SQL injection vulnerability allowing login bypass
Hacking For Ramen
> Objective
This lab contains an SQL injection vulnerability in the login function.
To solve the lab, perform an SQL injection attack that logs in to the application as the administrator user.
> Solving the challenge
In this challenge, we will work with the vulnerable e-shop website:

As the objective says where exactly look for the vulnerability, let's head to the login page directly:

We will try the most basic SQL injection again:

And that will solve the challenge for us.
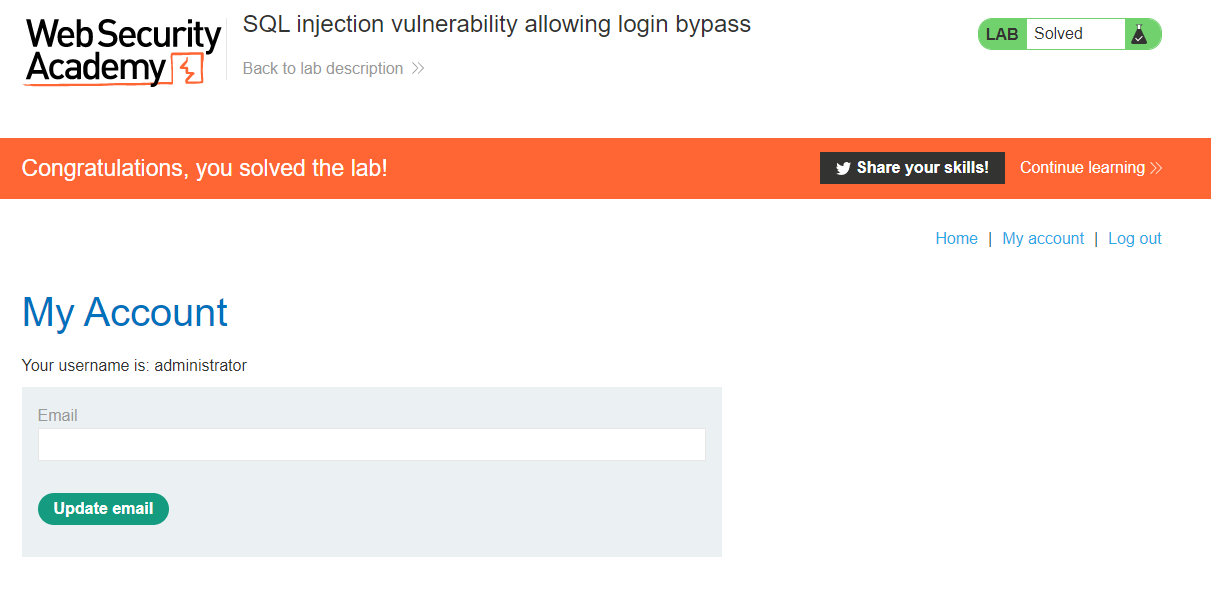
The more important question is why did that work. We know that usernames and their passwords are stored in the database. By providing the 'or 1=1--, or just the '-- we are manipulating the initial SQL query and submitting the request without specifying the password.
It might look silly at this point, but the idea will not change on the further harder challenges about SQL injections - we will find the way how to manipulate the initial SQL query, and bypass mitigation that are in place.
In this case, there is nothing to bypass, so it is simple like that.