Virtual Private

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Virtual Private
Sign up with email
Sign up
Sign up with Google
Sign up with GitHub
Sign up with Facebook
Active
2 years, 8 months ago
c++ polymorphism access-specifier
6,789 10 10 gold badges 28 28 silver badges 23 23 bronze badges
I think the question is backwards. The reason for making something virtual is always the same: to allow derived classes to override it. So the question should be: what is the advantage of making a virtual method private? To which the answer is: make everything private by default. :-)
– ShreevatsaR
Apr 2 '14 at 16:58
@ShreevatsaR But you didn't even answer your own question......
– Spencer
Mar 1 '18 at 23:35
@ShreevatsaR I thought you mean backwards in a different way: What is the advantage of making a virtual method not private?
– Peter - Reinstate Monica
Oct 22 '19 at 8:24
84.5k 43 43 gold badges 230 230 silver badges 336 336 bronze badges
As you might guess from my answer, I think Sutter's guideline #3 rather shoves guideline #2 out the window.
– Spencer
Nov 9 '16 at 14:52
What if a derived class needs to override the method but call the parent method from inside there? That's common enough that I can't imagine private virtuals being recommended if it blocks that. Does C++ have a mechanism like super(...) to call the parent method from within an overridden version, which works even if it's private?
– flarn2006
Aug 14 '20 at 2:28
14.8k 33 33 silver badges 57 57 bronze badges
196k 49 49 gold badges 260 260 silver badges 352 352 bronze badges
It appears that the C++ FAQ Lite has since changed its recommendation: " the C++ FAQ formerly recommended using protected virtuals rather than private virtuals. However the private virtual approach is now common enough that confusion of novices is less of a concern. "
– Zack The Human
Apr 1 '12 at 5:37
Confusion of experts, however, remains a concern. None of the four C++ professionals sitting next to me were aware of private virtuals.
– Newtonx
Apr 20 '17 at 22:13
1,020 8 8 silver badges 22 22 bronze badges
I find your argument invalid. You as a developer of an API should strive for an interface that is hard to use incorrectly and not set another developer up for your own mistakes in doing so. What you want to do in your example could be implemented with only private virtual methods.
– sigy
Jan 18 '17 at 9:18
That's not what I was saying. But you can restructure your code to achieve the same effect without the need to call a private base class function
– sigy
Jan 18 '17 at 14:14
In your example you want to extend the behavior of set_data . Instructions m_data = ndata; and cleanup(); could thus be considered an invariant that must hold for all implementations. Therefore make cleanup() non-virtual and private. Add a call to another private method that is virtual and the extension point of your class. Now there is no need for your derived classes to call base's cleanup() anymore, your code stays clean and your interface is hard to use incorrectly.
– sigy
Jan 18 '17 at 14:38
@sigy That just moves the goalposts. You need to look beyond the miminal example. When there are further descendants that need to call all of the cleanup() s in the chain, the argument falls apart. Or are you recommending an extra virtual function for each descendant in the chain? Ick. Even Herb Sutter allowed protected virtual functions as a loophole in his guideline #3. Anyway, without some actual code you'll never convince me.
– Spencer
Jan 18 '17 at 14:52
Then let's agree to disagree ;)
– sigy
Jan 18 '17 at 14:54
1,509 1 1 gold badge 21 21 silver badges 42 42 bronze badges
1,204 14 14 silver badges 5 5 bronze badges
Stack Overflow
Questions
Jobs
Developer Jobs Directory
Salary Calculator
Help
Mobile
Disable Responsiveness
Products
Teams
Talent
Advertising
Enterprise
Company
About
Press
Work Here
Legal
Privacy Policy
Terms of Service
Contact Us
Stack Exchange Network
Technology
Life / Arts
Culture / Recreation
Science
Other
Join Stack Overflow to learn, share knowledge, and build your career.
What is the advantage of making a private method virtual in C++?
I have noticed this in an open source C++ project:
Herb Sutter has very nicely explained it here .
Guideline #2: Prefer to make virtual functions private.
This lets the derived classes override the function to customize the behavior as needed, without further exposing the virtual functions directly by making them callable by derived classes (as would be possible if the functions were just protected). The point is that virtual functions exist to allow customization; unless they also need to be invoked directly from within derived classes' code, there's no need to ever make them anything but private
If the method is virtual it can be overridden by derived classes, even if it's private. When the virtual method is called, the overridden version will be invoked.
(Opposed to Herb Sutter quoted by Prasoon Saurav in his answer, the C++ FAQ Lite recommends against private virtuals , mostly because it often confuses people.)
Despite all of the calls to declare a virtual member private, the argument simply doesn't hold water. Frequently, a derived class's override of a virtual function will have to call the base class version. It can't if it's declared private :
You have to declare the base class method protected .
Then, you have to take the ugly expedient of indicating via a comment that the method should be overridden but not called.
Thus Herb Sutter's guideline #3...But the horse is out of the barn anyway.
When you declare something protected you're implicitly trusting the writer of any derived class to understand and properly use the protected internals, just the way a friend declaration implies a deeper trust for private members.
Users who get bad behavior from violating that trust (e.g. labeled 'clueless' by not bothering to read your documentation) have only themselves to blame.
Update : I've had some feedback that claims you can "chain" virtual function implementations this way using private virtual functions. If so, I'd sure like to see it.
The C++ compilers I use definitely won't let a derived class implementation call a private base class implementation.
If the C++ committee relaxed "private" to allow this specific access, I'd be all for private virtual functions. As it stands, we're still being advised to lock the barn door after the horse is stolen.
I first came across this concept while reading Scott Meyers' 'Effective C++', Item 35: Consider alternatives to virtual functions. I wanted to reference Scott Mayers for others that may be interested.
It's part of the Template Method Pattern via the Non-Virtual Interface idiom : the public facing methods aren't virtual; rather, they wrap the virtual method calls which are private. The base class can then run logic before and after the private virtual function call:
I think that this is a very interesting design pattern and I'm sure you can see how the added control is useful.
From a C++ perspective, it's completely legitimate to override a private virtual method even though you won't be able to call it from your class. This supports the design described above.
I use them to allow derived classes to "fill in the blanks" for a base class without exposing such a hole to end users. For example, I have highly stateful objects deriving from a common base, which can only implement 2/3 of the overall state machine (the derived classes provide the remaining 1/3 depending on a template argument, and the base cannot be a template for other reasons).
I NEED to have the common base class in order to make many of the public APIs work correctly (I'm using variadic templates), but I cannot let that object out into the wild. Worse, if I leave the craters in the state machine- in the form of pure virtual functions- anywhere but in "Private", I allow a clever or clueless user deriving from one of its child classes to override methods that users should never touch. So, I put the state machine 'brains' in PRIVATE virtual functions. Then the immediate children of the base class fill in the blanks on their NON-virtual overrides, and users can safely use the resulting objects or create their own further derived classes without worrying about messing up the state machine.
As for the argument that you shouldn't HAVE public virtual methods, I say BS. Users can improperly override private virtuals just as easily as public ones- they're defining new classes after all. If the public shouldn't modify a given API, don't make it virtual AT ALL in publicly accessible objects.
By clicking “Post Your Answer”, you agree to our terms of service , privacy policy and cookie policy
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
site design / logo © 2021 Stack Exchange Inc; user contributions licensed under cc by-sa . rev 2021.2.2.38474
What Is a VPN? - Virtual Private Network - Cisco
polymorphism - Private virtual method in C++ - Stack Overflow
Types of Virtual Private Network (VPN) and its Protocols - GeeksforGeeks
Virtual Private Networking (VPN) | Microsoft Docs
Virtual Private Server (VPS) | Белтелеком
Types of Virtual Private Network (VPN) and its Protocols
Last Updated :
10 Apr, 2019
Difference Between Virtual Private Network (VPN) and Proxy
Difference between Virtual Private Network (VPN) and Multi-Protocol Label Switching (MPLS)
Introduction to Virtual Private Network (VPN)
Difference between site to site VPN and remote access VPN
Difference between Express VPN and IPVanish VPN
Network Protocols and Communications
14 Most Common Network Protocols And Their Vulnerabilities
Routing v/s Routed Protocols in Computer Network
Controlled Access Protocols in Computer Network
Multiple Access Protocols in Computer Network
Collision-Free Protocols in Computer Network
Virtual Circuit in Computer Network
Know your public and private IP addresses
Difference between Private key and Public key
Difference between Private and Public IP addresses
Difference between Storage Area Network (SAN) and Network Attached Storage (NAS)
Differences between Wireless Adhoc Network and Wireless Sensor Network
favorite_border
Like
Sandwich Testing | Software Testing
Software Engineering | Software Review
Easy
Normal
Medium
Hard
Expert
Data Structures and Algorithms – Self Paced Course
Ad-Free Experience – GeeksforGeeks Premium
More related articles in Computer Networks
5th Floor, A-118,
Sector-136, Noida, Uttar Pradesh - 201305
Company
About Us
Careers
Privacy Policy
Contact Us
Copyright Policy
Learn
Algorithms
Data Structures
Languages
CS
Subjects
Video Tutorials
Practice
Courses
Company-wise
Topic-wise
How to begin?
Contribute
Write an Article
Write Interview
Experience
Internships
Videos
@geeksforgeeks
, Some rights reserved
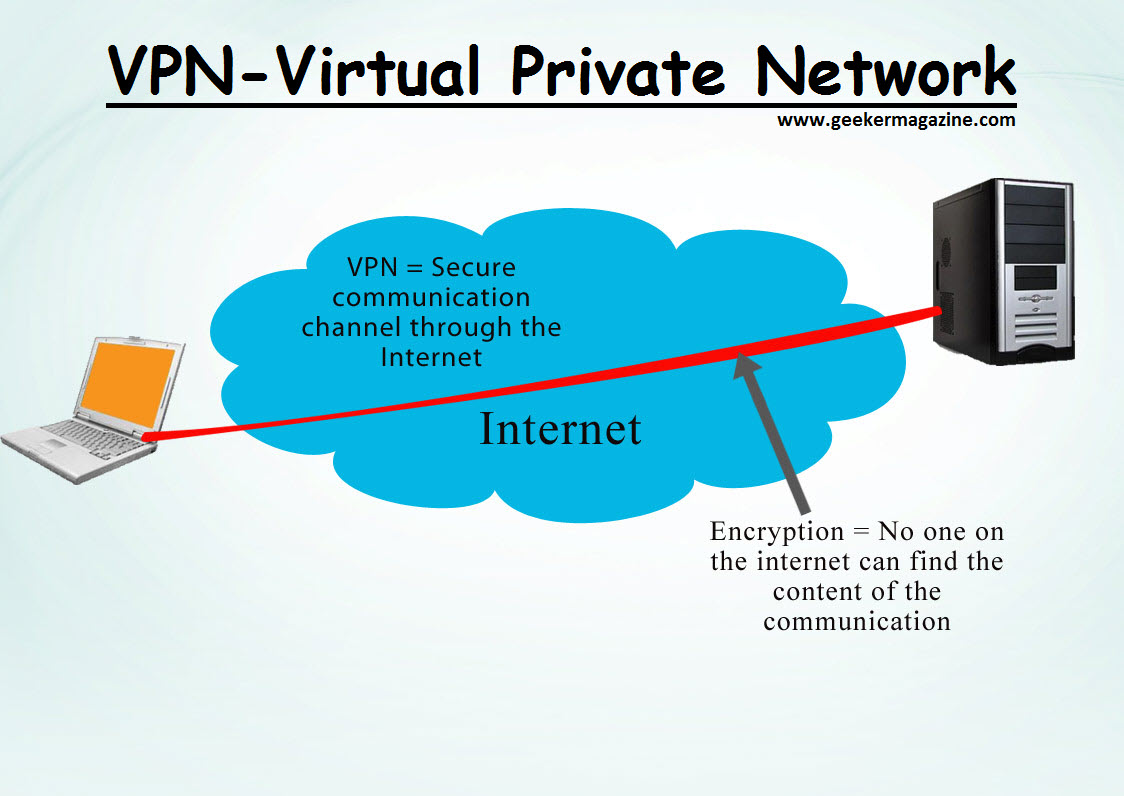
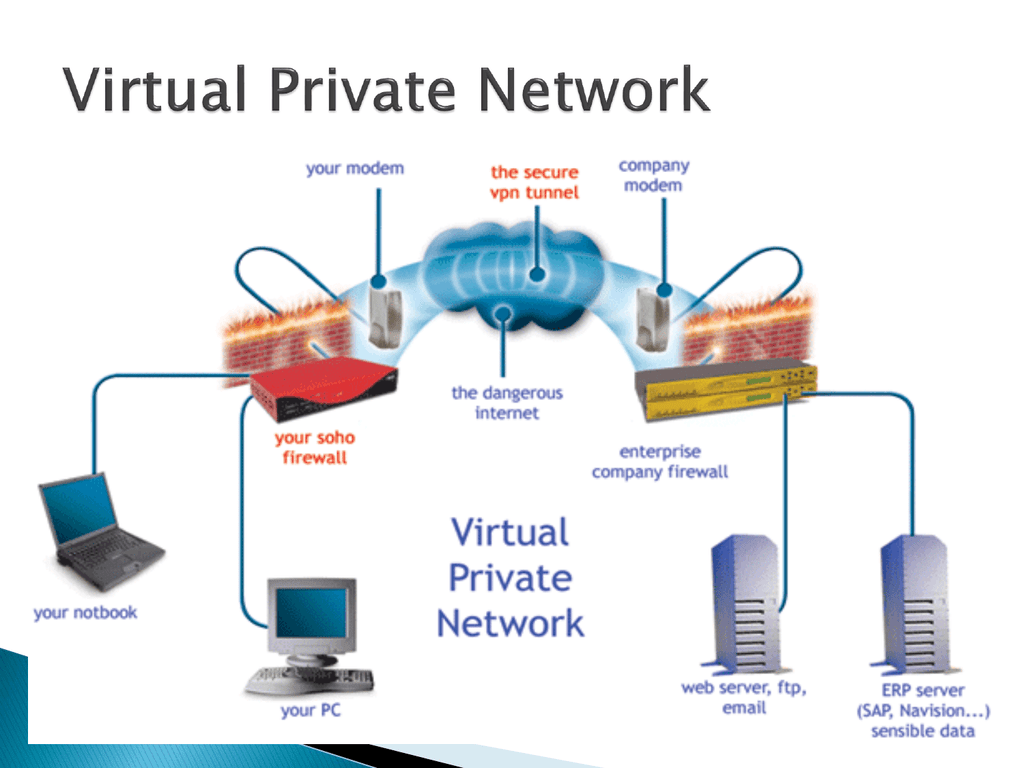
VPN stands for Virtual Private Network (VPN) , that allows a user to connect to a private network over the Internet securely and privately. VPN creates an encrypted connection that is called VPN tunnel, and all Internet traffic and communication is passed through this secure tunnel.
Virtual Private Network (VPN) is basically of 2 types:
An employee of a company, while he/she is out of station, uses a VPN to connect to his/her company’s private network and remotely access files and resources on the private network. Private users or home users of VPN, primarily use VPN services to bypass regional restrictions on the Internet and access blocked websites. Users aware of Internet security also use VPN services to enhance their Internet security and privacy.
Basically, Site-to-site VPN create a imaginary bridge between the networks at geographically distant offices and connect them through the Internet and sustain a secure and private communication between the networks. In Site-to-site VPN one router acts as a VPN Client and another router as a VPN Server as it is based on Router-to-Router communication. When the authentication is validated between the two routers only then the communication starts.
Types of Virtual Private Network (VPN) Protocols:
The work of transport mode is to encrypt the message in the data packet and the tunneling mode encrypts the whole data packet. IPSec can also be used with other security protocols to improve the security system.
Attention reader! Don’t stop learning now. Get hold of all the important CS Theory concepts for SDE interviews with the CS Theory Course at a student-friendly price and become industry ready.
Writing code in comment?
Please use ide.geeksforgeeks.org ,
generate link and share the link here.
Lesbian Me
Big Tits Oral Porn
Hairy Amateur Homemade
Karma Rx Double Penetration
Sexy Lingerie Sets