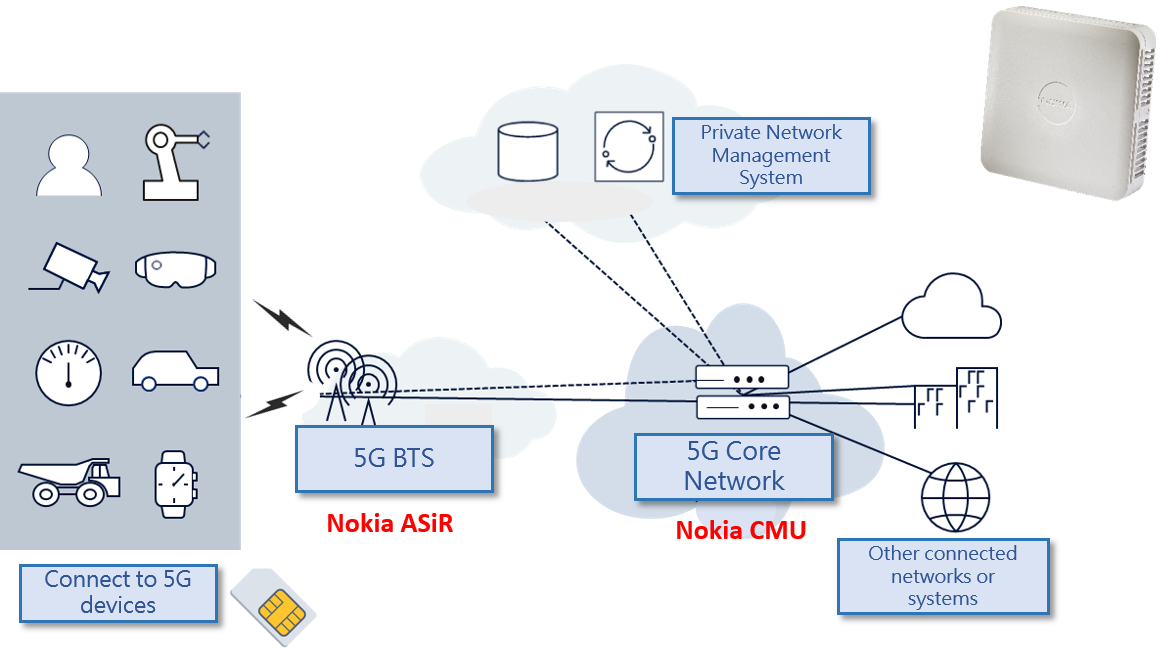
Private Network 5g Implementation

💣 👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
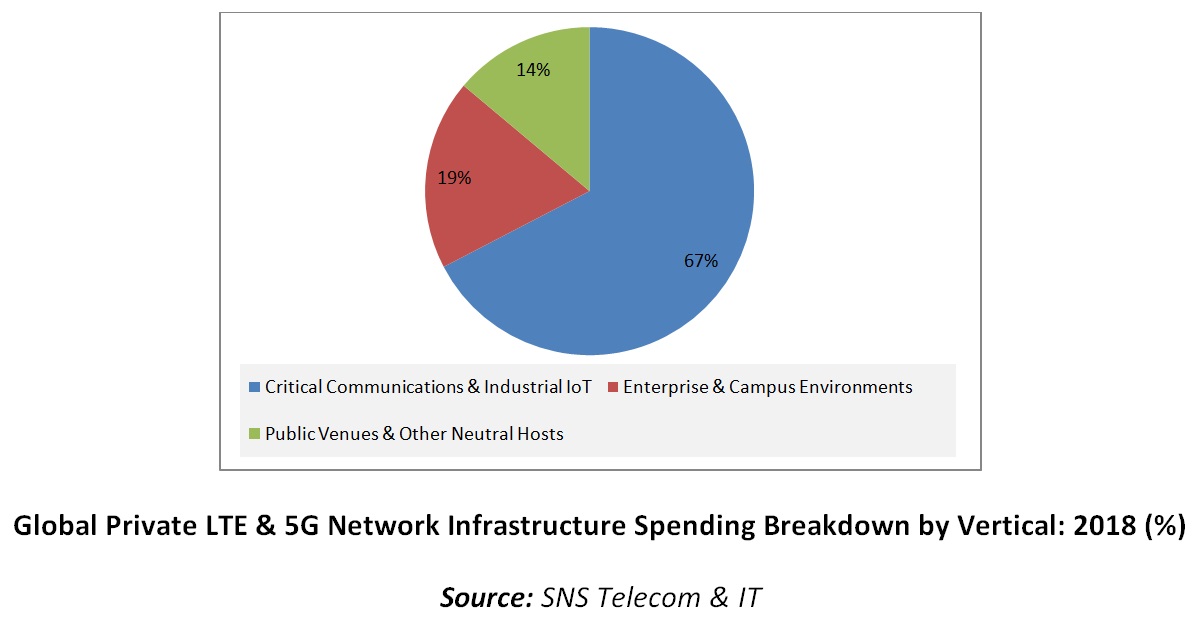
7 Deployment Scenarios of Private 5G Networks
October 21, 2019 | By Harrison J. Son (son@netmanias.com)
In this blog, we will analyze how to build a Private 5G network.
Private 5G network can be implemented in two ways.
1) Isolated 5G LAN built by enterprise (Local 5G Frequency, Full Private, No-Sharing)
2) Isolated 5G LAN built by mobile operator (Licensed Frequency, Full Private, No-Sharing)
3) RAN sharing between private network and public network
4) RAN and Control Plane Sharing between private and public network
5) RAN and Core Sharing (End-to-End Network Slicing) between private and public network
6) N3 LBO (Local Breakout)
7) F1 LBO (Local Breakout)
1) Isolated 5G LAN built by the enterprises (Local 5G Frequency, Full Private, No-Sharing)
Enterprise deploys 5G Network Full Set (gNB, UPF, 5GC CP, UDM, MEC) within its premise(site/building). The 5G frequency in the enterprise is Local 5G frequency, not mobile operators' Licensed frequency. This is a constructable architecture in the case of countries where this private frequency is allocated by government(At present, advanced countries such as Japan, Germany and the United States are possible).
Who builds: In this case, usually enterprises build their own private 5G networks, but depending on the government policy of each country, third parties, including mobile network operators, may build private 5G networks for enterprises.
Enterprises can build their own 5G LAN using local 5G frequency, freeing them from the traditional wired LAN and the wireless LAN's annoyance (LAN cable wiring work of wired LAN, short distance, security concern and network stability of wireless LAN). In addition, the ultra-low latency and ultra-connectivity capabilities of 5G technology enable the creation of new enterprise applications or optimization of existing applications.
Pros: As there are independent 5G network full sets in the enterprise on premise,
2) Isolated 5G LAN built by Mobile Operators (Licensed 5G Frequency, Full Private, No-Sharing)
The private 5G network architecture is the same as 1). The only difference with 1) is that Mobile operators build and operate 5G LAN in the enterprise with their own licensed 5G Frequency.
3) RAN sharing between private network and public network
UPF, 5GC CP, UDM, and MEC are deployed in the enterprise and physically separated from the public network.
Only 5G base stations (gNBs) located within the enterprise are shared between private and public network (RAN Sharing).
Data traffic (■) of the devices belonging to the private slice (private network) is delivered to the private UPF in the enterprise, data traffic (■) of the devices belonging to the public slice (public network) is delivered to the UPF in the mobile operator's edge cloud. In other words, private network traffic such as in-house device control data, in-house video data, etc. stays in the enterprise only, and public network service traffic such as voice and Internet are transferred to the mobile operator's network. Although the base stations are not physically but logically separated, it is almost difficult to collect the data information in the private network at the RAN level, so the security of private network data traffic in the enterprise is also confirmed.
Private and dedicated 5GC CP and UDM are built in the enterprise, so subscription information and operation information of private network devices in the enterprise are stored and managed in-house so that they do not leak outside the enterprise.
UPF and MEC are located in the enterprise, providing ultra low delay communication between device-gNB-UPF-MEC, making it suitable for companies using URLLC applications such as autonomous driving and real-time robot / drone control.
4) RAN and Control Plane Sharing between private and public network
Private and dedicated UPF, MEC are built in enterprise. 5G base stations (gNBs) in enterprise and 5GC CPs, UDMs in mobile operator's edge cloud are shared between private and public networks (RAN and Control Plane Sharing). The gNB, 5GC CP, and UDM are logically separated between the private network and the public network, and the UPF and MEC are physically separated.
Data traffic (■) of the devices belonging to the private slice (private network) is delivered to the private UPF in the enterprise, data traffic (■) of the devices belonging to the public slice (public network) is delivered to the UPF on the edge of the mobile operator. In other words, private network traffic such as in-house device control data, in-house video data, etc. stays in the enterprise only, and public network service traffic such as voice and Internet are transferred to the mobile operator's network. Like 3) RAN Sharing, the security of data traffic within the enterprise is also clear.
Control plane functions (authentication, mobility, etc.) for private network devices and public network devices are performed by 5GC CP and UDM in mobile operator's networks.
That is, the private network devices, gNB and UPF in the enterprise are interworked with and managed by the mobile operator's network (via N2, N4 interface). It may be a concern for that the operation information and subscription information of the private network devices are stored in the mobile operator's server rather than in-house.
Since UPF and MEC are located in the enterprise, it provides ultra low delay communication between device-gNB-UPF-MEC and is suitable for companies using URLLC applications such as autonomous driving and real-time robot / drone control.
5) RAN and Core Sharing (End-to-End Network Slicing) between private and public network
This is the case when only gNB is deployed inside the enterprise and UPF and MEC exist only in the mobile operator's edge cloud. Private network and public network share "logically separated 5G RAN and Core" (gNB, UPF, 5GC, MEC, UDM) (End-to-End Network Slicing).
Unlike 3, 4 where UPF and MEC are located in the enterprise, in this case there is only gNB in the enterprise. Therefore, there is no local traffic path between the private 5G devices and the intranet (LAN) devices such as PCs or local intranet servers, so the traffic must go up to the UPF in the edge cloud of the operator and then come back inside the enterprise through a leased line to communicate with the LAN devices.
In addition, MEC, which provides 5G application services to 5G devices in the enterprise, is located in the edge cloud of the mobile operator far from the devices.
In this architecture, network latency (RTT) can be a major problem, depending on the distance between the enterprise (5G devices) and the operator's edge cloud (UPF, MEC).
Since the traffic of private network devices is transferred from the enterprise to the mobile operator's network, there is a concern about data traffic security. While mobile operator will slice UPF and MEC on its edge cloud to keep our private network traffic separate from public and other private network traffic, timid CEOs are concerned about the fact that e.g., their internal CCTV video traffics are leaking outside their enterprise.
As with case 4, it is disturbing for an enterprise to have operational and subscription information stored on a mobile operator's network rather than on the company's private network.
This architecture costs the least to build a private 5G network for mobile operators compared to case 2, 3 and 4 that require the deployment of UPF and/or 5GC CP inside the enterprise.
However, the enterprise has concerns in aspect of security (data traffic generated from private network terminals, subscription information and operational information of private network devices) and network delay (between private 5G devices and MEC application servers, and between private 5G devices and intranet/LAN devices).
6) N3 LBO (Local Breakout): Case of SK Telecom in Korea
As shown in above (a), gNB is deployed in the enterprise as in case 5. N3 GTP Tunnel is created between gNB and UPF when a device is connected, whether CCTV camera or smartphone. These devices are all public network devices.
As shown in above (b), the enterprise introduces MEC Data Plane (non-3GPP equipment, ETSI MEC) and MEC Applications (MEC Applications). The Mobile Edge Platform (MEP) in the mobile operator's Orchestrator sends a traffic rule to the MEC DP via the Mp2 interface (If Destination IP address is a Local Network - private 5G devices, local wired LAN devices, local MEC application servers - then Local Breakout!).
The MEC DP looks at the destination IP addresses of the packets belonging to all GTP Tunnels coming up from the gNB (GTP Decap) and routes the User IP packet to the internal private network if it is local traffic.
Although this method is not standard method of 3GPP, it will be possible to separate private network traffic from public traffic.
(This is the ETSI MEC's Bump in the Wire method).
Compared to case 5, private network traffic is not transferred to the mobile operator's network, so the security of private network data traffic is also as clear as case 3 and 4.
Unlike case 3 and 4, the cost of building a private 5G network is greatly reduced (UPF is the most expensive equipment among the 5G standard equipments) by adding low-cost MEC DP (actually, SDN/P4 switch) without having to bring expensive UPFs into the enterprise.
In addition, because the MEC also exists in the enterprise and handles the traffic that MEC DP breakouts, it will be able to provide ultra-low delay application services.
However, since MEC DP is not 3GPP UPF, MEC DP cannot perform mobility management and charging function for private network devices.
(Of course, MEC DP can implement some of these functions since the operator can make a proprietary specification that implements these capabilities)
As with case 4 and 5, it is disturbing for an enterprise to have operational and subscription information stored on a mobile operator's network rather than on the company's private network.
7) F1 LBO (Local Breakout): Case of KT in Korea
The same as in case 6, but the difference is that only the RU/DU in the enterprise is deployed and the CU is placed in the mobile network's edge cloud, and that private network traffic is locally-breakouted from the F1 interface, not from the N3 interface.
There is always a plurality of ideas in every choice situation in any field. We want to have the prettiest and most coveted option first.
But which option to choose at the final stage of selection is "What do I need?" and "How much money do I have?"
Similarly, the architectures of the Private 5G network described above have their respective advantages and disadvantages, and one architecture is not optimal for all situations. Each enterprise can choose an architecture that is optimized for them based on their requirements and implementation/operating budget they have.
Rajarshi Pathak 2019-10-22 15:17:43
Thanks a lot Harrison for sharing this very useful article. It's always a pleasure to learn from your write-ups. From Enterprise's control and security perspectives, Option 3 looks good but it's expensive.
For cost savings perspective, Option 5 is reasonable but it's the least secured wrt traffic routing as well as subscription info storage.
In Option 6 though enterprise traffic doesn't leave the private network but subscription information gets stored in the public network and also we need to maintain MEC DP equipment & Orchestrator.
As you mentioned, there is no "one size, fits all" approach. Private network deployments will be based on mutual trust and partnerships between Enterprises and Operators along with the targeted service offerings. Together they can also become niche Service Providers for offering URLLC & mMTC services for public and private networks in the dynamic 5G world.
SKT case seems good with well balance between Security and Cost
Thanks a lot. Great document. Any idea which vendor MEC DP deployed mention in option 7?
Very nice. I think at the high level, the isolated models can provide service independent of the availability of connectivity between the two sides. That and great indoor coverage will probably be important factors. The shared scenarios to me are still evolving, probably most useful for smartphones....
This is an excellent summary of all NPN scenarios but not sure I understand how scenario 6&7 works. The data stored on the MEC within enterprise is ciphered using the mobile network keys, so nobody can inspect it directly? Does this mean that nobody else except the user that stored the information could decipher it because the keys are different? Thanks in advance for clarification.
Thank a lot. It is a useful document and It helps a lot to me.
Thank you so much for sharing your knowledge.
May i know which is the Application you illustrated these paragraph ?
Could you estimate the total number of cells neede dto operate a small, medium and large industrial campus? can you estimate the mixture (small cells, micro and macro)?
What is required and missing to operate private network by yourself? what wouls make inrustry operators to chose to own a provate netwrok?
Mohamed Abdirahman Abdullahi 2020-08-22 17:18:58
very importand and useful information
Thank a lot. Very informative article.
Thank you for taking the time to explain the options in great detail!
Page 16-17 of Altran's Whitepaper, "The Adoption of Private Networks For Enterprises" steals Netmanias' Content, "7 Deployment Scenarios of Private 5G Networks" without any permission.
We recommend that Altran must delete Page 16-17 from Atran's white paper.
References
- Atran White Paper, adoption-private-networks-enterprises.pdf (2020.11.24)
- https://www.altran.com/uk/en/insight/adoption-of-private-networks/
- Neymanias' Articles: https://www.netmanias.com/en/?m=view&id=blog&no=14500
- Netmanias' PDF file: Netmanias.2019.10.21.Private 5G Deployment Scenarios (en).pdf
Address: 201, Hanho Building 33, Nonhyeon-ro 64-gil, Gangnam-gu, Seoul, 06228, Rep. of KOREA
Syed Kashif Zahid 2021-05-21 01:23:24
Excelllent elaboration. Thanks for putting in the hard work!!
Ananth Kollipara 2021-05-23 03:05:03
Thanks a lot for compiling and presenting details on the 5G deployments. Are there any new developments or update in specs on the 5G MEC DP? Please share the same.
Thank you for visiting Netmanias! Please leave your comment if you have a question or suggestion.
HQ: 201, Hanho Building 33, Nonhyeon-ro 64-gil, Gangnam-gu, Seoul, 06228, Rep. of KOREA
Netmanias USA: 5214 36th Ave. NE Seattle, WA 98105 USA
Netmanias was founded in year 2002, and provides in-depth analysis and overview of 4G & 5G mobile,
IoT, SDN/NFV, Gigabit Internet and video streaming technologies as well as trends in the evolution
of Korean operators’ networks and services
Copyright ⓒ 2002-2018 NMC Consulting Group. All rights reserved.
Please enter your registered comment password.
Telecoms.com is part of the Informa Tech Division of Informa PLC
This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. Informa PLC’s registered office is 5 Howick Place, London SW1P 1WG. Registered in England and Wales. Number 3099067.
Private 5G networks: inside the operator opportunity
Telecoms.com periodically invites expert third parties to share their views on the industry’s most pressing issues. In this piece Arnab Das, VP, Global Service Line, Advanced Networking & IoT, Capgemini Engineering, explores the possibilities presented to operators by private networks.
The global private 4G/5G infrastructure market will hit close to $6 billion by 2024, IDC predicts. Is that actually good news or bad news for mobile operators?
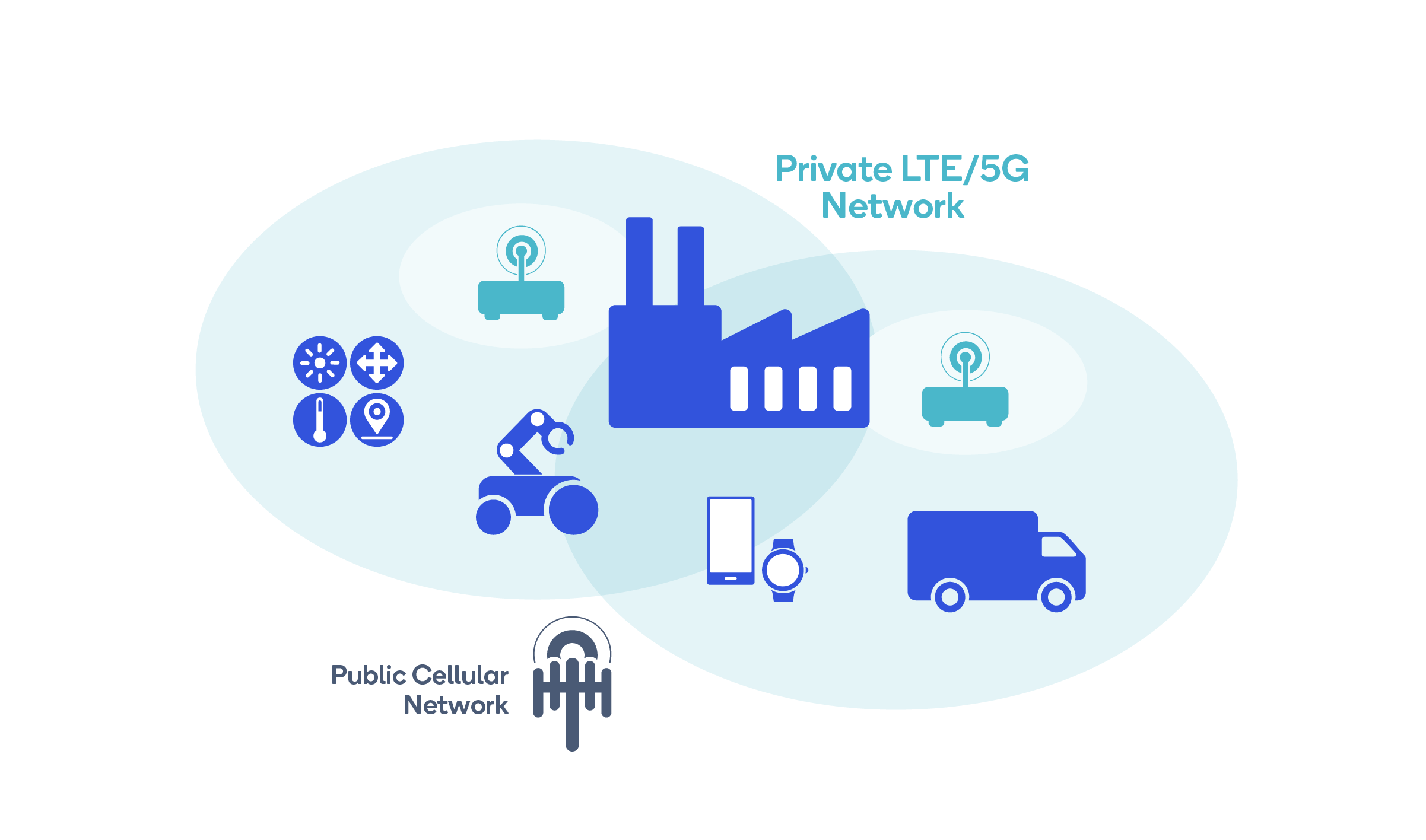
It’s easy to view the rise of private networks as a negative for mobile operators. After all, the more that factory owners, oil/gas companies, electric utilities and other businesses build their own networks, the less they’ll spend with mobile operators. Right? So although many of those companies will still need public networks for wide-area connectivity, the bulk of their local traffic — such as the 1 million IoT devices per square kilometer that mMTC enables — is lost business for mobile operators.
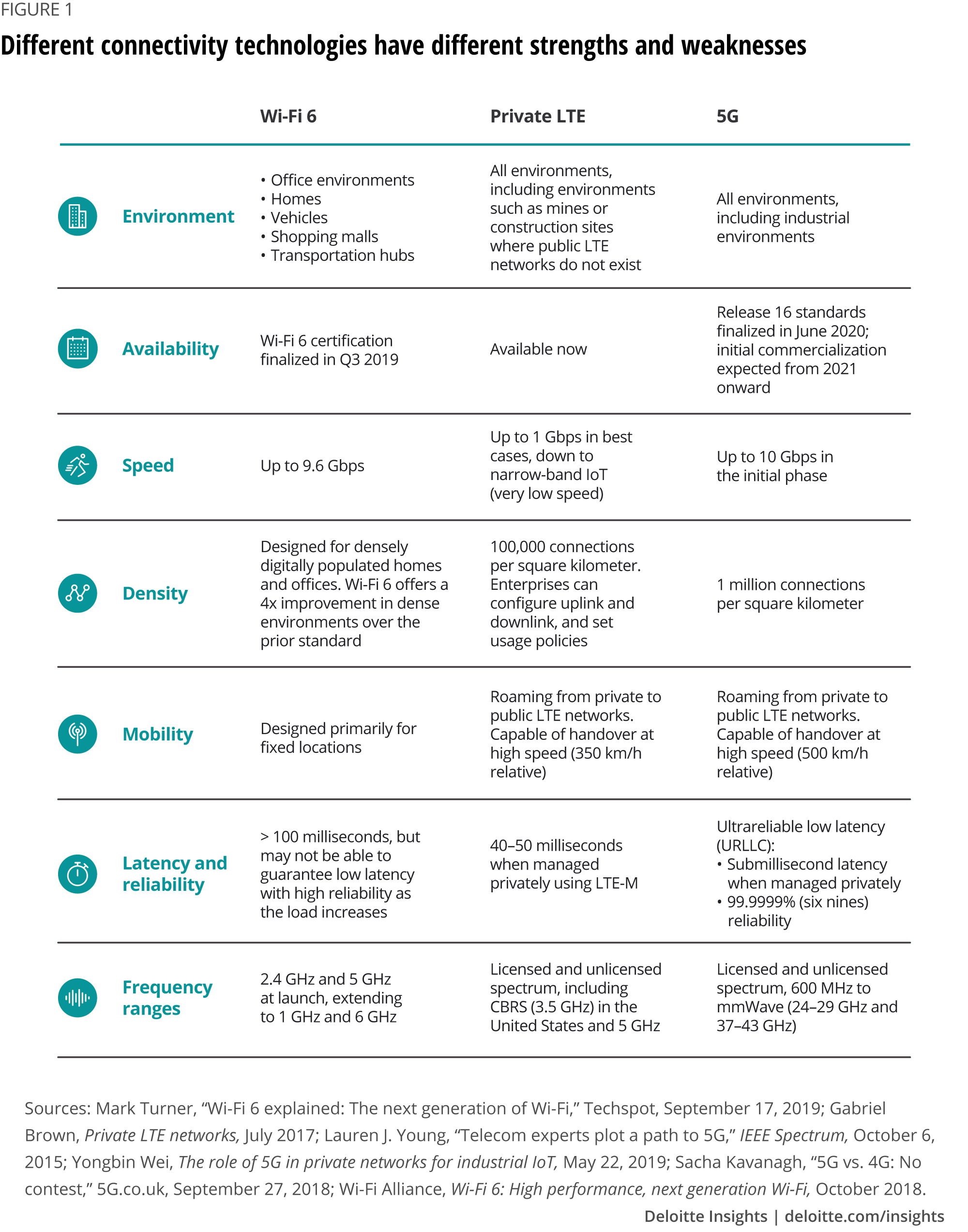
There’s a silver lining to what initially looks like a very dark cloud. For starters, a cellular network is orders of magnitude more complex than a Wi-Fi LAN, which typically is the only type of wireless network that most enterprises have experience running. Designing, deploying and operating a cellular network requires an enormous amount of expertise — especially if it uses 5G, which has a particularly steep learning curve simply because it’s a new technology. Many enterprises will choose 5G for future proofing and capabilities such as URLLC.
This complexity and unfamiliarity highlights opportunities for mobile operators. With private 4G, enterprises often outsourced design and deployment to a specialist. In some cases, that was an infrastructure vendor or systems integrator. In others, it was a mobile operator. This outsourcing model will continue with 5G.
Some mobile operators offer private networks as a service, and engage system integration specialists for geographic or vertical expertise. In this model, the operator provides the spectrum and outsources the managed services.
Regardless of whether a mobile operator, infrastructure vendor or systems integrator is doing the work, all of them need an implementation solution that enables the new network to adapt to the enterprise, without having to be re-engineered completely. This can be achieved with software-based platforms that can plug and play on Layer 1, depending on the 5G band and the type of device connected to the use case. Such solutions can address the business challenge and deliver flexibility for global enterprises which may require product customization.
Some enterprises will have unique requirements, such as edge computing and security, that will affect implementation choices. One example is whether to deploy all the equipment on site versus using a shared RAN with a common core, which can have security and access challenges.
Most private network deployments can fit into two categories: physically isolated or sharing the mobile operator’s public 5G network resources. In both cases, an enterprise can deploy a complete 5G network with gNodeB (gNB), User Plane Function (UPF), 5G Core Control Plane (5GC CP), Unified Data Manager (UDM) and Mobile Edge Computing (MEC) within its premises. It also can be a constructible architecture in countries where the private network frequency is allocated by the government, as is the case in countries such as Japan, Germany and the United States. This can particularly well with network slicing.
Mobile operators can provide dedicated ‘slices’ – leveraging existing network infrastructure – to fit specific use cases. As the slices are virtualized, operators can deliver dedicated network r
Drama Erotika Filmi Brat I Sestra Incest
Cheating Best Tube
Wives Amatrice Porno Photo
Wife Double Hd
Vintage Pornostar Candy Andes Tube
Private 5G networks | Deloitte Insights
5G Private Networks - Telecom Infra Project
7 Deployment Scenarios of Private 5G Networks | NETMANIAS
Private 5G networks: inside the operator opportunity ...
Private 5G Networks - IEEE Innovation at Work
Implement Private Wireless | Nokia
5G IoT Private & Dedicated Networks for Industry 4
Private Networks in a 5G World - KNect365
Here’s why Enterprises 5G private networks are the next ...
TIP Launches 5G Private Networks Solution Group - Telecom ...
Private Network 5g Implementation