Security incident report No. 1
TelePay Team
Our payments gateway has gone through a security incident today. Following our core transparency principle, we're posting a report with detailed information. All events described occurred during 2022-06-15.
11:58:07 UTC
At 11:58:07 UTC, the attacker joined the @TonXAdsBot, which we operate.
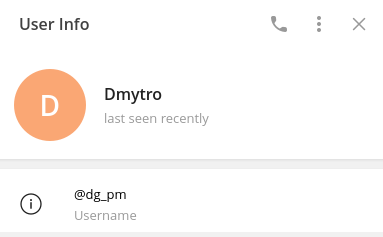
Here's info about the Telegram account that the attacker used to perform the actions described in this report. We publish this information with the hope of other users to be careful, and as a public request to the @wallet team, to which funds arrived, to freeze his account and return the funds back to TelePay, if it's not too late right now.
- Telegram chat_id: 134464737
- Telegram username: @dg_pm
- First name: Dmytro
- Last name: not defined
- Selected language: English
- On-chain wallet: EQCoVVpWl8rG-ekbQIVI3T-iSskCFMlhSjeM6rE6vCK2P2a6
11:59:44 to 12:04:02 UTC
The attacker tried performing two deposits of 10 TON each by using TelePay, but both expired.
- Invoice: E6WCU1MON2
- Invoice: A7SOSNGSGH
12:26:30 UTC
The attacker performed a deposit of 5 TON successfully, which was later used to pay for an ad at the TON ads bot.
- Invoice: TJ8HPR4X2R
- Transaction: https://tonscan.org/tx/28777934000003:CgbkkQyKrkbBGnKtJgrEdtb4RF3YJ+VYalweASz6doc=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
12:31:20 UTC
The attacker sent an ad with the text "Buy pizza 🍕 https://dominos.ua", paying a total price of 2.78735 TON and reaching 521 users.
20:19:26 UTC
1) The attacker tried to perform a withdrawal of 2.21265 TON, which was its current wallet balance after depositing 5 TON and sending an ad.
2) TelePay applied a withdrawal fee and extracted 2.10202 TON on-chain. Transaction: https://tonscan.org/tx/28786834000003:zpW7MQOKR1bshD0HusppMR9iLpYynOeq9BDHQGyWssc=:EQCoVVpWl8rG-ekbQIVI3T-iSskCFMlhSjeM6rE6vCK2P2a6
3) TelePay failed to discount the balance from the merchant (TONxAds) virtual wallet on TelePay. The error was caused by an internal communication problem between different parts of the platform, leaving the balance untouched.
4) TelePay reported the withdrawal as failed to the TON ads bot, but the balance was moved on-chain.
5) Here is when the attacker discovered the vulnerability that allowed him to withdraw funds over and over again. Imagine an ATM to which you request funds, it gives you cash and never reduces your card balance. Something like that happened.
20:19:43 UTC
Just a few seconds later, the attacker realized the vulnerability and tried performing the 2nd withdrawal, now of 2 TON. One more time, TelePay applied a withdrawal fee and extracted the funds successfully, and failed to deduce the balance internally on the merchant wallet, as described in the previous points from 1) to 4) equally.
20:20:09 to 20:24:13 UTC
The attacker extracted a total amount of 18,0614 TON in 9 different withdrawals. The reason for doing it was because the TON ads bot won't allow him to extract more than its current limit, given by the current internal virtual wallet amount: 2.21265 TON.
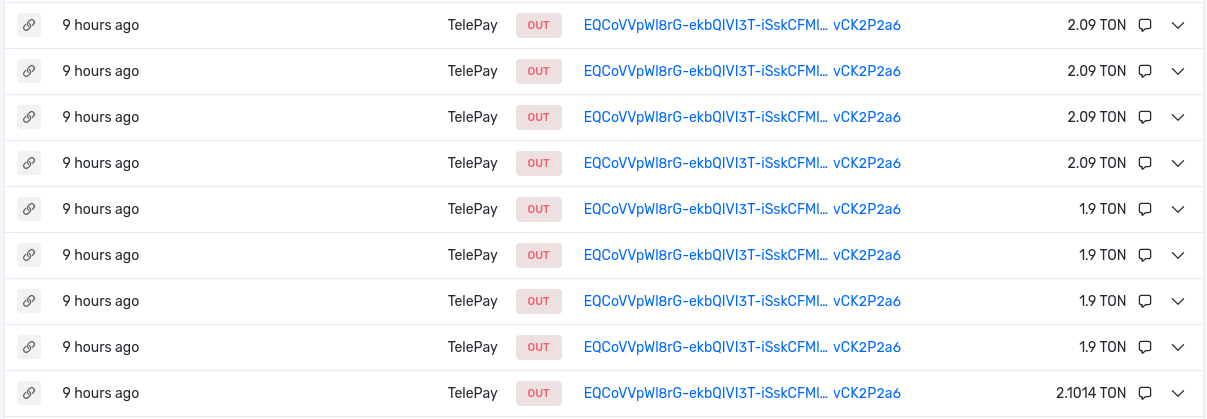
Transactions:
- https://tonscan.org/tx/28786849000001:59Rnq%2FODlU4Jyq+chrEKp1RQjdobS7MowgeK6vNc4ig=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786857000001:xxb+QlNzb6GZ74VErFnQSyNegaPM6QFebvQO2ChogTE=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786885000001:HT1xpnJKhvhgNAt0FTkMsIz+EGcwRvKMDE9kbJpOyuM=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786891000001:GYuHJ3yRyvclHL5JEK0hbgkKwLE63Nef9lrJuRgWpcw=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786898000001:GyMjbmiuRyPaGPKfOWZusuE5ZhYtrLrdSaWoCUa4sBQ=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786907000001:pWbu5mhHpwgz370VxwHWMtvXlo9H7RNVm%2FoZufBrRQI=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786916000001:9ZWYrxM0v3nEphILbqmyrUikuvsw9pMukdHURQIFDAQ=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786920000001:RqptF3hB+5ZXUOzIdWQgvt9vVEwYKoyDmEQIiNrqTt8=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786927000001:QGhob%2Fl3TNS7wdEswl+mv1skOd5EZhhZ3UoKmV67eGo=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
20:24:47 UTC
The attacker realized he could rise the limit to extract more funds quickly by depositing more TON into the TON ads bot. And he performed a deposit of 38 TON.
- Invoice: EC4ELT08IM.
- Transaction: https://tonscan.org/tx/28786951000003:IOWw8KeHRR+D9qz28NNVDf77LShrPXCA+rSKFWDVRaw=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
20:25:41 to 20:27:50 UTC
The attacker extracted a total amount of 266 TON in 7 different withdrawals.
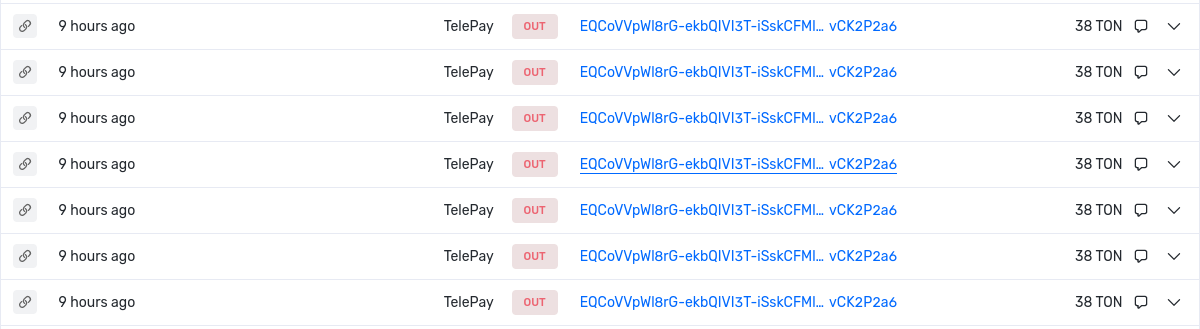
Transactions:
- https://tonscan.org/tx/28786960000001:A%2FuMP%2FPhkdvYYUQOz35z4lmY5sJJERnM7jxZJNqiw7A=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786972000001:Ge7hUCpJzZl74V1K9hfcJuj7OpoD2mXF3oI8zKAqfrU=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786979000001:1vHnuW4isnkrL2b5aRW9mZL5mg3IqbZaf9%2FWProc3P4=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786986000001:dNxK6nUxEUndvIgyo%2FtE3bL8fVzjXIxScZCz9OmhMB8=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786991000001:LdGR1NHlGm1RRlFt0lRahGu+qLasxWQhtQmCZE5zdms=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28786997000001:SoUTNzgd+e7d7tex6I+wbi+3qPjjKxblXsI2JHb161s=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
- https://tonscan.org/tx/28787002000001:RMBzB7rnBsxRmkXtoXMPPmNAgWueaJaBb6eLc8p+KhM=:EQA5Pxp_EC9pTlxrvO59D1iqBqodajojullgf07ENKa22oSN
20:27:58 UTC
1) Our team realized an unusual flow of transactions and stopped by to inspect them and detected the attack.
2) We immediately shut down both TelePay and the TON Ads bot, to inspect the situation closely and prevent more funds to be stolen.
20:32:24 UTC
1) Realizing it was not possible to keep stealing, the attacker moved the funds from wallet A to wallet B by a total amount of 274.95 TON.
2) Then, it moved the funds from wallet B to @wallet bot, to hide the funds from public view and us auditing the transactions.
3) We contacted the @wallet team via its support bot at @wallet_supportbot to report the situation and ask them to freeze the user funds, and if possible, return them to us. At the moment of writing this report, they haven't replied to our message.
2022-06-16 04:33:00 UTC
We implemented a hotfix to restrict withdrawals, both on TelePay and the TON ads bot, and recovered the services back online.
Our CEO announced he deposited the equivalent amount of what the attacker stole, to compensate liquidity previously lost on the platform, and to save users from being affected.
2022-06-17 18:41 UTC
The attacker commented in our public Telegram chat in English, confessing the committed crime. We attach the message here as proof of confession.
The user says it "proposed to return money", but we've never received any official contact intent from him, nor our team has contacted him, nor anyone in our team has been authorized to establish any kind of contact.
We're very sorry for this incident and offer apologies to all of our users. Our team will keep working hard to improve security, preventing events like this to happen again. If you need to contact us, you can do it via support@telepay.cash or in our live chat at telepay.cash.
This report is being actively updated. Latest update: 2022-06-16 06:15:00 UTC.