Pi Hole Openwrt

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Network Ad Blocking with Pi-hole and OpenWrt
Pi-hole is a self-proclaimed "black hole" for internet advertisements. A simple bash one-liner allows you to set up a network-wide ad blocking appliance, on hardware as basic as a Raspberry Pi. A typical configuration would take no more than ten minutes to set up, assuming some prior experience with Linux. It's really quite easy: install Pi-hole, then set your DNS server to the local IP address of your Pi. This basic installation will do just fine for the majority of users. However, there is still some room for improvement. Some applications and devices use hard-coded DNS servers specifically to get around this type of ad blocking. The main offender is Google, who forces most Android clients to ignore the DNS server being broadcasted by the router. Using OpenWrt, we can tighten things up a bit. Here are the three goals that I was looking to achieve in my setup, and the steps I took to achieve them:
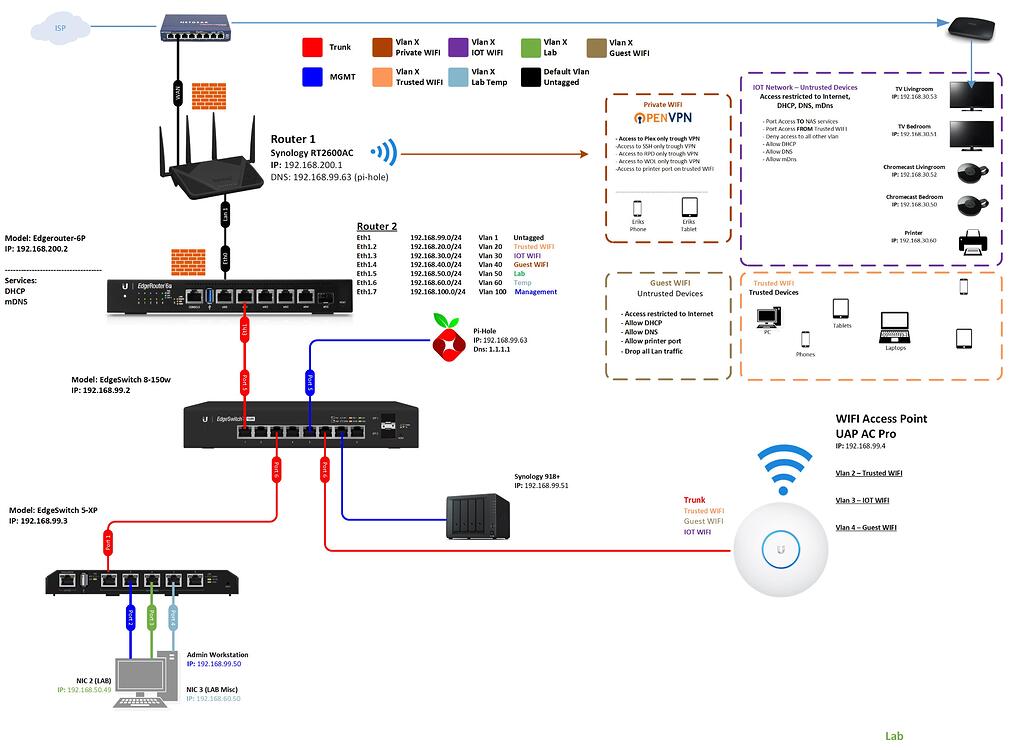
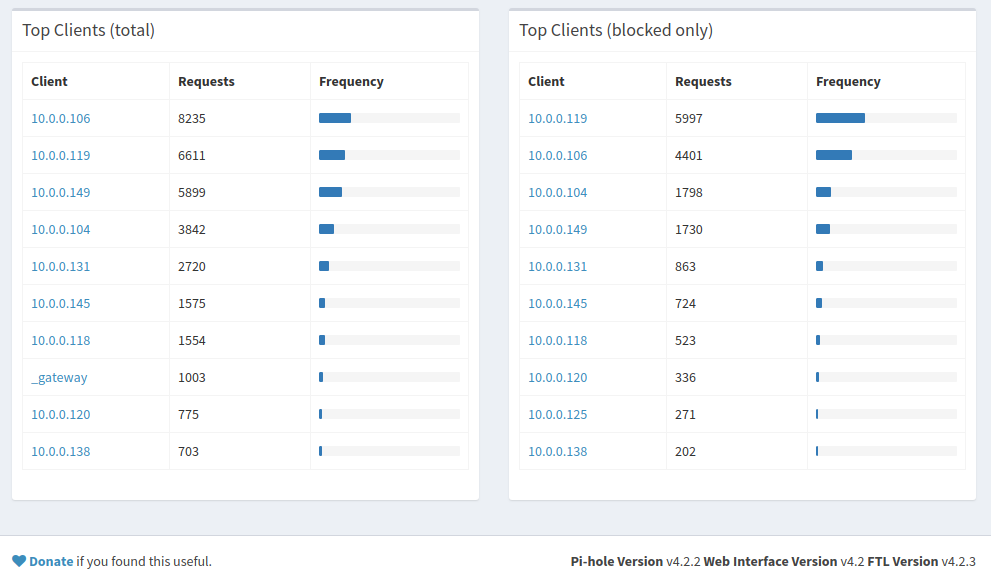
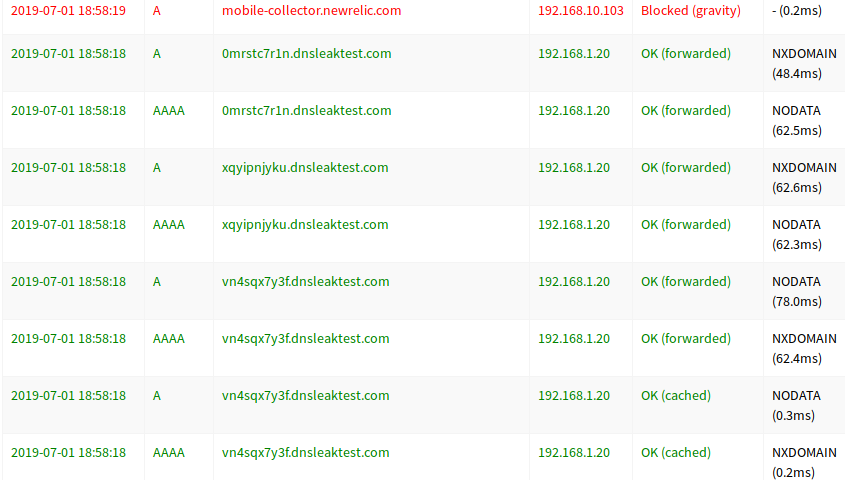
Several of my housemates have Android smartphones. After setting up Pi-hole, they noticed that they were still receiving the same amount of advertisements as before. By looking at the Pi-hole interface I could see that only a small portion of their DNS requests were going through the Pi-hole. Naturally, I wanted the Pi-hole to filter all traffic originating from these devices as well as other devices that often use hard-coded DNS servers such as IoT devices and Smart TVs.
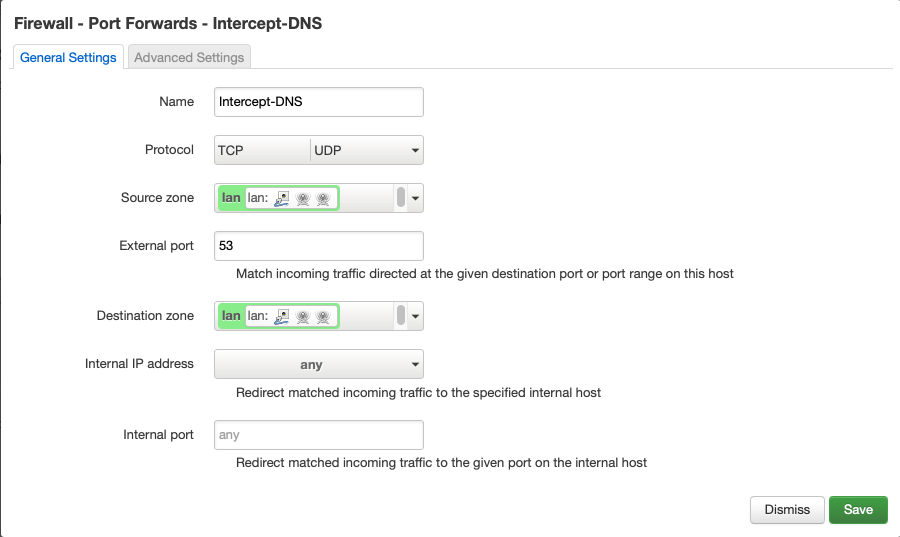
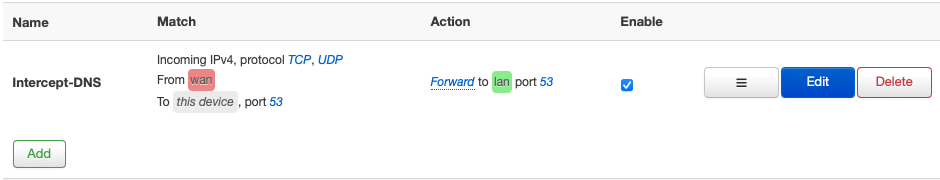
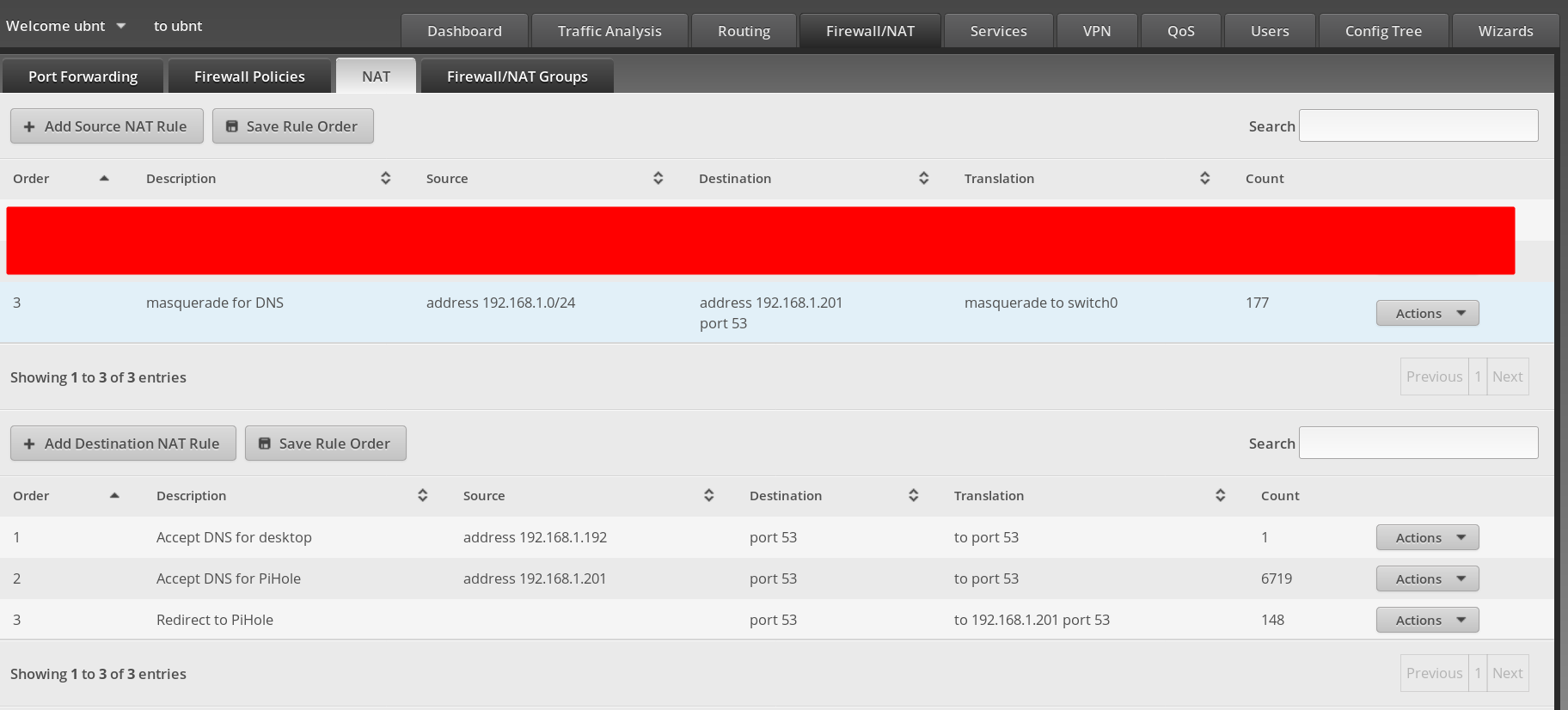
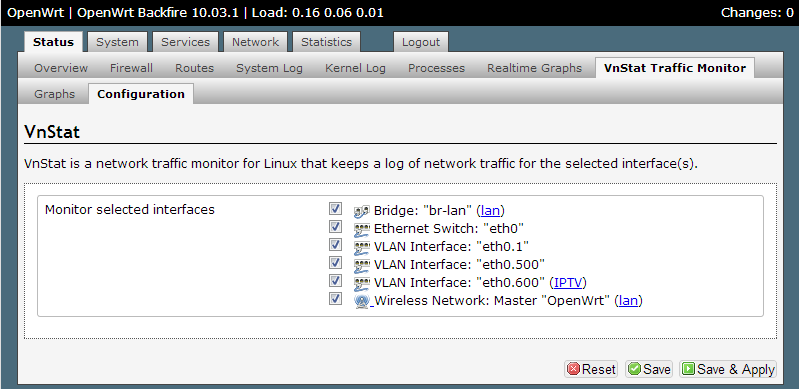
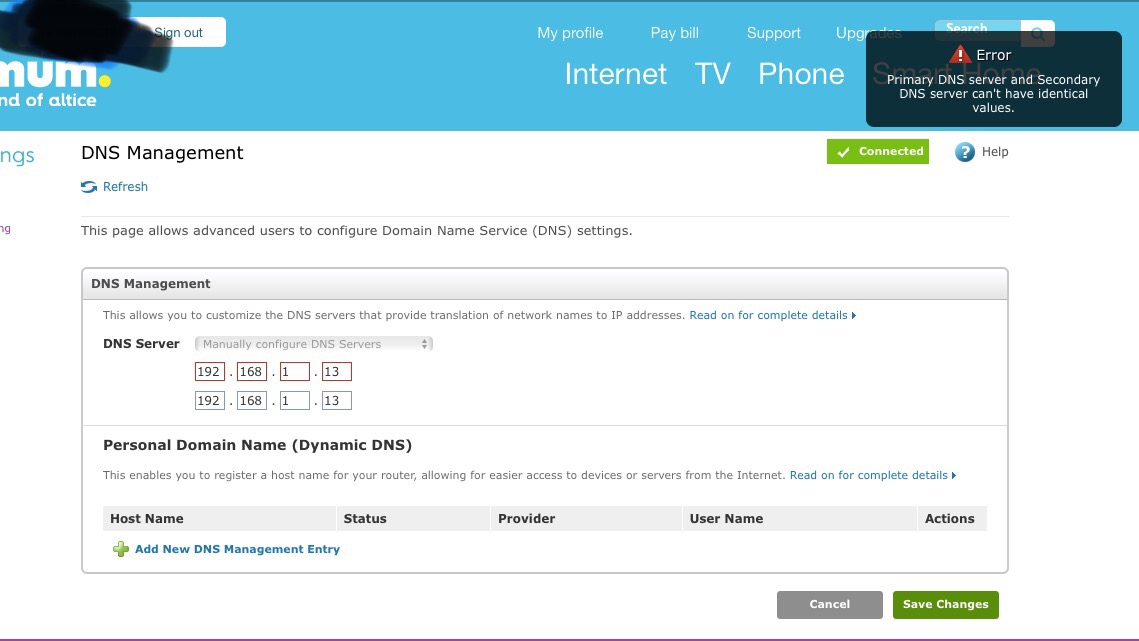
This problem is solved by using some custom firewall rules in OpenWrt. Choose Firewall from the Network menu, then click on the Custom Rules tab. Here you can directly input iptables commands which offer more flexibility than the LuCI interface. The following rules redirect port 53 traffic from all devices to the Pi-hole.
A nice side effect of these rules is that any client that attempts to manually use a DNS server other than the Pi-hole will fail to resolve any requests. A second set of rules allows the Pi-hole to forward unblocked requests to the upstream DNS server.
Don't forget to substitute your Pi-hole's local IP address. Keep in mind that depending on your router model, interface names such as eth0 and br-lan may differ. You can view the names of your router's interfaces in OpenWrt by choosing Interfaces from the Network menu. After inputting the rules, click the Save button and reboot the router.
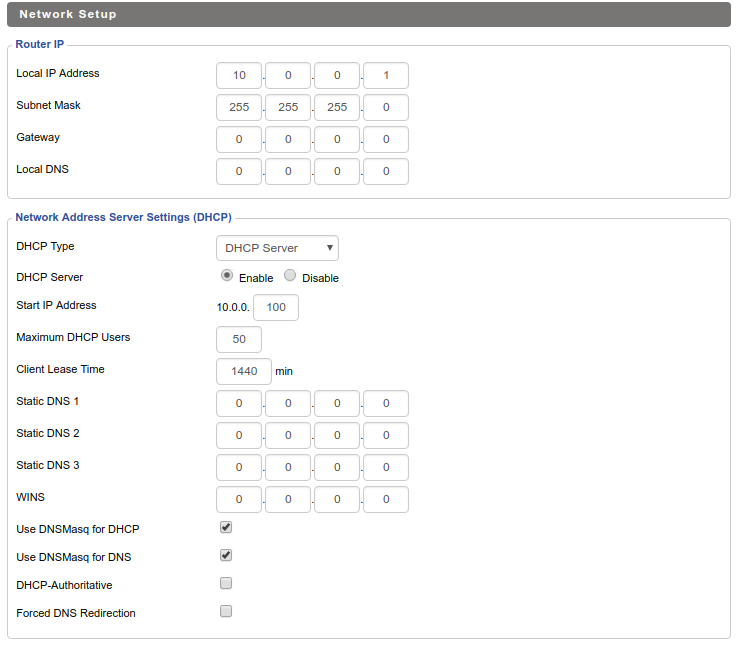
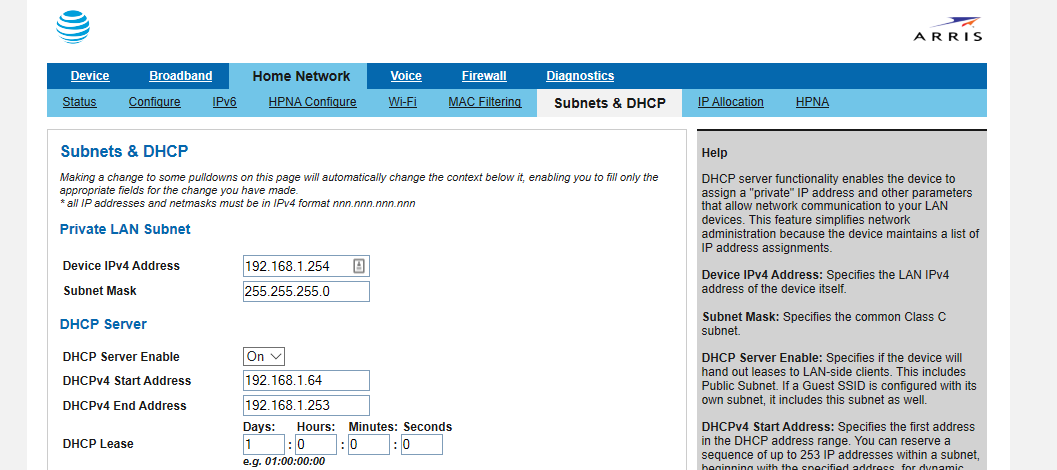
This is perhaps a contentious one. It would be a lot easier to run the DHCP server on the Pi, but that would create a single point of failure for both DHCP and DNS. If the Pi goes down, new clients wouldn't be able connect to the network. Additionally I found OpenWrt's interface for DHCP related tasks to be much nicer, since it is designed for use on routers.
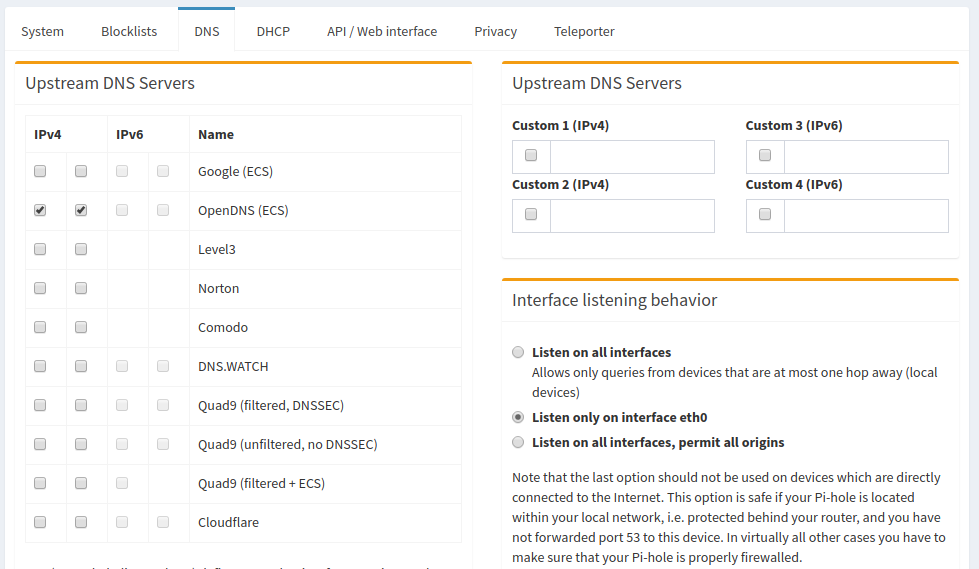
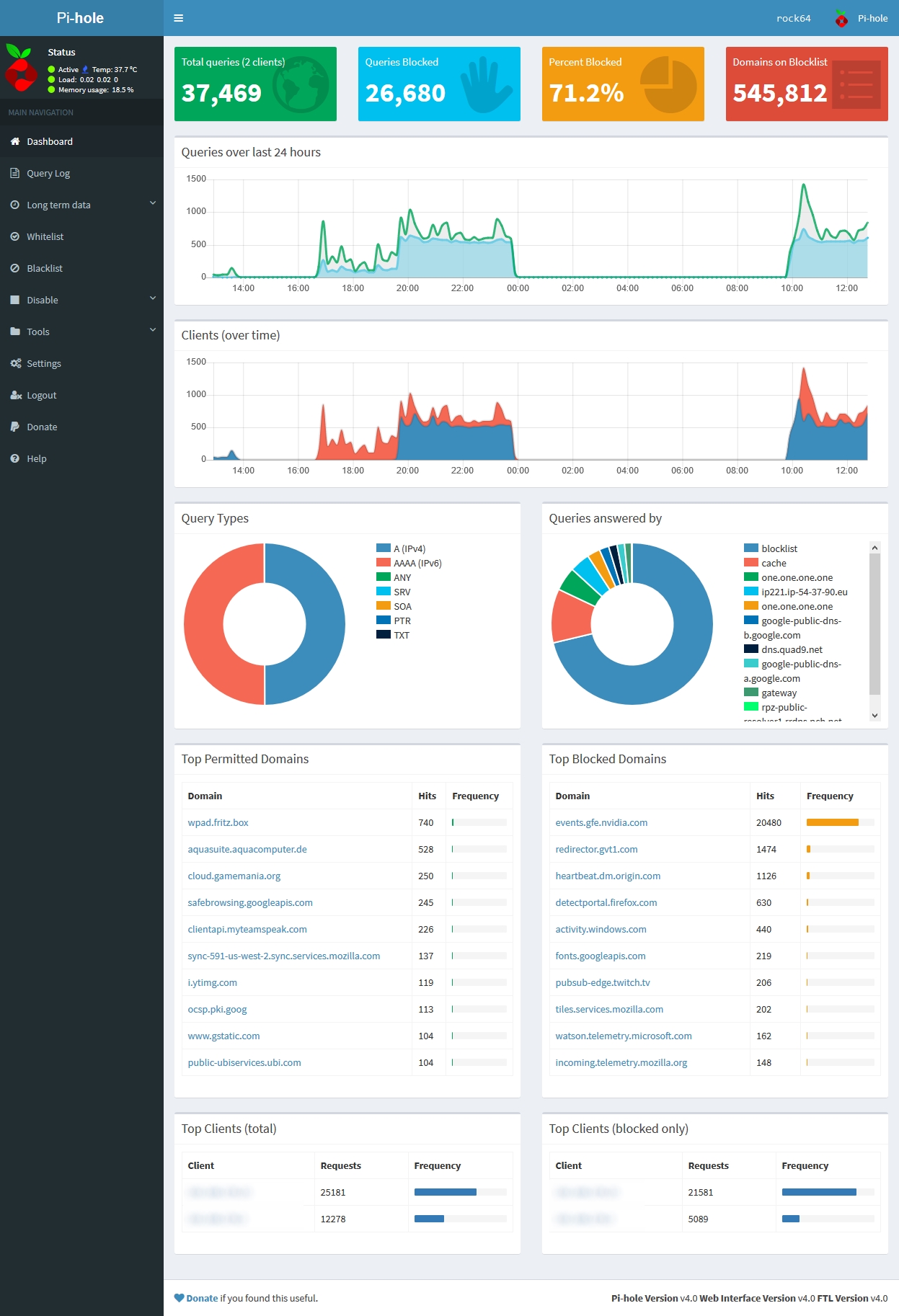
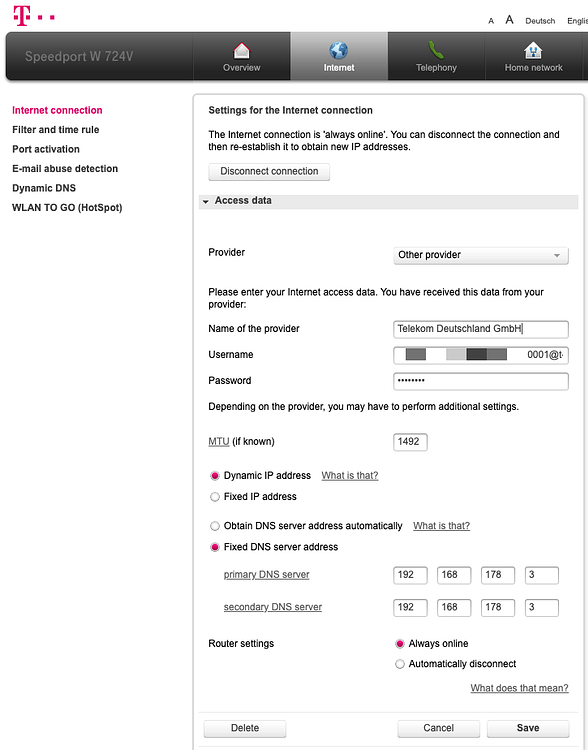
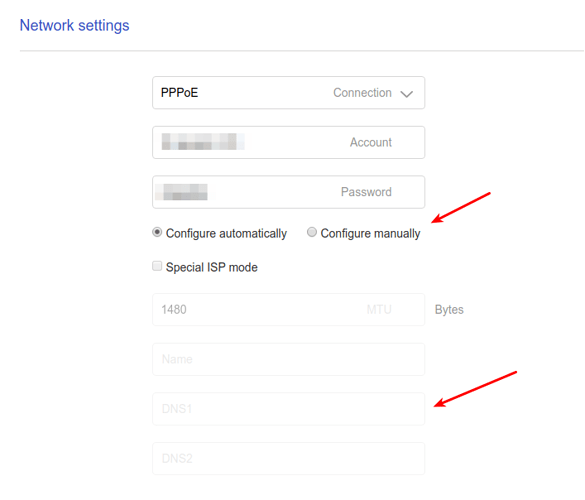
Some Pi-hole setup guides recommend changing your router's DNS server to the Pi. If you are running a stock router firmware, often times this is the only solution if you don't want to use the Pi-hole's DHCP server. The downside to this method is that all requests in the Pi-hole interface will be shown as originating from your router, regardless of the client that initiated the request. This was unacceptable to me as I wanted to take advantage of the detailed statistics offered by Pi-hole. There are also features such as Group Management that are essentially useless without discrete clients.
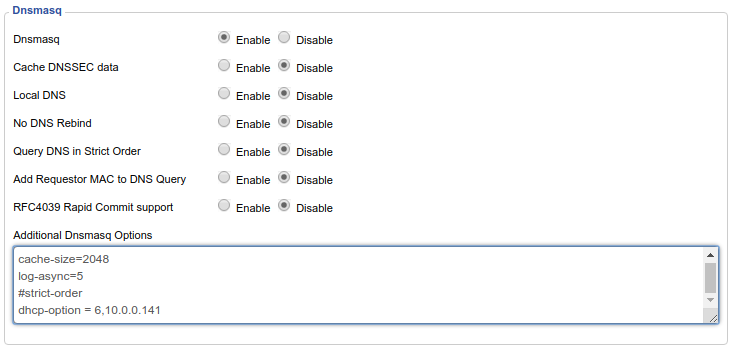
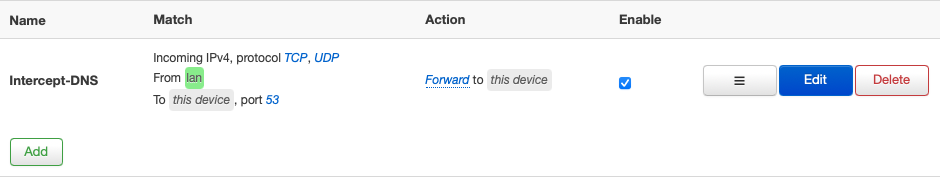
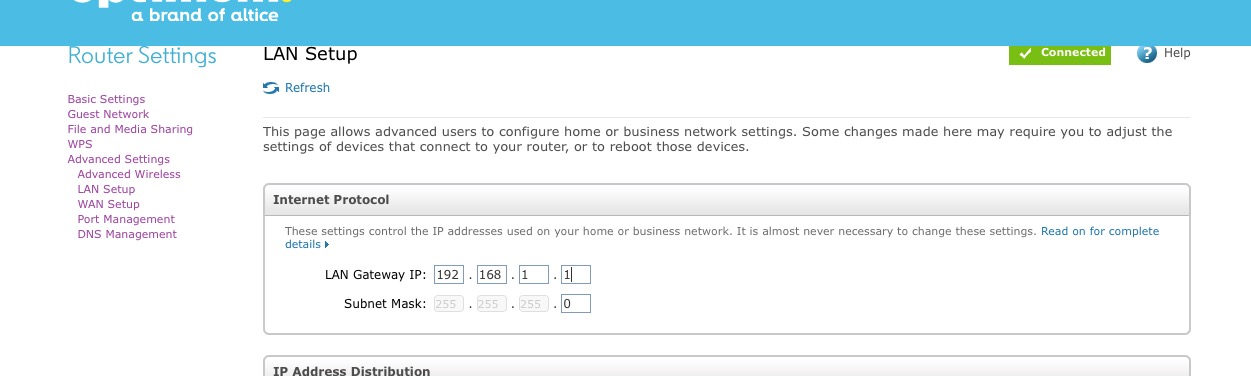
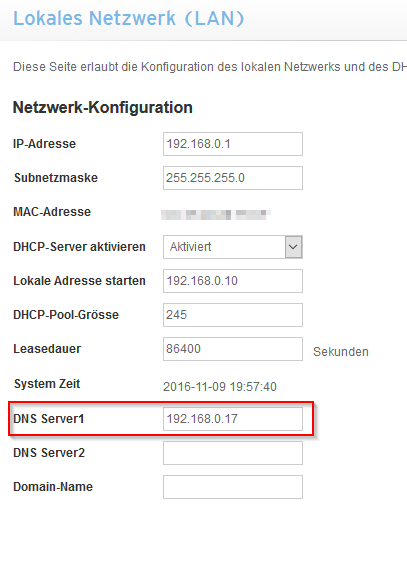
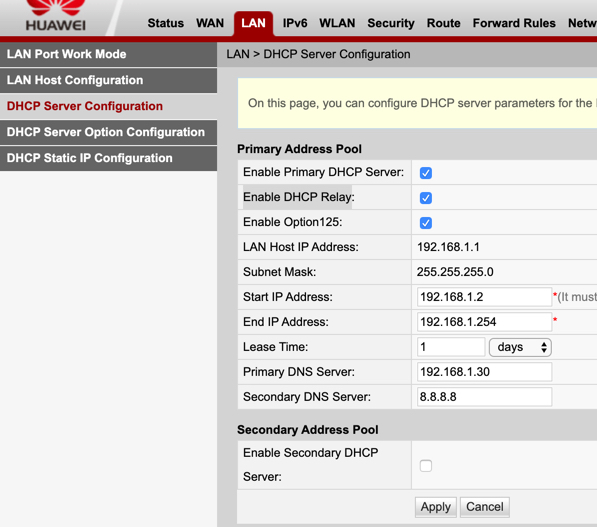
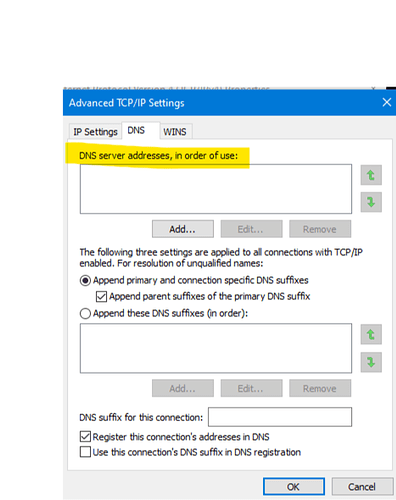
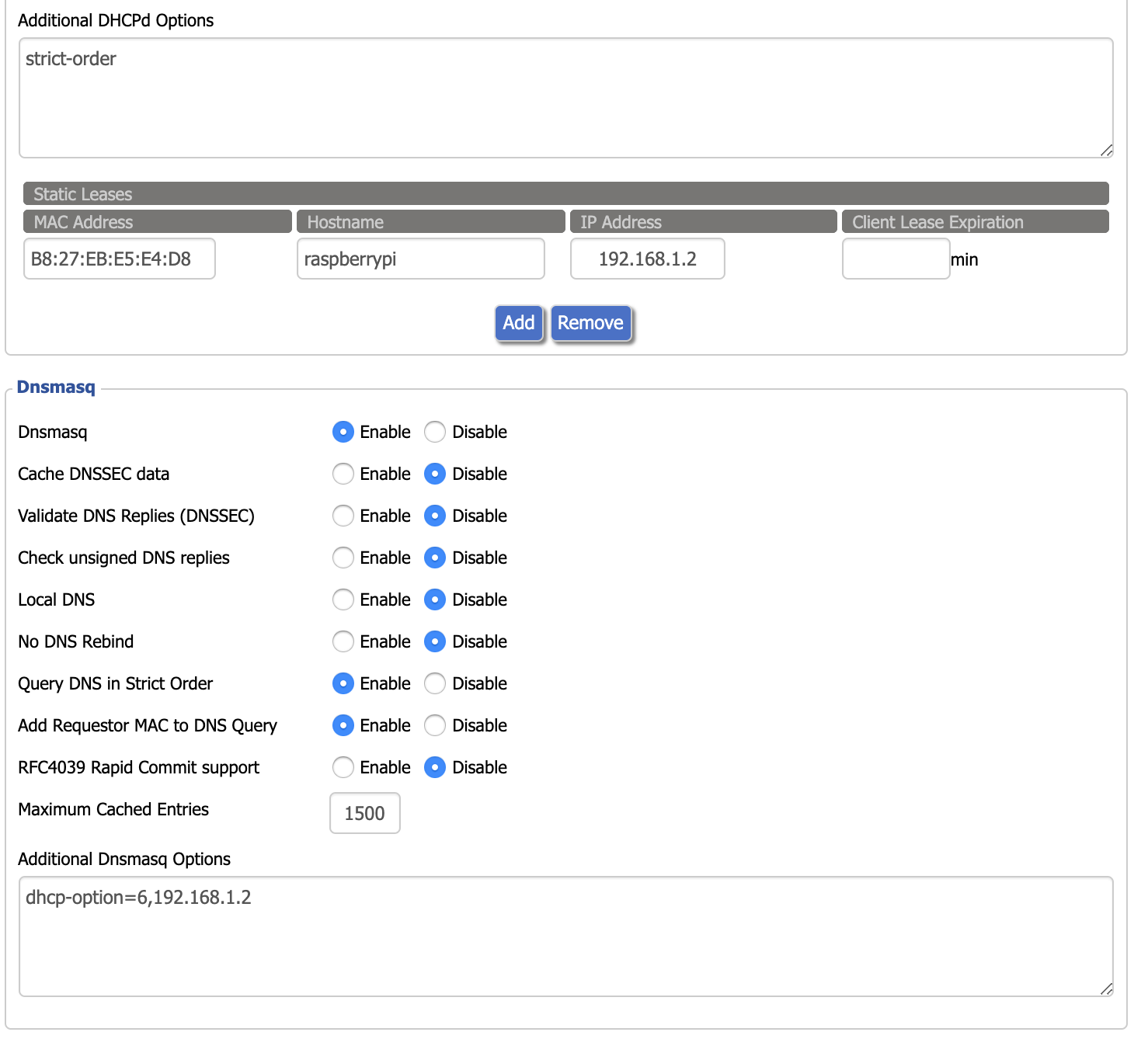
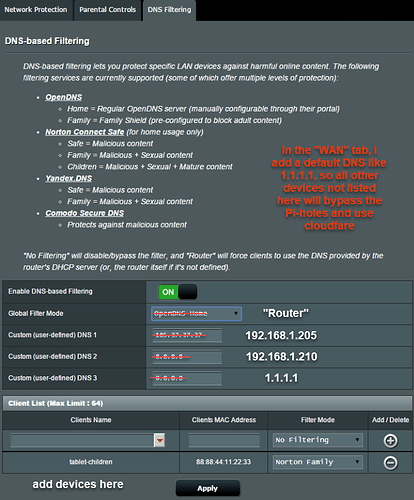
The solution to this problem is to advertise the Pi-hole's DNS server to clients using dnsmasq. In OpenWrt, navigate to the Interfaces page under the Network menu. Then click the blue Edit button on your LAN interface. Next, go to the DHCP Server tab and then the Advanced Settings tab underneath. In the DHCP-Options field, type 6,192.168.X.X substituting your Pi-hole's local IP address. Click the Save button and restart the LAN interface. If you want more information on other cool things you can do with DHCP-Options in dnsmasq, this is a good resource.
I find this particularly useful since it allows me to easily identify devices on my network. It's much more pleasant to SSH into openwrt/ or raspberry/ than a string of numbers when configuring devices. Also in the Pi-hole interface it is much more convenient to see a list of names such as maxs-iphone and Apple-TV when managing clients or examining query logs. Again, I concede that running the DHCP server on the Pi-hole would eliminate this problem. But I'm stubborn.
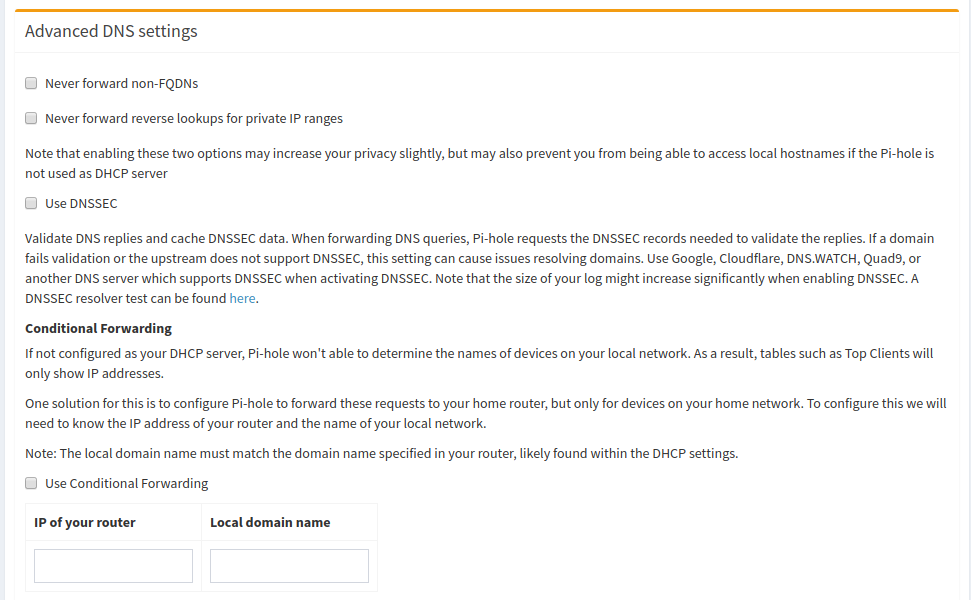
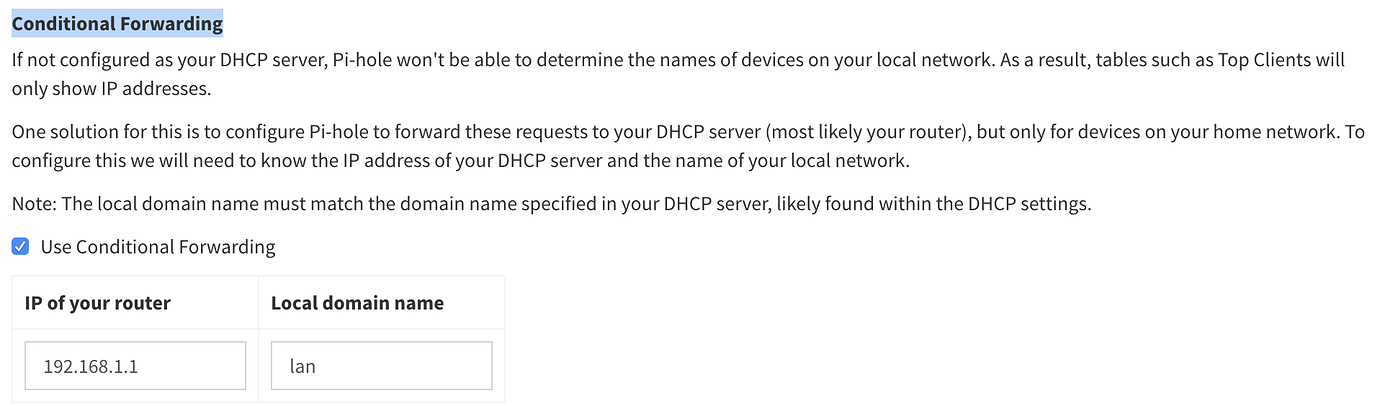
Luckily the Pi-hole has a feature for us stubborn folks, called Conditional Forwarding. In the Pi-hole Admin Interface, navigate to the DNS Settings page. Scroll all the way to the bottom and fill out the Conditional Forwarding section with your OpenWrt router's local IP address. Although the Local Domain Name field is marked as optional, I found that it is necessary if you are using a local domain name other than .lan. In either case, make sure you match everything with the OpenWrt settings.
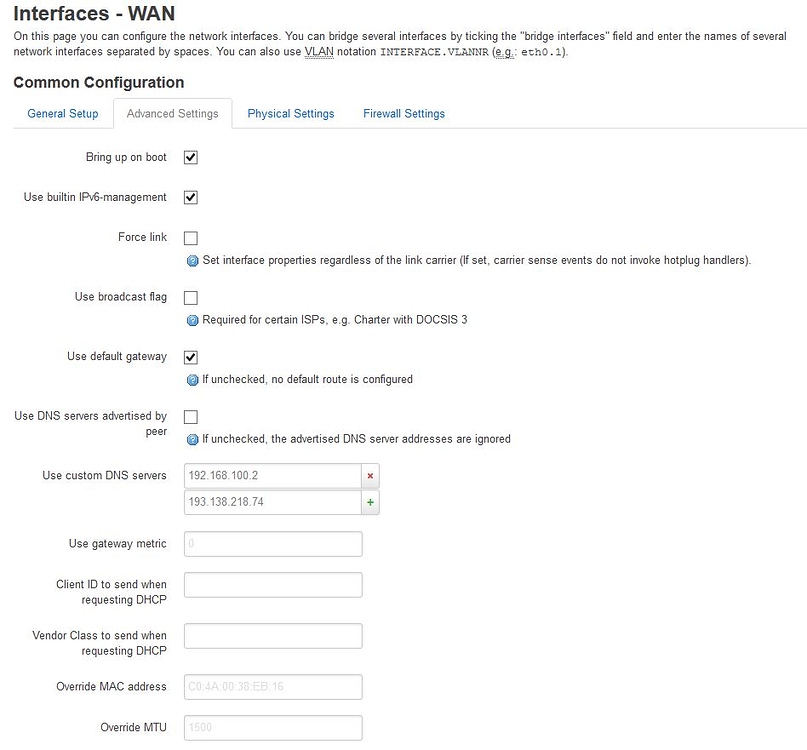
During my troubleshooting of Android circumventing the Pi-hole DNS server, I changed some other settings in OpenWrt. If you still have issues with ad blocking on Android clients after following the above steps, you may need to do some or all of these things to get it working smoothly. First, make sure that "Use DNS servers advertised by peer" is unchecked in the Advanced Settings of both the WAN and WAN6 interfaces. With this setting enabled, the Android clients were still receiving advertisements.
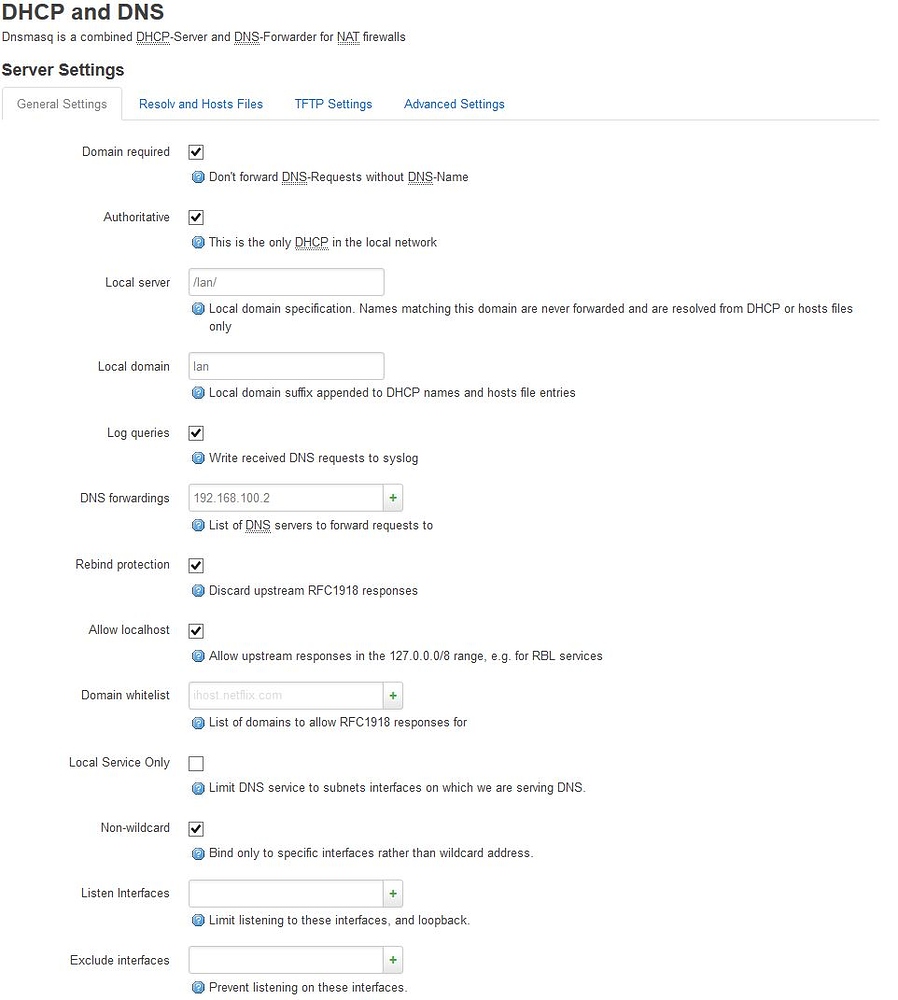
I also made sure that there were no DNS forwarding servers set in the DHCP and DNS settings page in the Networking menu. This had a side effect of making the Raspberry Pi itself not able to resolve queries to the outside world, but editing the nameserver entry in the Pi's /etc/resolv.conf to point to Google's DNS instead of the router took care of that issue.
Another thing that may be getting in the way is Android's Private DNS feature. According to Google's knowledge base article, it is enabled by default on all networks that support it. It can only be manually disabled by the user on a per-device basis, and I can't figure out a way to prevent it at the router firewall level.
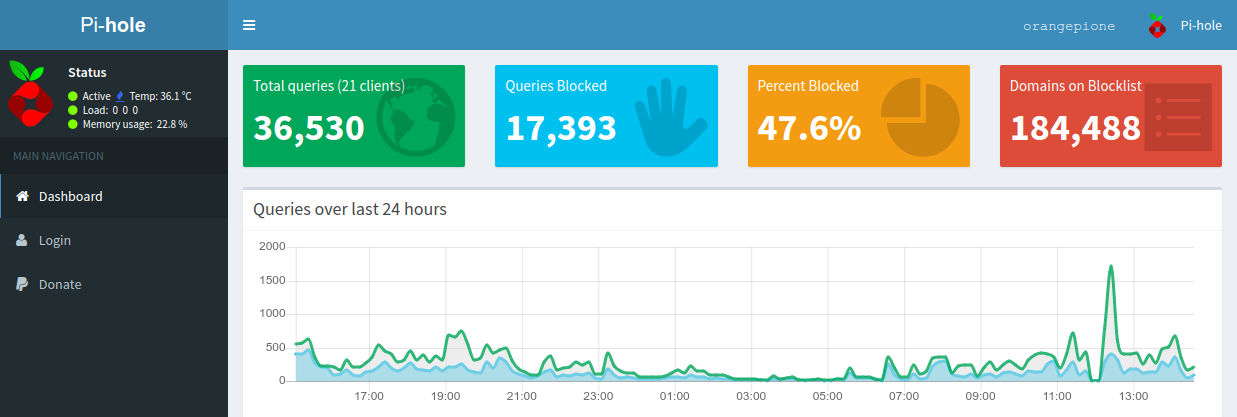
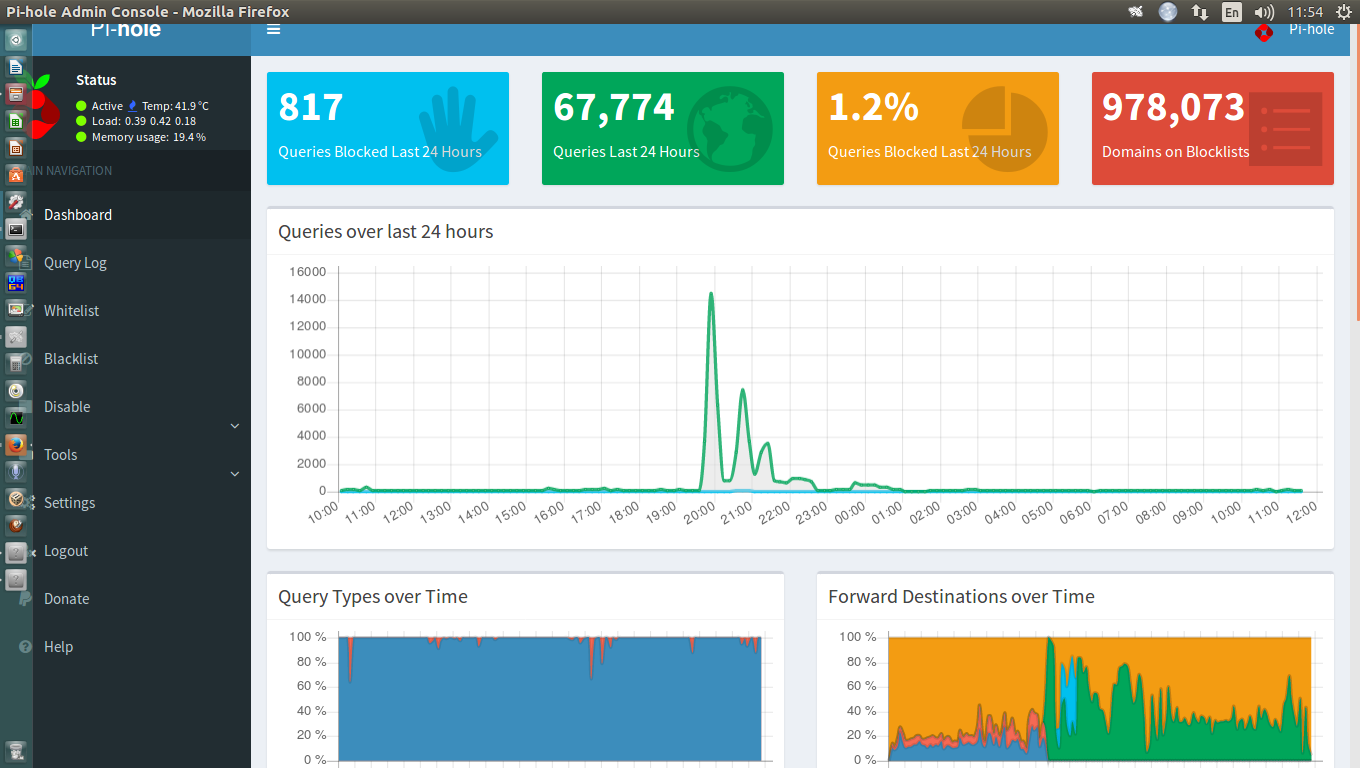
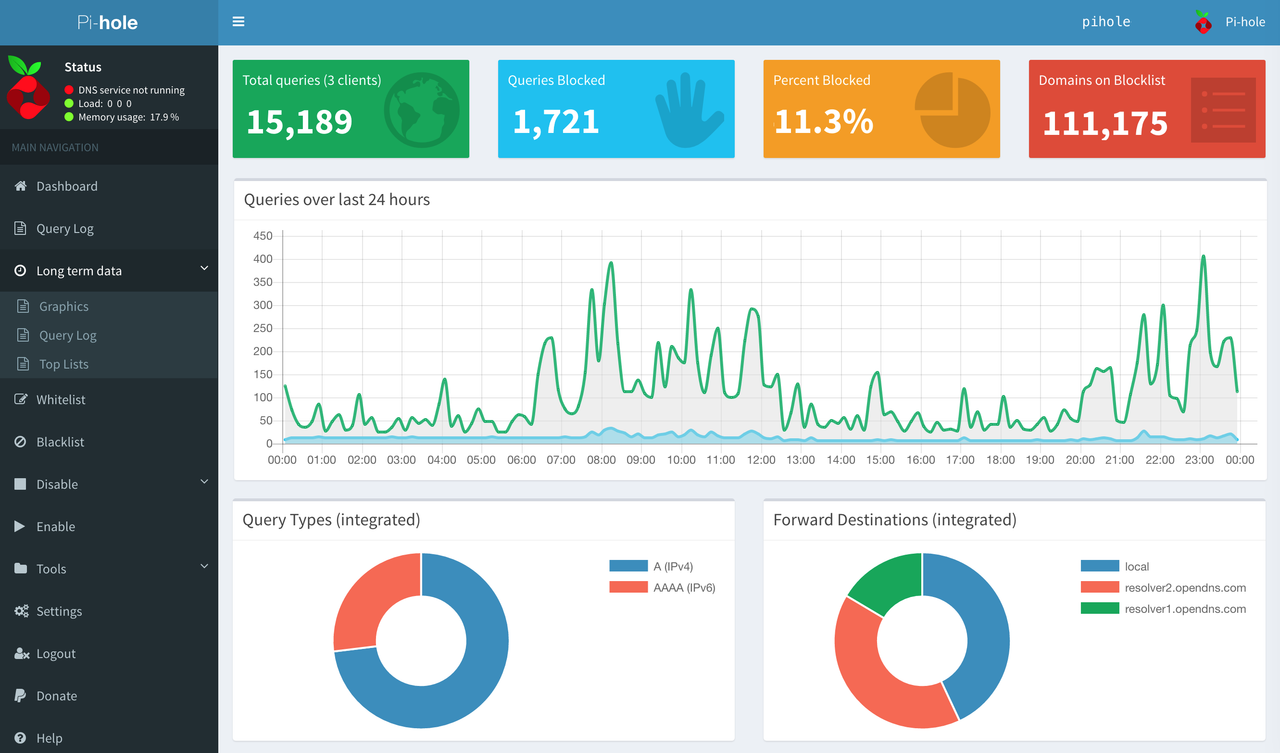
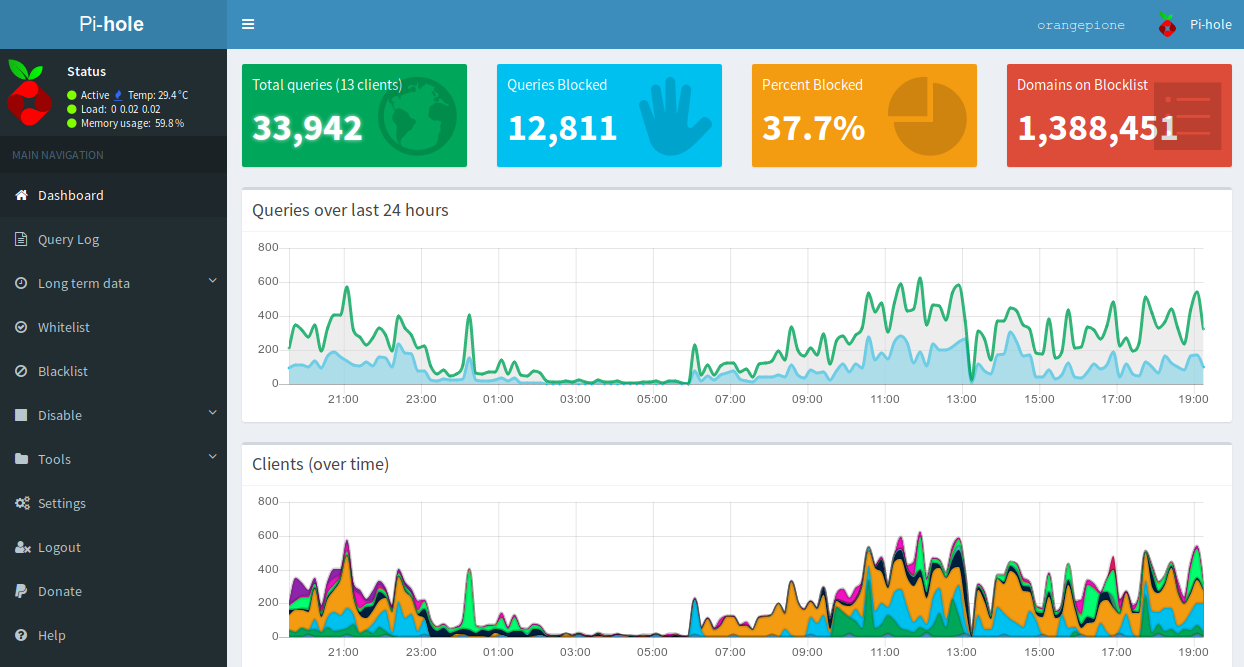
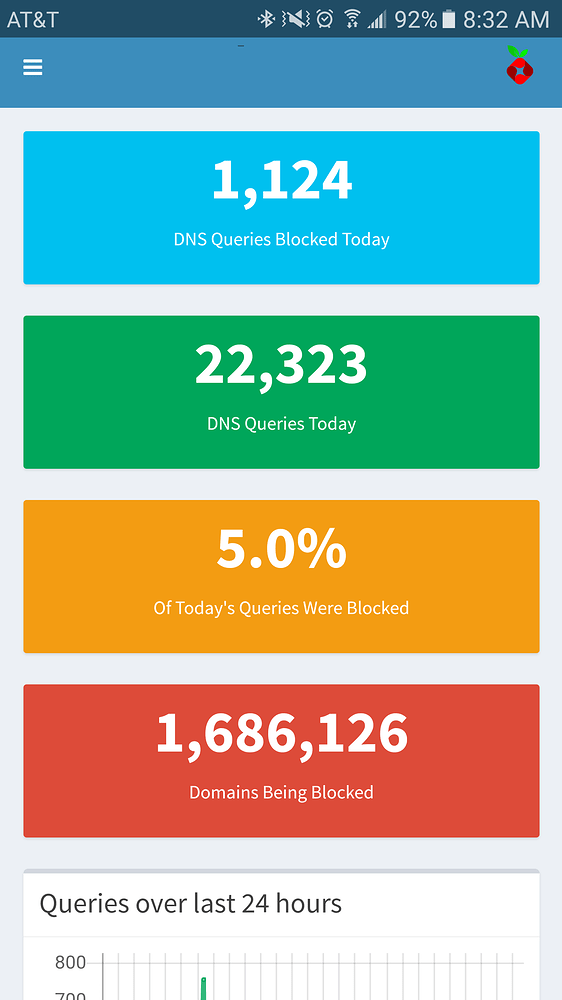
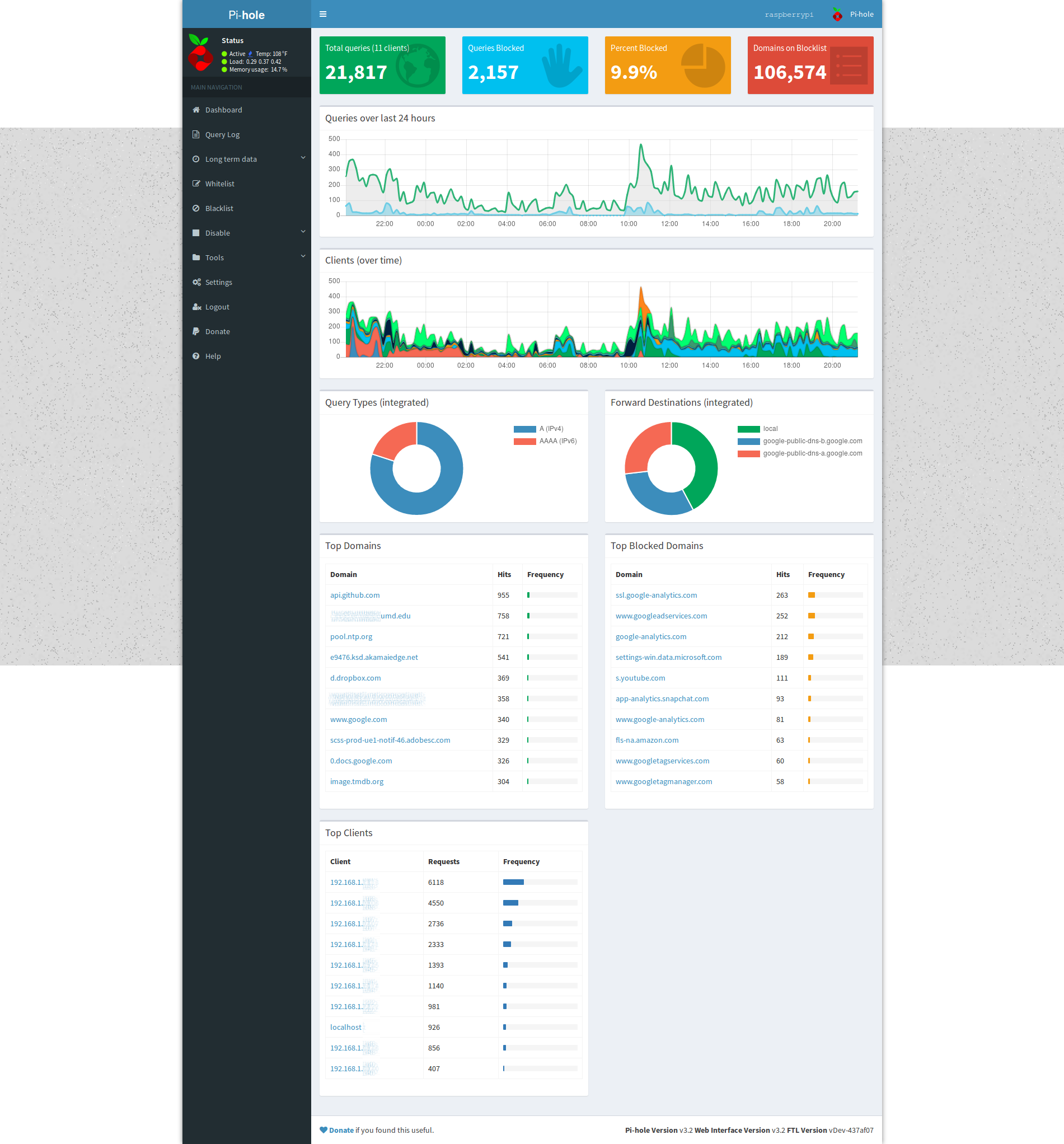
Overall Pi-hole has done an excellent job at reducing the amount of advertising and tracking traffic on my network. At the time of writing, Pi-hole blocks on average around 20.4% of the queries it receives. It is quite alarming to look through the query logs and see how often devices on your network are "phoning home" with analytics data.
I encourage anyone to give Pi-hole a shot, whether it be a basic installation or a setup as convoluted as my own. If you run into any issues, both the Pi-hole Userspace and the subreddit have many resources and knowledgable individuals who would be more than happy to help get you up and running.
A black hole for Internet advertisements
This branch is 4 commits ahead, 2300 commits behind pi-hole:master.
Failed to load latest commit information.
Block ads for all your devices without the need to install client-side software. The Pi-hole™ blocks ads at the DNS-level, so all your devices are protected.
Digital Ocean helps with our infrastructure, but our developers are all volunteers so your donations help keep us innovating. Sending a donation using our links below helps us offset a portion of our monthly costs.
If you wish to read over the script before running it, run nano basic-install.sh to open the file in a text viewer.
Once installed, configure your router to have DHCP clients use the Pi as their DNS server and then any device that connects to your network will have ads blocked without any further configuration. Alternatively, you can manually set each device to use Pi-hole™ as their DNS server.
The Pi-hole™ is an advertising-aware DNS/Web server. If an ad domain is queried, a small Web page or GIF is delivered in place of the advertisement.
The gravity.sh does most of the magic. The script pulls in ad domains from many sources and compiles them into a single list of over 1.6 million entries (if you decide to use the mahakala list). This script is controlled by the pihole command. Please run pihole -h to see what commands can be run via pihole.
The automated install is only for a clean install of a Debian family or Fedora based system, such as the Raspberry Pi. However, this script will work for most UNIX-like systems, some with some slight modifications that we can help you work through. If you can install dnsmasq and a web server, it should work OK. If there are other platforms you'd like supported, let us know.
The Web interface will be installed automatically so you can view stats and change settings. You can find it at:
http://192.168.1.x/admin/index.php or http://pi.hole/admin
Domains can be whitelisted and blacklisted using either the web interface or the command line. See the wiki page for more details
The settings page lets you control and configure your Pi-hole™. You can do things like:
Pi-hole™ ships with a built-in DHCP server. This allows you to let your network devices use Pi-hole™ as their DNS server if your router does not let you adjust the DHCP options.
A basic read-only API can be accessed at /admin/api.php. It returns the following JSON:
The same output can be achieved on the CLI by running chronometer.sh -j
You can view real-time stats via ssh or on an 2.8" LCD screen. This is accomplished via chronometer.sh.
A black hole for Internet advertisements
Audio Porno Rasskaz Mom Com
Naked Men Fuck
Nude Outdoor Tube
Granny 1.7 Mod Apk
Ass Kiss Cuckold
How To Setup Pi-hole with OpenWrt - Embedded Knowledge Sharing
Network Ad Blocking with Pi-hole and OpenWrt
GitHub - drkno/pi-hole-lede-openwrt: A black hole for ...
How to Use Pi Hole on your OpenWrt Router
Настройка Pi-Hole на OpenWRT - allqa.app
Setting up Pi-Hole on OpenWRT : pihole - reddit
PiHole directly on Routers (Tomato ... - Pi-hole Userspace
Best way to integrate Pi-Hole : openwrt
Pi Hole Openwrt