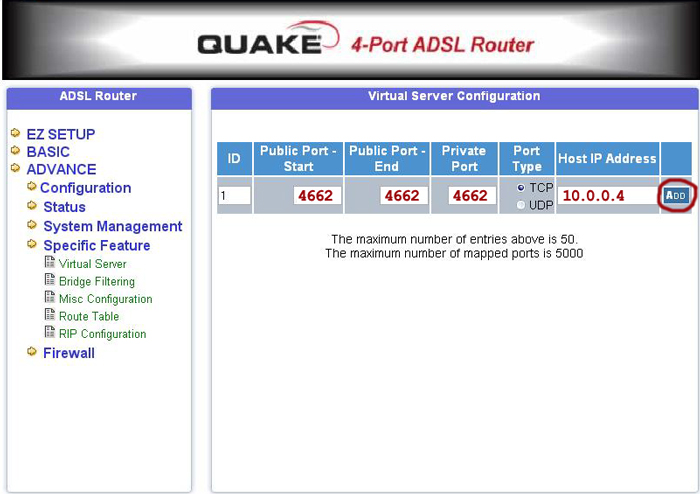
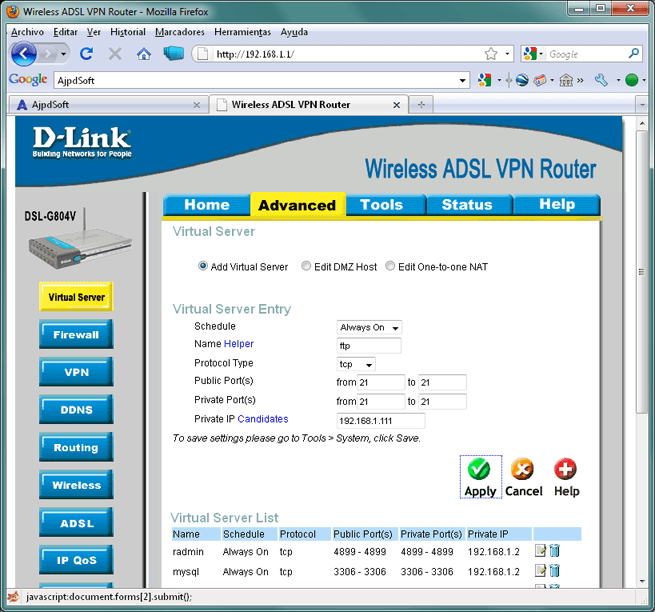
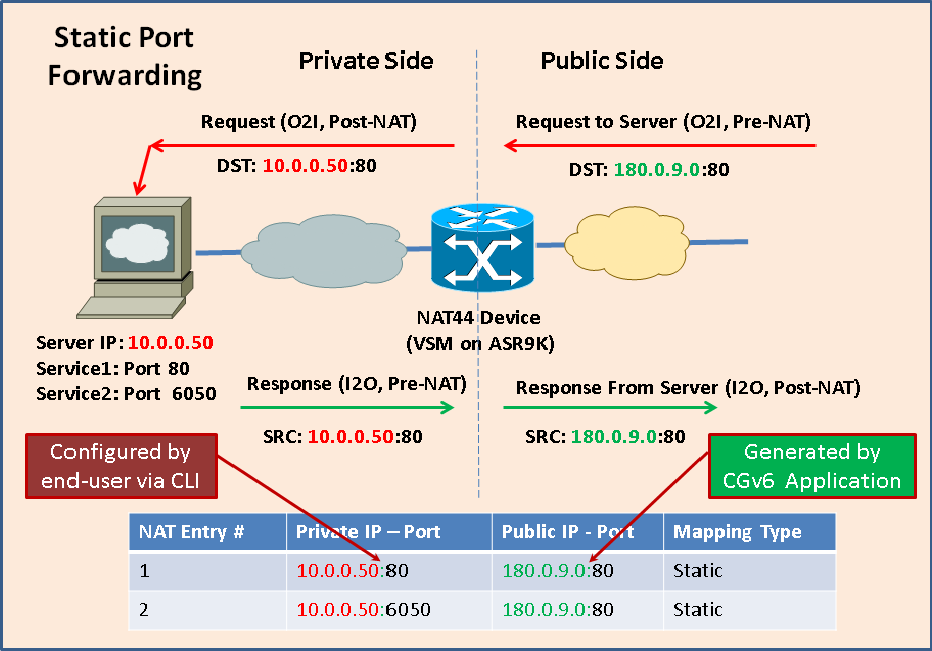
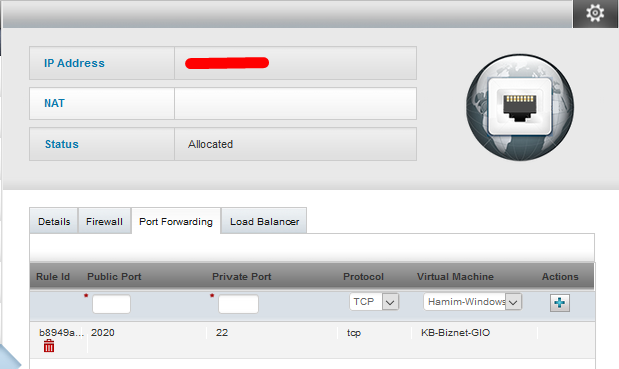
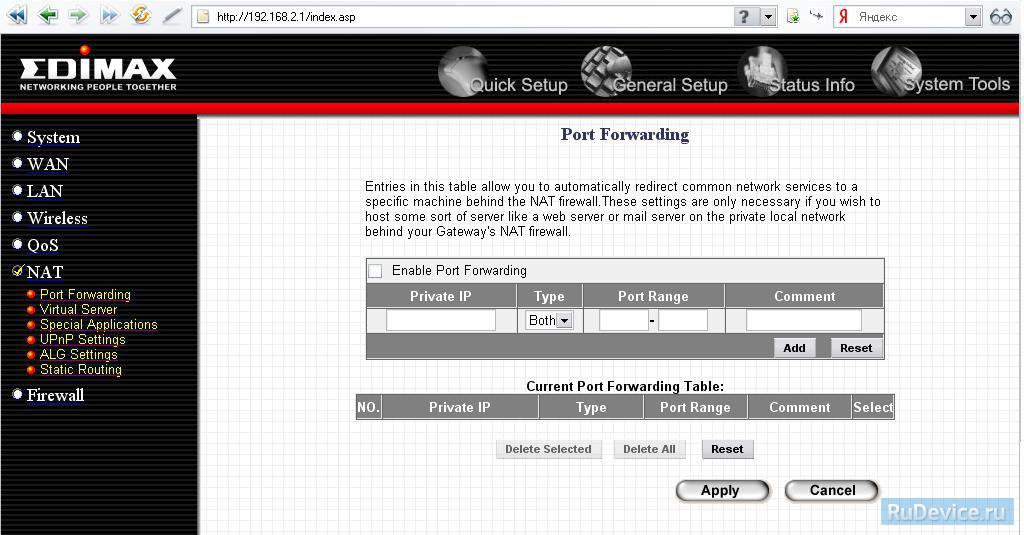
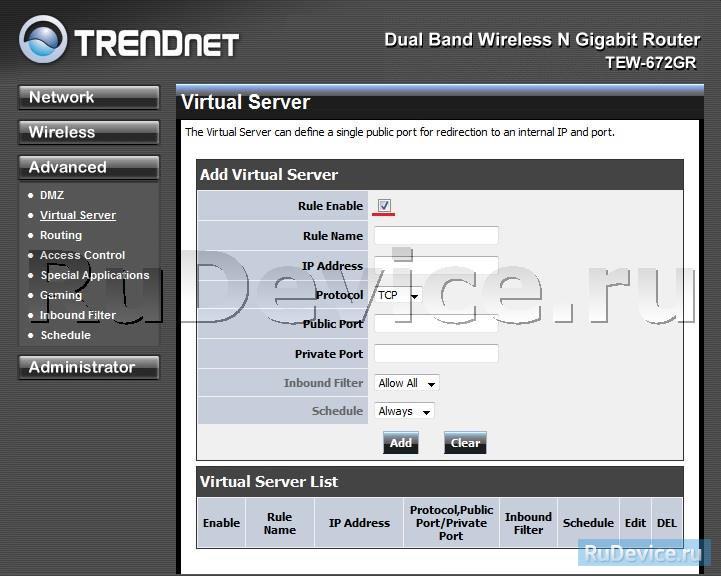
Private Port

🛑 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
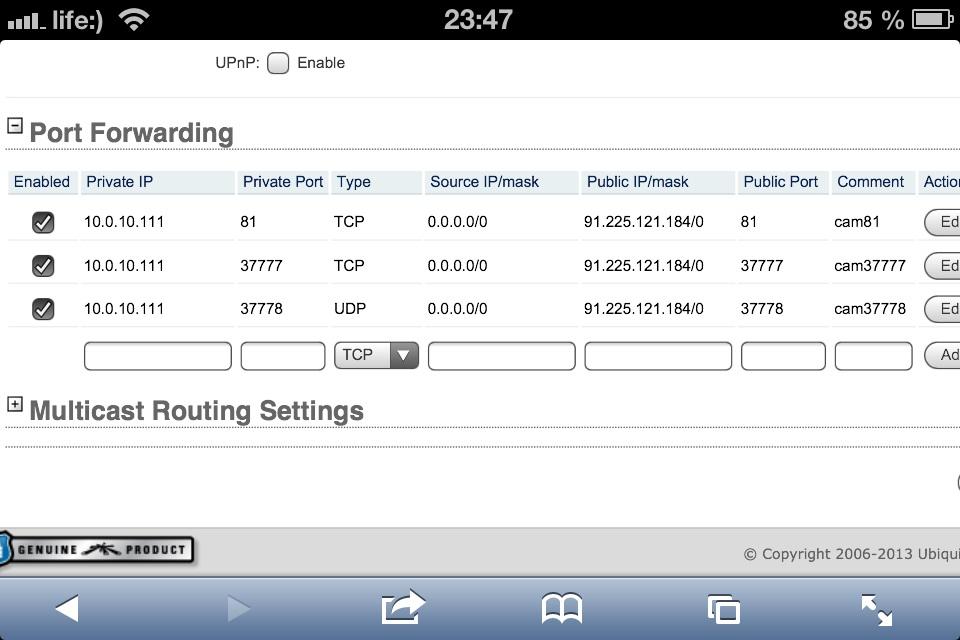
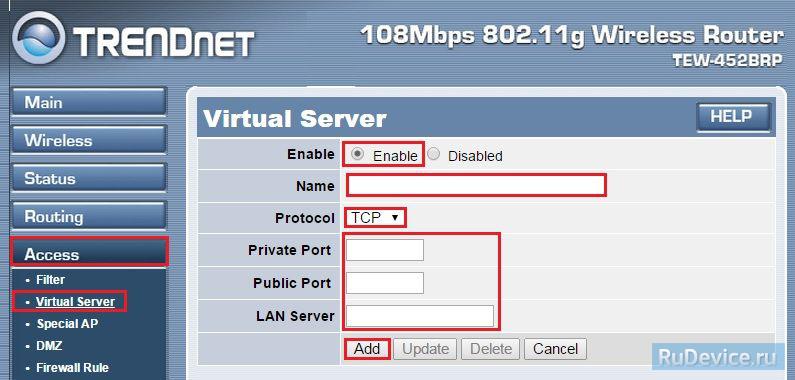
Private Port
From Wikipedia, the free encyclopedia
Private VLAN , also known as port isolation , is a technique in computer networking where a VLAN contains switch ports that are restricted such that they can only communicate with a given "uplink". The restricted ports are called "private ports". Each private VLAN typically contains many private ports, and a single uplink. The uplink will typically be a port (or link aggregation group) connected to a router , firewall , server , provider network, or similar central resource.
This concept was primarily introduced as the number of network segregation (number of vlans) in a Network switch are generally restricted to a specific number and all the resources could be used up in highly scaled scenarios. Hence, there was a requirement to create multiple network segregation with minimum resources.
The switch forwards all frames received from a private port to the uplink port, regardless of VLAN ID or destination MAC address . Frames received from an uplink port are forwarded in the normal way (i.e. to the port hosting the destination MAC address, or to all ports of the VLAN for broadcast frames or for unknown destination MAC addresses). As a result, direct peer-to-peer traffic between peers through the switch is blocked, and any such communication must go through the uplink. While private VLANs provide isolation between peers at the data link layer , communication at higher layers may still be possible depending on further network configuration.
A typical application for a private VLAN is a hotel or Ethernet to the home network where each room or apartment has a port for Internet access . Similar port isolation is used in Ethernet-based ADSL DSLAMs . Allowing direct data link layer communication between customer nodes would expose the local network to various security attacks, such as ARP spoofing , as well as increasing the potential for damage due to misconfiguration.
Another application of private VLANs is to simplify IP address assignment. Ports can be isolated from each other at the data link layer (for security, performance, or other reasons), while belonging to the same IP subnet . In such a case direct communication between the IP hosts on the protected ports is only possible through the uplink connection by using MAC-Forced Forwarding or a similar Proxy ARP based solution.
Private VLAN divides a VLAN (Primary) into sub-VLANs (Secondary) while keeping existing IP subnet and layer 3 configuration. A regular VLAN is a single broadcast domain , while private VLAN partitions one broadcast domain into multiple smaller broadcast subdomains.
There are mainly two types of ports in a Private VLAN: Promiscuous port (P-Port) and Host port. Host port further divides in two types – Isolated port (I-Port) and Community port (C-port).
Example scenario: a switch with VLAN 100, converted into a Private VLAN with one P-Port, two I-Ports in Isolated VLAN 101 (Secondary) and two community VLANs 102 and 103 (Secondary), with 2 ports in each. The switch has one uplink port (trunk), connected to another switch. The diagram shows this configuration graphically.
The following table shows the traffic which can flow between all these ports.
Traffic from an Uplink port to an Isolated port will be denied if it is in the Isolated VLAN. Traffic from an Uplink port to an isolated port will be permitted if it is in the primary VLAN.
Private VLANs are used for network segregation when:
Private VLANs in hosting operation allows segregation between customers with the following benefits:
An Isolated VLAN can be used to segregate VDI desktops from each other, allowing filtering and inspection of desktop to desktop communication. Using non-isolated VLANs would require a different VLAN and subnet for each VDI desktop.
On a backup network, there is no need for hosts to reach each other. Hosts should only reach their backup destination. Backup clients can be placed in one Isolated VLAN and the backup servers can be placed as promiscuous on the Primary VLAN, this will allow hosts to communicate only with the backup servers.
Private Ports in Azure Virtual Machine - Stack Overflow
Private VLAN - Wikipedia
Solved: How to change L port from public to private on... - Dell Community
VPC with public and private subnets (NAT) - Amazon Virtual Private Cloud
private ports 🎓² | Словари и энциклопедии на Академике
Products
Solutions & Services
Support
Community
Dell Community
:
Networking
:
Storage Networking
:
Connectrix
:
How to change L port from public to private on Brocade 4900b / 5.1.0a
Subscribe to RSS Feed
Mark Topic as New
Mark Topic as Read
Float this Topic for Current User
Bookmark
Subscribe
Mute
Printer Friendly Page
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
How to change L port from public to private on Brocade 4900b / 5.1.0a
All forum topics
Previous Topic
Next Topic
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
Re: How to change L port from public to private on Brocade 4900b / 5.1.0a
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
Re: How to change L port from public to private on Brocade 4900b / 5.1.0a
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
Re: How to change L port from public to private on Brocade 4900b / 5.1.0a
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
Re: How to change L port from public to private on Brocade 4900b / 5.1.0a
Mark as New
Bookmark
Subscribe
Mute
Subscribe to RSS Feed
Permalink
Email to a Friend
Report Inappropriate Content
Re: How to change L port from public to private on Brocade 4900b / 5.1.0a
About Dell
Careers
Community
Events
Partner Program
Premier
Dell Technologies
© 2020 Dell
Terms of Sales
Privacy Statement
Ads & Emails
Legal & Regulatory
Corporate Social Responsibility
Contact
Feedback
Locking the ports as G-ports sound like what your looking for this issue.
It will prevent the device logging in as a L-port.
portcfggport -> this force's the port to pass the AL verification and only negotiates as an E or F port.
You should test on one port and see if it resolves the issue/
-> portcfggport 'port index',1 --> 1 adds the lock
-> portcfggport 'port index',0 --> 0 removes the lock
If you add the lock against a port it prevents it from logging in as a L-port.
I have the same problem, can someone please help.
There is a command called portCfgLport, you can use this command to designate a port as an L_Port, and to configure its behavior. When a port is designated as an L_Port, the switch attempts to initialize that port as a fabric L_Port (FL_Port). The switch will never attempt a point-to-point (F_Port) initialization on the port. By default the L_Port will be a public L_Port. It can be configured as a private L_Port, in which case it will reject fabric login (FLOGI).
The command can be used as follows:
portcfglport [[slot/]port] locked_mode [private_mode] [duplex_mode]]
When invoked without operands, this command reports the L_Port conditions for all ports present. The following operands are supported:
slot For bladed systems only, specify the slot number of the port to be configured, followed by a slash (/).
port Specify a port number to be configured, relative to its slot for bladed systems. Use switchShow to display a list of valid ports. This operand is optional; if omitted, this command displays the L_Port conditions for all ports.
locked_mode Specify 1 to configure the specified port as a locked L_Port. Specify 0 to remove the locked L_Port configuration from the port (default). This operand is required if port is specified.
private_mode Specify 1 to configure the L_Port as a private L_Port. Specify 0 to configure the L_Port as a regular public L_Port. This operand is optional; if omitted; the default value of 0 is used. Private devices are supported only on Brocade enterprise-class platforms with FC2-16 and FC2-16 blades. On all other platforms, option 1 is blocked.
duplex_mode Specify 2 to configure the specified port as a full-duplex L_Port with fairness. Specify 0 to configure the L_Port as a full-duplex L_Port. This operand is optional; if omitted, the default value of 0 is used.
I hope this is what you are looking for.
Unfortunately, thats not what I am looking for and I guess , I was not very clear on my requirement.
I have got Brocade switches in my environment and all the ports have been configured to accept the E_Port/L_Port/F_Port. Now my problem is that , lot of my solaris servers when rebooted come up and the HBA's are logged in as L_Port which is a loop , so they loose their reduandancy as one is still logged in as F_Port. I know there is settings on the HBA level which we can use and make sure the HBA can log in only as F_Port but somehow, the system guys don't wana do that and I am fed up enabling and disabling the ports or do the port configuration per port which will take me days for all the ports.
Is there a way, i can issue a command on the switch which will by default make sure that i don't have anything logged in as L_Port ?
Locking the ports as G-ports sound like what your looking for this issue.
It will prevent the device logging in as a L-port.
portcfggport -> this force's the port to pass the AL verification and only negotiates as an E or F port.
You should test on one port and see if it resolves the issue/
-> portcfggport 'port index',1 --> 1 adds the lock
-> portcfggport 'port index',0 --> 0 removes the lock
If you add the lock against a port it prevents it from logging in as a L-port.
Granny Girls
Busty Private
Www Youporn Com Video
Outdoor Unit
Young Girls Naturists Nudists
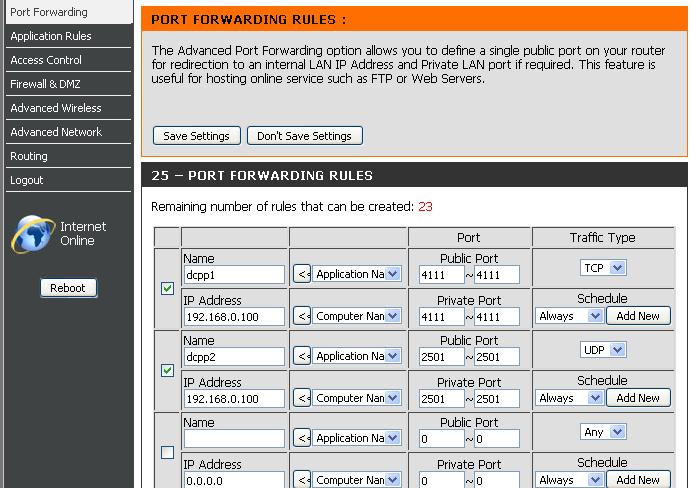
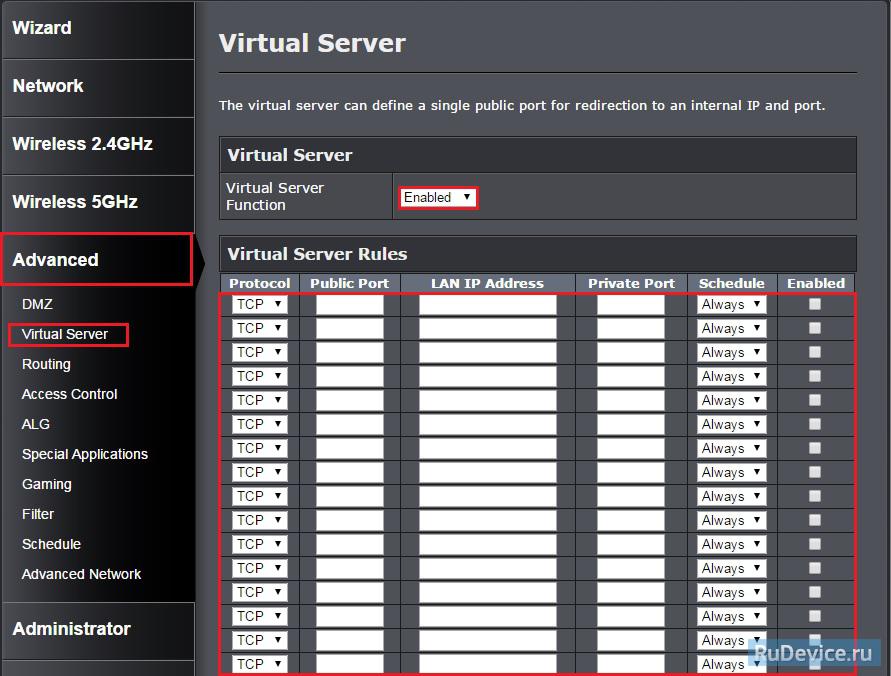
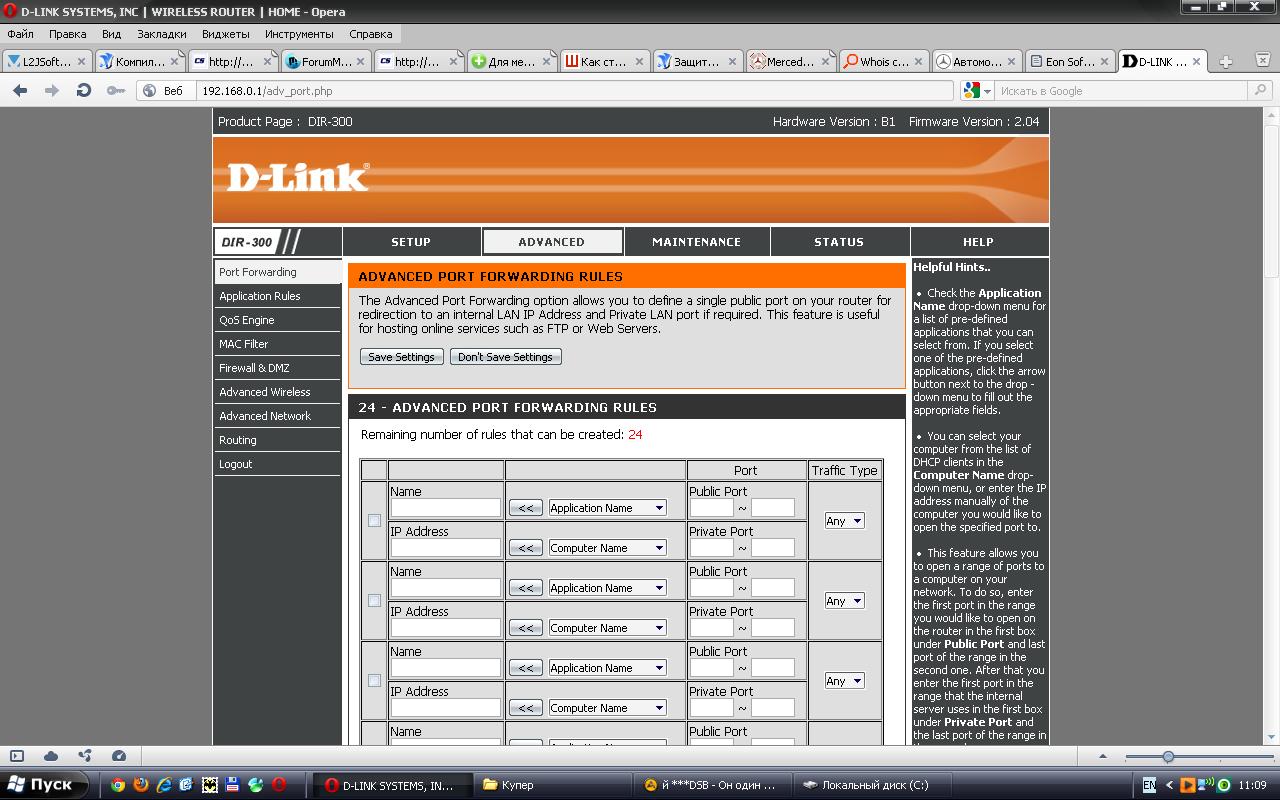

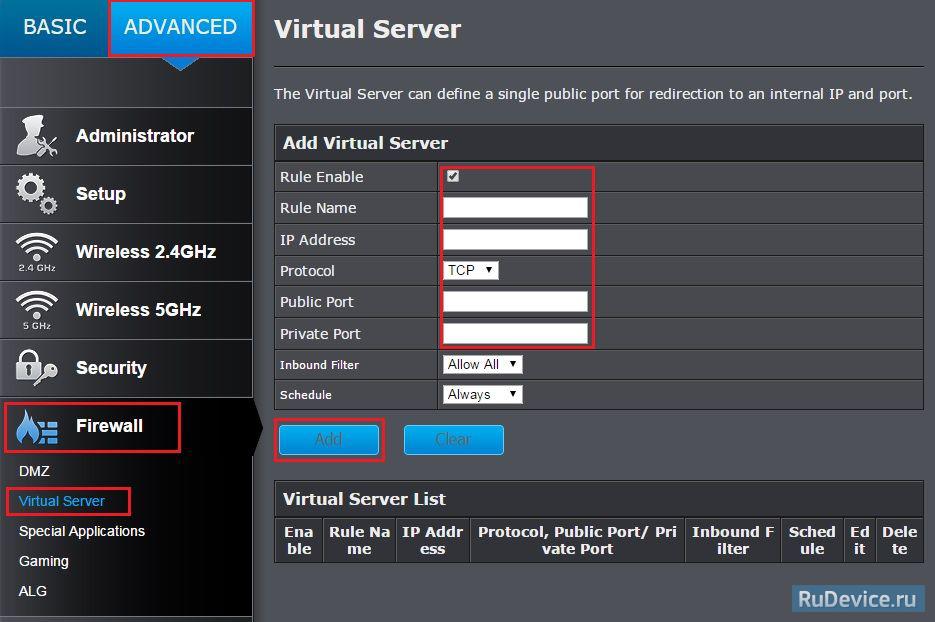






 f_auto/p/b5151690-9b2e-11e6-bdd1-00163ec9f5fa/1785686845/megaping-screenshot.jpg" width="550" alt="Private Port" title="Private Port">
f_auto/p/b5151690-9b2e-11e6-bdd1-00163ec9f5fa/1785686845/megaping-screenshot.jpg" width="550" alt="Private Port" title="Private Port">