Private Link Link

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Private Link Link
Azure
Product documentation
Compute
Networking
Storage
Web
Mobile
Containers
Databases
All products
Architecture
Get started
Reference architectures
Cloud Adoption Framework for Azure
Azure Well-Architected Framework
Design patterns
Assessments
Learn Azure
Self-paced learning paths
Pluralsight
Instructor-led courses
Develop
Python
.NET
JavaScript
Java
Go
Resources
Pricing
Contact sales
Videos
Webinars
Updates
White papers
Blog
Support
More
Product documentation
Compute
Networking
Storage
Web
Mobile
Containers
Databases
All products
Architecture
Get started
Reference architectures
Cloud Adoption Framework for Azure
Azure Well-Architected Framework
Design patterns
Assessments
Learn Azure
Self-paced learning paths
Pluralsight
Instructor-led courses
Develop
Python
.NET
JavaScript
Java
Go
Resources
Pricing
Contact sales
Videos
Webinars
Updates
White papers
Blog
Support
Portal
Free account
Yes
No
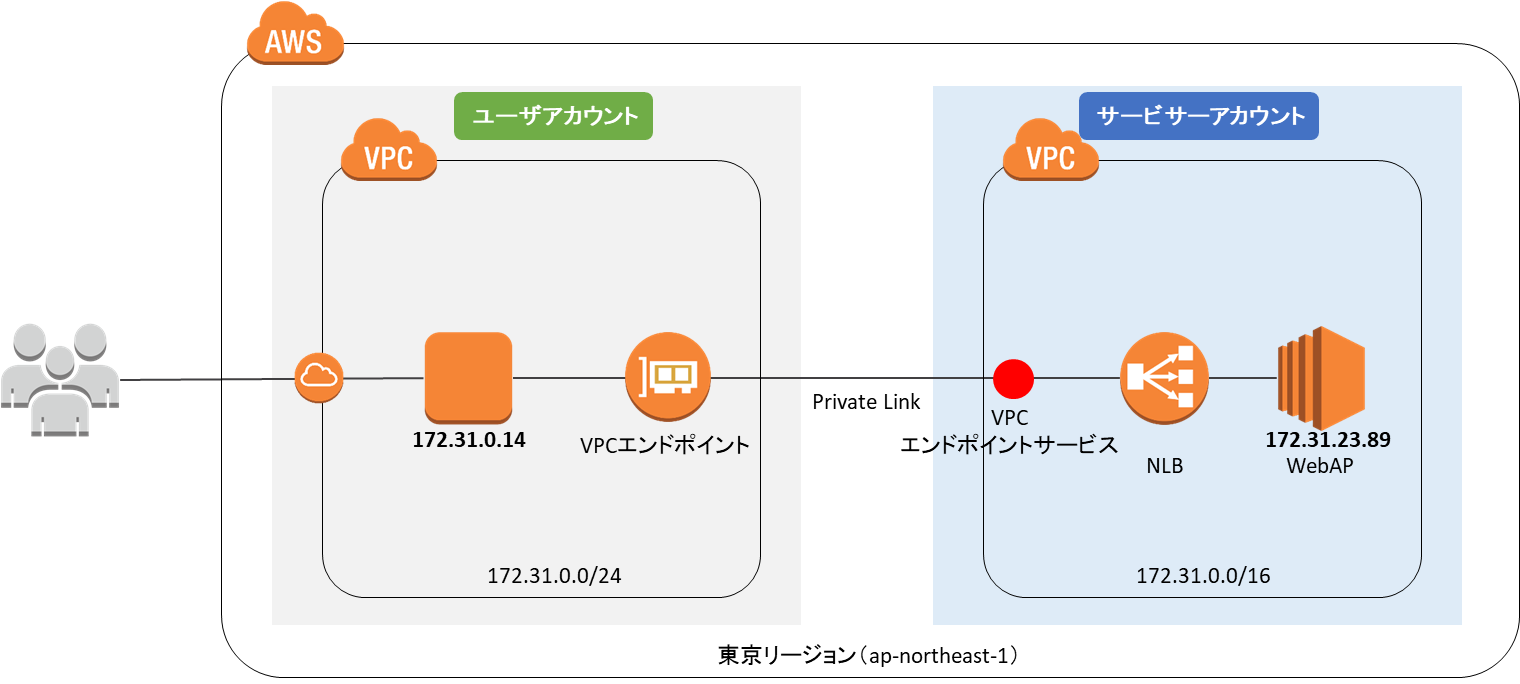
Azure Private Link service is the reference to your own service that is powered by Azure Private Link. Your service that is running behind Azure Standard Load Balancer can be enabled for Private Link access so that consumers to your service can access it privately from their own VNets. Your customers can create a private endpoint inside their VNet and map it to this service. This article explains concepts related to the service provider side.
Figure: Azure Private Link Service.
Figure: Azure Private Link service workflow.
Configure your application to run behind a standard load balancer in your virtual network. If you already have your application configured behind a standard load balancer, you can skip this step.
Create a Private Link Service referencing the load balancer above. In the load balancer selection process, choose the frontend IP configuration where you want to receive the traffic. Choose a subnet for NAT IP addresses for the Private Link Service. It is recommended to have at least eight NAT IP addresses available in the subnet. All consumer traffic will appear to originate from this pool of private IP addresses to the service provider. Choose the appropriate properties/settings for the Private Link Service.
Azure Private Link Service is only supported on Standard Load Balancer.
After you create a Private Link service, Azure will generate a globally unique named moniker called "alias" based on the name you provide for your service. You can share either the alias or resource URI of your service with your customers offline. Consumers can start a Private Link connection using the alias or the resource URI.
After a consumer initiates a connection, the service provider can accept or reject the connection request. All connection requests will be listed under the privateendpointconnections property on the Private Link service.
If the Private Link service is no longer in use, you can delete it. However, before your delete the service, ensure that there are no private endpoint connections associated with it. You can reject all connections and delete the service.
A Private Link service specifies the following properties:
Private Link service can be accessed from approved private endpoints in any public region. The private endpoint can be reached from the same virtual network, regionally peered VNets, globally peered VNets and on premises using private VPN or ExpressRoute connections.
When creating a Private Link Service, a network interface is created for the lifecycle of the resource. This interface is not manageable by the customer.
The Private Link Service must be deployed in the same region as the virtual network and the Standard Load Balancer.
A single Private Link Service can be accessed from multiple Private Endpoints belonging to different VNets, subscriptions and/or Active Directory tenants. The connection is established through a connection workflow.
Multiple Private Link services can be created on the same Standard Load Balancer using different front-end IP configurations. There are limits to the number of Private Link services you can create per Standard Load Balancer and per subscription. For details, see Azure limits .
Private Link service can have more than one NAT IP configurations linked to it. Choosing more than one NAT IP configurations can help service providers to scale. Today, service providers can assign up to eight NAT IP addresses per Private Link service. With each NAT IP address, you can assign more ports for your TCP connections and thus scale out. After you add multiple NAT IP addresses to a Private Link service, you can't delete the NAT IP addresses. This is done to ensure that active connections are not impacted while deleting the NAT IP addresses.
Alias is a globally unique name for your service. It helps you mask the customer data for your service and at the same time creates an easy-to-share name for your service. When you create a Private Link service, Azure generates an alias for your service that you can share with your customers. Your customers can use this alias to request a connection to your service.
The alias is composed of three parts: Prefix . GUID . Suffix
Complete alias: Prefix . {GUID}. region .azure.privatelinkservice
Private Link service provides you options to control the exposure of your service through "Visibility" setting. You can make the service private for consumption from different VNets you own (Azure RBAC permissions only), restrict the exposure to a limited set of subscriptions that you trust, or make it public so that all Azure subscriptions can request connections on the Private Link service. Your visibility settings decide whether a consumer can connect to your service or not.
Consumers having exposure (controlled by visibility setting) to your Private Link service can create a private endpoint in their VNets and request a connection to your Private Link service. The private endpoint connection will be created in a "Pending" state on the Private Link service object. The service provider is responsible for acting on the connection request. You can either approve the connection, reject the connection, or delete the connection. Only connections that are approved can send traffic to the Private Link service.
The action of approving the connections can be automated by using the auto-approval property on the Private Link service. Auto-Approval is an ability for service providers to preapprove a set of subscriptions for automated access to their service. Customers will need to share their subscriptions offline for service providers to add to the auto-approval list. Auto-approval is a subset of the visibility array. Visibility controls the exposure settings whereas auto-approval controls the approval settings for your service. If a customer requests a connection from a subscription in the auto-approval list, the connection is automatically approved and the connection is established. Service providers don’t need to manually approve the request anymore. On the other hand, if a customer requests a connection from a subscription in the visibility array and not in the auto-approval array, the request will reach the service provider but the service provider has to manually approve the connections.
When using private link service, the source IP address of the packets coming from private endpoint is network address translated (NAT) on the service provider side using the NAT IP allocated from provider's virtual network. Hence the applications receive the allocated NAT IP address instead of actual source IP address of the service consumers. If your application needs actual source IP address from consumer side, you can enable Proxy protocol on your service and retrieve the information from the proxy protocol header. In addition to source IP address, proxy protocol header also carries the LinkID of the private endpoint. Combination of source IP address and LinkID can help service providers uniquely identify their consumers. For more information on Proxy Protocol, visit here .
This information is encoded using a custom Type-Length-Value (TLV) vector as follows:
Service provider is responsible for making sure that the service behind the standard load balancer is configured to parse the proxy protocol header as per the specification when proxy protocol is enabled on private link service. The request will fail if proxy protocol setting is enabled on private link service but service provider's service is not configured to parse the header. Similarly, the request will fail if the service provider's service is expecting a proxy protocol header while the setting is not enabled on the private link service. Once proxy protocol setting is enabled, proxy protocol header will also be included in HTTP/TCP health probes from host to the backend virtual machines, even though there will be no client information in the header.
The following are the known limitations when using the Private Link service:
Provisioning State (provisioningState)
A read-only property that lists the current provisioning state for Private Link service. Applicable provisioning states are: "Deleting; Failed; Succeeded; Updating". When the provisioning state is "Succeeded", you have successfully provisioned your Private Link service.
Alias is a globally unique read-only string for your service. It helps you mask the customer data for your service and at the same time creates an easy-to-share name for your service. When you create a Private Link service, Azure generates the alias for your service that you can share with your customers. Your customers can use this alias to request a connection to your service.
Visibility is the property that controls the exposure settings for your Private Link service. Service providers can choose to limit the exposure to their service to subscriptions with Azure role-based access control (Azure RBAC) permissions, a restricted set of subscriptions, or all Azure subscriptions.
Auto-approval controls the automated access to the Private Link service. The subscriptions specified in the auto-approval list are approved automatically when a connection is requested from private endpoints in those subscriptions.
Load Balancer Frontend IP Configuration (loadBalancerFrontendIpConfigurations)
Private Link service is tied to the frontend IP address of a Standard Load Balancer. All traffic destined for the service will reach the frontend of the SLB. You can configure SLB rules to direct this traffic to appropriate backend pools where your applications are running. Load balancer frontend IP configurations are different than NAT IP configurations.
NAT IP Configuration (ipConfigurations)
This property refers to the NAT (Network Address Translation) IP configuration for the Private Link service. The NAT IP can be chosen from any subnet in a service provider's virtual network. Private Link service performs destination side NAT-ing on the Private Link traffic. This ensures that there is no IP conflict between source (consumer side) and destination (service provider) address space. On the destination side (service provider side), the NAT IP address will show up as Source IP for all packets received by your service and destination IP for all packets sent by your service.
Private endpoint connections (privateEndpointConnections)
This property lists the private endpoints connecting to Private Link service. Multiple private endpoints can connect to the same Private Link service and the service provider can control the state for individual private endpoints.
This property lets the service provider use tcp proxy v2 to retrieve connection information about the service consumer. Service Provider is responsible for setting up receiver configs to be able to parse the proxy protocol v2 header.
PP2_SUBTYPE_AZURE_PRIVATEENDPOINT_LINKID (0x01)
UINT32 (4 bytes) representing the LINKID of the private endpoint. Encoded in little endian format.
Private Link Documentation - Quickstarts, How to guides... | Microsoft Docs
What is Azure Private Link service? | Microsoft Docs
Azure Private Link & Snowflake — Snowflake Documentation
Azure SQL network settings ( Private Link , VNET Service...) | Medium
oracle11g - Private DB Link in Oracle - Stack Overflow
Docs »
Managing Security in Snowflake »
Networking & Private Connectivity »
Azure Private Link & Snowflake
"privateLinkServiceNetworkPolicies" : "Disabled" ,
"privateEndpointNetworkPolicies" : "Disabled"
Name CloudName SubscriptionId State IsDefault
------- ---------- ------------------------------------ ------- ----------
MyCloud AzureCloud 13c91033-8b4e-40f7-9031-16c8f69233e3 Enabled True
az cloud set --name
az account set --subscription
az group deployment create --resource-group CUSTOMER_RESOURCEGROUP_NAME --template-file customer-privatelink-template.json --parameters customer-privatelink-parameters.json
Name CloudName SubscriptionId State IsDefault
------- ---------- ------------------------------------ ------- ----------
MyCloud AzureCloud 13c91033-8b4e-40f7-9031-16c8f69233e3 Enabled True
Platform
Cloud Data Platform
Architecture
Pricing
Data Marketplace
Solutions
Snowflake for Healthcare & Life Sciences
Snowflake for Marketing Analytics
Snowflake for Retail
Snowflake for Education
Snowflake for Developers
Resources
Resource Library
Webinars
Community
Legal
Explore
News
Blog
Trending
About
About Snowflake
Leadership & Board
Careers
Contact
Privacy Notice
Site Terms
This feature requires Business Critical (or higher).
If you are using Business Critical (or higher) and wish to use Azure Private Link with your account, please contact Snowflake Support and request it to be enabled, as described in this topic.
This topic describes how to configure Azure Private Link to connect your Azure Virtual Network (VNet) to the Snowflake VNet in Azure.
Note that Azure Private Link is not a service provided by Snowflake. It is a Microsoft service that Snowflake enables for use with your Snowflake account.
If you are using Business Critical (or higher) and wish to use Azure Private Link with your account, please contact Snowflake Support and request it to be enabled.
Azure Private Link provides private connectivity to Snowflake by ensuring that access to Snowflake is through a private IP address. Traffic can only occur from the customer virtual network (VNet) to the Snowflake VNet using the Microsoft backbone and avoids the public Internet. This significantly simplifies the network configuration by keeping access rules private while providing secure and private communication.
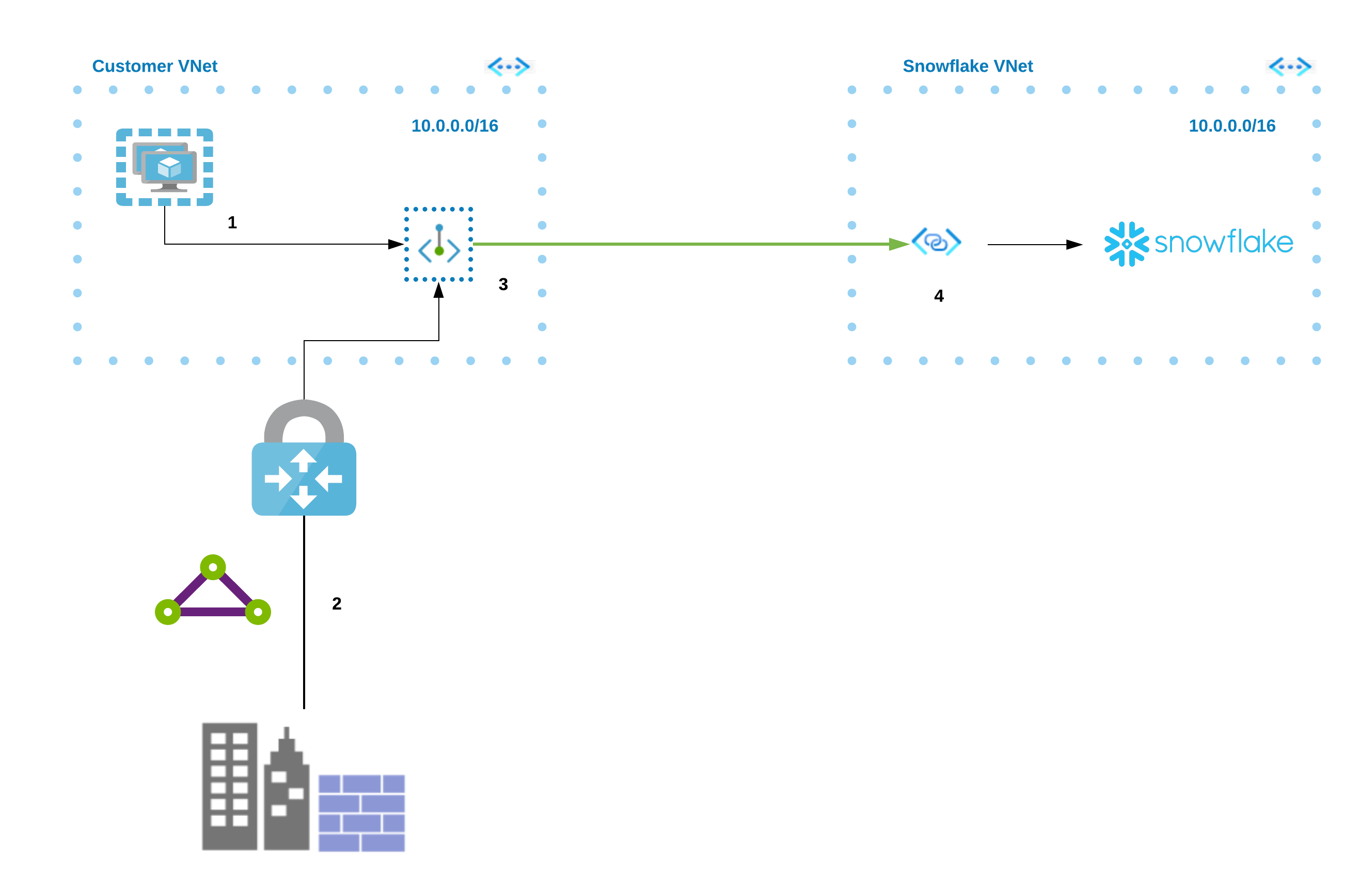
The following diagram summarizes the Azure Private Link architecture with respect to the customer VNet and the Snowflake VNet.
From either a virtual machine (1) or through peering (2), you can connect to the Azure Private Link endpoint (3) in your virtual network. That endpoint then connects to the Private Link Service (4) and routes to Snowflake.
Here are the high-level steps to integrate Snowflake with Azure Private Link:
Create a Private Endpoint and request approval from Snowflake as described in Configuring Access to Snowflake with Azure Private Link .
Contact Snowflake Support , and request for approval by providing the value of the Private Endpoint that you created. After Snowflake approves it, using Azure Portal, verify if the Private Endpoint displays a CONNECTION STATE value of Approved . Verify your account URL and the OCSP URL with Snowflake Support.
Update your outbound firewall settings to allow the Snowflake account URL and OCSP URL.
Update your DNS server to resolve your account URL and OCSP URL to the Private Link IP address. You can add the DNS entry to your on-premise DNS server or private DNS on your VNet, and use DNS forwarding to direct queries for the entry from other locations where your users will access Snowflake.
After the Private Endpoint displays a CONNECTION STATE value of Approved , test your connection to Snowflake with SnowCD (Connectivity Diagnostic Tool) and SYSTEM$WHITELIST_PRIVATELINK .
Connect to Snowflake using SnowSQL .
Before attempting to configure Azure Private Link to connect your Azure VNet to the Snowflake VNet on Azure, evaluate the following requirements and limitations:
The subnet containing the Private Endpoint needs to have its network policy disabled . Specifically, the subnet properties need to include the following two attributes:
If your corporate network protocols require the subnet in which the Azure Private Link endpoint resides to have network policies enabled, then you must configure a separate subnet that contains only the Azure Private Link endpoint and route requests from other subnets to the subnet containing the Azure Private Link endpoint.
If you are using a SaaS application to connect to Snowflake, you cannot use the SaaS application and Azure Private Link together. You can continue to use the SaaS application to connect to Snowflake through pathways that do not use Azure Private Link.
For more information on the requirements and limitations of Microsoft Azure Private Link, see the Microsoft documentation on Private Endpoint Limitations and Private Link Service Limitations .
This section only covers the Snowflake-specific details for configuring your VNet environment. Also, note that Snowflake is not responsible for the actual configuration of the required firewall updates and DNS records. If you encounter issues with any of these configuration tasks, please contact Microsoft Support directly.
This section describes how to configure your Azure VNet to connect to the Snowflake VNet on Azure using Azure Private Link. After initiating the connection to Snowflake using Azure Private Link, you can determine the approval state of the connection in the Azure portal.
For installation help, see the Microsoft documentation on the Azure CLI or Azure PowerShell .
Complete the Prerequisite Steps and either Option 1: Use Template Files or Option 2: Create Azure Resources Manually to configure your Microsoft Azure VNet and initiate the Azure Private Link connection to Snowflake.
Determine whether multiple Snowflake accounts in the same Azure region will use the same Azure SubscriptionID . During the initial configuration, one Snowflake account and one Azure SubscriptionID are necessary.
If you desire to tether multiple Snowflake accounts in the same Azure region to a single Azure SubscriptionID , please contact Snowflake Support while completing Step 2 in Option 1: Use Template Files .
Configure secure access to data files in your Azure Blob storage using Configuring an Azure Container for Loading Data .
This step ensures that bulk data loading from your Azure Blob storage external stage into Snowflake remains on the Azure networking backbone and does not use the public Internet.
Evaluate your Azure environment to determine whether you need a dedicated subnet with an Azure Private Link endpoint or only the Azure Private Link endpoint.
If you already have a dedicated subnet to use Azure Private Link to connect to Snowflake, it is only necessary to create a Private Endpoint in this subnet. Therefore, download these two files for use in Option 1 or configure manually as shown in Option 2.
If you do not have a dedicated subnet and choose to configure with template files, follow the instructions in Option 1. Otherwise, configure manually as shown in Option 2.
Options 1 and 2 make the following two assumptions:
Your use case does not involve Using SSO with Azure Private Link .
It is necessary to create both the subnet and the Private Endpoint. If your use case requires only the Private Endpoint, use the corresponding files in Step 1 of Option 1: Use Template Files .
This sequence of steps uses two different configuration files to create and initialize the necessary Azure Private Link resources to use Azure Private Link to connect to Snowflake on Azure. The configuration files are of two types:
Use this file to create a Private Endpoint and a subnet for that endpoint.
Use this file to initialize the resources the template file creates.
Depending on your Azure environment, it may not be necessary to create a dedicated subnet. If you already have a dedicated subnet for the Private Endpoint, you can use the corresponding files to create the endpoint in that subnet.
As a representative example, the following steps assume both a dedicated subnet and Private Endpoint are necessary.
The template files and scripts create resources in your Azure environment to facilitate connecting to Snowflake using Azure Private Link. Exercise caution when completing the configuration procedure. For additional help and support, please contact your internal Azure administrator.
Download these two files for use in the next steps:
As a representative example using the Azure CLI, execute az account list --output table . Note the output values in the Name and CloudName columns.
Contact Snowflake Support and share the SubscriptionId value and your account URL to access Snowflake with a note indicating that these values are to use Azure Private Link. Snowflake will then allow the SubscriptionId value for auto-approval. After receiving the approval response from Snowflake, run SYSTEM$GET_PRIVATELINK_CONFIG to obtain the URL to access Snowflake through Azure Private Link.
It may take up to 48 hours for Snowflake Support to process the ticket and allow the SubscriptionID value. Please wait patiently for Snowflake Support to provide confirmation. After receiving confirmation, continue with the remaining steps in this procedure.
If you desire to tether multiple Snowflake accounts in the same Azure region to a single Azure SubscriptionID , please contact Snowflake Support .
For each parameter in customer-privatelink-parameters.json , update the value to match your environment. For example, replace the virtualNetworkName value of privateLinkConsumer_vnet with myVirtualNetwork .
To determine the correct alias value for snowflakePrivatelinkServiceAlias , execute SYSTEM$GET_PRIVATELINK_CONFIG in Snowflake and use the value for privatelink-pls-id .
In the Azure CLI, execute the following three commands using the values from the previous step. Note that these values are representative examples.
Replace with AzureCloud .
Replace with MyCloud .
You can choose an arbitrary name for CUSTOMER_RESOURCE_GROUP .
DNS Setup. All requests to Snowflake need to be routed via the Private Endpoint. Update your DNS to resolve the Snowflake account and OCSP URLs to the private IP address of your Private Endpoint.
To get the Private Endpoint IP address, navigate to the Azure portal Private Link Center . Click Private endpoints and click on the endpoint.
Copy the value for the Private IP address (i.e. 10.0.27.5 ).
Configure your DNS to have your account and OCSP URLs resolve to the private IP address. In Snowflake, execute SYSTEM$GET_PRIVATELINK_CONFIG and use the values for private-link-account-url and private-link-ocsp-url .
If you are using any of the following features or may use these features in the future, it is necessary to create an additional DNS record with the following values or combine the following values with the Snowflake account and OCSP cache server values. This step ensures access to these features via a Private Endpoint.
app..privatelink.snowflakecomputing.com
A full explanation of DNS configuration is beyond the scope of this procedure. For example, you can choose to integrate an Azure Private DNS zone into your environment.
Please consult your internal Azure and Cloud Infrastructure administrators to configure and resolve the URLs in DNS properly.
After verifying your outbound firewall settings and DNS records to include your Azure Private Link account and OCSP URLs, test your connection to Snowflake with SnowCD (Connectivity Diagnostic Tool) and SYSTEM$WHITELIST_PRIVATELINK .
Connect to Snowflake using SnowSQL .
You can now connect to Snowflake using Azure Private Link.
This sequence of steps manually creates and initializes the necessary Azure Private Link resources to use Azure Private Link to connect to Snowflake on Azure.
Verify that a dedicated subnet exists to contain the Private Endpoint and that network policies are disabled. For more information, see Disable network policies for private endpoints .
As a representative example using the Azure CLI, execute az account list --output table . Note the output values in the Name and CloudName columns.
Contact Snowflake Support and share the SubscriptionId value and your account URL to access Snowflake with a note indicating that these values are to use Azure Private Link. Snowflake will then allow the SubscriptionId value for auto-approval. After receiving the approval response from Snowflake, run SYSTEM$GET_PRIVATELINK_CONFIG to obtain the URL to access Snowflake through Azure Private Link.
It may take up to 48 hours for Snowflake Support to process the ticket and allow the SubscriptionID value. Please wait patiently for Snowflake Support to provide confirmation. After receiving confirmation, continue with the remaining steps in this procedure.
If you desire to tether multiple Snowflake accounts in the same Azure region to a single Azure SubscriptionID , please contact Snowflake Support .
Navigate to the Azure portal. Search for Private Link and click Private Link .
Click Private endpoints and then click Add .
In the Basics section, complete the Subscription , Resource group , Name , and Region fields for your environment and then click Next: Resource .
In the Resource section, complete the Connection Method and the Resource ID or Alias Field fields. The Request message value is optional.
For Connection Method , select the Connect to an Azure resource by resource ID or alias .
In Snowflake, execute SYSTEM$GET_PRIVATELINK_CONFIG and input the value for privatelink-pls-id into the Resource ID or Alias field. Note that the screenshot in this step uses the alias value for the east-us-2 region as a representative example, and that Azure confirms a valid alias value with a green checkmark.
Return to the Private endpoints section and allow a few minutes to wait. On approval, the Private Endpoint displays a CONNECTION STATE value of Approved .
DNS Setup. All requests to Snowflake need to be routed via the Private Endpoint. Update your DNS to resolve the Snowflake account and OCSP URLs to the private IP address of your Private Endpoint.
To get the endpoint IP address, navigate to Azure portal search bar and enter the name of the endpoint (i.e. the NAME value from Step 6). Locate the Network Interface result and click it.
Copy the value for the Private IP address (i.e. 10.0.27.5 ).
Configure your DNS to have your account and OCSP URLs resolve to the private IP address. In Snowflake, execute SYSTEM$GET_PRIVATELINK_CONFIG and use the values for private-link-account-url and private-link-ocsp-url .
If you are using any of the following features or may use these features in the future, it is necessary to create an additional DNS record with the following values or combine the following values with the Snowflake account and OCSP cache server values. This step ensures access to these features via a Private Endpoint.
app..privatelink.snowflakecomputing.com
A full explanation of DNS configuration is beyond the scope of this procedure. For example, you can choose to integrate an Azure Private DNS zone into your environment. Please consult your internal Azure and Cloud Infrastructure administrators to configure and resolve the URLs in DNS properly.
After verifying your outbound firewall settings and DNS records include your Azure Private Link account and OCSP URLs, test your connection to Snowflake with SnowCD (Connectivity Diagnostic Tool) and SYSTEM$WHITELIST_PRIVATELINK .
Connect to Snowflake using SnowSQL .
You can now connect to Snowflake using Azure Private Link.
Snowflake supports using SSO with Azure Private Link. For more information, see:
After testing the Azure Private Link connectivity with Snowflake, you can optionally block public access to Snowflake using Network Policies .
Configure the CIDR block range to block public access to Snowflake using your organization’s IP address range . This range can be from within your virtual network.
Once the CIDR Block ranges are set, only IP addresses within the CIDR block range can access Snowflake.
To block public access using a network policy:
Create a new network policy or edit an existing network policy. Add the CIDR block range for your organization.
Activate the network policy for your account.
© 2021 Snowflake Inc. All Rights Reserved
Granny Eating
Spying Peeing Women
Real Homemade Mature Mom Sex
Start Line Hobby Outdoor
First Anal Homemade









































.full.1977633.jpg)