Public And Private Keys

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
РекламаМужское нижнее бельё KEY! Купить! Сезонная распродажа! Скидки от 5 до 40% на всё! · Москва · пн-пт 10:00-18:00, сб 11:00-17:00
Public and private keys are an integral component of cryptocurrencies built on blockchain networks that are part of a larger field of cryptography known as Public Key Cryptography (PKC) or Asymmetric Encryption.
www.ledger.com/academy/blockchain/what …
Is it possible to find private key using only public key?
Is it possible to find private key using only public key?
However it’s impossible to find the private key using only the public key. Public and private keys are an integral component of cryptocurrencies built on blockchain networks that are part of a larger field of cryptography known as Public Key Cryptography (PKC) or Asymmetric Encryption.
www.ledger.com/academy/blockchain/what …
How are public and private keys used in cryptography?
How are public and private keys used in cryptography?
Public and private keys form the basis for public key cryptography , also known as asymmetric cryptography. In public key cryptography, every public key matches to only one private key. Together, they are used to encrypt and decrypt messages.
www.preveil.com/blog/public-and-private-k…
By generating a Public Key, we have a way to interact with other people on the network openly, for example we may have some Bitcoin “ attached ” to our Public Key What is a Private Key?
medium.com/coinmonks/private-and-public …
Which is the best definition of a private key?
Which is the best definition of a private key?
What is a Private Key? 1 A private key, is simply an extremely large and highly random number 2 The image below shows a Private Key generated by a wallet program written by me 3 DO NOT USE THIS NUMBER AS YOUR PRIVATE KEY
medium.com/coinmonks/private-and-public …
https://learn.bybit.com/blockchain/what-is-public-keys-and-private-keys-in...
Cryptography Methods Used in Cryptocurrencies
How Does Private and Public Keys Work?
The Differences Between Public Keys and Private Keys
Benefits and Limitations of Public and Private Key Encryption
When to Choose A Public Or Private Key?
Closing Thoughts
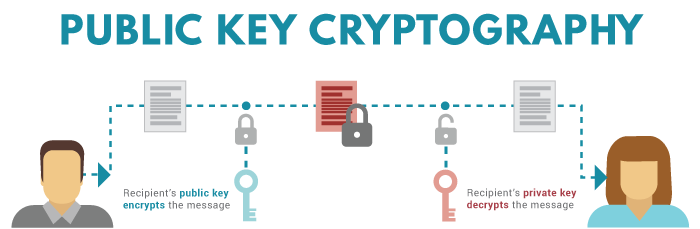
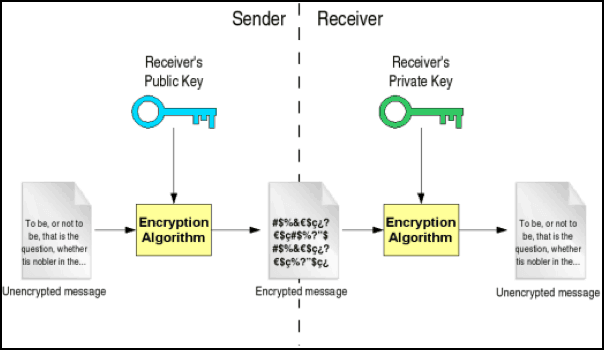
Public key cryptography has two primary use cases— identification and confidentiality. In simple words, it can be described in the following way: 1. A sender gets an addressee’s public key. 2. The sender uses this key to encrypt information. 3. The sender sends the encrypted information to an addressee. 4. The addressee uses his or her private key to decrypt the data. Let’s say, Alex (…
https://www.ledger.com/academy/blockchain/what-are-public-keys-and-private-keys
Public Key Cryptography
The Concept of Public and Private Keys
How A Transaction Works
The general purpose of PKC is to enable secure, private communication using digital signatures in a public channel where there can be potentially malicious eavesdroppers. In the context of cryptocurrencies, the goal is to prove that a spent transaction was indeed signed by the owner of the funds, and was not forged, all occurring over a public blockchain network between peers. Whe…
What is Public and Private Key Encryption?
How To Generate RSA Public and Private Key Pair with OpenSSL
How do private and public keys work? Digital signatures explained
Public and Private Keys - CompTIA Security SY0-401: 6.3
Python generate RSA public and private key
Asymmetric Encryption: Public and Private Keys
https://www.preveil.com/blog/public-and-private-key
Public and Private Keys: An Example
Generating Public and Private Keys
Digital Signatures
Diffie-Helman Key Exchange
Conclusion
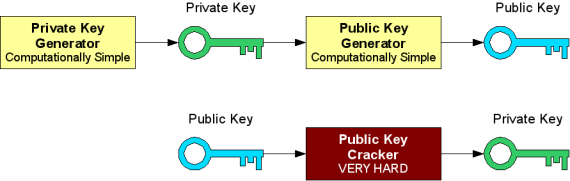
The public and private key are not really keys but rather are really large prime numbers that are mathematically related to one another. Being related in this case means that whatever is encrypted by the public key can only be decrypted by the related private key. A person cannot guess the private key based on knowing the public key. Because of this, a public key ca…
https://www.tutorialspoint.com/difference-between-private-key-and-public-key
Строк: 7 · 15.04.2020 · The public key is used to encrypt and a private key is used decrypt the data. The private key is shared between the sender and receiver of the encrypted sensitive information. The public key is also called asymmetric cryptography. The following are some of the important differences between Private Key and Public Key.
https://freewallet.org/blog/public-private-keys
15.10.2019 · The combination of public and private keys works to safely store cryptocurrency. The public key is the address of your wallet and the private key works as a password. The public key is tied to a single private key (or set of private keys in case of multisig) and vise versa. How private keys …
https://medium.com/coinmonks/private-and-public-key-cryptography-explained-simply-4c...
26.02.2018 · Private keys are simply extremely large and random numbers Public Keys are (x, y) points on an Elliptic Curve, generated by using the Private Key as a scalar Private and Public Key …
https://www.geeksforgeeks.org/difference-between-private-key-and-public-key
29.01.2020 · In Public key, two keys are used one key is used for encryption and another key is used for decryption. One key (public key) is used for encrypt the plain text to convert it into cipher text and another key (private key) …
https://en.m.wikipedia.org/wiki/Public-key_cryptography
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys (which may be known to others), and private keys (which may never be known by any except the owner). The generation of such key …
https://stackoverflow.com/questions/273396
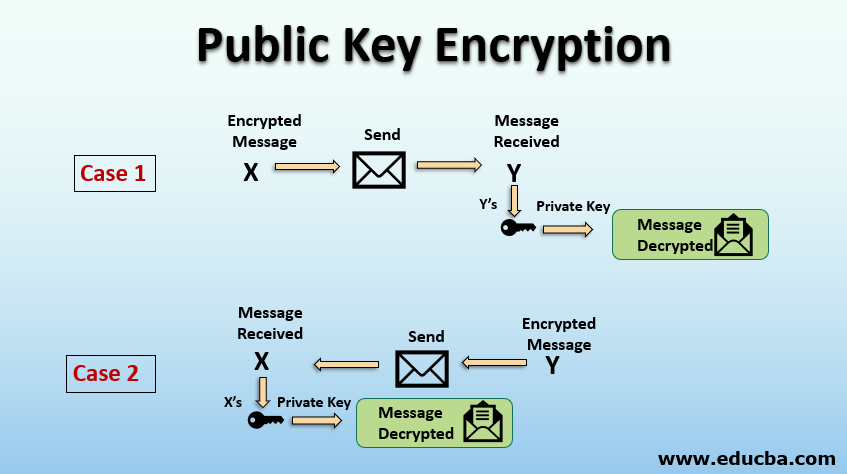
Public-key cryptography involves two related keys for each recipient involved - a private key which is a secret known only by the recipient, and a related public key which is known by all senders. The sender encrypts the message using the recipient's public key.
РекламаНедорого! Клавиатура и мышь Wireless Canyon SET W3 105 keys chocolate key caps b
Не удается получить доступ к вашему текущему расположению. Для получения лучших результатов предоставьте Bing доступ к данным о расположении или введите расположение.
Не удается получить доступ к расположению вашего устройства. Для получения лучших результатов введите расположение.
A password will be e-mailed to you.
Join our community & learn for free
No Spams. Only heaps of sweet content and industry updates in the crypto space.
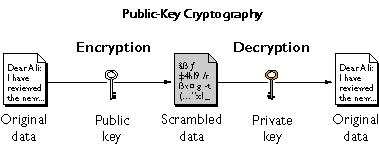
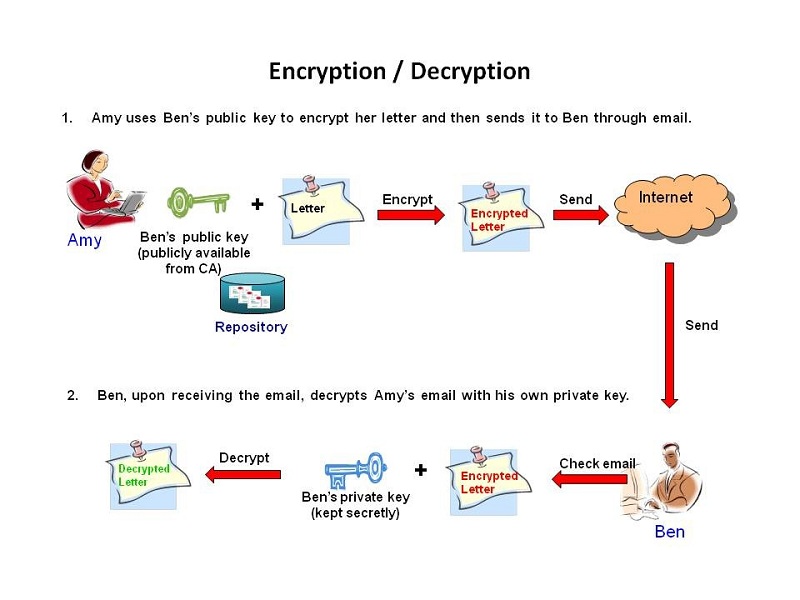
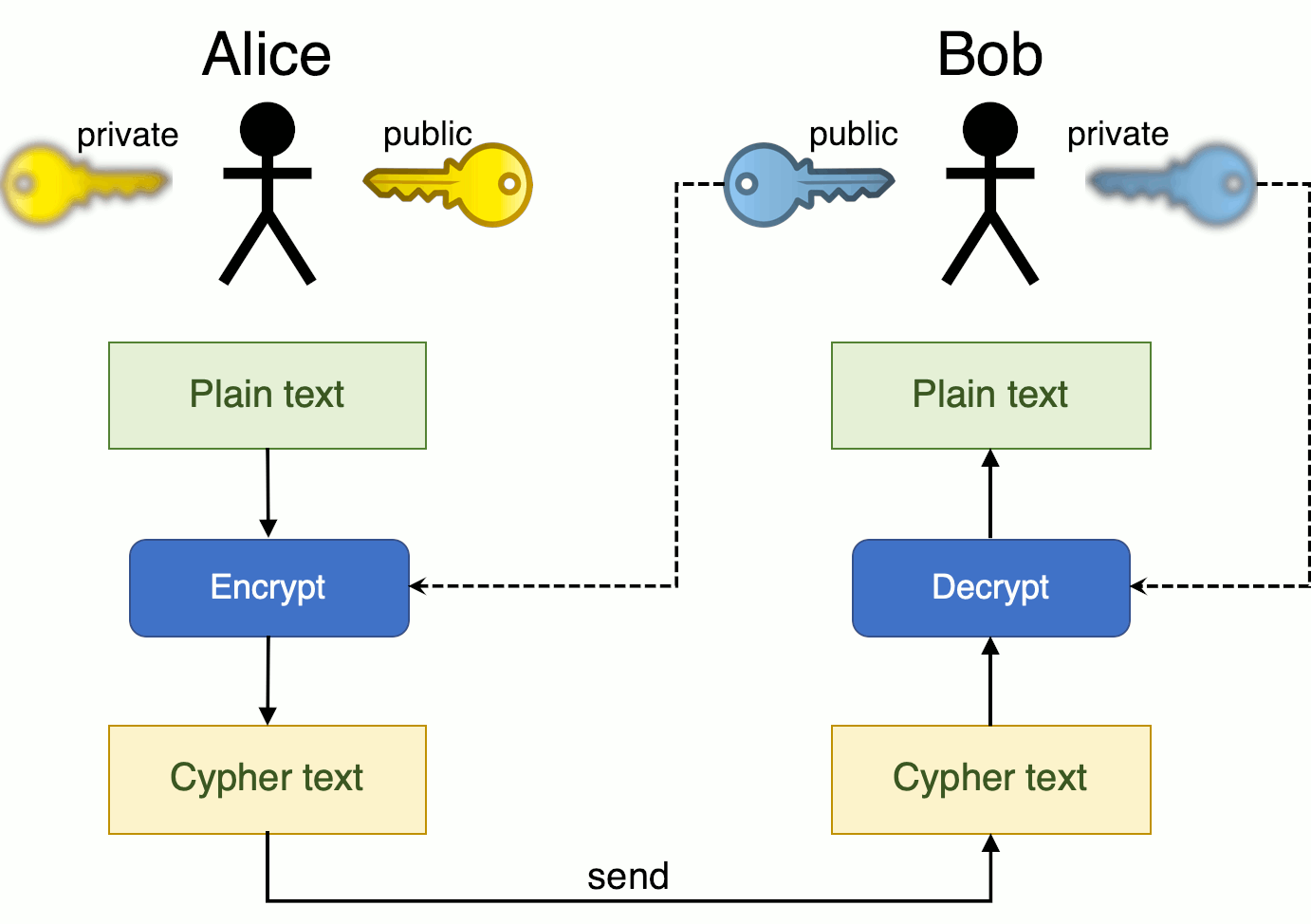
Cryptography is the core of cryptocurrency, and without it, none of the transactions will be secured, nor the integrity of any information is upheld. Think of it this way, when you perform peer-to-peer (P2P) transfers, your data may be exposed without secure encryption, and anyone can attempt to read the data structure without knowing the data has been tampered with. That’s exactly why private and public keys are so essential to authorize these transactions.
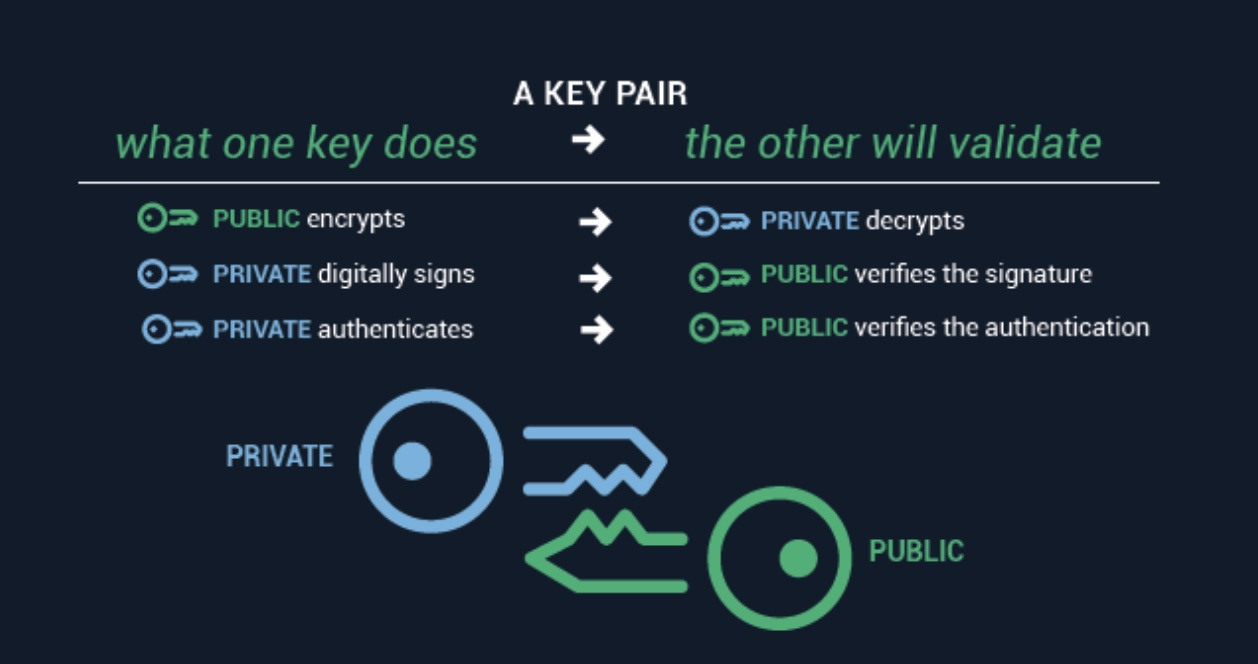
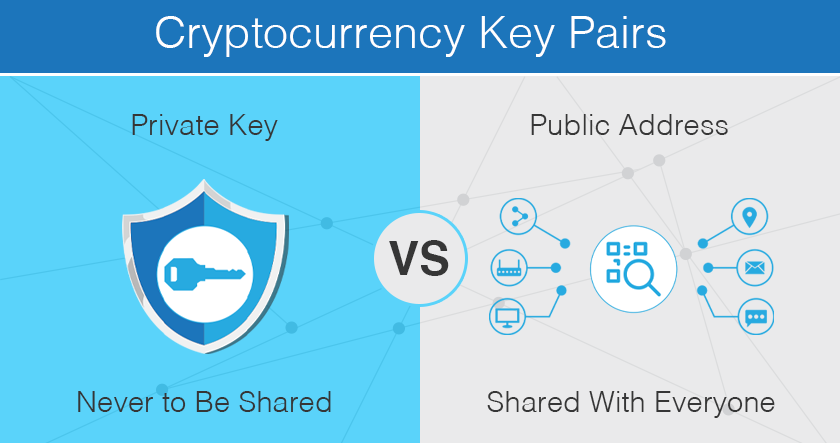
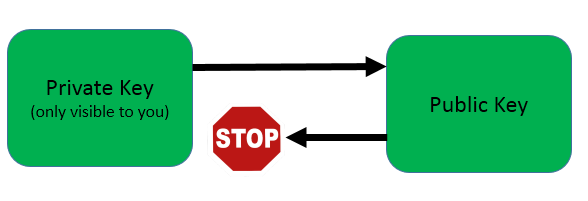
While both the public and private keys strive to secure a transaction, they are distinctively different, corresponding with their purposes. When comparing them side-by-side, a public key is used to verify a transaction after a transaction has been requested. Commonly a public key is also translated as an ‘address’ to receive cryptocurrencies. Whereas a private key that is associated with a cryptocurrency account focuses on authorizing the transaction.
Typically, a private key is not shared and only the owner should know it. In another word, if anyone granted access to your private key will have the authority to deplete your asset in a wallet.
That is why you must understand what they are, why they are so important. Perhaps, to learn how not to be the person who locked out millions from their Bitcoin fortunes.
A public and private key is basically used to decrypt the messages encrypted in a complex mathematical algorithm within the cryptography methodology. While a public key can be widely distributed, a private key used in the crypto context is meant to be kept discretely as a password to safeguard your digital assets.
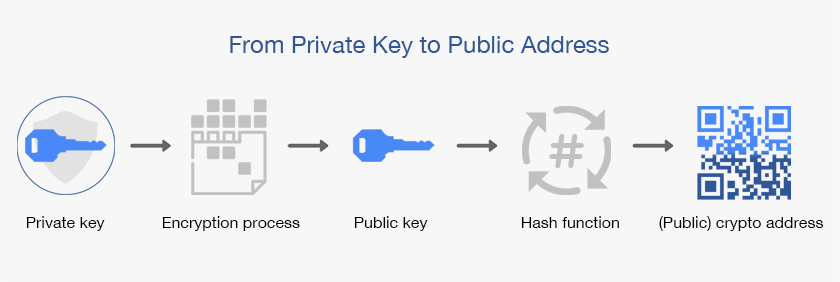
Usually, these private keys vary depending on the different types of cryptocurrency, although almost all of them use 256-bit encryption. That includes BTC, ETH, LTC, and more. For example, a Bitcoin private key is formatted with the values:
0x01 and 0xFFFF FFFF FFFF FFFF FFFF FFFF FFFF FFFE BAAE DCE6 AF48 A03B BFD2 5E8C D036 4140, representing nearly the entire range of 2256-1 values.
An example of a public key is as below:
3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001
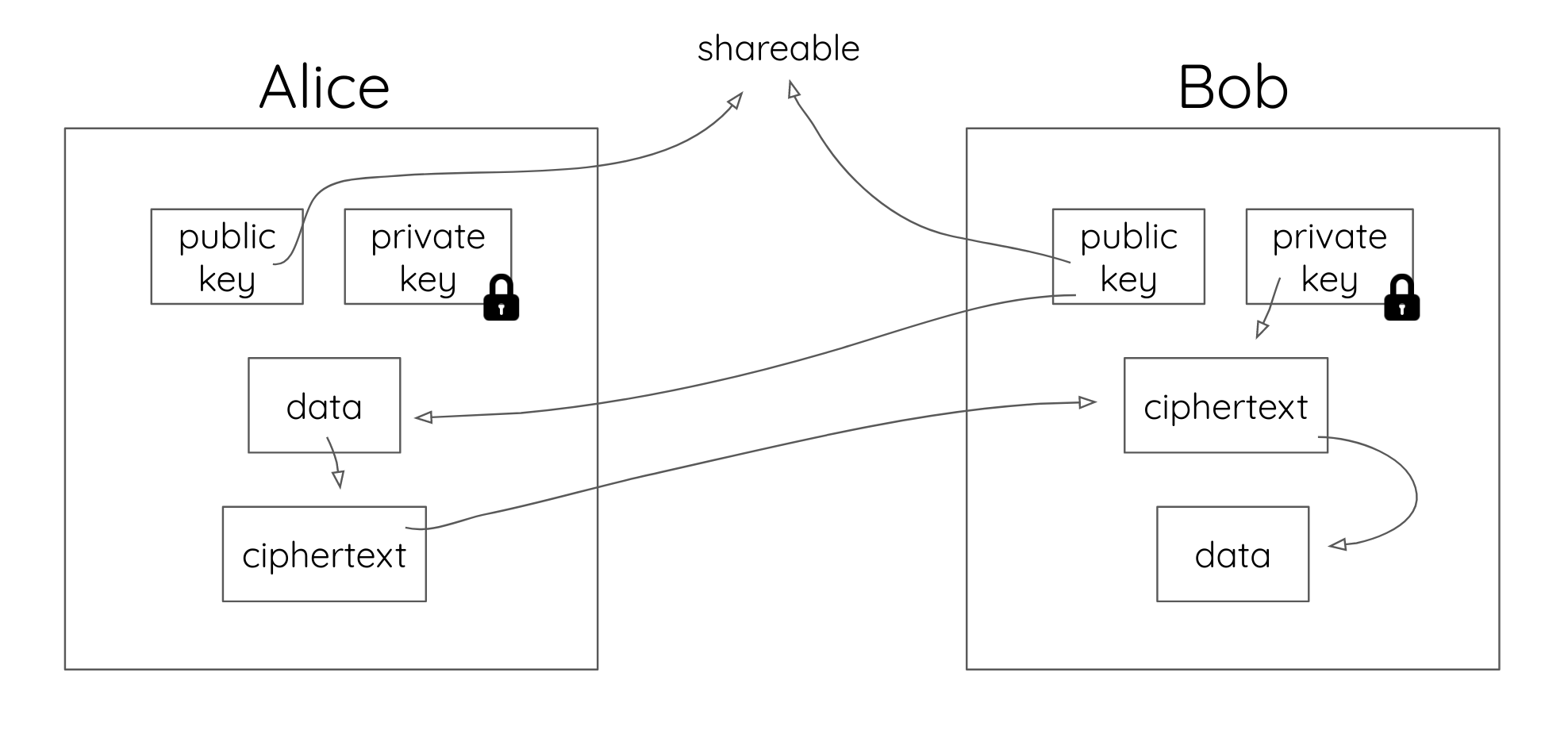
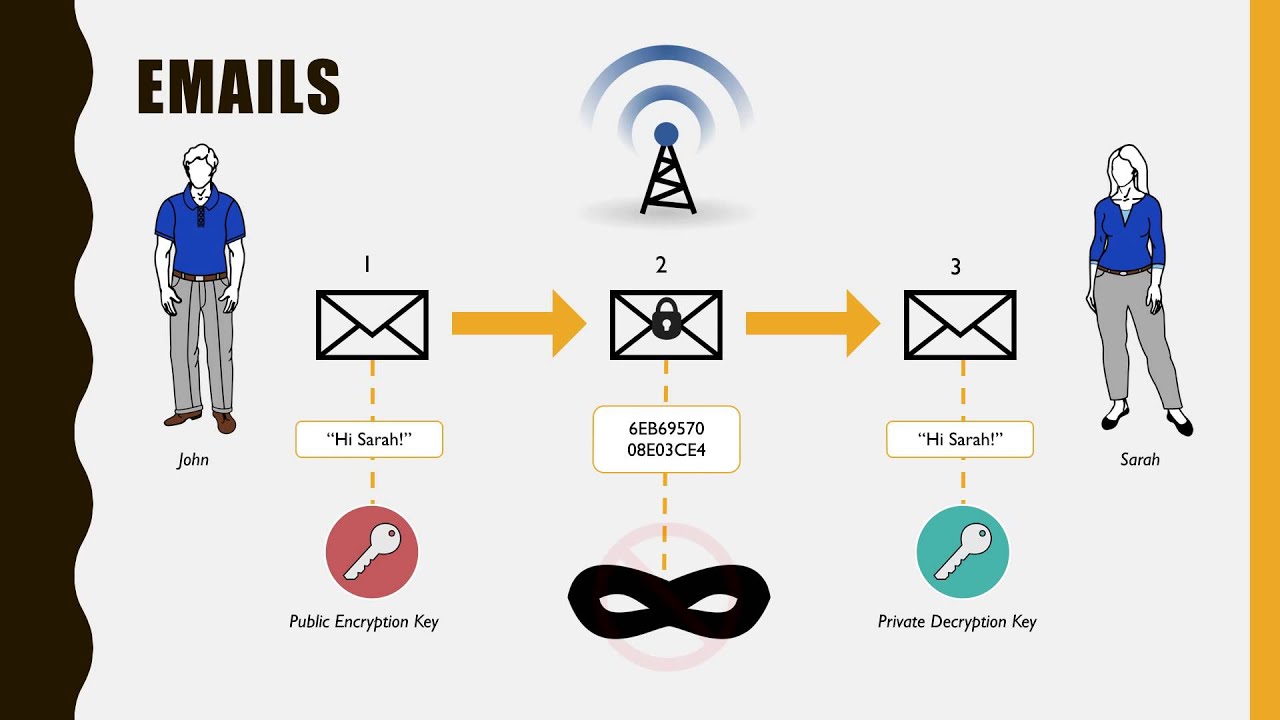
The key is a sequence of random symbols available to any person (public key) or known only by its owner (private key). The public key is used for encryption, but it is only a private key that can help one to decrypt the information. That said, it is possible to find out a public key if you know a private key, but it is relatively impossible to find out a private key with a public key.
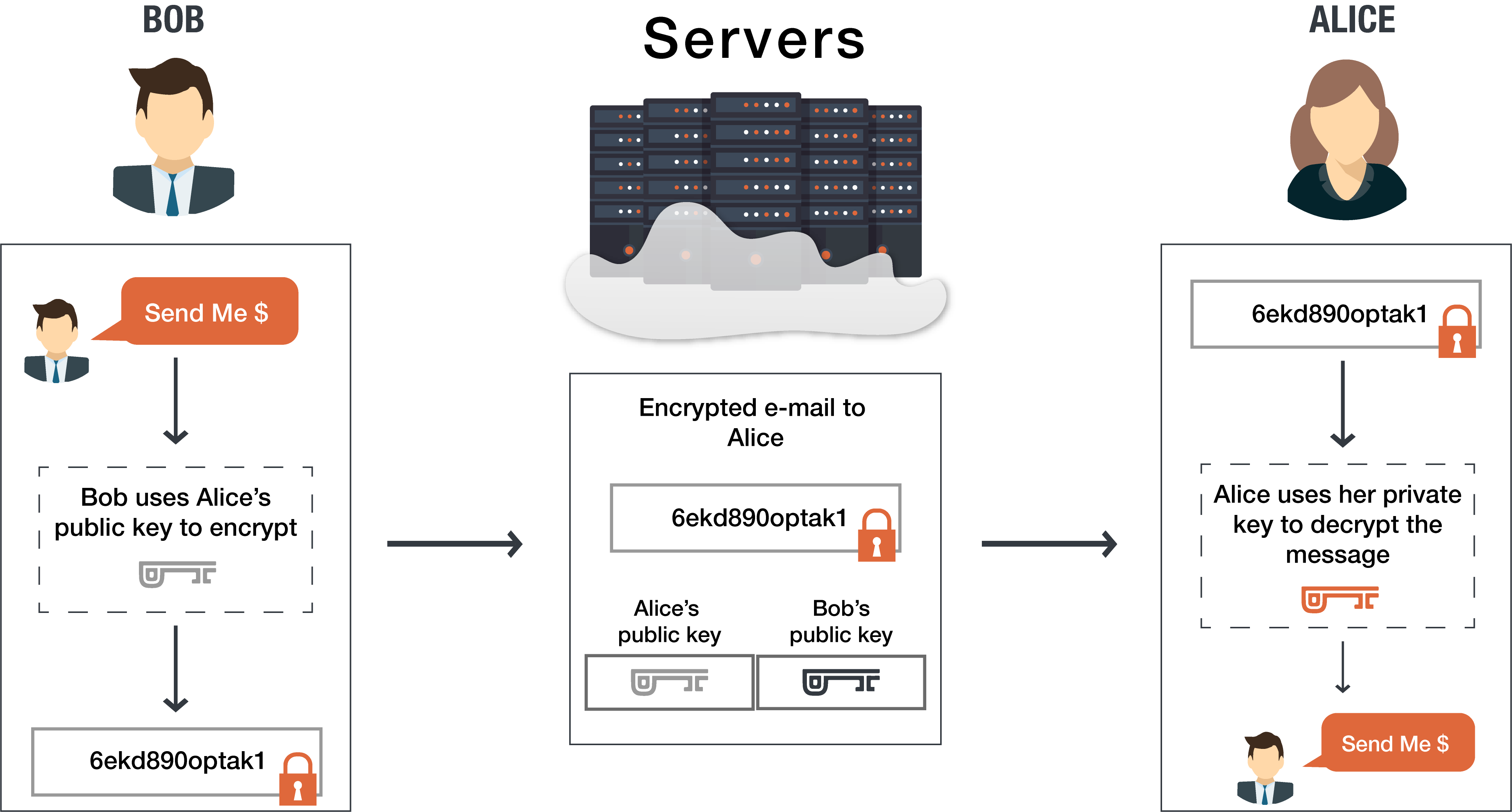
Cryptocurrency wallets are excellent examples of public and private keys utilization. When considering wallets, a public key is a user’s address, and it gives other network participants a point of access to send tokens to this wallet. But if a user wants to send crypto from one to another, they’ll need their private keys to confirm the transaction.
Just like logging into your email, you’ll need a password. The email address is a fixed point for other email network participants to send messages. While the password is required to get full access to the email account.
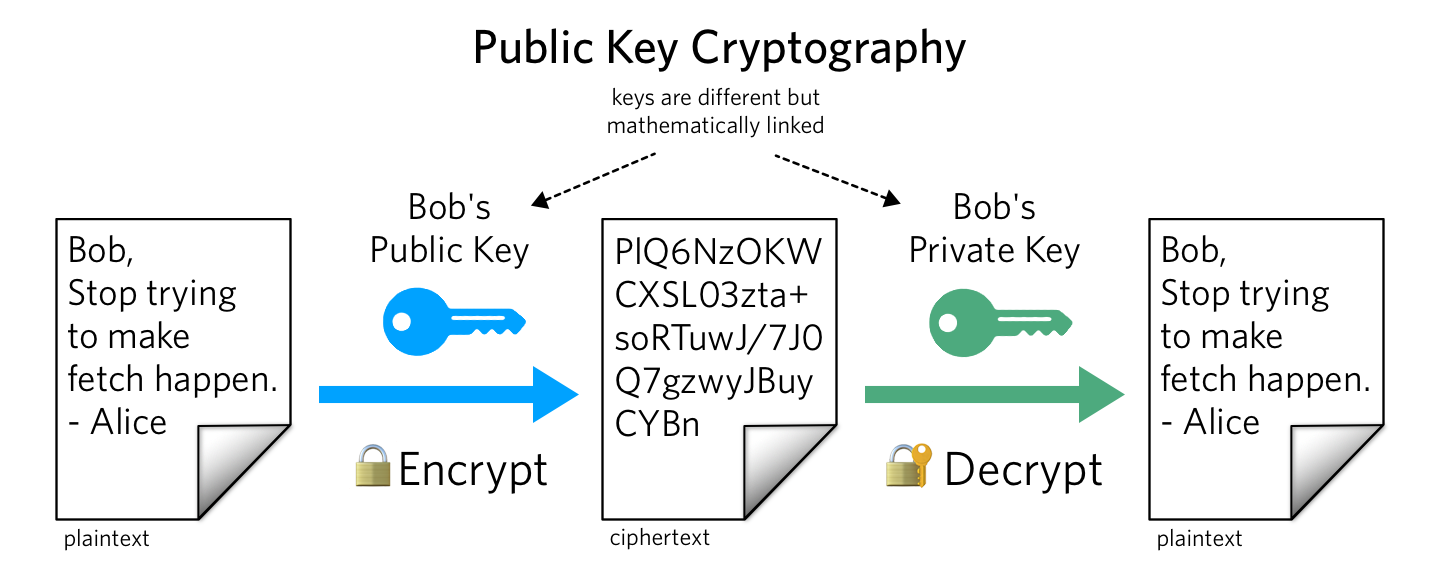
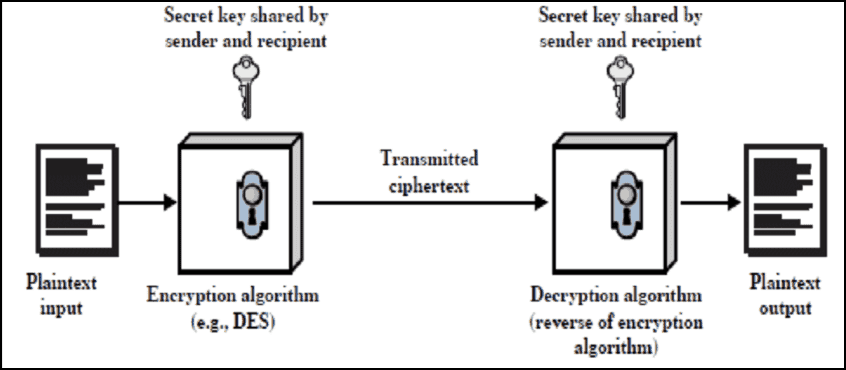
However, for the longest time, symmetric encryption was the primary encryption type where every message was encrypted and decrypted with the same code (key). Still, it raises serious doubts about its security. Thus, asymmetric encryption is designed to meet these security challenges with a pair of keys (one public and one private) used separately to encrypt and decrypt messages.
Unlike symmetric encryption with one key to encrypt and decrypt information, public and private keys must “match” the encrypted data. They are generated and used simultaneously. But what is it about?
When it comes to cryptography in cryptocurrency, there are several methods, and that includes symmetric encryption, asymmetric encryption, and hashing.
Hashing is designed to encode the user’s account addresses to encrypt transactions between accounts. To ensure the encryption is secured, random letters and numbers are added to the stored value. That is mainly to mitigate the risks of easy decryption. While the stored value refers to digital fingerprint or hash value once the conversion is completed.
It is one of the most popular, easiest, yet effective encryption. The messages are encrypted with a single key in which the key could be identical or different between parties simultaneously. It is then transmitted to a recipient and to be decrypted once it is received and verified.
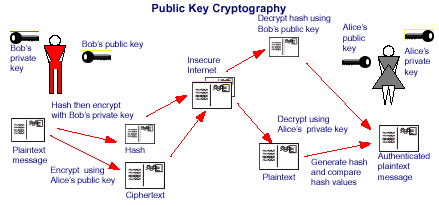
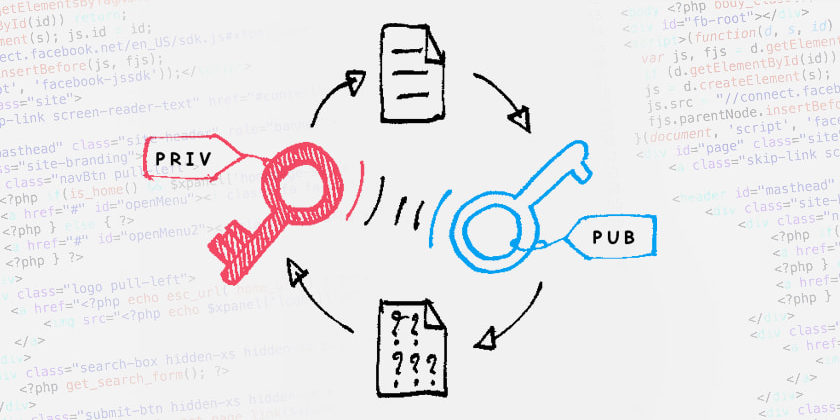
Unlike symmetric, the encryption and decryption of messages usually involve two keys— Private and Public Key. Public keys are used to verify a transaction after a transaction has been requested. Whereas a private key is to decipher the message or transaction. The concept is to uphold the transaction’s authenticity and to mitigate the possibility of security downfall. That also means, if the private keys are misplaced, there are no ways to find them. Similarly, if the private key is exposed, any transactions can be granted, and it’s unretrievable because it’s authorized.
Public key cryptography has two primary use cases— identification and confidentiality. In simple words, it can be described in the following way:
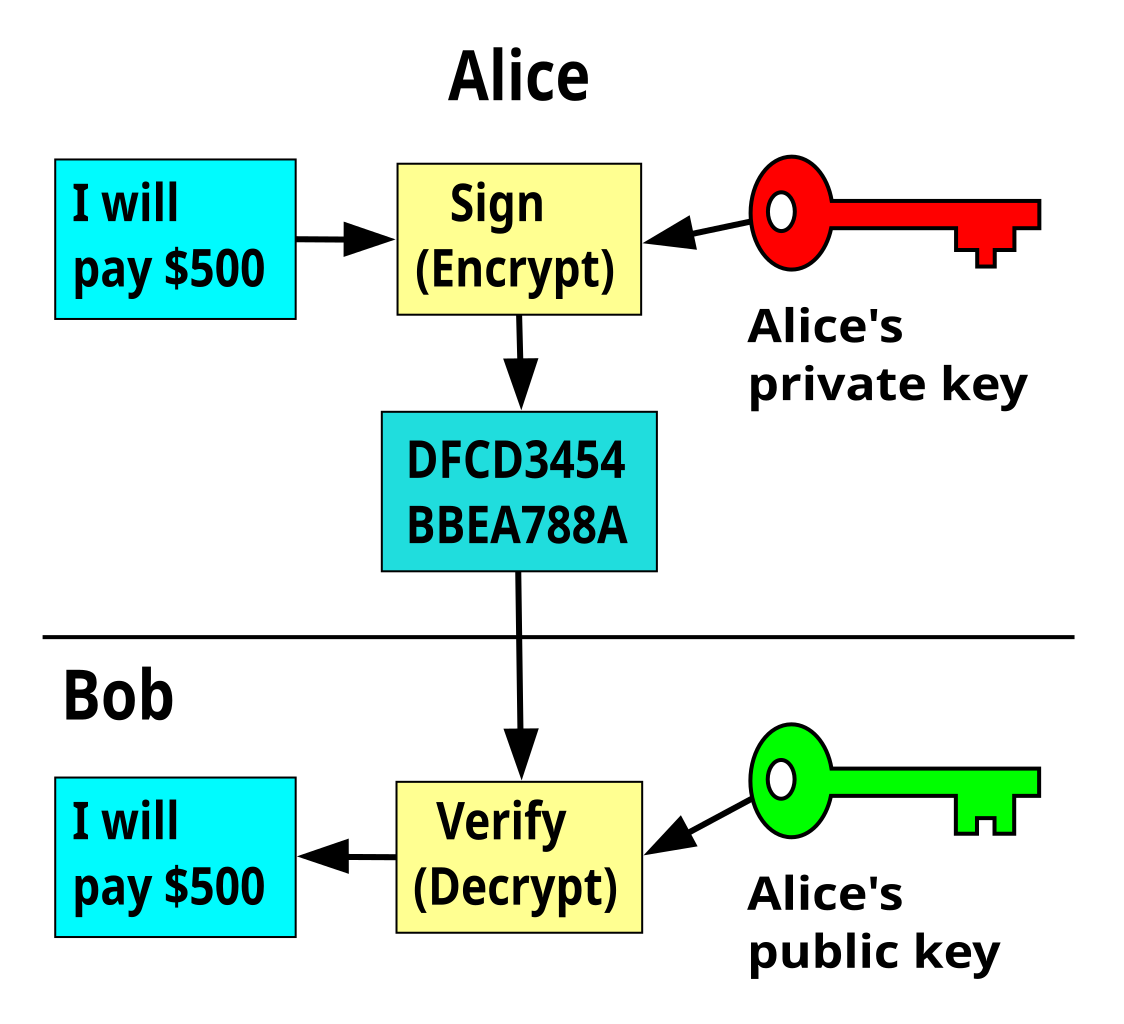
Let’s say, Alex (sender) wants to send 1 BTC to Jane (recipient). He knows her public key and uses it to encrypt the transaction. Jane receives the transaction and decrypts Alex’s transfer of 1 BTC with her private key. Jane should be the only person who can authorize the transaction as nobody else knows her private key.
When it comes to cryptocurrency, a private key is what you own physically. It proves your rights to manage your digital assets and to authorize any transactions. Whoever knows this key can spend the associated funds.
Both private and public keys’ goal is to verify that a given transaction was spent by the party who signed it and not forged out of thin air. Though both types of encryption cater a similar purpose, they differ in many ways. Here’s what you need to understand:
In public-key encryption, there must be two separate keys for encryption and decryption. The private key is for the owner only, while the public key is available to anyone. One key is required for transmission between the two parties involved in symmetric key cryptography. The same private key is used both to encrypt and decrypt the information. It is shared between the sender and receiver of an encrypted message.
The private key mechanism is much faster than the public key. That’s because a private key requires only one key while the public key requires two keys.
The private key is kept secret and not disclosed to anyone apart from the wallet’s owner. Once lost, the private key is impossible to restore, and the encrypted file becomes unusable. Typically, these keys are difficult to remember as it involves complex numberings. Still, the safety of private keys is entirely up to its owner. That is why the best method to keep your private keys safe is an offline storage device. On the other hand, the public key is open to all users and should be available upon search. It is unlikely to lose the public key.
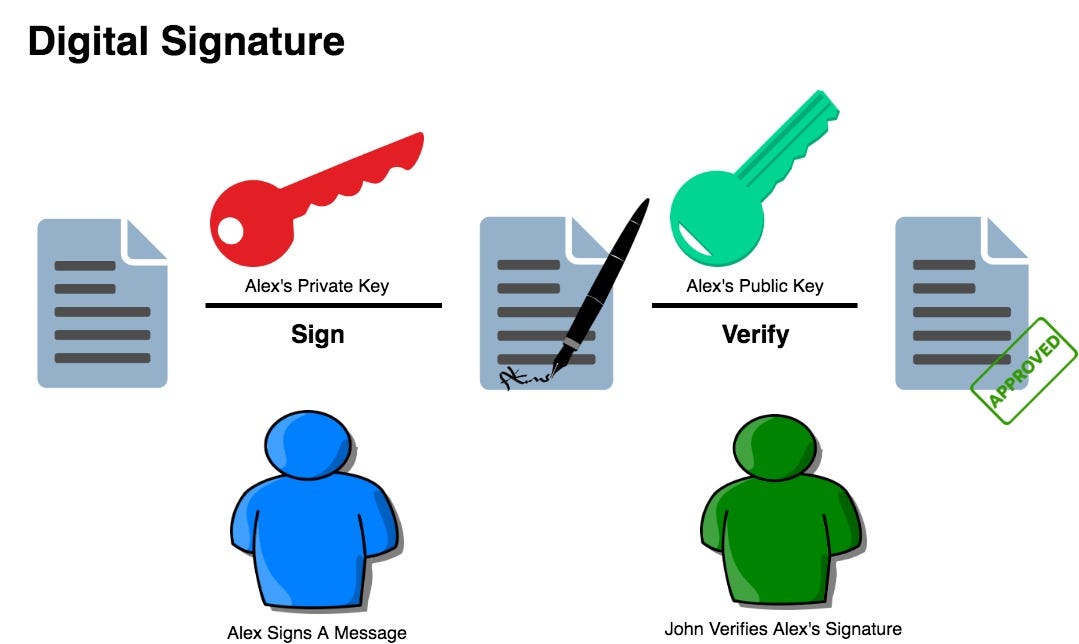
The web content can be digitally signed with the user’s private key and verified by the user’s public key. That makes it easy to identify the message sender in the network and confirm that a trusted identity sent a message.
The digital signature provides certain security benefits such as:
The content is encrypted with the user’s public key and can only be decrypted with its private key. That is the only way to convert the message back.
Encryption provides the following security benefits:
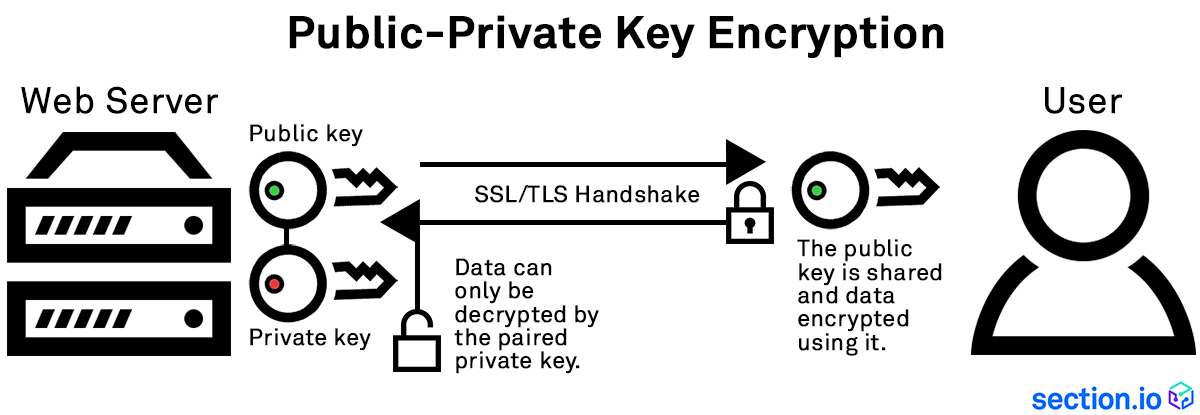
Public key cryptography is used in a large number of protocols and data formats, which are implemented by a vast range of applications and system software. That includes the SSL protocol, SSH, digitally signed PDF files, OpenPGP, S/MIME, etc. It is widely applied to software programs, such as browsers, to ensure secure connections in insecure networks. Asymmetric cryptography forms the base for the blockchain algorithm, which constitutes a base for all cryptocurrencies.
There is no perfection for any methodologies or encryption, and that includes the public and private keys. Here are the pros and cons:
Adopting private key encryption technology is an excellent way for any business to protect important information from prying eyes. Regardless if you choose a symmetric or asymmetric encryption method. They both have their advantages and disadvantages as any other technology.
However, symmetric encryption is faster and easier to carry out. The system performs a single, reversible mathematical equation to encrypt or decrypt a file. That is why this method requires fewer computer resources than asymmetric encryption.
Simultaneously, while private key encryption provides a much higher security level, it still has some setbacks. The main problem associated with this method is the problem of key transportation. It involves insecure forms of communication to transmit the key. It’s risky to allow third parties to be granted access to the key that unlocks the data. This method cannot guarantee the origin and authenticity of the message and may cause some problems if there is a dispute or doubt.
If a user wants to segregate the data or funds among groups, it is necessary to generate and manage multiple private keys. Too many keys are not so convenient, and a new shared key with every different party may result in increased insecurity.
The disadvantages of this method are associated with some severe weaknesses. First, the loss of the private key should lead to dismal consequences. That means that no one can ever decrypt the received data. In terms of cryptocurrency, the wallet owner will not be able to get access to his or her wallet if the private key is lost.
The choice of the encryption method varies depending on your preference and convenience. Symmetric encryption is beneficial if you value speed and data protection over the rest. For example, the Advanced Encryption Standard (AES) adopted symmetric encryption algorithm is used by many big companies and entities like Apple and Microsoft.
Besides, if you focus on data storage, symmetric encryption is ideal. It works well if the encrypted data is stored on a device and that data is not being transferred.
Asymmetric cryptography will be your preferred choice if increased security is the priority over speed and computing power. It is also important when identity verification is required, as symmetric cryptography doesn’t support it. Blockchain technologies rely on identity confirmations to authorize transactions. Thus, crypto traders and investors would prefer this.
As we move towards the digitized sphere, data storage and security have increasingly become important. Public key encryption helps users maintain reasonable security practices as nobody knows the private key paired with the open public key. It is advantageous when to avoid potential interceptions and cyber frauds. However, all you need is to ensure your private key secure and inaccessible to others.
To start trading is hard, but securing your funds is even more challenging. Bybit urges you to secure your data and learn about the importance of respecting privacy, safeguarding data, and enabling trust.
This article is intended for and only to be used for reference purposes only. No such information provided through Bybit constitutes advice or a recommendation that any investment or trading strategy is suitable for any specific person. These forecasts are based on industry trends, circumstances involving clients, and other factors, and they involve risks, variables, and uncertainties. There is no guarantee presented or implied as to the accuracy of specific forecasts, projections, or predictive statements contained herein. Users of this article agree that Bybit does not take responsibility for any of your investment decisions. Please seek professional advice before trading.
Join our community & learn for free
No Spams. Only heaps of sweet content and industry updates in the crypto space.
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept”, you consent to the use of ALL the cookies.
This website uses cookies to improve your experience while you navigate through the website. Out of
Pov Fuck 1080
Retro Vintage Blowjob
Watcntullscene And More Mainstream Guide Taboo Videos
Seks Movies Tube
A Wife And Mother Game Fan Art
Public Keys vs. Private Keys: What Is It & How Do They ...
What Are Public Keys and Private Keys? | Ledger
Public and private encryption keys | PreVeil
Difference between Private Key and Public Key
Bitcoin Public and Private key explained | Freewallet
A Beginner’s Guide: Private and Public Key Cryptography ...
Difference between Private key and Public key - GeeksforGeeks
Public-key cryptography - Wikipedia
Public And Private Keys