Private Git

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Private Git
Release Notes
Change Logs
Forums
Support Ticket
Try Demo
All
cPanel
WHM
EA4
Knowledge Base
Manage2
Webmail
API
versioncontrol
whmadvanced
Overview
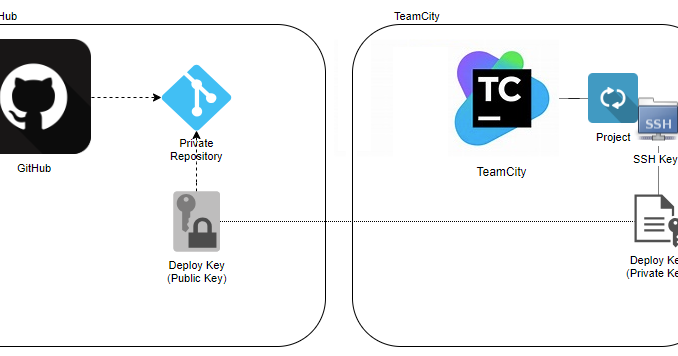
Set up access to private repositories
Generate an SSH key
Confirm that you generated the SSH key correctly
Register your SSH key with the private repository host
Test the SSH key
Clone the repository
Guide to Git™ - Set Up Access to Private Repositories
This tutorial uses GitHub as an example host for a private repository. However, most of the steps in this tutorial are similar to the steps for any other private repository host.
The steps in this tutorial require the Shell Access setting in cPanel & WHM version 70 or earlier or the Shell Access & Terminal setting in cPanel & WHM version 72 or later.
ssh - keygen -t rsa -b 4096 -C "username@example"
cat : / home /username/ . ssh / id_rsa . pub : No such file or directory
git clone git @example . com : MyStuff / private - repository . git
Guide to Git™ - Common Git Commands
Guide to Git™ - Deployment
Guide to Git™ - For System Administrators
Guide to Git™ - Git Terms
Guide to Git™ - How to Set Up Deployment
cPanel, WebHost Manager and WHM are registered trademarks of cPanel, L.L.C. for providing its computer software that facilitates the management and configuration of internet web servers.
Did you find this document helpful?
This document demonstrates how to set up a private repository on your local host. This allows the user to use cPanel as an automatic deployment location for their project that can run PHP, Ruby, Node.js™, or other desktop applications.
Because they require SSH access, you must perform additional steps in order to clone a privately-hosted remote repository.
This feature enforces several restrictions on clone URLs, and it verifies the remote host’s public SSH keys for ssh:// clone URLs. For more information, read our Git Version Control documentation.
If you do not perform these steps, you may see errors that resemble the following examples:
To set up access to private repositories, perform the following steps:
If you have not already configured one, run the following command to generate an SSH key:
In this example, username represents the cPanel account username and example represents the domain name.
After you run this command, the system will prompt you to enter a passphrase. Do not enter a passphrase, and press Enter to continue.
To confirm that the key exists and is in the correct location, run the following command:
The output should resemble the following example, where AAAAB3Nza... represents a valid SSH key:
Retain the full SSH key. Step 3 requires it.
If the output resembles the following example, ensure that you entered it correctly, and then run the command in Step 1 again:
If the output resembles the following example, ensure that you ran the cat command with the correct path:
For information about how to register your SSH key with another private repository host, consult that host’s website or documentation.
Some repository hosts, such as Bitbucket, do not allow you to configure write access for your access keys.
To register an SSH key with GitHub, perform the following steps:
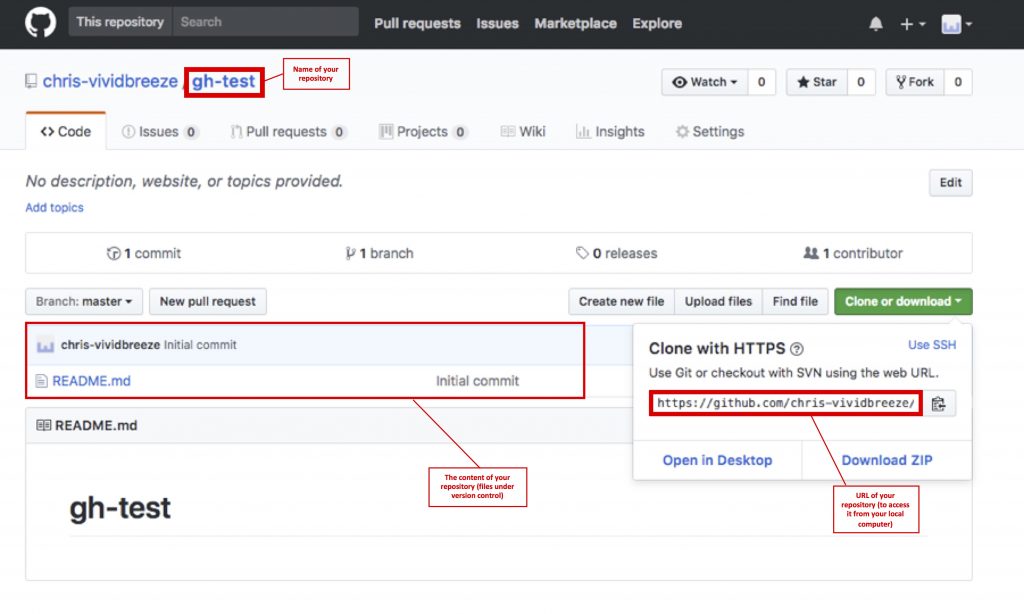
Navigate to your private repository.
In the top right corner of the page, click Settings . A new page will appear.
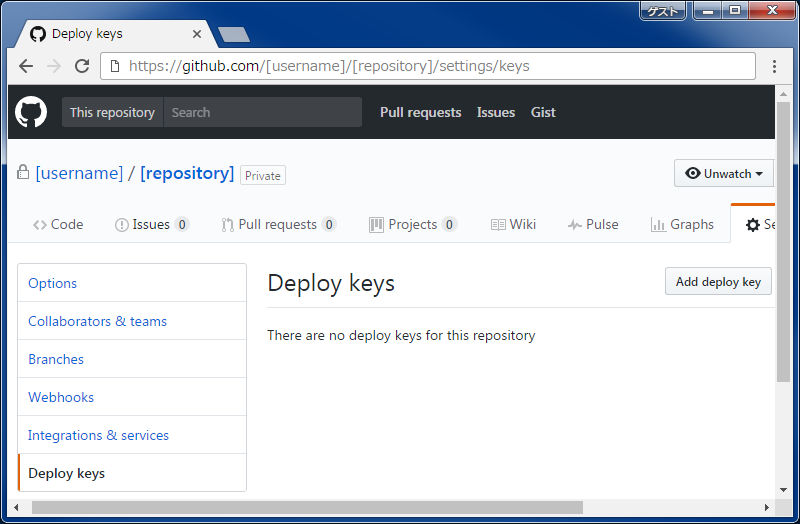
In the left side menu, click Deploy keys . A new page will appear.
In the top right corner of the page, click Add deploy key . A new page will appear.
In the Title text box, enter a display name for the key.
In the Key text box, paste the entire SSH key.
If you want to push code from your cPanel account to your GitHub account, select the Allow write access checkbox.
If you do not select this checkbox, you can only deploy changes from your GitHub repository to the cPanel-hosted repository.
To test your SSH key, run the following command, where example.com represents the private repository’s host:
To clone the repository, run the following command on the cPanel account, where git@example.com:MyStuff/private-repository.git represents the private repository’s clone URL:
© 2020 All Rights Reserved / Legal Notices / Privacy Policy / Transparency Report
Error: (XID dugfmj) “/usr/local/cpanel/3rdparty/bin/git” reported error code “128” when it ended: fatal: could not read Username for 'https://github.com': No such device or address
Error: “/usr/local/cpanel/3rdparty/bin/git” ended prematurely because it received the “TERM” (15) signal:
-----BEGIN RSA PRIVATE KEY-----
AQKCAgByFAHL2301vtIuUQ+jy7+6MoHlXwa0G7Ob/R1KOthYw3KMr/cCQycZimcZ
GitHub - searKing/PrivateGitHub: Use private repository with a free...
Guide to Git ™ - Set Up Access to Private Repositories | cPanel & WHM...
Private Git Repositories: Part 1 - Best Practices
Go Modules with Private Git Repositories | by Tim Jones | Medium
How To Set Up a Private Git Server on a VPS | DigitalOcean
As I hinted in my previous posts, OpenShift Virtualization opens up new infrastructure design possibilities. I believe one of the biggest things that will come down the pipeline is OpenShift on ...
Introduction OpenShift comes by default with a static Grafana dashboard, which will present cluster metrics to cluster administrators. It is not possible to customize this Grafana instance. However, ...
Just a short blog entry, here, to alert y'all to the availability of a new guide from DZone, describing how to get started with OpenShift. From the piece: What is Red Hat’s OpenShift Container ...
How we use cookies We use cookies on our websites to deliver our online services. Details about how we use cookies and how you may disable them are set out in our Privacy Statement . By using this website you agree to our use of cookies.
August 31, 2017 | by
Graham Dumpleton
When you deploy applications to OpenShift from source code, you will typically provide the source code by specifying a URL to a repository managed by a Git hosting service such as GitHub, GitLab or Bitbucket. When the build process runs to create the image for your application, the first step will be to pull down the source code from that hosted Git repository.
If the hosted Git repository is publicly accessible, there is nothing else to do. If, however, you want to use a private Git repository, you will need to provide to OpenShift access credentials which the build process can use when accessing the Git repository.
The principles of using private Git repositories with OpenShift have been covered in a number of prior posts:
These looked at key generation and setting up a build configuration to use it, however, beyond these basics there are additional features in OpenShift which make using private Git repositories easier. There are also various best practices you can adopt to ensure you are using the most secure mechanism possible, without risking your most important access credentials.
In this series of posts I will look again at the topic of accessing private Git repositories, but explore new and more recommended ways of using OpenShift, and hosting services such as GitHub, GitLab, and Bitbucket, to best secure access to your source code.
To access a hosted Git repository, a number of different protocol types are supported.
For more information about communicating with a Git repository using these protocols see the hosted version of the Pro Git book .
When accessing a repository, Git repository hosting services such as GitHub, GitLab, and Bitbucket support using both the HTTPS and SSH protocols. The terminology for each can vary, but the credential types offered by these hosting services then fall into the following categories:
When using a private Git repository with OpenShift, you should always aim to use a unique repository SSH key and ensure it has read-only access to the repository. This is because you will need to upload the private key of the key-pair to OpenShift.
When setting up a repository SSH key you should not use your primary identity SSH key. This is because you should never upload its private key to a system you do not control or which can be accessed by others. Using a primary identity key carries additional risk as it is likely used for other purposes, such as gaining secure shell access over SSH to other hosts. If someone were able to get the private key, they could access those other systems.
One saving grace is that OpenShift will not allow you to use a key-pair where the private key has a passphrase. A best practice, which I am sure you are following, is that your primary identity SSH key should always have a passphrase; this will prevent you from inadvisedly using your primary identity SSH key.
So repository SSH keys and accessing a repository over the SSH protocol is the preferred method of accessing a repository. One situation where this will not work though is where the OpenShift instance you are using sits behind a firewall, and that firewall blocks SSH connections to an external Git hosting service.
In this situation, you would have to fallback to using a personal access token over a HTTPS connection. Although the access rights of personal access tokens can be limited to read-only access, they cannot be linked to just a single repository and could be used with any repository accessible to the user account. If you are deploying a personal project to OpenShift, this may be acceptable. However, if this were a project of your company hosted on the hosting service under an organization, you should not rely on using a personal access token of a specific developer. If that developer were to leave you now have the problem that your builds are linked to that developer's account and they could revoke the access token and break the builds. The developer also puts themselves at risk, as the access token could be used to access other private repositories they have which are not related to their work at the company.
If you cannot use the SSH protocol and must use a personal access token with the HTTPS protocol, for a company it would be better to create a separate machine user account on the Git repository hosting service and use it as the owner of the personal access token.
In this post we have covered the different protocols and credential types you can use to access a hosted Git repository, as well as listed some best practices around the credential type used. In the next post in this series, we will look at setting up a repository SSH key, using the GitHub hosting service as an example.
Access the rest of the series here:
OpenShift Container Platform ,
How-tos ,
OpenShift Dedicated ,
OpenShift Online
Red Hat OpenShift is an open source container application platform based on the Kubernetes container orchestrator for enterprise application development and deployment.
Nudists Free Hd
Lesbian Squirt Pussy
Nasty Me
Name Nasty
Futa Catfight Mutual Penetration Mega Porn Pics