Private Key Encryption

💣 👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Home » What is Private Key Encryption?
In an age where breaches occur daily, businesses need to protect confidential information including customer data, intellectual property, research and development, future business plans, and all sorts of other information. Confidential information needs to be secured at rest, as well as when it is exchanged between employees, executives, partners, and others, via phone call, text message or email. Data is secured in many different ways, one of which is private key encryption. What, exactly, is private key encryption?
Encryption has been around for centuries. Encryption is the process of transforming information into a form that is unreadable by anyone other than those the information is intended for. It has long been used by the military and governments to protect communications.
In today’s world, we use encryption to protect a variety of data, both in transit and at rest. It is used to protect home Wi-Fi networks, mobile telephones, ATM machines, secure websites and a slew of other devices and services.
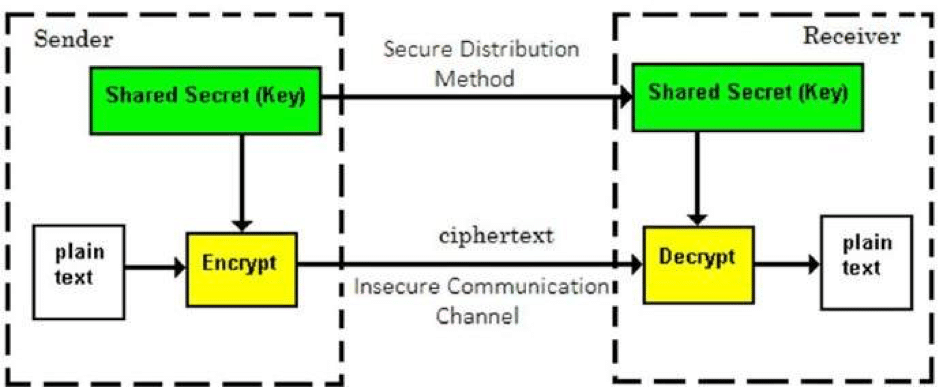
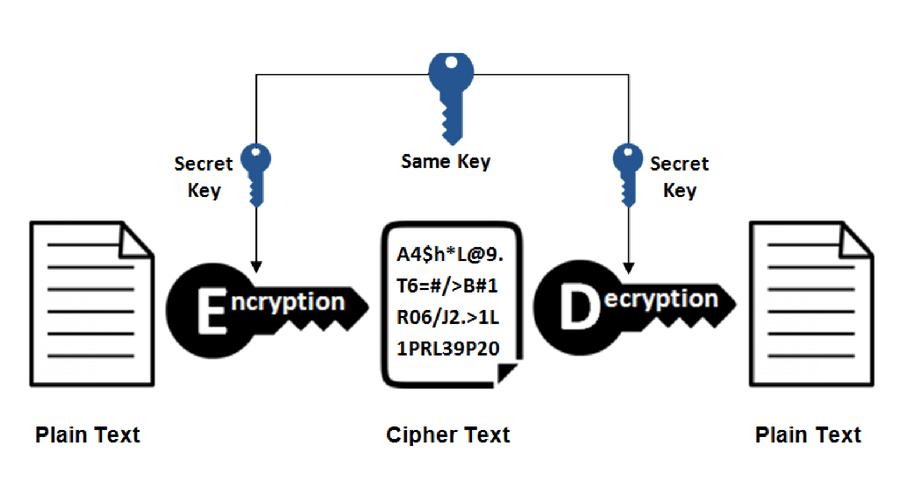
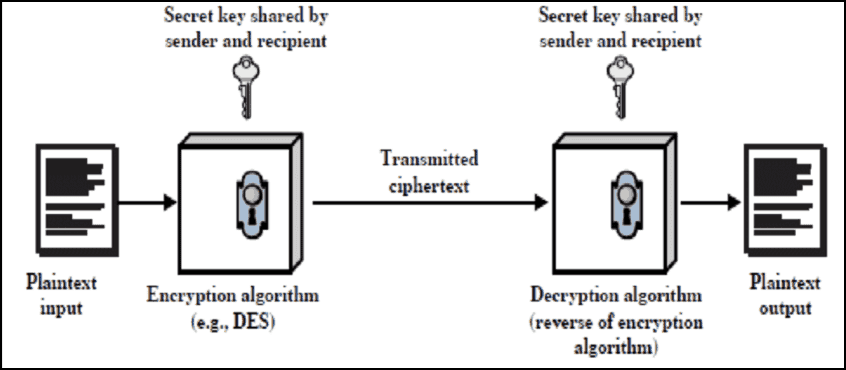
Encryption makes use of an algorithm (also called a cipher) to transform information into an unreadable format and requiring a “key” to decrypt the data into its original, readable format. A key for electronic/digitally encrypted information is really just bits of code that use an algorithm to lock and unlock information.
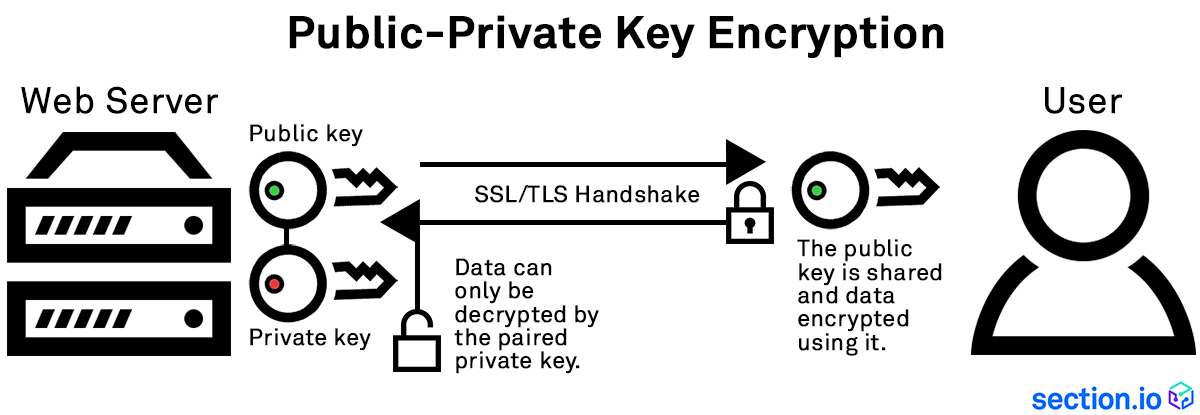
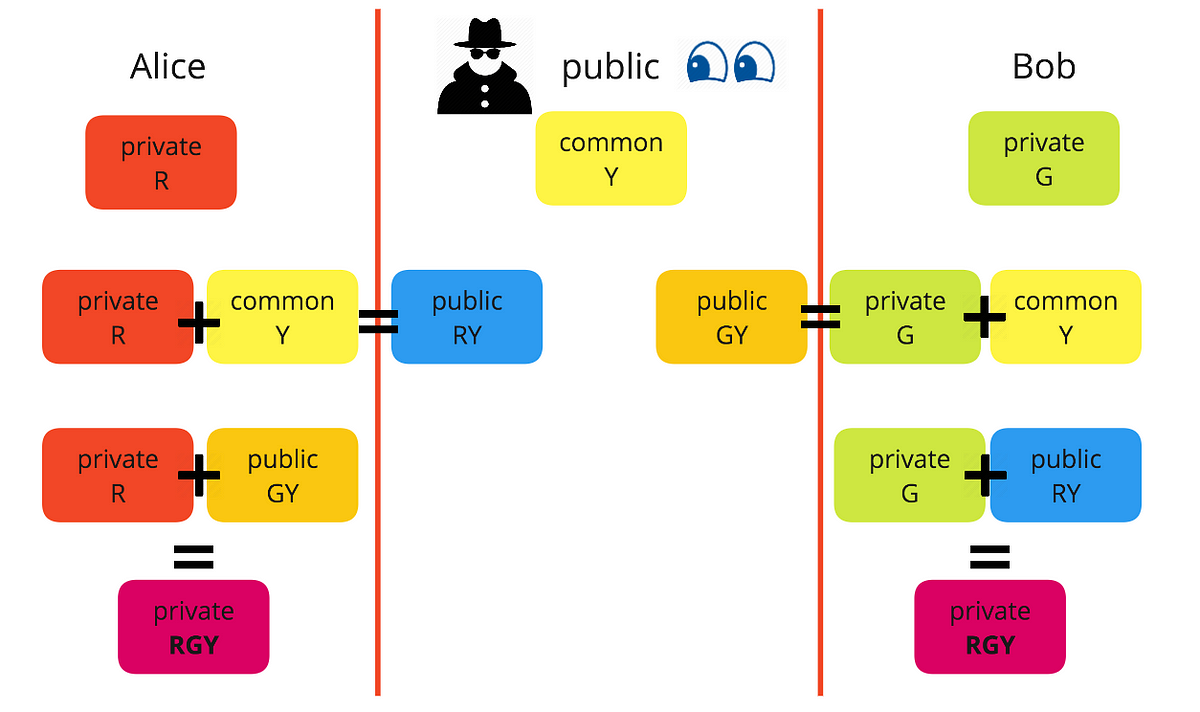
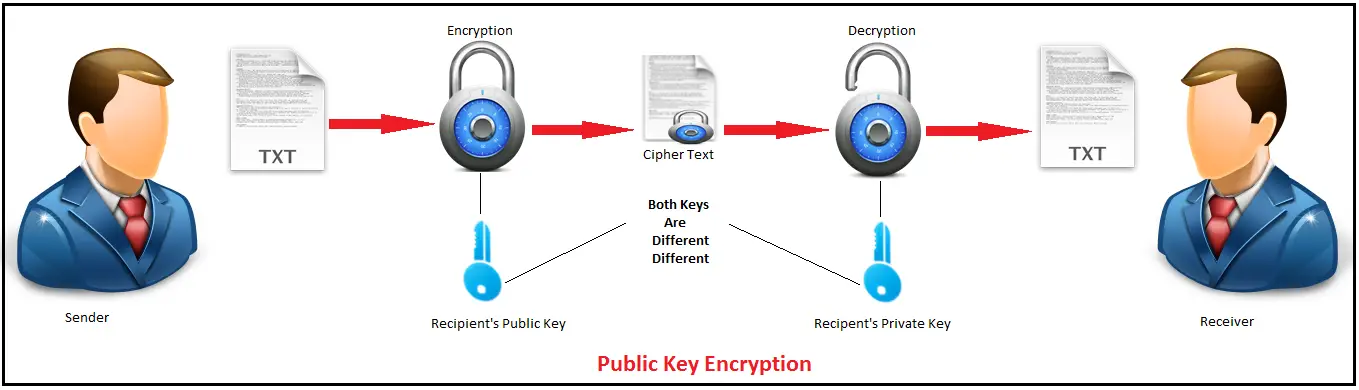
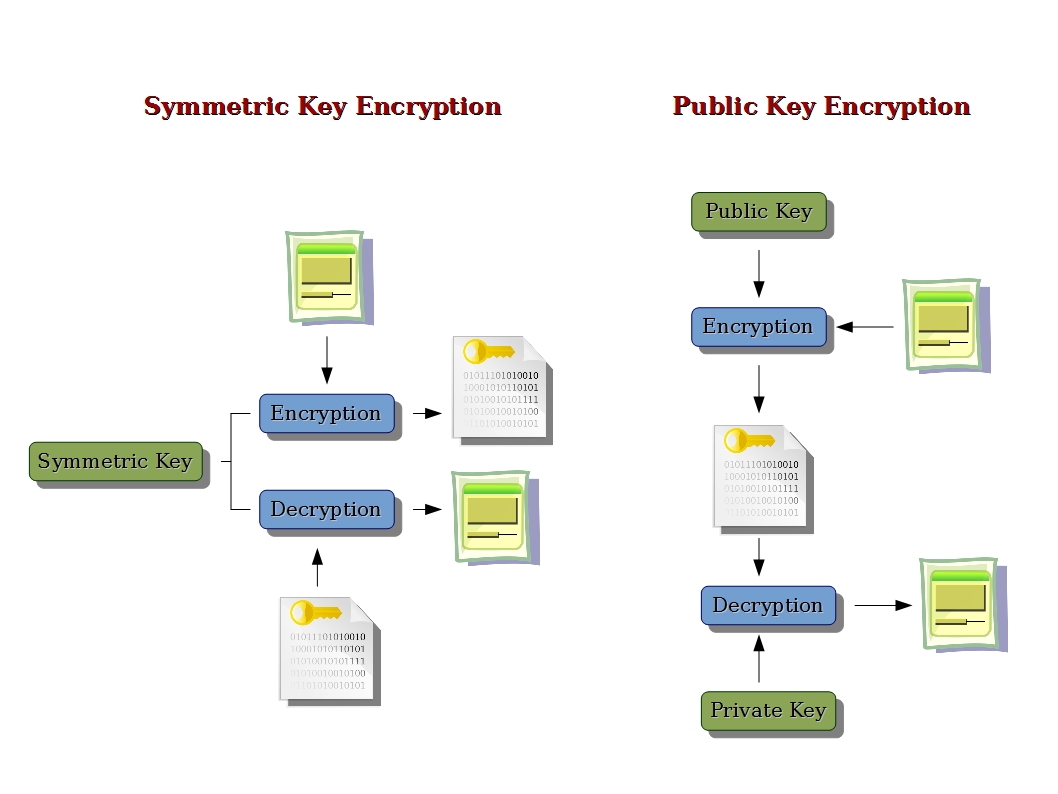
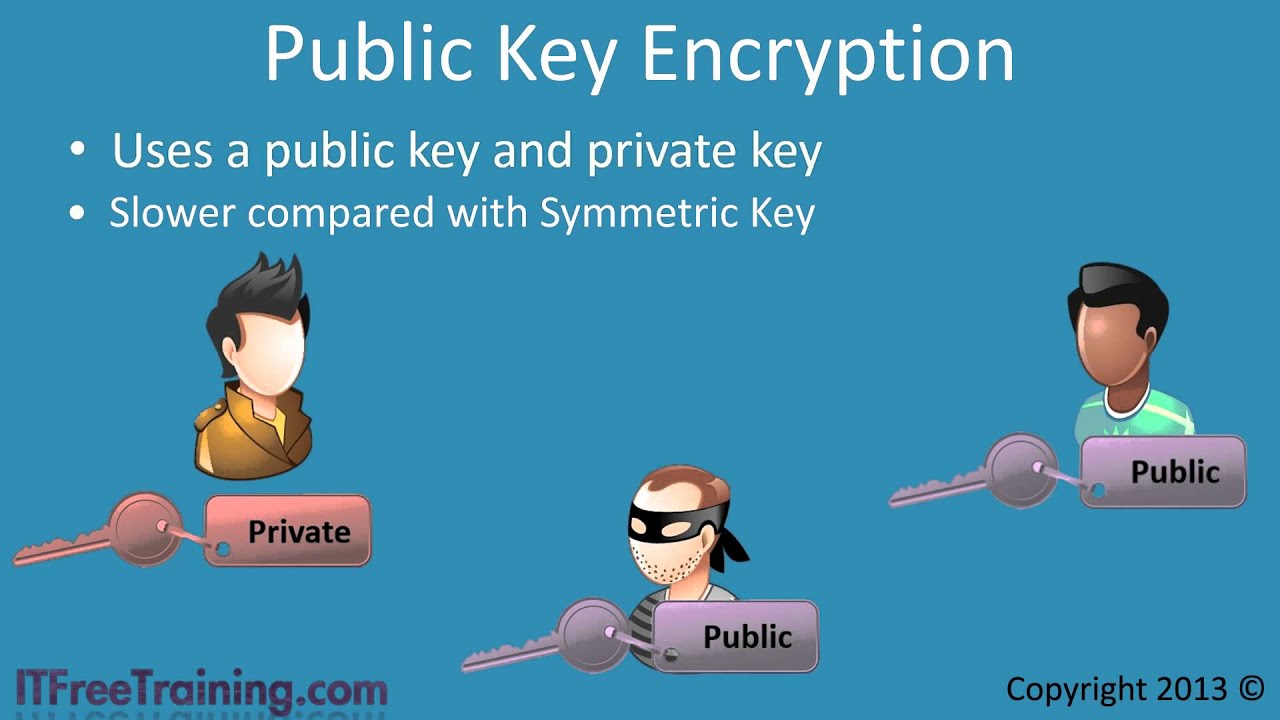
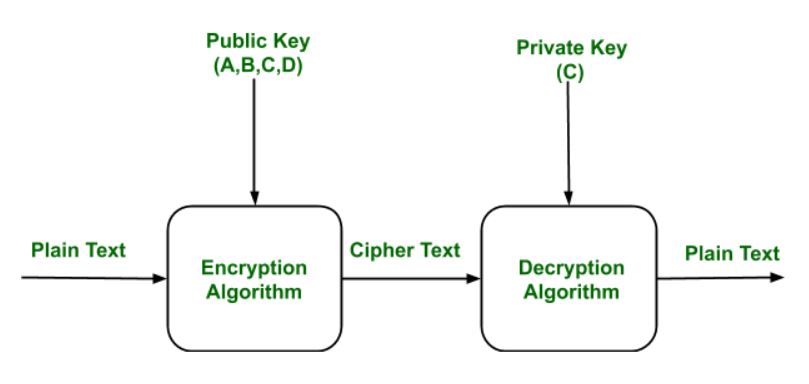
Public and private keys refer to the ‘keys’ used to encrypt and decrypt information. A public key is available to many, and made available in an online directory. A private key is private, and only made available to the originator of the encrypted content, and those it is shared with.
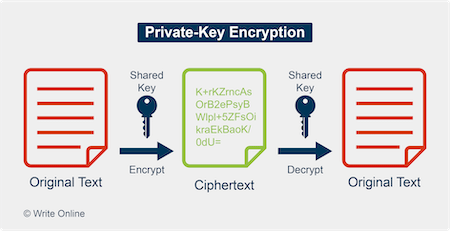
Private key encryption is the form of encryption where only a single private key can encrypt and decrypt information. It is a fast process since it uses a single key. However, protecting one key creates a key management issue when everyone is using private keys. The private key may be stolen or leaked. Key management requires prevention of these risks and necessitates changing the encryption key often, and appropriately distributing the key.
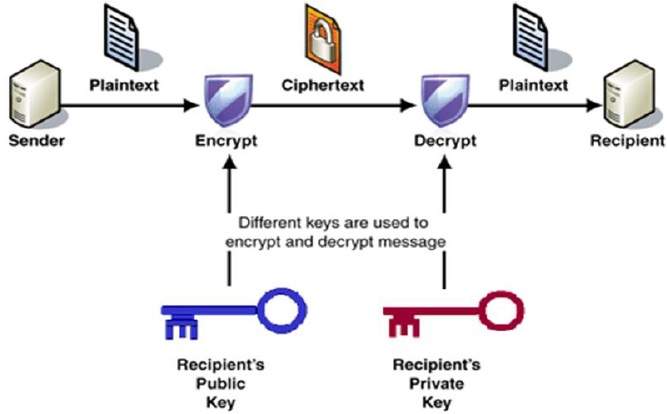
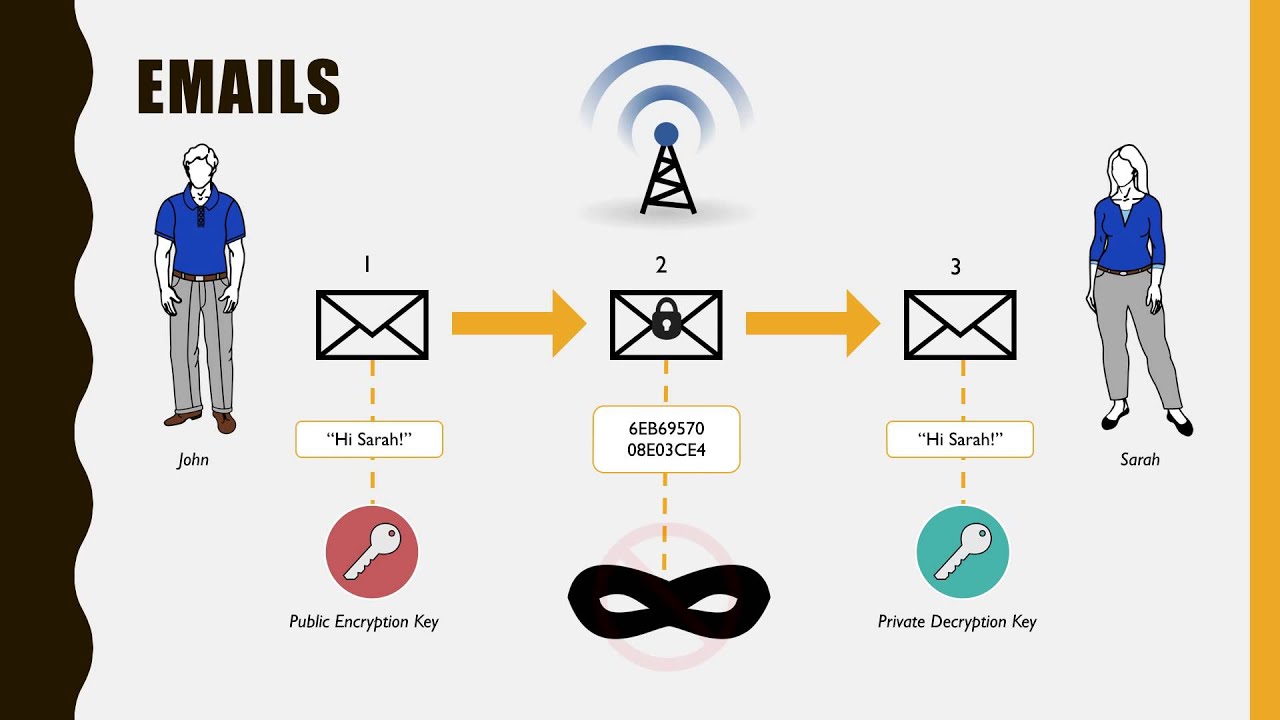
In contrast to private key encryption, Public Key Infrastructure, commonly referred to as PKI, uses two keys – one private and one public. The public key is distributed, whereas the private key is never shared.
Across the web, PKI is extremely common. For example, when you make an online purchase, you are using Secure Sockets Layer (SSL) to encrypt the web session between yourself and the site. This type of method makes use of PKI.
Private encryption is more commonly used to protect – and access – data stores, such as disk drives, confidential information and the like.
Not long ago, encryption was used exclusively to protect the information of generals, diplomats and governments. Now, all of us are accessing data sources, transferring information over the Internet, storing and accessing confidential information, sometimes on the go, sometime remotely. Encryption allows us to conduct our online business securely.
KoolSpan TrustCall utilizes PKI to secure mobile phone calls and text messages – ensuring your confidential information is always encrypted and remains secure and private. Looking for more information? Contact KoolSpan about TrustCall.
Francis Knott has over 17 years of mobility, technology, interactive media, software and healthcare experience. Mr Knott is an expert at building companies, growing revenue and launching and marketing new products. In the past, he has worked in software and product development, mobile social media, and mobile applications development.
Main 240 880-4400
Fax 240 880-4419
Sales 240 880-4400, Option 1
Int. Sales 240 880-4403
OEM Inquiries 240 880-4404
We're not around right now. But you can send us an email and we'll get back to you, asap.
I consent to KoolSpan collecting my details through this form.
Выбрать язык
русский
английский
арабский
вьетнамский
иврит
испанский
итальянский
китайский (упрощенный)
корейский
немецкий
португальский
французский
японский
We use cookies to ensure that we give you the best experience on our website. If you continue to use this site we will assume that you are happy with it.Ok
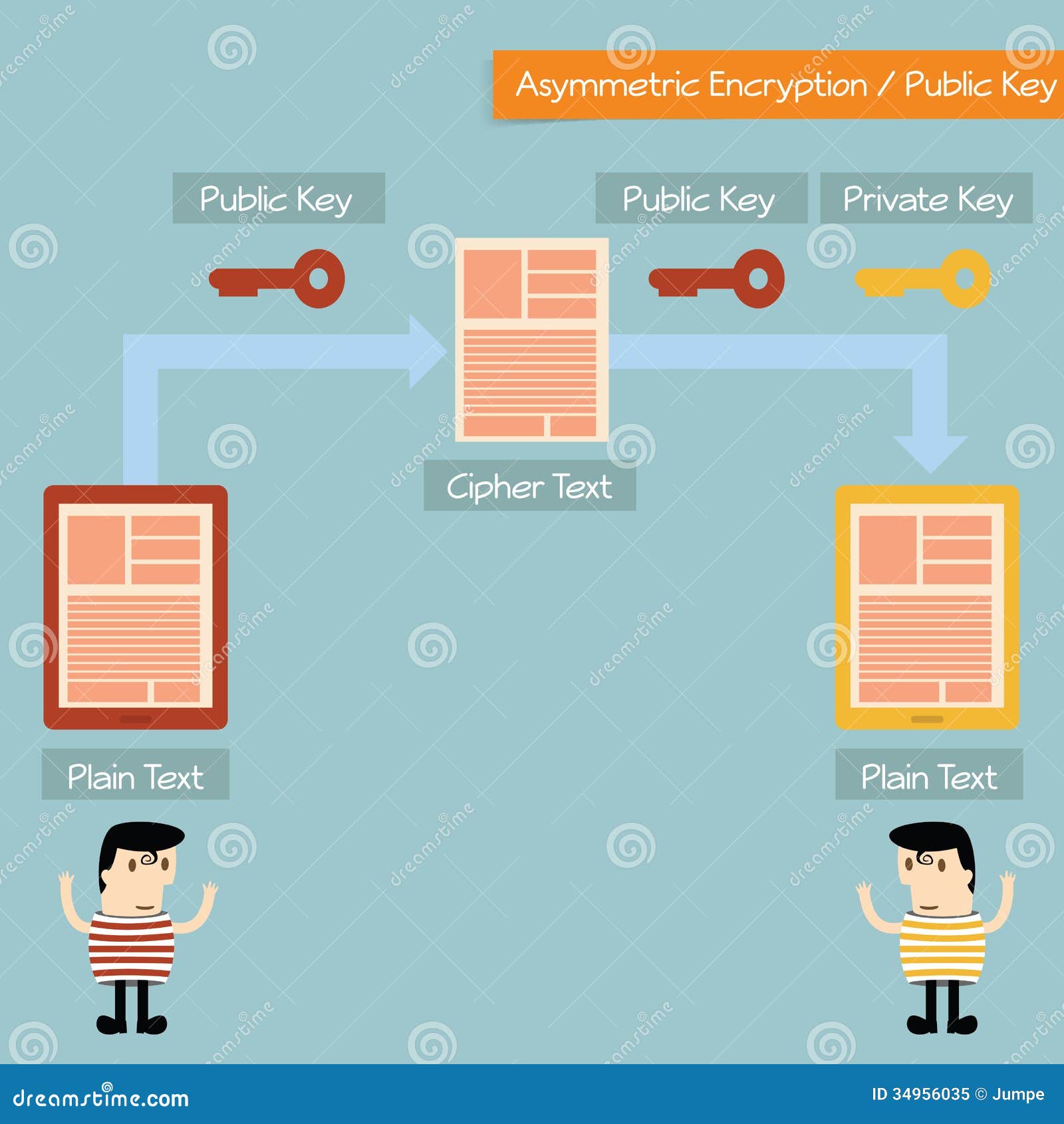
Public-key encryption systems are quite different from the popular private-key encryption systems like DES. They rely on a substantially different branch of mathematics that still generates nice, random white noise. Even though these foundations are different, the results are still the same.
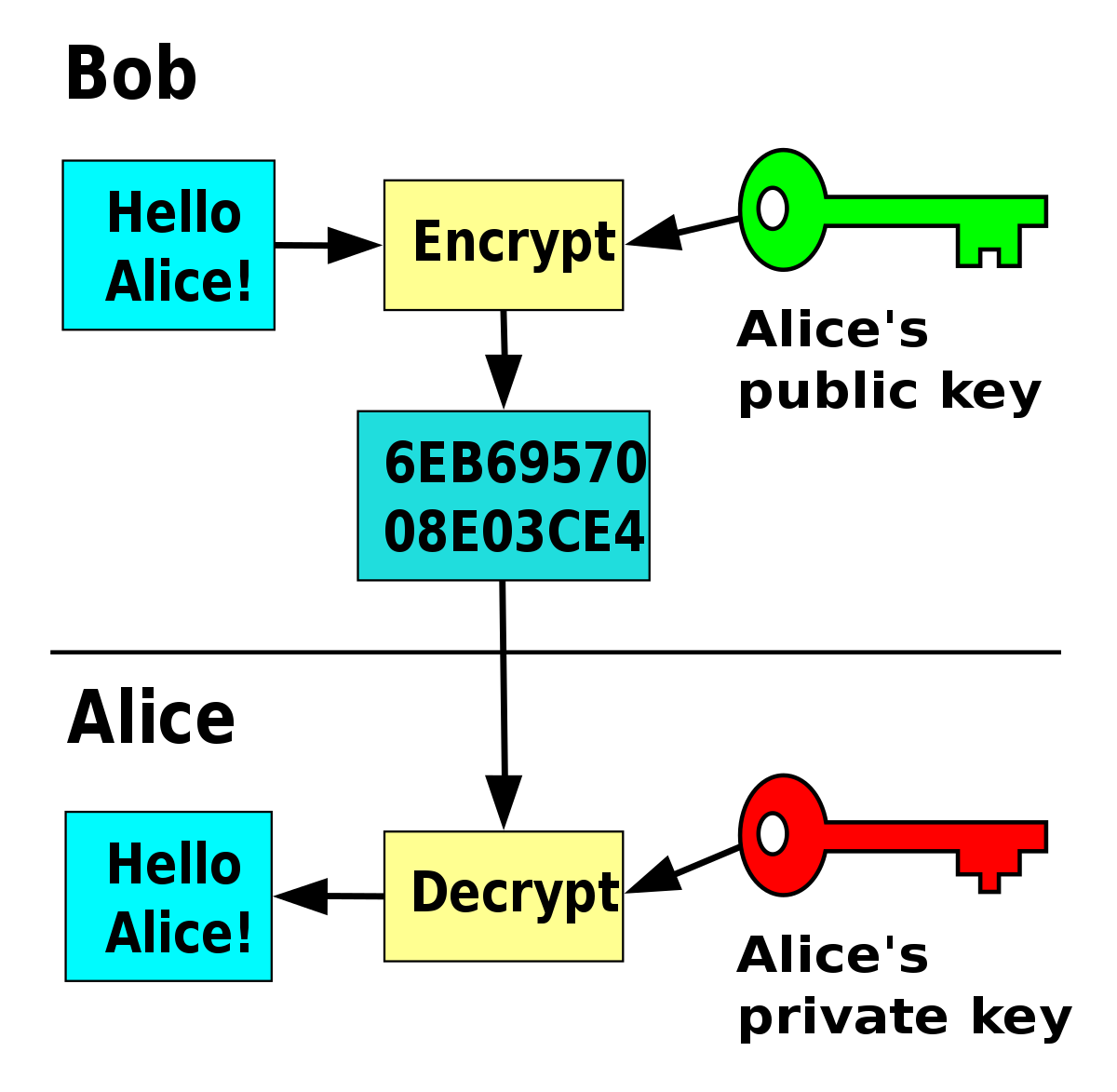
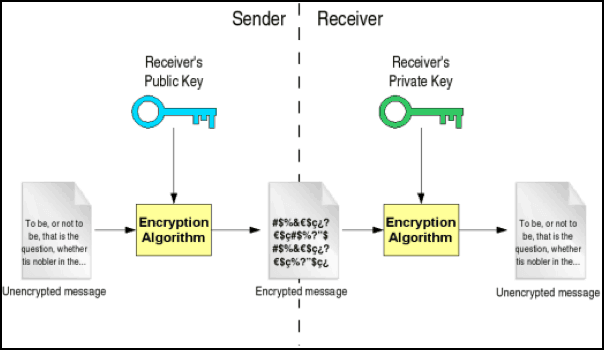
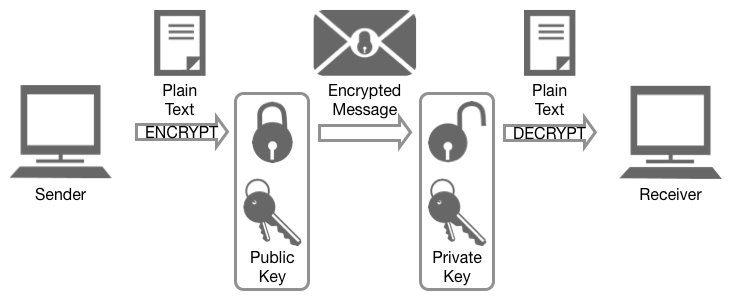
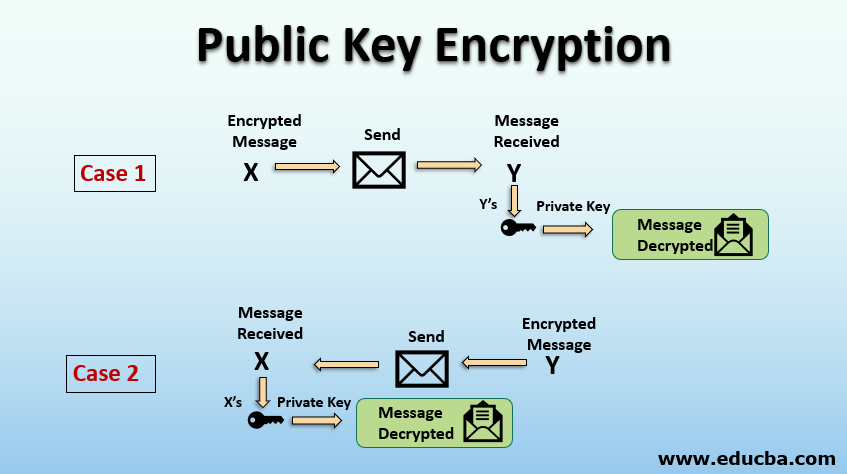
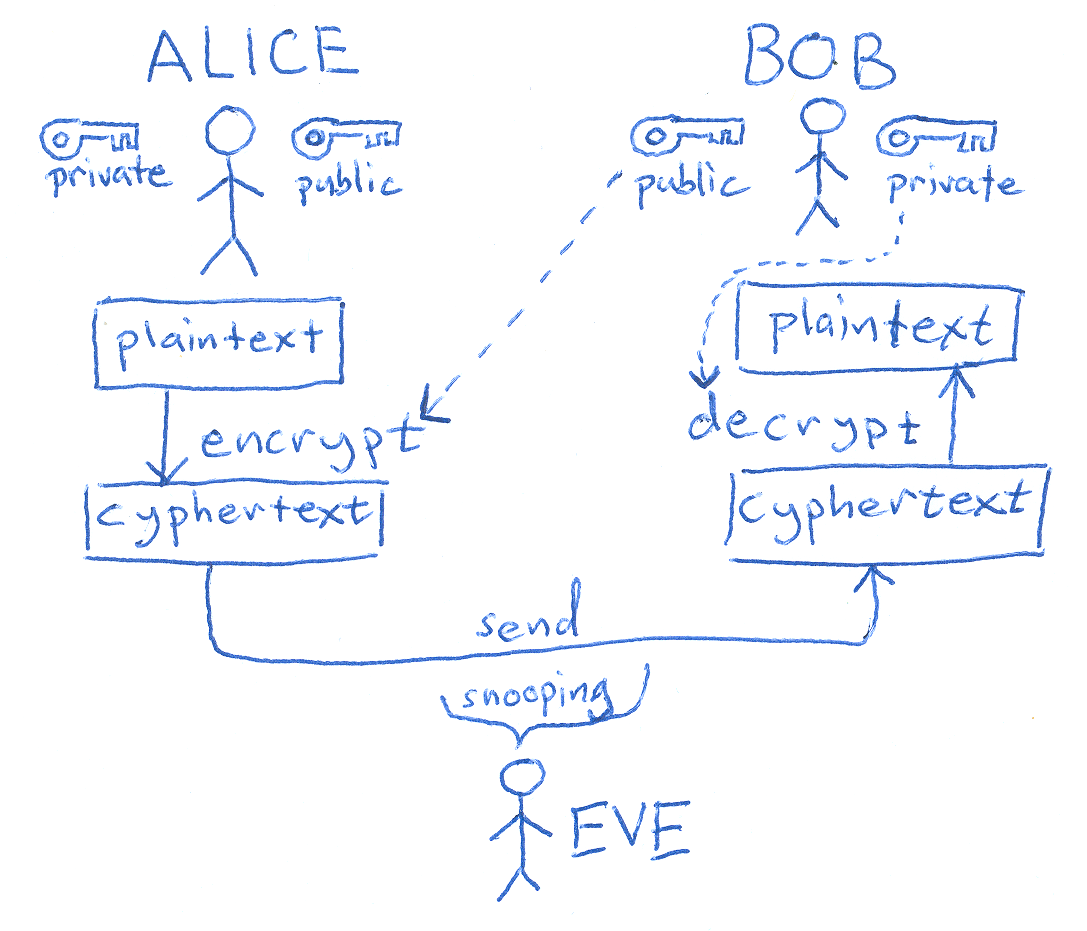
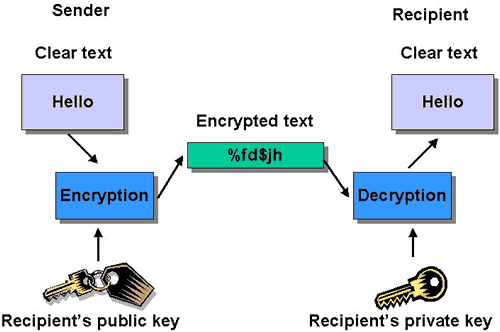
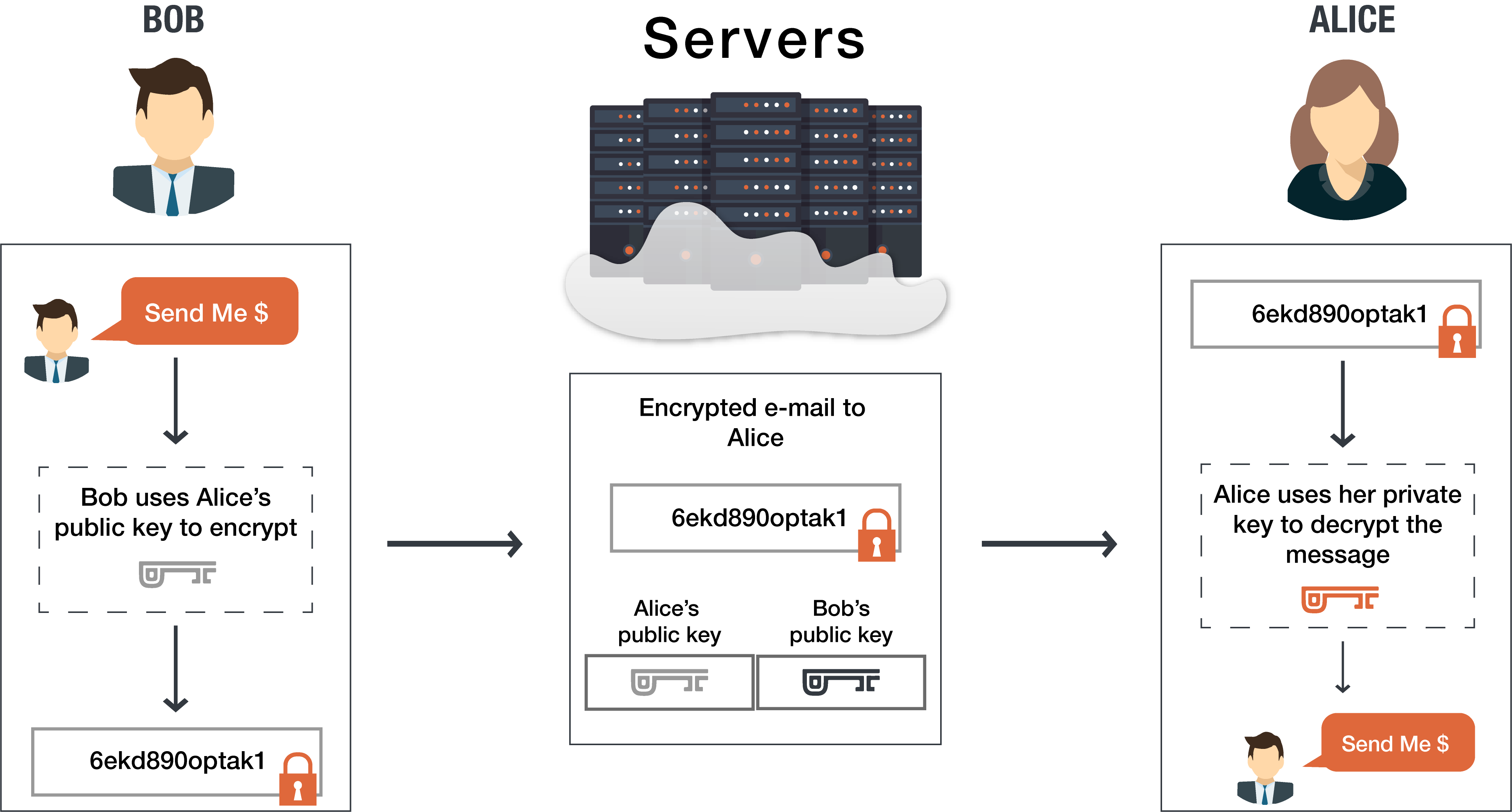
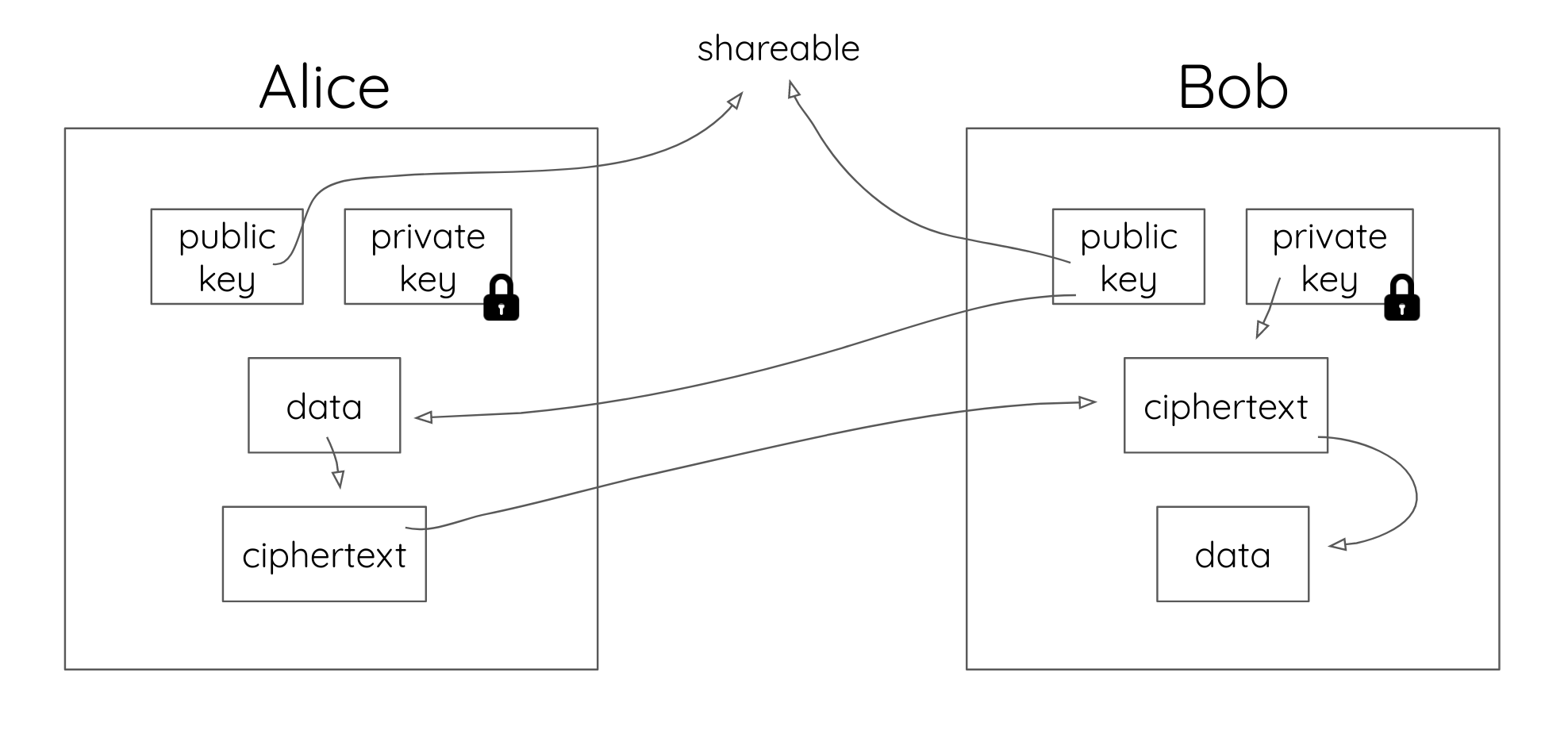
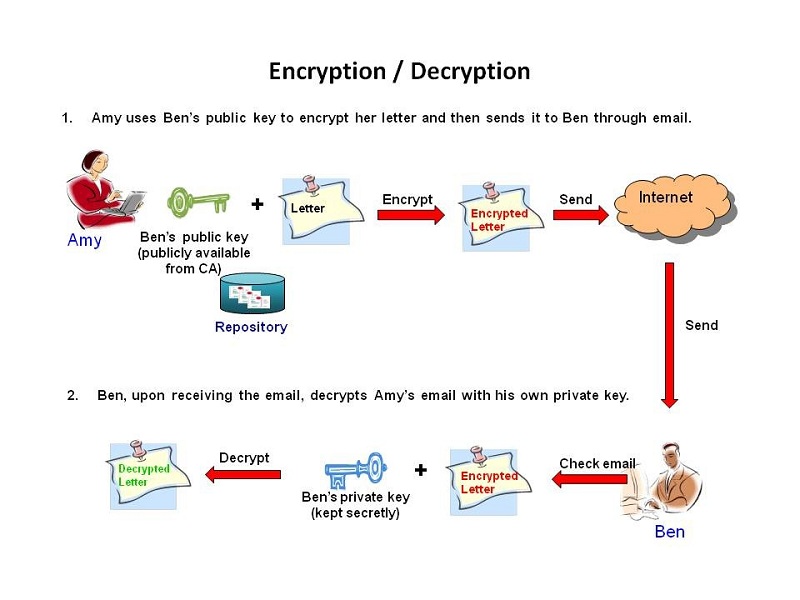
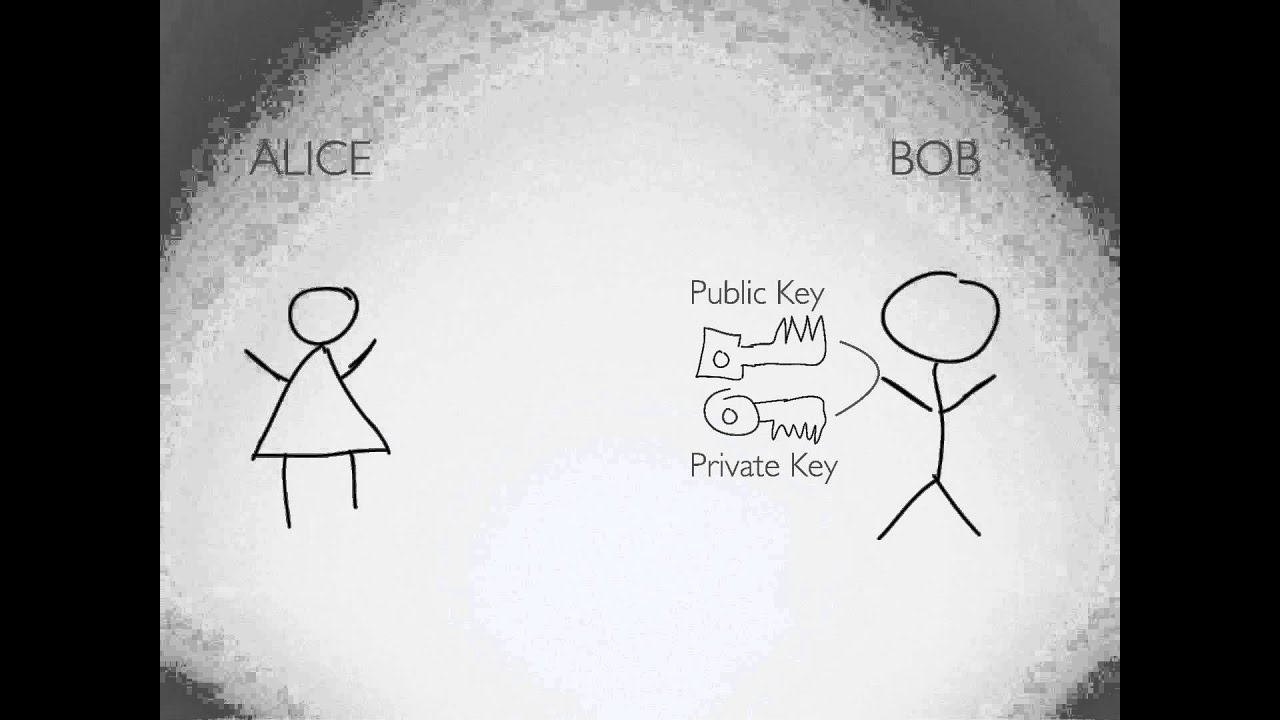
The most popular public-key encryption system is the RSA algorithm that was developed by Ron Rivest, Adi Shamir, and Len Adleman when they were at MIT during the late 1970s. Ron Rivest, Adi Shamir, and Len Adleman The system uses two keys. If one key encrypts the data, then only the other key can decrypt it. After the encryption, first key becomes worthless It can't decrypt the data. This is not a bug, but a feature. Each person can create a pair of keys and publicize one of the pair, perhaps by listing it in some electronic phone book. The other key is kept secret. If someone wants to send a message to you, they look up your public key and use it to encrypt the message to you. Only the other key can decrypt this message now and only you have a copy of it.
In a very abstract sense, the RSA algorithm works by arranging the set of all possible messages in a long, long loop in an abstract mathematical space. The circumference of this loop, call it n, is kept a secret. You might think of this as a long necklace of pearls or beads. Each bead represents a possible message. There are billions of billions of billions of them in the loop. You send a message by giving someone a pointer to a bead.
The public key is just a relatively large number, call it k. A message is encrypted by finding its position in the loop and stepping around the loop k steps. The encrypted message is the number at this position. The secret key is the circumference of the loop minus k. A message is decrypted by starting at the number marking the encrypted message and marching along the n − k steps. Because the numbers are arranged in a loop, this will bring you back to where everything began– the original message.
Two properties about this string of pearls or beads make it possible to use it for encryption. The first is that given a bead, it is hard to know its exact position on the string. If there is some special first bead that serves as the reference location like on a rosary, then you would need to count through all of the beads to determine the exact location of one of the beads. This same effect happens in the mathematics. You would need to multiply numbers again and again to determine if a particular number is the one you want.
The second property of the string of beads in this metaphor does not make as much sense, but it can still be easily explained. If you want to move along the string k beads, then you can jump there almost instantaneously. You don't need to count each of the k beads along the way. This allows you to encrypt and decrypt messages using the public-key system.
The two special features are similar but they do not contradict each other. The second says that it is easy to jump an arbitrary number of beads. The first says it's hard to count the number of pearls between the first bead and any particular bead. If you knew the count, then you could use the second feature. But you don't so you have to count by hand.
The combination of these two features makes it possible to encrypt and decrypt messages by jumping over large numbers of beads. But it also makes it impossible for someone to break the system because they can't determine the number of steps in the jump without counting.
This metaphor is not exactly correct, but it captures the spirit of the system. Figure 2.3 illustrates it. Mathematically, the loop is constructed by computing the powers of a number modulo some other number. That is, the first element in the loop is the number. The second is the square of the number, the third is the cube of the number, and so on. In reality, the loop is more than one-dimensional, but the theme is consistent.
Figure 2.3. RSA encryption works by arranging the possible messages in a loop with a secret circumference. Encryption is accomplished by moving a random amount, k, down the loop. Only the owners know the circumference, n, so they can move n − k steps down the loop and recover the original message.
URL: https://www.sciencedirect.com/science/article/pii/B9780123744791500071
As an alternative to SSL, some Web-based mail services are using Secure HTTP (S-HTTP). S-HTTP is an extension to the Hypertext Transfer Protocol. Whereas SSL operates between the session and transport layers of the OSI/RM, Secure HTTP works at the application layer. Each S-HTTP file is encrypted and can contain a digital certificate like SSL. S-HTTP does not use any single encryption system, but it does support a public-and-private key encryption system.
Both SSL and S-HTTP can be used by a browser user, but only one can be used within a given document. S-HTTP is more likely to be used in situations where the server represents a bank and requires authentication from the user that is more secure than a user ID and password. Most Web-based mail services use SSL. Currently, few use S-HTTP.
SSL uses an encryption that utilizes a 128-bit encryption. While this encryption is better than no encryption, it is still not the safest out there. There have been many documented hacks on up to 512-bit encryption. Services such as HushMail use up to 1024-bit key encryption. When using standard SSL for encryption, the email is encrypted once the Send button is hit, and then gets decoded once received by the recipient.
URL: https://www.sciencedirect.com/science/article/pii/B9781928994237500082
A PKI combines public key cryptography with digital certificates to create a secure environment where network traffic such as authentication packets can travel safely.
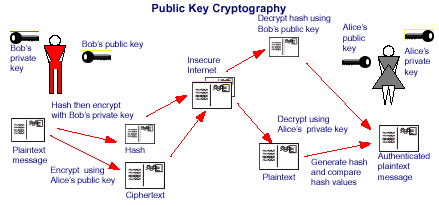
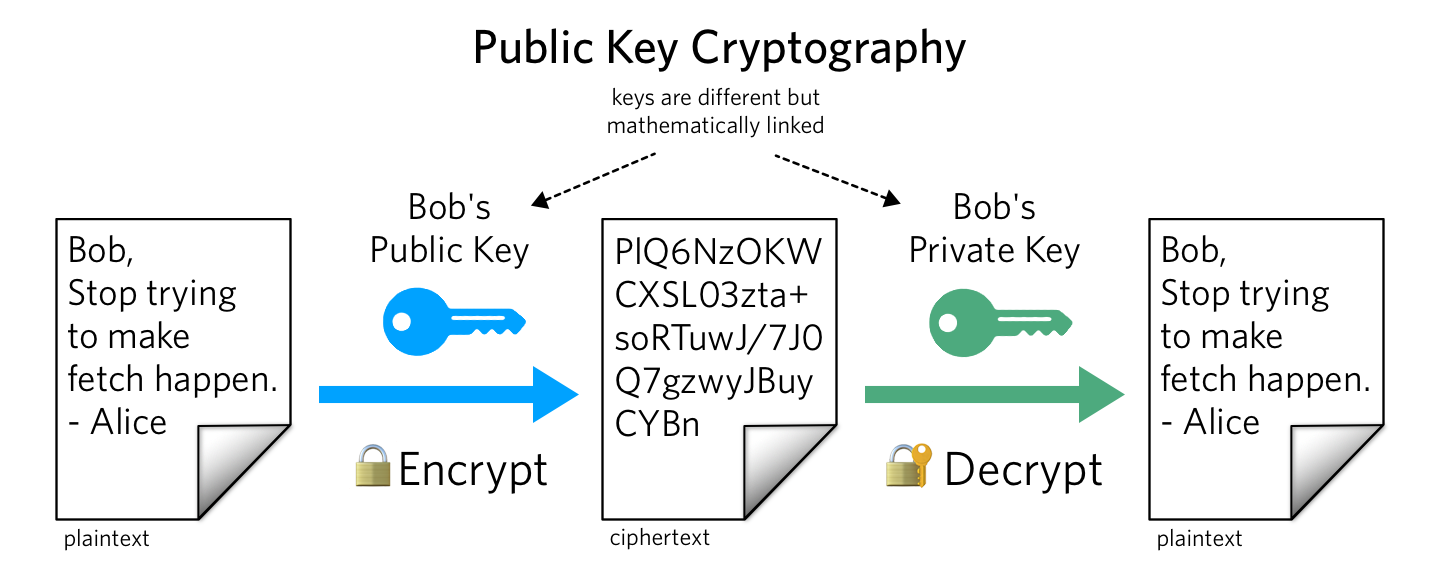
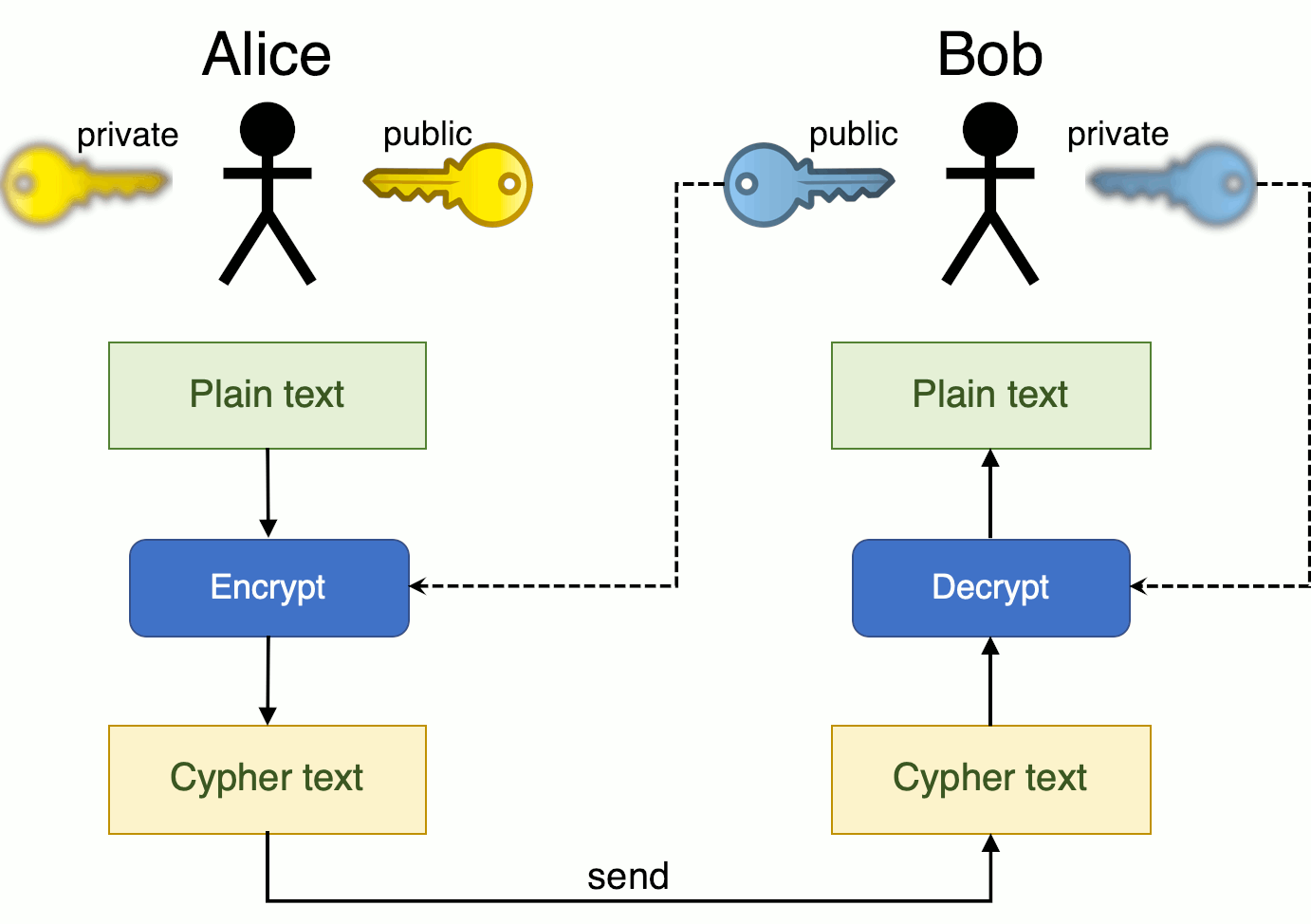
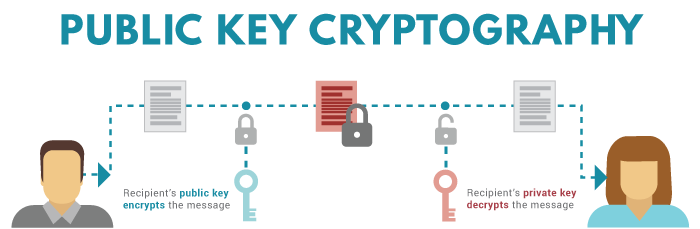
Public keys and private keys always come in pairs. If the public key is used to encrypt data, only the matching private key can decrypt it.
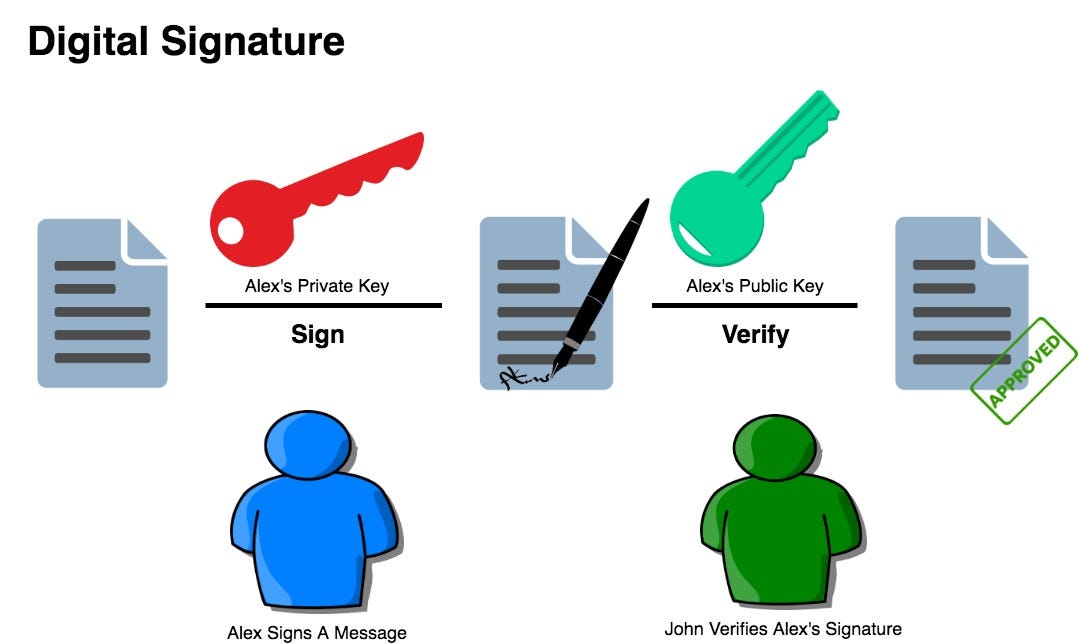
When public key-encrypted data is encrypted again by a private key, that private key encryption is called a digital signature.
Digital signatures provided by ordinary users aren't very trustworthy, so a trusted authority is needed to provide them. The authority (which can be Windows-based) issues certificates, which are basically digitally signed containers for public keys and other information.
Certificates are used to safely exchange public keys, and provide the basis for applications such as IPSec, EFS, and smart card authentication. A CA hierarchy is structured with a root and one or more level of subordinates—three levels are common. The bottom level of subordinates issues certificates. The intermediate level controls policies.
Enterprise CAs require and use Active Directory to issue certificates, often automatically. Stand-alone CAs can be more secure, and need an administrator to manually issue or deny certificate requests.
Certificate needs are based on which applications and communications an organization uses and how secure they need to be. Based on these needs, CAs are created by installing certificate services and are managed using the Certification Authority snap-in.
CAs need to be backed up consistently and protected against attacks. Keys can be archived and later retrieved if they are lost. This is a new feature for Windows Server 2008.
CAs can revoke as well as issue certificates. Once a certificate is revoked, it needs to be published to a CRL distribution point. Clients check the CRL periodically before they can trust a certificate.
URL: https://www.sciencedirect.com/science/article/pii/B978159749280500002X
John F. Buford, ... Eng Keong Lua, in P2P Networking and Applications, 2009
Cryptographic schemes offer the most effective solutions for many information security issues. They are also essential to security in P2P. Among various crypto tools, encryption and authentication are two fundamental and the most frequently used crypto primitives.
Encryption is the process of disguising a message in such a way that its content is hidden and cannot be revealed without a proper decryption key. This is a fundamental security tool that implements confidentiality with coding. Symmetric key and asymmetric key encryptions are the two types of encryption algorithms. Symmetric key encryption algorithms, also called private key encryption algorithms, are a class of encryption algorithm that uses identical keys for both encryption and decryption. Popular examples of symmetric key encryption algorithms include Data Encryption Standard (DES) and Advanced Encryption Standard (AES), which are standardized by the National Institute of Standards and Technology (NIST) and are widely adopted by many applications. Asymmetric key encryption algorithms, a.k.a. public key encryption algorithms, such as the RSA encryption algorithm, are another class of encryption algorithm that employs different keys at encryption and decryption. Note that in general, asymmetric key algorithms are much more computationally intensive than symmetric algorithms.
Encryption can play many positive roles in P2P security. It makes it difficult for attackers to carry out interception and modification classes of attack. If all confidential information is encrypted, even if some is shared or leaked over some insecure P2P file-sharing communication channels, adversaries would have a hard time decrypting the information without a proper key. The security risks will be subsequently reduced. Therefore, in the ID theft case discussed early in this chapter, the offender would not have been able to get access to others' financial information that easily. The number of victims would have been greatly reduced in that case.
Authentication, another essential security tool in computer systems, is the process of verifying whether an object is in fact who or what that object declares itself to be. A one-way hash that is nonreversible, sensitive to input changes, and collision resistant is used for authentication as well as data integrity verification. Authentication can also play many positive roles in P2P security. For example, combining secure authentication of each peer with message encryption, a P2P system can prevent eavesdropping attacks. With content authentication, information substitution and insertion attacks can not easily be realized.
URL: https://www.sciencedirect.com/science/article/pii/B9780123742148000143
Martin Grasdal, ... Dr.Thomas W. Shinder, in MCSE (Exam 70-293) Study Guide, 2003
A PKI combines public key cryptography with digital certificates to create a secure environment where network traffic such as authentication packets can travel safely.
Public keys and private keys always come in pairs. If the public key is used to encrypt data, only the matching private key can decrypt it.
When public key-encrypted data is encrypted again by a private key, that private key encryption is called a digital signature.
Digital signatures provided by ordinary users aren’t very trustworthy, so a trusted authority is needed to provide them. The authority (which can be Windows-based) issues certificates, which are basically digitally signed containers for public keys and other information.
Certificates are used to safely exchange public keys and to provide the basis for applications such as IPSec, EFS, and smart card authentication.
Certificate needs are based upon which applications and communications an organization uses and how secure they need to be. Based on these needs, CAs are created by installing certificate services and are managed using the Certification Authority snap-in.
A CA hierarchy is structured with a root and one or more level of subordinates – three levels is common. The bottom level of subordinates issues certificates. The intermediate level controls policies.
nterprise CAs require and use Active Directory to issue certificates, often automatically. Stand-alone CAs can be more secure and need an administrator to manually issue or deny certificate requests.
CAs need to be backed up consistently and protected against attacks. Keys can be archived and later retrieved if they are lost. This is a new feature for Windows Server 2003.
CAs can revoke as well as issue certificates. After a certificate is revoked, it needs to be published to a CRL distribution point. Clients check the CRL periodically before they can trust a certificate.
Templates control how a CA acts when handed a request and how to issue certificates. There are quite a few built-in templates, or you can create your own using the Certificate Template snap-in. Templates must be enabled before a CA can use them.
Certificates can be requested with the Certificates snap-in or by using Internet Explorer and pointing to http://servername/certsrv on the CA.
Machine and user certificates can be requested with no user intervention requirement by using auto-enrollment. Auto-enrollment for user certificates is new to Windows Server 2003.
Role-based administration is recommended for larger organizations. Different users can be assigned permissions relative to their positions, such as certificate manager.
Smart cards are credit card-like devices that embed a microprocessor. They can securely hold public/private keys, certificates, and other information.
Users insert smart cards into readers and enter a PIN to use information contained on the card. Authentication is the most popular application of the technology, followed by secure e-mail services.
To deploy smart cards, you need to configure the CA to issue smart card and enrollment agent certificates, set up an enrollment agent, and set up an enrollment station. Smart cards have to be enrolled, or set up with appropriate information, before someone can use one.
Smart cards are increasingly used for remote access authentication, such as over a company VPN. Cards can also be used for securely logging on to a terminal server.
URL: https://www.sciencedirect.com/science/article/pii/B9781931836937500166
We use cookies to help provide and enhance our service and tailor content and ads. By continuing you agree to the use of cookies.
Copyright © 2021 Elsevier B.V. or its licensors or contributors. ScienceDirect ® is a registered trademark of Elsevier B.V.
ScienceDirect ® is a registered trademark of Elsevier B.V.
1460 Sex Pistols
Russian Granny Pantyhose
Bbw Mega Tits
Xxx Video Lesbi Strapon
Huge Ass Mature Anal
What is Private Key Encryption? | KoolSpan
Private Key Encryption - an overview | ScienceDirect Topics
Private Key Cryptography - an overview | ScienceDirect Topics
Public and private encryption keys | PreVeil
Private-key (or Secret-key) Cryptography - CCM
Public Keys vs. Private Keys: What Is It & How Do They ...
Private Key Encryption











































.png)