Penetration Test

🔞 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Penetration Test
40 Best Penetration Testing (Pen Test) Vapt Tools in 2021
Netsparker, the developers of Proof Based Scanning technology, have sponsored the Guru99 project to help raise web application security awareness and allow more developers to learn about writing secure code
© Copyright - Guru99 2021
Privacy Policy | Affiliate Disclaimer | ToS
Intruder is a powerful, automated penetration testing tool that discovers security weaknesses across your IT environment. Offering industry-leading security checks, continuous monitoring and an easy-to-use platform, Intruder keeps businesses of all sizes safe from hackers.
Intrusion Detection Software is a tool that enables you to detect all types of advanced threats. It provides compliance reporting for DSS (Decision Support System) and HIPAA. This application can continuously monitor suspicious attacks and activity.
Traceroute NG is application that enables you to analyze network path. This software can identify IP addresses, hostnames, and packet loss. It provides accurate analysis through command line interface
ExpressVPN secures internet browsing against three-letter agencies and scammers. It offers unlimited access to music, social media, and video such that these programs never log IP addresses, browsing history, DNS queries, or traffic destination.
The Open Web Application Security Project ( OWASP ) is a worldwide non-profit organization focused on improving the security of software. The project has multiple tools to pen test various software environments and protocols. Flagship tools of the project include
The OWASP testing guide gives "best practice" to penetration test the most common web application
Wireshark is a network analysis pentest tool previously known as Ethereal. It captures packet in real time and display them in human readable format. Basically, it is a network packet analyzer- which provides the minute details about your network protocols, decryption, packet information, etc. It is an open source and can be used on Linux, Windows, OS X, Solaris, NetBSD, FreeBSD and many other systems. The information that is retrieved via this tool can be viewed through a GUI or the TTY mode TShark Utility.
w3af is a web application attack and audit framework. It has three types of plugins; discovery, audit and attack that communicate with each other for any vulnerabilities in site, for example a discovery plugin in w3af looks for different url's to test for vulnerabilities and forward it to the audit plugin which then uses these URL's to search for vulnerabilities.
It can also be configured to run as a MITM proxy. The request intercepted could be sent to the request generator and then manual web application testing can be performed using variable parameters. It also has features to exploit the vulnerabilities that it finds.
This is the most popular and advanced Framework that can be used for pentest. It is an open source tool based on the concept of 'exploit' which means you pass a code that breach the security measures and enter a certain system. If entered, it runs a 'payload', a code that performs operations on a target machine, thus creating the perfect framework for penetration testing. It is a great testing tool test whether the IDS is successful in preventing the attacks that we bypass it
Metaspoilt can be used on networks, applications, servers, etc. It has a command line and GUI clickable interface, works on Apple Mac OS X, works on Linux and Microsoft Windows.
Kali works only on Linux Machines. It enables you to create a backup and recovery schedule that fit your needs. It promotes a quick and easy way to find and update the largest database of security penetration testing collection to-date. It is the best tools available for packet sniffing and injecting. An expertise in TCP/IP protocol and networking can be beneficial while using this tool.
The Samurai Web Testing Framework is a pen testing software. It is supported on VirtualBox and VMWare that has been pre-configured to function as a web pen-testing environment.
Aircrack is a handy wireless pentesting tools. It cracks vulnerable wireless connections. It is powered by WEP WPA and WPA 2 encryption Keys.
ZAP is one of the most popular open source security testing tool. It is maintained by hundreds of international volunteers. It can help users to find security vulnerabilities in web applications during the developing and testing phase.
Sqlmap is an open source penetration testing tool. It automates the entire process of detecting and exploiting SQL injection flaws. It comes with many detection engines and features for an ideal penetration test.
Sqlninja is a penetration testing tool. It is aimed to exploit SQL Injection vulnerabilities on a web application. It uses Microsoft SQL Server as back-end. It also provides a remote access on the vulnerable DB server, even in a very hostile environment.
The Browser Exploitation Framework. It is a pentesting tool that focuses on the web browser. It uses GitHub to track issues and host its git repository.
Dradis is an open source framework for penetration testing. It allows maintaining the information that can be shared among the participants of a pen-test. The information collected helps users to understand what is completed and what needs to completed.
Nexpose Rapid 7 is a useful vulnerability management software. It monitors exposures in real-time and adapts to new threats with fresh data which helps users to act at the moment of impact.
Hping is a TCP/IP packet analyzer pen testing tool. This interface is inspired to the ping (8) UNIX command. It supports TCP, ICMP, UDP, and RAW-IP protocols.
Superscan is a free Windows-only closed-source penetration testing tool. It also includes networking tools such as ping, traceroute, whois and HTTP HEAD.
The IBM Internet Scanner is a pen testing tool which offers the foundation for the effective network security for any business.
Scapy is a powerful and interactive pen testing tool. It can handle many classical tasks like scanning, probing, and attacks on the network.
IronWASP is an open source software for web application vulnerability testing. It is designed to be customizable so that users can create their custom security scanners using it.
Ettercap is a comprehensive pen testing tool. It supports active and passive dissection. It also includes many features for network and host analysis.
Security Onion is a penetration testing tool. It is used for intrusion detection, and network security monitoring. It has an easy-to-use Setup wizard allows users to build an army of distributed sensors for their enterprise.
Personal Software Inspector is an open source computer security solution. This tool can identify vulnerabilities in applications on a PC or a Server.
HconSTF is Open Source Penetration Testing tool based on different browser technologies. It helps any security professional to assists in the Penetration testing. It contains web tools which are powerful in doing XSS, SQL injection, CSRF, Trace XSS, RFI, LFI, etc.
Download link: http://www.hcon.in/
IBM Security AppScan helps to enhance web application security and mobile application security. It improves application security and strengthens regulatory compliance. It helps users to identify security vulnerabilities and generate reports.
Arachni is an open source Ruby framework based tool for penetration testers & administrators. It is used for evaluating the security of modern web applications.
Websecurify is a powerful security testing environment. It is a user -friendly interface which is simple and easy to use. It offers a combination of automatic and manual vulnerability testing technologies.
Vega is an open source web security scanner and pen testing platform to test the security of web applications.
Wapiti is another famous penetration testing tool. It allows auditing the security of the web applications. It supports both GET and POST HTTP methods for the vulnerability check.
Kismet is a wireless network detector and intrusion detection system. It works with Wi-Fi networks but can be expanded via plugins as it allows to handle other network types.
Kali Linux is an open source pen testing tool which is maintained and funded by Offensive Security.
Parrot Security is a pen testing tool. It offers fully portable laboratory for security and digital forensics experts. It also helps users to protect their privacy with anonymity and crypto tools.
This toolkit is licensed under an Apache-style license. It is free and open source project that provides a full-featured toolkit for the TLS and SSL protocols.
Snort is an open-source intrusion detection and pen testing system. It offers the benefits of signature-protocol- and anomaly-based inspection methods. This tool helps users to get maximum protection from malware attacks.
BackBox is an Open Source Community project with the objective of enhancing the culture of security in IT environment. It is available in two different variations like Backbox Linux and Backbox Cloud. It includes some of the most commonly known/used security and analysis tools.
Hydra is a parallelized login cracker and pen testing tool. It is very fast and flexible, and new modules are easy to add. This tool allows researchers and security consultants to find unauthorized access.
Open Threat Exchange Reputation Monitor is a free service. It allows professionals to track their organization's reputation. With the help of this tool, businesses and organizations can track the public IP and domain reputation of their assets.
John the Ripper known as JTR is a very popular password cracking tool. It is primarily used to perform dictionary attacks. It helps identify weak password vulnerabilities in a network. It also supports users from brute force and rainbow crack attacks.
Safe3WVS is one of the most powerful web vulnerability testing tool. It comes with web spider crawling technology, especially web portals. It is the fastest tool to find issues like SQL injection, upload vulnerability, and more.
CloudFlare is CDN with robust security features. Online threats range from comment spam and excessive bot crawling to malicious attacks like SQL injection. It provides protection against comment spam, excessive bot crawling, and malicious attacks.
Zenmap is the official Nmap Security Scanner software. It is a multi-platform free and open source application. It is easy to use for beginners but also offers advanced features for experienced users.
The other tools that might be useful for penetration testing are
What is Penetration Testing | Step-By-Step Process & Methods | Imperva
40 Best Penetration Testing (Pen Test ) Vapt Tools in 2021
Penetration Testing Step By Step Guide Stages Methods And Application
GitHub - wtsxDev/ Penetration - Testing : List of awesome penetration ...
19 Powerful Penetration Testing Tools Used By Pros in 2021
Cloud & Security
Technical Skills
Data Science & Programming
Professional Skills
Premium Resources
Training Courses
Free Resources
OpenCampus
Blog
Mock Exams
Downloadables
Dates: February 09,10,11,12,23,24,25,26 2021
Dates: February 13,14,20,21,27 2021
i love this post thanks for sharing this articles
Thank you for providing such nice piece of article. I’m glad to leave a comment. Expect more articles in future
Company
About us
Contact us
Privacy policy
Terms of use
Customer speak
Cancellation policy
Careers
Contacts
sales@greycampus.com
support@greycampus.com
USA +1 518 302 6767
UK +44 20 8144 4436
IND +91 741 666 4433
HKG +852 8192 9294
Enquiries
Become our affiliate
Become our Instructor
Scholarships
IT Service Management:
ITIL® 4 Foundation Training and Certification
Data Science and AI:
Data Science Career Program
Data Science Foundation Program
Abu Dhabi
Atlanta
Bangalore
Charlotte
Chennai
Chicago
Dallas
Dubai
Hong Kong
Houston
Hyderabad
Jakarta
Jeddah
Kuala Lumpur
Los Angeles
Manila
Mumbai
New Delhi
New York
Pune
Raleigh
Riyadh
San Francisco
Singapore
Sydney
Toronto
Washington DC
Abu Dhabi
Atlanta
Dubai
Riyadh
Singapore
Sydney
Toronto
Abu Dhabi
Atlanta
Bangalore
Charlotte
Chennai
Chicago
Dallas
Dubai
Hong Kong
Houston
Hyderabad
Jakarta
Jeddah
Kuala Lumpur
Los Angeles
Manila
Mumbai
New Delhi
New York
Pune
Raleigh
Riyadh
San Francisco
Singapore
Sydney
Toronto
Washington DC
Abu Dhabi
Atlanta
Austin
Bangalore
Charlotte
Chennai
Chicago
Dallas
Doha
Dubai
Frankfurt
Hong Kong
Houston
Hyderabad
Istanbul
Jakarta
Jeddah
Kuala Lumpur
Kuwait
Los Angeles
Manila
Melbourne
Mumbai
New Delhi
New York
Pune
Raleigh
Riyadh
San Francisco
Singapore
Sydney
Toronto
Washington DC
Atlanta
Bangalore
Chennai
Chicago
Dubai
Houston
Hyderabad
Kuala Lumpur
Manila
Mumbai
New York
Pune
Singapore
Toronto
Washington DC
Dubai
Hyderabad
Kuala Lumpur
Riyadh
Singapore
Sydney
Hyderabad
Mumbai
Pune
Sydney
Abu Dhabi
Atlanta
Bangalore
Charlotte
Chennai
Chicago
Dallas
Dubai
Hong Kong
Houston
Hyderabad
Jakarta
Jeddah
Kuala Lumpur
Los Angeles
Manila
Mumbai
New Delhi
New York
Pune
Raleigh
Riyadh
San Francisco
Singapore
Sydney
Abu Dhabi
Atlanta
Bangalore
Charlotte
Chennai
Chicago
Dallas
Dubai
Hong Kong
Houston
Hyderabad
Jakarta
Jeddah
Kuala Lumpur
Los Angeles
Manila
Mumbai
New York
Pune
Raleigh
Riyadh
San Francisco
Singapore
Sydney
Toronto
Washington DC
Atlanta
Bangalore
Chennai
Chicago
Hyderabad
Mumbai
New Delhi
Pune
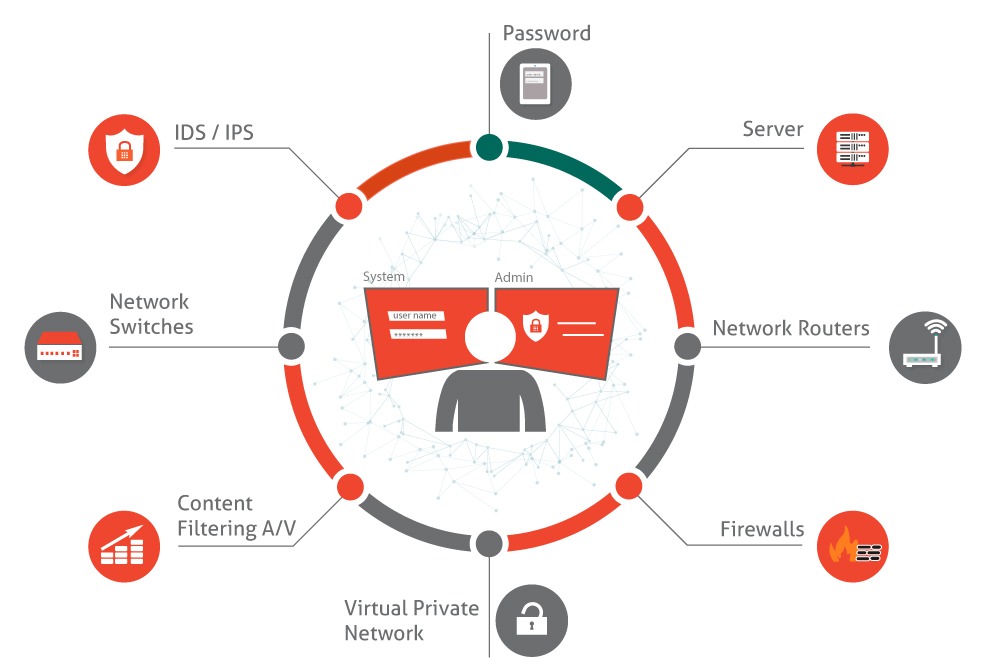
The architecture of companies today is complex- networks, applications, servers, storage devices, WAF, DDOS protection mechanisms , cloud technology and so much more is involved. With such options in hand, the system becomes complex (here's some resource to help you navigate through the types of cloud services ). Since a single person is not handling these things, complete knowledge is impossible. Some teams handle network and create rules on business demand, some handle the configuration part and ensure that the functionality is taken care of; these scenarios leave space for weaknesses. An attacker can identify these vulnerabilities and launch attacks that can do a lot of damage. This possibility cannot be brought down to zero but can be reduced to an acceptable level. The need is to bring an ethical hacker to the environment and get the things tested. He/she will be responsible for performing penetration tests on the target agreed upon.
Penetration testing is the art of finding vulnerabilities and digging deep to find out how much a target can be compromised, in case of a legitimate attack. A penetration test will involve exploiting the network, servers, computers, firewalls, etc., to uncover vulnerabilities and highlight the practical risks involved with the identified vulnerabilities.
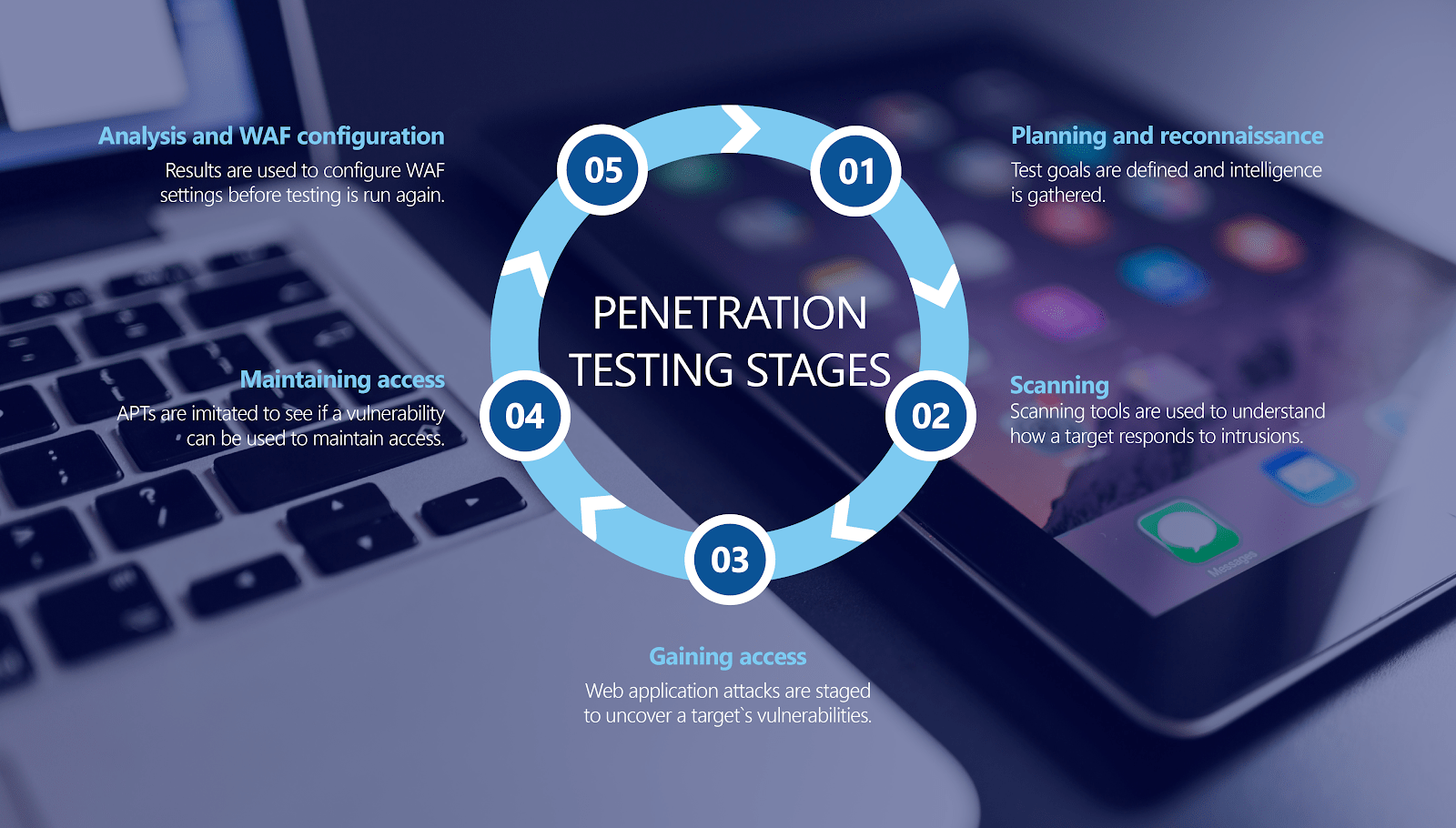
Penetration testing can be broken down into multiple phases; this will vary depending on the organization and the type of test conducted– internal or external. Let’s discuss each phase:
In this phase, there is a mutual agreement between the parties; the agreement covers high-level details- methods followed and the exploitation levels. The attacker cannot bring down the production server even if the testing has been done at non-peak hours. What if the attacker changes the data that has been contained in the database in production? This will unveil the vulnerabilities but at the cost of business. A non-disclosure agreement has to be signed between the parties before the test starts.
In this phase, the attacker gathers as much information about the target as possible. The information can be IP addresses, domain details, mail servers, network topology, etc. An expert hacker will spend most of the time in this phase, this will help with further phases of the attack.
This is the phase where the attacker will interact with the target with an aim to identify the vulnerabilities. An attacker will send probes to the target and records the response of the target to various inputs. This phase includes- scanning the network with various scanning tools, identification of open share drives, open FTP portals, services that are running, and much more. In case of a web application, the scanning part can be either dynamic or static. In static scanning, the application code is scanned by either a YTool or an expert application vulnerability analyst. The aim is to identify the vulnerable functions, libraries and logic implemented. In dynamic analysis, the tester will pass various inputs to the application and record the responses; various vulnerabilities like injection, cross-site scripting, remote code execution can be identified in this phase.
Once the vulnerabilities have been identified, the next step is to exploit the vulnerabilities with an aim to gain access to the target. The target can be a system, firewall, secured zone or server. Be aware that not all vulnerabilities will lead you to this stage. You need to identify the ones that are exploitable enough to provide you with access to the target.
The next step is to ensure that the access is maintained; i.e., persistence. This is required to ensure that the access is maintained even if the system is rebooted, reset or modified. This kind of persistence is used by attackers who live in the system and gain knowledge about them over a period of time, and when the environment is suitable, they exploit.
This is the phase where the actual damage is done. An attacker will try to get the data, compromise the system, launch dos attacks, etc (Here's a resource that will navigate you through cyber security attacks ). Usually, this phase is controlled in penetration testing so as to ensure that the mayhem on the network is limited. This phase is modified in this way- a dummy flag is placed in the critical zone, may be in the database; the aim of the exploitation phase will be to get the flag. Revealing the contents of the flag will be enough to ensure practical exploitation of the network or data theft.
Once the penetration test is complete, the final aim is to collect the evidence of the exploited vulnerabilities and report it to the executive management for review and action. Now, it is the management’s decision on how this risk has to be addressed. Whether they want to accept the risk, transfer it or ignore it (least likely option).
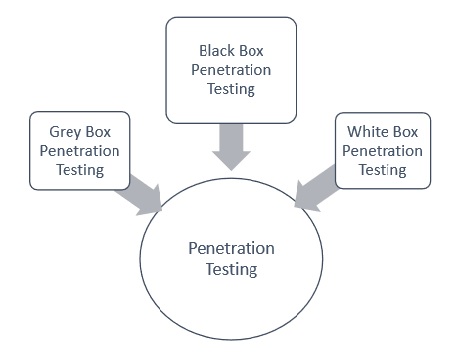
Types of penetration testing can be categorized on the basis of either, the knowledge of the target or the position of the penetration tester. There are a few other parameters to the categorization of penetration.
When the penetration tester is given the complete knowledge of the target, this is called a white box penetration test. The attacker has complete knowledge of the IP addresses, controls in place, code samples, etc. When the attacker has no knowledge of the target, this is referred to as a black box penetration test. Please note that the tester can still have all the information that is publically available about the target. When the tester is having partial information about the target, this is referred to as gray box penetration testing. In this case, the attacker is having some knowledge of the target like URLs, IP addresses, etc., but does not have complete knowledge or access. This is with respect to the knowledge.
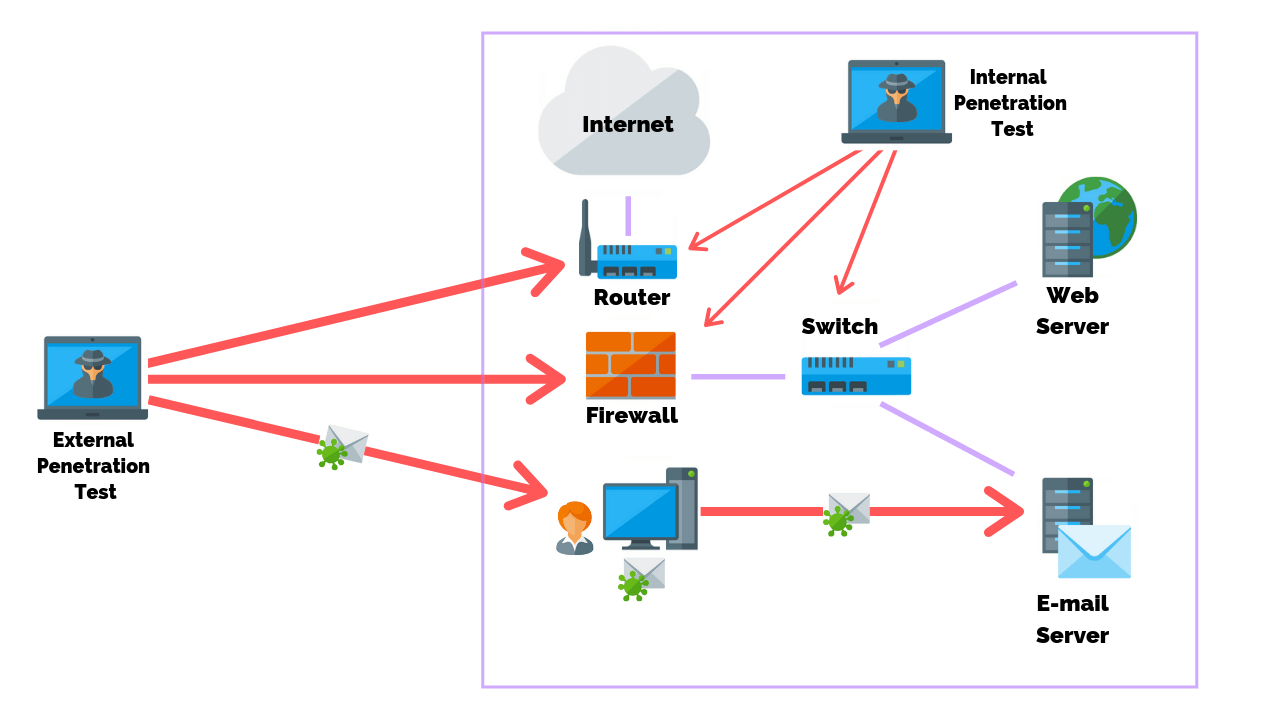
If the penetration test is conducted from outside the network, this is referred to as external penetration testing. If the attacker is present inside the network, simulation of this scenario is referred to as internal penetration testing. Since the attacker is an internal person, the knowledge about the system and the target will be abundant when compared to a test conducted from outside.
When the test is conducted by an in-house security team, it is another form of internal penetration testing. Companies often hire third-party organizations to conduct these tests, this is referred to as third-party penetration testing.
In a blind penetration test, the penetration tester is provided with no prior information but the organization name. The penetration tester will have to do all the homework, just like a legitimate attacker would do. This will surely take more time, but the results would be more close to the practical attacks. A double-blind test is like a blind test but the security professionals will not know when the testing will start. Only the senior management will have this information. This will test the processes, controls and the awareness of the security teams if and when a real attack occurs.
For an organization, the most important thing is business continuity. Second most important thing is the supporting services that ensure the business runs smoothly. Thus, to ensure that senior management is involved and pays attention, a penetration tester should highlight the risks that a business might face due to the findings. Let’s discuss a few important pointers that cover two things:
What is in this for the business, in terms of capital?
What is there for the security teams?
A penetration test will ensure that:
1) Weaknesses in the architecture are identified and fixed before a hacker can find and exploit them; thus, causing a business loss or unavailability of services.
2) Organisations these days need to comply with various standards and compliance procedures. A penetration test will ensure that the gaps are fixed in time to meet compliance. One of the examples is PCI-DSS; an organization which deals with customer’s credit card information (store, process or transmit) have to get them PCI-DSS certified. One of the requirement is to get penetration testing done.
3) Penetration tests will be an eye-opener or a check on the organization’s internal security team. How much time do they take to identify attacks and take responsive steps? Do they realize that a breach has happened? If yes, what do they do? And, when they do, is it sufficient?
4) What will be the effect if a real attack occurs? What damage can be done? We can actually calculate the potential loss to the organization if an attack occurs.
Now that we have talked enough about what is the need of a penetration test. We need to talk about the tools that a penetration tester can use to conduct this test.
Nessus is a network and web application vulnerability scanner , it can perform different types of scans and help a penetration tester identify vulnerabilities. The attacker can then spend time in determining what can be exploited further. The free version of the tool is having some interesting features disabled. The full version is powerful and has a lot of features that will help during the scanning phase of the penetration test.
Dirbuster is a directory busting tool, this will help the attacker to find the directories that are present. The tool will take an input list and will help in testing their availability. This will allow for footprinting of the directory structure and find directories that will be difficult to find.
Metasploit is an exploitation framework that has been packed with various capabilities. A skilled attacker can generate payloads, shellcodes, gain access, and perform privilege escalation attacks. The knowledge of python and ruby will be helpful since the framework uses them for most of the scripts.
This tool is specifically used for testing web applications. Let us assume that you have uncovered a test web application that is no longer used after production push. You can use this tool to dig deeper into the application and hunt vulnerabilities. The high severity vulnerabilities can be further exploited to move forward with the attack.
Saves time and effort- a well-known vulnerability will take a significant amount of time to be identified. Tools will identify them and you can work on the next stage.
Will be more accurate with findings; there will be false positives, but that can be minimized over a period of time.
A penetration tester cannot be an expert in all phases of the test. Thus, tools will be of much help.
They help in generating easy to understand reports that can be used by the business teams and executive management. Most of the tools offer various reporting formats that can be used by developers, testers, management or fed to other tools for further usage.
Automates the manual tasks- teams can focus on skilled work rather than redundant tasks.
The tool will gather a lot of data that will be reported to the tester; this data may not be exploitable always, though it offers a lot of knowledge. The data is used by internal teams to create strong architecture.
1) What is penetration testing, and why is it necessary for business and organization as a whole?
2) What is done after a penetration test is complete?
If you do not have these questions already, then you might be thinking from only one side. Once the test is done, the management has to take a call on what is the risk and what they can do- do they put in place a security control to mitigate the risk? You might think that, yes, that is necessary; but this is wrong. Sometimes, the loss due to vulnerability is less than the cost of control. In these cases, the organization may opt to accept the risk. It takes time and effort to be an expert penetration tester; today, most of the penetration testers are just vulnerability analysts. To be a fine penetration tester, you should know the art of exploitation. You need to sharpen your instincts at identifying, what can be exploited and what can be extended.
Harpreet Passi is an Information Security enthusiast with a great experience in different areas of Information Security. Harpreet holds CEH v9 and many other online certifications in the cybersecurity domain. Standard Chartered Bank acknowledged him for outstanding performance and a leading payment solution firm rewarded him for finding vulnerabilities in their online and local services. He loves to write, meet new people and is always up for extempore, training sessions and pep talks.
Nasty Mature Ass
Utp4 C5e Solid Outdoor 40 500
Porno Public Outdoor
Homemade Wife Anal
Homemade Missionary Creampie