Penetration Testing Nessus

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
The most comprehensive risk-based vulnerability management solution.
Tenable.ep fully integrates all capabilities as part of one solution for ultimate efficiency.
The #1 vulnerability assessment solution.
Spend less time and effort assessing, prioritizing and remediating vulnerabilities so you can stay one step ahead of attackers.
Secure Active Directory and disrupt attack paths.
Discover and prioritize Active Directory vulnerabilities and misconfigurations to disrupt attack paths before attackers exploit them.
See everything. Predict what matters. Managed on-prem.
Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities.
See everything. Predict what matters. Managed in the cloud.
Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities.
Complete visibility into your converged IT/OT infrastructure.
Get the operational technology security you need. Reduce the risk you don't.
Calculate, communicate and compare your cyber exposure.
The visualization, analytics and measurement solution to transform vulnerability data into meaningful insights.
Our goal is to ensure an outstanding customer experience at every touch point.
Our Vision: Empower all Organizations to Understand and Reduce their Cybersecurity Risk
At Tenable, we're committed to collaborating with leading security technology resellers, distributors and ecosystem partners worldwide.
Technology Partners
Technology Ecosystem
Your modern attack surface is exploding. Learn how you can see and understand the full cyber risk across your enterprise
All
Careers
Company
Cyber Exposure Alerts
Engineering
News and Views
Products
Remote Workforce
Research
Team Tenable | News and Views
July 15, 2020 | 4 Min Read
Penetration tests and vulnerability assessments make for an excellent tandem approach to cybersecurity.
While similar — and sometimes confused for each other — penetration tests and vulnerability assessments are decidedly not the same thing. There are important, fundamental differences that actually allow these two tactics to be used in tandem.
Vulnerability assessments and penetration tests both look for weaknesses in your network. In the former, the key goal is to identify, quantify and analyze vulnerabilities within IT infrastructure, enumerating all of the hypothetical routes to a cyberattack. This applies to everything from compromised IoT devices to applications with glitches in their source code. The process is often automated, and in many organizations, can ultimately identify hundreds, if not thousands, of vulnerabilities.
A penetration test, meanwhile, is an authorized attack on your own systems — a form of ethical hacking — that exploits vulnerabilities so that a pen tester can attempt to gain access to systems and data. The idea is to see how easy or difficult it is to overcome your defenses, testing the hypothetical risks found during a vulnerability assessment. Pen testers use a well-known arsenal of "white hat" hacking tools to complete their sanctioned attacks, including the Social Engineering Toolkit1 and Pen Testers Framework.2 But a pen tester's manual skill and creativity are just as important to successfully find an exploitable system, map the network, gain access to other systems and test defenses. Think of it as the infosec version of criminal profiling: Only by imagining the mindset of a malicious hacker and mimicking their activities can a well-intentioned pen tester truly understand the risk an organization faces and adequately prepare to face it.
Active scanning proactively searches for vulnerability signs at the time the scan is initiated. Passive scans monitor network activity and wait to see indicators of vulnerabilities. Active scanning is a core function of Nessus Professional, and for organizational users, it is the most direct method of searching for vulnerabilities and an excellent complement to any penetration test. As an example, if a pen tester is looking for an exploitable hole in a website, they could use a web application scanner to identify specific ways in which applications are vulnerable to attacks, such as cross-site scripting or SQL injections, and then explore those areas in greater detail (either with pen testing tools or manual methods).
Vulnerability scan results save time and resources by identifying the areas a pen test should focus on most closely. For example, imagine that scan results show your Apache framework is vulnerable. But if you know you can easily mitigate the vulnerability by removing the application entirely, simply go ahead and do that! That's a much more efficient approach than using pen testing resources to explore the weaknesses of a program in great detail.
The goal of active scanning should be to focus pen testing efforts, not expand them. If you’re using penetration testing to double-check everything your active scanning solution finds, you’re just adding more work.
Vulnerability scanning is necessary for hardening systems to ensure information security. At Tenable, results from your Nessus scans can be integrated with popular penetration testing tools. This makes it even easier to start penetration testing from a solid foundation.
While active scanning can help focus your penetration testing efforts, what about identifying flaws and vulnerabilities while offline? This is especially important if you have not been running your scans on a frequent basis: Any new applications you added between scans won't have been screened for weaknesses, leaving you potentially exposed to glitches you didn't know about. Unmanaged assets with vulnerabilities — or those with settings that aren’t consistent with policy — are great targets to exploit.
Nessus Professional's Live Results feature, once activated, performs an offline vulnerability assessment separately from your standard scan every time plugins are updated. Based on its examination of data from past scans, it searches for possible glitches and sends alerts of suspicious findings. At that point, you can run an active scan with Nessus to validate the findings.
Preceding a penetration test and other usual scans with Live Results can make life easier for the pen tester. Live Results can help guide infosec professionals while they conduct their tests, aiding them in identifying how their examination can be redirected. From there, testers can comprehensively assess the situation and conclude which vulnerabilities must be closely tested and explored to gauge how easily they can be exploited.
The combination of active scanning with offline vulnerability assessments using Live Results from Nessus represents a strong strategy for improving penetration testing success and protecting your network.
Try it out for yourself with a free 7-day trial of Nessus Professional.
Nessus
Penetration Testing
Threat Management
Vulnerability Scanning
Enter your email to receive the latest cyber exposure alerts in your inbox.
© 2021 Tenable®, Inc. All Rights Reserved | Privacy Policy | Legal | 508 Compliance
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Sign up now.
By registering for this trial license, Tenable may send you email communications regarding its products and services. You may opt out of receiving these communications at any time by using the unsubscribe link located in the footer of the emails delivered to you. You can also manage your Tenable email preferences by visiting the Subscription Management Page.
Tenable will only process your personal data in accordance with its Privacy Policy.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
2 Years
429 908,08 руб
(Save 9 186,07 ₽)
3 Years
628 327,19 руб
(Save 27 558,21 ₽)
Please contact us or a Tenable partner.
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Nessus® is the most comprehensive vulnerability scanner on the market today. Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Details regarding your eval will be sent to this email.
By registering for this trial license, Tenable may send you email communications regarding its products and services. You may opt out of receiving these communications at any time by using the unsubscribe link located in the footer of the emails delivered to you. You can also manage your Tenable email preferences by visiting the Subscription Management Page.
Tenable will only process your personal data in accordance with its Privacy Policy.
You will receive an email within 10 minutes with details on how to activate your Nessus eval.
Nessus® is the most comprehensive vulnerability scanner on the market today. Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year. Full details here.
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable.io platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
By registering for this trial license, Tenable may send you email communications regarding its products and services. You may opt out of receiving these communications at any time by using the unsubscribe link located in the footer of the emails delivered to you. You can also manage your Tenable email preferences by visiting the Subscription Management Page.
Tenable will only process your personal data in accordance with its Privacy Policy.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Please contact us or a Tenable partner.
Thank you for your interest in Tenable.io Web Application Scanning. A representative will be in touch soon.
Enjoy full access to the only container security offering integrated into a vulnerability management platform. Monitor container images for vulnerabilities, malware and policy violations. Integrate with continuous integration and continuous deployment (CI/CD) systems to support DevOps practices, strengthen security and support enterprise policy compliance.
By registering for this trial license, Tenable may send you email communications regarding its products and services. You may opt out of receiving these communications at any time by using the unsubscribe link located in the footer of the emails delivered to you. You can also manage your Tenable email preferences by visiting the Subscription Management Page.
Tenable will only process your personal data in accordance with its Privacy Policy.
Tenable.io Container Security seamlessly and securely enables DevOps processes by providing visibility into the security of container images – including vulnerabilities, malware and policy violations – through integration with the build process.
Thank you for your interest in the Tenable.io Container Security program. A representative will be in touch soon.
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
Visualize and explore your Cyber Exposure, track risk reduction over time and benchmark against your peers with Tenable Lumin.
By registering for this trial license, Tenable may send you email communications regarding its products and services. You may opt out of receiving these communications at any time by using the unsubscribe link located in the footer of the emails delivered to you. You can also manage your Tenable email preferences by visiting the Subscription Management Page.
Tenable will only process your personal data in accordance with its Privacy Policy.
Contact a Sales Representative to see how Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Thank you for your interest in Tenable.ot. A representative will be in touch soon.
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Thank you for your interest in Tenable.ad. A representative will be in touch soon.
The most comprehensive risk-based vulnerability management solution.
Tenable.ep fully integrates all capabilities as part of one solution for ultimate efficiency.
The #1 vulnerability assessment solution.
Spend less time and effort assessing, prioritizing and remediating vulnerabilities so you can stay one step ahead of attackers.
Secure Active Directory and disrupt attack paths.
Discover and prioritize Active Directory vulnerabilities and misconfigurations to disrupt attack paths before attackers exploit them.
See everything. Predict what matters. Managed on-prem.
Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities.
See everything. Predict what matters. Managed in the cloud.
Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities.
Complete visibility into your converged IT/OT infrastructure.
Get the operational technology security you need. Reduce the risk you don't.
Calculate, communicate and compare your cyber exposure.
The visualization, analytics and measurement solution to transform vulnerability data into meaningful insights.
Our goal is to ensure an outstanding customer experience at every touch point.
Our Vision: Empower all Organizations to Understand and Reduce their Cybersecurity Risk
At Tenable, we're committed to collaborating with leading security technology resellers, distributors and ecosystem partners worldwide.
Technology Partners
Technology Ecosystem
Your modern attack surface is exploding. Learn how you can see and understand the full cyber risk across your enterprise
All
Careers
Company
Cyber Exposure Alerts
Engineering
News and Views
Products
Remote Workforce
Research
Ron Gula |
February 23, 2012 | 6 Min Read
Cross referencing the results of your vulnerability scans with the list of public exploits helps identify likely targets for authorized penetration testing teams. Removing these vulnerabilities significantly raises the value of a penetration test since the team will have to work much harder to find issues that aren’t found through automation. There are many subtle issues to consider when correlating available exploits with vulnerabilities. In this blog entry, we’ll highlight these issues by considering exploit correlation with attacks available from the Metasploit project, Core, and Immunity with the results of a very large Nessus scan of several thousand web servers.
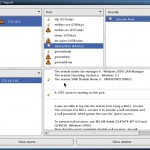
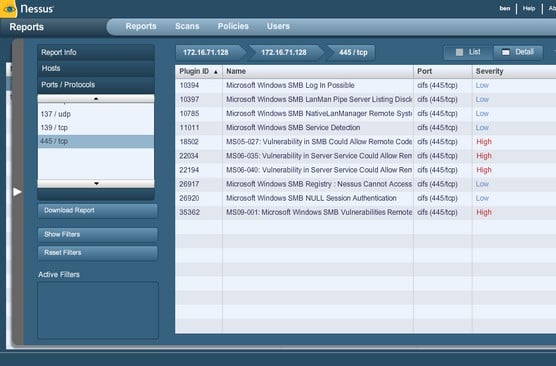
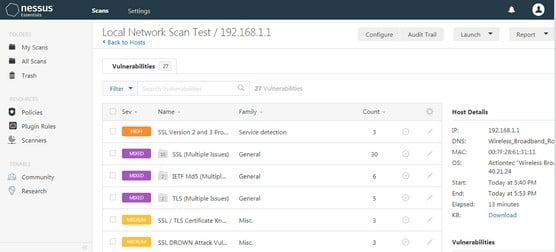
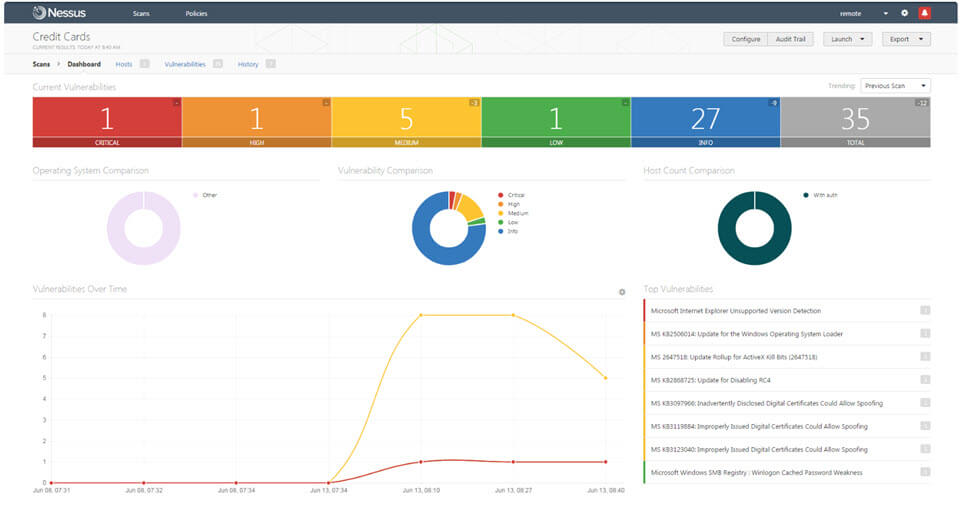
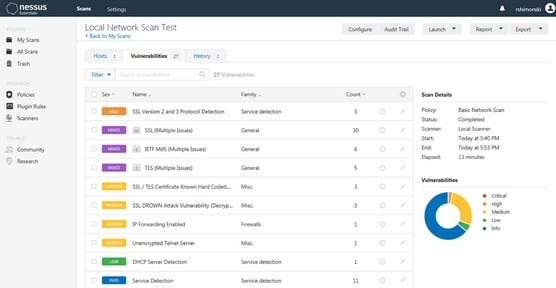
In the screenshot below, we’ve loaded the results of a Nessus scan of several thousand Internet-facing web servers into Nessus 5. We can see right away that there are six unique types of vulnerabilities that are “critical.” These are typically vulnerabilities with a CVSS score of 10. There are also ten instances of these six “critical” types of vulnerabilities. This is a very small percentage of the total population of scanned web servers.
When viewing the “high” vulnerabilities, it can be seen that there are many issues occurring on hundreds and thousands of the scanned systems.
If we add a filter to only show those vulnerabilities which can be exploited with an exploit from the CANAVAS framework, we see that it identifies two unique high and one medium severity vulnerabilities.
The type of issues that can be exploited by Core IMPACT can be seen in the following screen shot. In this case, CORE had an exploit available for one of the critical vulnerabilities identified by the original Nessus scan. A total of four unique vulnerabilities were identified as exploitable.
Finally, when using the list of exploits available with the Metasploit framework, a total of four unique vulnerabilities were identified as exploitable.
If you are using penetration testing to add value to your security audits, consider the following questions:
Were there any Critical or High vulnerabilities for which we didn’t have any exploits?
For Critical issues, Nessus plugin 45004 (Apache 2.2 < 2.2.15 Multiple Vulnerabilities) fired for three web sites and was correctly correlated by Core IMPACT and Metasploit, but there were five other critical vulnerabilities identified that were left untouched by the penetration tools. The bulk of these were critical remote security issues in HP’s System Management and Adobe’s Flash Media server web interfaces.
For the High issues, both Core IMPACT and Metasploit had exploits for Nessus plugin 50069 (Apache 2.0 < 2.0.64 Multiple Vulnerabilities), and these were on more than 5,000 systems. Neither had an exploit for Nessus plugin 32655 (Apache < 2.0.59 mod_rewrite LDAP Protocol URL Handling Overflow).
However, aside from these Apache issues, the bulk of the high severity issues identified by Nessus are spread across PHP versioning issues and web application vulnerabilities for which there aren’t identifying items, such as, CVE numbers on which to correlate. This shows how in some cases, it may be very easy to point out the presence of a vulnerability with a scanner, yet be very difficult to exploit with a penetration testing framework.
Were there any vulnerabilities the exploit tools agreed on?
If you have access to multiple penetration testing tools, knowing what sort of exploits are readily compromised by a majority of attackers can help you prioritize what to fix. Within Nessus 5, the filtering can be used to select any vulnerability for which all of the penetration testing frameworks have documented exploits. The following is an example screen shot:
In this case, Nessus plugin 39806 (FCKeditor ‘CurrentFolder’ Arbitrary File Upload) identified something that was exploitable by all three exploit frameworks. This was a high-severity vulnerability, but given our list of thousands of audited web sites, wasn’t even shown on our initial summary screen shot. Without the ability to correlate a known exploit with this vulnerability, it may not have been given much attention.
Although not shown in this example, both Core IM
Incest Movie Watch Online Full
Camkittys Camkittys Stickam Omegle
Forced Orgasm Fetish
Sensual Adventures Video
Veila Massage Pillow 3440
Using Nessus 5 to Raise the Value of Penetration Testing ...
Learning Nessus for Penetration Testing - DropPDF
Learning Nessus for Penetration Testing | Packt
(PDF) Web Penetration Testing using Nessus and Metasploit Tool
A brief introduction to the Nessus vulnerability scanner ...
Best Penetration Testing Tools that Integrates with Nessus
Читайте онлайн Learning Nessus for Penetration Testing ...
Download Nessus Vulnerability Assessment | Tenable®
(PDF) Learning Nessus for Penetration Testing
Penetration Testing Nessus





































.jpg)