Openssl Generate Private Key

🛑 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE👈🏻👈🏻👈🏻
OpenSSL is a CLI (Command Line Tool) which can be used to secure the server to generate public key infrastructure (PKI) and HTTPS. This article helps you as a quick reference to understand OpenSSL commands which are very useful in common, and for everyday scenarios especially for system administrators.
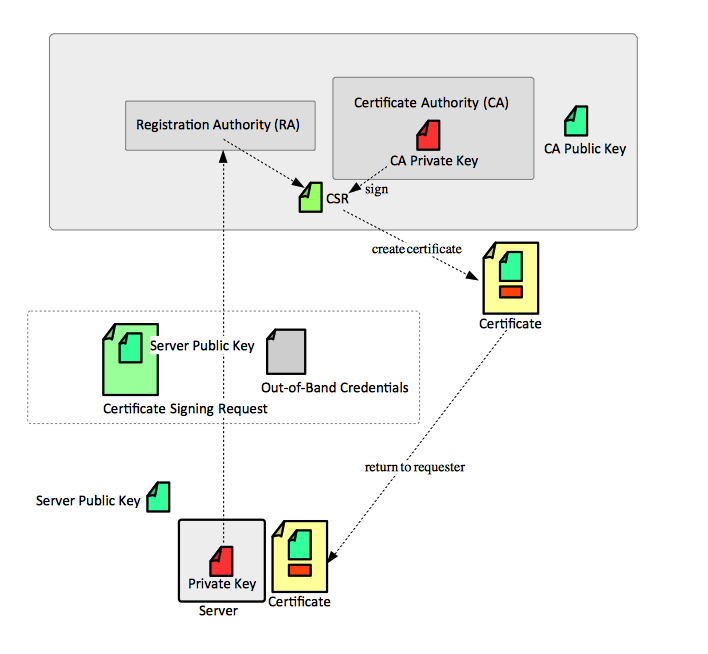
If we want to obtain SSL certificate from a certificate authority (CA), we must generate a certificate signing request (CSR). A CSR consists of mainly the public key of a key pair, and some additional information. Both these components are merged into the certificate whenever we are signing for the CSR.
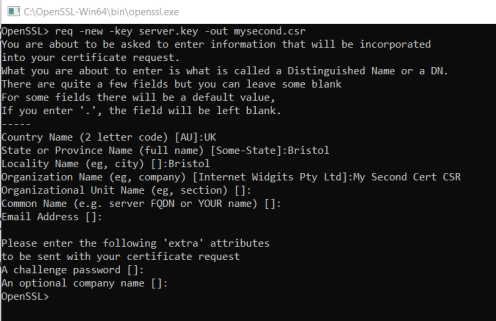
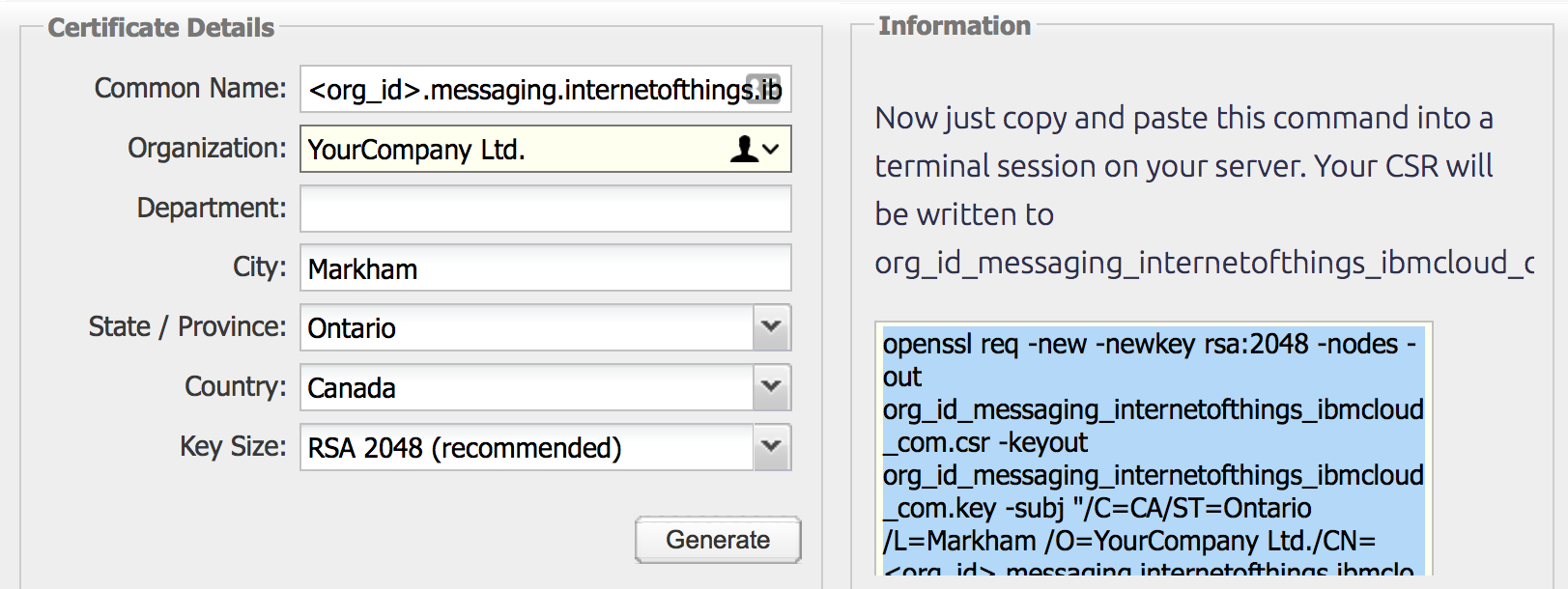
While generating a CSR, the system will prompt for information regarding the certificate and this information is called as Distinguished Name (DN). The important field in the DN is the Common Name (CN) which should be the FQND (Fully Qualified Domain Name) of the server or the host where we intend to use the certificate with.
The next item in a DN is to provide the additional information about our business or organization. If we purchase an SSL certificate from a certificate authority (CA), it is very important and required that these additional fields like “Organization” should reflect your organization for details.
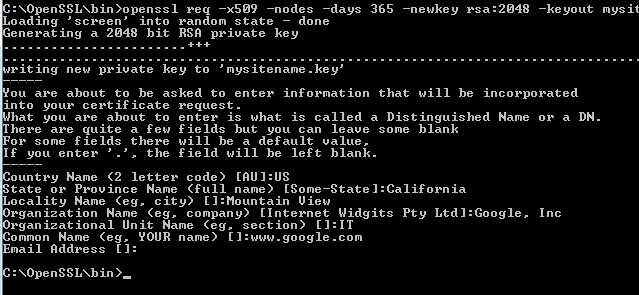
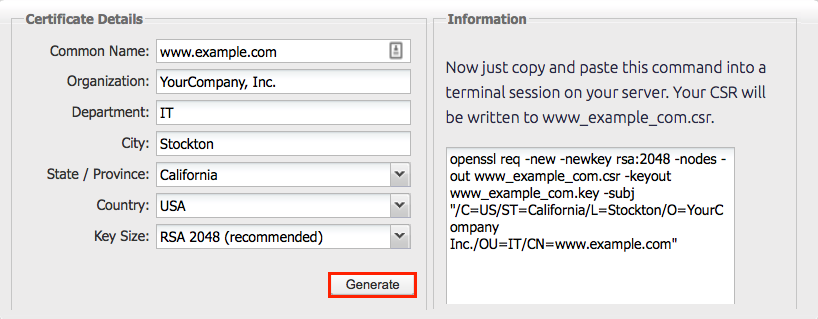
Here is a general example for the CSR information prompt, when we run the OpenSSL command to generate the CSR.
We can also provide the information by non-interactive answers for the CSR information generation, we can do this by adding the –subj option to any OpenSSL commands that we try to generate or run.
Below is an example for the –subj option where we can provide the information of the organization where we want to use this CSR.
In this section, we will cover about OpenSSL commands which are related to generating the CSR. This CSR can be used to request an SSL certificate from a certificate authority.
If we want to use HTTPS (HTTP over TLS) to secure the Apache or Nginx web servers (using a Certificate Authority (CA) to issue the SSL certificate). Also, the ‘.CSR’ which we will be generating has to be sent to a CA for requesting the certificate for obtaining CA-signed SSL.
Below is the command to create a 2048-bit private key for ‘domain.key’ and a CSR ‘domain.csr’ from the scratch.
The ‘–newkey rsa:2048’ is the option which we are specifying that the key should be 2048-bit using the RSA algorithm. The ’ –nodes’ option is to specifying that the private key should not be encrypted with a pass phrase. The ‘-new’ option, indicates that a CSR is being generated.
Here we will learn about, how to generate a CSR for which you have the private key.
Below is the command to create a new .csr file based on the private key which we already have.
Here we can generate or renew an existing certificate where we miss the CSR file due to some reason. Here, the CSR will extract the information using the .CRT file which we have.
Below is the example for generating –
Where -x509toreq is specified that we are using the x509 certificate files to make a CSR.
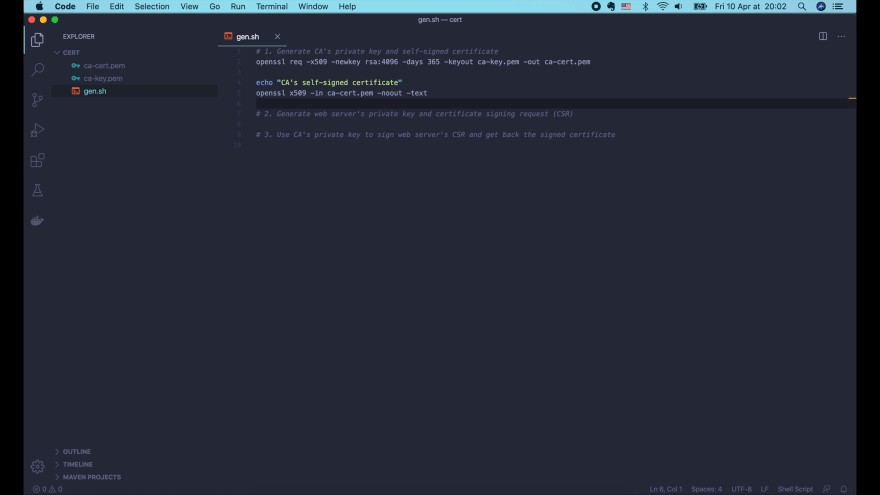
Here we will generate the Certificate to secure the web server where we use the self-signed certificate to use for development and testing purpose.
Here, we generate self-signed certificate using –x509 option, we can generate certificates with a validity of 365 days using –days 365 and a temporary .CSR files are generated using the above information.
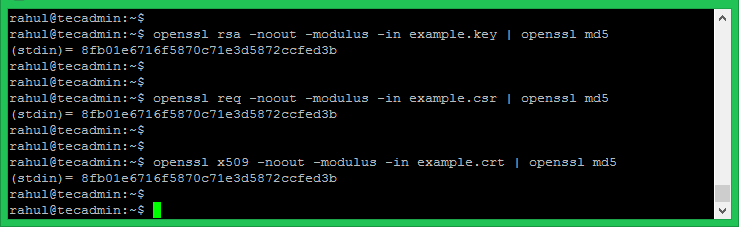
Please note that, CSR files are encoded with .PEM format (which is not readable by the humans). This is required to view a certificate. In this section, we can cover the OpenSSL commands which are encoded with .PEM files.
The below command will be used to view the contents of the .CRT files Ex (domain.crt) in the plain text format.
In this section, will see how to use OpenSSL commands that are specific to creating and verifying the private keys.
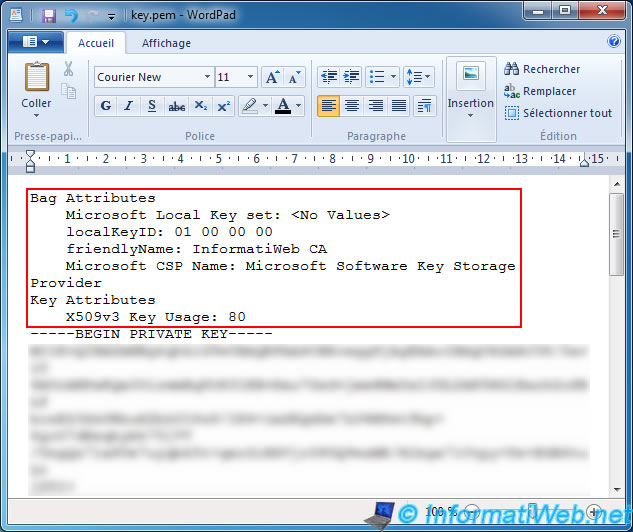
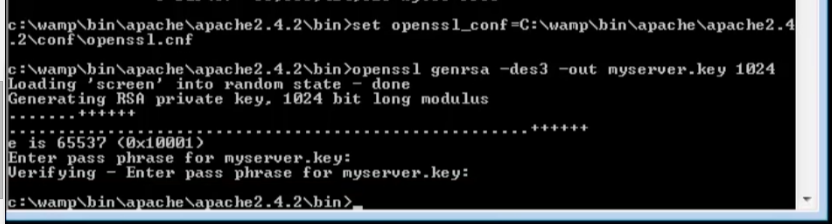
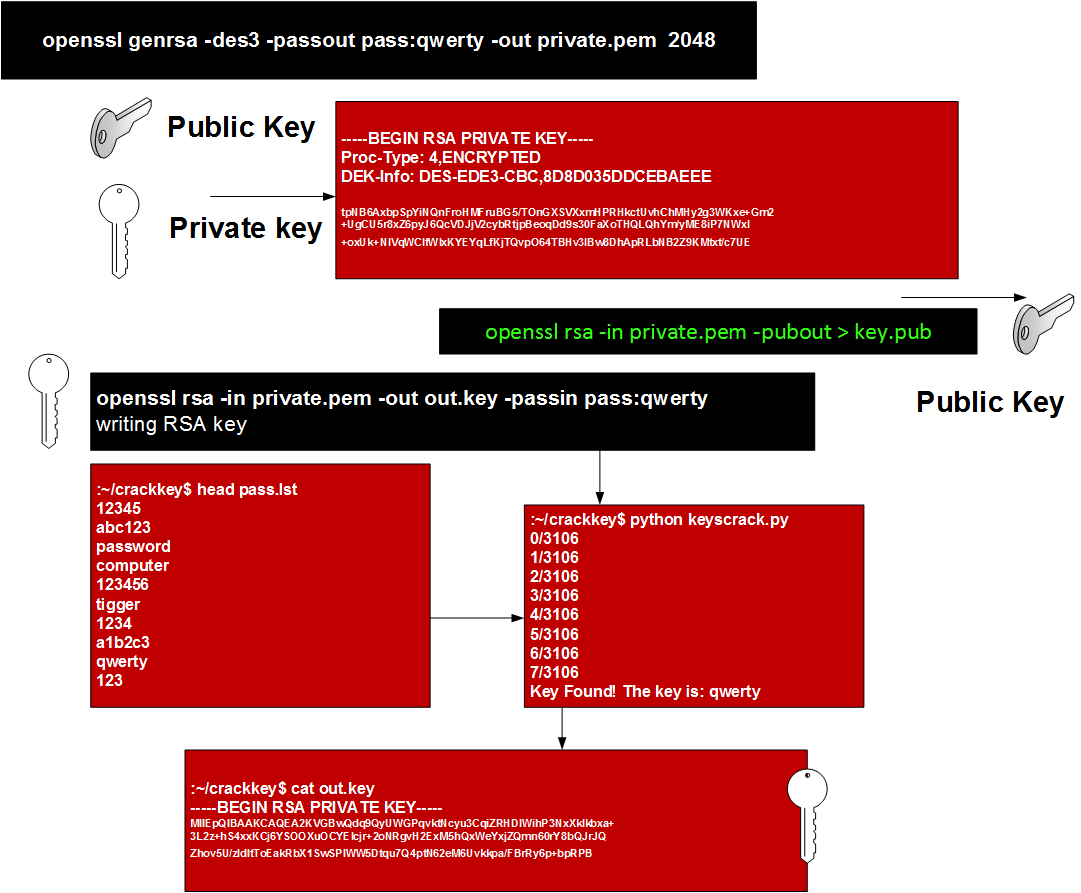
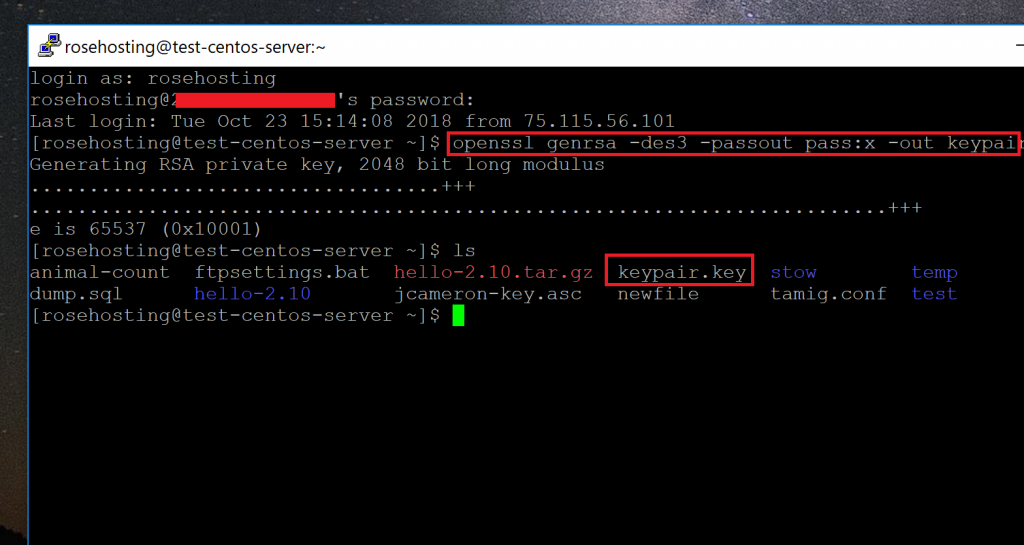
Below is the command to create a password-protected and, 2048-bit encrypted private key file (ex. domain.key) –
Enter a password when prompted to complete the process.
Below is the command to check that a private key which we have generated (ex: domain.key) is a valid key or not
If the private key is encrypted, you will be prompted to enter the pass phrase. Upon the successful entry, the unencrypted key will be the output on the terminal.
In this article, we have learnt some commands and usage of OpenSSL commands which deals with SSL certificates where the OpenSSL has lots of features. We will learn more features and usage in the future. I hope this article will help us to understand some basic features of the OpenSSL.
© Copyright 2021. All Rights Reserved.
Instantly share code, notes, and snippets.
How to generate & use private keys using the OpenSSL command line tool
These commands generate and use private keys in unencrypted binary (not Base64 “PEM”) PKCS#8 format. The PKCS#8 format is used here because it is the most interoperable format when dealing with software that isn't based on OpenSSL.
OpenSSL has a variety of commands that can be used to operate on private key files, some of which are specific to RSA (e.g. openssl rsa and openssl genrsa) or which have other limitations. Here we always use openssl pkey, openssl genpkey, and openssl pkcs8, regardless of the type of key.
The first section describes how to generate private keys. The second and third sections describe how to extract the public key from the generated private key. The last section describes how to inspect a private key's metadata.
Ed25519 isn't listed here because OpenSSL's command line utilities do not support Ed25519 keys yet.
The key will use the named curve form, i.e. the only correct form, which unfortunately isn't the default form in all versions of OpenSSL.
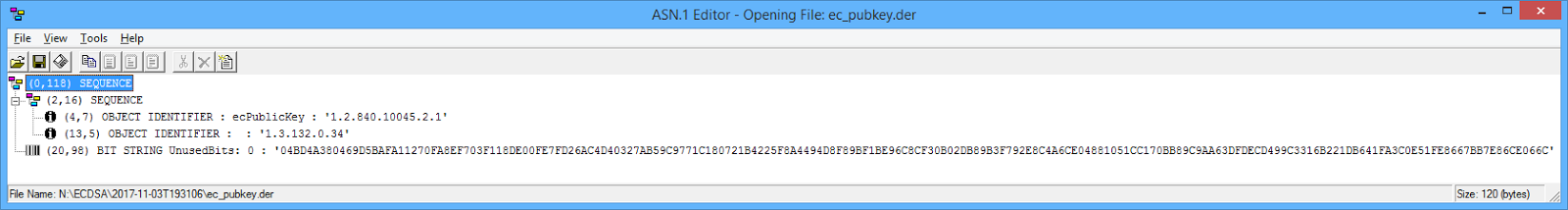
The algorithm identifier will be id-ecPublicKey (1.2.840.10045.2.1), which is what software for signing and verifying ECDSA signatures expects.
openssl genpkey -algorithm EC \
-pkeyopt ec_paramgen_curve:P-256 \
-pkeyopt ec_param_enc:named_curve | \
openssl pkcs8 -topk8 -nocrypt -outform der > p256-private-key.p8
openssl genpkey -algorithm EC \
-pkeyopt ec_paramgen_curve:P-384 \
-pkeyopt ec_param_enc:named_curve |
openssl pkcs8 -topk8 -nocrypt -outform der > p384-private-key.p8
The key will have two primes (i.e. it will not be a multi-prime key), and public exponent 65537, which are by far the most interoperable parameters. Unless you have special requirements, generate a 2048-bit key.
The key's algorithm identifier is rsaEncryption (1.2.840.113549.1.1.1), which is the most interoperable form. Almost all software will accept keys marked as such for use in RSA encryption and for RSA PKCS#1 1.5 signatures and RSA-PSS signatures.
openssl genpkey -algorithm RSA \
-pkeyopt rsa_keygen_bits:2048 \
-pkeyopt rsa_keygen_pubexp:65537 | \
openssl pkcs8 -topk8 -nocrypt -outform der > rsa-2048-private-key.p8
openssl genpkey -algorithm RSA \
-pkeyopt rsa_keygen_bits:3072 \
-pkeyopt rsa_keygen_pubexp:65537 | \
openssl pkcs8 -topk8 -nocrypt -outform der > rsa-3072-private-key.p8
PKCS#8 files are self-describing, and PKCS#8 private key files contain the public key, so the public key can be extracted from the private key file:
openssl pkey -pubout -inform der -outform der \
-in \
-out
openssl pkey -pubout -inform der -outform der \
-in p256-private-key.p8 \
-out p256-public-key.spki
openssl pkey -pubout -inform der -outform der \
-in p384-private-key.p8 \
-out p384-public-key.spki
openssl pkey -pubout -inform der -outform der \
-in rsa-2048-private-key.p8 \
-out rsa-2048-public-key.spki
openssl pkey -pubout -inform der -outform der \
-in rsa-3072-private-key.p8 \
-out rsa-3072-public-key.spki
Above, we said we would only need openssl pkey, openssl genpkey, and openssl pkcs8, but that's only true if you don't need to output the legacy form of the public key. If you need the legacy form in binary (“DER”) format then can do the conversion following this example:
openssl pkey -pubout -inform der -outform der \
-in rsa-2048-private-key.p8 | \
openssl rsa -pubin -RSAPublicKey_out -inform DER -outform DER \
-out rsa-2048-public-key-legacy-form.der
The Base64 (“PEM”) form can be output following this example:
openssl pkey -pubout -inform der -outform der \
-in rsa-2048-private-key.p8 | \
openssl rsa -pubin -RSAPublicKey_out -inform DER -outform PEM \
-out rsa-2048-public-key-legacy-form.pem
PKCS#8 files are self-describing, and PKCS#8 private key files contain the public key, so a single command can output all the public properties for any private key.
WARNING: By default OpenSSL's command line tool will output the value of the private key, even when you ask for it to output the public metadata; the -noout parameter suppresses this.
openssl pkey -noout -text_pub -inform der -in
For example, if you generated p256-private-key.p8 as described in the in the section on generating private keys, then given the command:
openssl pkey -noout -text_pub -inform der -in p256-private-key.p8
you'd see output like this (with a different value for pub, the public key):
As another example, if you generated rsa-2048-private-key.p8 as described in the section on generating private keys, then this:
openssl pkey -noout -text_pub -inform der -in rsa-2048-private-key.p8
would output something like this (with a different modulus value):
I've started using this for ed25519 keys:
That will generate a private key in a format that only OpenSSH can process, not the standard format, IIUC.
Is there another test, method or tool I can use to see metadata?
Is ed25519 too new? Or superseded?
Can it be converted into the expected der/pem?
I'm reading up on DJB's published work, got lost on attack vectors, trying to find a head-to-head comparison against other EC schemes....
Is there another test, method or tool I can use to see metadata?
Is ed25519 too new? Or superseded?
It looks like it will be a while before OpenSSL adds Ed25519 support: openssl/openssl#487
For now I recommend trying the tool I made:
cargo install kt && kt generate ed25519 --out=ed25519.pk8
Awesome @briansmith - I'll check it out.
Thanks a lot for this guide, it's very helpful. Can you tell me if there is any difference between the ecparam and the genpkey command line tools? They seem to do the same thing. - Thanks!
Is it possible to generate a PKCS#8-Package with (multiple) "OneAsymmetricKey"-Elements in openssl? If yes, how?
Hi briansmith, I have a public key (x, y) from ECDSA, both x and y are bigint string, how can I convert it into a ring::signature::UnparsedPublicKey ?
Sign up for free to join this conversation on GitHub. Already have an account? Sign in to comment
Kick Up Ass
It S A Mommy Thing 3
Creampie Retro Vintage
Old Man And Teen Porno Foto
Shemale Ass Balls
How to use openssl for generating ssl certificates priva…
How to generate & use private keys using the OpenSSL ...
How To Generate Private Key From SSL Certificate? | SSL
Generate public key and private key with OpenSSL in ...
Generate OpenSSL RSA Key Pair from the Command Line
Openssl Generate Private Public Key Pair
OpenSSL Tutorial: How Do SSL Certificates, Private Keys ...
How to Generate Self-Signed SSL Certificates using OpenSSL
Openssl Generate Private Key

















/image%252F6201714%252F20201224%252Fob_9dd8b8_openssl-generate-ec-private-key.png)