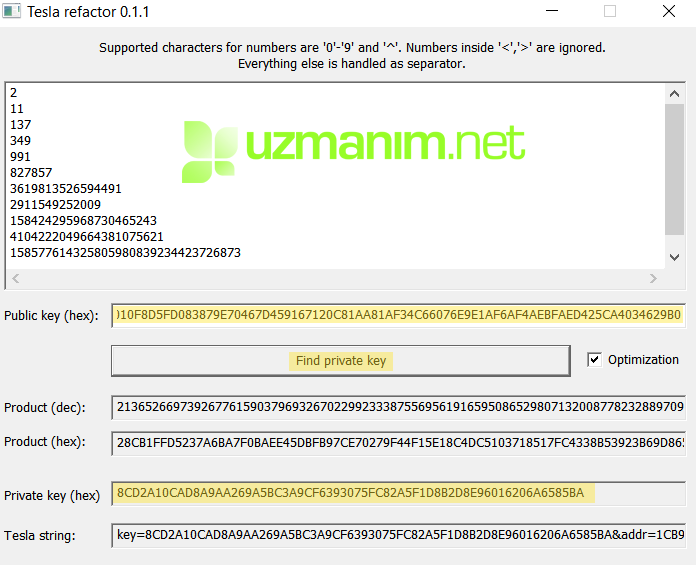
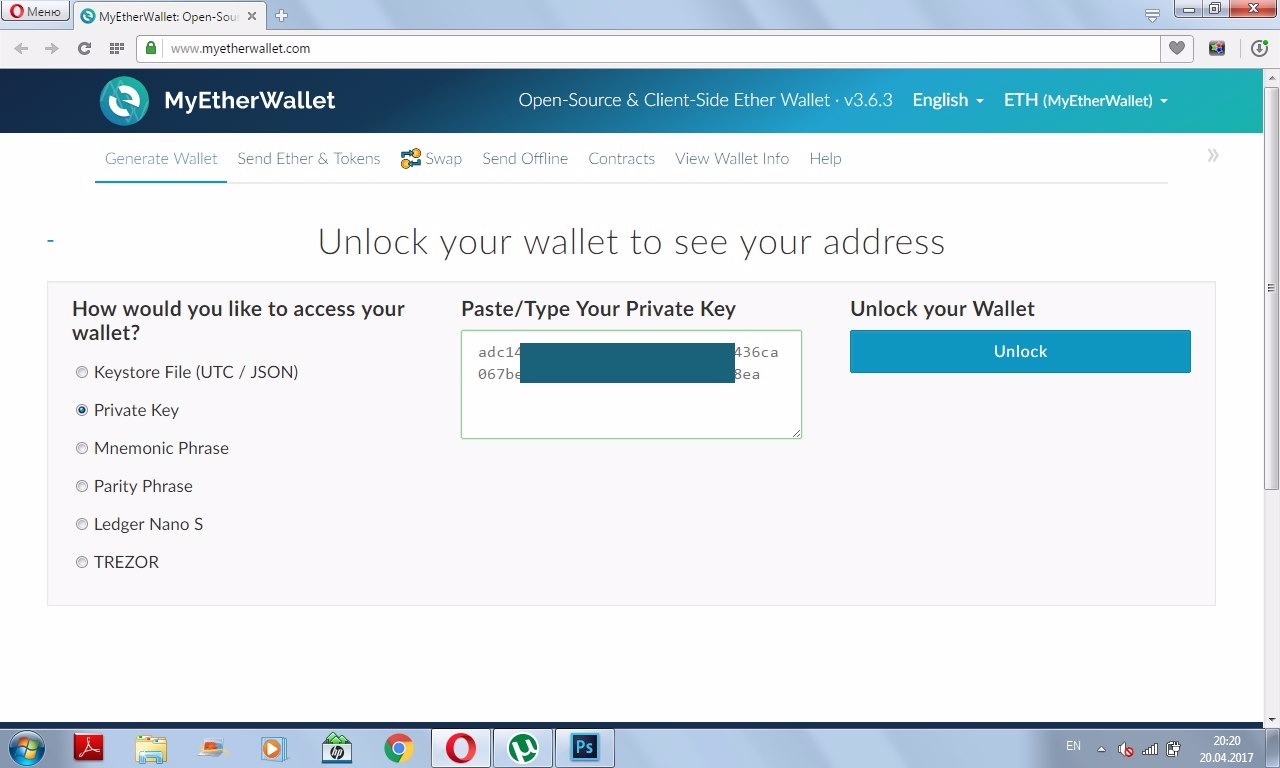
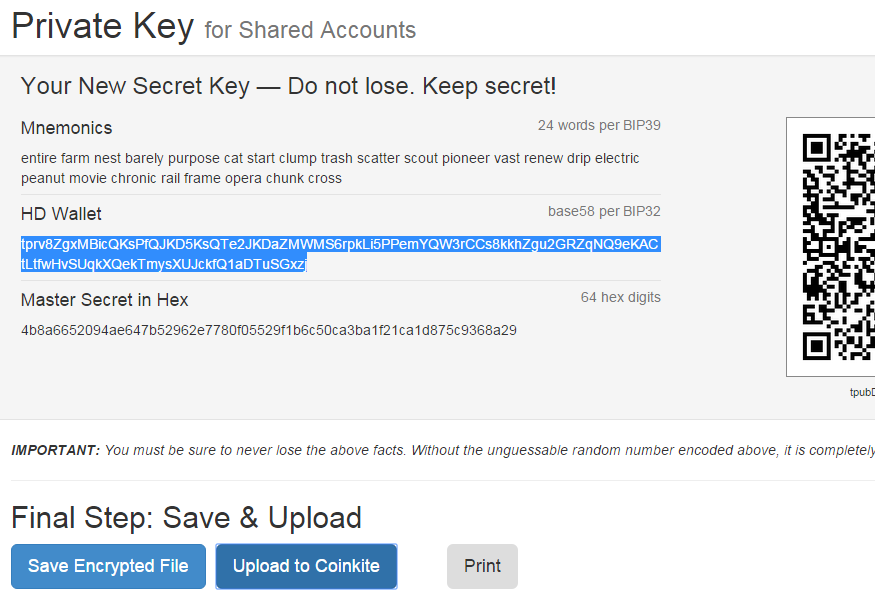
Private Key C

🛑 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Private Key C
0x49F2867812F678F7f4Ce78c8af1593ad67b1f2CA
PrivateKeys.pw is the most complete Bitcoin , Bitcoin Segwit,
Bitcoin Cash, Bitcoin SV, Ethereum, Litecoin, Dogecoin, Dash, Zcash, CLAM
private keys explorer. Our directory contains all possible
Elliptic Curve Digital Signature Algorithm (ECDSA) secp256k1 private keys in
decimal, hexadecimal, raw, and WIF formats.
For each private key we list both compressed and uncompressed public key with
Bitcoin address and balance .
Explore all private keys ,
view random private keys and
used brainwallets
or use Key Finder to
search private key with balance.
It takes a lot of computing power and money to calculate bitcoin private keys and read the blockchain.
Please donate to keep PrivateKeys.pw up: 1KEYS19ev7xLST4JTZxbpfKyrqgPLvhawr.
0fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
f9b21c4bda58a63179532e9c042abbe99dbd276e70e159b304efd58ed0c7a2e3
investment
Generating Public/ Private Keys In C # And .NET
Bitcoin Private Keys Directory
RSA Library with Private Key Encryption in C # - CodeProject
PrivateKey C # Reference Documentation
C # JWT ecdsa import private key · Issue #25 · dvsekhvalnov/jose-jwt
RSA Library with Private Key Encryption in C#
RSA encryption library with full OAEP padding and private key encryption support
This article discusses the RSA encryption library with full OAEP padding and private key encryption support.
Screenshot 2: Test and Performance Window
You must Sign In to use this message board.
Spacing
Relaxed Compact Tight
Layout
Normal Open Topics Open All Thread View
Per page
10 25 50
Article Copyright 2012 by Arpan Jati Everything else
Copyright © CodeProject , 1999-2021
Web04
2.8.20210202.1
RSA is one of the most important Public key cryptographic algorithms which is keeping the web alive. From secure transactions, secure mail to authentication and certificates, its use is universal.
The basic design of RSA is very simple and elegant and uses simple mathematical operations, yet it is very strong. If used properly, it is nearly impossible to break, given the mathematical complexity of the factoring problem.
The .NET Framework provides native support for RSA and it is pretty useful for most of the purposes. But, for certain cases like some signature schemes, we may require to perform 'private key encryption', which is not natively supported. So, for a project, I had to implement the RSA encryption and decryption from scratch. And, as without proper padding this scheme is vulnerable to attacks, I have also implemented OAEP and PKCS v1.5 padding schemes. This library (RSAx) is fully compatible with the .NET Framework's implementation of RSA.
RSA being a public key crypto-system has two keys, the Public key and the Private key. The Encryption is done using one and the decryption is done using the other. Normally, the encryption is done using the Public key and the decryption is done using the Private key. The RSA modulus (explained below) length is called the key length of the cipher. The currently largest factored prime number had 768 bit. As the security of RSA depends on the factoring problem, using a modulus of 1024 bits is a bare minimum. It is recommended to use at least 2048 bits for good security. 4096 bit is pretty much unbreakable, anything beyond 4096 bits is over the top and would also be painfully slow.
The most critical part of the RSA encryption is the padding scheme. A padding scheme is normally used to increase the length of the plain-text in such a way, that a symmetric algorithm can use it. But, even though the RSA can work without a padding scheme, it is critical for the security of the data, as without proper padding, the cipher-text becomes vulnerable to many different attacks. The padding schemes also brings a randomness to the encrypted data. Every time the data is encrypted, the cipher-text is different, but after decryption, the plain-text remains the same.
There are two major padding schemes in general use, the PKCS and OAEP (Optimal Asymmetric Encryption Padding). PKCS is very simple and is still widely used being an older standard, but, is vulnerable to some newer attacks. OAEP was designed by Bellare and Rogaway to prevent these attacks and is currently recommended for use. But, OAEP is a little complex to implement. I will try to explain the OAEP padding scheme in some detail.
Before encoding, the Hash and the parameter array has to be fixed. For most purposes, the parameter string is an empty byte array. Normally, three different types of hashes are defined by the standard. SHA1, SHA256 and SHA512. SHA1 is default hashing algorithm. Its important that the parameter array and hash algorithm remains same during decoding, otherwise the decoding should fail.
That's all. The encoded message is simply encrypted using RSA.
The decoding process is just the opposite of the encoding. Because, the length of the maskedSeed is known, we can easily separate the maskedSeed and maskedDB .
seedMask is generated from maskedDB using MGF , the generated seedMask is XORed with the maskedSeed to get the Seed .
The Seed is expanded using MGF to get dbMask .
dbMask and maskedDB are XORed together to get the DB.
We can easily obtain pHash and M from DB , because the length of pHash is known and the M starts after a sequence of ' 0 's followed by a 1 .
If pHash matches with the Hash of the parameter array during decryption, the M is returned as the result. Otherwise, the process fails.
It is important that the decoding algorithm does not allow the user to know the exact nature of the error, otherwise some attacks can be mounted.
The whole point of the OAEP scheme is to make sure that even 1 bit error in decryption renders the complete packet worthless. This is made sure by the hashes, as even a single bit change causes a complete change in the output bits.
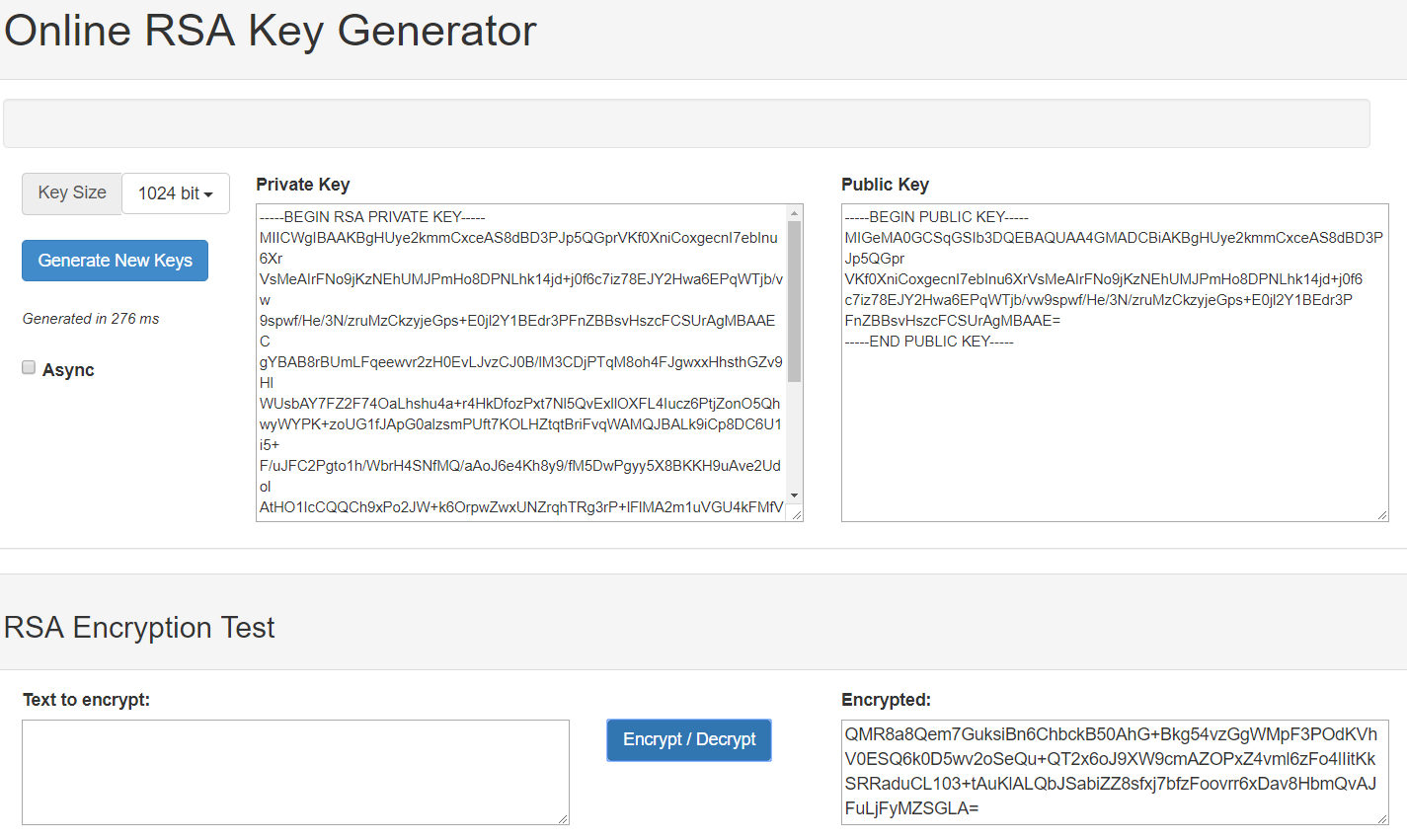
Showing a test Application for the RSAx library. Any combination of encryption and decryption is allowed, using both Public and Private keys. I have tested the library with keys up to 8192 bits in length. Make sure that different keys (Public and Private) is used for different (Encryption and Decryption) operations, otherwise the decryption will not work properly. While using OAEP, make sure to use the same Hash Algorithm in case of a single Encryption and Decryption. Make sure to Perform File->'Generate Key Pair' after changing the modulus size, for the program to work properly.
I've implemented a basic test bench to verify the functioning of the library. It simply encrypts and decrypts random data and verifies the outcome with the expected result. It uses the settings from the previous tab.
Using the library is pretty straightforward.
The RSAx class can be created from an XML string similar to the native .NET counterpart. It can also be created by using a RSAxParameters class which allows to manually specify the public and the private key parts.
It can also be created from a System.Security.Cryptography.RSAParameters structure.
Private key encryption and Public key decryption can be done as follows:
Writing the code was pretty straightforward. One interesting thing I found out was that there's a GetNonZeroBytes() function provided in the
System.Security.Cryptography. RNGCryptoServiceProvider class, pretty neat! I was just wondering about the internal implementation; if the resultant byte array contains of all non-zero bytes, won't there be some bias in the randomness?
Another thing I realized is that sometimes the RFCs [ http://tools.ietf.org/html/rfc3447 ] are the only source of information about some protocol or algorithm and we have to keep reading it again and again until we understand the whole thing in its entirety.
Sometimes, after the last step of CRT-RSA, the result in the BigInteger was coming negative. And, this negative result plays havoc on the decrypted result. To fix this, I applied a simple hack. Whenever the result is negative, simply add the Modulus N to the result, in order to bring the result back to positive. This is trivial, but it fixed the problem completely.
This article, along with any associated source code and files, is licensed under The Code Project Open License (CPOL)
General News Suggestion Question Bug Answer Joke Praise Rant Admin
Use Ctrl+Left/Right to switch messages, Ctrl+Up/Down to switch threads, Ctrl+Shift+Left/Right to switch pages.
Last Visit: 31-Dec-99 19:00 Last Update: 2-Feb-21 19:37
Girl 13 Naked
Double Penetration Porno Hd
Stockings Double Penetration Porno
Private 1.6
Double Vaginal Penetration Porn