Penetration Testing

🔞 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Penetration Testing
Request Demo
or learn more
Advanced Bot Protection Handling More Traffic Than Ever
Edward Roberts
■
Nov 12
■
2 min read
The Advantages and Risks of Serverless Computing
Peter Klimek
■
Dec 29
■
3 min read
Virtual Hackathon Generates Next Generation of Imperva Innovation
Nadav Avital
■
Nov 30
■
2 min read
Holidays Are Coming - the State of Security for E-commerce in 2020
Edward Roberts
■
Nov 19
■
2 min read
Copyright © 2021 Imperva. All rights reserved
Home > Learning Center > AppSec > Penetration Testing
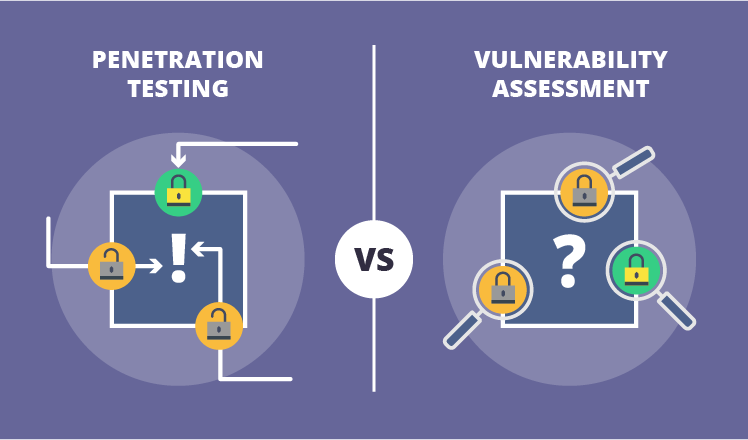
A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF) .
Pen testing can involve the attempted breaching of any number of application systems, (e.g., application protocol interfaces (APIs), frontend/backend servers) to uncover vulnerabilities, such as unsanitized inputs that are susceptible to code injection attacks.
Insights provided by the penetration test can be used to fine-tune your WAF security policies and patch detected vulnerabilities.
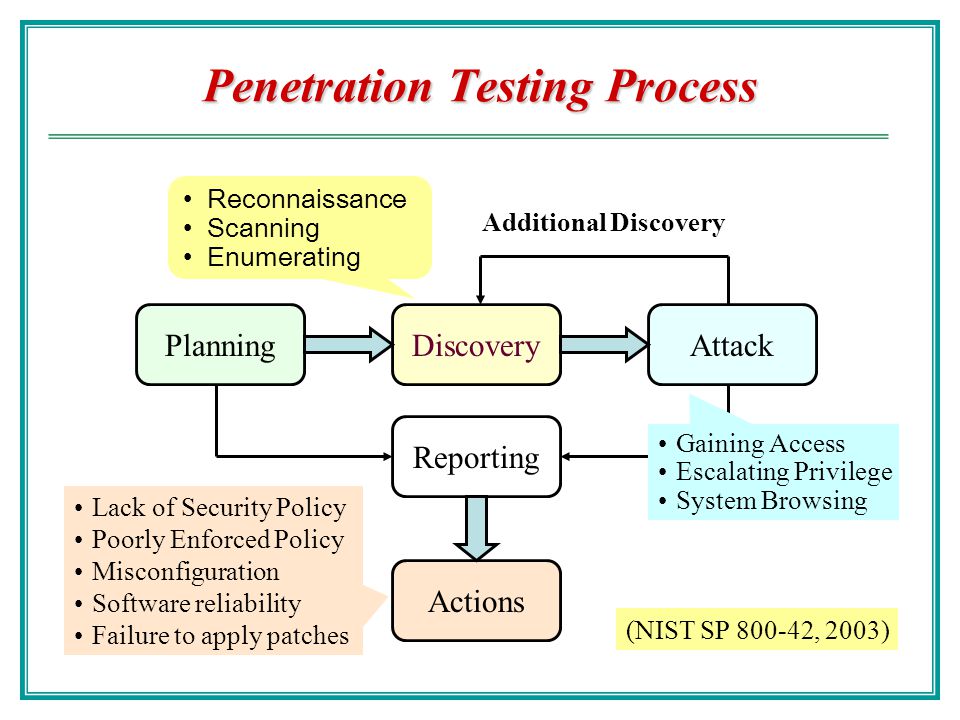
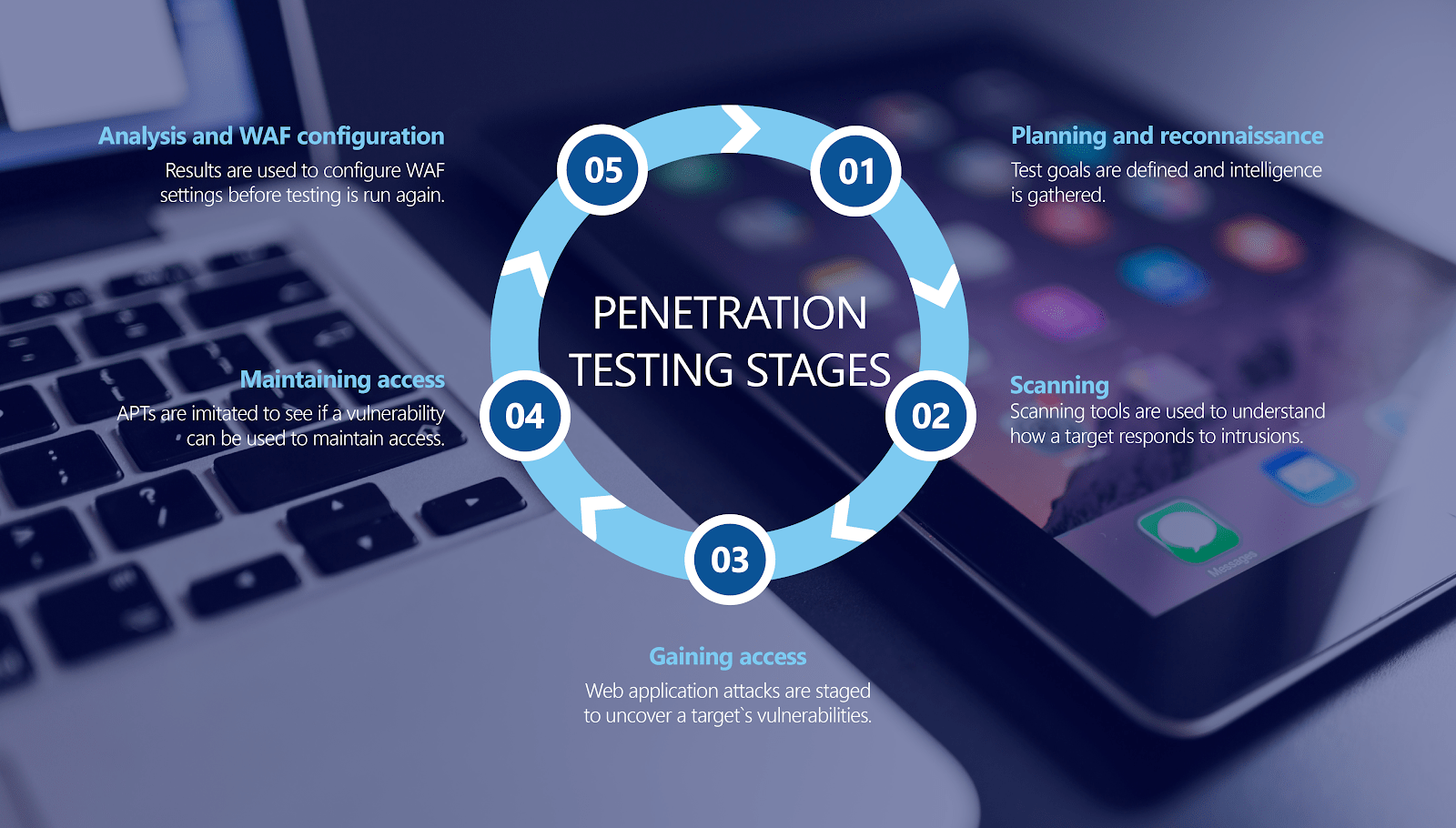
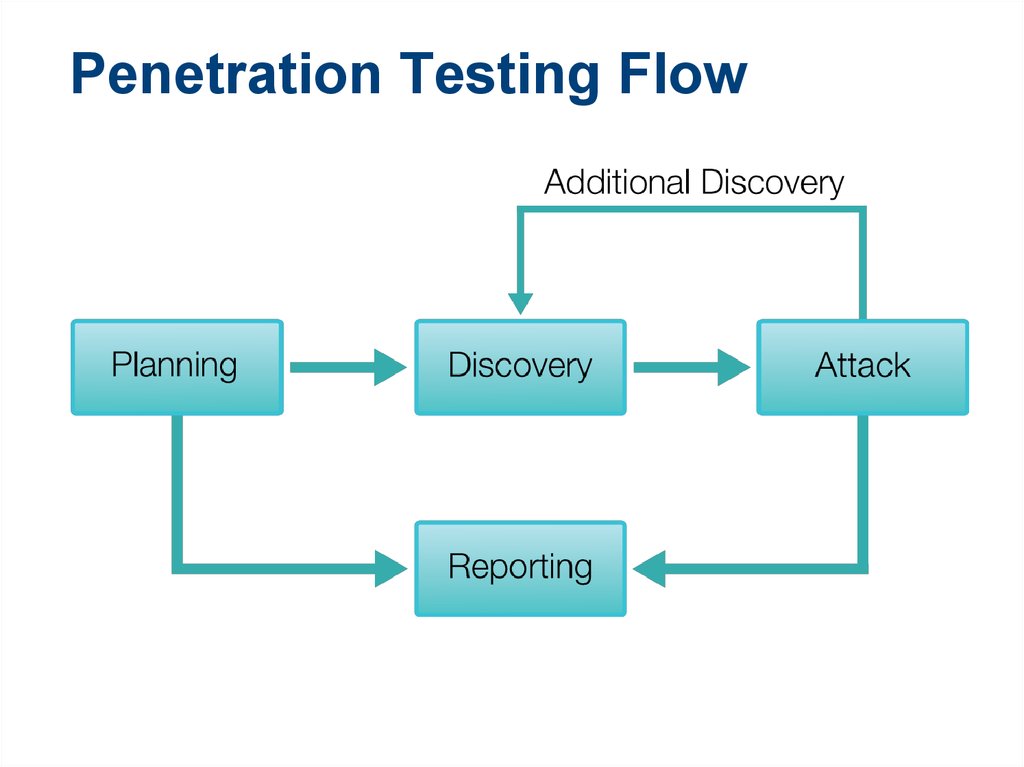
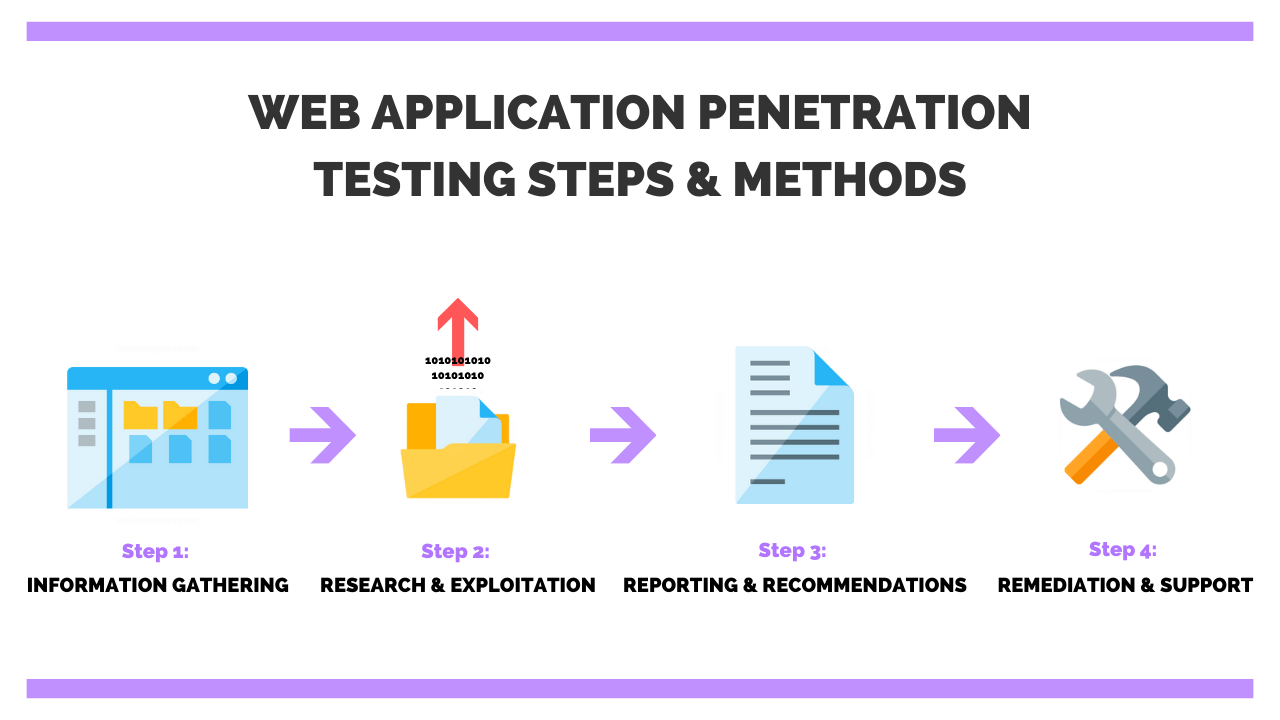
The pen testing process can be broken down into five stages.
1. Planning and reconnaissance
The first stage involves:
2. Scanning
The next step is to understand how the target application will respond to various intrusion attempts. This is typically done using:
3. Gaining Access
This stage uses web application attacks, such as cross-site scripting , SQL injection and backdoors , to uncover a target’s vulnerabilities. Testers then try and exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause.
4. Maintaining access
The goal of this stage is to see if the vulnerability can be used to achieve a persistent presence in the exploited system— long enough for a bad actor to gain in-depth access. The idea is to imitate advanced persistent threats , which often remain in a system for months in order to steal an organization’s most sensitive data.
5. Analysis
The results of the penetration test are then compiled into a report detailing:
This information is analyzed by security personnel to help configure an enterprise’s WAF settings and other application security solutions to patch vulnerabilities and protect against future attacks.
External penetration tests target the assets of a company that are visible on the internet, e.g., the web application itself, the company website, and email and domain name servers (DNS). The goal is to gain access and extract valuable data.
In an internal test, a tester with access to an application behind its firewall simulates an attack by a malicious insider. This isn’t necessarily simulating a rogue employee. A common starting scenario can be an employee whose credentials were stolen due to a phishing attack .
In a blind test, a tester is only given the name of the enterprise that’s being targeted. This gives security personnel a real-time look into how an actual application assault would take place.
In a double blind test, security personnel have no prior knowledge of the simulated attack. As in the real world, they won’t have any time to shore up their defenses before an attempted breach.
In this scenario, both the tester and security personnel work together and keep each other appraised of their movements. This is a valuable training exercise that provides a security team with real-time feedback from a hacker’s point of view.
See how Imperva Web Application Firewall can help you with website security.
Penetration testing and WAFs are exclusive, yet mutually beneficial security measures.
For many kinds of pen testing (with the exception of blind and double blind tests), the tester is likely to use WAF data, such as logs, to locate and exploit an application’s weak spots.
In turn, WAF administrators can benefit from pen testing data. After a test is completed, WAF configurations can be updated to secure against the weak spots discovered in the test.
Finally, pen testing satisfies some of the compliance requirements for security auditing procedures, including PCI DSS and SOC 2 . Certain standards, such as PCI-DSS 6.6, can be satisfied only through the use of a certified WAF. Doing so, however, doesn’t make pen testing any less useful due to its aforementioned benefits and ability to improve on WAF configurations.
40 Best Penetration Testing (Pen Test ) Vapt Tools in 2021
What is Penetration Testing | Step-By-Step Process & Methods | Imperva
24 Essential Penetration Testing Tools in 2020 | Varonis
GitHub - wtsxDev/ Penetration - Testing : List of awesome penetration ...
19 Powerful Penetration Testing Tools Used By Pros in 2021
“This really opened my eyes to AD security in a way defensive work never did.”
Get a highly customized data risk assessment run by engineers who are obsessed with data security.
Live Cyber Attack Lab 🎯 Watch our IR team detect & respond to a rogue insider trying to steal data! Choose a Session
Inside Out Security Blog » IT Pros » 24 Essential Penetration Testing Tools
Penetration testing has become an essential part of the security verification process. While it’s great that there are many penetration testing tools to choose from, with so many that perform similar functions it can become confusing which tools provide you the best value for your time.
We are going to review some of the best pentesting tools available to pentesters today and organize them by category.
While pentesting tools are usually used in the context of a larger security assessment of a network or service, there’s nothing holding back sysadmin’s or developers from deploying the exact same tools to validate the strength of their own work.
Below is a list of the best pentesting tools to tackle different penetration testing tasks. We also included what each tool is best used for and which platforms they’re supported on.
The PowerShell-suite is a collection of PowerShell scripts that extract information about the handles, processes, DLLs, and many other aspects of Windows machines. By scripting together specific tasks, you can quickly navigate and check which systems on a network are vulnerable to exploit.
Zmap is a lightweight network scanner that is capable of scanning everything from a home network to the entire Internet. This free network scanner is best used to gather baseline details about a network. If you only have an IP range to go off of, use to get a lay of the land quickly.
Xray is an excellent network mapping tool that uses the OSINT framework to help guide its tactics. Xray uses wordlists, DNS requests , and any API keys to help identify open ports on a network from the outside looking in.
SimplyEmail is an email recon tool used to help gather associated information found on the internet based on someone’s email address. SimplyEmail is based on the harvester solution and works to search the internet for any data that can help provide intelligence around any given email address.
Wireshark is likely the most widely used network protocol analyzer across the world. Network traffic captured via Wireshark can show what protocols and systems are live, what accounts are most active, and allow attackers to intercept sensitive data.
Hashcat is one of the fastest password recovery tools to date. By downloading the Suite version, you have access to the password recovery tool, a word generator, and a password cracking element. Dictionary, combination, brute-force, rule-based, toggle-case, and Hybrid password attacks are all fully supported. Best of all is hashcat has a great online community to help support the tool with patching, a WiKi page, and walkthroughs.
John the Ripper is the original password cracking tool. Its sole purpose is to find weak passwords on a given system and expose them. John the Ripper is a pentesting tool that can be used for both a security and a compliance perspective. John is famous for its ability to expose weak passwords within a short timeframe quickly.
Hydra is another password cracking tool but with a twist. Hydra is the only password pentesting tool that supports multiple protocols and parallel connections at once. This feature allows a penetration tester to attempt to crack numerous passwords on different systems at the same time without losing connection if unbeaten.
Aircrack-ng is a wireless network security tool that is an all in one package for penetration testing. Aircrack-ng has four primary functions that make it the ultimate standout in its class; It does monitoring of network packets, attacking via packet injection, testing of WiFi capabilities , and finally, password cracking.
For pentesting web applications, Burp Suite is your go-to tool. Incorporating not only vulnerability scanning but Fully Proxy capturing and command injection services as well. Burps UI is fully optimized for the working professional with built-in profiles to allow you to save your configurations on a per-job basis.
Comparable to Burp Suite, Metasploit started as an open-source solution and has gained some traction over the years. Some of the tasks that can be accomplished in Metasploit from a pentesting perspective include vulnerability scanning, listening, exploiting known vulnerabilities, evidence collection, and project reporting.
Nikto is a loud and proud web application scanning solution. It is open-source and contains features like a web server scanner, a pre-packaged list of potentially dangerous files, and a misconfiguration checker as well. Nikto is not stealthy, nor does it try to be; it doesn’t try to hide its presence, but it will get the job done.
Fuzzdb is a special kind of penetration testing tool as it contains pre-built attack payloads to run against web applications to discover if vulnerabilities are genuinely exploitable. On top of being able to simulate attack patterns, Fuzzd b can run discovery scans and perform analysis on the responses received from these scans to narrow better the focus of where vulnerabilities exist.
NMAP is a pentesters best friend. This network security mapping tool gives you a quick look at the open ports on any given network. NMAP commands allow you to dig into the feasibility of specific network-level vulnerabilities. NMAP also has a friendly GUI interface called ZenMap that is easy to use for any skill level. NMAP also comes with a debugging tool, a comparison tool for comparing scan results, and a packet generation tool as well.
Sqlmap is an open-source penetration tool that helps bring validity to possible SQL injection flaws that may affect your database servers. This automated testing tool comes with a slew of detailed features, including DB fingerprinting, remote commands , and its detection engine.
For mobile platform vulnerability discovery, MobSF is your tool. This hacking tool is an all in one platform for pen-testing and vulnerability discovery via static and dynamic application analysis. MobSF also has built-in REST APIs to provide an integrated experience into your development pipeline. ModSF is ultimately a vulnerability scanner for mobile applications.
Linux-Exploit-Suggester is an excellent tool for on the fly security testing of Linux systems without dealing with the overhead of a beefy vulnerability scanner. LES was created for system admins to get a quick sense of the. Based on its lightweight compatibility, LES is a great vulnerability catalog for pentesters looking to get a quick overview of a systems configuration, without creating too much noise via resource consumption.
Apktool is for those Pentesters or security researchers that are attempting to reverse engineer malware to determine a way to better protect against it. Apktool only supports 3rd party, android applications. Apktool’s feature set includes being able to disassemble and reassemble to original form, debugging and help to automate repetitive tasks.
Resource Hacker is a windows specific file editor that allows anyone to decompile a windows file and recompile it at a later time. The great thing about this reverse engineering tool is that it comes with a GUI interface that makes it easy for novice pentesters to learn and use.
IDA is the Kleenex of disassembler tools as it is widely supported and used in commercial validation testing. IDA is interactive as a disassembler as well as a debugger, thus providing you with a whole solution as a professional. Best of all, it supports all major OS system types.
Lastly, we have Radare , which is one of the most widely accepted and versatile disassembly tools available. Some of its features include multiple OS and mobile OS support, file system forensics, data carving capabilities, and visualizing data structures.
If it is available to you, the best way to send out compromised data is through the account you compromised in the first place. Most of the time you will have the ability to use the user’s account to send ether emails out or you could try to use the installed enterprise chat solution in place to accomplish the same outcome. For pentesters trying to remain anonymous, this is a great technique as long as you limit the size of the emails so that it isn’t detected as an anomaly by any DLP solution that might be watching.
Srm stands for Secure remove, and it takes the hassle out, ensuring a file is entirely removed from a system. As a pentester, Srm is great for removing temporary files created while accessing a system, If your intent is to cover up your tracks, Srm is the tool required to remove any rootkit files that may have been used during the exploit process. Srm removes and rewrites over the data location to ensure all traces of the data are thoroughly wiped from the system. Best of all, it is a command-line program that is quick to set up and use.
Catfish is a pentesting tool that is used by many to quickly search for specific files that tend to contain sensitive data or can provide them with additional access (like a password file). Catfish allows the end-user to explore a system for any files containing a particular string within its name. It is simple but highly effective at what it does.
Performing penetration tests is an essential part of verifying that systems are secure. Using the right penetration testing tools saves time and helps to improve your overall security posture.
Jeff has been working on computers since his Dad brought home an IBM PC 8086 with dual disk drives. Researching and writing about data security is his dream job.
© 2021 Inside Out Security | Policies | Certifications
This site uses cookies to provide you with a better browsing experience. Further information may be found in the Varonis Site Privacy Policy
Accept
Super Oral Sex
Big Ass Jeans
Outdoor Version
Porno Photo Outdoor
Overwatch Match