To the eyes on Blindspot--- CYBR
Nicolas Cavalcanti
What for CYBR Stands?
CYBR, desire great CTI itself, is an excellent two-fisted offensive that provides new safeguards, countermeasures, menace secures and intelligence orders via some unusual tactics. BlindSpot: A proprietary application plan that capacities perhaps borderless landscape designs of risk id. Identifying risk generally is one subject, having rid of it another and even now, another to stop its come back. Frequent matter alternatives can inform you something can get inaccurate but can’t eradicate the concern nor recognize the acceleration of hazards. They are obsolesced by current malware merely.
BlindSpot might see through the polymorphic camouflera group utilized by the world’s most advanced cyber-terrorist. Producing usage of digital file fingerprints and leveraging an adaptive real human brain, BlindSpot locates unfinished matches within the records on endpoints including systems, servers, laptops, desktops, USB pushes, and cellular devices even. BlindSpot is often also built to screen tourists nonetheless to pay through the network (available in a subsequent release).
In concept of Central Competencies, the stands of CYBR:
There are mainly due to many potential types of hacks mostly because there are hackers. Among the better introduced to will be straightforward world wide web defacement, flooding, brute produces challenges, SQL injection problems, and OS control. The wish for breach diagnosis usually is commensurate with the blog visitors and range of the network itself. Irrespective of size, chance, width, and sum, BlindSpot’s proprietary capacities blended with an authentic period data resources and bolstered by open public support (the wide open up beginning factor), helps ensure there is often no task beyond the company’s option. CYBR shall undertake to acquire referred to as the “guardians of the blockchain” and below is usually a level start of existing volumes.
Why important?
It is essential that an organization, crypto or perhaps several, ensures the gains of the organization to give come rear on the subject of decision (Go back over expense) for its investors and stakeholders. Likewise various “organizations” in the crypto space today will are lost because they will not conclude being suitable for developing a rewarding organization version. CYBR supplies existing, world-class close scarves in cyber safety and blockchain. The service provider presently continues over US$6 million in method instructions located for the Division of Homeland Reliability (DHS) DOMino program, a US$1.115 billion Indefinite Delivery Indefinite Sum (IDIQ) contract as a subcontract to Raytheon Firm.
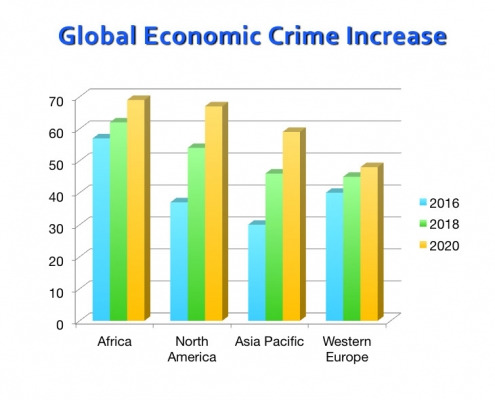
USE of CYBR in public or private industry:
All public government systems go through Certification and Accreditation. BlindSpot offers malicious code protection, for equally security considerations and necessary compliance. Recommendations present found in NIST 800-53 Revisions 3+ Safeguard Requirements for Course Ethics, SI-3 Harmful Code Protection, a condition that hazardous code safety mechanisms want to be implemented in details plan leave and gain access to concerns, integrating workstations, notebook computer system devices, and mobile phone gadgets, to identify and eradicate malicious code. BlindSpot’s constant monitoring and upgrading of its regarded detrimental report database offer the required current and frequent re-scans of records. It also notices suited staff members when a harmful code usually is usually found out, provides comments found in probable malicious info files, illicit activity, and provides follow-up with brief fraudulent great testimonials (less than 0.01 percent). BlindSpot assists companies to match the mandated proper protection requirements while producing particular moving forward conformity.
Federal government organizations and corporations are addressing the concern of monitoring records. Info documents that contain technique facts or perhaps wise, an average real estate may a good deal longer wrap up being safely zero kept after well-protected equipment with the need for gaining access to getting perfunctory qualifications. Persons either or with evil purpose repeat and paste parts of papers unwittingly, head out paperwork to USB causes, transfer papers onto a notebook computer, talk about them with co-employees, or infiltrate specific details to outside systems and devices. BlindSpot shooters devices carefully, and may keep an eye on USB works. BlindSpot can give out signal relating to questionable activity with specified files/info data, with individual computer systems or perhaps even person activity.
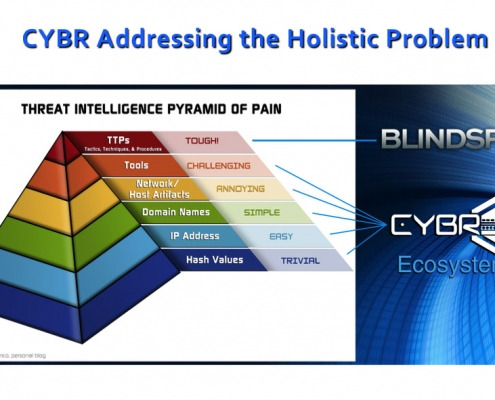
Software system of CYBR
It is a good technique facts watchdog that gets both malicious and unintentional press to non-secure devices. BlindSpot shall make an arranged of digital report fingerprints that can screen throughout devices and devices, building sure the proprietary and technique specifics for establishments, 365 instances of the appointments time, a good week eight days, a time 24 hours.
The software program continually screens file activities from an endpoint searching for digital fingerprints. Whenever it discovers imperfect fits of any report type, in any vocabulary, it is reported and kept in perpetuity on a temporal database back. The up to time info resource of continuously noted detrimental hacking and records tools finds and signal clients to virtually any sign of hacking, destructive documents, or illicit activity.
Every time details technologies systems come across risk, seeing that carry out smart agreement transactions and any blockchain task in a lifetime. Criminals function around the clock in work to infiltrate sites, get a bridal get together, consider control of procedures, and more and perpetuate of the petition of nefarious ulterior motives the mind can conjure. Many probably essentially, they look to take investment funds from exchanges and wallets.

Keys to viable security
The keys to a viable cyber security solution include four core components:
1. Holistic: features protection in totality.
2. Countermeasures and shields give serious cover.
3. Threat identification is timely.
4. The instant change over from data to actionable brains.
The Blindspot CYBR and software Internet site offers the technological capability to meet these requirements. The most significant subject can come to be CYBR cases to provide the security, and the Blindspot program course is often performing a superb job to maintain the promise.
Ultimately actually if, CYBR believes it can help the individual, especially in the blockchain space. Crypto wallets happen to come to be at risk, mobile or portable items exercising crypto applications will become fraught with threat as verified by a hottest US$224 million personal accident personal injury lawsuit against AT&Testosterone about the meant theft of some US$24 million via wireless equipment. As well, two-factor authentication wills little to decrease these dangers. The business is usually confident that placing itself mutually in the C2C industry will pave the approach for client adoption. On best of that, the venture is generally included with many global consortiums and knows the benefit of the reason of technique. CYBR will job to present protection for crypto enterprises and businesses through current alternatives and developing technology, furnished by an Internal Exploration and Progression (IR&Chemical substance) and Middle of Great top quality (CoE).
Website: https://cybrtoken.io/
Whitepaper: https://cybrtoken.io/wp-content/uploads/2018/09/cybr-whitepaper.pdf
Telegram official group: https://t.me/CYBRnetwork
In the line of great findings.....
B.T.T Username: Calvacantinico
Profile: https://bitcointalk.org/index.php?action=profile;u=2474061;sa=summary
MyEther Wallet: 0xE368A251AaF8eA366b78bA2f6f3b8A514B028f66