Openssl Private Key

🛑 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Openssl Private Key
Product Docs
API Docs
Sign in to
Community
Control Panel
Build with DigitalOcean
Community Tools and Integrations
Hatch Startup Program
Marketplace Partner Program
Solutions Partner Program
Presentation Grants
DigitalOcean on GitHub
Keeping Your Sites and Users Safe Using SSL
Tutorial
What is a VPN?
Tutorial
Comments
Follow-Up Questions
schumann
September 26, 2014
manicas
September 29, 2014
gauravkhandelwa
November 5, 2014
luissquall
October 15, 2015
KS7000
September 30, 2019
anujaggarwal
June 22, 2016
mckennatim
January 19, 2017
sgarg31
December 11, 2017
nparthibann
September 3, 2018
carlusia17
November 24, 2019
starrychloe
January 16, 2020
Company
About
Leadership
Blog
Careers
Partners
Referral Program
Press
Legal
Security & Trust Center
Products
Pricing
Products Overview
Droplets
Kubernetes
Managed Databases
Spaces
Marketplace
Load Balancers
Block Storage
API Documentation
Documentation
Release Notes
Community
Tutorials
Q&A
Tools and Integrations
Tags
Product Ideas
Write for DigitalOcean
Presentation Grants
Hatch Startup Program
Shop Swag
Research Program
Open Source
Code of Conduct
Contact
Get Support
Trouble Signing In?
Sales
Report Abuse
System Status
navigate
go
exit
Get the latest tutorials on SysAdmin and open source topics.
Hub for Good
Supporting each other to make an impact
Write for DigitalOcean
You get paid, we donate to tech non-profits.
Hacktoberfest
Contribute to Open Source
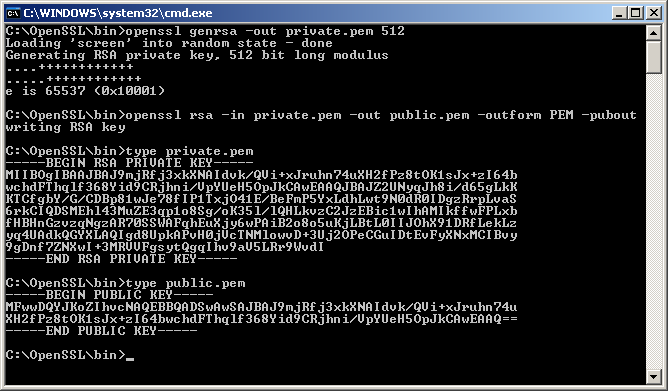
OpenSSL is a versatile command line tool that can be used for a large variety of tasks related to Public Key Infrastructure (PKI) and HTTPS (HTTP over TLS). This cheat sheet style guide provides a quick reference to OpenSSL commands that are useful in common, everyday scenarios. This includes OpenSSL examples of generating private keys, certificate signing requests, and certificate format conversion. It does not cover all of the uses of OpenSSL.
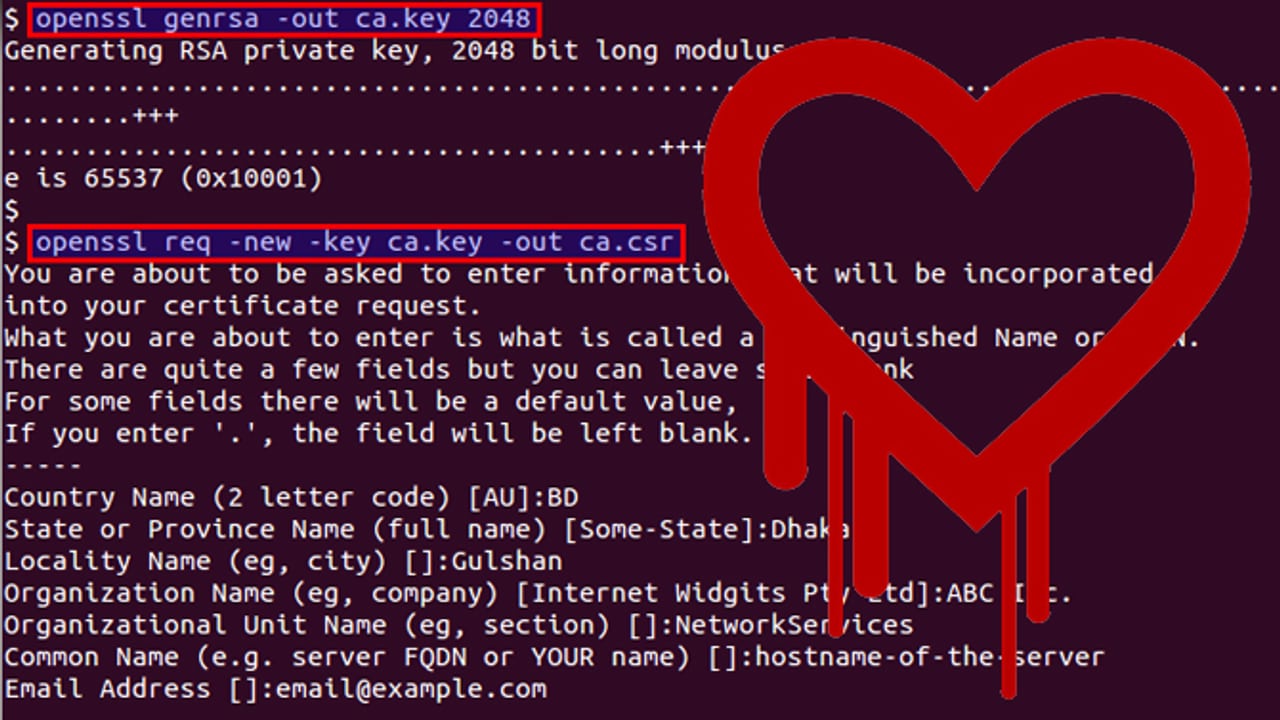
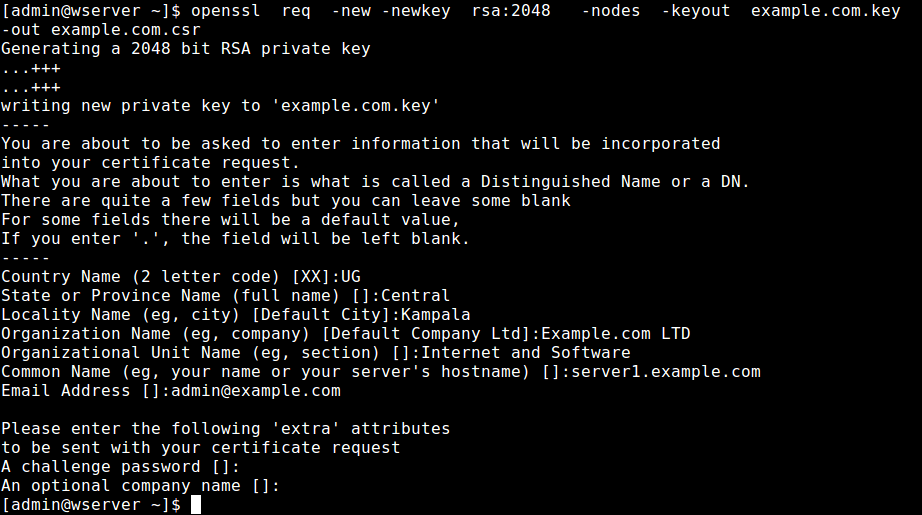
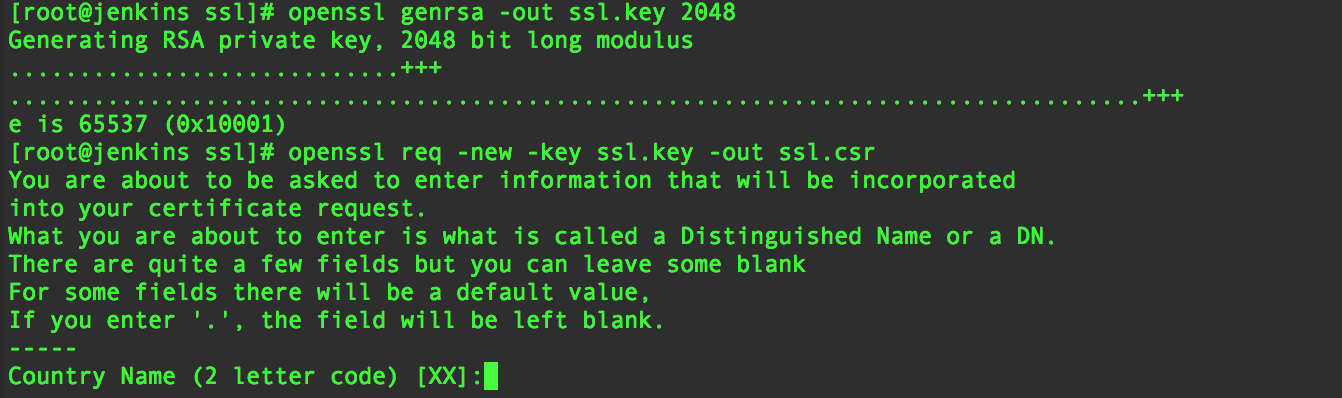
If you would like to obtain an SSL certificate from a certificate authority (CA), you must generate a certificate signing request (CSR). A CSR consists mainly of the public key of a key pair, and some additional information. Both of these components are inserted into the certificate when it is signed.
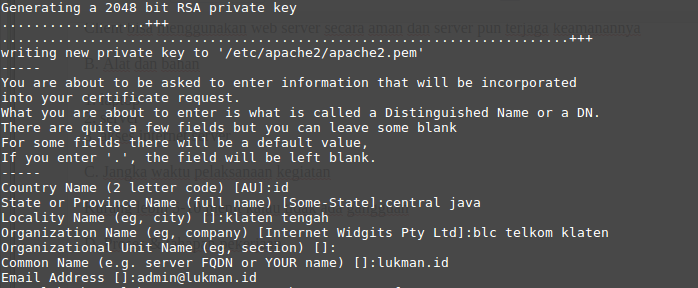
Whenever you generate a CSR, you will be prompted to provide information regarding the certificate. This information is known as a Distinguised Name (DN). An important field in the DN is the Common Name (CN), which should be the exact Fully Qualified Domain Name (FQDN) of the host that you intend to use the certificate with. It is also possible to skip the interactive prompts when creating a CSR by passing the information via command line or from a file.
The other items in a DN provide additional information about your business or organization. If you are purchasing an SSL certificate from a certificate authority, it is often required that these additional fields, such as “Organization”, accurately reflect your organization’s details.
Here is an example of what the CSR information prompt will look like:
If you want to non-interactively answer the CSR information prompt, you can do so by adding the -subj option to any OpenSSL commands that request CSR information. Here is an example of the option, using the same information displayed in the code block above:
Now that you understand CSRs, feel free to jump around to whichever section of this guide that covers your OpenSSL needs.
This section covers OpenSSL commands that are related to generating CSRs (and private keys, if they do not already exist). CSRs can be used to request SSL certificates from a certificate authority.
Keep in mind that you may add the CSR information non-interactively with the -subj option, mentioned in the previous section.
Use this method if you want to use HTTPS (HTTP over TLS) to secure your Apache HTTP or Nginx web server, and you want to use a Certificate Authority (CA) to issue the SSL certificate. The CSR that is generated can be sent to a CA to request the issuance of a CA-signed SSL certificate. If your CA supports SHA-2, add the -sha256 option to sign the CSR with SHA-2.
This command creates a 2048-bit private key ( domain.key ) and a CSR ( domain.csr ) from scratch:
Answer the CSR information prompt to complete the process.
The -newkey rsa:2048 option specifies that the key should be 2048-bit, generated using the RSA algorithm. The -nodes option specifies that the private key should not be encrypted with a pass phrase. The -new option, which is not included here but implied, indicates that a CSR is being generated.
Use this method if you already have a private key that you would like to use to request a certificate from a CA.
This command creates a new CSR ( domain.csr ) based on an existing private key ( domain.key ):
Answer the CSR information prompt to complete the process.
The -key option specifies an existing private key ( domain.key ) that will be used to generate a new CSR. The -new option indicates that a CSR is being generated.
Use this method if you want to renew an existing certificate but you or your CA do not have the original CSR for some reason. It basically saves you the trouble of re-entering the CSR information, as it extracts that information from the existing certificate.
This command creates a new CSR ( domain.csr ) based on an existing certificate ( domain.crt ) and private key ( domain.key ):
The -x509toreq option specifies that you are using an X509 certificate to make a CSR.
If you would like to use an SSL certificate to secure a service but you do not require a CA-signed certificate, a valid (and free) solution is to sign your own certificates.
A common type of certificate that you can issue yourself is a self-signed certificate . A self-signed certificate is a certificate that is signed with its own private key. Self-signed certificates can be used to encrypt data just as well as CA-signed certificates, but your users will be displayed a warning that says that the certificate is not trusted by their computer or browser. Therefore, self-signed certificates should only be used if you do not need to prove your service’s identity to its users (e.g. non-production or non-public servers).
This section covers OpenSSL commands that are related to generating self-signed certificates.
Use this method if you want to use HTTPS (HTTP over TLS) to secure your Apache HTTP or Nginx web server, and you do not require that your certificate is signed by a CA.
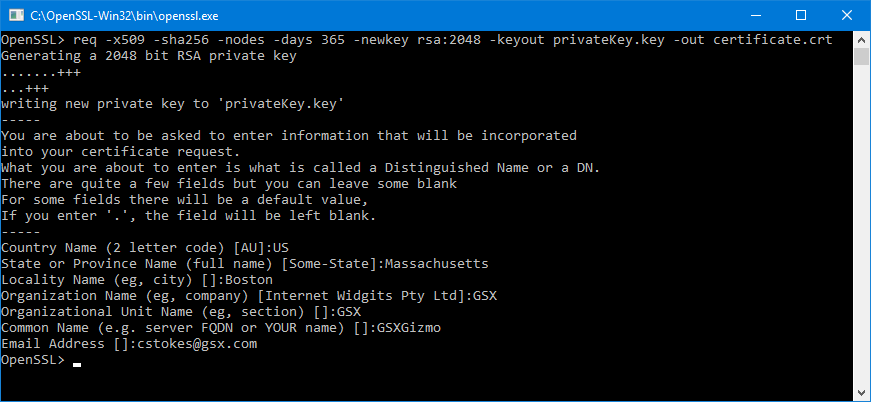
This command creates a 2048-bit private key ( domain.key ) and a self-signed certificate ( domain.crt ) from scratch:
Answer the CSR information prompt to complete the process.
The -x509 option tells req to create a self-signed cerificate. The -days 365 option specifies that the certificate will be valid for 365 days. A temporary CSR is generated to gather information to associate with the certificate.
Use this method if you already have a private key that you would like to generate a self-signed certificate with it.
This command creates a self-signed certificate ( domain.crt ) from an existing private key ( domain.key ):
Answer the CSR information prompt to complete the process.
The -x509 option tells req to create a self-signed cerificate. The -days 365 option specifies that the certificate will be valid for 365 days. The -new option enables the CSR information prompt.
Use this method if you already have a private key and CSR, and you want to generate a self-signed certificate with them.
This command creates a self-signed certificate ( domain.crt ) from an existing private key ( domain.key ) and ( domain.csr ):
The -days 365 option specifies that the certificate will be valid for 365 days.
Certificate and CSR files are encoded in PEM format, which is not readily human-readable.
This section covers OpenSSL commands that will output the actual entries of PEM-encoded files.
This command allows you to view and verify the contents of a CSR ( domain.csr ) in plain text:
This command allows you to view the contents of a certificate ( domain.crt ) in plain text:
Use this command to verify that a certificate ( domain.crt ) was signed by a specific CA certificate ( ca.crt ):
This section covers OpenSSL commands that are specific to creating and verifying private keys.
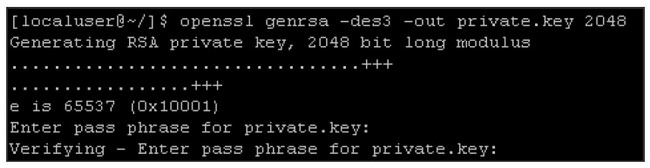
Use this command to create a password-protected, 2048-bit private key ( domain.key ):
Enter a password when prompted to complete the process.
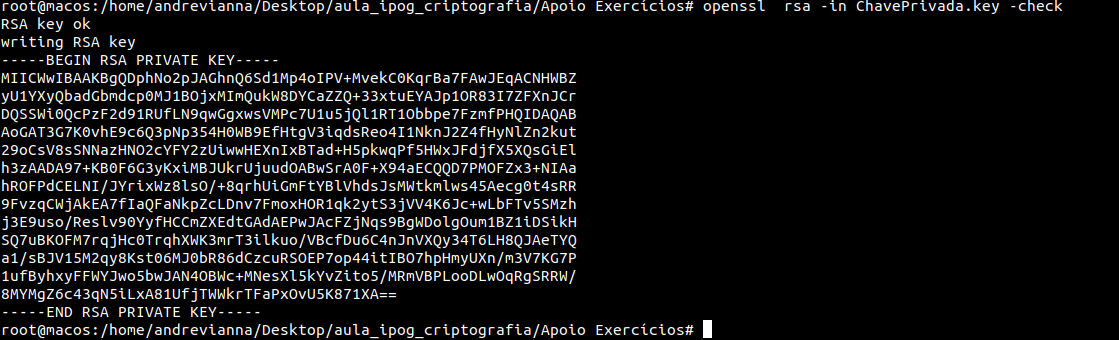
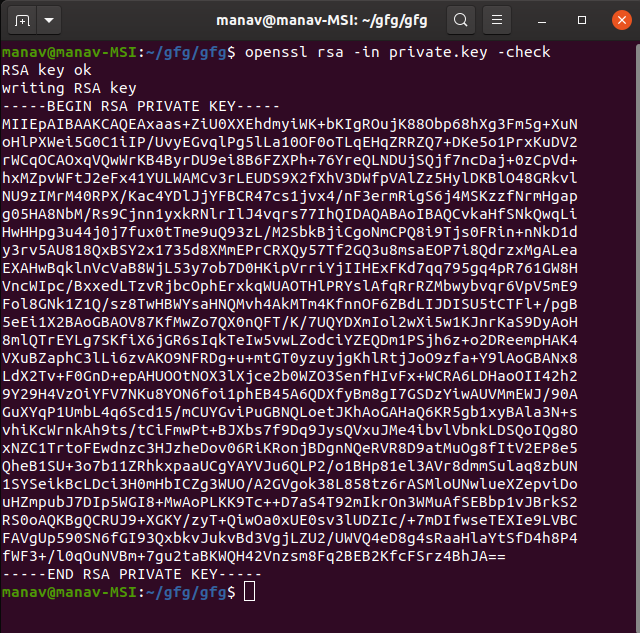
Use this command to check that a private key ( domain.key ) is a valid key:
If your private key is encrypted, you will be prompted for its pass phrase. Upon success, the unencrypted key will be output on the terminal.
Use these commands to verify if a private key ( domain.key ) matches a certificate ( domain.crt ) and CSR ( domain.csr ):
If the output of each command is identical there is an extremely high probability that the private key, certificate, and CSR are related.
This takes an unencrypted private key ( unencrypted.key ) and outputs an encrypted version of it ( encrypted.key ):
Enter your desired pass phrase, to encrypt the private key with.
This takes an encrypted private key ( encrypted.key ) and outputs a decrypted version of it ( decrypted.key ):
Enter the pass phrase for the encrypted key when prompted.
All of the certificates that we have been working with have been X.509 certificates that are ASCII PEM encoded. There are a variety of other certificate encoding and container types; some applications prefer certain formats over others. Also, many of these formats can contain multiple items, such as a private key, certificate, and CA certificate, in a single file.
OpenSSL can be used to convert certificates to and from a large variety of these formats. This section will cover a some of the possible conversions.
Use this command if you want to convert a PEM-encoded certificate ( domain.crt ) to a DER-encoded certificate ( domain.der ), a binary format:
The DER format is typically used with Java.
Use this command if you want to convert a DER-encoded certificate ( domain.der ) to a PEM-encoded certificate ( domain.crt ):
Use this command if you want to add PEM certificates ( domain.crt and ca-chain.crt ) to a PKCS7 file ( domain.p7b ):
Note that you can use one or more -certfile options to specify which certificates to add to the PKCS7 file.
PKCS7 files, also known as P7B, are typically used in Java Keystores and Microsoft IIS (Windows). They are ASCII files which can contain certificates and CA certificates.
Use this command if you want to convert a PKCS7 file ( domain.p7b ) to a PEM file:
Note that if your PKCS7 file has multiple items in it (e.g. a certificate and a CA intermediate certificate), the PEM file that is created will contain all of the items in it.
Use this command if you want to take a private key ( domain.key ) and a certificate ( domain.crt ), and combine them into a PKCS12 file ( domain.pfx ):
You will be prompted for export passwords, which you may leave blank. Note that you may add a chain of certificates to the PKCS12 file by concatenating the certificates together in a single PEM file ( domain.crt ) in this case.
PKCS12 files, also known as PFX files, are typically used for importing and exporting certificate chains in Micrsoft IIS (Windows).
Use this command if you want to convert a PKCS12 file ( domain.pfx ) and convert it to PEM format ( domain.combined.crt ):
Note that if your PKCS12 file has multiple items in it (e.g. a certificate and private key), the PEM file that is created will contain all of the items in it.
The openssl version command can be used to check which version you are running. The version of OpenSSL that you are running, and the options it was compiled with affect the capabilities (and sometimes the command line options) that are available to you.
The following command displays the OpenSSL version that you are running, and all of the options that it was compiled with:
This guide was written using an OpenSSL binary with the following details (the output of the previous command):
That should cover how most people use OpenSSL to deal with SSL certs! It has many other uses that were not covered here, so feel free to ask or suggest other uses in the comments.
If you are having issues with any of the commands, be sure to comment (and include your OpenSSL version output).
Software Engineer @ DigitalOcean. Former Señor Technical Writer (I no longer update articles or respond to comments).
Great summary, was recently looking for exactly something like that. Thank you for the write up.
I recently stumbled across https://shaaaaaaaaaaaaa.com/ summarizing the soon to come retirement of SHA-1.
It may be of use also for this tutorial to add the option
I did that for a recent request from StartSSL and they offered a certificate accommodating the more secure requirements (passing also A+ on ssllabs.com)
Since you especially describe how to generate CSR for obtaining a certificate, it may be worth adding the option in order to be more future proof.
Great Summary. I want to know how can I add a key usage extension to a certificate. Specifically to make it act as a local-CA to sign other certificates?
I need to copy paste the Certificate Signing Request (CSR) how do i get a hold of it?
One way to view the CSR is to type cat domain.csr . This will print the contents of the file to the screen (which you then can copy).
Make sure you are in the same directory that you generated the CSR in.
thanks i see it now but cant do Ctrl+c
You are probably using a terminal, Putty, Cygwin or something similar. In those programs you commonly can Ctrl + Insert to copy and Shift + Insert to paste.
In addition to what @tiangolo mentioned, you can probably right-click and select copy from the menu.
Too good. I was very happy after going through the articles. It helped me a lot. Especially the verification part.
Someone else created a csr request, and we got the final mail from CA which gave the X509 Certificates and intermediates only certificates. Now I am not sure that whether I am supposed to generate another private key based on the certificate, it would be great if you can explain about this part.
The CSR is created from the private key. Whoever created the CSR should also have the private key.
The command provided in section “Generate a CSR from an Existing Certificate and Private Key” generates a file with the plaintext csr and encoded version:
Is there any option to output only the encoded version?
Great article. Learnt a lot. Thanks for sharing.
Mitchell - Fantastic post! Just one slight correction:
The option uses a lowercase “f”, as in:
⏿ I saw that too! Maybe here we can use like RFC « Errata exists » but like my way , at top: « Errata existed, see bottom » (I mean, text fixed with a numbered superscript and the last-last-last section for explain every errata, if exists).
That “little” change will need consensus between moderators and after write the code (and remember, don’t deploy CSM’s code on Friday , ja, ja, ja)
P.S.: I have read and translated into Spanish (with some tutorials have learned so much, like this) and erratas are very-little-few! Congratulations for a good job!
Thanks for this wonderful article, DO has always been of great article.
I am facing an issue with my SSL certificate installation, if you could help me.
I bought a Rapid SSL and used the below command to generate the .csr and .key files:
I answered all questions which this command asked. I then provided the .csr to name.com and successfully generated the server/intermediate certificates. I then followed the steps mentioned at https://knowledge.rapidssl.com/support/ssl-certificate-support/index?page=content&actp=CROSSLINK&id=SO17664 and installed this certificate at my nginx server. I was able to open the HTTPS version of my site as well.
Now, to try something else, I run the command (sudo openssl req… ) again with different answers this time and regenerated a new server.key file. Unfortunately, I didn’t save the first server.key file. Post modification of nginx .conf file, when I tried to restart the server, I got the below error:
Seeing this error, I realized I have overwritten the server.key file. I tried to generate the key again with same answers I gave for the first time but still the key mismatch error is coming.
My nginx server is still running and I am able to access the HTTPS version of the site but my life is in trouble without the private key. I have gone through the below links but still stuck:
I confirmed by running the below commands that my certificate (issued by name.com) and private keys don’t match:
Is there anything which I can do to find out the private key since Nginx is still up and running? In case not, should I get the certificate re-issued by Geotrust?
Any help would be deeply appreciated.
It will be very useful to explain creation of self-signed local CA pairs, signing CSR and install this CA certt on clients.
Normally one would want the baddest certifcate you can get, un-deciferable cifers, un-stealable keys …
I have a different need, a dumbed down tls1.1 small key/cipher/cert that will work on esp8266’s, these tiny, wifi enabled, mqtt protoocol running, $2, iot devices. OK so I made a 512byte private key. Now I need to make a cert and a sha-1 thumbprint that will work with small memory devices using tls1.1, TLS RSA WITH AES 128 CBC SHA or RC4-MD5 ciphers.
Any ideas on an oppenssl command to get that?
Thanks DO for the great article. Can you explain the command to create the intermediate cert with the csr and private key
Great and concise guide. Saved a lot of my time, thanks for sharing!
Great article. For https ,I had created client private key and certificate key. When i had tried connect the https server below logs were coming. But finally able to connect the server(Taking more time).
connected to server
.......................................................
I had used “openssl verify -verbose -CAFile ca.crt domain.crt” for to create the client certificate and “openssl genrsa -des3 -out domain.key 2048 ” for to create privare key.
Could you please tell me if I missed something in my configuration of SSL?
Am i doing wrong?? any suggestions ??please
I have created a sample project using python to create and manage SSL certificates, if anyone interested can have a look at it. https://github.com/parthibann/shield
openssl rsa -des3 \
-in unencrypted.key \
-out encrypted.key
I’ve followed through and been able to create my rsa domain.key, domain.csr and domain.crt THANK YOU SO MUCH! :)
I’m using windows terminal to ssh into my Ubuntu droplet.
Once you started using multi-line commands which are indented I haven’t been able to run these. Can I have your advice please.
I’ve tried copying and pasting, typing, and I read the comment below regarding Ctrl+ins and Shift+ins from community/users/tiangolo with no success. I’ve tried stringing your command lines together into one line but I can’t get a result. I can’t encrypt my private.key for the same reason.
SOLVED
Odly, I just reset, ssh logged back in and it works fine just copying and right click pasting!
Thanks again:)
Hello, great article! I just want to ask you, maybe you know or you can give me a hint or suggestion.
How can I create a CSR by passing the information from a json file, not with -subj? Thank you for your time.
You can also create your own certificate authority and sign your own certificates, then trust your own certificate authority so you don’t get warnings.
Sign up for Infrastructure as a Newsletter.
Working on improving health and education, reducing inequality, and spurring economic growth? We'd like to help.
You get paid; we donate to tech nonprofits.
DigitalOcean makes it simple to launch in the cloud and scale up as you grow – whether you’re running one virtual machine or ten thousand.
We use cookies to provide our services and for analytics and marketing.
To find out more about our use of cookies,
please see our
Privacy Policy
and
Cookie and Tracking Notice .
By continuing to browse our website, you agree to our use of cookies.
Common OpenSSL Commands with Keys and Certificates · GitHub
OpenSSL Essentials: Working with SSL Certificates, Private Keys and CSRs
OpenSSL Tutorial: How Do SSL Certificates, Private Keys , & CSRs Work?
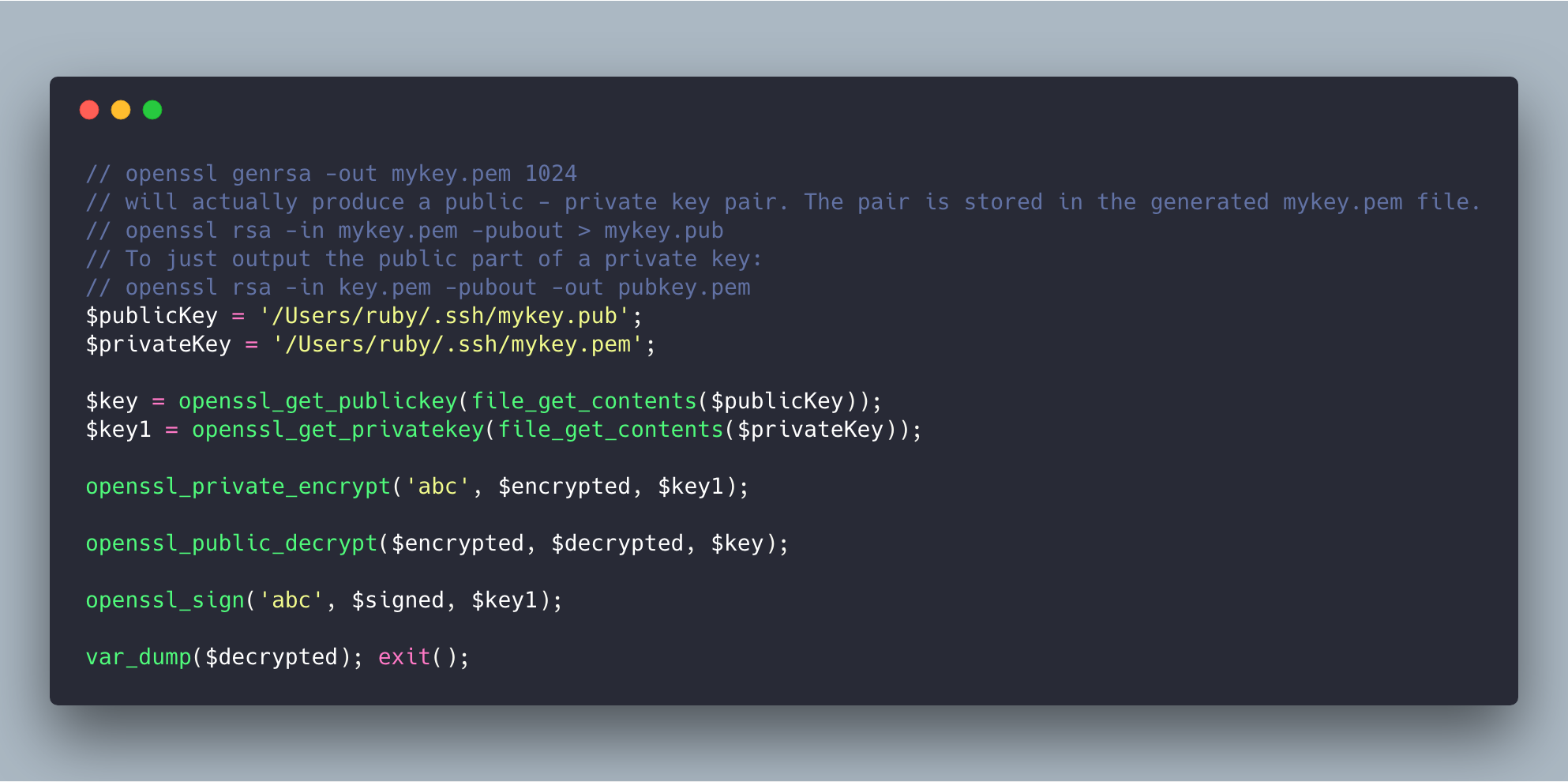
openssl _ privatekey - Generate OpenSSL private keys . — Ansible Documentation
PHP: openssl _get_ privatekey - Manual
OpenSSL Tutorial: How Do SSL Certificates, Private Keys, & CSRs Work?
What is an SSL Certificate? How Does SSL Work?
What’s the Difference Between TLS and SSL?
How Can I Know Whether a Web Page is Secured With SSL?
Where Can I Get an SSL Certificate?
Multiple Domain (SAN/UC Certificates)
openssl-1.0.1e-48.el6_8.1.x86_64
openssl-devel-1.0.1e-48.el6_8.1.x86_64
openssl-1.0.1e-48.el6_8.1.i686
What’s a Certificate Signing Request (CSR)?
openssl req –out certificatesigningrequest.csr -new -newkey rsa:2048 -nodes -keyout privatekey.key
openssl req -in server.csr -noout -text
Option 2: Generate a CSR for an Existing Private Key
openssl req -out CSR.csr -key privateKey.key -new
Option 3: Generate a CSR for an Existing Certificate and Private Key
openssl x509 -x509toreq -in certificate.crt -out CSR.csr -signkey privateKey.key
Option 4: Generate a Self-Signed Certificate
openssl req -newkey rsa:2048 -nodes -keyout domain.key-x509 -days 365 -out domain.crt
Option 5: Generate a Self-Signed Certificate from an Existing Private Key and CSR
openssl x509 \ -signkey domain.key \ -in domain.csr \ -req -days 365 -out domain.crt
How to Copy the Contents of a CSR File
Certificate Renewal – Don’t Reuse Old CSRs
How to Verify Your CSR, SSL Certificate, and Key
openssl req -text -noout -verify -in server.csr
openssl x509 -in server.crt -text –noout
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQCVqGpH2S7F0CbEmQBgmbiDiOOGxhVwlG+yY/6OBQoPKcx4Jv2h
vLz7r54ngjaIqnqRNP7ljKjFLp5zhnAu9GsdwXbgLPtrmMSB+MVFHTJvKjQ+eY9p
dWA3NbQusM9uf8dArm+3VrZxNHQbVGXOIAPNHTO08cZHMSqIDQ6OvLma7wIDAQAB
AoGAbxKPzsNh826JV2A253svdnAibeSWBPgl7kBIrR8QWDCtkH9fvqpVmHa+6pO5
5bShQyQSCkxa9f2jnBorKK4+0K412TBM/SG6Zjw+DsZd6VuoZ7P027msTWQrMBxg
Hjgs7FSFtj76HQ0OZxFeZ8BkIYq0w+7VQYAPBWEPSqCRQAECQQDv09M4PyRVWSQM
S8Rmf/jBWmRnY1gPPEOZDOiSWJqIBZUBznvOPOOQSH6B+vee/q5edQA2OIaDgNmn
AurEtUaRAkEAn7/65w+Tewr89mOM0RKMVpFpwNfGYAj3kT1mFEYDq+iNWdcSE6xE
2H0w3YEbDsSayxc36efFnmr//4ljt4iJfwJAa1pOeicJhIracAaaa6dtGl/0AbOe
f3NibugwUxIGWkzlXmGnWbI3yyYoOta0cR9fvjhxV9QFomfTBcdwf40FgQJAH3MG
DBMO77w8DK2QfWBvbGN4NFTGYwWg52D1Bay68E759OPYVTMm4o/S3Oib0Q53gt/x
TAUq7IMYHtCHZwxkNQJBAORwE+6qVIv/ZSP2tHLYf8DGOhEBJtQcVjE7PfUjAbH5
lr++9qUfv0S13gXj5weio5dzgEXwWdX2YSL/asz5DhU=
-----END RSA PRIVATE KEY-----
openssl x509 -noout -modulus -in server.crt| openssl md5
openssl rsa -noout -modulus -in server.key| openssl md5
The System Doesn’t Fetch the Private Key Automatically
I Need to Locate My Previously Installed Private Key
OpenSSL 1.0.2g 1 Dec 2016
built on: reproducible build, date unspecified
platform: debian-amd64
options: bn(64,64) rc4(16x,int) des(idx,cisc,16,int) blowfish(idx)
compiler: cc -I. -I.. -I../include -fPIC -DOPENSSL_PIC -DOPENSSL_THREADS -
D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -m64 -DL_ENDIAN -g -O2 -fstack-protector-
strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 -Wl,-
Bsymbolic-functions -Wl,-z,relro -Wa,--noexecstack -Wall -DMD32_REG_T=int -
DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -
DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DAES_ASM -
DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM -DECP_NISTZ256_ASM
OPENSSLDIR: "/usr/lib/ssl"
Open the Microsoft Management Console (MMC).
Located under Console Root, expand the Certificates (Local Computer) tree.
Your certificate is either located in the Personal or Web Hosting folder . Find the certificate you are looking for. You can identify each certificate by its Common Name (Domain).
Right-click the certificate you wish to export, and then select All Tasks > Export .
Follow the guided wizard to export the .pfx file.
How to Move an SSL Certificate from a Windows Server to Non-Windows server?
OpenSSL Commands for Converting CSRs
openssl pkcs12 \ -inkey domain.key \ -in domain.crt \ -export -out domain.pfx
openssl pkcs12 \ -in domain.pfx \ -nodes -out domain.combined.crt
openssl x509 \ -in domain.crt \ -outform der -out domain.der
openssl x509 \ -inform der -in domain.der \ -out domain.crt
openssl rsa -des3 \ -in unencrypted.key \ -out encrypted.key
openssl rsa \ -in encrypted.key \ -out decrypted.key
Recent Posts
How to Use the Linux tee Command
RHEL Becomes Free for Small Production Workloads
Netstat Command in Linux – 28 Commands with Examples
© 2021 Copyright phoenixNAP | Global IT Services. All Rights Reserved.
Initially developed by Netscape in 1994 to support the internet’s e-commerce capabilities, Secure Socket Layer (SSL) has come a long way. Amidst all the cyber attacks, SSL certificates have become a regular necessity for any live website.
Even though Secure Socket Layer (SSL) and Transport Socket Layer (TLS) have become quite ubiquitous, we will take a brief moment to explain what they do and how they do it.
Do not skip the OpenSSL Tutorial section.
A Secure Socket Layer (SSL) certificate is a security protocol which secures data between two computers by using encryption.
Note : Simply put, an SSL certificate is a data file that digitally ties a Cryptographic Key to a server or domain and an organization’s name and location.
Typically, SSL certificates are used on web pages that transmit and receive end-user sensitive data, such as Social Security Number, credit card details, home address or password. Online payment forms are a good example and usually encrypt the aforementioned delicate information using 128 or 256-bit SSL technology.
SSL certificates ensure the identity of a remote computer, most commonly a server, but also confirms your computer’s identity to the remote computer to establish a safe connection. Keeping the internet safe has always been a two-way street and thanks to SSL encryption, the server “shakes hands” with your personal computer and both sides know with whom they are communicating.
There is none . Transport Layer Security (TLS) is an updated version of Secure Socket Layer (SSL). Even though most secure connections are via TLS protocols, people keep calling it SSL. In this case, it’s safe to say that old habits do die hard.
As an internet user, you have probably noticed a padlock and the site info bar turning green in your web browser, as well as the https connection protocol.
That’s your browser letting you know that a website is secured using SSL encryption. Clicking the site info bar will provide additional details about the connection as well as insight into the SSL certificate itself.
You’re an e-commerce site owner who just leased a server with phoenixNAP and launched a couple of new e-commerce stores. You want your visitors to feel safe when visiting your e-store and, above all, not feel hesitant to log in and make a purchase.
An SSL certificate and HTTPS connection instills consumer confidence. The e-commerce industry is tied closely to consumer trust, and we might even say that your business depends on your customers feeling safe during the entire buying experience.
Besides the obvious security reasons, an SSL certificate increases your site’s SEO and Google Ranking and builds customer trust, consequently improving overall conversion rates.
If that is not enough to make you consider getting an SSL certificate for your domain, Google is sure to persuade you. Namely, starting from July 2018 Google flags each website without SSL as unsafe.
SSL certificates are verified and issued by a Certificate Authority (CA). You apply by generating a CSR with a key pair on your server that would, ideally, hold the SSL certificate. The CSR contains crucial organization details which the CA verifies.
Note : It is not uncommon for popular browsers to distrust all certificates issued by a single Certificate Authority. For example, Google Chrome has distrusted Symantec root certificates, due to Symantec breaching industry policies on several occasions. This means that all certificates rooted at Symantec have become invalid, no matter what their “valid through” date is.
Make sure that you choose a CA that supports the certificate type you need. For your convenience, below is a description of each certificate type:
This type is meant to be used for a single domain and offers no support for subdomains. For example, if the certificate is to be used for www.phoenixnap.com, it will not support any other domain name.
Multiple domain certificates are used for numerous domains and subdomains. Besides the FQDN, you can add support for other (sub)domains by adding them to the Subject Alternative Name Field. For example, a SAN certificate can include the domain www.phoenixnap.com, its subdomain help.phoenixnap.com as well as another domain (e.g., www.examplesite.com).
Wildcard certificates can be used for a domain, including all of its subdomains. The main difference is that instead of it being issued for a specific FQDN, wildcard certificates are used for a wide range of subdomains. For example, a wildcard certificate issued to *.phoenixnap.com could be used for a wide range of subdomains under the main www.phoenixnap.com domain, as seen in the image below.
CAs have diversified certificate validation levels in response to a growing demand for certificates. Some organizations use SSL just for encryption, while others want to show their customers that they are a trusted company. Different needs have resulted in different certificate validation levels.
This type of SSL certificate is ideal for securing blogs, social media apps, and personal websites. The certificate authority does not guarantee for an organization’s identity, and only domain ownership is verified.
The certificate authority verifies domain ownership and conducts a thorough investigation of the organization associated with the EV certificate. Strict rules are followed when reviewing an extended validation request, and the CA has to verify the following:
How to generate a certificate signing request solely depends on the platform you’re using and the particular tool of choice.
We will be generating a CSR using OpenSSL .
OpenSSL is a widely-used tool for working with CSR files and SSL certificates and is available for download on the official OpenSSL website. It is an open-source implementation tool for SSL/TLS and is used on about 65% of all active internet servers, making it the unofficial industry standard.
If the OpenSSL packet is installed, it will return the following result:
If you do not see such a result, run the following command to install OpenSSL:
Red Hat (release 7.0 and later) should come with a preinstalled limited version of OpenSSL. It offers only limited support for IDEA, RC5, and MDC2, so you may want to install the missing features. To read more about this, see OpenSSL’s documentation.
To check whether OpenSSL is installed on a yum server (e.g., Red Hat or CentOS), run the following command:
This command should return the following result:
If your output format differs, it means that OpenSSL is not installed on your server. Run the following command to install OpenSSL:
A certificate signing request (CSR) contains the most vital information about your organization and domain.
Usually, you would generate a CSR and key pair locally on the server where the SSL certificate will be installed. However, that is not a strict rule. You can generate a CSR and key pair on one server and install the certificate on another. However, that makes things more complicated. We shall cover that scenario as well.
Note : A certificate signing request (CSR) is an encrypted block of text that includes your organization’s information, such as country, email address, fully qualified domain name, etc. It is sent to the Certificate Authority when applying for an SSL certificate.
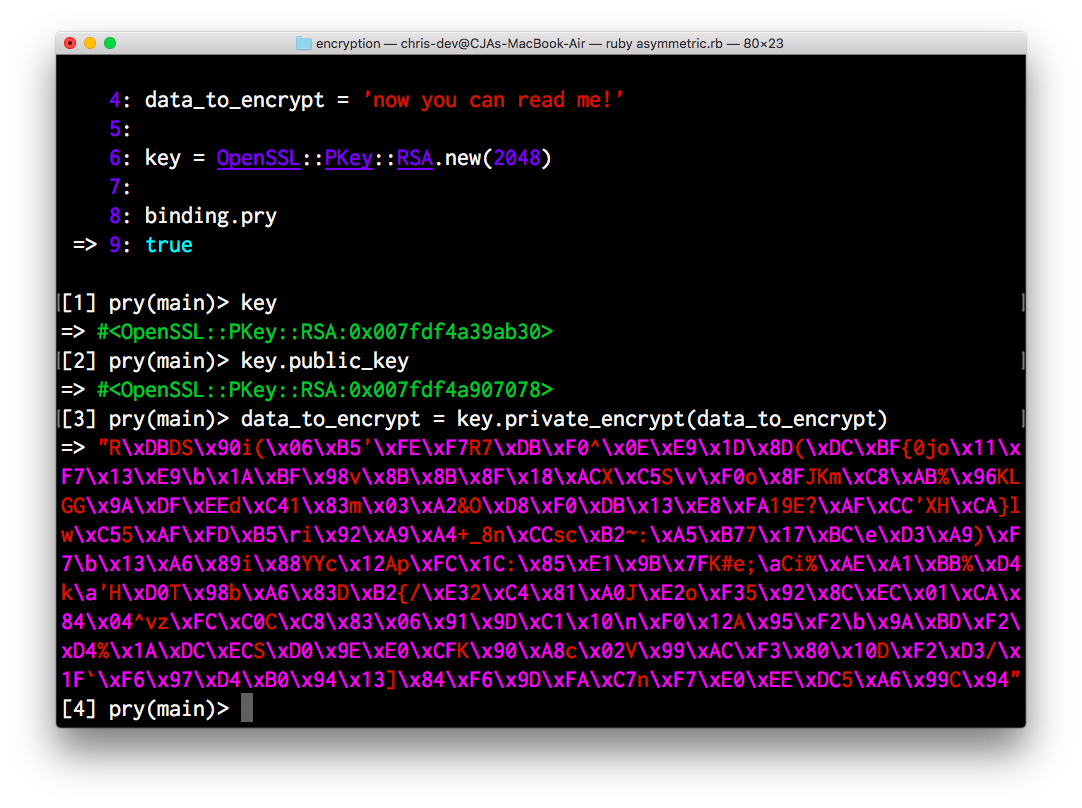
Secure Socket Layer (SSL) uses two long strings of randomly generated numbers, which are known as private and public keys . A public key is available to the public domain as it is a part of your SSL certificate and is made known to your server.
The private key must correspond to the CSR it was generated with and, ultimately, it needs to match the certificate created from the CSR. If the private key is missing, it could mean that the SSL certificate is not installed on the same server which generated the Certificate Signing Request .
A CSR usually contains the following information:
Please note there are certain naming conventions to be considered. Organization Name and Organizational Unit Name must not contain the following characters: < > ~ ! @ # $ % ^ * / \ ( ) ?.,&
Certificate signing requests (CSR) are generated with a pair of keys – a public and private key. Only the public key is sent to a Certificate Authority and included in the SSL certificate, and it works together with your private key to encrypt the connection. Anyone can have access to your public key, and it verifies that the SSL certificate is authentic.
A private key is a block of encoded text which, together with the certificate, verifies the secure connection between two machines. It must not be publicly accessed, and it shouldn’t be sent to the CA.
The integrity of a certificate relies on the fact that only you know the private key. If ever compromised or lost, re-key your certificate with a new private key as soon as possible. Most CAs do not charge you for this service.
Note : Most key pairs are 2048-bits. Even though 4096-bits key pairs are more secure, they slow down SSL handshakes and put a strain on server processors. Due to this, most websites still use 2048-bit key pairs.
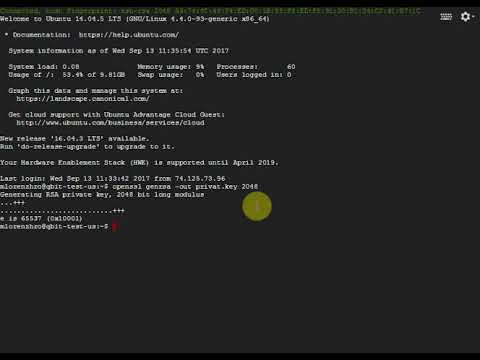
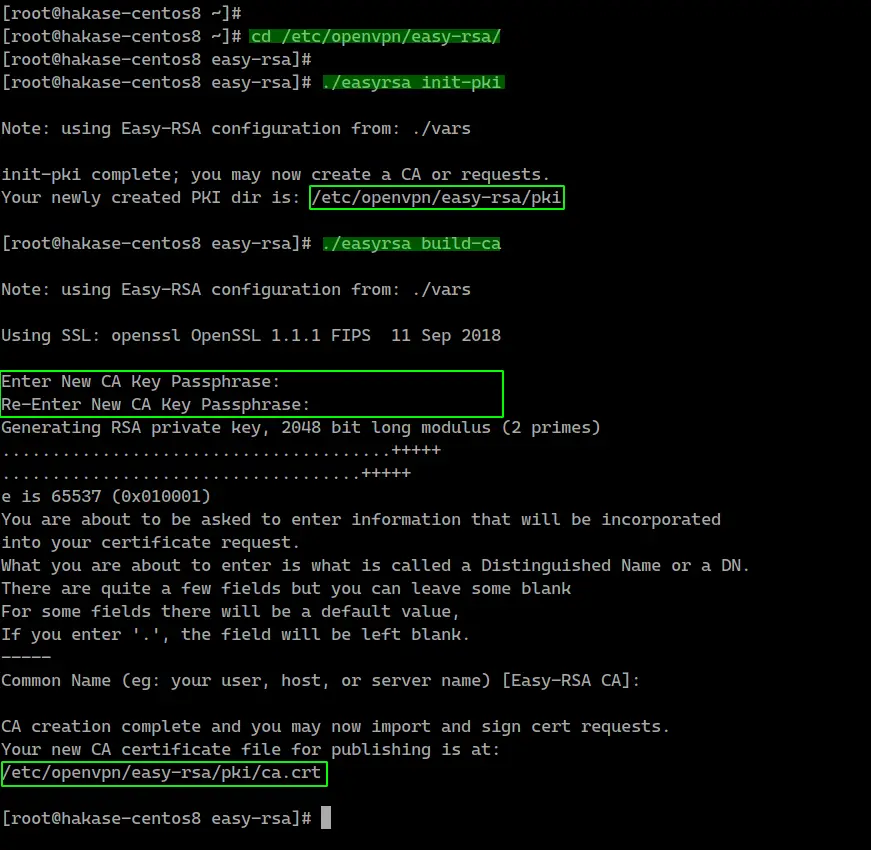
The first thing to do would be to generate a 2048-bit RSA key pair locally. This pair will contain both your private and public key. You can use Java key tool or some other tool, but we will be working with OpenSSL.
To generate a public and private key with a certificate signing request (CSR), run the following OpenSSL command:
Once you have generated a CSR with a key pair, it is challenging to see what information it contains as it will not be in a human-readable format. You can easily decode the CSR on your server using the following OpenSSL command:
It is advised to decode the CSR and verify that it contains the right information about your organization before it’s sent off to a certificate authority. There are a lot of CSR decoders on the web that can help you do the same just by copy-pasting the content of your CSR file.
For your convenience, we have listed two (2) online CSR decoder tools:
Note : A certificate signing request generated with OpenSSL will always have the .csr file format.
It is recommended to issue a new private key whenever you are generating a CSR. If, for any reason, you need to generate a certificate signing request for an existing private key, use the following OpenSSL command:
One unlikely scenario in which this may come in handy is if you need to renew your existing certificate, but neither you nor your certificate authority have the original CSR. This will extract information about your domain and organization from the SSL certificate and use it to create a new CSR, thus saving you time.
A self-signed certificate is usually used for test and development environments and on an intranet. Let’s generate a self-signed certificate using the following OpenSSL command:
The –days parameter is set to 365, meaning that the certificate is valid for the next 365 days. The x509 parameter indicates that this will be a self-signed certificate. A temporary CSR is generated, and it is used only to gather the necessary information.
Certificate Authorities do not verify self-signed certificates. Thus, they are not as secure as verified certificates. If a CA has not signed the certificate, every major browser will display an “untrusted certificate” error message, like the one seen in the image below.
If you do not want to protect your private key with a password, you can add the –nodes parameter.
Cloud for software development starting at only $4.35/month
If you already have a CSR and private and need to generate a self-signed certificate, use the following command:
The – days parameter is set to 365, meaning that the certificate is valid for the next 365 days.
Open the directory in which your CSR file is located. Type the following command:
Replace d omain with the FQDN parameter of your CSR. This command will display the content of the CSR file. Copy all the content, starting from “BEGIN CERTIFICATE REQUEST” and ending with “END CERTIFICATE REQUEST”.
Just because some web servers allow using old CSRs for certificate renewal doesn’t mean you should use them. As a security precaution, always generate a new CSR and private key when you are renewing a certificate. Clinging to the same private key is a road paved with security vulnerabilities.
Also, it is recommended to renew an SSL certificate before the expiration date. Otherwise, a new certificate purchase will be required.
As we have already mentioned, it would be wise to check the information provided in the CSR before applying for a certificate. Use the following commands to verify your certificate signing request, SSL certificate, and key:
This command will verify the CSR and display the data provided in the request.
The following command will verify the key and its validity:
When you need to check a certificate, its expiration date and who signed it, use the following OpenSSL command:
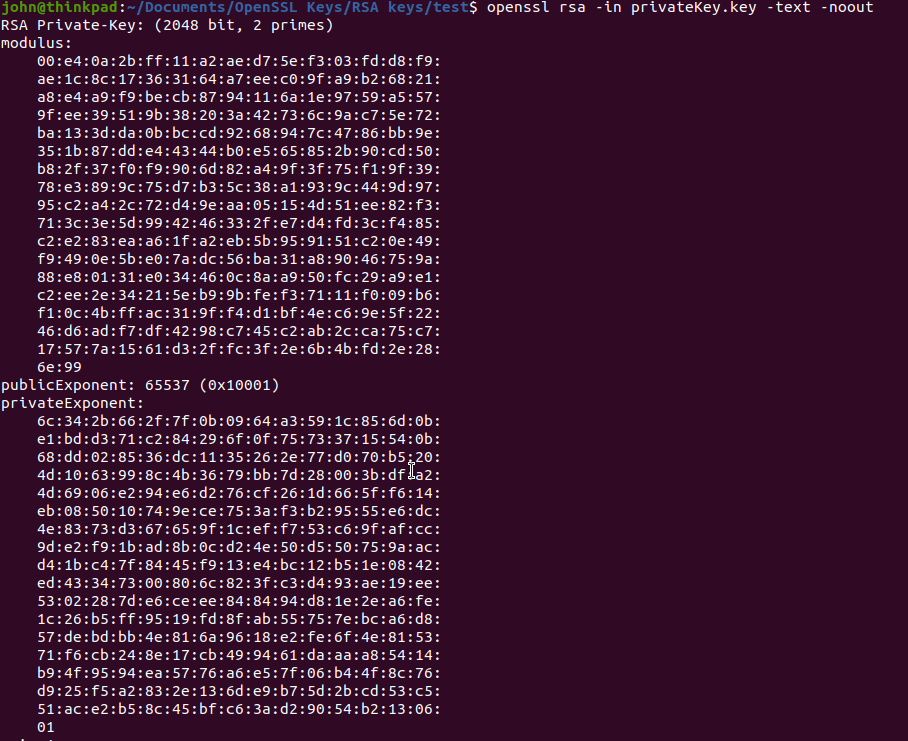
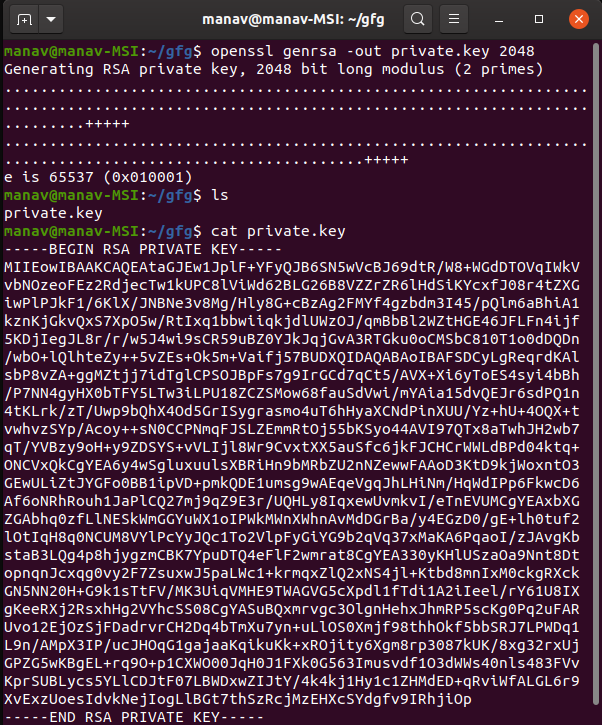
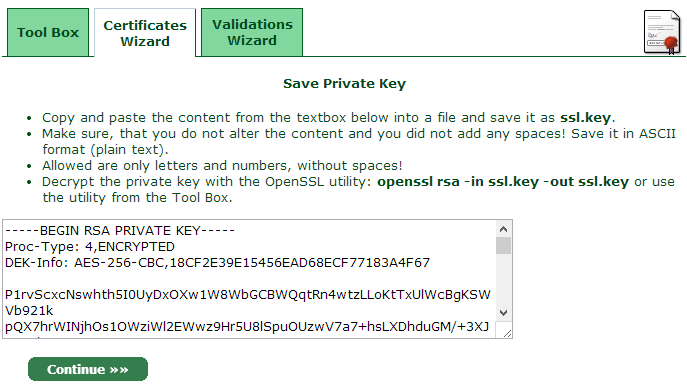
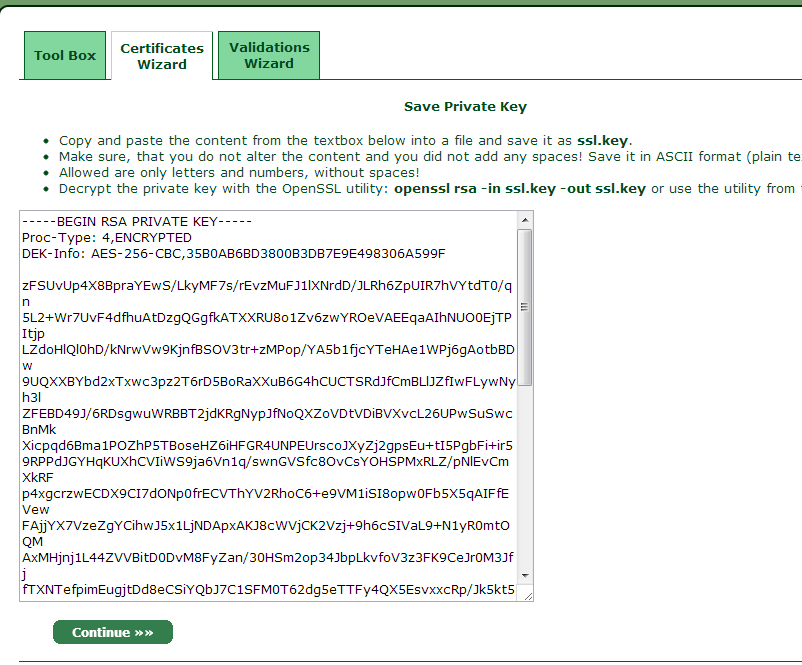
A private key is encoded and created in a Base-64 based PEM format which is not human-readable. You can open it with any text editor, but all you will see is a few dozen lines of what seem to be random symbols enclosed with opening and closing headings. See below an example of a private key:
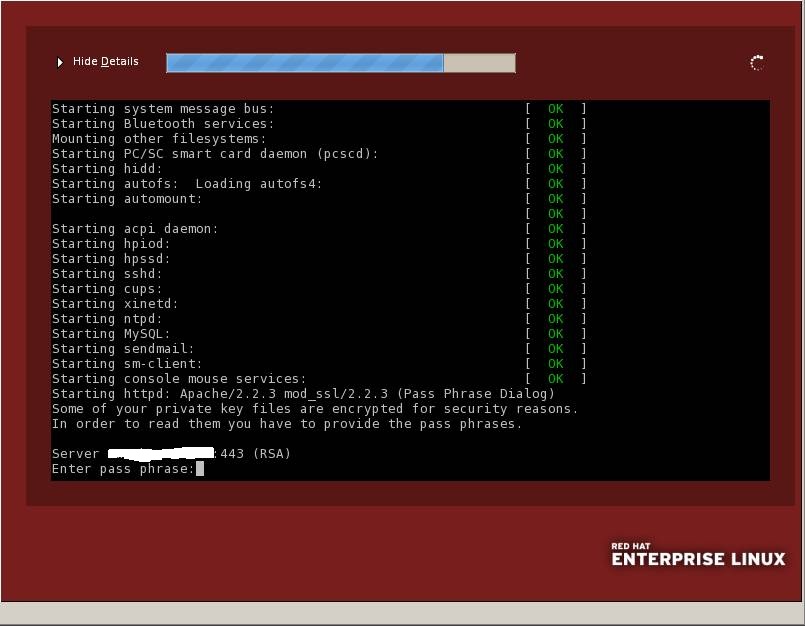
In most cases, you won’t need to import the private key code into the server’s filesystem, as it will be created in the background while you generate the CSR and then saved onto the server automatically. During SSL certificate installation , the system fetches the key.
Verify Whether a Certificate and Private Key Match
To verify, you need to print out md5 checksums and compare them. Execute the following command:
Some systems do not automate the procedure of fetching a private key. Furthermore, if you need to install an existing certificate on another server, you obviously cannot expect that it will fetch the private key. The main difficulty here is how to find the exact location of the key. How you can retrieve the key depends on the server OS in use and whether a command line interface or a web-hosting control panel of a particular type was used for CSR generation.
If the case is that your certificate has already been installed, follow the steps below which will help you locate your private key on popular operating systems.
You should be able to find the location of your server’s private key in your domain’s virtual host file.
Navigate to the site’s root server location (usually, it’s /var/www/directory ) and open the site’s main configuration file. Look for the ssl_certificate_key directive that will supply the file path of the private key.
If you cannot find the ssl_certificate_key directive, it might be that there’s a separate configuration file for SSL details. Look for something descriptive, such as ssl.conf .
When using the OpenSSL library on Apache, the private key is saved to /usr/local/ssl by default. Run openssl version –a , a OpenSSL command which identifies which version of OpenSSL you’re running .
The output will display the directory which holds the private key. See the example output below:
The last line OPENSSLDIR defines the file path. In the example provided, it is the default location /usr/lib/ssl .
If you didn’t generate the CSR with OpenSSL, you need to find and access your main Apache configuration file, which is apache2.conf or httpd.conf . The SSLCertficateKeyFile directive will specify the file path of the private key.
On servers running Windows Internet Information Services, the operating system saves the private key in a hidden folder, much like any regular Windows OS stores critical system data.
However, by exporting a .pfx file, you can fetch the private key and certificate(s). To do so follow the steps below:
You have what you need if you want to save a backup or install the certificate on another Windows server.
If you need to install the certificate on another server that’s not running Windows (e.g., Apache) you need to convert the .pfx file and separate the .key and .crt/.cer files. You can do so with OpenSSL.
In order to move a certificate from a Windows server to a non-Windows server, you need to extract the private key from a .pfx file using OpenSSL.
Where mypfxfile.pfx is your Windows server certificates backup.
If you can’t find the private key, look for clues. One thing to note is whether the server is providing a working HTTPS connection. If that is the case, then the private key is accessible to the server and is most likely somewhere on the server.
The logical step would be to search for a .key file. In some cases, OpenSSL stores the .key file to the same directory from where the OpenSSL –req command was run.
If you tried everything and still can’t find the .key file, there is a slight possibility that the key is lost. Don’t panic, the smart thing to do would be to generate a new CSR and reissue the certificate. Make sure to remember the location of the private key this time.
If you are working with Apache servers, certificate signing requests (CSRs) and keys are stored in PEM format. But what if you want to transfer CSRs to a Tomcat or Windows IIS server? Well, you would have to convert a standard PEM file to a PFX file. The following commands will help you do exactly that.
Note: Use the -nodes parameter when you don’t want to encrypt the .key file. If you do not use this parameter, you will need to provide a password.
Convert a PEM CSR and private key to PKCS12 (.pfx .p12)
FKCS12 files are used to export/import certificates in Windows IIS.
This will take the private key and the CSR and convert it into a single .pfx file. You can set up an export passphrase, but you can leave that blank. Please note that by joining certificate character strings end-to-end in a single PEM file, you can export a chain of certificates to a .pfx file format.
If the .pfx file contains a chain of certificates, the .crt PEM file will have multiple items as well.
DER is a binary format usually used with Java. To convert an ASCII PEM file to DER, use the following OpenSSL command:
If you need to convert a .der file to PEM, use the following OpenSSL command:
The following OpenSSL command will take an unencrypted private key and encrypt it with the passphrase you define.
Define the passphrase to encrypt the private key.
The following OpenSSL command will take an encrypted private key and decrypt it.
When prompted, enter the passphrase to decrypt the private key.
After this tutorial guide should know how to generate a certificate signing request using OpenSSL , as well as troubleshoot most common errors.
Make sure to verify each certificate authority and the types of certificates available to make an educated purchase.
Learn how to obtain and install SSL Certificates on Apache CentOS 7. The article explains how to use an…
OpenSSL is an open-source cryptographic library and SSL toolkit. The applications contained in the library…
A Certificate Signing Request (CSR) is the first step in setting up an SSL Certificate on your website. An…
Are you running into the ERR_SSL_VERSION_OR_CIPHER_MISMATCH error? This error happens in a user’s browser…
Dejan is the Technical Writing Team Lead at phoenixNAP with over 6 years of experience in Web publishing. Prior to joining phoenixNAP, he was Chief Editor of several websites striving to advocate for emerging technologies. He is dedicated to simplifying complex notions and providing meaningful insight into data center and cloud technology.
FQDN is the fully qualified domain name of your website. It must be the same as what users type in the web browser.
The full legal name of your organization, including suffixes such as LLC, Corp, etc.
The division in your organization that deals with this certificate.
The city in which your organization is located.
The state or region in which your organization is located.
The country in which your organization is located. Always entered as a two-letter ISO code.
Email address used to contact the site’s webmaster.
An automatically-created key that’s generated with the CSR and goes into the certificate.
An encoded text block similar to the private key. See an example of a private key below.
Landscape Lighting Outdoor Lighting Led Lighting
Private Beach
21 Outdoor
Gaming Naked
Amateur Hardcore Sex Video