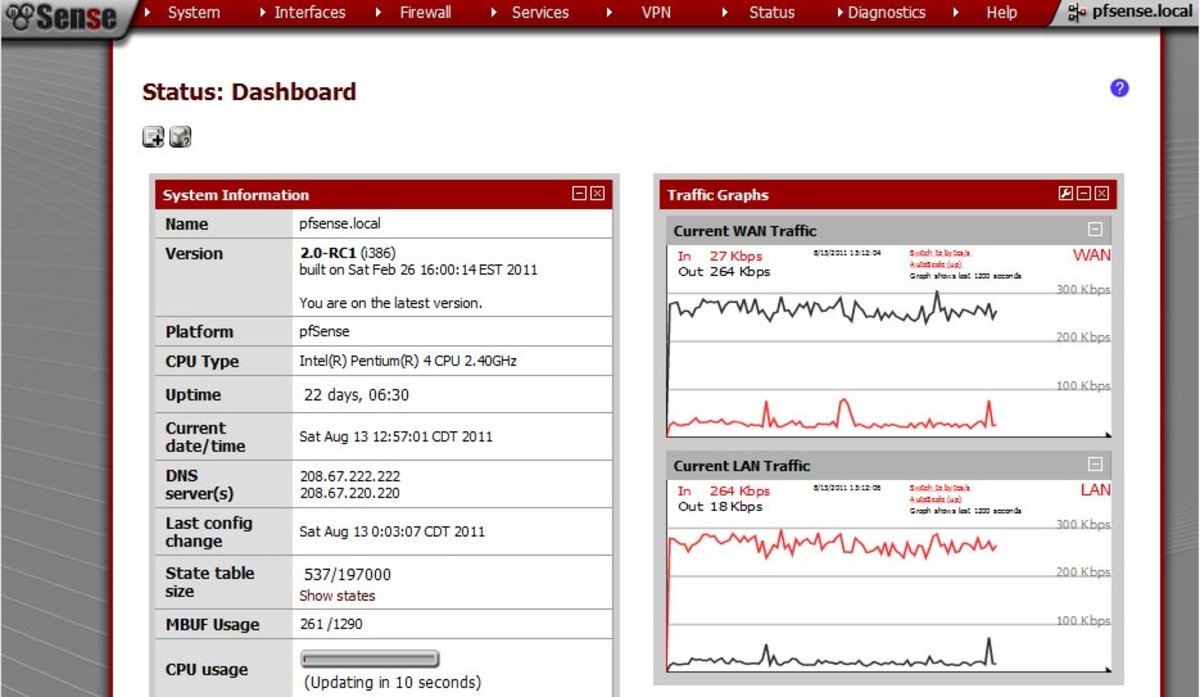
Pfsense Private Users

🛑 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE👈🏻👈🏻👈🏻
Эта тема была удалена. Только пользователи с правом управления темами могут её видеть.
I recently wrote a tutorial on configuring pfSense as a VPN Client to Private Internet Access: http://www.bodenzord.com/archives/324
I thought I'd reproduce it here as a way to say thanks to the developers as well as give back to the pfSense community. My hope is that it'll help others through the process of setting this up.
If you find errors or I'm incorrect in any way, please let me know.
Configuring pfSense as VPN Client to Private Internet Access
Configuring pfSense as a VPN Client to Private Internet Access(PIA) is relatively easy. However, there are a few things to watch out for, especially after pfSense version 2.1.1. In this tutorial, I'll show you how.
There are other tutorials available around the internet, but I feel that some are severely inaccurate or missing a couple key steps. When I was configuring my setup, I could not find a single tutorial that was complete and accurate. As a result, I had to piecemeal everything together to get it to work.
Additionally, pfSense changed some of the code in version 2.1.1 with regards to Outbound NAT rules to OpenVPN interfaces. Beforehand, things were a bit easier. But starting with version 2.1.1, there are additional configuration settings that need to be set. It's not that big of a deal. Before it was automatic. Now it's manually configured.
Anyway, I am going to break this down into a step-by-step process without any explanation along the way. Then afterwards, I'll do my best to explain a few details and to highlight what change was made in pfSense 2.1.1.
This tutorial assumes the following:
You have a current subscription to Private Internet Access with a valid username and password.
You are using pfSense version 2.1.1 or newer
You have pfSense setup and configured as a base installation with a single WAN interface connected to a modem and a single LAN interface with one or more clients.
Firewall LAN rules have a default "Allow All". (I know that this is not best practice, but after following this tutorial, you can then revise your firewall LAN rules accordingly.)
Also note that I will be referencing Private Internet Access as PIA throughout the tutorial.
We need to acquire a few things first. Start by downloading openvpn.zip from Private Internet Access, https://www.privateinternetaccess.com/openvpn/openvpn.zip. This supplies their ca.crt file and .ovpn files, which include the names of their servers. You won't be using any of the .opvn files directly, but you can view them in a text editor to get the name of a specific server you want to connect to. Additionally, you'll need your username and password, which were provided to you by PIA. We'll be using these later.
Next, log into your pfSense administration panel. Now let's go through the following steps in greater detail:
Create password file to store your PIA username and password
Create/configure an OpenVPN interface
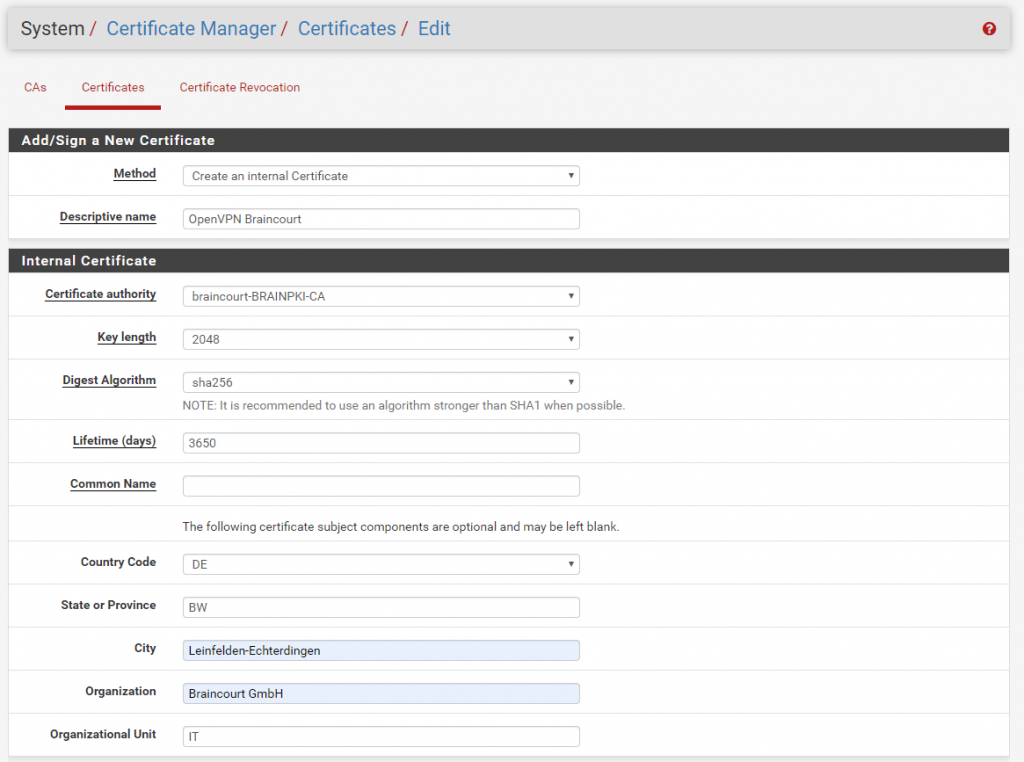
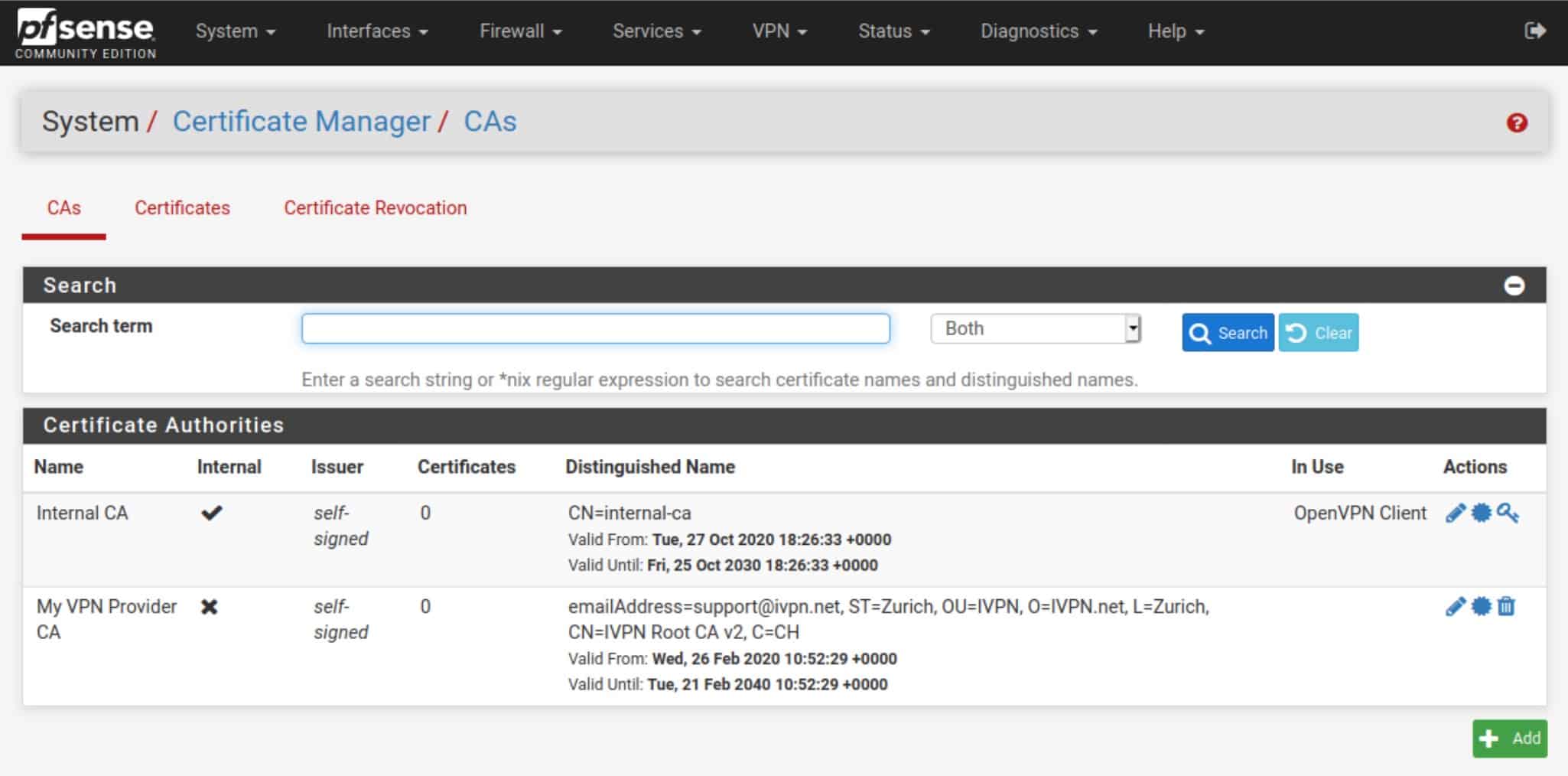
Select menu item: System->Cert Manager
Click Plus symbol to add CA Certificate
Method = Import an existing Certificate Authority
Certificate data = (copy/paste your ca.crt certificate provided by PIA)
–---BEGIN CERTIFICATE-----
.
.
.
-----END CERTIFICATE-----
Certificate Private Key = (leave blank)
Serial for next certificate = (leave blank)
Select menu: Diagnostics->Edit File
Enter the following in the Save/Load from path: /etc/openvpn-password.txt
Add the following two lines in the text box, substituting your username and password provided to you by PIA:
username
password
Server Mode = Peer To Peer (SSL/TLS)
Server host or address = us-texas.privateinternetaccess.com (or any server you choose that PIA offers)
Proxy host or address = (leave blank)
Proxy authentication extra options = none
Server host name resolution = checked, Infinitely resolve server
Description = PIA OpenVPN (or whatever you desire)
TLS Authentication = unchecked, Enable authentication of TLS packets
Peer Certificate Authority = PIAVPN
Client Certificate = *webConfigurator default In use
Encryption algorithm = BF-CBC (128-bit)
Hardware Crypto = No Hardware Crypto Acceleration
IPv4 Tunnel Network = (leave blank)
IPv6 Tunnel Network = (leave blank)
IPv4 Remote Network/s = (leave blank)
IPv6 Remote Network/s = (leave blank)
Limit outgoing bandwidth = (leave blank)
Compression = checked, Compress tunnel packets using the LZO algorithm
Advanced = (enter the following into the text field, one item per line with a semi-colon separating each)
auth-user-pass /etc/openvpn-password.txt;
verb 5;
remote-cert-tls server
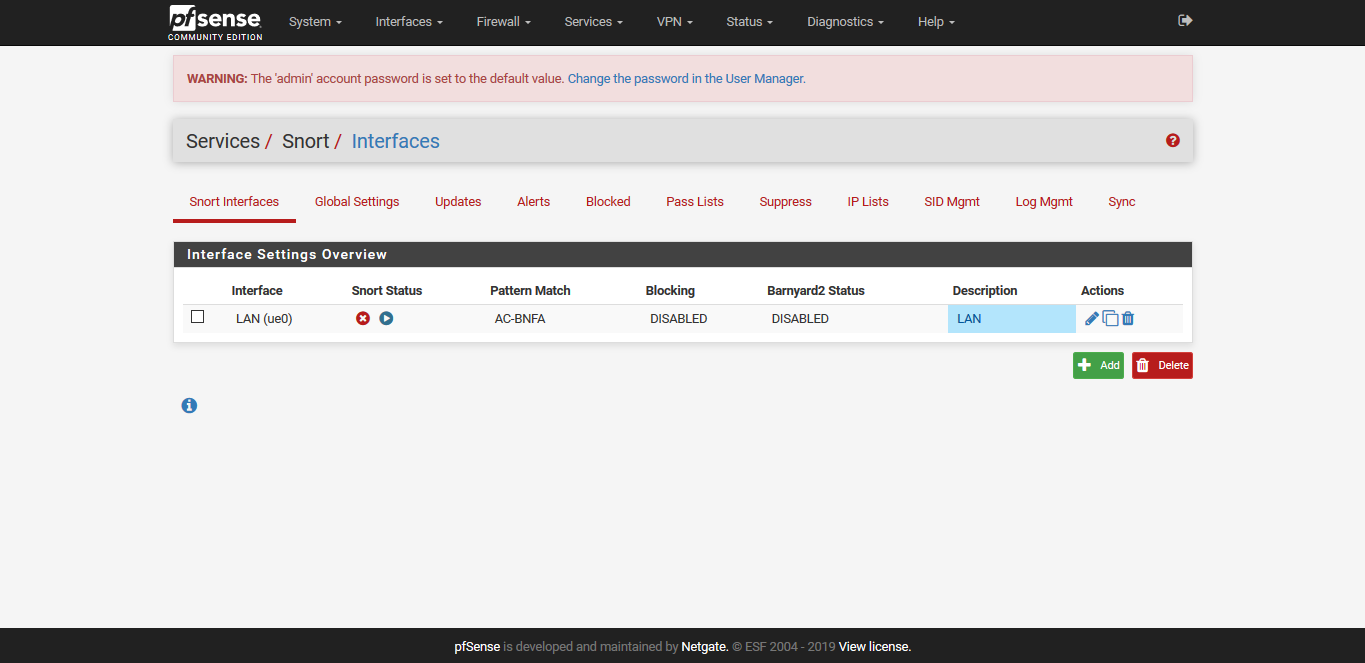
Click the Plus button to add new interface. The new interface will be named OPT1 with a network port of ovpnc1().
Click on OPT1 to edit the interface
Check the radio button: Manual Outbound NAT rule generation (AON - Advanced Outbound NAT)
At this point, automatic rules that were in use in Automatic outbound NAT will be generated. It will look like the following, with the exception that the Source IP subnet will match your LAN IP subnet.
The next step is to duplicate each of these rules, but change the NAT Address from WAN to PIAVPN. Start with the first rule by clicking the Plus sign immediately to the right of the line "to add a new NAT based on this one." A new page will open. Configure as follows:
Description = Auto created rule for ISAKMP - LAN to PIAVPN
Repeat this process for the other two rules. When completed, it should resemble the following:
Finally, click the Apply Changes button
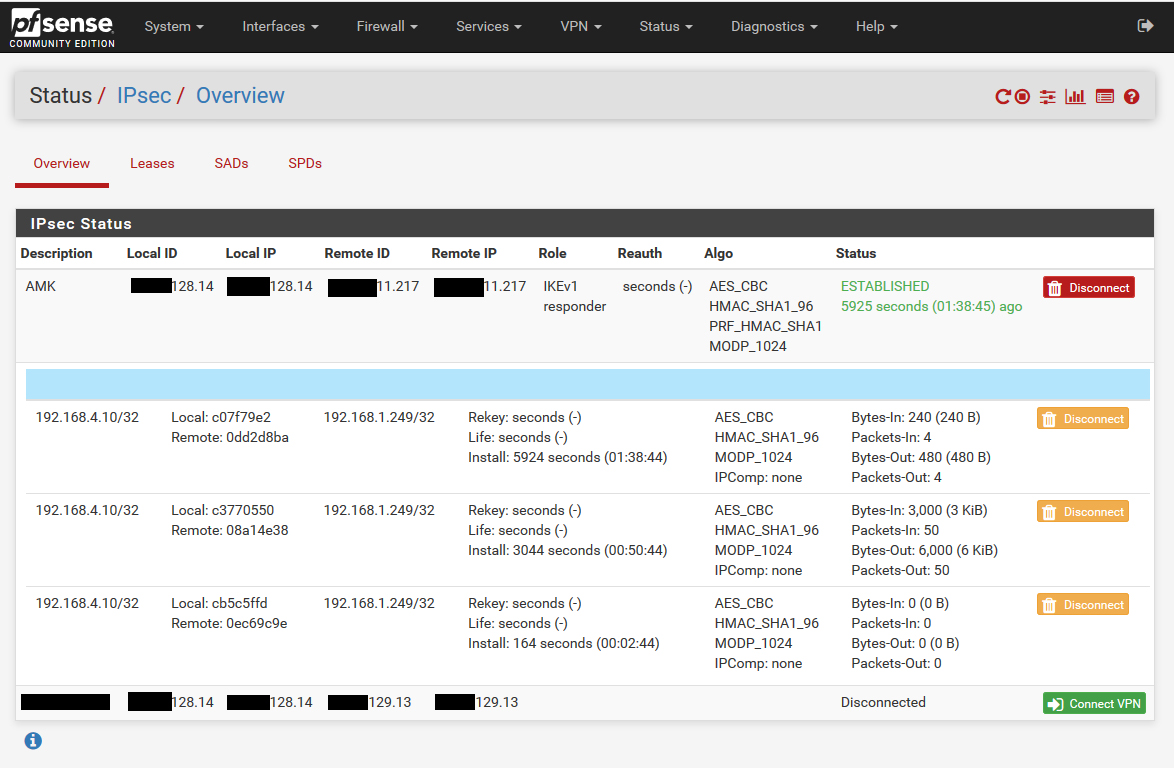
At this point, your system is configured. The only thing you may need to do is restart your OpenVPN Service.
Status should be UP (but it may be DOWN)
My recommendation is to click on the Restart OpenVPN Service button no matter what the status is. It's the middle button to the right of the service.
Look for confirmation in your logs:
With a client on the LAN, use a browser and go to ifconfig.me
Now that we have the VPN up and running, allow me to explain a few things.
When I setup the OpenVPN client, you will have noticed that I added an advanced directive: verb 5. This advanced setting is simply used to increase the verbosity of the OpenVPN log files. This is a personal preference and you can adjust accordingly. However, as I continue to explain a few things, I'll reference the log files. Without this advanced directive, your log files will differ and you may not see the same logs that I reference.
Another advanced directive I configured was: remote-cert-tls. This advanced setting is used to prevent Man-In-The-Middle attacks, and the server needs to be configured properly for this to work, which Private Internet Access servers are.
–remote-cert-tls client|server
Require that peer certificate was signed with an explicit key usage and extended key usage based on RFC3280 TLS rules.
This is a useful security option for clients, to ensure that the host they connect to is a designated server.
This is an important security precaution to protect against a man-in-the-middle attack where an authorized client attempts to connect to another client by impersonating the server. The attack is easily prevented by having clients verify the server certificate using any one of –remote-cert-tls, --tls-remote, or --tls-verify.
Thus, 'remote-cert-tls server' means that the certificate has "TLS Web Server Auth" as an extended property.
So when configuring your OpenVPN client with this directive, take a look at your logs. You will see the following lines that validate and verify the certificate. Without this advanced setting, these lines will not be in your logs and this validation is not performed:
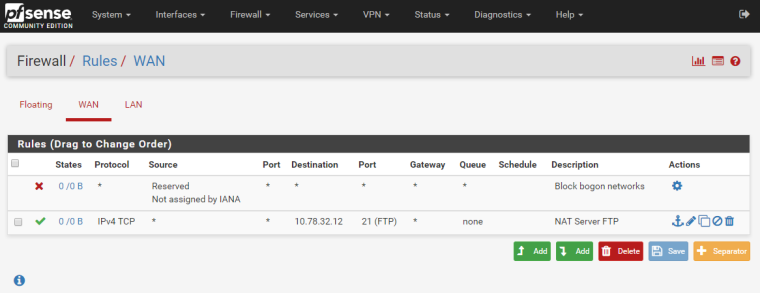
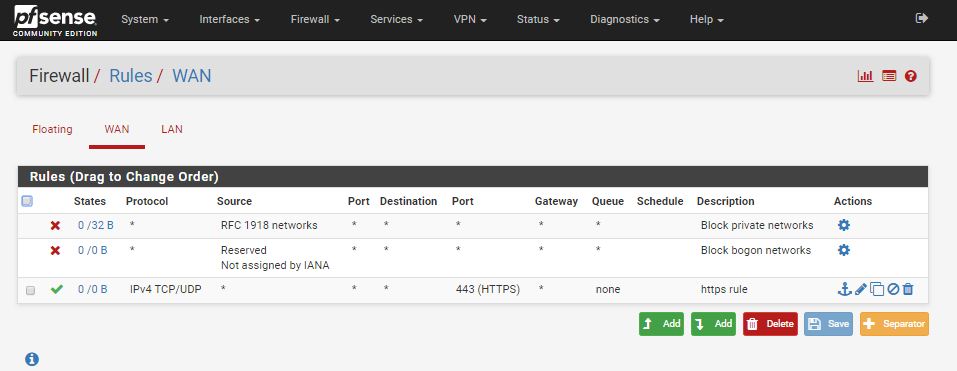
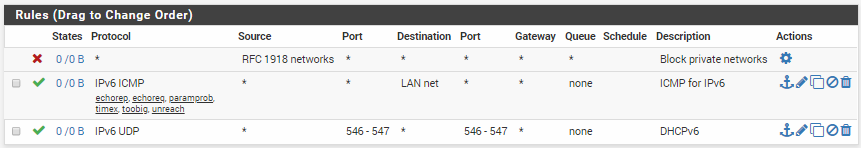
In some tutorials I found, I was instructed to configure my Firewall LAN rules with an advanced setting to specifically choose my Gateway. I found that this wasn't necessary be default with a base installation of pfSense. It's only necessary with more advanced firewall configurations. The following image is how the default firewall rules are for the LAN.
Take note of the middle rule for IPv4 protocol. This is the default "Allow All" rule that says that any Source IP with any Port is allowed to go to any Destination IP to any Port on any Gateway. With this rule, the decision of which Gateway(interface) to use, WAN or PIAVPN, is made via the system routing table. Now we can override this so that we force LAN traffic to use a specific gateway. As an example, do the following:
Click on the Edit button for this default "Allow All" rule. (The button with lower-case 'e' to the right of the rule.)
Scroll all the way to the bottom to the Advanced Features section.
Click the Advanced button next to Gateway.
Change the dropdown box to PIAVPN_VPN4
You'll return to Firewall->Rules->LAN tab. Click the Apply Changes button.
Now that this has changed, you'll see that your OpenVPN Gateway has been specified for this rule, and this means that all LAN traffic bypasses the system routing table and always goes out your OpenVPN interface to the Private Internet Access server.
Now I want to point out that we haven't made the VPN function any differently. All we've done is force LAN traffic out the VPN interface instead of having the system routing table make that same decision for us. Why would we want to do this? Well, by creating specific rules for your firewall, you can then force certain clients out the VPN or out the WAN or whatever you want to do. This is just one more tool to allow you to control the firewall exactly how you want.
If you were setting up your own peer-to-peer VPN and you had control of both the VPN Server and VPN Client, then you wouldn't need to NAT the client-side LAN subnet to the VPN tunnel IP as we're doing in this tutorial. Instead, you would use routing and NAT on the server to achieve your goal of reaching the internet through the VPN Server. Obviously, we have no control of PIA's servers. Additionally, PIA doesn't know the specific subnet we're using on our LAN so that they can configure their servers to route and NAT our traffic out their public IP. Instead, they route and NAT the VPN tunnel IP, because that's what they have control over. This is why we have to create an OpenVPN interface, which the VPN tunnel IP attaches to, and NAT our LAN traffic to it. In the end, this is a double-NAT situation, once from LAN-to-VPN-tunnel-IP on the VPN Client, and again from VPN-tunnel-IP-to-public-IP on the VPN Server.
As you'll recall, we configured our Outbound NAT rules manually. These rules are what NATs our LAN subnet to the VPN tunnel IP. But why do we have to manually configure these rules? Why aren't they automatically created?
With versions of pfSense prior to 2.1.1, it wasn't necessary to manually configure the NAT rules as we've done. However, the configuration change from Automatic Outbound NAT to Manual Outbound NAT was still required. It's just that prior to 2.1.1, the necessary rules you needed to get your LAN subnet NAT'ed to your VPN tunnel IP were automatically created for you when you made this change to Manual Outbound NAT - as odd as that may sound.
So you may be wondering, "Why are NAT rules automatically created in Manual mode but not in Automatic mode? Isn't this a break in logic?" I thought the same, so I posted my questions to the pfSense forum in the hopes of discovering why: https://forum.pfsense.org/index.php?topic=73727.0. The funny thing is, I got my answers, but the end result was a change in code starting with version 2.1.1 which requires manual configuration for Outbound NAT to OpenVPN interfaces.
To put it simply, prior to version 2.1.1, Automatic Outbound NAT rules skipped OpenVPN interfaces, yet these interfaces were still considered when automatically creating the first set of manual rules. Starting with version 2.1.1, the code was since been changed so that OpenVPN interfaces are also skipped when automatically creating the first set of manual rules. Here is the bug submission at Redmine if you want further clarification: https://redmine.pfsense.org/issues/3528
I appreciate your taking the time to cobble together such an thoroughly written tutorial on setting up PIA on pfSense. I struggled with this and found much like yourself that I had to use bits and pieces of several tutorials before I could get the VPN up and running.
This should probably be a sticky to make it easy to find.
Much appreciated, thank you for taking the time to do this.
What do you use / recommend using as a DNS server?
Specifically, can I use PIA's DNS servers? Reason to ask is when I do, after some time (a day or two) the system stops internet communication with DNS failure.
That's a good in depth tutorial, thanks for all your efforts :)
One (very) minor nit, I would suggest that you remove the "verb 5" entry once you have verified that the connection is up and running properly. I use that entry myself when I'm trying to diagnose OpenVPN issues (sometimes I'll even use verb 7 for more info). In the long run I find the log files just get filled with too much excess using 'verb 5' for a stable connection.
It's useful for seeing the initial configuration of your setup, but is a bit excessive in normal operation.
Just my $0.02, thanks for all your work ;D
What do you use / recommend using as a DNS server?
Specifically, can I use PIA's DNS servers?
The easiest way that I've found is to go to System->General Setup, and enter the DNS servers that you want to use. It can be Google's or PIA's or any other. But then uncheck: "Allow DNS server list to be overridden by DHCP/PPP on WAN". After saving, a DNS Leak test at www.dnsleaktest.com or ipleak.net, will show the DNS servers you specified.
One (very) minor nit, I would suggest that you remove the "verb 5" entry once you have verified that the connection is up and running properly. I use that entry myself when I'm trying to diagnose OpenVPN issues (sometimes I'll even use verb 7 for more info). In the long run I find the log files just get filled with too much excess using 'verb 5' for a stable connection.
Thanks for the tip. Much appreciated.
Hello. I appreciate the tutorial in getting things running with PIA, and I've been able to get all outbound on my network through PIA just fine however that is not what I want.
The thing is, it seems that the tunnel takes over all outbound over the WAN as soon as it is started. That is, when starting the tunnel, if using the automatic NAT rules - I cannot get out to the WAN at all. Once creating the manual rules, you can get out to the WAN but everything is going out to the WAN. I really just wanted to keep the tunnel up but have the LAN continue to go directly to the WAN until I specifically change something to selectively go through the tunnel (such as, only for a specific LAN IP).
What am I missing here in terms of setting things up so at the very least I have this situation as a starting point:
Basically, I thought bringing the tunnel up would just be like adding another NIC to the system with no link or further configuration. Clearly I was wrong - I need to disable the tunnel for now as it is just not workable for us to have everything always going through it.
Edit: Well, I've figured out I need the route-nopull client option to keep the vpn server from mangling up my default routes. I just need to figure out the rest now in terms of getting specific IPs traffic all through the tunnel … do I use route options in openvpn or outbound nat or...? Fun stuff...
Edit Again: Okay, had to assign an interface to the tunnel. The tunnel refused to work with route-nopull... so that had to stay. Then I created manual firewall lan rule for specific host to use the VPN gateway and modified the existing LAN to WAN rule placed underneath to use the WAN gateway. Then I needed to create a new rule for the VPN interface just to allow traffic through it. Finally, I added outbound NAT for the host above the auto created rule for the VPN interface.
It all seems rather messy to me, I may very well be doing more than I really need to but it seems to be working. All hosts on the LAN are using the normal WAN except for a specific one that I want always routing through the VPN.
This is much better than the old situation of that host having to open it's own tunnel which was prone to going down during network interruptions, and the other host has a much lower power CPU than my pfSense router so distributing the load of OpenVPN to the router in this case frees up a lot of cycles on that host.
I think you may be overcomplicated things here. If you follow the tutorial, when finished the tunnel should be routing all traffic due to the firewall rule that was created in the tutorial, you would just need to disable or edit it to only push the traffic you need. It's pretty easy to set up for one host. Just createa new/edit the existing rule with the source being the machine ip that you want to go through the tunnel, and under advanced the VPN interface you have created, usually OPT1. You can do the same using specific destination ports or destination ip ranges if you want to get fancy and only push certain traffic through the tunnel. i.e. for geoblocked services etc.
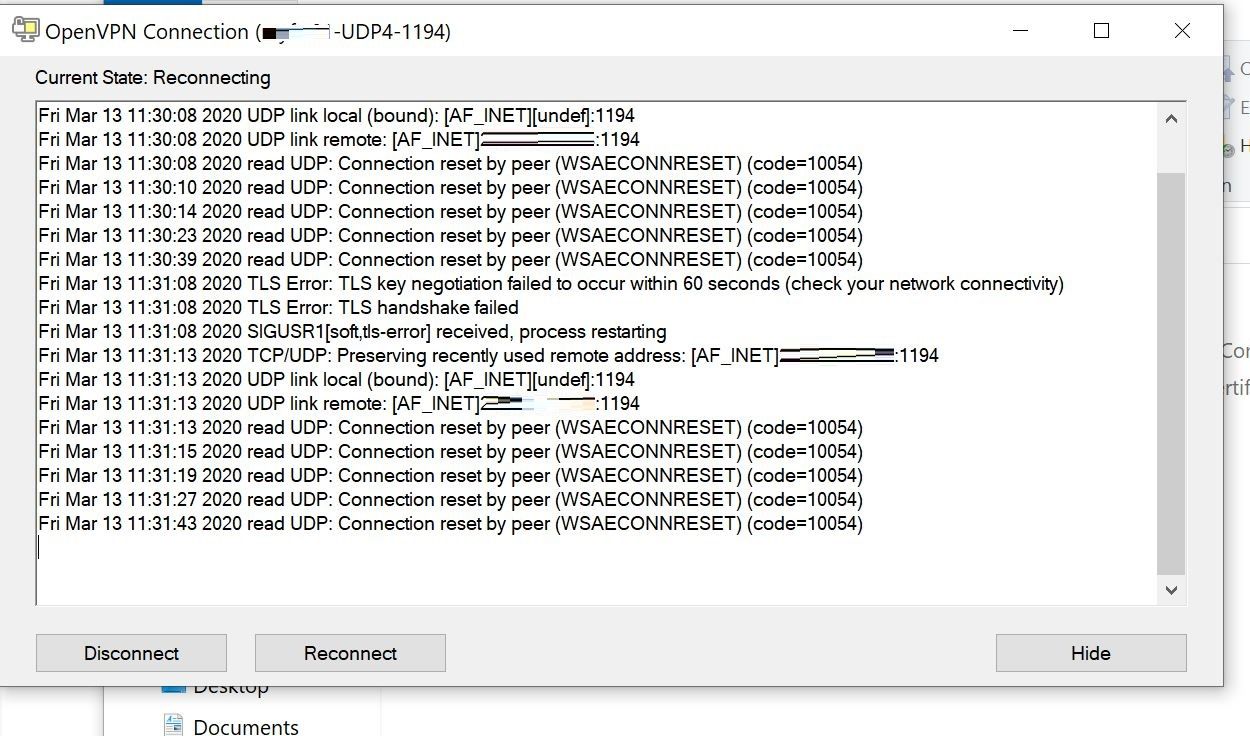
Anyone else have the tunnel go down rather frequently using this service? I am connecting to the US-East server and I find my connection reset rather frequently at times? FWIW my WAN connection very rarely goes down so it's not that. All I see in the logs is the following when it disconnects:
Just wondering if this is normal for PIA? Seems to be happening multiple times daily. I don't recall having this issue when I had PIA openvpn setup on one of my linux boxes but maybe I just wasn't watching it as closely. :-)
the tunnel takes over all outbound over the WAN as soon as it is started.
This tutorial is written so that all LAN traffic is routed through the VPN using the system routing table. So this is to be expected.
If you followed this tutorial exactly, then there are two ways that I know of to accomplish what you want.
Go to Advanced settings under every firewall rule and assign the WAN interface as your Gateway.
Then create a specific rule for your single computer on the LAN, with the PIAVPN gateway selected.
Move this new rule to the top of the list.
With this setup, all traffic bypasses the system routing table, and the traffic is routed via each rule through a specific gateway.
Add route-nopull to the Advanced Configuration settings of the VPN
Create a firewall rule for the specific computer on the LAN with an Advanced setting that specifically chooses the PIAVPN Gateway.
Move this new rule to the top of the list.
To explain how option 2 works, this is from the OpenVPN manual:
So, this tells the client not to pull the default route from the server, yet it pulls all other necessary TCP/IP settings. And if you look at your system routing table (Diagnostics->Routes) before and after changing this setting, you'll see the pulled route pres
Anime Blonde Busty
Nude Lingerie Lowdown Digest
Search Xvideos Hist Android App
Brazzers House 2 Episodes
Mature Nl Hairy Porno
Certificate Management — Certificate Management | pfSen…
GUIDE: PFSense with Private Internet Access and Plex : PFSE…
User Management and Authentication — Manage Loca…
pfSense® - World's Most Trusted Open Source Firewall
pfsense Privacy Policy
Protect home network using subnets with pfSense - NetOSec
pfSense - Part 3: Allowing and Blocking Individual ...
Announcing pfSense® Plus - Netgate
Pfsense Private Users