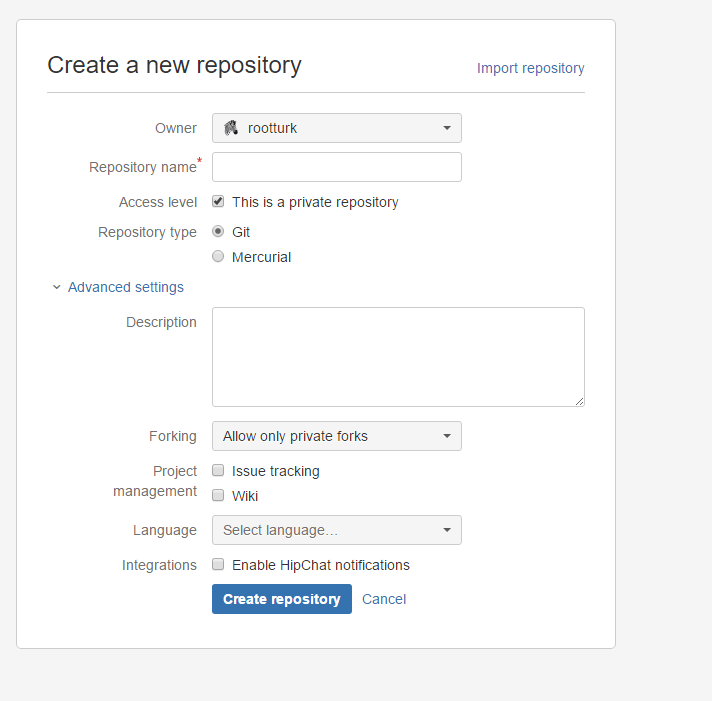
Private Git Repository

💣 👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
August 31, 2017 | by Graham Dumpleton
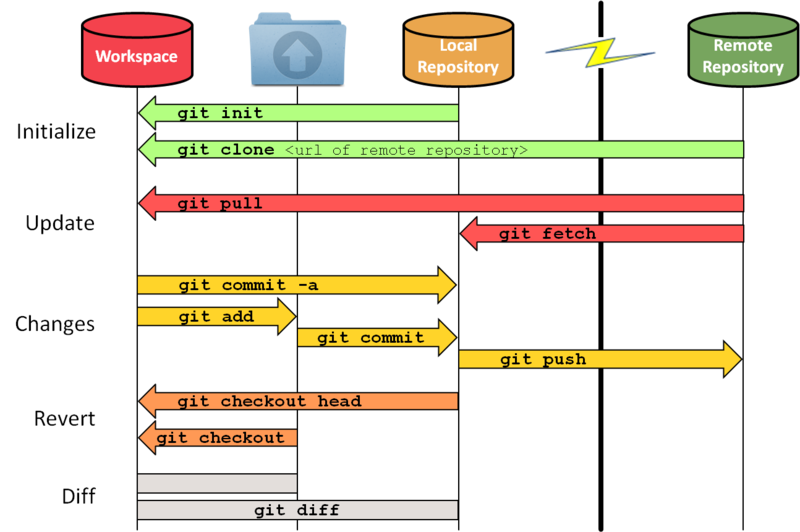
When you deploy applications to OpenShift from source code, you will typically provide the source code by specifying a URL to a repository managed by a Git hosting service such as GitHub, GitLab or Bitbucket. When the build process runs to create the image for your application, the first step will be to pull down the source code from that hosted Git repository.
If the hosted Git repository is publicly accessible, there is nothing else to do. If, however, you want to use a private Git repository, you will need to provide to OpenShift access credentials which the build process can use when accessing the Git repository.
The principles of using private Git repositories with OpenShift have been covered in a number of prior posts:
These looked at key generation and setting up a build configuration to use it, however, beyond these basics there are additional features in OpenShift which make using private Git repositories easier. There are also various best practices you can adopt to ensure you are using the most secure mechanism possible, without risking your most important access credentials.
In this series of posts I will look again at the topic of accessing private Git repositories, but explore new and more recommended ways of using OpenShift, and hosting services such as GitHub, GitLab, and Bitbucket, to best secure access to your source code.
To access a hosted Git repository, a number of different protocol types are supported.
For more information about communicating with a Git repository using these protocols see the hosted version of the Pro Git book.
When accessing a repository, Git repository hosting services such as GitHub, GitLab, and Bitbucket support using both the HTTPS and SSH protocols. The terminology for each can vary, but the credential types offered by these hosting services then fall into the following categories:
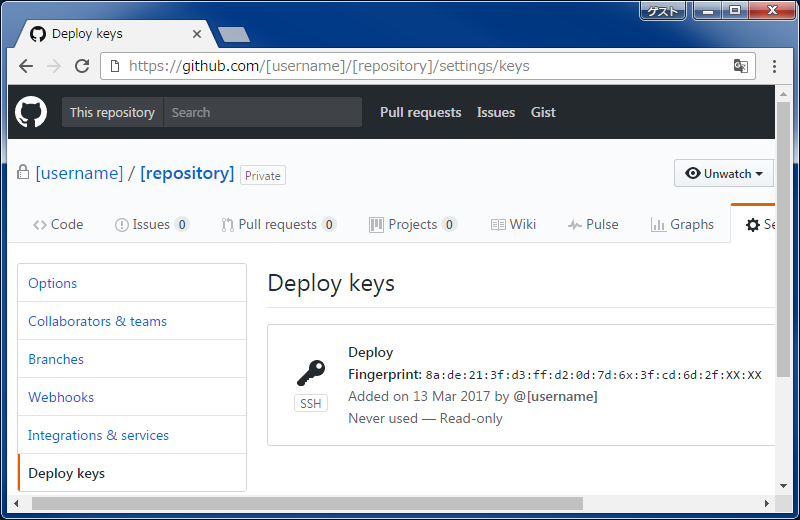
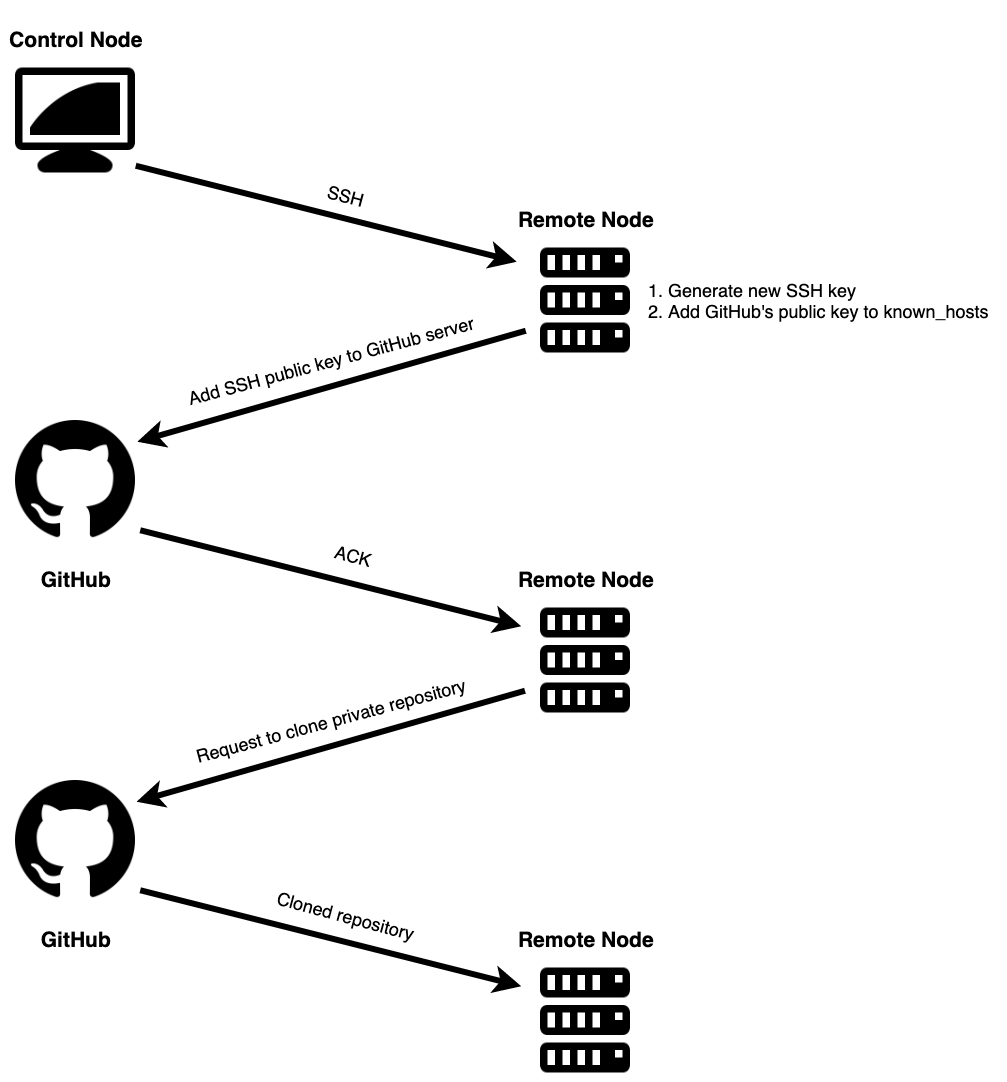
When using a private Git repository with OpenShift, you should always aim to use a unique repository SSH key and ensure it has read-only access to the repository. This is because you will need to upload the private key of the key-pair to OpenShift.
When setting up a repository SSH key you should not use your primary identity SSH key. This is because you should never upload its private key to a system you do not control or which can be accessed by others. Using a primary identity key carries additional risk as it is likely used for other purposes, such as gaining secure shell access over SSH to other hosts. If someone were able to get the private key, they could access those other systems.
One saving grace is that OpenShift will not allow you to use a key-pair where the private key has a passphrase. A best practice, which I am sure you are following, is that your primary identity SSH key should always have a passphrase; this will prevent you from inadvisedly using your primary identity SSH key.
So repository SSH keys and accessing a repository over the SSH protocol is the preferred method of accessing a repository. One situation where this will not work though is where the OpenShift instance you are using sits behind a firewall, and that firewall blocks SSH connections to an external Git hosting service.
In this situation, you would have to fallback to using a personal access token over a HTTPS connection. Although the access rights of personal access tokens can be limited to read-only access, they cannot be linked to just a single repository and could be used with any repository accessible to the user account. If you are deploying a personal project to OpenShift, this may be acceptable. However, if this were a project of your company hosted on the hosting service under an organization, you should not rely on using a personal access token of a specific developer. If that developer were to leave you now have the problem that your builds are linked to that developer's account and they could revoke the access token and break the builds. The developer also puts themselves at risk, as the access token could be used to access other private repositories they have which are not related to their work at the company.
If you cannot use the SSH protocol and must use a personal access token with the HTTPS protocol, for a company it would be better to create a separate machine user account on the Git repository hosting service and use it as the owner of the personal access token.
In this post we have covered the different protocols and credential types you can use to access a hosted Git repository, as well as listed some best practices around the credential type used. In the next post in this series, we will look at setting up a repository SSH key, using the GitHub hosting service as an example.
Access the rest of the series here:
The new Multi-Instance GPU (MIG) feature lets GPUs based on the NVIDIA Ampere architecture run multiple GPU-accelerated CUDA applications in parallel in a fully isolated way. The compute units of the ...
Traditionally, the creation of a Red Hat OpenShift on AWS (ROSA) cluster required an Identity and Access Management (IAM) user with elevated permissions. However, with the implementation of the ...
Building a Metro HA Postgres Cluster with OpenShift Data Foundation Getting your database-backed application up and running on OpenShift is straightforward, but what about deploying a ...
How we use cookies
We use cookies on our websites to deliver our online services. Details about how we use cookies and how you may disable them are set out in our Privacy Statement. By using this website you agree to our use of cookies.
This chapter build is in progress, expect to change and not working as expected
At the end of this chapter you will be able to :
How to push linux contianer image to external registry
How to clone from a private Github respository
In many parctical usecase you might need to pull from private Git repsoitories or might need to push to external container registry such as Quay.io. In both the cases the access requires you to authenticate. With Tekton this is achieved using the Kubernetes Service Account(SA) and Kubernetes Secret.
If you are not in tutorial chapter folder, then navigate to the folder:
cd $TUTORIAL_HOME/private_repos_reg
Let us create a new namespace called workspace-auth-demo and switch to that namespace context.
It is assumed that you have completed Workspaces and the reusing the same namespace that was prepared in that chapter.
You have container registry account with Quay.io or Docker Hub
You have GitHub account and a private repository
In this exercise we will see how to pull i.e. clone the source code from the private source reporsitory. For this example we will use the GitHub as the remote source repository.
To be able to run this exercise you need:
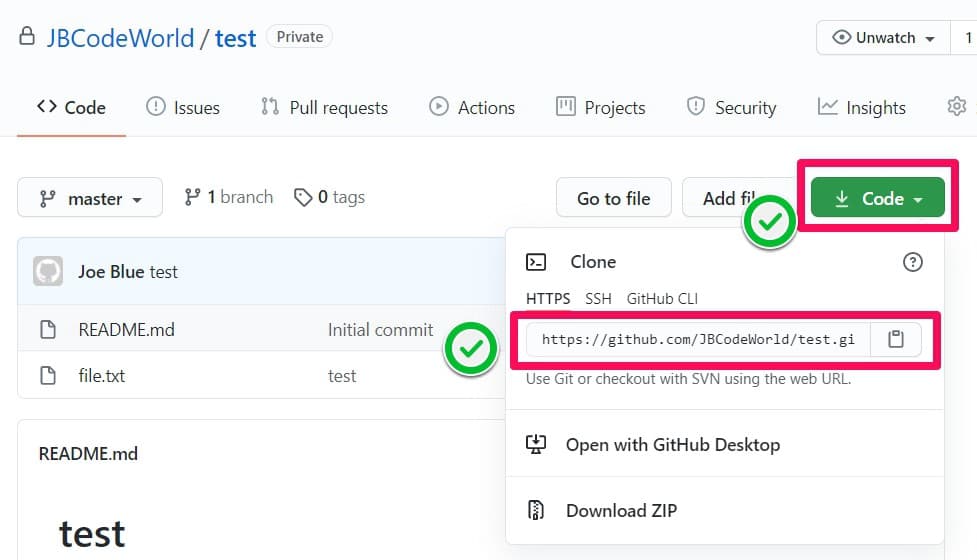
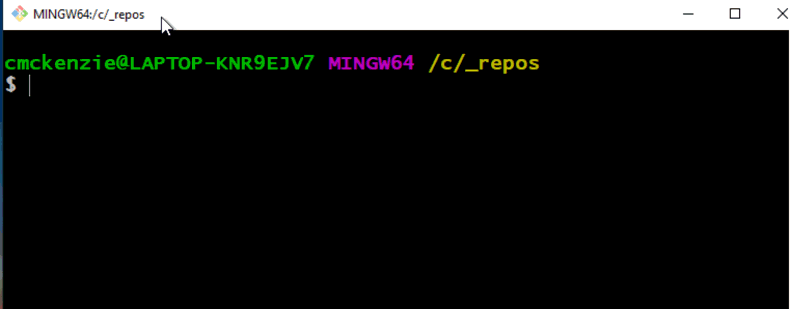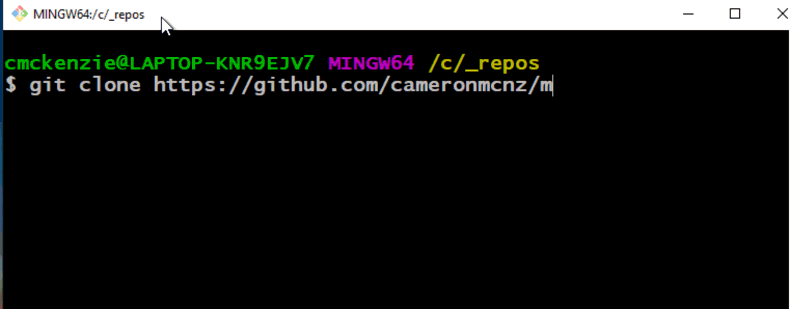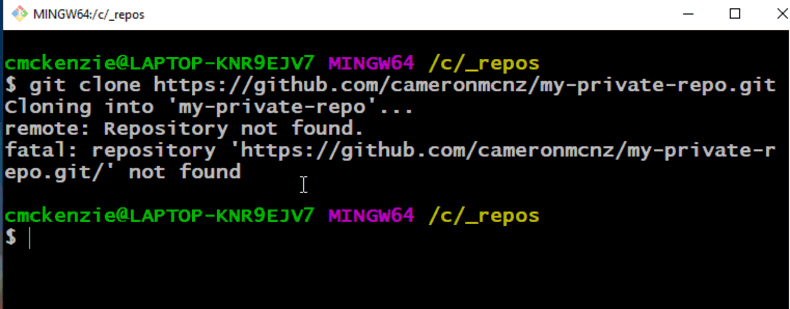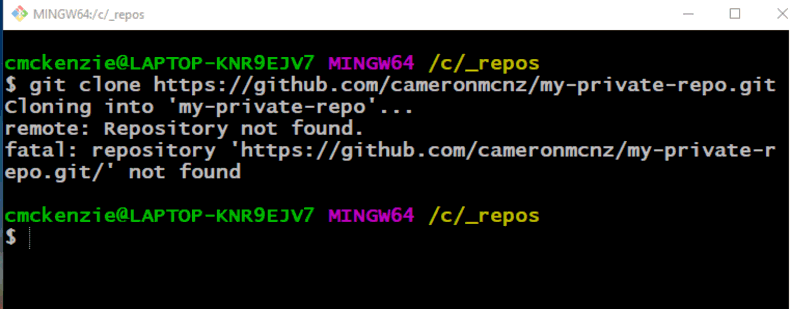
A remote GitHub Repository, you can pull fork the https://github.com/redhat-scholars/tekton-tutorial-greeter and push that as your private repository
A GitHub Personal Access Token(PAT) to access the remote repository.
Set the requried environment variables to be used when creating the github-pat-secret:
export GITHUB_USERNAME=''
export TEKTON_TUTORIAL_GITHUB_PAT=''
Create the Kubernetes secret that can hold your GitHub.com credentials:
kubectl create secret -n workspace-auth-demo generic github-pat-secret --dry-run=client -o yaml \
| yq w - type kubernetes.io/basic-auth \
| yq w - stringData.username $GITHUB_USERNAME \
| yq w - stringData.password $TEKTON_TUTORIAL_GITHUB_PAT \
| kubectl apply -f -
To make Tekton use the Secret github-pat-secret with github.com, we need to annotate the Secret with tekton.dev/git-0=https://github.com.
kubectl annotate -n workspace-auth-demo secret github-pat-secret \
"tekton.dev/git-0=https://github.com"
Verify the github-pat-secret as right type, annoations and credential values:
kubectl get -n workspace-auth-demo secret github-pat-secret -o yaml
The command should show an output(trimmed for brevity) as shown in the following listing, with your GitHub.com username and PAT.
apiVersion: v1
data:
password: REDACTED
username: REDACTED
kind: Secret
metadata:
annotations:
tekton.dev/git-0: https://github.com
name: github-pat-secret
namespace: workspace-auth-demo
type: kubernetes.io/basic-auth
Let us create a Kubernetes ServiceAccount that could be used pull from the private GitHub repository:
kubectl create sa -n workspace-auth-demo github-bot
Now patch the github-bot service account to use the github-pat-secret credentials:
kubectl patch serviceaccount github-bot \
-p '{"secrets": [{"name": "github-pat-secret"}]}'
Lets verify if the service account has the secret added:
kubectl get sa -n workspace-auth-demo github-bot -o yaml
The command should show an output(trimmed for brevity) like:
apiVersion: v1
kind: ServiceAccount
metadata:
name: github-bot
namespace: workspace-auth-demo
secrets:
- name: github-pat-secret
- name: github-bot-token-9p2wg
Create the git clone pipeline which will clone from the private GitHub repo and simply list the contents:
kubectl apply -n workspace-auth-demo -f secretworld-app-clone.yaml
pipeline.tekton.dev/secretworld-app-clone created
tkn pipeline start secretworld-app-clone \
--namespace=workspace-auth-demo \
--serviceaccount=github-bot \
--param private-github-repo-url='https://github.com/redhat-scholars/tekton-secretworld' \
--workspace name=source,claimName=tekton-tutorial-sources \
--use-param-defaults \
--showlog
Ensure that the pipeline run has been set to run with the Service Account github-bot
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: secretworld-app-clone-
labels:
tekton.dev/pipeline: secretworld-app-clone
spec:
serviceAccountName: github-bot (1)
pipelineRef:
name: secretworld-app-clone
params:
- name: private-github-repo-url
value: https://github.com/redhat-scholars/tekton-secretworld
workspaces:
- name: source
persistentVolumeClaim:
claimName: tekton-tutorial-sources
Please make sure you have updated the private GitHub repository to match your private repository
kubectl create -n workspace-auth-demo -f secretworld-app-clone-run.yaml
tkn pr logs -f -a $(tkn pr ls -n workspace-auth-demo | awk 'NR==2{print $1}')
A successful clone from private repo will show the following output ( trimmed brevity):
[clone-sources : credential-initializer] {"level":"info","ts":1595922122.9077983,"caller":"creds-init/main.go:44","msg":"Credentials initialized."}
[clone-sources : clone] + CHECKOUT_DIR=/workspace/output/
[clone-sources : clone] + '[[' true '==' true ]]
[clone-sources : clone] + cleandir
[clone-sources : clone] + '[[' -d /workspace/output/ ]]
[clone-sources : clone] + rm -rf /workspace/output//Dockerfile /workspace/output//README.md /workspace/output//k8s /workspace/output//mvnw /workspace/output//mvnw.cmd /workspace/output//pom.xml /workspace/output//src
[clone-sources : clone] + rm -rf /workspace/output//.dockerignore /workspace/output//.git /workspace/output//.gitignore /workspace/output//.mvn
[clone-sources : clone] + rm -rf '/workspace/output//..?*'
[clone-sources : clone] + test -z
[clone-sources : clone] + test -z
[clone-sources : clone] + test -z
[clone-sources : clone] + /ko-app/git-init -url https://github.com/redhat-scholars/tekton-secretworld -revision master -refspec -path /workspace/output/ '-sslVerify=true' '-submodules=true' -depth 1
[clone-sources : clone] {"level":"info","ts":1595922137.4565356,"caller":"git/git.go:139","msg":"Successfully cloned https://github.com/redhat-scholars/tekton-secretworld @ 5250e1fa185805373e620d1c04a0c48129efd2ee (grafted, HEAD, origin/master) in path /workspace/output/"}
[clone-sources : clone] {"level":"info","ts":1595922137.4990256,"caller":"git/git.go:180","msg":"Successfully initialized and updated submodules in path /workspace/output/"}
[clone-sources : clone] + cd /workspace/output/
[clone-sources : clone] + git+ tr -d '\n'
[clone-sources : clone] rev-parse HEAD
[clone-sources : clone] + RESULT_SHA=5250e1fa185805373e620d1c04a0c48129efd2ee
[clone-sources : clone] + EXIT_CODE=0
[clone-sources : clone] + '[' 0 '!=' 0 ]
[clone-sources : clone] + echo -n 5250e1fa185805373e620d1c04a0c48129efd2ee
[list-cloned-repo : credential-initializer] {"level":"info","ts":1595922139.7837844,"caller":"creds-init/main.go:44","msg":"Credentials initialized."}
[list-cloned-repo : list-directory] total 44
[list-cloned-repo : list-directory] drwxr-xr-x 4 root root 4096 Jul 28 07:42 src
[list-cloned-repo : list-directory] -rw-r--r-- 1 root root 4147 Jul 28 07:42 pom.xml
[list-cloned-repo : list-directory] -rwxr-xr-x 1 root root 6607 Jul 28 07:42 mvnw.cmd
[list-cloned-repo : list-directory] -rwxr-xr-x 1 root root 10069 Jul 28 07:42 mvnw
[list-cloned-repo : list-directory] drwxr-xr-x 2 root root 4096 Jul 28 07:42 k8s
[list-cloned-repo : list-directory] -rw-r--r-- 1 root root 111 Jul 28 07:42 README.md
[list-cloned-repo : list-directory] -rw-r--r-- 1 root root 87 Jul 28 07:42 Dockerfile
[list-cloned-repo : show-readme] 🥳 Yay! 🎉
[list-cloned-repo : show-readme]
[list-cloned-repo : show-readme] You have successfully cloned from private GitHub repository. 👏👏
[list-cloned-repo : show-readme]
[list-cloned-repo : show-readme] 😺 Tekton Rocks!! 🚀
To able push to external container registry, its requried that the Pipline is run with a ServiceAccount that has container registry credentials configured via ServiceAccount secrets. Kubernetes provider a Secret type called docker-registry, that can be used to configure the container registry credentials.
Set the requried environment variables to be used when creating the container-registry-secret:
export CONTAINER_REGISTRY_SERVER='https://quay.io' (1)
export CONTAINER_REGISTRY_USER=''
export CONTAINER_REGISTRY_PASSWORD=''
The container registry server URL, for Quay.io its https://quay.io and for DockerHub it is https://index.docker.io/v2/
kubectl create secret -n workspace-auth-demo docker-registry container-registry-secret \
--docker-server=$CONTAINER_REGISTRY_SERVER \
--docker-username=$CONTAINER_REGISTRY_USER \
--docker-password=$CONTAINER_REGISTRY_PASSWORD
secret/container-registry-secret created
kubectl create sa -n workspace-auth-demo build-bot
Now patch the build-bot service account to use the container-registry-secret credentials:
kubectl patch serviceaccount build-bot \
-p '{"secrets": [{"name": "container-registry-secret"}]}'
Lets verify if the service account has the secret added:
kubectl get sa -n workspace-auth-demo build-bot -o yaml
The command should show an output like:
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2020-07-28T03:34:32Z"
name: build-bot
namespace: auth-demo
resourceVersion: "53879"
selfLink: /api/v1/namespaces/auth-demo/serviceaccounts/build-bot
uid: 628067fd-91d1-4cdd-b6a6-88b4f7280ff0
secrets:
- name: container-registry-secret
- name: build-bot-token-8nl2v
Create the build and push app pipeline:
kubectl apply -n workspace-auth-demo \
-f greeter-app-build.yaml
pipeline.tekton.dev/greeter-app-build created
tkn pipeline start greeter-app-build \
--namespace=workspace-auth-demo \
--serviceaccount=build-bot \
--workspace name=maven-settings,config=maven-settings \
--workspace name=source,claimName=tekton-tutorial-sources \
--use-param-defaults \
--showlog
Ensure that the pipeline run has been set to run with the Service Account build-bot
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: greeter-app-build-
labels:
tekton.dev/pipeline: greeter-app-build
spec:
serviceAccountName: build-bot
pipelineRef:
name: greeter-app-build
workspaces:
- name: maven-settings
configmap:
name: maven-settings
- name: source
persistentVolumeClaim:
claimName: tekton-tutorial-sources
kubectl create -n workspace-auth-demo -f greeter-app-build-run.yaml
tkn pr logs -f -a $(tkn pr ls -n workspace-auth-demo | awk 'NR==2{print $1}')
A successful build and push will show the following output ( trimmed brevity):
...
[build-java-app-image : push] + buildah --storage-driver=overlay push --tls-verify=true --digestfile /workspace/source/image-digest quay.io/rhdevelopers/tekton-tutorial-greeter docker://quay.io/rhdevelopers/tekton-tutorial-greeter
[build-java-app-image : push] Getting image source signatures
[build-java-app-image : push] Copying blob sha256:90c2e42f948b524cf98005073e0b0aa2065160abf9e8b314976c064e270d92ac
[build-java-app-image : push] Copying blob sha256:869b43e5dca37fa63d84e9bc588613678c4fe6fa2072a72a6ab5487424db2891
[build-java-app-image : push] Copying blob sha256:f9ddbcc4e7954a705b700c35c5e5beceabd86af121a6e561d86437a8512a6be6
[build-java-app-image : push] Copying blob sha256:7b08010864ba4c7ce9dfe1b90244b459b77c0387051659d37454783d10ab1113
[build-java-app-image : push] Copying config sha256:5bd61d725dc47d1f8b7c225d8d52f2730321cadad65988a0de60300a711a2e2b
[build-java-app-image : push] Writing manifest to image destination
[build-java-app-image : push] Copying config sha256:5bd61d725dc47d1f8b7c225d8d52f2730321cadad65988a0de60300a711a2e2b
[build-java-app-image : push] Writing manifest to image destination
[build-java-app-image : push] Storing signatures
[build-java-app-image : digest-to-results] + cat /workspace/source/image-digest
[build-java-app-image : digest-to-results] + tee /tekton/results/IMAGE_DIGEST
[build-java-app-image : digest-to-results] sha256:0e9e267a96f1ea48fe00642cd82ef689e44c7d467d6db3a3a543fa5b42fe53dc
A successful pipeline should have pushed the image to the external container registry. The following screen shot shows the image pushed to rhdevelopers Quay.io container registry repo:
If you noticed the highlighted sha256 from the log above, is same as that of the sha256 listed in the contianer registry repository.
When need to pull from remote source repository or push to external container registry:
A Kubernetes Secret to hold the container registry credentials
A Kubenretes Service Account, with the container registry Secret added to it
Use the Service Account as serviceAccountName in PipelineRuns/TaskRuns
Annotate Secerts to map which Secret to be used with source repository
You can find more details about using Authentication with Tekton here.
Delete the workspace and its resources:
kubectl delete ns workspace-auth-demo
Mila Kunis Leaked Naked Pictures
Download Brazzers Me
Erotic Story Breeding
Russian Teen Homemade Anal Piss
Web Girls Porno Vk
Want a private GitHub repository? It comes with a catch
Private Git Repositories: Part 1 - Best Practices
Using Private Repositories and Registries :: Tekton Tutorial
6 places to host your git repository | Opensource.com
Azure Repos – Git Repositories | Microsoft Azure
Bitbucket | The Git solution for professional teams
Pricing · Plans for every developer · GitHub
How to Setup Passwordless Authentication to GitHub Private ...
Private Git Repository