Private Key Encryption

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
РекламаМужское нижнее бельё KEY! Купить! Сезонная распродажа! Скидки от 5 до 40% на всё! · Москва · пн-пт 10:00-18:00, сб 11:00-17:00
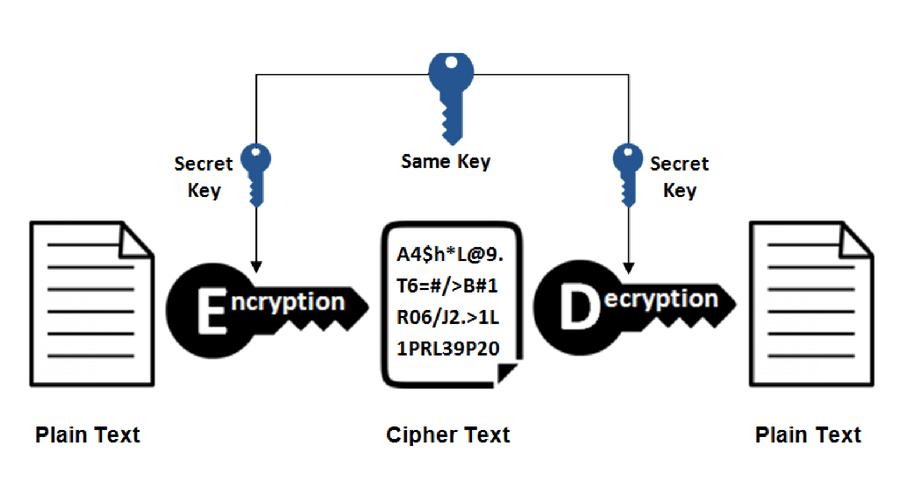
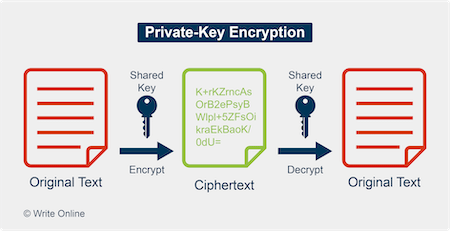
Private key encryption is the form of encryption where only a single private key can encrypt and decrypt information. It is a fast process since it uses a single key. However, protecting one key creates a key management issue when everyone is using private keys. The private key may be stolen or leaked.
koolspan.com/private-key-encryption/
How are public and private keys used in encryption?
How are public and private keys used in encryption?
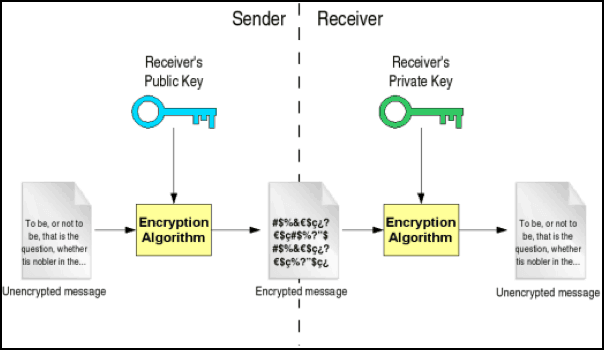
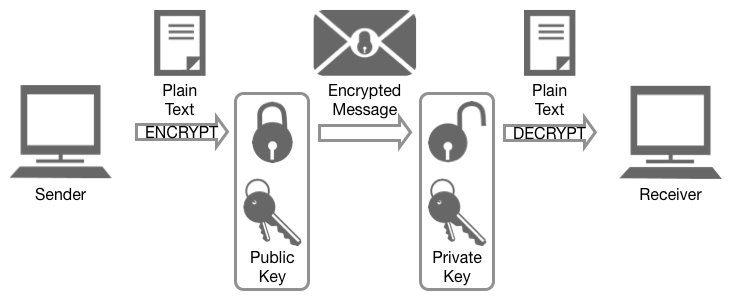
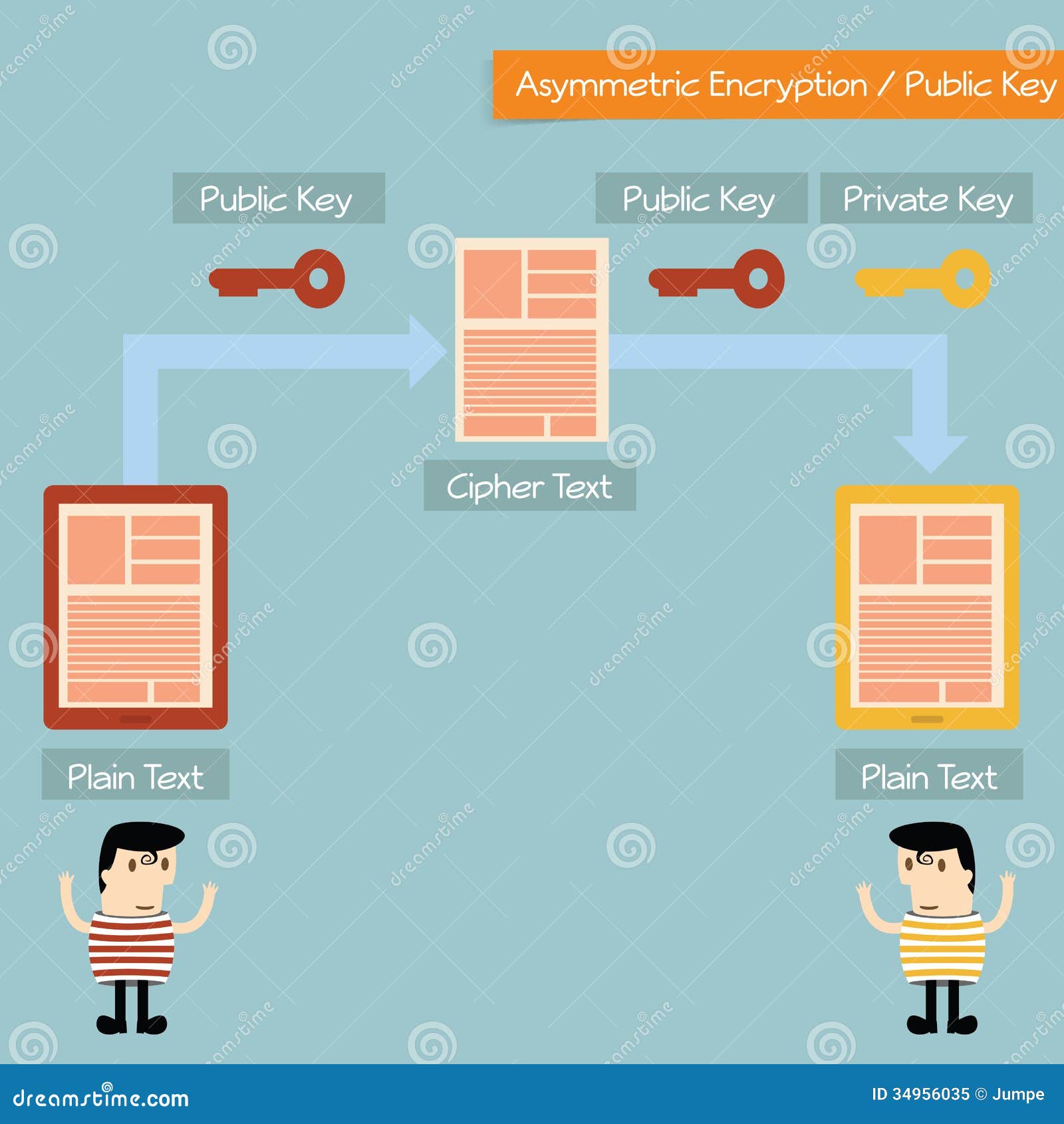
How public and private key encryption works Public and private keys form the basis for public key cryptography, also known as asymmetric cryptography. In public key cryptography, every public key matches to only one private key. Together, they are used to encrypt and decrypt messages.
www.preveil.com/blog/public-and-private-…
How to decrypt a password protected RSA private key?
How to decrypt a password protected RSA private key?
You can use the openssl command to decrypt the key: For example, if you have a encrypted key file ssl.key and you want to decrypt it and store it as mykey.key, the command will be How to generate a pair of RSA private and public key in Linux?
www.systutorials.com/how-to-decrypt-a-p…
Can a message be decrypted without the public key?
Can a message be decrypted without the public key?
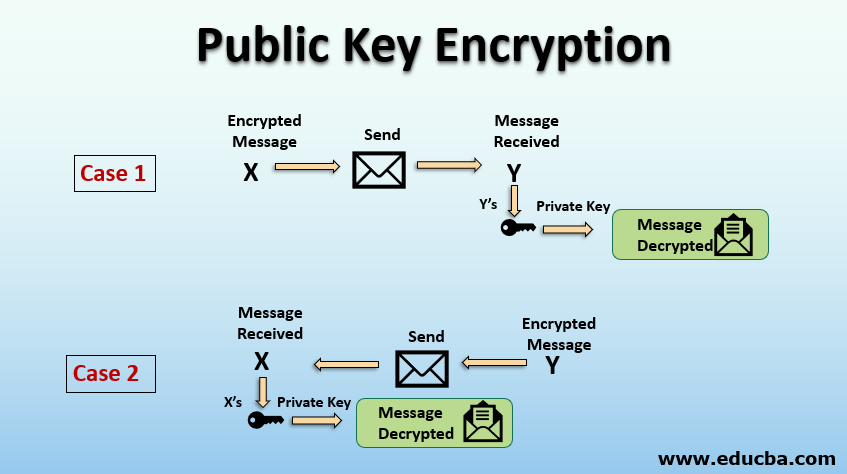
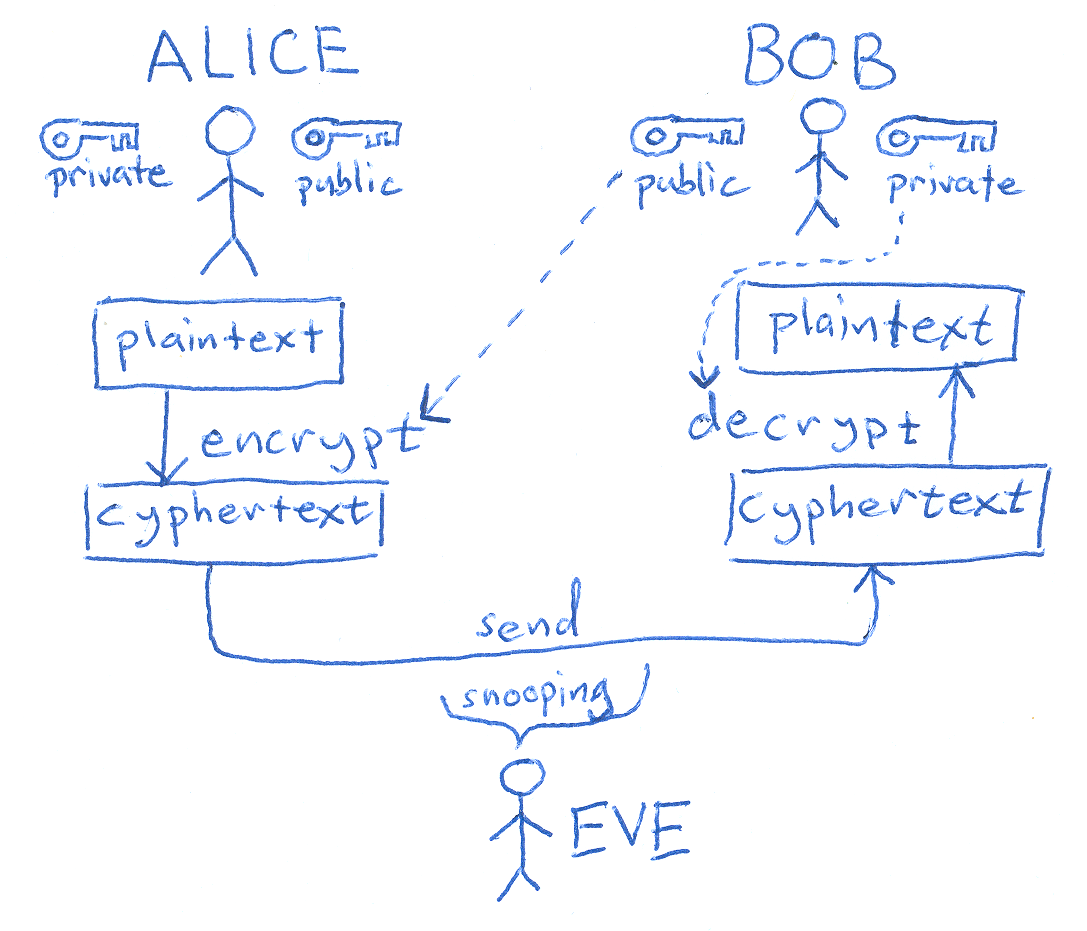
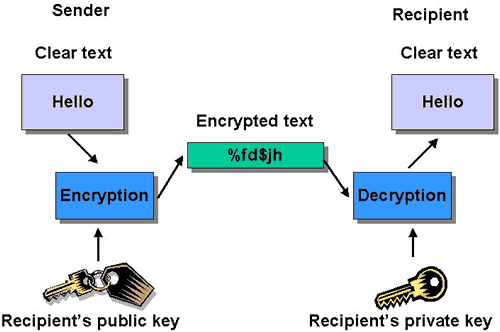
A message encrypted with the public key cannot be decrypted without using the corresponding private key. The public and private key are not really keys but rather are really large prime numbers that are mathematically related to one another.
www.preveil.com/blog/public-and-private-…
Is there a way to decrypt Alice's private key?
Is there a way to decrypt Alice's private key?
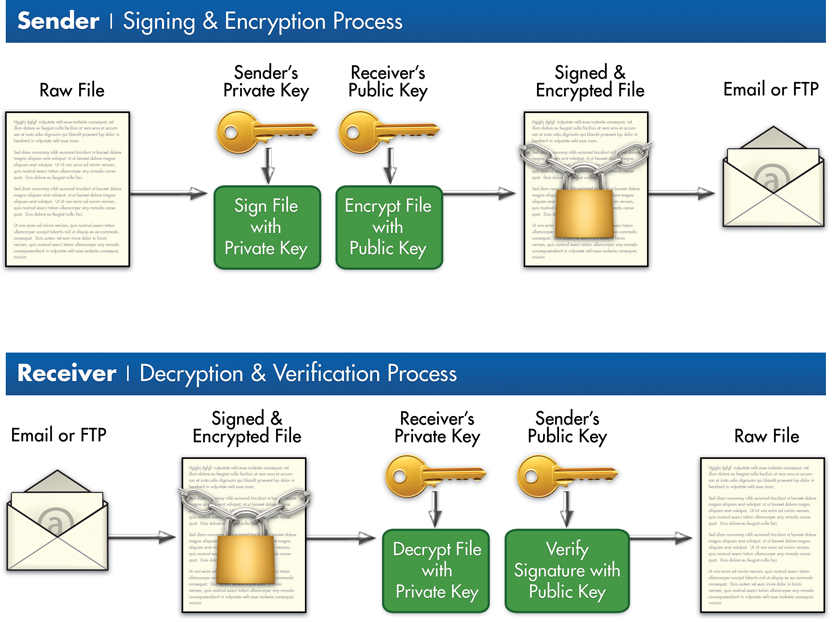
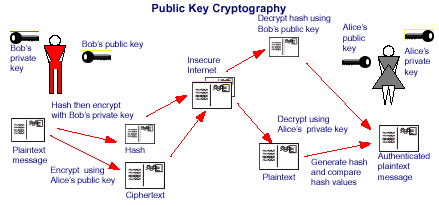
The only way to decrypt Alice’s private key is with her public key, which Bob can access. By signing the message with her private key, Alice ensures the authenticity of the message and shows that it really did come from her. Public and private key pairs form the basis for very strong encryption and data security.
www.preveil.com/blog/public-and-private-…
https://koolspan.com/private-key-encryption
Encryption
Public and Private Keys
Private Key Encryption
Public Key Infrastructure
Private key encryption is the form of encryption where only a single private key can encrypt and decrypt information. It is a fast process since it uses a single key. However, protecting one key creates a key management issue when everyone is using private keys. The private key may be stolen or leaked. Key management requires prevention of these risks and necessitates changing the encryption key often, and …
https://www.sciencedirect.com/topics/computer-science/private-key-cryptography
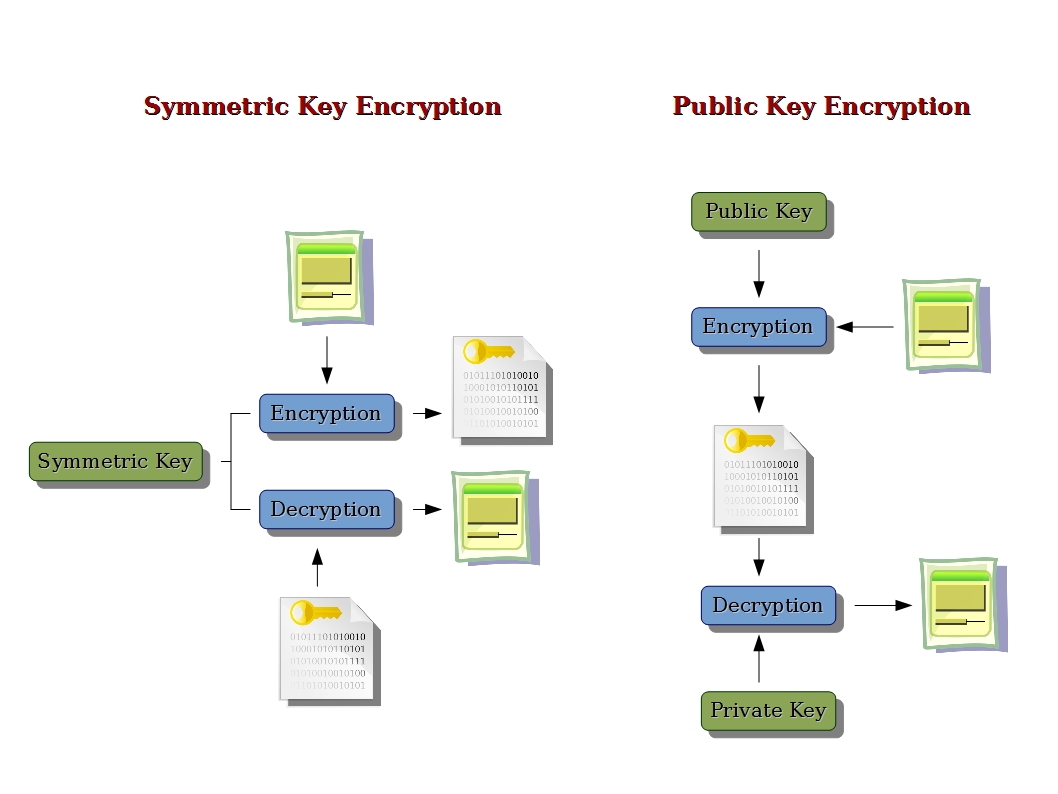
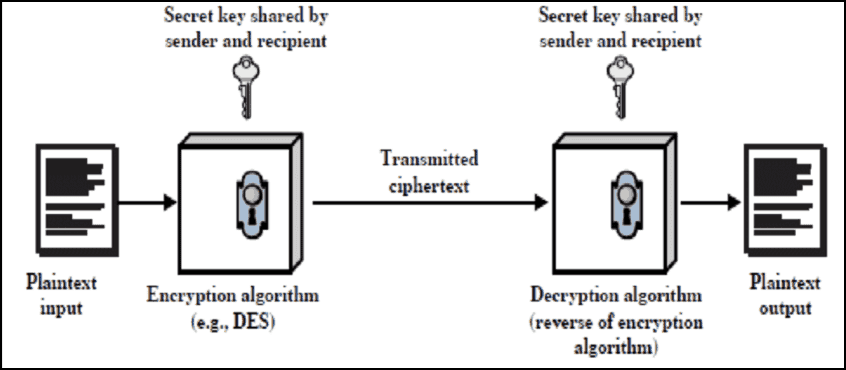
Symmetric: One method of cryptography is symmetric cryptography (also known as secret key cryptography or private key cryptography). Symmetric cryptography is best suited for bulk encryption because it is much faster than asymmetric cryptography.
How To: Public-Private Key Encryption - Cryptography
YouTube › Redport Information Assurance
What is Public and Private Key Encryption?
Private Key Encryption (Symmetric Key Encryption)
C# Public/Private Key Encryption using Visual Studio 2019 | RSA Cryptography
JAVA PRIVATE KEY ENCRYPTION Example
IT Security Tutorial - What is public key encryption?
https://www.youngwonks.com/blog/Public-Key-and-Private-Key-Encryption-Explained
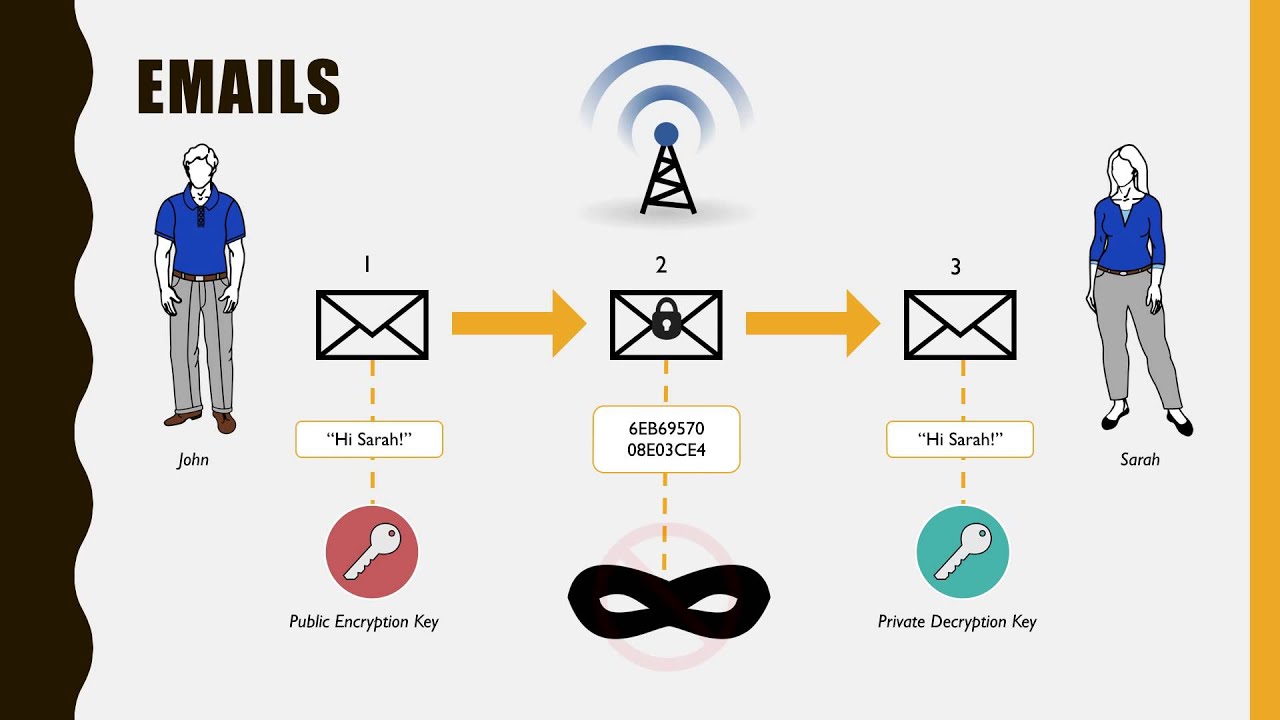
18.09.2018 · For that, one needs the private key; in this case, it’s the mailbox key that only its owner has. So when a person uses asymmetric key encryption to send a message, both the sender and the recipient begin by generating a key pair (i.e. a public and a private key each) on their respective computers.
https://www.preveil.com/blog/public-and-private-key
Public and Private Keys: An Example
Generating Public and Private Keys
Digital Signatures
Diffie-Helman Key Exchange
Conclusion
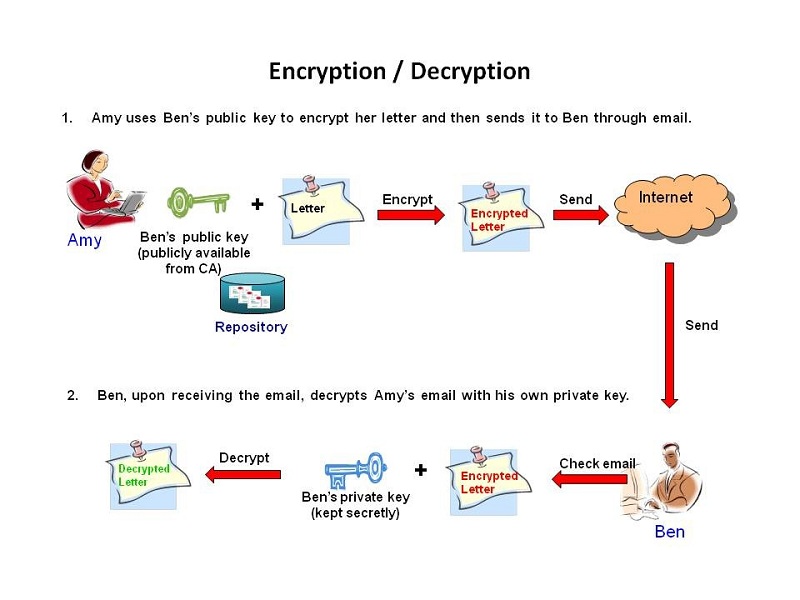
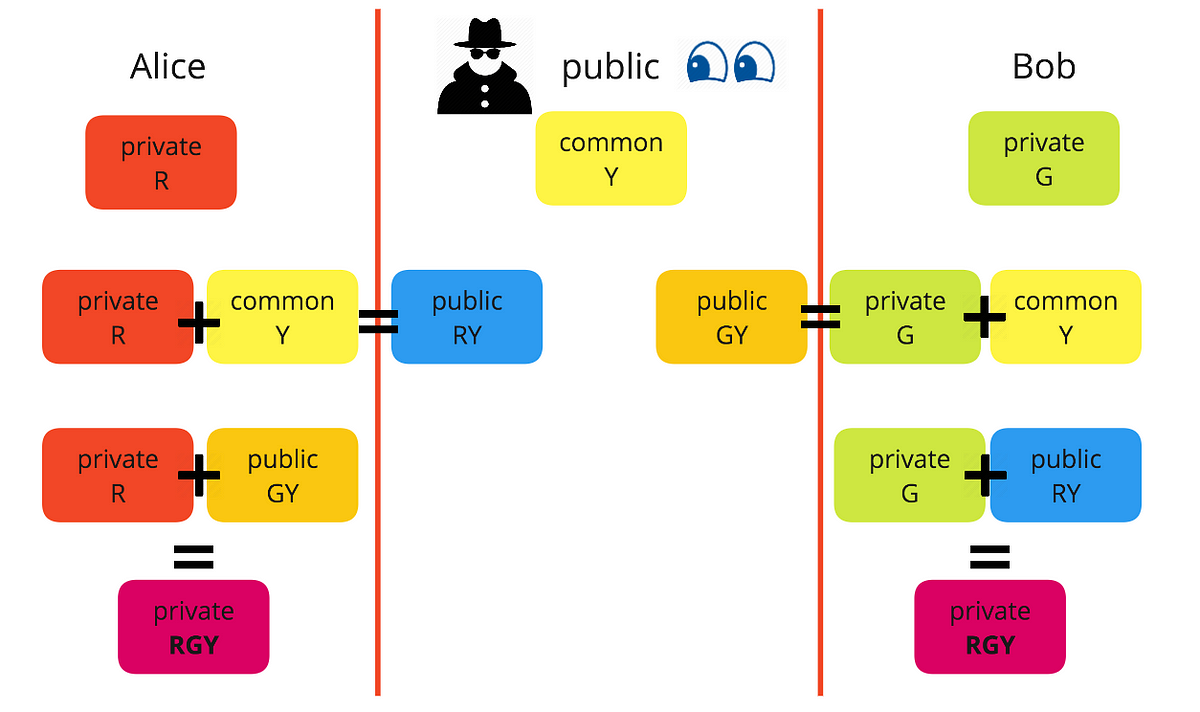
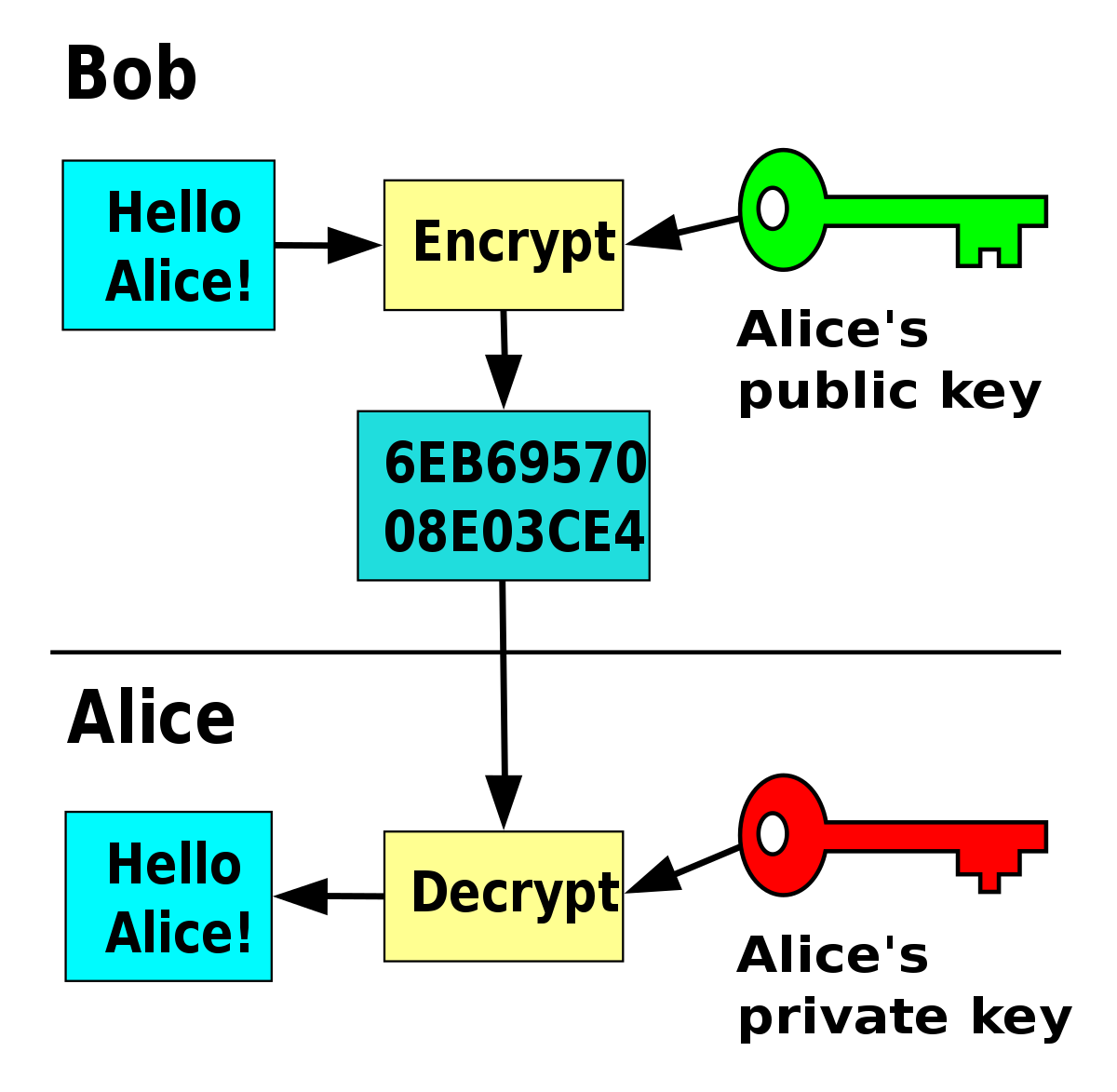
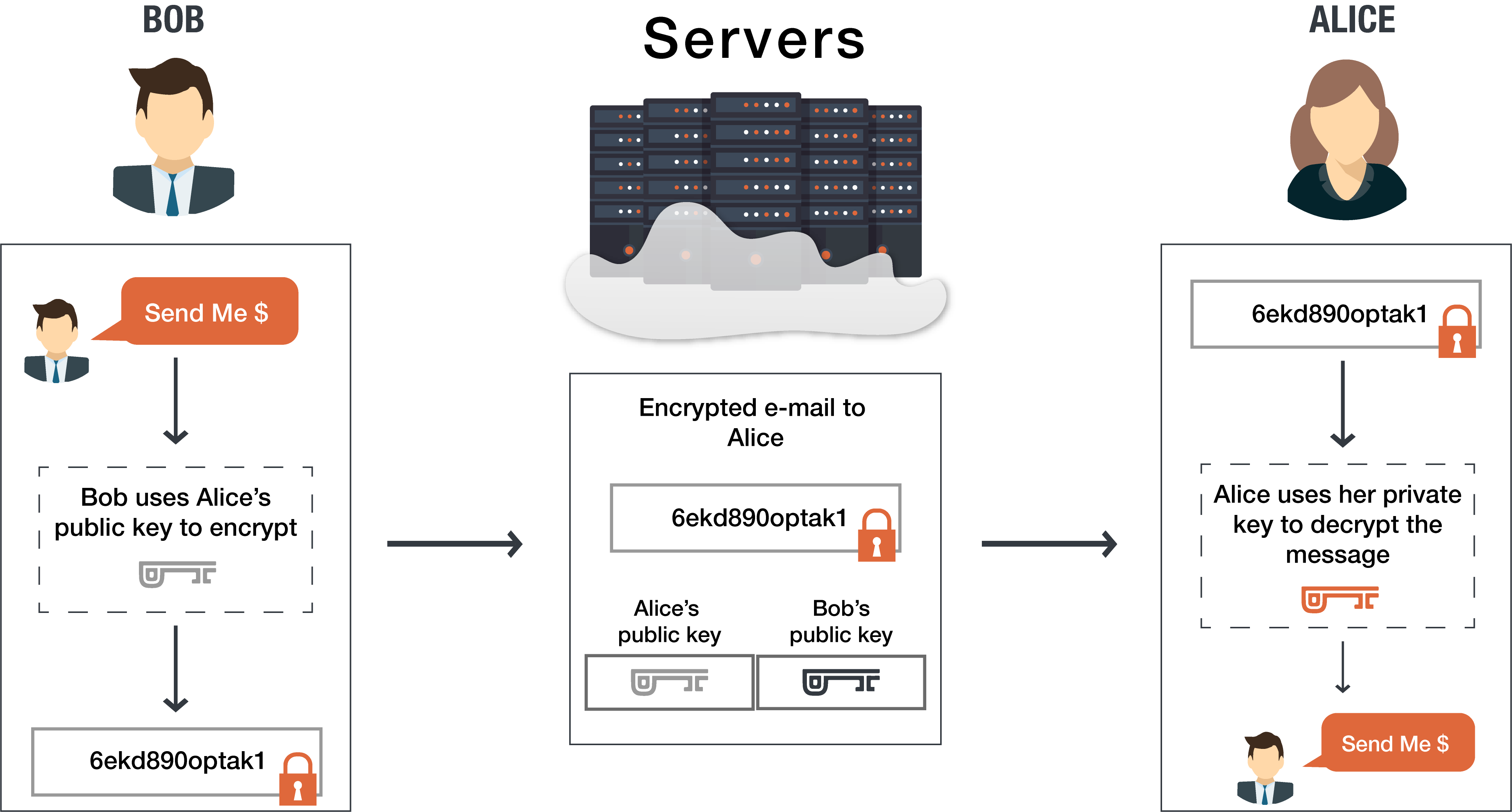
Bob wants to send Alice an encrypted email. To do this, Bob takes Alice’s public key and encrypts his message to her. Then, when Alice receives the message, she takes the private key that is known only to her in order to decrypt the message from Bob. Although attackers might try to com…
https://www.section.io/blog/private-public-key-encryption
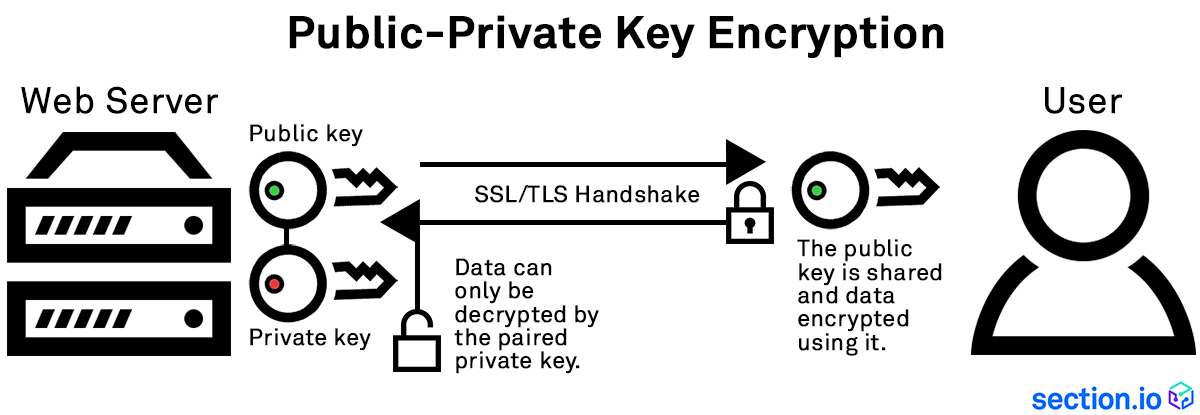
11.01.2017 · This public-private key encryption uses unique keys to encrypt and decrypt data passing between a website server and browser, meaning that any content sent between a browser and the web server cannot be read by a third party that intercepts that data without the appropriate key…
https://stackoverflow.com/questions/5817254
25.08.2012 · 2 Answers2. Public Key Encryption - when done "by the book" - seperates encryption and signing ("cannot be altered"). In your case, use two key pairs, one within the application and one at your site. Encrypt the file using the public application key and sign the file using your private …
https://learn.bybit.com/blockchain/what-is-public-keys-and-private-keys-in...
Cryptography Methods Used in Cryptocurrencies
How Does Private and Public Keys Work?
The Differences Between Public Keys and Private Keys
Benefits and Limitations of Public and Private Key Encryption
When to Choose A Public Or Private Key?
Closing Thoughts
When it comes to cryptography in cryptocurrency, there are several methods, and that includes symmetric encryption, asymmetric encryption, and hashing.
https://en.m.wikipedia.org/wiki/Public-key_cryptography
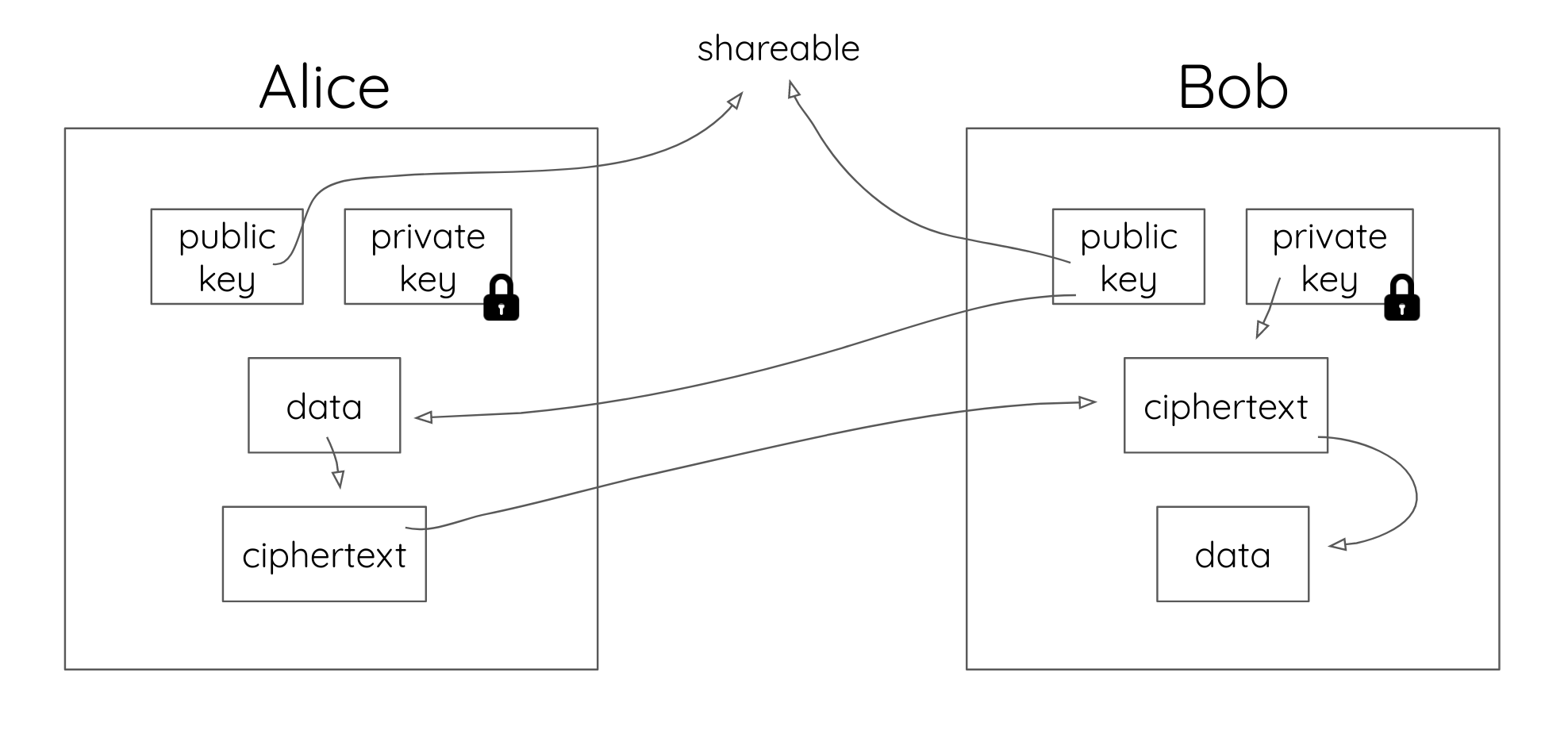
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys (which may be known to others), and private keys (which may never be known by any except the owner). The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way functions. Effective security requires keeping the private key private; the public key can be openly distributed without compromising security.
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys (which may be known to others), and private keys (which may never be known by any except the owner). The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way functions. Effective security requires keeping the private key private; the public key can be openly distributed without compromising security.
In such a system, any person can encrypt a message using the intended receiver's public key, but that encrypted message can only be decrypted with the receiver's private key. This allows, for instance, a server program to generate a cryptographic key intended for a suitable symmetric-key cryptography, then to use a client's openly-shared public key to encrypt that newly generated symmetric key. The server can then send this encrypted symmetric key over an insecure channel to the client; only the client can decrypt it using the client's private key (which pairs with the public key used by the server to encrypt the message). With the client and server both having the same symmetric key, they can safely use symmetric key encryption (likely much faster) to communicate over otherwise-insecure channels. This scheme has the advantage of not having to manually pre-share symmetric keys (a fundamentally difficult problem) while gaining the higher data throughput advantage of symmetric-key cryptography.
With public-key cryptography, robust authentication is also possible. A sender can combine a message with a private key to create a short digital signature on the message. Anyone with the sender's corresponding public key can combine that message with a claimed digital signature; if the signature matches the message, the origin of the message is verified (i.e., it must have been made by the owner of the corresponding private key).
Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols which offer assurance of the confidentiality, authenticity and non-repudiability of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), S/MIME, PGP, and GPG. Some public key algorithms provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some provide digital signatures (e.g., Digital Signature Algorithm), and some provide both (e.g., RSA). Compared to symmetric encryption, asymmetric encryption is rather slower than good symmetric encryption, too slow for many purposes. Today's cryptosystems (such as TLS, Secure Shell) use both symmetric encryption and asymmetric encryption.
https://stackoverflow.com/questions/49230122
11.03.2018 · TH above key is in PKCS#8 format. I want to convert it into a RSA Private Key PKCS#1 format. The command I use is: openssl rsa -in servenc.key -out serv.key. The output which i get is in the below format: -----BEGIN RSA PRIVATE KEY …
РекламаНедорого! Клавиатура и мышь Wireless Canyon SET W3 105 keys chocolate key caps b
РекламаOpensource. Надежный хеш алгоритм MD55, используйте в своих приложениях – Free.
Не удается получить доступ к вашему текущему расположению. Для получения лучших результатов предоставьте Bing доступ к данным о расположении или введите расположение.
Не удается получить доступ к расположению вашего устройства. Для получения лучших результатов введите расположение.
Home » What is Private Key Encryption?
In an age where breaches occur daily, businesses need to protect confidential information including customer data, intellectual property, research and development, future business plans, and all sorts of other information. Confidential information needs to be secured at rest, as well as when it is exchanged between employees, executives, partners, and others, via phone call, text message or email. Data is secured in many different ways, one of which is private key encryption. What, exactly, is private key encryption?
Encryption has been around for centuries. Encryption is the process of transforming information into a form that is unreadable by anyone other than those the information is intended for. It has long been used by the military and governments to protect communications.
In today’s world, we use encryption to protect a variety of data, both in transit and at rest. It is used to protect home Wi-Fi networks, mobile telephones, ATM machines, secure websites and a slew of other devices and services.
Encryption makes use of an algorithm (also called a cipher) to transform information into an unreadable format and requiring a “key” to decrypt the data into its original, readable format. A key for electronic/digitally encrypted information is really just bits of code that use an algorithm to lock and unlock information.
Public and private keys refer to the ‘keys’ used to encrypt and decrypt information. A public key is available to many, and made available in an online directory. A private key is private, and only made available to the originator of the encrypted content, and those it is shared with.
Private key encryption is the form of encryption where only a single private key can encrypt and decrypt information. It is a fast process since it uses a single key. However, protecting one key creates a key management issue when everyone is using private keys. The private key may be stolen or leaked. Key management requires prevention of these risks and necessitates changing the encryption key often, and appropriately distributing the key.
In contrast to private key encryption, Public Key Infrastructure, commonly referred to as PKI, uses two keys – one private and one public. The public key is distributed, whereas the private key is never shared.
Across the web, PKI is extremely common. For example, when you make an online purchase, you are using Secure Sockets Layer (SSL) to encrypt the web session between yourself and the site. This type of method makes use of PKI.
Private encryption is more commonly used to protect – and access – data stores, such as disk drives, confidential information and the like.
Not long ago, encryption was used exclusively to protect the information of generals, diplomats and governments. Now, all of us are accessing data sources, transferring information over the Internet, storing and accessing confidential information, sometimes on the go, sometime remotely. Encryption allows us to conduct our online business securely.
KoolSpan TrustCall utilizes PKI to secure mobile phone calls and text messages – ensuring your confidential information is always encrypted and remains secure and private. Looking for more information? Contact KoolSpan about TrustCall.
Francis Knott has over 17 years of mobility, technology, interactive media, software and healthcare experience. Mr Knott is an expert at building companies, growing revenue and launching and marketing new products. In the past, he has worked in software and product development, mobile social media, and mobile applications development.
Main 240 880-4400
Fax 240 880-4419
Sales 240 880-4400, Option 1
Int. Sales 240 880-4403
OEM Inquiries 240 880-4404
We're not around right now. But you can send us an email and we'll get back to you, asap.
I consent to KoolSpan collecting my details through this form.
Выбрать язык
русский
английский
арабский
вьетнамский
иврит
испанский
итальянский
китайский (упрощенный)
корейский
немецкий
португальский
французский
японский
We use cookies to ensure that we give you the best experience on our website. If you continue to use this site we will assume that you are happy with it.Ok
A Wife And Mother Sophia
Female Pov Creampie
Youtube Hidden Camera Naked Men S Dagestan
Jerk Voyeur Video
24video Massage Lesbian
What is Private Key Encryption? | KoolSpan
Private Key Cryptography - an overview | ScienceDirect Topics
Public and private encryption keys | PreVeil
How Private-Public Key Encryption Keeps Data Safe | Section
c# - PRIVATE key encryption in .Net - Stack Overflow
Public Keys vs. Private Keys: What Is It & How Do They ...
Public-key cryptography - Wikipedia
Private Key Encryption