"Leaked and Unprotected: What the Exposure of a Critical US Defense Document Means for National Security" DEFENSE INFORMATION SYSTEMS NETWORK (DISN) Document leaked
World News
In today's digital landscape, the security of military and government infrastructure is more critical than ever. The Defense Information Systems Network (DISN) serves as the backbone of the Department of Defense’s global communications, supporting essential operations and safeguarding national security. Detailed documentation related to DISN—including connection approvals, security protocols, and network configurations—is classified as highly sensitive. Unauthorized disclosure of this information could lead to catastrophic consequences, both operational and financial.
The Sensitivity of Defense Network Documentation Leaked documented can be located here on DISA as the file is mistakenly shared > disn_cpg.pdf
SEE PICTURE BELOW SHOWING THAT THE SIGNER SIGNATURE COULD NOT BE VERIFIED:
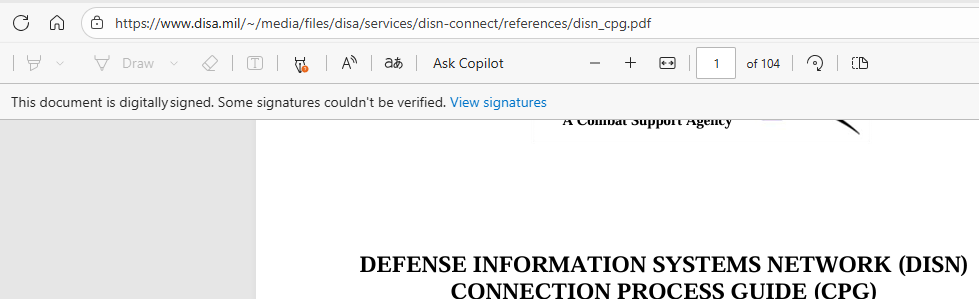
SEE BELOW PICTURE SHOWING A DIRECTORY BACK COULD NOT BE ACCESSED BUT THE FILE TO THE SENSITIVE DISN COULD BE ACCESSED:
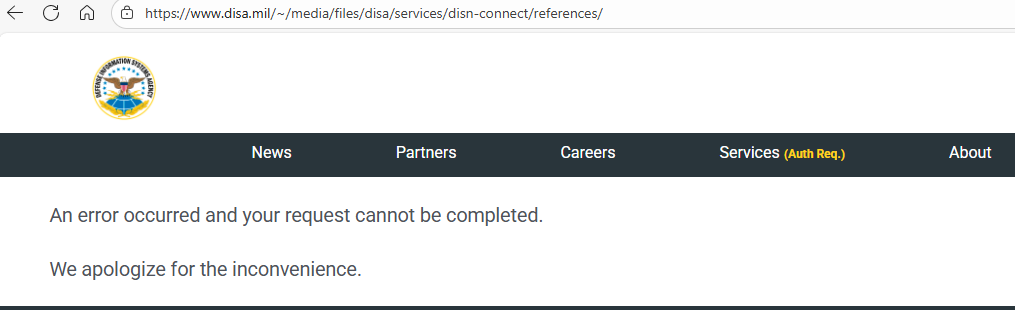
Our researchers asked ChatGPT if this document is considered sensitive see below reply
AI RESPONSE:
This document is highly sensitive because it contains detailed information about the DISN (Defense Information Systems Network) connection approval processes, configuration requirements, security protocols, network architecture diagrams, and procedures related to cybersecurity assessments, risk management, and accreditation. It includes specific contact information, technical standards, and process workflows that, if disclosed publicly, could compromise the security and integrity of the Department of Defense's critical communications infrastructure.
Final conclusion: The document is classified as highly sensitive and should not be exposed to the public. Its distribution should be restricted to authorized personnel with a need to know, and it must be handled in accordance with appropriate security protocols to prevent any potential security risks.
The Sensitivity of Defense Network Documentation Leaked documented that is Unclassified but Sensitive and show not be disclosed to public can be located here on DISA as the file is mistakenly shared > Cloud Connection Process Guide Version 2 January 2017
AI RESPONSE: The document you've provided appears to be a comprehensive procedural guide for connecting cloud services and information technology projects within the Department of Defense (DoD). While it contains detailed process descriptions, contact points, and technical standards, it does not seem to include specific classified information such as detailed network configurations, security credentials, or operational plans.
However, it does reference sensitive areas such as:
Security assessment procedures and requirements (e.g., FedRAMP+),
Specific security standards and control frameworks,
Contact points for cybersecurity teams,
Protocols for approval, authorization, and connection management,
Mention of classified impact levels (including Impact Level 6, which relates to classified information).
Assessment:
Unclassified but Sensitive: The document is primarily unclassified but contains sensitive information regarding security processes, standards, and procedures that, if misused, could compromise security if disclosed to adversaries. It is a controlled document meant for authorized personnel in the DoD and its contractors.
Classified Content: It does include references to classified impact levels (Level 6), but the content itself does not reveal classified information. Appendix H discusses procedures for handling classified Level 6 (SECRET) data, indicating that any actual classified data or specific handling instructions are outside the scope of this particular document.
Conclusion:
This document is sensitive and should be handled in accordance with DoD security protocols. It is not classified at the top secret level but is not intended for public dissemination. It should be stored, transmitted, and accessed only by authorized personnel within the DoD or approved contractors. Unauthorized disclosure could potentially aid adversaries in understanding DoD cloud connection procedures, security standards, and points of contact, which could be exploited.
Recommendation:
Keep this document in a secure environment.
Limit distribution to authorized individuals.
Follow your organization’s classification guidance and handling procedures.
=============================================
Technical details about DISN are carefully guarded. They include comprehensive procedures, network architecture diagrams, contact information, and security standards. While these documents are vital for authorized personnel to maintain the network’s integrity, their exposure to malicious actors can be disastrous.
Estimated Damages from a Data Leak
1. National Security Threats
Leaked information could enable adversaries to launch targeted cyberattacks, potentially compromising classified military operations. The resulting damage could threaten national security and operational effectiveness.
2. Financial Impact—Potential in the Hundreds of Billions
The financial repercussions of such a leak are staggering. Experts estimate that the cost of cyberattacks exploiting sensitive defense infrastructure could reach $100 billion or more. This includes:
Operational Disruptions: Interruptions in military communications could delay or sabotage critical missions.
Cybersecurity Response and Recovery: Costly incident response efforts, investigations, and system overhauls.
Intellectual Property Loss: Theft of sensitive technology and strategic information, diminishing technological advantages.
Legal and Diplomatic Penalties: Fines, lawsuits, and diplomatic fallout could further inflate costs.
Economic Disruptions: Broader impacts on national and global markets due to compromised military capabilities.
3. Erosion of Trust and Credibility
A breach undermines confidence among allies, partners, and the American public, potentially leading to diplomatic isolation and loss of strategic influence.
4. Long-Term Strategic Vulnerabilities
Adversaries could use leaked information to develop advanced cyber weapons or physical attacks, increasing the risk of future conflicts and escalating costs.
Prevention is Paramount
Protecting such sensitive information demands rigorous access controls, continuous security audits, and a culture of vigilance among personnel. Proactive measures help prevent leaks and safeguard national interests.
In summary, the leak of detailed defense network documentation could result in damages exceeding $100 billion, considering the broad scope of operational, financial, and strategic impacts. The potential costs underscore the importance of unwavering commitment to cybersecurity and information protection within defense circles.
Leaking sensitive or even unclassified but sensitive defense documentation like the DISN (Defense Information Systems Network) network details can have severe and far-reaching consequences, both operationally and strategically. Here are some key risks and potential impacts:
1. National Security Threats
Operational Compromise: Adversaries could use leaked information to identify vulnerabilities, plan cyberattacks, or even disrupt military communications.
Intelligence Exposure: Details about security protocols or network architecture could reveal defensive measures and intelligence strategies.
Targeted Attacks: Knowledge of specific contact points, procedures, or network configurations could enable tailored cyber operations against military infrastructure.
2. Financial and Operational Disruption
Cyberattack Costs: Exploitation of leaked data could lead to costly cyber incidents, with estimates reaching hundreds of billions of dollars in recovery, damages, and operational delays.
Mission Delays: Disruption of critical communications can delay or sabotage military or national security operations.
Recovery Expenses: Incident response, forensic investigations, and system repairs can be exorbitant.
3. Loss of Trust and Alliances
Diplomatic Fallout: Leaks undermine confidence among allies, partners, and the public, potentially causing diplomatic rifts.
Strategic Disadvantage: Competitors or adversaries may gain insights into U.S. defense capabilities, diminishing strategic advantages.
4. Erosion of Technological Edge
Intellectual Property Theft: Sensitive proprietary technologies and security standards could be stolen, affecting technological superiority.
Development of Countermeasures: Adversaries may develop advanced cyber weapons or physical attacks based on leaked details.
5. Legal and Diplomatic Consequences
Legal Penalties: Unauthorized disclosures can lead to legal actions against personnel or contractors involved.
Diplomatic Strain: Leaks may trigger investigations and diplomatic responses, complicating international relations.
6. Long-Term Strategic Vulnerabilities
Future Attacks: Leaked information could be used to develop future cyber or physical attacks.
Escalation of Conflicts: Knowledge of vulnerabilities might embolden adversaries, increasing the risk of escalation.
Estimated Damages
The potential costs of such a leak are staggering, with estimates exceeding $100 billion when factoring:
Disruption of military operations
Cybersecurity incident recovery
Loss of intellectual property
Diplomatic and legal repercussions
Broader economic impacts on national security and global markets
Conclusion & Recommendations
The leak of defense network details—even if unclassified but sensitive—poses a grave threat to national security, financial stability, and international relations. To mitigate these risks:
Strict access controls and encryption should be enforced.
Personnel handling such information must follow rigorous security protocols.
Continuous monitoring and auditing are essential.
Any suspected leak should be swiftly investigated and contained.