Private Tunnel

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
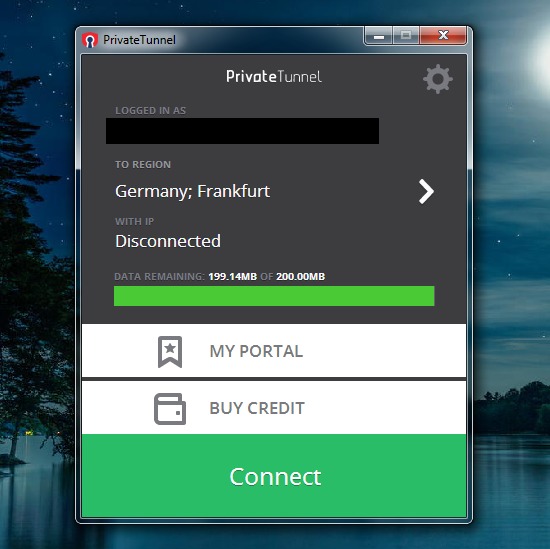
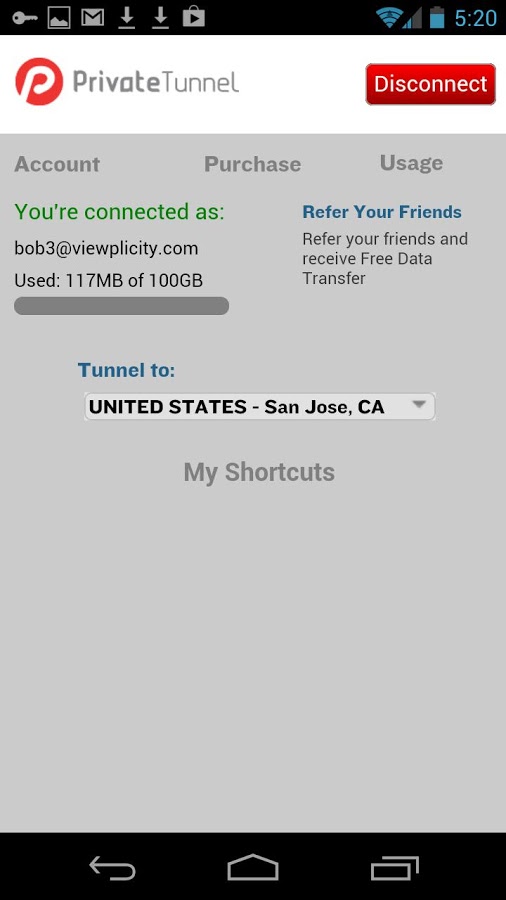
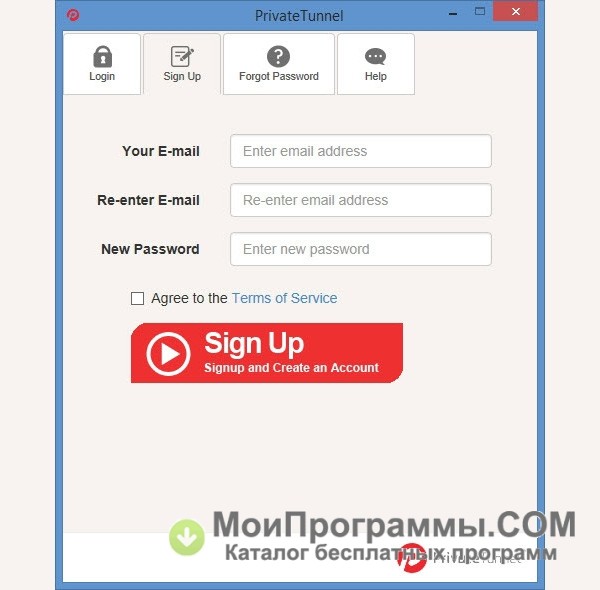
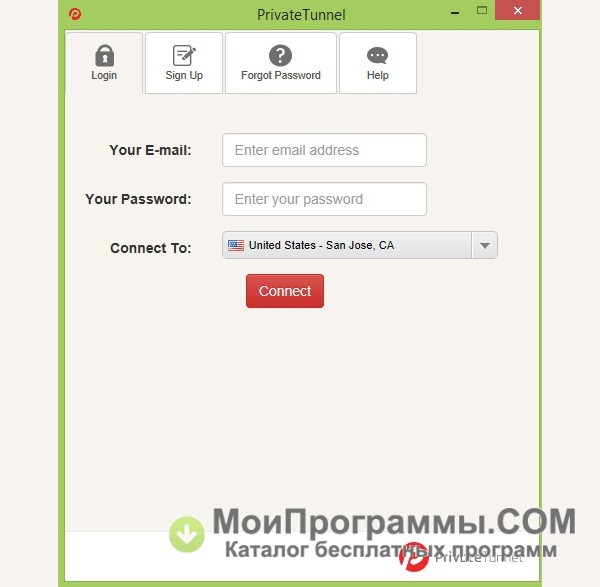
Private Tunnel
We offer the worldwide standard in encryption. AES’s block size makes it less open to attacks than other popular ciphers, making it the leading encryption algorithm.
We're here for you on every level, providing 24/7 support online with our ticketing system. You can also access chat support right here and talk to someone immediately, at any time.
Private Tunnel is built and developed by OpenVPN, the de-facto standard in the open source networking space with over 50 million downloads since inception.
COPYRIGHT 2020 OPENVPN INC. ALL RIGHTS RESERVED
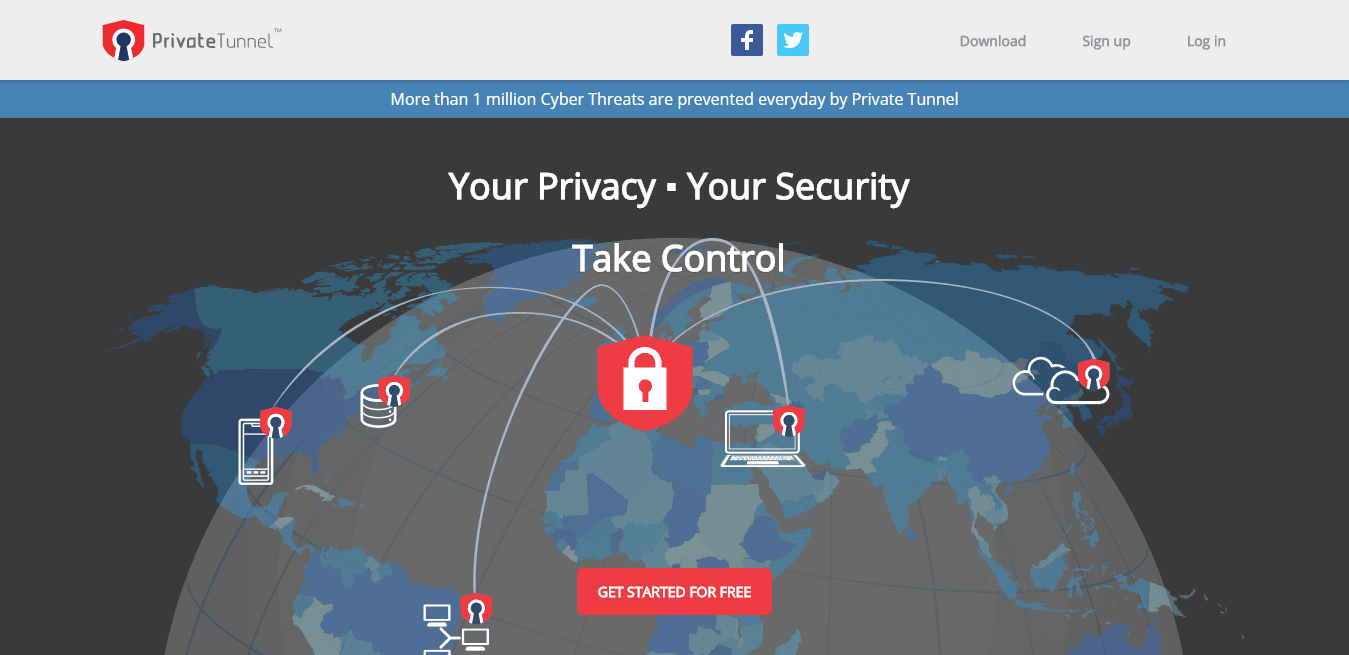
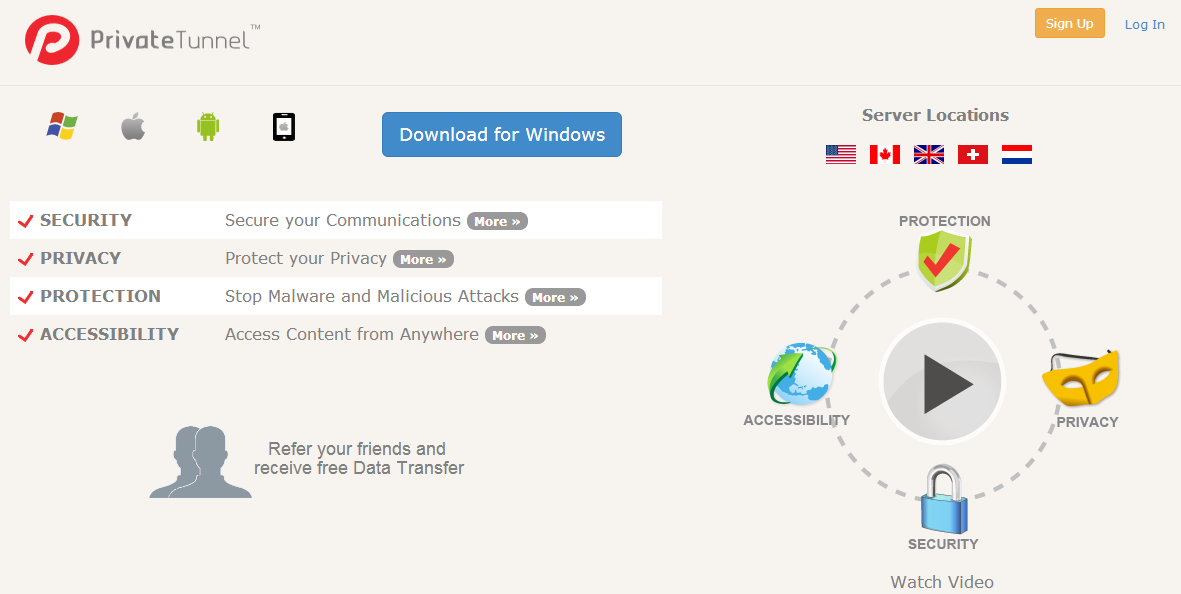
Be secure, be protected, be private, wherever and whenever you surf the net. Mask your public IP address and encrypt connections. Use our superior authentication strength to protect privacy and impede unauthorized access to your devices and network.
DDoS attacks count for a third of all downtime incidents, time when your network is vulnerable. Avert these cyber attacks and protect your devices against online threats and malware. We prevent more than one million cyber attacks per day. We’ll help you to take charge and secure your network.
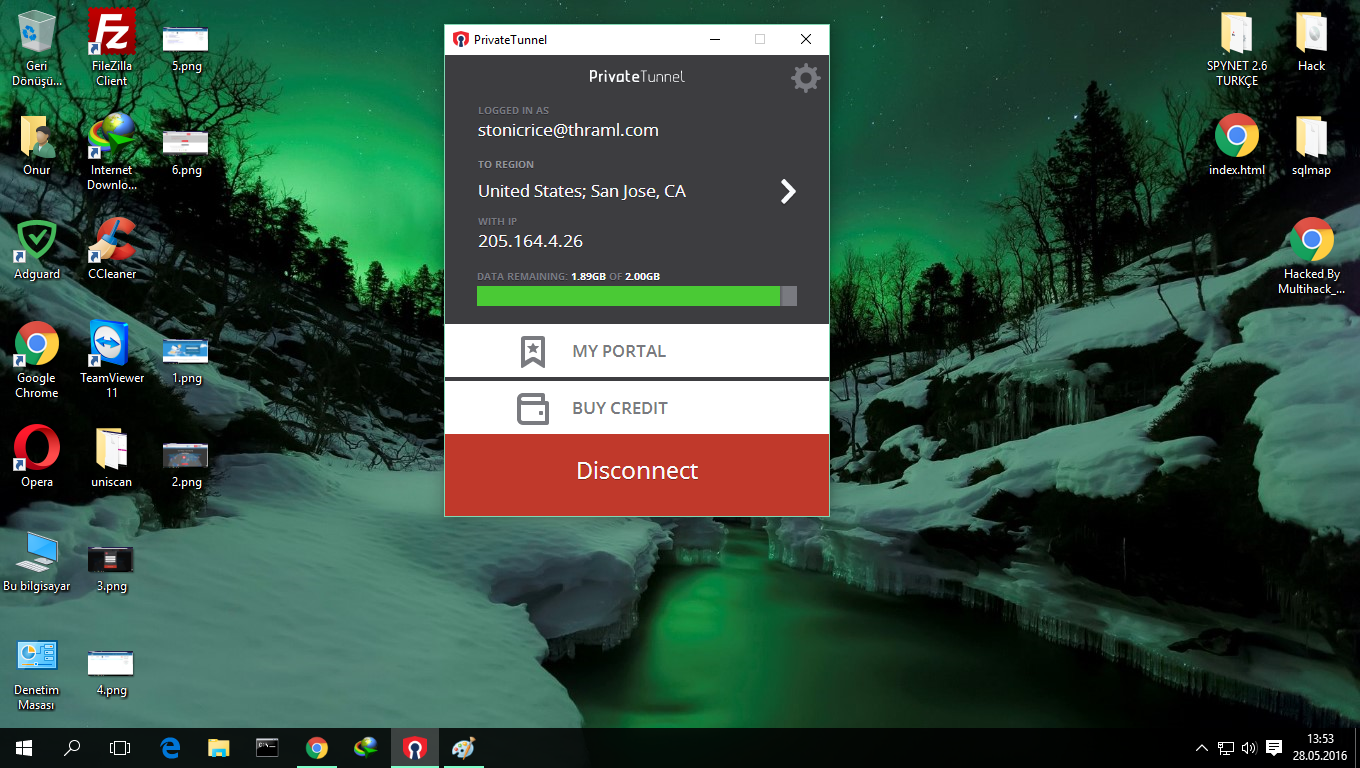
Connect your devices or network to any of our servers in the world for unrestricted access to websites and information. Be where you want to be with the confidence of knowing your identity, your data and your connections are secure and private.
VPN Pricing & Free Trials & Data | Private Tunnel
Private & Secure VPN Features | Private Tunnel
Private Tunnel - Публикации | Facebook
Private Tunnel для Андроид - скачать APK
PrivateTunnel (@ PrivateTunnel ) | Твиттер
Открыть Страницу «Private Tunnel» на Facebook
We get this question all the time. What the heck is a VPN? And why do I need one? 1. Everyone needs Protection when it comes to the public internet Digital s...
Marion Eisfeldt I have a yearly subscription that I paid for but that doesn't work and email support is extremely unhelpful.
Facebook has a new Android app called ‘Study by Facebook’ that will compensate users for letting the company see which apps/devices they use. Is this a good idea and should consumers be wary with their data privacy?
In short, email is still one of the most secure forms of online communication, although who it protects you from largely depends on how far you go to secure your own email. Here's everything you need to know about email security.
Here are some basic tips on how to encrypt your devices, because even if you’re not a huge company, you, too, are susceptible to hackers constantly searching for security flaws.
The thought of setting up a VPN may be daunting, but it's actually really simple. We laid out an easy-to-follow guide.
We answer: how to set up Private Tunnel and how to use Private tunnel.
Li-Fi is an alternative to Wi-Fi. It uses light emitting diodes (LEDs) in place of wireless transmitters to communicate between networks and devices.
It uses the same setup as Wi-Fi networks except the wireless transmitter is replaced with a Li-Fi transmitter. The transmitter sends visible light signals to receivers on users' devices.
Data security needs to be one of your main focuses as you conduct important aspects of life on the internet — and you should be well-versed in various methods of securing data.
The top method of securing data is through data encryption. If you use a lot of data, and especially use the internet over unsecured channels, then you will need strong encryption practices to make sure that you can keep all of your sensitive information safe and secure.
Check out complete beginner's guide to encryption here: http://ow.ly/od4C30oXjNC
One benefit of a VPN - it might improve your internet speed. A lot of internet service providers throttle internet speeds — usually to get you to buy a more expensive subscription.
ISPs typically throttle your speeds when it comes to downloading content or streaming material, so when you’re watching TV online you might notice it buffering more or taking longer to load. This can be frustrating, but there is a way around it that doesn’t involve caving in and spending even more money.
When you use a VPN, your activity is hidden from the ISP. If they can't see your online activity, it's much harder to reduce your speeds.
Using the browser password tool could be a good way for you to improve your password practices, but guess what? These helpful lightweight browser tools are being exploited!
Here's a quick summary of what's happening:
1. You visit a website that has ads on it. … 2. Those ads run scripts that inject invisible login forms into the background of the webpage. 3. Those login forms scoop up anything your helpful browser autofills into the form. 4. That information is used to track you from page to page and target advertising.
Creating, storing, and remembering passwords can be a pain — we won't convince you otherwise.
If you’ve managed to memorize all your passwords, then you either created a really easy password or you're using the same password for just about everything.
We get this question all the time. What is a VPN? And why do I need one anyway?
1. Yes, there are ill-intended people hacking your personal accounts and gaining access to your private information.
Consider tunneling your traffic and encrypting it with a virtual private network (VPN) like Private Tunnel.
Two-factor Authentication or 2FA is an extra layer of security, used to verify that the people requesting access to an online account are actually authorized to access it. Francis Dinha, CEO of OpenVPN, explained two-factor authentication as “a second step taken to confirm a process. It can be used to finish an online purchase, gain access to an online account or complete any transaction by verifying your identity.”
There are three common types of two-factor authentication: http://ow.ly/TobA30oXjet
The Internet is necessary to get things done these days. You can change your address, replace your license, book a flight, transfer money, order delivery, connect with friends, finish work, and watch a movie to unwind in the time you used to spend waiting in line at the DMV.
With this convenience comes responsibility, and we must be careful how we wield it. If you’re not careful, all of it could come grinding to a halt. With these five simple online security tips, you’ll be prepared for nearly anything the Internet throws your way.
While no online security method is 100% impenetrable, VPNs are one of the most effective means of maintaining online security.
There is virtually no risk for the average user, with one notable exception: when an individual chooses the wrong VPN.
Not all VPNs are created equal – using the wrong VPN can be even more dangerous than not using one at all.
‘Study By Facebook’ – a new app created by Facebook to compensate users for allowing them to see which apps or devices they use.
This isn’t the first time Facebook created an app for this use. ‘Facebook Research’ was their first app, which used the code from its free mobile VPN Onavo Protect to spy on users’ browsing activity and use that information for market research.
Francis Dinha, CEO of OpenVPN, says “Consumers need to do their research and due diligence when downloadin … g any apps or participating in online studies or research groups, whether through Facebook or another organization. For Facebook specifically, though, its decade-long history of data privacy issues should send warning signals to consumers looking into this app.”
Email is still one of the most secure forms of online communication - but it still needs to be secured.
Ultimately, the service provider has access to scan and archive your messages, whether sent via text, email, or other routes.
Desktop email readers stand out, however, because they allow you to encrypt information on your machine level so even the service provider can’t see your data.
How important are the photos, emails, and messages on your phone and how are you protecting that data? If your phone is not encrypted, that means anyone who happens across it can easily access your data.
A lot of people don’t bother with encryption because they don’t feel they have anything on their devices worth protecting — but aren’t your pictures and emails worth protecting?
Keep your personal information - personal. More on upping your privacy on your phone: http://ow.ly/fSyO30oXhja
A nurse in Sudan told us she used Private Tunnel to protect medical convoys.
Turns out the local warlords would intercept their emails to find out where the medical convoys were going. She used Private Tunnel to hide the time and date of the convoys' travels and keep them safe.
We believe that when everyone can freely access information, our society is stronger. We build products to protect users and provide them with more privacy, security, and freedom online.
A lot of people wonder, “Can my ISP track me on HTTPS websites?” And the answer is: Yes. Your Internet Service Provider (ISP) can still see what you’re up to online even when you’re on HTTPS encrypted sites.
But what about downloads? Find out: http://ow.ly/GnrJ30oXenG
The Internet of Things enables us to connect devices that weren’t traditionally connected to the Internet. One such device is our automobiles: both commercial fleets and personal vehicles are now utilizing telematics to keep vehicles connected.
As with all technology, the convenience comes at a price. Connected cars have a lot of security issues — by connecting your car’s computer to the Internet, you’re essentially creating a hackable car.
Here's how to protect yourself: http://ow.ly/sV0v30oJvGi
Did you know you don’t control the hot spot you’re connected to when surfing the web at your favorite coffee shop? Our software makes sure your traffic is encrypted no matter who operates that public Wi-Fi.
BitTorrenting is a method of downloading files using a peer-to-peer file sharing system.
While there are a few legitimate uses for BitTorrenting, the simple reality is that the primary use of BitTorrenting is to illegally download copyrighted, trademarked, and patented materials. This is called piracy, and there is no other way to slice it: it’s stealing.
Our VPN does not allow BitTorrent. Many VPN providers allow these things because they generate more revenue; however, at O … penVPN and Private Tunnel, we cannot and will not put a price tag on our integrity or your security, which will always be our absolute highest priority.
Cybersecurity workers are in-demand. There are more jobs available than individuals looking. NIST stated that the number of current employed cybersecurity workers compared to job openings is two-to-three. This shortage is dangerous, because it puts our digital infrastructure and privacy at risk.
Get trained! The top five specific cybersecurity jobs in demand are cybersecurity engineer, cybersecurity analyst, cybersecurity manager/administrator, cyberse … curity consultant, and penetration and vulnerability tester.
Электронный адрес или номер телефона
Porno Double Penetration
Home Homemade Amateur
Hard Sex Metacafe
Forced Penetration
Overwatch Levels