Tcp Hole Punching

💣 👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
TCP NAT traversal and TCP hole punching (sometimes NAT punch-through) occurs when two hosts behind a network address translation (NAT) are trying to connect to each other with outbound TCP connections. Such a scenario is particularly important in the case of peer-to-peer communications, such as Voice-over-IP (VoIP), file sharing, teleconferencing, chat systems and similar applications.
TCP hole punching is an experimentally used NAT traversal technique for establishing a TCP connection between two peers on the Internet behind NAT devices. NAT traversal is a general term for techniques that establish and maintain TCP/IP network and/or TCP connections traversing NAT gateways.
In the following, the terms host, client and peer are used almost interchangeably.
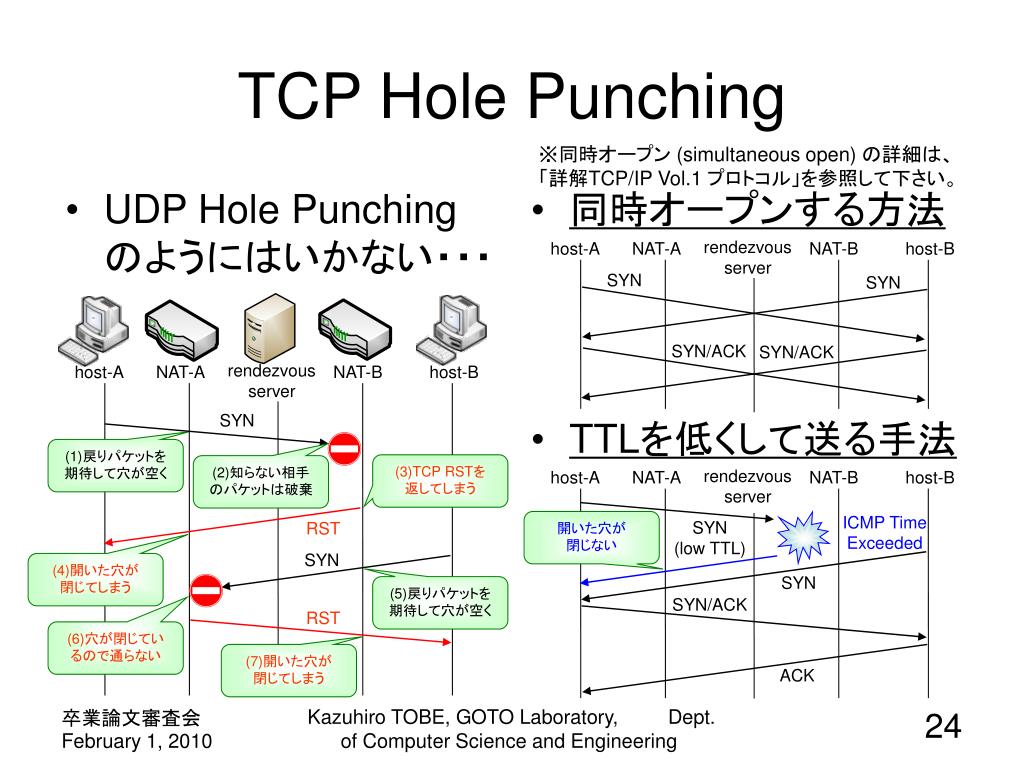
NAT traversal, through TCP hole punching, establishes bidirectional TCP connections between Internet hosts in private networks using NAT. It does not work with all types of NATs, as their behavior is not standardized. When two hosts are connecting to each other in TCP, both via outbound connections, they are in the "simultaneous TCP open" case of the TCP state machine diagram.[1]
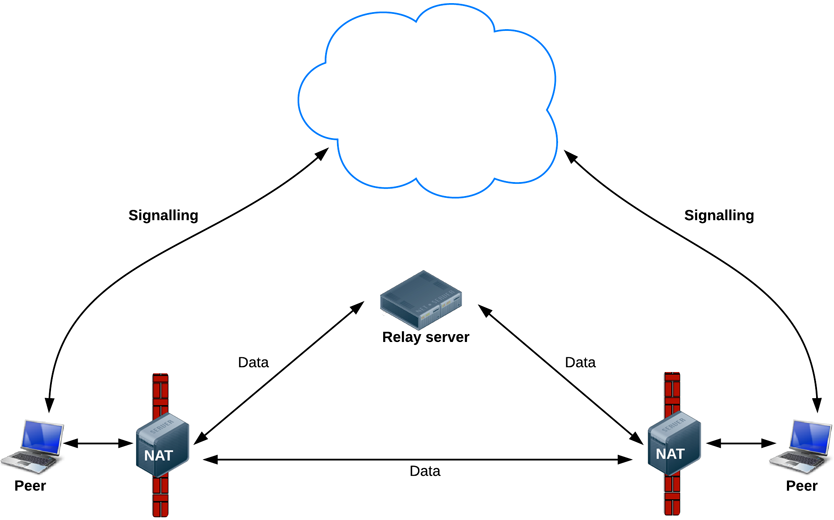
Peer A ←→ Gateway A (NAT-a) ← .. Network .. → Gateway B (NAT-b) ←→ Peer B
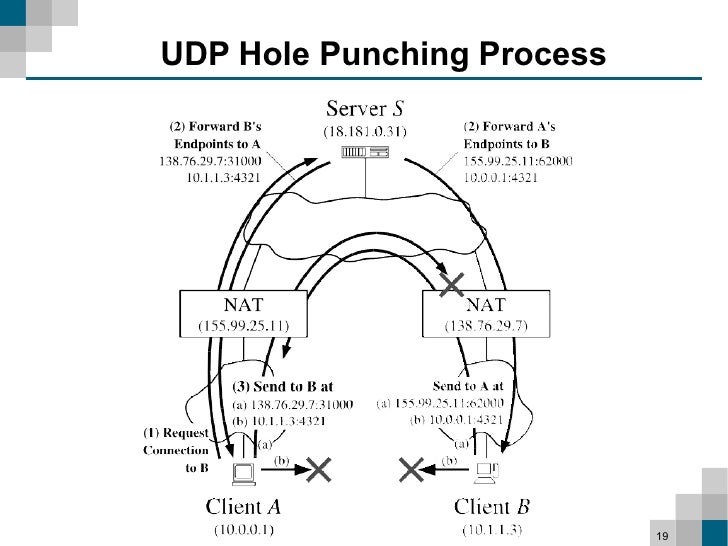
The availability of TCP hole punching depends on the type of computer port allocation used by the NAT. For two peers behind a NAT to connect to each other via TCP simultaneous open[clarify], they need to know a little bit about each other. One thing that they absolutely need to know is the "location" of the other peer, or the remote endpoint. The remote endpoint is the data of the IP address and a port that the peer will connect to. So when two peers, A and B, initiate TCP connections by binding to local ports Pa and Pb, respectively, they need to know the remote endpoint port as mapped by the NAT to make the connection. When both peers are behind a NAT, how to discover the public remote endpoint of the other peer is a problem called NAT port prediction. All TCP NAT traversal and hole punching techniques have to solve the port prediction problem.
A NAT port allocation can be one of the two:
Depending on whether the NATs exhibit a predictable or non-predictable behavior, it will be possible or not to perform the TCP connection via a TCP simultaneous open, as shown below by the connection matrix representing the different cases and their impact on end-to-end communication:
Here are some of the methods used by NATs to allow peers to perform port prediction:
If the remote peer has the information of one mapping, then it can guess the value of subsequent mappings. The TCP connection will happen in two steps, at first the peers make a connection to a third party and learn their mapping. For the second step, both peers can then guess what the NAT port mapping will be for all subsequent connections, which solves port prediction. This method requires making at least two consecutive connections for each peer and requires the use of a third party. This method does not work properly in case of Carrier-grade NAT with a lot of subscribers behind each IP addresses, as only a limited number of ports are available and allocating consecutive ports to the same internal host may be impractical or impossible.
In this case, port prediction is trivial, and the peers simply have to exchange the port to which they are bound through another communication channel (such as UDP, or DHT) before making the outbound connections of the TCP simultaneous open. This method requires only one connection per peer and does not require a third party to perform port prediction.
With this solution, the peers will first connect to a third party server that will save their port mapping value and give to both peers the port mapping value of the other peer. In a second step, both peers will reuse the same local endpoint to perform a TCP simultaneous open with each other. This unfortunately requires the use of the SO_REUSEADDR on the TCP sockets, and such use violates the TCP standard and can lead to data corruption. It should only be used if the application can protect itself against such data corruption.
We assume here that port prediction has already taken place through one of the methods outlined above, and that each peer knows the remote peer endpoint. Both peers make a POSIX connect call to the other peer endpoint. TCP simultaneous open will happen as follows:
For the TCP simultaneous open to work, the NAT should:
This is enough to guarantee that NATs behave nicely with respect to the TCP simultaneous open.
The technique described above works fine within a CGN. A CGN can also make use of a port overloading behavior, which means that distinct internal endpoints with the same port value can be mapped to the same public endpoint. This does not break the uniqueness of the {protocol, public address, public port, remote address, remote port} quintuple and, as a result, is acceptable. TCP port preservation can also lead to cases where the CGN ports are overloaded and is not an issue for protocol soundness. Port overloading for TCP allows the CGN to fit more hosts internally while preserving TCP end-to-end communication guarantees.
^ Information Sciences Institute (September 1981). "Transmission control protocol: DARPA internet program protocol specification". IETF. Defense Advanced Research Projects Agency.
Content is available under CC BY-SA 3.0 unless otherwise noted.
Sign up or log in to view your list.
Question is below. Here is my current test code which did not succeed.
How do I do TCP hole punching? I am testing using a remote server. I'm running wget local_public_ip:port/test. I have my router setup for port 80 so it doesn't need a hole punch. My code got a connection. Now I try on other ports and I can't exactly figure out how to punch the hole.
I thought maybe I need to setup the local endpoint on the out tcp connection.
I made a mistake and got this exception
Fixing up the byte array to 192,168,1,5 it appears to make outgoing connects correctly. Now that I have a out connection to the remote IP using my listening port I thought wget would be able to connect to me. It wasn't the case
Did you set up the local port of o to be the 8090? You talk about it but the code doesn't match. Please update the code.; Remove all undefined variables such as bytearray and port.; wget needs to connect from port 123. Did you make it do that? If not use a different client. – usr Nov 10 '14 at 16:26
@usr: I wrote wget http://mylocalip:8090/test The TcpClient o is to make a dummy outgoing connection. port is = 8090. I thought if the local port of the outgoing connection is the local port i'm listening on then maybe when the remote connection tries to connect using the same port the router will let it through. Maybe it does work but not on my router. BUT there are software that successfully punch a hole in my router. – user34537 Nov 10 '14 at 21:36
@usr: After some fiddling I notice the code in my question works. I just need to choose the linux port carefully. It appears not to work if I block incoming connections on my linux box (to simulate router blocking a connection) I used this iptable rule gist.github.com/anonymous/514cdd23f749ca5d2385 So now I'm wondering if I need to be able to connect to the remote party before I can hole punch. Which defeats the point really since this problem assumes two parties can't communicate and a 3rd part is used to help punch the hole. Maybe I can ask a friend to run the code later – user34537 Nov 11 '14 at 12:15
@usr: That link is long. I'll try to read it before the bounty is up. Also I forgot to mention if I don't block the connection but forget to send a connection it doesn't work (which makes sense). My gut suggest maybe the REJECT and DROP in iptables sends some kind of signal which ruins the hole punch – user34537 Nov 11 '14 at 12:16
@usr If you want a simple test program which can listen to a port, socat is handy, and has a windows port... It's like telnet or netcat, but with more interesting options... – Stobor Nov 12 '14 at 2:11
I'd use the "sequential hole punching technique" detailed in http://www.bford.info/pub/net/p2pnat/index.html. It seems much simpler to do that simultaneous connections and socket reuse. It is not necessary for hole punching to do anything exactly simultaneously (that is a meaningless notion in distributed systems anyway).
I have implemented hole punching. My router seems not to like it. Wireshark shows the outbound hole punching SYN is correct but the remote party can't get through to me. I verifies all ports with TcpView.exe and disabled all firewalls. Must be a router issue. (It is a strange and invasive router.)
You can try both values for useParallelAlgorithm. Both should work.
This code is for the server. It punches a hole into the local NAT. You can then connect from the remote side using any client that allows to pick the local port. I used curl.exe. Apparently, telnet on Windows does not support binding to a port. wget apparently neither.
Verify that the ports are correct on both sides using TcpView or Process Explorer. You can use Wireshark to verify packets. Set a filter like tcp.port = 1234.
When you "call out" to punch a hole you enable the tuple (your-ip, your-port, remote-ip, remote-port) to communicate. This means that all further communication must use those values. All sockets (inbound or outbound) must use these exact port numbers. In case you aren't aware: outgoing connections can control the local port as well. This is just uncommon.
usr
usr 163k●3333 gold badges●225225 silver badges●348348 bronze badges
Ivan G.
540●77 silver badges●1515 bronze badges
This appears to work. I tested it using useParallelAlgorithm=false. I waited for the hole to be punched before running it on my remote server. It works. It appears to punch a hole through iptables as well – user34537 Nov 12 '14 at 21:29
@acidzombie24 great, good to know! Finally, there is clean hole punching code on the web. All code that I found was awful. – usr Nov 12 '14 at 21:56
Here is a clean hello world like hole punch you may like. It only uses TcpClient and TcpListener. No reuse address or raw sockets. Are you sure your router doesn't like/support the hole punch? if you have a remote linux box to test with I can hand you some IPTable rules to test the block – user34537 Nov 13 '14 at 2:11
I'm not 100% sure it's the router but I cannot think of any other explanation. I have a Windows server connected directly to the Internet. I used it to test this. – usr Nov 13 '14 at 12:30
@DiaaEddin it does not work for me either for unknown reasons but it did work for someone else. If you ever find the reason for it not working please comment. – usr Mar 4 '17 at 15:03
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Mature Hard Compilation
Cuckold Sms Vk
Ver Peliculas Online Nudist On The Beach
Rammstein Till The End Pornhub
Homemade Modern Com
TCP hole punching - Wikipedia
GitHub - jasonpang/tcp-holepunching: A TCP hole punc…
Пробивка отверстий TCP - TCP hole punching - Википедия
NAT Traversal (TCP/UDP Hole Punching) | Haven200
Socket And TCP Hole Punching - CodeProject
TCP simultaneous open for TCP Hole Punching
TCP hole punching не работает - Сети - Киберфорум
Tcp Hole Punching