Tracking Down Funds in Operation DK [First Transaction Set]
Zerononcense / ProofofResearchPreface:
‘Operation DK’ name given as a pseudonymous identity of the individual that contacted me on Twitter at approximately 13:00 EST ; May 18th, 2019 requesting the tracking of allegedly stolen/hacked funds.
Transactions in Question:
- https://www.blockchain.com/btc/tx/c858f268d7e6a78e4884a7bb719307767a82f9560c0c6e8f7b49e4bb2b1c5780
- https://www.blockchain.com/btc/tx/279c41ebbc52423f5534122978126bfe44ab82f2f01aee7fbc02213c50464240
Reviewing the First Transaction
The following addresses are related to the first transaction (victim):
- 3FcMSKLBEmAbrEQiyaMJi2degEjc2u1VP6
- 33kCc7cKMdm6VQsNcboUjV7Yq6P9LnNeEH
- 3Kdicut9TR3tVWDfZCNAqWM3JiNGutUXLa
- 34wgYFFeyVbjGzjRoRMydMSpfzRPeBtzRw
- 3AgnKUyVhtz4k7MB4L6q3RPFmh36QmFqmF
- 3NcTwMWWNkYw8Xd6H16pBmkqb9cWNtEZiw
- 329ag7SEzVC5vysdmoKsxvD7d3XAGVXxwL
- 389bAh5YXvQBjN9TFbYQfYTrjs83fuqEfZ
- 31hDJJ43N7BrBc59BhpLnL7YG2xwEwC9b7
- 3KCL7pF4jyrMPBwy7Adv7oNofcPBQkLgpm
- 37Tcwid9QDyz8eahq9QRPNTNBP8xuo45sG
- 33cym8zAKKnyTSJq4H2TQkXFreMDKQsShA
- 3MDuTe1ZmFcTKnFe273GTbBwr1KwZHkEYP
- 3E2bEvCbbtP3gNkJHdSqSwJhMiWbTkG5bA
These addresses are all inputs that sent funds to the hacker, which is: 1KcnVpU4ajCpp1dBK7VhRTZvEdu5QEBVdq
The transaction ID = c858f268d7e6a78e4884a7bb719307767a82f9560c0c6e8f7b49e4bb2b1c5780
The address where the hacked funds went to has been active since March 13, 2019.
Notably, victim was hacked on May 17th, 2019.
In addition, funds were received from 3JjPf13Rd8g6WAyvg8yiPnrsdjJt1NP4FC , which is strongly attached to illicit activity on behalf of HitBTC.
The funds were sent from the illicit address to the address that received the hacked funds in 6 separate transactions.
Below are the transaction IDs:
- 6ba85c11f7e3b6900fcfad85ef2cac2174c623b9c29749e232a1003bc6551007
- 43fd4fc503567d1ee2c57031da2b12fc7cf8e52388f5c3d678f964a8ea547ee8
- c68024e551b3a6ea77ed037d39bf7ae5438d0da91fc7320119b890b839ff2d3e
- 2b91d168c3f324eca9dfb16cad9f4634b4b77e9a67606802f378f20d06aa4e96
- 18abeec7f7f3ac29ffe552c3fb9127527c7880951902e7fdef6c124b48a08620
- 5081cbf50841fa81c985fe790212f97615a936c3f76bf0d484de3b2f2d6bdaa1
For reference, this article here should be viewed: https://bitcoinexchangeguide.com/hitbtc-appears-insolvent-blockchain-analysis/
Looking at the Visualization for Crystal Blockchain
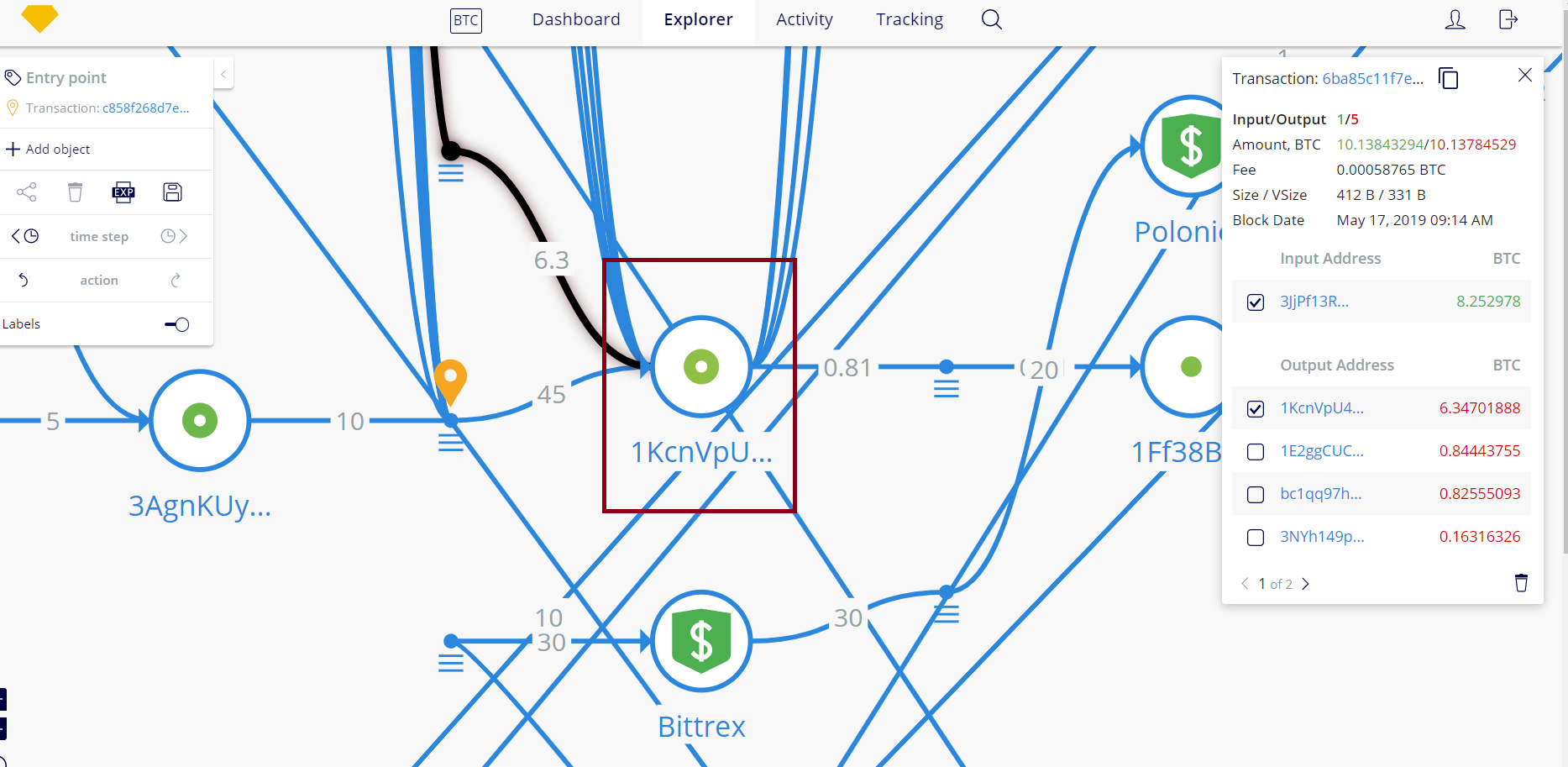
Above is the address that received the hacked funds from victim. The web of connections is somewhat complex, so this visualization will be tailored in a manner that helps whatever interested parties view the passage of funds in an easier manner.
The two addresses in the picture above received funds directly from the hacker’s address.
Specifically, these addresses are:
Both addresses have been hyperlinked with the transaction ID that shows this transfer of funds.
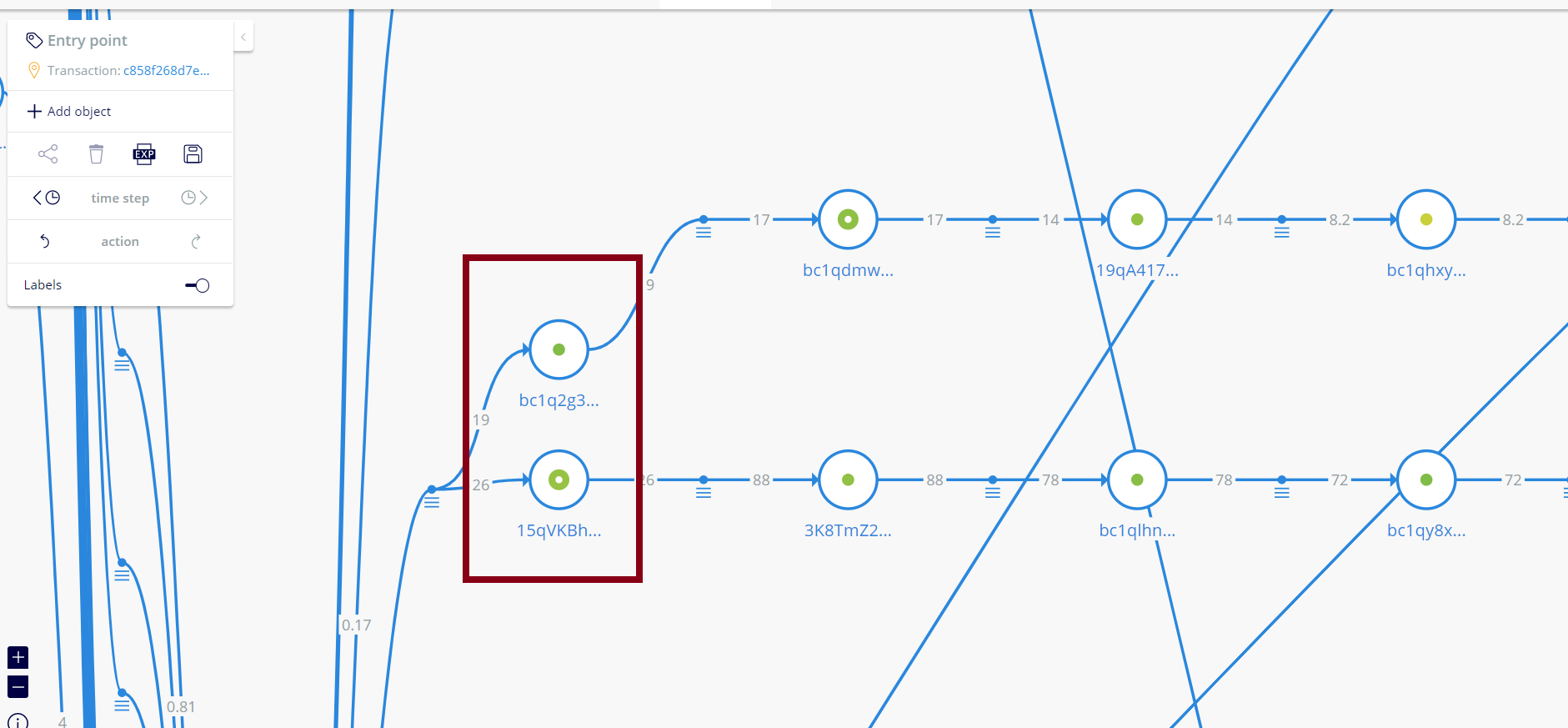
If we pan back the image (zoom out) slightly, we can see some of the funds leading directly to a Binance deposit address (belongs to some customer at Binance).
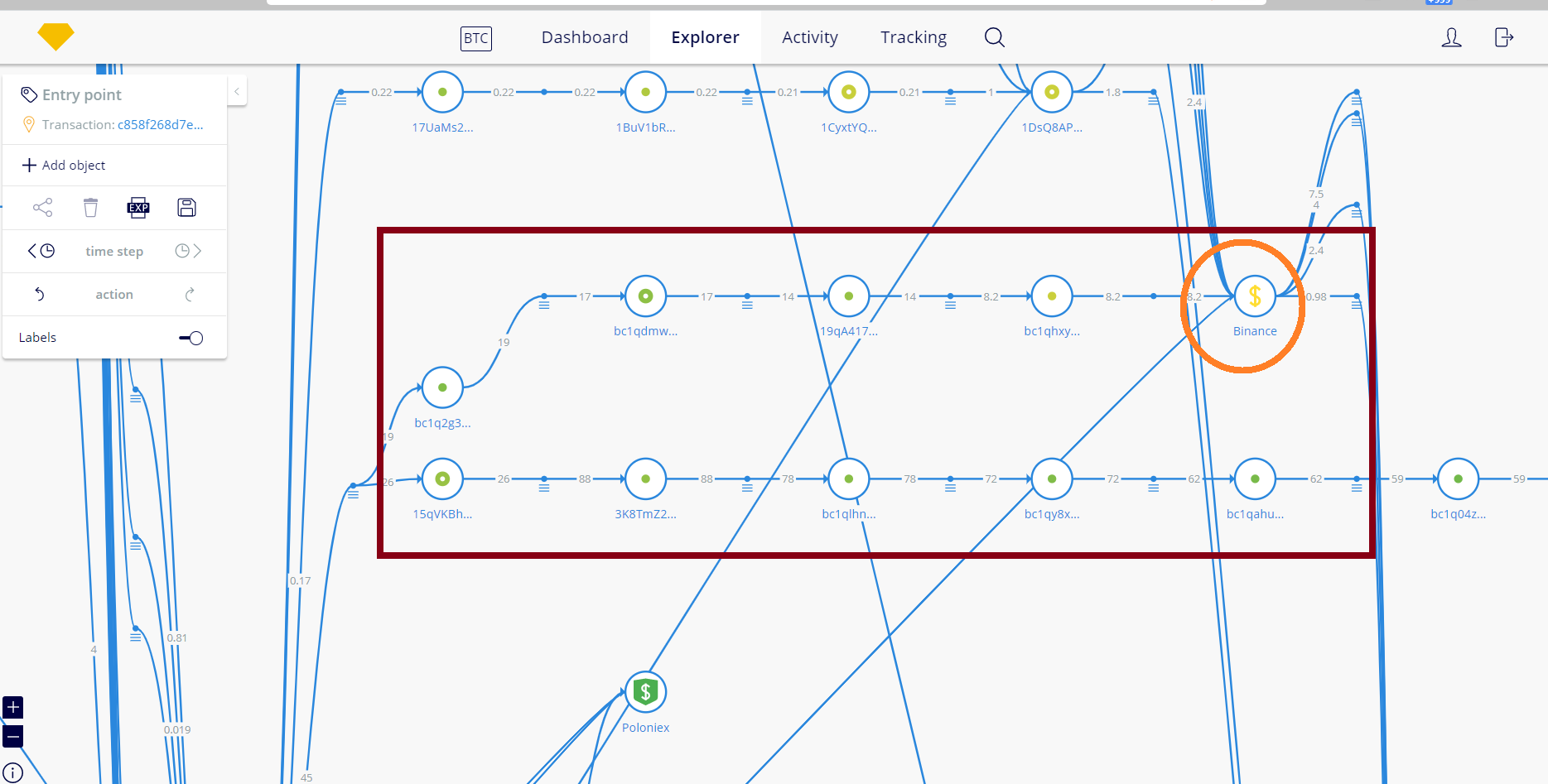
The Binance deposit address in question that has received these funds is: 1LncA9soMJaxkCNDehGN7abGXorcLW3e6H
Specifically, this address received its funds from bc1q2g3tfxu6lq453kyqyeenj3dh4qteha99f4kj3c
The other address sent a string of funds that leads to 1CNfUWjmDQBYK3xw9Mqg3dQj7uf9SfgiSJ , where 18.20136927 bitcoins are parked at the time of writing. These funds are not at an exchange.
Since the funds are commingled with funds from other sources (that may or may not be illicit), it is nearly impossible to tell which funds are explicitly tied to this hack and which ones come from other sources.
One thing that can be said though is that all of the funds commingled with this address and the others that have been identified in connection with the hacked funds, specifically, should all be considered tainted.
Other Addresses Funds Are Parked At
- 1Cpf8CCwYRwXbjH4V8x6bhGR7NQ2VZNYez ; 12.77225288 bitcoins
- 1AwqZ1LyUTRDJc3fxjVXh14ATVnAaqYcbb ; 20.79284085 bitcoins
- 18dppbiRVeCh8oXnNVBvPYx7B9dQsdMX3s ; 20.30903456 bitcoins
- 1Le5BbPTakNW5eFKGMhbn4X3Z6XDy4jX9B ; 1.55076306 bitcoins
- 3ApPvGS1Bsk4f879teGVABxPP7LF3WpXqc ; 4 bitcoins
If one were to view the transaction history of the addresses listed above, it would be immediately apparent that there are funds coming from multiple different addresses.
Second Binance Address That Received Funds
Below is a visualization of another Binance deposit address that received funds:
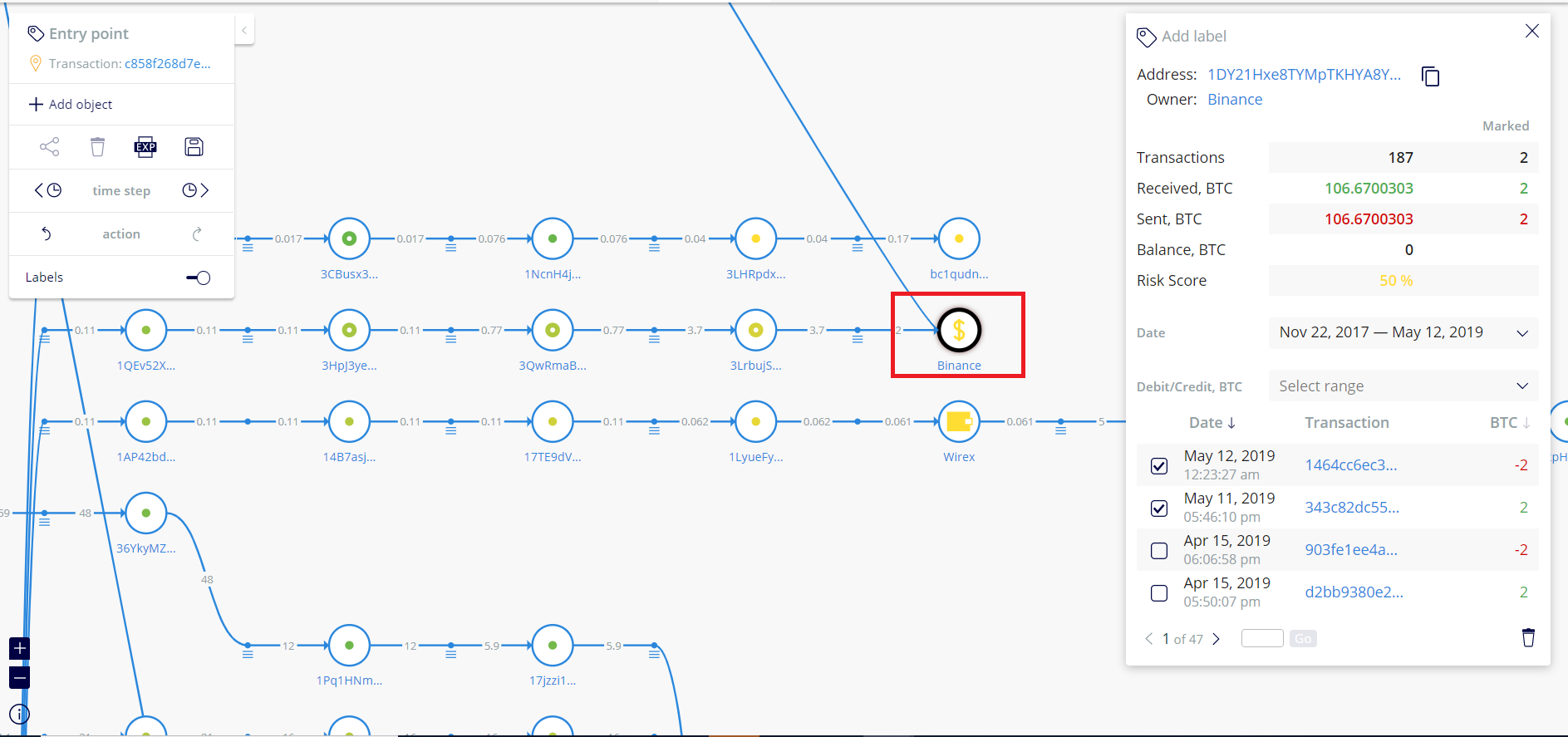
Again, in this instance, this address did not receive 100% of the funds that were extracted from the victim. Some of the funds from the victim were diverted elsewhere and some of the funds that did end up in that Binance deposit address also stem from other sources.
The Binance Deposit Address in question in the picture above = 1DY21Hxe8TYMpTKHYA8YpZDSCnJchcXGdy
In specific, only 0.1356124 bitcoins from the address that received the hacked funds were sent to the Binance deposit address shown above.
Here is the link to the transaction ID that shows this passage of funds: https://www.blockchain.com/btc/tx/0af88fb5c99df1e737e7b7611a620530c402ef5237c5db41bfd9f7fd3384def4
Another path with a negligible amount of bitcoins leads to ‘Wirex’ as well.
Here is the transaction ID that shows this passage of funds: https://www.blockchain.com/btc/tx/02961a68cc92226966bc70e67be066166114ceaeb89b86bc50bb1b6f091f4089
Conclusion
Funds mainly went to the first Binance deposit address mentioned in this report, which is: 1LncA9soMJaxkCNDehGN7abGXorcLW3e6H
Specifically, 19.12544137 bitcoins from that wallet belong to the victim of this hack.
TX ID: https://www.blockchain.com/btc/tx/b8b02851613e473e3ccc16c29588907b6d8220a66b42fa65c8806357471f225e
The vast majority of the other bitcoins have not yet ended up at an exchange thus far (from what can be seen). So far, they are parked at a # of addresses as well as commingled with additional funds from other outside sources.
Those wallets should be monitored consistently with alerts if the appropriate software is on hand to do so.
Addendum (Path of Extracted Funds)
The path of the client's funds are as follows (to the Binance address):
- 44.72658966 bitcoins are extracted from legitimate victim's wallets (listed at the top of this document) and sent to 1KcnVpU4ajCpp1dBK7VhRTZvEdu5QEBVdq in transaction ID: c858f268d7e6a78e4884a7bb719307767a82f9560c0c6e8f7b49e4bb2b1c5780
- After these are siphoned from the client, an equivalent amount are sent to two wallet addresses. Those addresses are 15qVKBhGsdR5kuR66hsoij9DygjAdi2kfk and bc1q2g3tfxu6lq453kyqyeenj3dh4qteha99f4kj3c. Here is the transaction ID: b8b02851613e473e3ccc16c29588907b6d8220a66b42fa65c8806357471f225e.
Below is a visual from 'blockchain.com':

We can validate that these are the victim's funds by clicking on the specific 'output' of the 44.72412802 bitcoins that are transferred.

That takes us to the initial transaction where the victim's wallets (possession proven by victim) were siphoned into the hacker's address (1KcnVpU4ajCpp1dBK7VhRTZvEdu5QEBVdq).

As mentioned above, this report has now established that the 44.72658966 bitcoins have indeed traveled from the hacker's first address to two addresses which are:
- 15qVKBhGsdR5kuR66hsoij9DygjAdi2kfk
- bc1q2g3tfxu6lq453kyqyeenj3dh4qteha99f4kj3c
Specifically, this report will follow the trail of funds stemming from bc1q2g3tfxu6lq453kyqyeenj3dh4qteha99f4kj3c to the Binance address that was listed above.
As listed above, 19.12544137 bitcoins were sent to this address in total. All of these bitcoins stem from the victim's original funds.
- Once these 19.12544137 bitcoins reach bc1q2g3tfxu6lq453kyqyeenj3dh4qteha99f4kj3c , they are then sent 1Cdc2dn3fJ9nzU1VnpJ9BrDBG39uq4bx41 and bc1qdmwwgmyx6h7qmyv2dd40ccum0nm8ju3d3m9q73. The former address receives 1.64943466 bitcoins and the latter address receives 17.47575831 bitcoins.
- These funds are transferred in transaction ID e93ec7e4039b9876b64b3464cd30e55b05a03212258aca989c4c647b8fcbdcb5.
- The address that receives the 17.47575831 bitcoins is the one that continues the chain of transactions directly to the Binance address that was listed above.
From the address that receives the 17.47575831 bitcoins, funds are then sent to another two addresses, which are:
- 19qA417hkU3BisV1f45NHGqCmDkyp55b6t (13.78002668)
- bc1ql0zej2acuhljxezl62903qm8xht7e8x4nvj3c6 (7.66472378)
In addition, 3.96985936 bitcoins were added to the transaction to these two addresses from the hacker's original address. In total, 21.44561767 bitcoins were sent in this transaction.
The transaction ID = 7e985e47f2fdde818b85a8ce991ed30bf83c76e4678f1d7b622f2d972f31fd1e
*Note: The author does not possess software that will allow for the parsing of each individual satoshi that reached one of these wallet addresses. Therefore, there is no way to specifically parse between which of the funds specifically and particularly belong to the victim and which derived from the original hack address (1KcnVpU4ajCpp1dBK7VhRTZvEdu5QEBVdq).
However, with the above note in mind, it reasonable to assert that 19qA417hkU3BisV1f45NHGqCmDkyp55b6t, which has received 13.78002668 bitcoins should be considered to have 13.78002668/17.47575831 bitcoins that belonged to the victim in the transaction.
The lowest amount of the victim's funds that the aforementioned address could have received in this transaction would be 9.81016732 bitcoins (if we take the total amount of bitcoins (13.78002668) received in this address and subtract the amount of bitcoins that derive from the original hack address [3.96985936 bitcoins]).
Sticking with the 19qA417hkU3BisV1f45NHGqCmDkyp55b6t address, we can see that 13.78002668 bitcoins leave it in a subsequent transaction. These bitcoins travel to two addresses, which are:
- bc1qhxy6cu3xe72fl08f0musfyuk3nz40tmm7jqda6 (received 8.16118224 bitcoins)
- 1J9aan3B4TUcbXEfJvVKEy78gN6tTx3L7v (received 5.61832101 bitcoins)
Again, it is reasonable to assume that all bitcoins that were involved in this tranasction (02119a8d96cedf18728f2f6fbf7eff30b15b1236c277a64bab6a4c255a5fa684) belong to the victim in this scenario.
From this point, if we track the bc1qhxy6cu3xe72fl08f0musfyuk3nz40tmm7jqda6 address, we can see that the funds are sent directly to a Binance deposit address.
The Binance deposit address = 1LncA9soMJaxkCNDehGN7abGXorcLW3e6H
Below is a visualization of the path:

In addition, here is a video that shows the complete path of funds leading to the Binance wallet as well as the Bitstamp wallet. The starting point is the hacker's address where they first extracted funds that belong to the victim.
The URL = https://streamable.com/tyrdw
The Bistamp address shown in the video = 36uwFSav1wadZMf7nWzg9SJg8RLFtUzmob
Opinion of the Researcher
It is undeniable that at least some of the funds were sent by the hacker ended up in the Binance address. However, the pertinent issue at hand in terms of asset recovery will be deliberating on how much of these funds the client is entitled to.
In the opinion of the researcher, the client should be entitled to all 44.72658966 bitcoins for the following reasons:
- Fungibility - Bitcoin, by nature, is fungible. In other words, there is no demonstrable difference that can be determined from one Bitcoin to another. Essentially, a bitcoin is no different than a $20 bill. There are countless $20 bills in circulation and, physically, they are all distinct and separate. However, each $20 bill is treated as one in the same. There is no difference between the $20 bill that John possesses and the one that Olivia possesses. The same is true of Bitcoin.
- All Funds in the Binance Address Belong to One Entity - The nature of exchanges dictates that each user that registers on an exchange be granted specific "deposit addresses" contingent on the cryptocurrency that they are depositing. For example, if one were to create an account at Binance and request to deposit 'Bitcoin' on the exchange to trade, they would be provided a "deposit address". This address would be unique to their account and their account alone. Thus, any and all funds that are sent to that account can be deduced to belong to the same owner. Therefore, since this report has conclusively demonstrated that the hacker has sent at least some of the Bitcoins that were extracted from the victim in their malicious hack, it must be deduced that the wallet/account in question belongs to the hacker.
- The Hacker Has Mixed and Commingled the Funds in a Number of Ways - Speaking to the fungibility aspect mentioned in point #1, it is also worth mentioning that the hacked funds have been commingled with a number of additional funds. In particular, some of these funds derive from the address 3JjPf13Rd8g6WAyvg8yiPnrsdjJt1NP4FC , which has been publicly reported as deriving its source of funding from a number of scams/frauds/hacks/other illicit and criminal activity in the blockchain space.
Given the points that have been made above, the most reasonable and prudent adjudication would be to grant the victim the full amount (44.72658966 bitcoins) that have been extracted from them in this theft if an amount in excess of this number has already been found and halted from being withdrawn from the exchange.
Credentials of Researcher
My name is James Edwards, and I have been cited in a number of publications this year alone for my investigative work in blockchain research.
Below is just a small sample of some of those references:
1. The Wall Street Journal (https://www.wsj.com/articles/a-crypto-mystery-is-140-million-stuck-or-missing-11549449001)
2. Vice News (https://news.vice.com/en_us/article/zma4w3/quadriga-crypto-gerald-cotten-canada)
3. CoinDesk (https://www.coindesk.com/crypto-exchange-bitfinex-denies-accusation-of-insolvency)
4. CoinTelegraph (https://www.wsj.com/articles/a-crypto-mystery-is-140-million-stuck-or-missing-11549449001)
5. Bitcoin Wiki (https://en.bitcoin.it/wiki/Privacy)
6. The Washington Post (https://www.washingtonpost.com/business/2019/02/04/cryptocurrency-company-owes-customers-million-it-cant-repay-because-owner-died-with-only-password/?utm_term=.89137bf01e75)
7. Engadget (https://www.engadget.com/2019/03/08/quadrigacx-bitcoin-missing-millions/)
8. Investing (.com) (https://m.investing.com/news/cryptocurrency-news/bitcoin-falls-report-finds-quadriga-stored-ethereum-on-other-exchanges-1796852)
9. Yahoo! Finance (https://finance.yahoo.com/news/bitcoin-falls-report-finds-quadrigacx-092000704.html)
10. FXStreet (https://www.fxstreet.com/cryptocurrencies/news/the-quadrigacx-story-takes-another-strange-twist-201902042301)
Among several others.
The author brings a wealth of investigative experience in thorough, deep diving research and asset recovery and has assisted in a number of local, state, federal and even international investigations throughout their tenure in the blockchain space.
If there are any questions for the author, please do not hesitate to reach out via e-mail at proofofresearch@protonmail.com
Thank you.