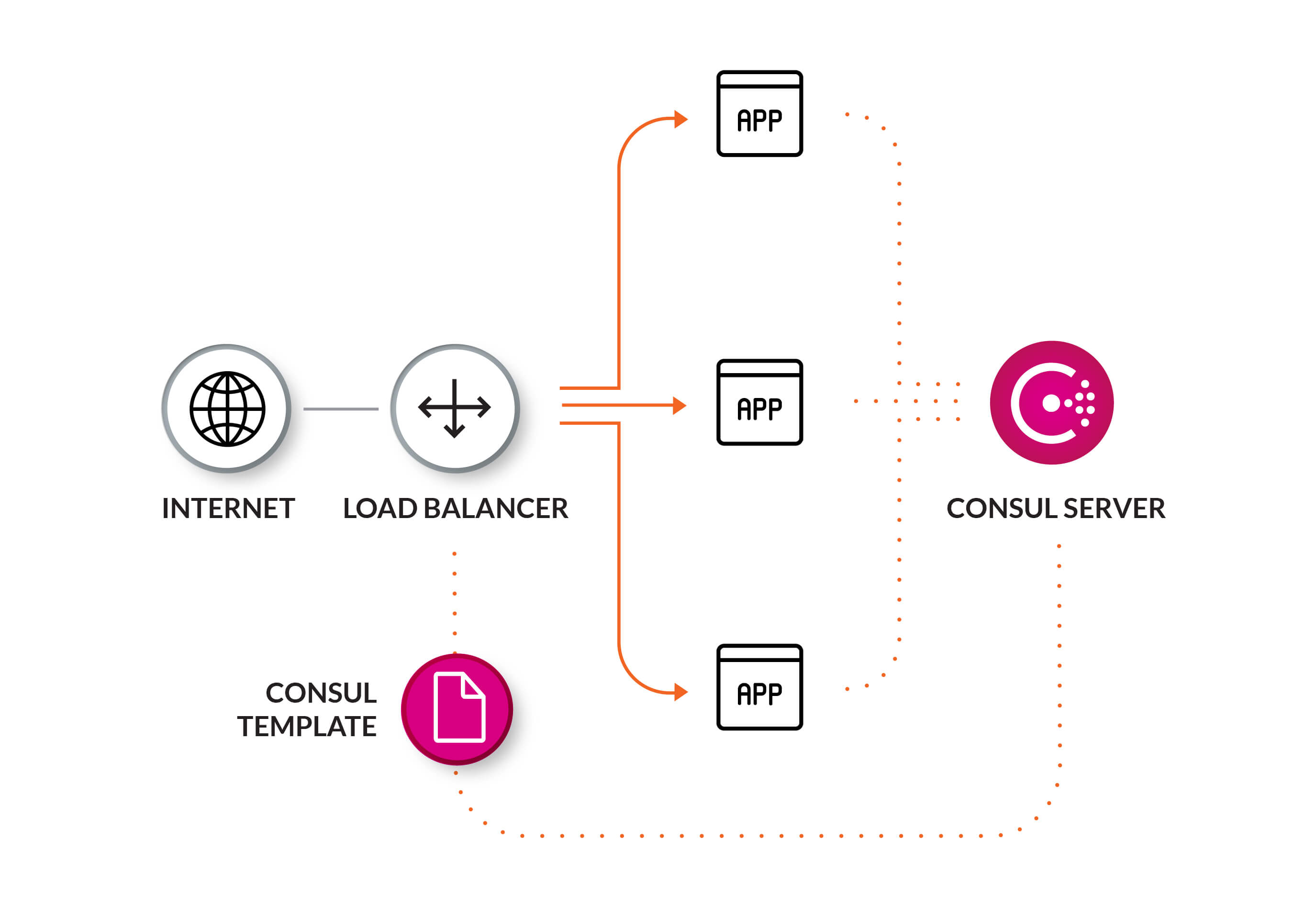
Unable To Load Private Key For Operation

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
Sign up or log in to view your list.
I am new to SSL/OpenSSL and I'm working on Windows 7. I'm trying to configure HTTPS for my ElasticBeanstalk environment following these instructions.
I'm at Step 2 in "Create a Private Key". After I issue the command to generate the key pair:
However, it does write a key to my directory. But after the second command:
I've tried Googling this a bit, but none of the solutions I've found seem to be relevant for me. I checked the generated key and it looks like
ethan123
ethan123 1,074●11 gold badge●1313 silver badges●2525 bronze badges
jww
85.3k●7272 gold badges●348348 silver badges●760760 bronze badges
unable to load Private Key 6312:error:0906D06C:PEM routines:PEM_read_bio:no start line:pem_lib.c:647:Expecting: ANY PRIVATE KEY
I ran your commands on OS X, and I could not reproduce the results.
I did use the -config option because I have an "OpenSSL server config template" that makes it easy to generate CSRs and self signed certificates:
The configuration file is named example-com.conf, and you can find it at How do I edit a self signed certificate created using openssl xampp?. Edit it to suit your taste (in particular, the DNS names).
If interested, here's the OpenSSL man pages on the req sub-command.
I checked the generated key and it looks like
-----BEGIN RSA PRIVATE KEY-----
{lots of characters}
-----END RSA PRIVATE KEY-----
You can validate the key you just created with:
This is a well known problem. OpenSSL uses a default configuration file. You can locate the configuration file with correct location of openssl.cnf file.
The default configuration file includes these lines:
To save the random file, you should point HOME and RANDFILE to a valid location. On Windows, you type set HOME=... and set RANDFILE=... in the command prompt. Or better, change it in the OpenSSL configuration file you use.
I'm trying to configure HTTPS for my ElasticBeanstalk environment following these instructions.
The instructions are wrong in the image below. Do not place a DNS name in the Common Name (CN).
Placing a DNS name in the Common Name is deprecated by both the IETF (the folks who publish RFCs) and the CA/B Forums (the cartel where browsers and CAs collude). You should pay articular attention to what the CA/B recommends because Browsers and CAs come up with those rules, and the browsers follow them (and they don't follow the RFCs). For reference, see RFC 5280, RFC 6125 and the CA/B Baseline Requirements.
Instead, place DNS names in the Subject Alternate Name (SAN). Both the IETF and CA/B specifies it.
The custom OpenSSL configuration file handles this for you. You just have to change the DNS names listed under the section [ alternate_names ]. For example, here's a set of names set up for the domain example.com. Notice there is no DNS name in the CN:
jww
jww 85.3k●7272 gold badges●348348 silver badges●760760 bronze badges
I don't think keyform would help since PEM is the default anyways (according to the docs). -nodes seems not be a good solution since "if this option is specified then if a private key is created it will not be encrypted". The whole point is that its encrypted, no? In any case, I don't think I can upload a key encrypted with a passphrase. – ethan123 Dec 21 '14 at 10:06
@ethan123 - you're right. I was not able to reproduce your results on OS X. What OS are you using? – jww Dec 21 '14 at 19:38
@ethan123 - I updated the answer to include instructions to test the key with the openssl rsa command. – jww Dec 21 '14 at 20:01
Can you check if you have appropriate permissions when you run both the commands? Maybe try doing the same using a user with Admin Rights.
Also make sure the created file privatekey.pem has appropriate permissions before executing the command below (Use chmod if necessary)
Submitting this as answer as I don't have enough reputation to comment.
Dhananjay
Dhananjay 554●44 silver badges●1515 bronze badges
I believe the root of the problem is the error
unable to write 'random state' e is 65537 (0x10001)
Searching StackOverflow found these results. I would stress that you run the openssl program as sudo or directly as root to avoid any possible permissions issues.
"I would stress that you run the openssl program as sudo or directly as root to avoid any possible permissions issues" - that's usually a bad idea. The idea is to avoid root for standard commands, and use it only when needed. – jww Dec 21 '14 at 4:29
@Mark I saw this solution and tried it. It didn't work for me – ethan123 Dec 21 '14 at 10:08
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
You are not logged in. Please login or register.
Please post questions or comments you have about wolfSSL products here. It is helpful to be as descriptive as possible when asking your questions.
You must login or register to post a reply
1 Topic by ravi.kumar 2016-09-10 01:23:03 (edited by ravi.kumar 2016-09-13 22:09:59)
ravi.kumar
Member
Offline
Registered: 2016-09-10
Posts: 18
I am using cyassl-3.3.0 cypto library for our product. I had one certificate consisted of RSA private key, client certificate, one intermediate CA and root CA. Please check the attachment. When I am using example project given with cyassl-3.3.0 or our product, I am getting following error "yassl error: can't load server private key file, check file and run from CyaSSL home dir". I debugged further and found that private key loading is failing from the function GetInt() which is called by RsaPrivateKeyDecode() due to ASN_PARSE_E (-140). I checked the private key through openssl utility of Linux
"openssl rsa -in private_key.pem -text -noout" and found correct parsing with openssl version 1.0.1e-fips 11 Feb 2013. I need help to resolve this issue. I downloaded the latest release wolfssl-3.9.8 from wolfssl site and got the same issue of loading private key failure.
See the out of "openssl rsa -in private_key.pem -text -noout" for the private_key.pem.
Private-Key: (2048 bit)
modulus:
00:d0:17:98:a5:7d:41:9f:45:72:45:c0:d0:e6:9b:
82:9e:02:74:c1:2f:d3:93:ea:83:6e:47:05:7d:88:
23:4c:99:ba:75:88:3f:2b:71:0a:98:76:ad:d2:0f:
82:b7:6a:07:01:72:03:12:f0:c5:be:29:78:f5:cf:
d1:f7:ae:19:d8:03:12:4c:b4:02:31:f6:22:34:11:
0e:10:37:39:4a:55:86:89:63:15:f4:5e:b2:3c:27:
d2:0e:05:16:36:5e:e3:90:dc:4e:da:60:2a:5e:f3:
aa:fe:76:d4:f7:f6:ab:ed:a3:13:6b:23:d3:b8:9d:
cc:68:94:c3:60:cd:4f:73:9f:6b:4d:e3:71:08:8d:
31:05:1e:c0:94:ac:18:f8:86:d1:29:df:55:91:ca:
f3:4e:1d:9a:db:1b:79:15:76:1e:5f:af:98:d9:db:
15:e5:d1:08:cc:9d:76:33:47:bb:f6:49:34:cc:3c:
2f:30:79:84:4c:9f:fa:af:90:bc:30:c6:e4:e1:94:
9d:e2:c6:8f:7e:57:54:1e:8a:86:c7:c1:0a:4e:de:
34:98:13:97:f6:b6:de:a1:a1:1f:c8:71:6b:12:51:
25:b4:fd:66:ca:9d:0e:0d:8a:13:6f:6b:a7:ee:f7:
aa:b7:50:c7:a5:69:57:e4:ab:6b:94:ea:a7:05:59:
13:d1
publicExponent: 65537 (0x10001)
privateExponent:
64:52:bb:f9:2d:06:32:2f:5d:04:5c:0d:5a:e0:a6:
7c:5f:5a:c2:b8:b8:1c:9b:f7:79:77:2c:22:75:3b:
ef:76:3d:fa:e4:10:f0:74:b3:53:06:04:8f:3d:83:
1b:c2:36:56:70:0d:23:58:89:3d:40:e9:5c:39:31:
55:63:ce:79:e2:21:34:71:a4:8d:49:c8:fb:a9:2d:
4a:8c:15:46:cd:2c:eb:97:a5:c2:06:d5:8f:42:f3:
76:66:e5:6a:99:1c:c5:7e:31:55:fe:fe:ee:80:33:
74:32:fe:41:fd:de:ad:d6:ed:49:be:20:18:e5:9a:
e2:e0:b5:c1:39:ba:90:56:ef:da:bf:a7:cc:29:44:
0e:8b:0b:e6:00:d8:81:73:8f:5f:ad:c8:0b:f4:10:
6a:ec:aa:58:a5:9e:20:8d:9c:37:dd:de:9b:80:89:
11:6c:63:d9:13:60:f8:4d:0d:40:ac:57:8f:7d:95:
af:b7:ae:bd:01:61:82:27:34:7a:a9:27:e4:ae:42:
0f:fc:ae:1f:39:d8:0b:a7:2f:64:f3:a8:3e:ea:b9:
15:b1:b3:cf:18:a7:dd:78:cf:c8:1c:8f:07:4d:03:
6e:3d:51:b7:72:56:48:1d:4e:df:b4:a9:5a:57:4b:
8a:fb:11:eb:ea:e4:25:08:9c:98:6e:68:4f:7d:db:
41
prime1:
00:fe:87:76:33:44:5a:37:e1:ce:a3:d4:19:6e:60:
cb:93:95:30:64:0d:83:f4:4a:b0:25:2b:bc:7c:fd:
ee:97:dd:e7:81:a3:90:e1:df:87:b2:fc:4a:5b:d8:
29:e8:fc:02:13:43:57:11:65:6d:85:f0:ec:1a:fa:
67:0d:cc:c9:77:5a:a9:a7:67:5e:b1:0c:6c:fd:fb:
e4:12:49:ac:56:be:eb:b3:d7:b9:c3:a9:a4:b6:b5:
88:ca:23:59:6e:7b:a4:65:25:09:b0:03:b2:d9:9e:
d8:c2:29:b0:1b:eb:e2:86:fb:4e:cb:fd:bc:4e:0c:
8c:bb:51:76:eb:7f:83:9a:85
prime2:
00:d1:4b:70:1a:e5:47:be:e6:74:ae:b6:f0:fd:37:
ab:8c:3e:77:33:ae:a2:9d:25:59:e8:1c:75:e8:6f:
32:c4:ea:40:78:7e:47:0e:0e:bb:c2:fd:05:eb:8f:
47:64:7b:17:63:f1:46:8f:ab:1c:db:de:89:97:89:
46:68:25:12:0d:41:c5:8a:58:cd:8d:42:c2:a4:21:
d0:55:dd:5f:1a:68:7b:34:6c:a5:d9:59:b4:ec:56:
43:12:74:06:01:ad:8e:2b:10:9c:3d:f3:0e:43:20:
54:a2:ad:0e:89:c8:ad:0e:f9:5e:99:e2:7d:f2:8a:
ea:45:0b:a6:cd:a8:12:a3:dd
exponent1:
00:f2:e5:b7:09:29:bb:a7:04:98:bc:83:56:59:9d:
89:e9:27:40:6c:da:f1:08:1a:96:8a:82:78:78:17:
a4:af:cd:16:77:02:ee:ea:7e:f4:f2:fc:0c:c2:25:
41:a9:93:85:2f:78:de:08:3d:f1:0d:17:63:5a:43:
88:41:05:23:66:01:61:51:de:35:e1:63:e8:47:61:
30:bf:bb:0a:fa:25:6c:ad:cd:ba:fb:5c:53:52:01:
5f:ae:f7:99:0a:f4:77:68:06:b6:7e:00:a9:97:40:
1d:be:fd:25:91:1f:c4:a7:e7:ff:c4:70:3a:59:89:
64:6c:06:4c:24:65:25:e4:39
exponent2:
78:b8:03:74:6f:f5:1f:06:3c:1d:1e:46:08:38:19:
09:ae:6a:00:f4:64:b5:31:7b:17:27:7b:56:d2:f4:
bc:a1:c5:07:fb:06:2e:f4:8e:96:5c:6d:12:be:b4:
d6:1f:2d:91:a6:f4:25:1f:f4:68:59:86:91:52:4b:
ba:fc:4e:da:38:aa:a1:2e:b1:79:1e:1d:b8:a0:0c:
53:ca:78:f5:79:78:3e:f7:bf:fd:8b:01:91:23:fc:
51:e3:7c:27:71:9c:c3:f8:33:b6:83:c0:21:35:bf:
bb:89:08:0e:af:22:2a:b5:e9:3b:e7:68:f0:01:f2:
38:5b:0d:1e:28:28:80:3d
coefficient:
00:c4:95:c3:5e:63:fd:17:98:68:56:53:fd:f8:e3:
99:28:40:f9:54:2d:03:52:e4:c9:2d:2c:93:65:bc:
ec:94:5d:fd:bf:1b:b4:4a:4f:18:3b:56:e1:4d:6f:
5c:20:81:64:df:74:7a:d6:e8:cb:cc:23:44:4d:00:
76:3f:6c:29:ee:0c:5a:03:50:0c:34:13:4f:d8:03:
a0:61:22:c4:dd:9f:6f:9f:b2:9b:38:e3:1c:9d:a2:
f1:39:ea:33:bb:8c:52:fa:5e:6b:35:b4:83:a9:3f:
4d:8e:e1:42:31:f7:10:52:43:45:b5:5a:22:b6:b7:
07:fd:48:63:b2:61:84:d8:18
Kaleb J. Himes
Moderator
Offline
From: Bozeman
Registered: 2014-05-09
Posts: 776
The key is improperly formatted. I'm honestly surprised openssl is able to parse it. Just do this command and compare the outputs:
openssl rsa -inform pem -in private_key.pem -outform pem -out private_key_try2.pem
now diff the two files and you'll see they do not match in any way. If you do the same command on our existing ca-key.pem in the /certs directory:
openssl rsa -inform pem -in ca-key.pem -outform pem -out ca-key_try2.pem
and diff those two files they remain identical in every way. Could you tell us where you got that RSA key you are using and how it was generated?
Fix for your issue is to use the resulting "private_key_try2.pem" from the command above. That is RFC compliant formatting and our libraries process it just fine.
3 Reply by Kaleb J. Himes 2016-09-13 09:56:41 (edited by Kaleb J. Himes 2016-09-13 09:58:16)
Kaleb J. Himes
Moderator
Offline
From: Bozeman
Registered: 2014-05-09
Posts: 776
Just as a followup I'll be discussing this with my colleagues and see if there is a fix we might introduce if the original format you sent is RFC compliant as well. We'll be doing some further investigation on this case for sure however testing multiple things and to fix the issue your currently facing it's easy enough to do as noted above and using the re-formatted "private_key_try2.pem".
openssl rsa -inform pem -in private_key.pem -outform pem -out private_key_try2.pem
I have verified the resulting "private_key_try2.pem" contains all the correct information, the modulus, privateExponent, prime1, prime2, exponent1, exponent2, and coefficient are all still the same, the only thing that changes is the hex representation of the key in the .pem file (the .pem format is the only thing that is modified).
We still look forward to hearing from you on how this key was generated / where it came from.
ravi.kumar
Member
Offline
Registered: 2016-09-10
Posts: 18
Thank you for your response. Finally I resolved the issue. Actually issue was with certificate. Whatever certificate we got from our customer is having private key in PKCS#8 format which has different ASN parsing code. If you see the input dump to RsaPrivateKeyDecode() function it is matching with the PKCS#8 ASN.1 parsing and it requires header and footer as "----BEGIN PRIVATE KEY---" and "---END PRIVATE KEY---" respectively. But customer is loading the private key as PKCS#1 format which has header and footer "---BEGIN RSA PRIVATE KEY---" and "---END RSA PRIVATE KEY----" respectively because of that Cyassl was throwing ASN parse error. If we just change the header and footer of private key to the PKCS#8 format. it started working.
FYI:
1. PKCS#8 has following ASN.1 parsing (see the RFC 5208).
PrivateKeyInfo ::= SEQUENCE {
version Version,
privateKeyAlgorithm AlgorithmIdentifier PrivateKeyAlgorithms,
privateKey PrivateKey,
attributes [0] Attributes OPTIONAL }
(v1,...)
PrivateKey ::= OCTET STRING
2. PKCS#1 has following ASN.1 parsing
RSAPrivateKey ::= SEQUENCE
{
version Version,
modulus INTEGER, -- n
publicExponent INTEGER, -- e
privateExponent INTEGER, -- d
prime1 INTEGER, -- p
prime2 INTEGER, -- q
exponent1 INTEGER, -- d mod (p-1)
exponent2 INTEGER, -- d mod (q-1)
coefficient INTEGER, -- (inverse of q) mod p
otherPrimeInfos OtherPrimeInfos OPTIONAL
}
Private key input was going as PKCS#8 format.
e.g.
0x30, 0x82, 0x4, 0xbe
0x2, 0x1, 0x0
0x30, 0xd, 0x6, 0x9, 0x2a, 0x86, 0x48, 0x86, 0xf7, 0xd, 0x1, 0x1, 0x1, 0x5, 0x0 (failed at this point as PKCS#8 is expecting 0x2 INTEGER)
0x4, 0x82, 0x4, 0xa8, 0x30 ...
You must login or register to post a reply
Jump to forum:
Announcements
General Inquiries
wolfSSL (formerly CyaSSL)
wolfCrypt
wolfMQTT
wolfSSH
wolfTPM
wolfBoot
cURL
yaSSL (Deprecated) [READ ONLY]
Ferro Network Mature Porno Movies
Femdom Foot Fist
Porno Dog Cook Long
Long Feet Hels Porno
Hairy Creampie Porno Tube
[SOLVED] Unable to load RSA private key (Page 1) — wolfSSL ...
linux - Can't get private key with openssl (no start line ...
windows - "Couldn't load private key (not a private key ...
Unable to use this private key file, Couldn’t load private ...
New Install unable to load Private Key | Netgate Forum
PostgreSQL failed to start. unable to load private key ...
engine_pkcs11-0.4.0-2.fc24 can't read private key from ...
Convert a certificate to PFX (GoDaddy, unable to load ...
[Solved] Permission denied (publickey) SSH Error in Linux
Unable To Load Private Key For Operation