Pornhub Adblock

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
There are currently no responses for this story.
We tried to find the most PG page on MindGeek’s network to use as an example- it wasn’t easy.
When I was building the prototype for BugReplay, I was evaluating different methods of capturing and analyzing network traffic from Chrome. One of the first things I saw that looked promising was the chrome.webRequest API.
From the docs: “Use the chrome.webRequest API to observe and analyze traffic and to intercept, block, or modify requests in-flight.”
That seemed to be exactly what I needed.
After experimenting with the Chrome webRequest API, I quickly realized there was a big problem. It didn’t allow me to analyze any WebSocket traffic, something I really wanted to support in BugReplay.
As I was searching the web trying to see if I was misreading the documentation or was looking in the wrong spot, I found a relevant bug report from 2012: “chrome.webRequest.onBeforeRequest doesn’t intercept WebSocket requests.” In the bug report, users were complaining that without the ability to block WebSockets, websites could get around ad blockers fairly easily. If WebSocket data was not visible to Chrome extensions via the webRequest API, they could not be blocked without some heavy duty hacks.
Initially, the risks to ad blockers seemed theoretical; the examples of sites that were employing this technique were very obscure. Then in August 2016, an employee of the company that owns Pornhub.com (MindGeek) started arguing against adding the WebSocket blocking capabilities to the Chrome API. Pornhub is the 63rd most visited site on the Internet according to Alexa. I checked out a few of MindGeek’s sites and sure enough, I could see ads coming through even though I had Adblock Plus on. The ads on Pornhub are marked ‘By Traffic Junky,’ which is an ad network owned by MindGeek.
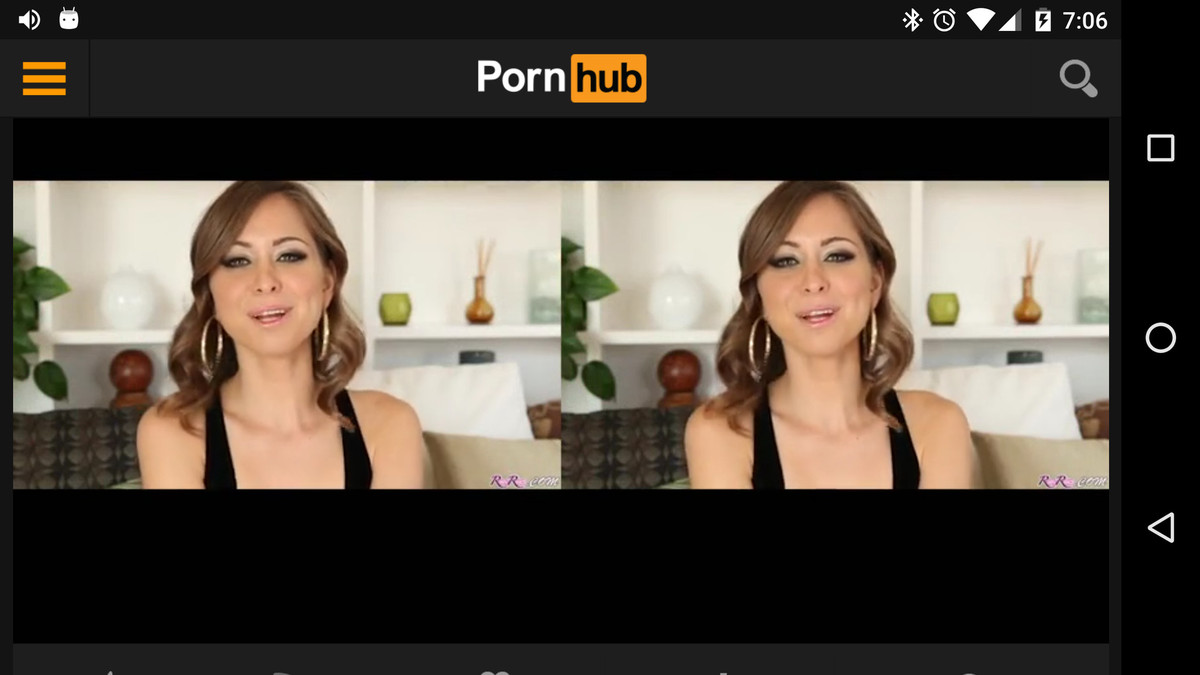
In the screenshot below, you can see a banner at the top of the page announcing that the site is aware that the user is using an Ad Blocker, with an invitation to subscribe to a premium ads free version of the site. On the right side of the page you can see an advertisement.
When you visit Pornhub.com, it tries to detect if you have an ad blocker. If it detects one, it opens a WebSocket connection that acts as a backup mechanism for delivering ads.
Watching the BugReplay browser recording, you can see a number of network requests triggered that are blocked by AdBlock: They are marked Failed in the network traffic, and if you click one to inspect the detail pane you can see the failed reason is net::ERR_BLOCKED_BY_CLIENT. That is the error reported by Chrome when an asset is blocked from loading.
You can find the WebSocket frames individually in the network panel or just look at the WebSocket create request which has links to all the individual frames. The name of the domain where the WebSocket connects is “ws://ws.adspayformy.site.” A decent joke aimed at ad blockers :)
When the WebSocket loads, the browser sends a frame with a JSON encoded payload for each of the spots it has available for ads. Checking out one of the WebSocket frames, you can see in the frame data the advertisement data is sent back with:
Ad Blockers primarily work using the webRequest API, so constructing the ad by transmitting the data over the WebSocket as base64 is a pretty clever way of dodging the blocker.
On October 25th, 2016, there was some new activity on the Chromium ticket. A contributor wrote a patch adding the ability to block WebSockets using the webRequest api. If it’s accepted, it will eventually wind up in Chrome stable.
When or if that rolls out, the ad blocker extension writers can choose to remove the hacks for users of the latest Chrome, leaving content providers like Pornhub to figure out their next move in the ad blocking war.
Since I started looking into this, AdBlock Plus and uBlock Origin have shipped workarounds to block this technique. AdBlock and others still do not.
For AdBlock Plus, “The wrapper performs a dummy web request before WebSocket messages are sent/received. The extension recognizes these dummy web requests as representing a WebSocket message. It intercepts and blocks them if the corresponding WebSocket message should be blocked. The WebSocket wrapper then allows / blocks the WebSocket message based on whether the dummy web request was blocked or not.” via
For uBlock Origin, they shipped a workaround that has the “ability to foil WebSocket using a CSP directive.”
Bug reporting tool that records your screen and syncs it with network traffic & JavaScript logs.
Bug reporting tool that records your screen and syncs it with network traffic & JavaScript logs.
Medium is an open platform where 170 million readers come to find insightful and dynamic thinking. Here, expert and undiscovered voices alike dive into the heart of any topic and bring new ideas to the surface. Learn more
Follow the writers, publications, and topics that matter to you, and you’ll see them on your homepage and in your inbox. Explore
If you have a story to tell, knowledge to share, or a perspective to offer — welcome home. It’s easy and free to post your thinking on any topic. Write on Medium
flyingzebras opened this issue on 6 Apr 2016 · 9 comments
flyingzebras opened this issue on 6 Apr 2016 · 9 comments
I got this message when I surfed pornhub.com: "Loading ..."
This is the HTML output I wish you to investigate:
Cannot you see the HTML that I posted above?
In order to view the wanted video without turning Javascript ON, do this:
Select the wanted video, right click the video player area and select Inspect Element
Select the javascript line that's above the currently highlighted one
Copy the wanted video quality string, open up a new tab, paste it & go
Only allow the video to be whitelisted, the html5 player that's built-in in the browser will take care of playing it
You'll also want to use the self-destructing cookie extension, and whitelist only those websites that you actually want to store cookies and utilize the localStorages.
@wifiextender
Thank you, but no need
@flyingzebras
it seems that if one uses uBO, the rule does not work, due to a rule of uBO, but I'll try to fix it
@reek I'm glad that you found the cause of this bug.
reek changed the title pornhub.com main page pornhub.com on 16 May 2016
Hi,
Anti-AdBlock Killer has been updated ! Changelog
Step 1: Update : UserScript
Step 2: Update : FilterList
Do not forget to donate, review, share, follow and add to favorites.
See you
Reek
Also blocking pornhub's ad can be done on network level by routing the domain of the sources of those ads to a blackhole using DNS or some other methods
Sign up for free to join this conversation on GitHub. Already have an account? Sign in to comment
Successfully merging a pull request may close this issue.
In Autosomal Dominant Inheritance Jsp Cid
pornhub.com · Issue #1279 · reek/anti-adblock-killer · GitHub
Интересное использование Adblock Plus / Хабр
AdBlock — best ad blocker - Chrome Web Store
pornhub popups appear when i hit the video? | Yahoo Answers
PornHub โดนบล็อค แล้ว แก้ไข อย่างไรมาดูกัน
Nordvpn Adblock Pornhub 😝GhostPathPros+
Pornhub Adblock














































(mh%3dZN6F-Bjh0RbNPG4F)thumb_1265811.jpg)























