a year. While I may not be a technical expert at VPNs yet, I have for sure found out more than I’ve ever really wanted to about these services.
My experiments have included the use of VPNs on various platform, including their android mobile apps , browser plugins and with different usage models. Some I’ve been pleasantly surprised at, but some utterly disappointed in.
I have to say that at the end of the day, no matter the capabilities of a product, there is absolutely no reason for any of these companies to have bad customer service. And yes, I rate incompetence and sloth as ‘bad customer service’.
For the most part, my tests were carried out using either an open source VPN client or a VPN app installed on a Windows-based machine. These are usually fine, and I have found that it is usually the case whereby the hardware we have at home limits our VPN more than the service itself.
The most important thing I learned about equipment is that if you intend to deploy the VPN directly on your router, you need to be aware of one very important factor – your VPN must have a kick-ass processor. These are usually limited to the ‘oh-my-God’ price range of consumer wireless routers, and even then, are quite limited.
As an example, I tried a few VPNs on a lowly Asus RT-1300UHP which if fine for most homes. It certainly can handle even full gigabit speeds (via LAN) and up to 400+ Mbps on WiFi. Yet it only managed a throughput of about 10 Mbps once the VPN was set up. At that rate, the processor was already straining at 100% constantly.
The kind of router you need that we’re talking about is in the range of the ROG Rapture GT-AC5300 or Netgear Nighthawk X10 – Expensive and not the norm for most households. Even then, if your Internet speeds are fast – the bottleneck will remain your router.
I started out testing VPNs on a 50 Mbps line which was giving me close to advertised speeds – I usually got around 40-45 Mbps. Eventually I shifted to a 500 Mbps line for which I get around 80% of advertised speeds – normally 400-410 Mbps.
It was only when I shifted to a higher speed line that I realised many VPNs struggle to manage at such speeds due to a combination of factors. This includes the machine you run it on, the distance between you and the VPN server you choose, what encryption rates you prefer, and more.
At first it was mostly speed testing, just to keep a track record as well as experiment. Once I had established a baseline, I began to test other download sites or streaming videos. For the most part, I found that almost all VPNs are capable of streaming 4k UHD videos.
Torrenting was tested as well, of course, and I found that a little disappointing. I think that once your home Internet speeds reach a certain point, you’ll find that the performance of your VPNs service drops dramatically unless you invest significantly into better infrastructure.
I don’t really game much (at least not the games that matter for VPN performance) but I did take note of ping times. If you’re a gamer hoping to use a VPN to access a game that’s out of your country, you might be disappointed. Ping times increase a lot the further you are from the VPN servers, even if speeds are fast and stable.
A VPN is designed to mask and protect your location and data, but you still require an Internet connection.
Like all service providers, VPN companies want you to stay with them for a long time, since that’s their income stream. Most VPN service providers offer various terms of payments such as monthly, quarterly and so on. Most times the longer the plan, the cheaper your monthly rate will be, but you will have to pay the entire contract in advance. Expect to pay between $9 to $12 per month on average for monthly contracts, with discounts of up to 75% for long term contracts. Here's the list of best VPN services where we compare the prices and features.
VPNs are designed first and foremost to protect your identity and keep your data safe. Unfortunately, one of the side effects of encryption that is used to protect your data is that it slows down your Internet connection. As a rule of thumb, expect to achieve no more than 70% of your actual line speed when using a VPN. Other factors such as distance from VPN server, server load and so on will also affect your Internet speed while using a VPN .
Most VPN service providers will tell you that they will not limit your speed. However, there are other circumstances to consider as well. As mentioned above, expect to get no more than a maximum of 70% of your actual line speed.
By right it should be as simple as installing an application and entering your username and password. Then all you must do is click a button and you’ll be connected to a VPN server. Unfortunately, this isn’t always the best solution and some connections may need to be tweaked for optimal performance. Many VPN service providers such as NordVPN , Surfshark and ExpressVPN will have tutorials on how to do this, failing which it’s time to get in touch with their customer service staff.
This depends on which VPN service provider you sign up with. Almost all providers will support Windows, MacOS, and Linux along with mainstream mobile platforms. Many will also support router deployment ( depending on model of router ) while a few cater to more exotic devices such as the Raspberry Pi.
This is a little tricky, since both encryption rates are quite strong. The question you should be asking yourself should be, ‘How much is my privacy and online safety worth to me?’
Some websites try to keep out VPN users and have ways to detect if an incoming connection is from a VPN server. Thankfully, VPNs are aware of this and have come up with countermeasures which help. Look out for service providers which offer Stealthing, or Server obfuscation.
I’ve tried out a few VPN browser extension and have found that for the most part, these fall into two main categories. There are those which act as proxies and merely bounce your connection off a server, and some which act as a browser control for a full VPN app. The latter means you’ll still need a VPN app installed in order to use the extension. VPN browser extensions are usually not full VPN services.
Yes and No. Although most countries do not have laws against VPN usages, some outright ban it. In extreme cases, some countries not only ban VPN usage but also potentially jail VPN users. Thankfully, there are only a handful of countries where VPNs have been banned so far.
This largely depends on how safely you use your VPN connection and which provider you choose. There have been many cases whereby VPN users have been arrested after putting their faith in a service provider that eventually turned over user logs to authorities.
Personal privacy online is under siege from so many directions and it seems to have happened overnight. Gone are the days when we only had to worry about cyber criminals, but now we also must worry about companies and governments who want to steal our data for the same reason – to exploit for their own purposes.
Naturally, your need for a VPN would largely depend on which country you are in, since each has different threat levels. The question is not something which can be answered by a simple yes or no.
However, from the rate of increase in value of the global VPN market , I will say that it is very likely you’ll need one sooner or later. It is past time that individual users started taking their privacy and security online for granted and look for ways to secure their information.
We have been complacently using the Internet much the same way in which we always have, just browsing as carefree as can be. True, viruses and Malware have made us more cautious, but not much has changed.
Personally, I feel that the adoption of a VPN service should be the next step each Internet user undertakes. There is a pressing need to break out of the mindset that we are not threatened by what we do online.
Take for example someone who just wants to go online and look for a few pictures of some cute cats. While doing that, information such as his/her browsing habits, likes/dislikes, location, and so much more is being collected by authorities or organizations. Isn’t that thought scary enough to compel some form of action?
So, I say yes, even if you think you don’t need a VPN – You really do .
Founder of WebHostingSecretRevealed.net (WHSR) - a hosting review trusted and used by 100,000's users. More than 15 years experience in web hosting, affiliate marketing, and SEO. Contributor to ProBlogger.net, Business.com, SocialMediaToday.com, and more.
* FTC Disclousre: WHSR receive referral fees from companies mentioned in this article.
WebHostingSecretRevealed (WHSR) publishes articles and develops tools for users who help in hosting and building a website.
What Is a VPN ? - Virtual Private Network - Cisco
Virtual Private Network ( VPN ): A Very Detailed Guide for Newbies - WHSR
What is a VPN ? Virtual Private Networks Explained
VPN .net – Hamachi by LogMeIn | Create virtual private networks on-demand
Virtual Private Networking ( VPN ) | Microsoft Docs
Home
Network Access Control
Virtualization
VPN (virtual private network)
This was last updated in December 2020
Related Terms
Martian address (Martian packet)
A Martian address is a source or destination IP address that apparently does not exist on Planet Earth and is, thus, invalid and/...
See complete definition
RIFAN 2
Reseau Internet de la Force Aeronavale etape 2 (RIFAN 2) is a secure internet developed for military applications.
See complete definition
What is zero trust? Ultimate guide to the network security model
Zero trust is a security strategy that assumes all users, devices and transactions are already compromised. The zero trust model ...
See complete definition
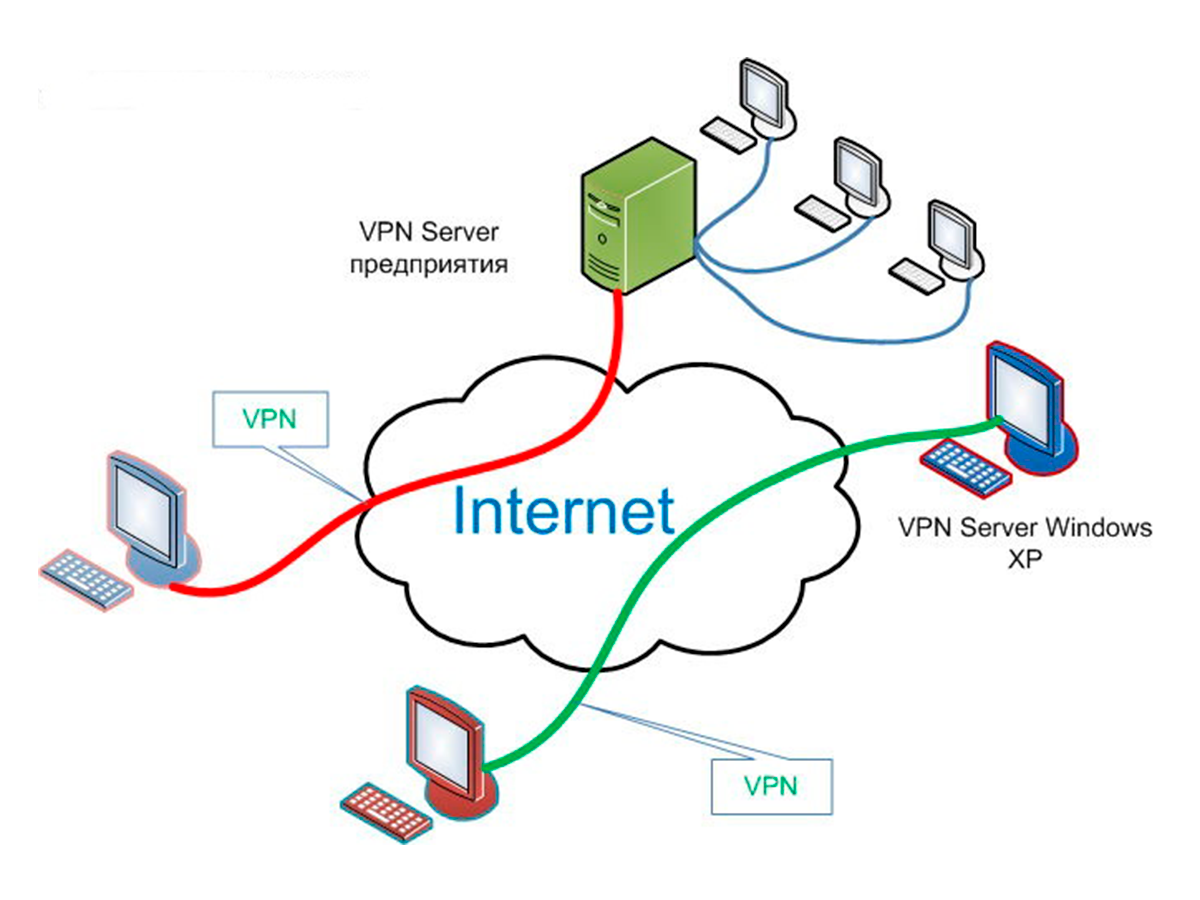
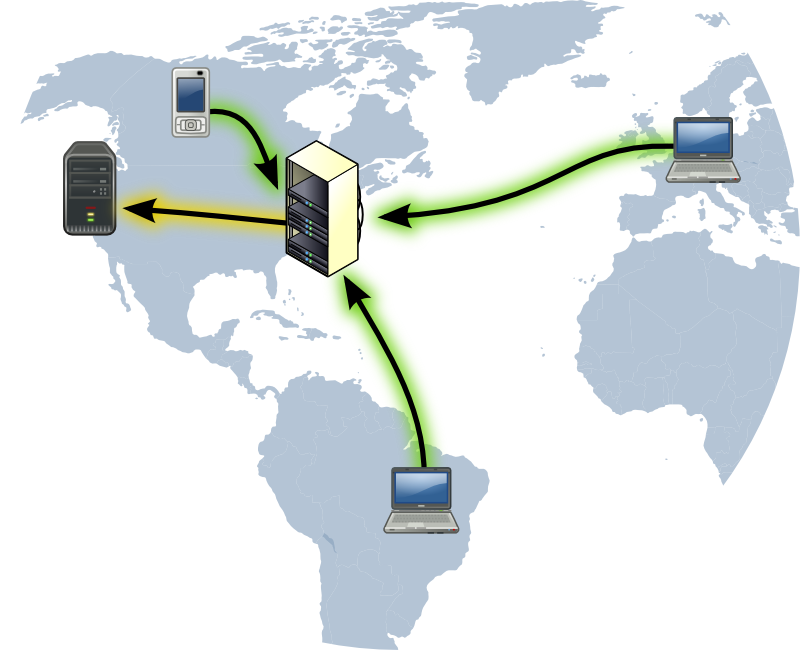
A VPN (virtual private network) is a service that creates a safe, encrypted online connection. Internet users may use a VPN to give themselves more privacy and anonymity online or circumvent geographic-based blocking and censorship. VPNs essentially extend a private network across a public network , which should allow a user to securely send and receive data across the internet.
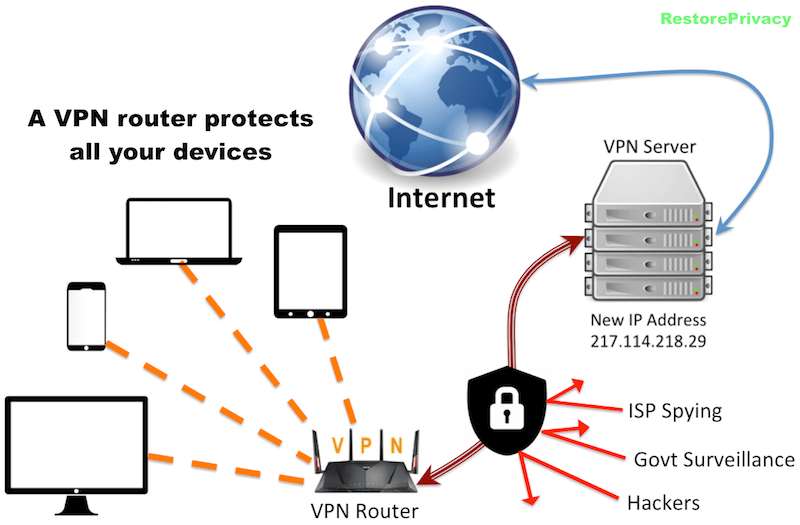
Typically, a VPN is used over a less secure network, such as the public internet. Internet service providers (ISPs) normally have a rather large amount of insight into a customer's activities. In addition, some unsecured Wi-Fi access points (APs) may be a convenient avenue for attackers to gain access to a user's personal data. An internet user could use a VPN to avoid these encroachments on privacy.
VPNs can be used to hide a user's browser history, Internet Protocol (IP) address and geographical location, web activity or devices being used. Anyone on the same network will not be able to see what a VPN user is doing. This makes VPNs a go-to tool for online privacy.
A VPN uses tunneling protocols to encrypt data at the sending end and decrypts it at the receiving end. The originating and receiving network addresses are also encrypted to provide better security for online activities.
VPN apps are often used to protect data transmissions on mobile devices. They can also be used to visit websites that are restricted by location. However, secure access through a mobile VPN should not be confused with private browsing. Private browsing does not involve encryption; it is simply an optional browser setting that prevents identifiable user data from being collected.
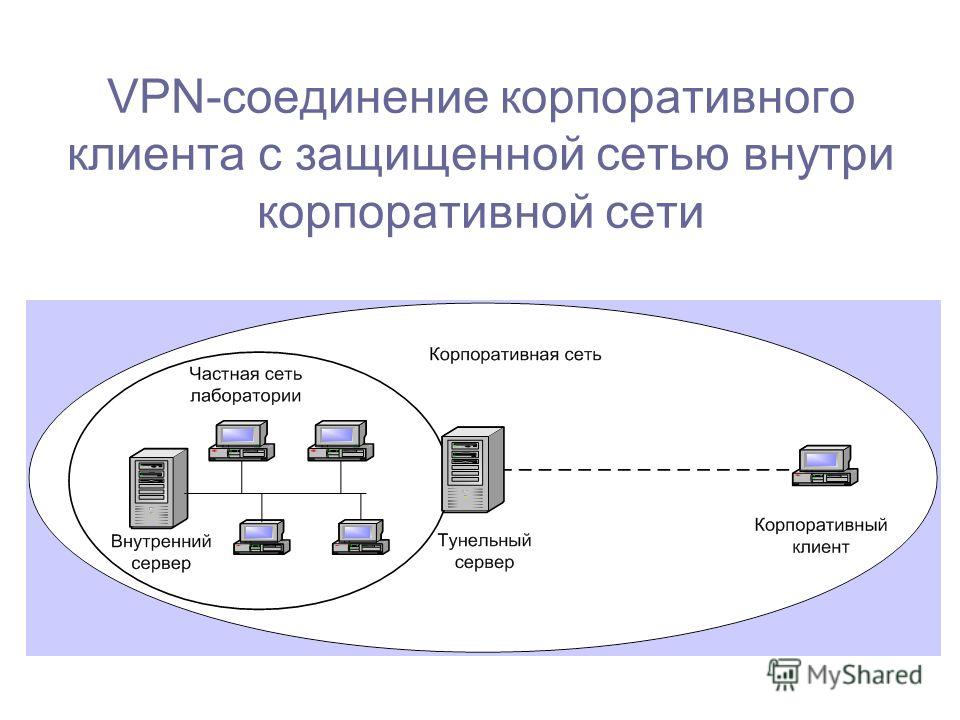
VPNs are used for virtual privacy by both normal internet users and organizations. Organizations may use a VPN in order to make sure any outside users that access their data center are authorized -- using encrypted channels. They can also use a VPN to connect to a database from the same organization located in a different area.
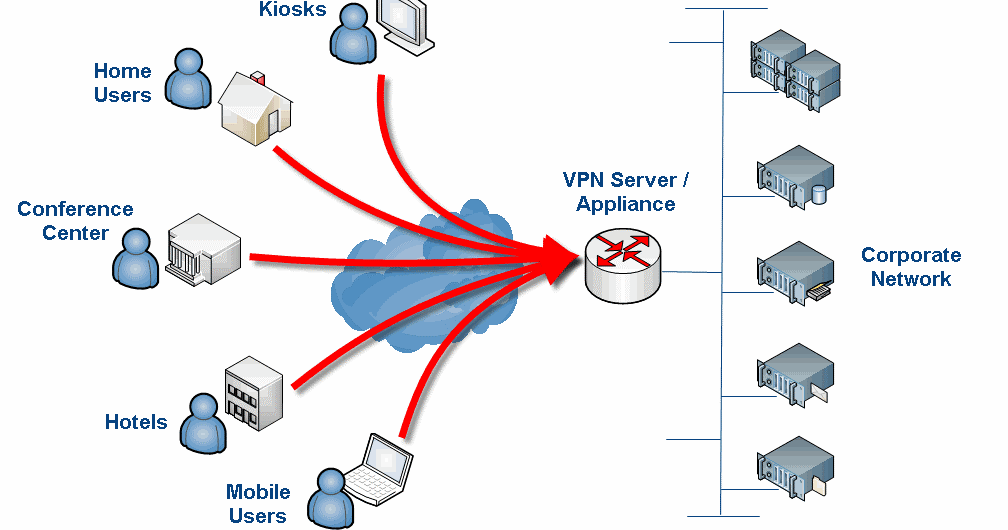
VPNs can also be used to provide remote employees, gig economy freelance workers and business travelers with access to software applications hosted on proprietary networks . To gain access to a restricted resource through a VPN, the user must be authorized to use the virtual private network app. They must provide one or more authentication factors. These can be passwords, security tokens or biometric data.
When surfing the web, an internet user could have information, including browsing habits or IP address, accessed by an attacker. If privacy is a concern, then a VPN can provide a user with peace of mind. Encryption, anonymity and the ability to get around geographically blocked content is what most individuals find valuable in a VPN. In addition, ISPs have been known to throttle a user's internet when using video services like Netflix, which is also closely related to net neutrality .
The ability to get around blocked content from another country, for example, might be extremely useful for journalists. If a country is likely to block internet content off from foreign entities, then journalists could use a VPN to look like they are within that country.
At its most basic level, VPN tunneling creates a point-to-point connection that cannot be accessed by unauthorized users. To actually create the tunnel, a tunneling protocol is used over existing networks. Different VPNs will use different tunneling protocols, such as OpenVPN or Secure Socket Tunneling Protocol (SSTP). The protocol used may depend on the platform the VPN is being used on, such as SSTP being used on Windows OS, and will provide data encryption at varying strengths. The endpoint device needs to be running a VPN client (software application) locally or in the cloud. The client will run in the background. It is not noticeable to the end user unless there are performance issues.
By using a VPN tunnel, a user's device will connect to another network while data is encrypted and IP address is hidden. This is what will hide private information from attackers or others hoping to get access to an individual's activities. The tunnel will connect a user's device to an exit node in another distant location, which makes it seem like the user is in another location.
VPNs will associate a user's search history with the VPN server's IP address. VPN services will have servers located in different geographical areas, so it will look like the user could be from any one of those locations.
The performance can be affected by many factors, like the speed of users' internet connections, the protocol types a VPN provider may use and the type of encryption it uses. In the enterprise, performance can also be affected by poor quality of service (QoS) outside the control of an organization's information technology (IT) department.
A kill switch is a last resort security feature in some VPN products. If the VPN connection is disrupted, the kill switch will automatically disconnect the device from the internet. This way, there is no chance of IP address exposure.
There are two types of kill switches:
VPN protocols ensure an appropriate level of security to connected systems when the underlying network infrastructure alone cannot provide it. There are several different protocols used to secure and encrypt users and corporate data. They include the following:
Benefits of using a VPN include the following:
Challenges of using a VPN, however, include the following:
Any device that accesses an isolated network through a VPN presents a risk of bringing malware to that network environment -- that is, unless there's a requirement in the VPN connection process to assess the state of the connecting device. Without an inspection to determine whether the connecting device complies with an organization's security policies, attackers with stolen credentials can access network resources, including switches and routers .
Security experts recommend that network administrators consider adding software-defined perimeter ( SDP ) components to their VPN protection infrastructure in order to reduce potential attack surfaces. The addition of SDP programming gives medium and large organizations the ability to use a zero-trust model for access to both on-premises and cloud network environments.
Network administrators have several options when it comes to deploying a VPN.
Remote access clients connect to a VPN gateway server on the organization's network. The gateway requires the device to authenticate its identity before granting access to internal network resources. This type usually relies on either IPsec or SSL to secure the connection.
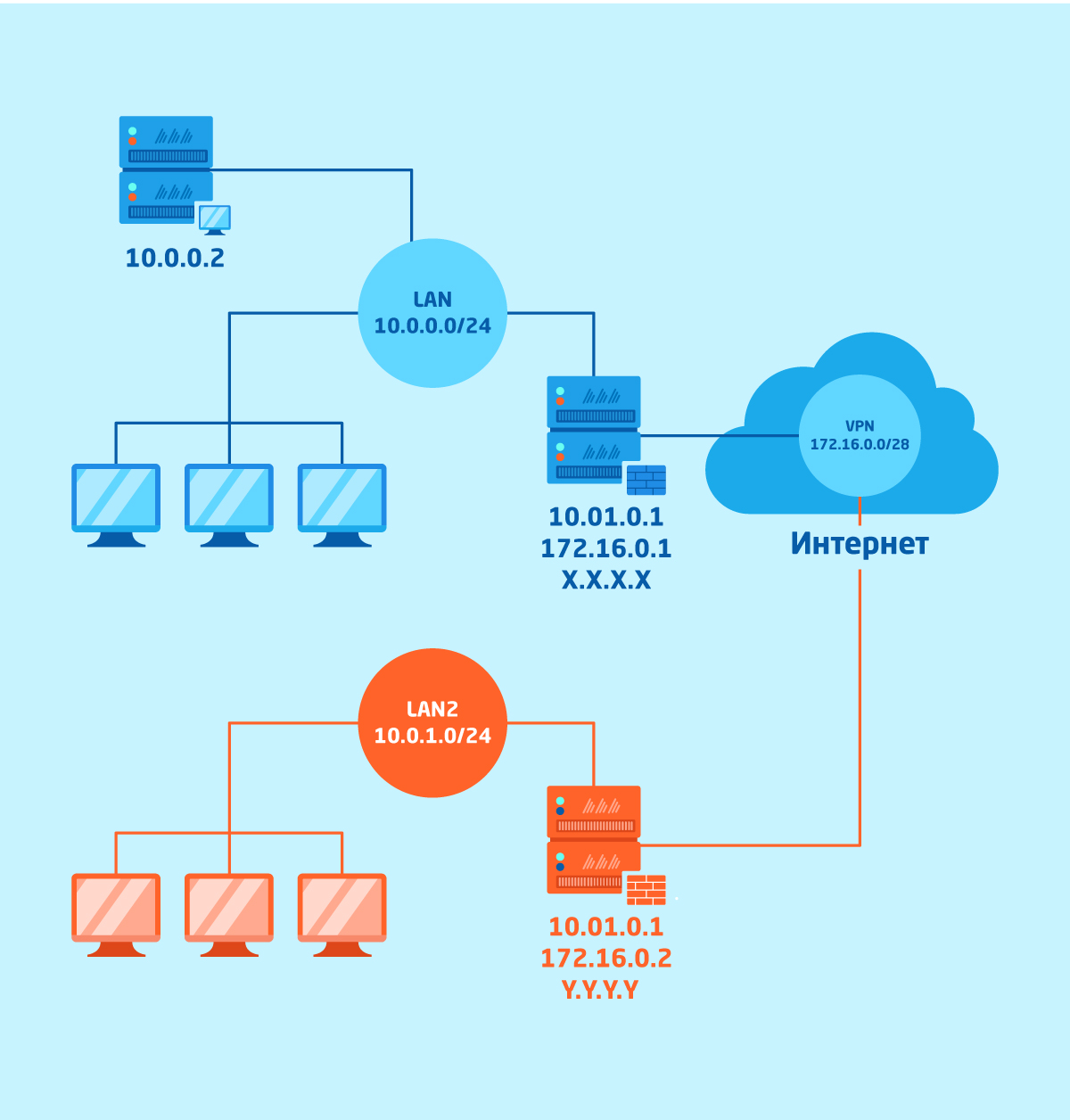
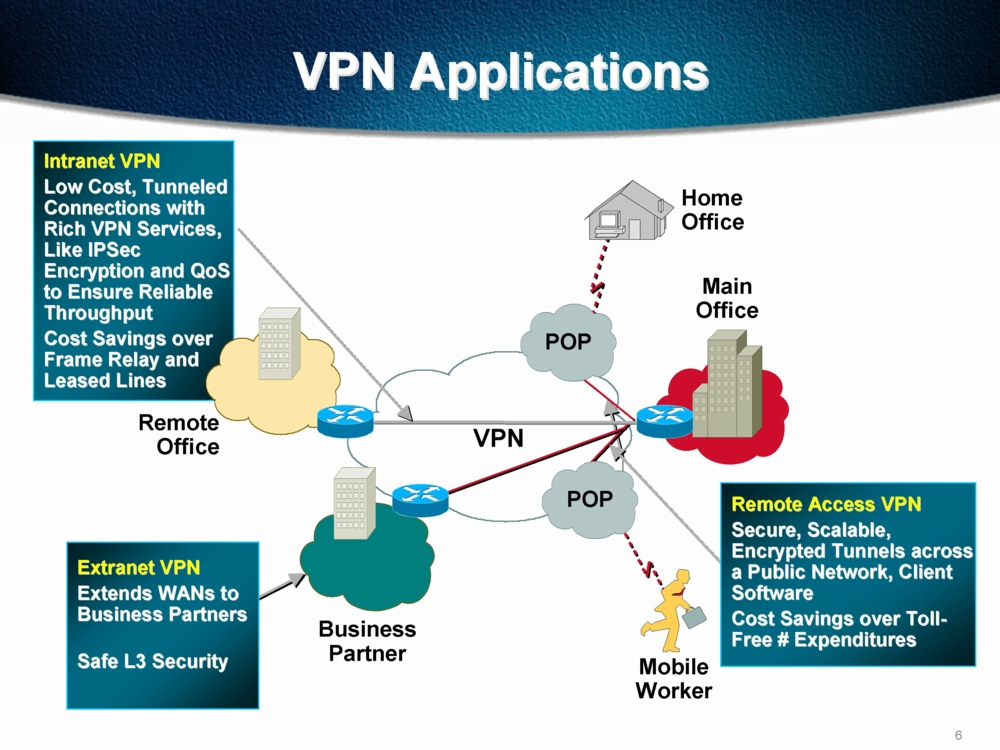
In contrast, a site-to-site VPN uses a gateway device to connect an entire network in one location to a network in another location. End-node devices in the remote location do not need VPN clients because the gateway handles the connection. Most site-to-site VPNs connecting over the internet use IPsec. It is also common for them to use carrier Multiprotocol Label Switching ( MPLS ) clouds rather than the public internet as the transport for site-to-site VPNs. Here, too, it is possible to have either Layer 3 connectivity (MPLS IP VPN) or Layer 2 ( virtual private local area network service ) running across the base transport.
In a mobile VPN , the server still sits at the edge of the company network, enabling secure tunneled access by authenticated, authorized clients. Mobile VPN tunnels are not tied to physical IP addresses, however. Instead, each tunnel is bound to a logical IP address. That logical IP address sticks to the mobile device, no matter where it may roam. An effective mobile VPN provides continuous service to users and can switch across access technologies and multiple public and private networks.
Hardware VPNs offer a number of advantages over strictly software-based ones. In addition to enhanced security, hardware VPNs can provide load balancing for large client loads. Administration is managed through a web browser interface. A hardware VPN is more expensive than a software-based one. Because of the cost, hardware VPNs are more viable for larger businesses. Several vendors, including Irish vendor InvizBox, offer devices that can function as hardware VPNs.
A VPN appliance , also known as a VPN gateway appliance , is a network device with enhanced security features. Also known as an SSL VPN appliance , it is a router that provides protection, authorization, authentication and encryption for VPNs.
A DMVPN exchanges data between sites without needing to pass through an organization's headquarter VPN server or router. A DMVPN creates a mesh VPN service that runs on VPN routers and firewall concentrators . Each remote site has a router configured to connect to the company's headquarters device ( hub ), providing access to the resources available. When two spokes are required to exchange data between each other -- for a voice over IP ( VoIP ) telephone call, for example -- the spoke will contact the hub, obtain the needed information about the other end and create a dynamic IPsec VPN tunnel directly between them.
VPN services are available in free or paid options. Paid vendor options tend to be recommended more often than free ones, however. Some example vendors include the following:
VPNs are legal in the United States; however, one should first check if they are legal in their own country first.
Many VPNs will offer what is close to the same technologies, so it can be hard to choose which VPN will work best. Paid VPN services tend to be more trusted and include other security features. Good VPN services will be upfront about their security, their strengths and weaknesses, and their transparency -- for example, by releasing third-party audits. So, when looking for a vendor, these traits and features should be on a potential customer's mind. Extra features that a VPN can have include split tunneling, access to the Tor network or multihop connections.
Once individuals look at the added features and find a service they think will work for them, then it is a good idea to start out with a short-term subscription. Many vendors will offer free trials of their paid versions. Some free trial versions may, however, include a limit to how much data can be used. The price of VPNs may range anywhere from $10-$13 a month.
VPN technology started in 1996 when a Microsoft employee developed the PPTP. The protocol creates a more secure private connection between a user device and the internet. A few years later, in 1999, this specification was published. As the need for a more secure connection to the internet rose, VPNs started their rise.
In the early 2000s, VPNs were mostly associated with and used by businesses. The technology wasn't quite yet in use by average online users. At this time, VPNs were being used by businesses to access private business networks. In this use case, organizations were able to access company data from anywhere while looking as if they were in the office. Secure file sharing between different offices became possible.
After this, encryption standards started to become more powerful, and new tunneling protocols started to be developed. As individuals started to learn of potential online threats and privacy issues, VPNs started to see a turn to a new market: individual, at-home users. Third-party VPN services began to be formed. Privacy scandals, such as WikiLeaks or the separate security leaks by Edward Snowden, injected themselves into the modern zeitgeist. Around 2017, internet users in the United States started to learn that ISPs could collect and sell their browsing history, and net neutrality became a concept citizens had to fight for -- and effectively lost. A bill in 2019 was passed by the U.S. House to bring back net neutrality but was ultimately blocked by the Senate and president. Since this time, different states have enacted versions of net neutrality laws. With this knowledge, the concept of VPNs rose to a more legitimate need for individuals.
Direct Routing for Microsoft Teams may be the best path to the PSTN for most companies. But organizations should weigh their ...
Verizon has resolved an issue in its fiber optic network that led to a major outage Tuesday. The outage affected tens of ...
Starting in mid-2021, Microsoft and SAP plan to integrate Teams into the latter's business application portfolio. The move is ...
The Korean manufacturer plans to ship large quantities of the 14-inch 90 Hz display by the end of the quarter. Potential buyers ...
There are plenty of viable Windows tablets for business tasks, but each tablet has unique features and components that purchase ...
Samsung has dropped the starting price of its latest Galaxy phones by 20%. The S21 line will start at $800 when it goes on sale ...
Top CTOs and analysts predict hyperscale architecture, hybrid cloud, IT as a service, containers and AI infrastructure will be ...
UPSes can provide backup power scalability and efficiency. Admins should consider modular setups for extra redundancy, mixed ...
Reporting its sharpest decline in five years, IBM revenues for 2020 dove 5%. CEO Arvind Krishna highlights opportunities and vows...
MSP software house ConnectWise has acquired Service Leadership Inc., a consultancy that offers financial and operational ...
The chore of revitalizing the mainframe involves a range of approaches and may call for modern languages, microservices and cloud...
Big Blue said it has laid the groundwork to rapidly grow hybrid cloud and AI business through its partner ecosystem, which ...
All Rights Reserved,
Copyright 2000 - 2021 , TechTarget
Privacy Policy
Cookie Preferences
Do Not Sell My Personal Info
Mature Teen Boy
Outdoor Legs
Homemade Big Naturals
Private Jpg
Wife Oral Sex