Openssh Private Key

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Applies to Windows Server 2019, Windows 10: Windows Server 2022,
Most authentication in Windows environments is done with a username-password pair, which works well for systems that share a common domain. When working across domains, such as between on-premises and cloud-hosted systems, it becomes vulnerable to brute force intrusions.
By comparison, Linux environments commonly use public-key/private-key pairs to drive authentication which doesn't require the use of guessable passwords. OpenSSH includes tools to help support this, specifically:
This document provides an overview of how to use these tools on Windows to begin using key-based authentication with SSH. If you are unfamiliar with SSH key management, we strongly recommend you review NIST document IR 7966 titled "Security of Interactive and Automated Access Management Using Secure Shell (SSH)".
Key pairs refer to the public and private key files that are used by certain authentication protocols.
SSH public key authentication uses asymmetric cryptographic algorithms to generate two key files – one "private" and the other "public". The private key files are the equivalent of a password, and should stay protected under all circumstances. If someone acquires your private key, they can log in as you to any SSH server you have access to. The public key is what is placed on the SSH server, and may be shared without compromising the private key.
When using key authentication with an SSH server, the SSH server and client compare the public key for a user name provided against the private key. If the server-side public key cannot be validated against the client-side private key, authentication fails.
Multi-factor authentication may be implemented with key pairs by entering a passphrase when the key pair is generated (see user key generation below). During authentication the user is prompted for the passphrase, which is used along with the presence of the private key on the SSH client to authenticate the user.
Public keys have specific ACL requirements that, on Windows, equate to only allowing access to administrators and System. On first use of sshd, the key pair for the host will be automatically generated.
You need to have OpenSSH Server installed first. Please see Getting started with OpenSSH.
By default the sshd service is set to start manually. To start it each time the server is rebooted, run the following commands from an elevated PowerShell prompt on your server:
Since there is no user associated with the sshd service, the host keys are stored under C:\ProgramData\ssh.
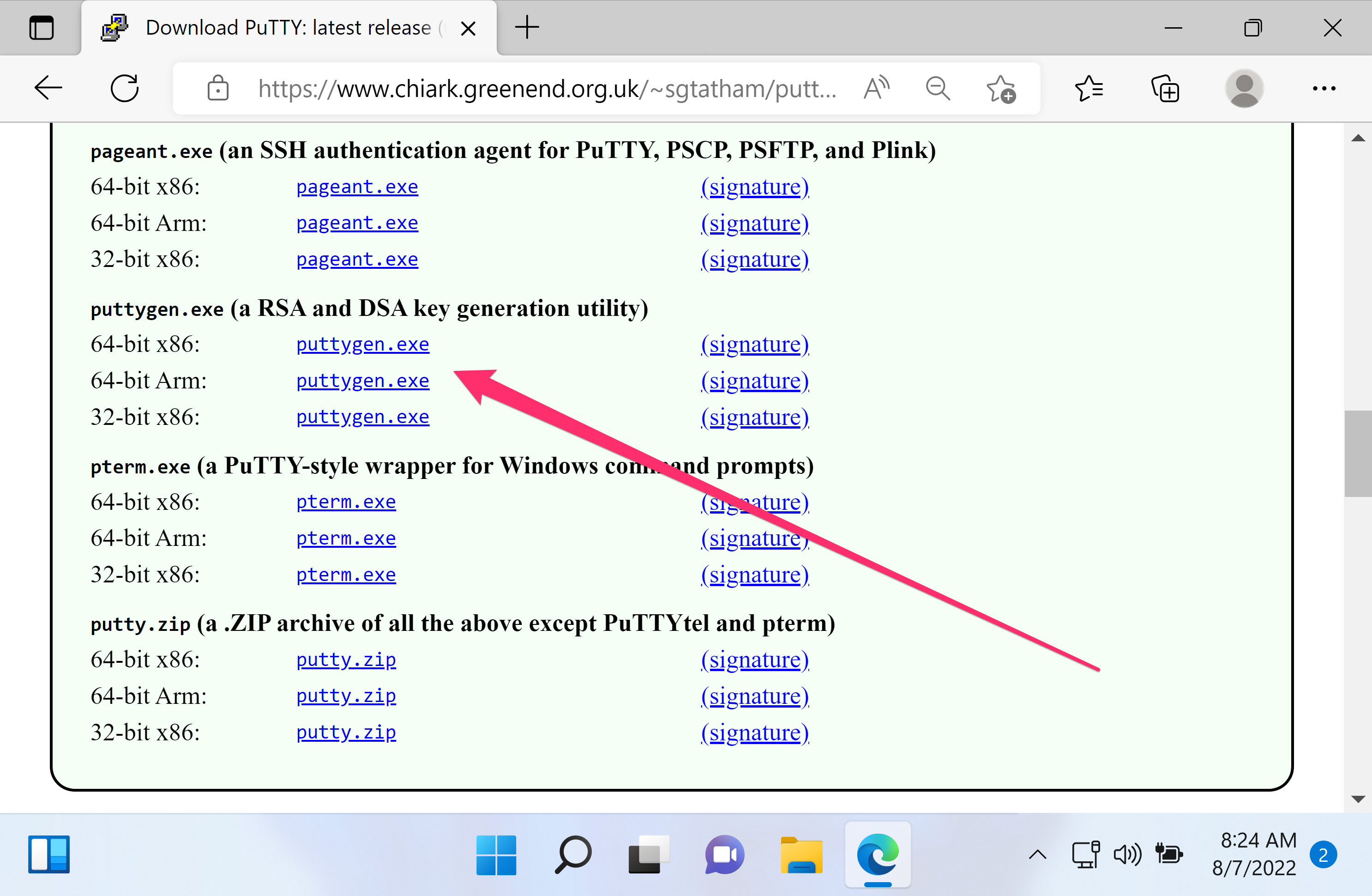
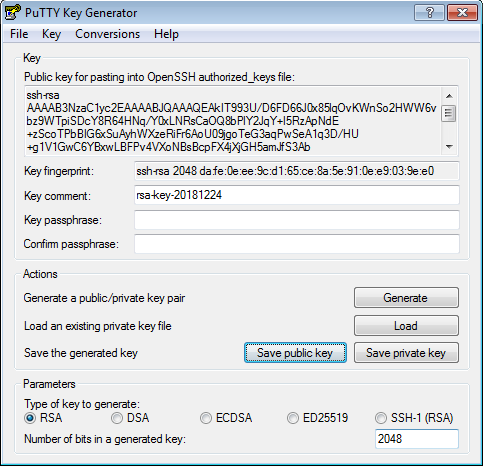
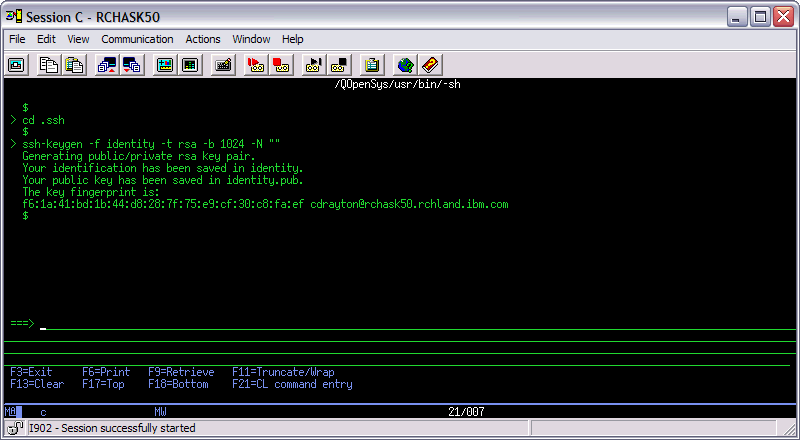
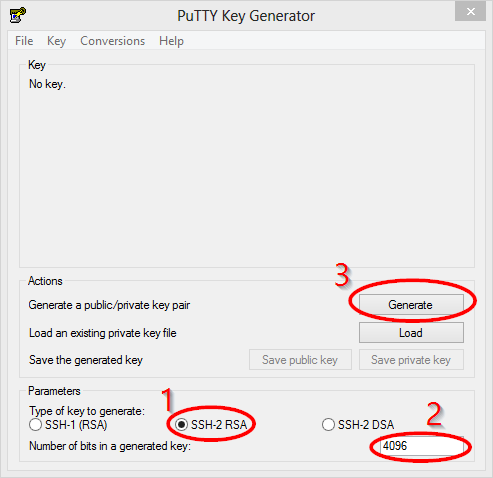
To use key-based authentication, you first need to generate public/private key pairs for your client. ssh-keygen.exe is used to generate key files and the algorithms DSA, RSA, ECDSA, or Ed25519 can be specified. If no algorithm is specified, RSA is used. A strong algorithm and key length should be used, such as Ed25519 in this example.
To generate key files using the Ed25519 algorithm, run the following from a PowerShell or cmd prompt on your client:
This should display the following (where "username" is replaced by your user name):
You can press Enter to accept the default, or specify a path and/or filename where you would like your keys to be generated. At this point, you'll be prompted to use a passphrase to encrypt your private key files. This can be empty but is not recommended. The passphrase works with the key file to provide two-factor authentication. For this example, we are leaving the passphrase empty.
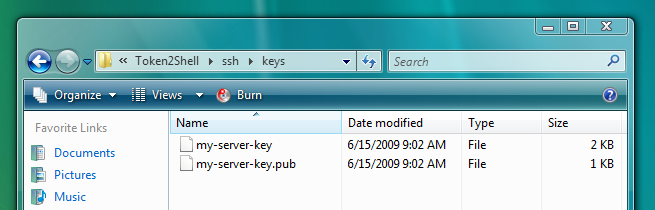
Now you have a public/private Ed25519 key pair in the location specified. The .pub files are public keys, and files without an extension are private keys:
Remember that private key files are the equivalent of a password should be protected the same way you protect your password. To help with that, use ssh-agent to securely store the private keys within a Windows security context, associated with your Windows login. To do that, start the ssh-agent service as Administrator and use ssh-add to store the private key.
After completing these steps, whenever a private key is needed for authentication from this client, ssh-agent will automatically retrieve the local private key and pass it to your SSH client.
It is strongly recommended that you back up your private key to a secure location, then delete it from the local system, after adding it to ssh-agent. The private key cannot be retrieved from the agent providing a strong algorithm has been used, such as Ed25519 in this example. If you lose access to the private key, you will have to create a new key pair and update the public key on all systems you interact with.
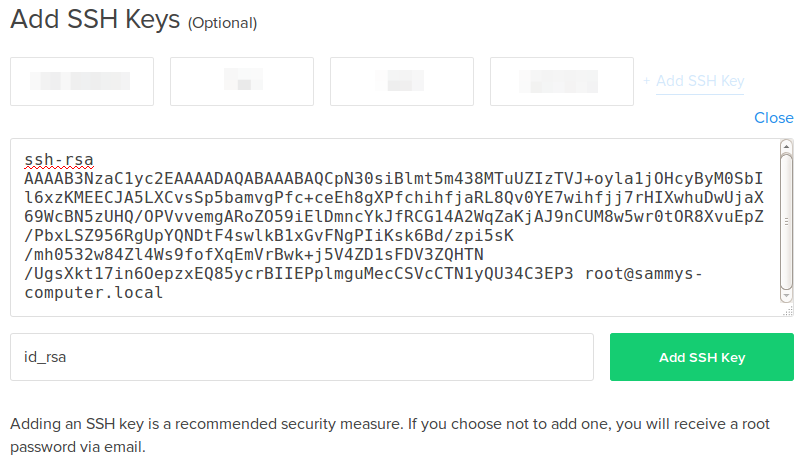
To use the user key that was created above, the contents of your public key (~\.ssh\id_ed25519.pub) needs to be placed on the server into a text file, the name and location of which depends on whether the user account is a member of the local administrators group or a standard user account.
The contents of your public key (~\.ssh\id_ed25519.pub) needs to be placed on the server into a text file called authorized_keys in C:\Users\username\.ssh\. The OpenSSH client includes scp, which is a secure file-transfer utility, to help with this.
The example below copies the public key to the server (where "username" is replaced by your user name). You will need to use the password for the user account for the server initially.
The contents of your public key (~\.ssh\id_ed25519.pub) needs to be placed on the server into a text file called administrators_authorized_keys in C:\ProgramData\ssh\. The OpenSSH client includes scp, which is a secure file-transfer utility, to help with this. The ACL on this file needs to be configured to only allow access to administrators and System.
The example below copies the public key to the server and configures the ACL (where "username" is replaced by your user name). You will need to use the password for the user account for the server initially.
This example shows the steps for creating the administrators_authorized_keys file. If it is run multiple times, it will overwrite this file each time. To add the public key for multiple administrative users, you need to append this file with each public key.
These steps complete the configuration required to use key-based authentication with OpenSSH on Windows. After this, the user can connect to the sshd host from any client that has the private key.
Feedback will be sent to Microsoft: By pressing the submit button, your feedback will be used to improve Microsoft products and services. Privacy policy.
Configuration information about OpenSSH Server for Windows 10 1809 and Windows Server 2019.
Overview about the OpenSSH tools used by administrators of Linux and other non-Windows for cross-platform management of remote systems.
Installing OpenSSH Client and Server for Windows.
In this tutorial, learn how to set up an SSH connection in Windows Terminal.
Learn how to install the Linux Subsystem on Windows Server. WSL is available for installation on Windows Server 2019 (version 1709) and later.
Instructions for how to manually download Windows Subsystem for Linux distributions.
Feedback will be sent to Microsoft: By pressing the submit button, your feedback will be used to improve Microsoft products and services. Privacy policy.
Sign up or log in to view your list.
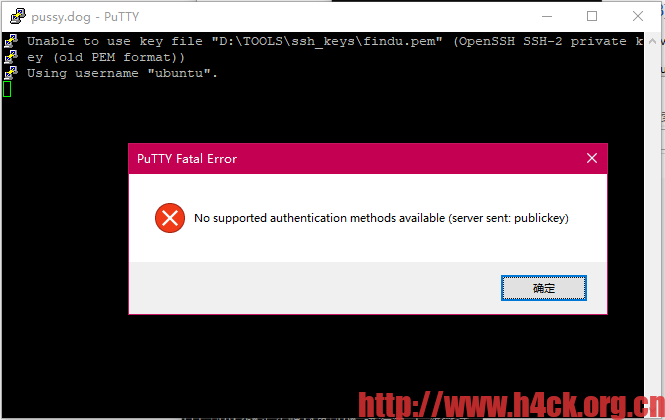
I have two servers. Both servers are in CentOS 5.6. I want to SSH from Server 1 to Server 2 using a private key I have (OpenSSH SSH-2 Private Key).
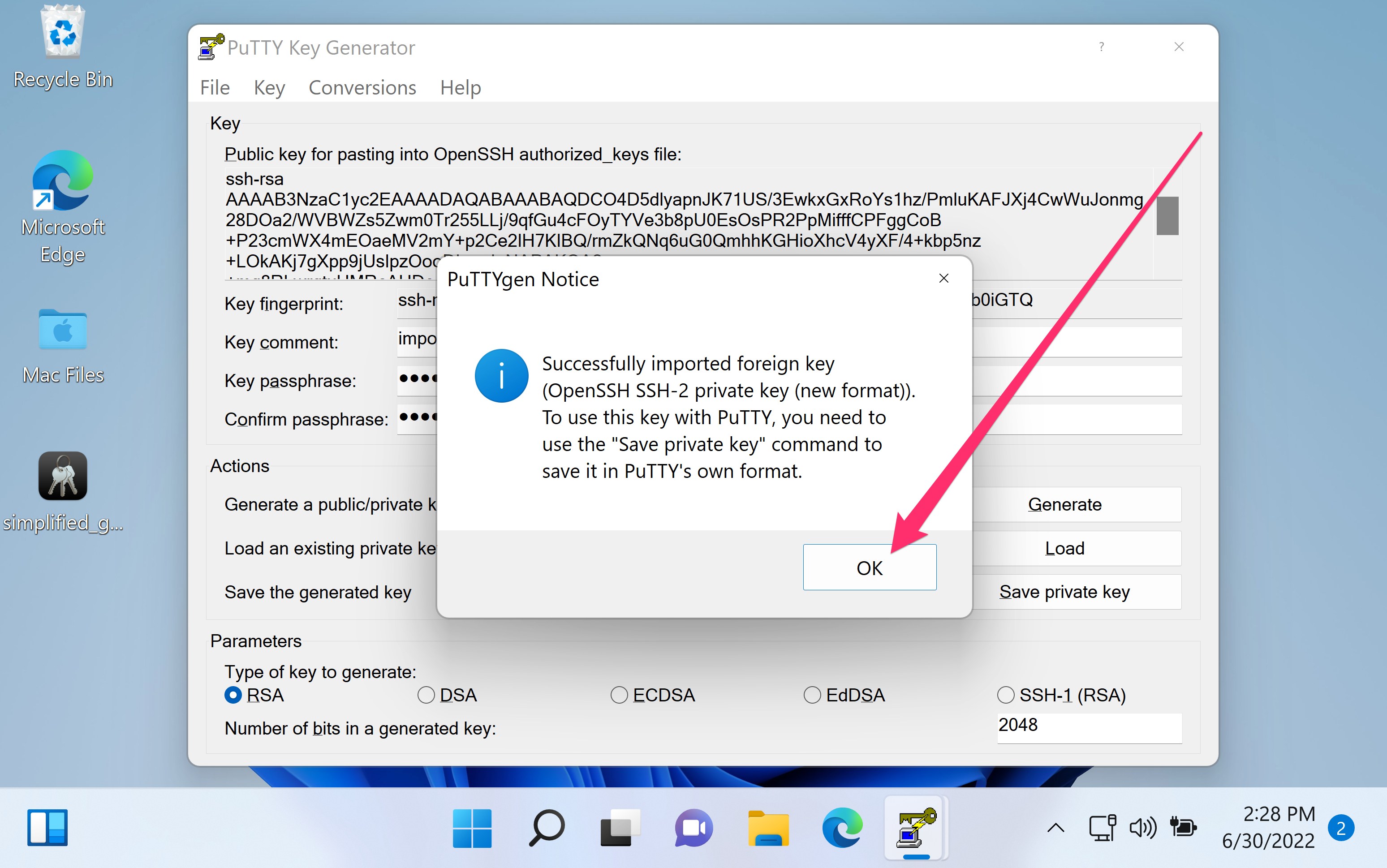
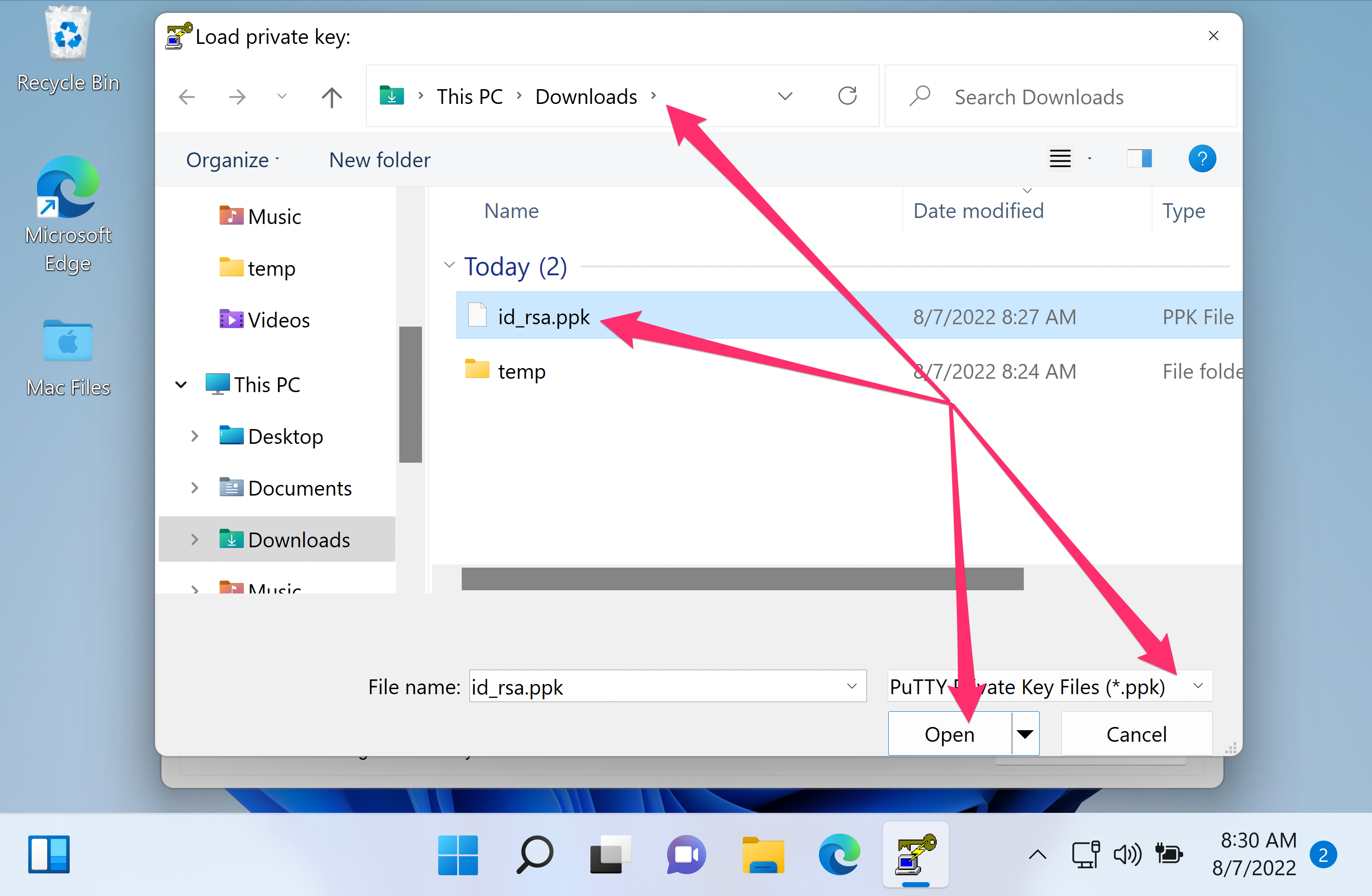
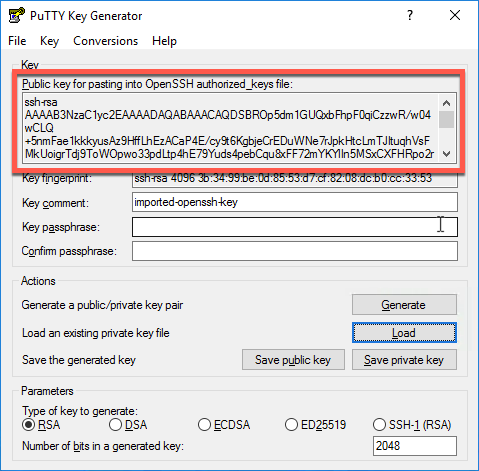
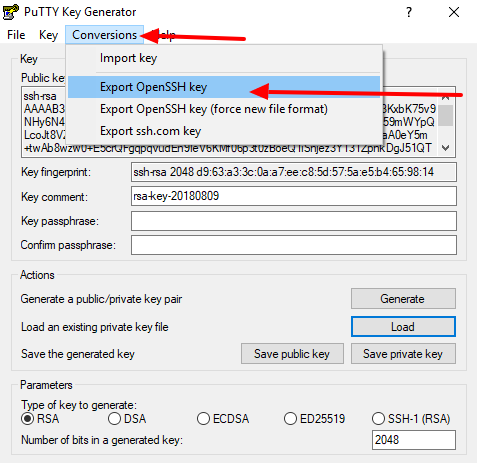
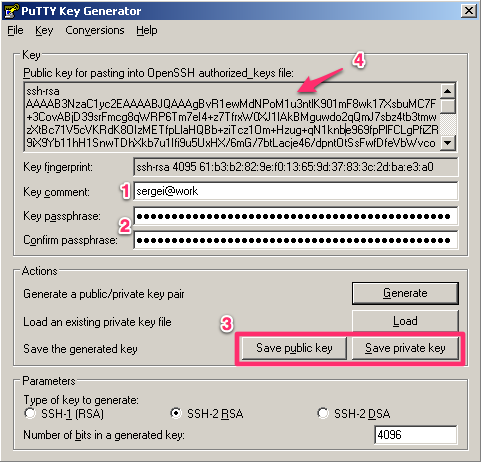
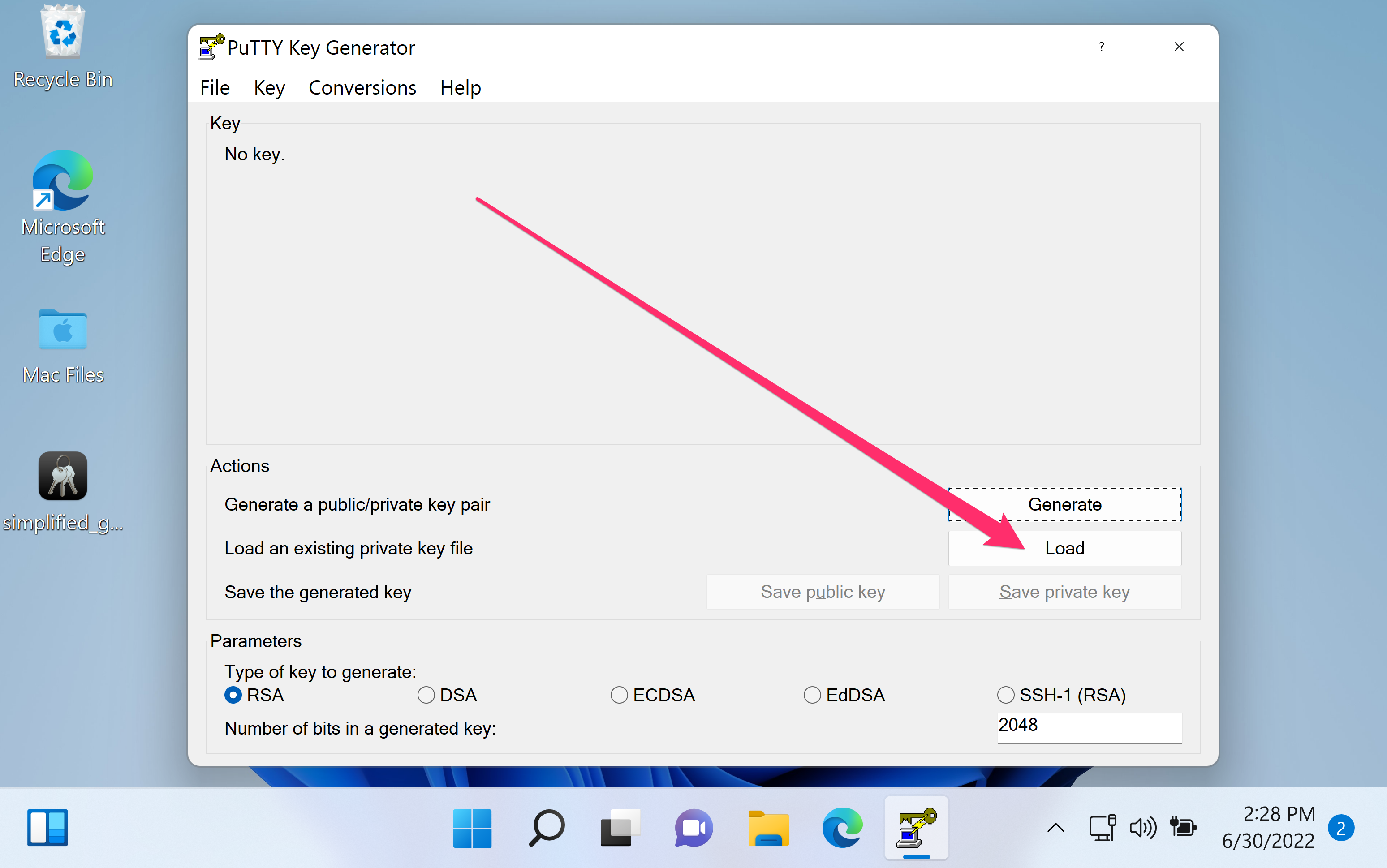
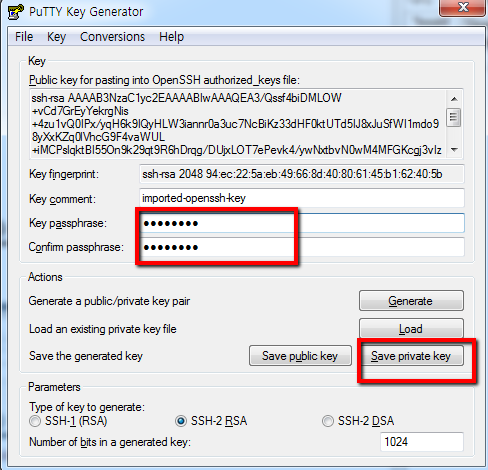
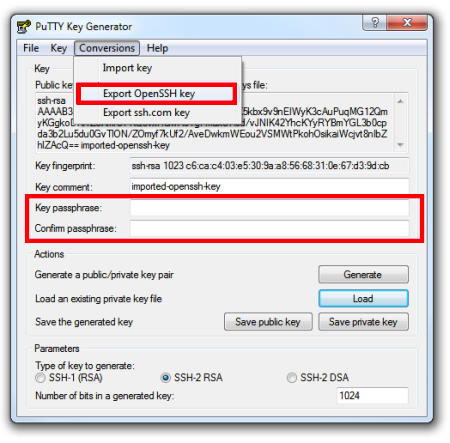
I don't know how to do it over unix. But what I did on windows using Putty was to feed my OpenSSH private key to putty-gen and generate a private key in PPK format.
However, I would be creating a bash script from server 1 that will execute some commands on server 2 via SSH.
How do I SSH to Server 2 using my private key file from Server 1?
Aivan Monceller
Aivan Monceller 1,243●11 gold badge●1010 silver badges●1010 bronze badges
On many Linux and Unix systems, this can be done using ssh-copy-id user@machine – Paul Tomblin Oct 25 '11 at 20:22
You need your SSH public key and you will need your ssh private key. Keys can be generated with ssh-keygen. The private key must be kept on Server 1 and the public key must be stored on Server 2.
This is completly described in the manpage of openssh, so I will quote a lot of it. You should read the section 'Authentication'. Also the openSSH manual should be really helpful: http://www.openssh.org/manual.html
Please be careful with ssh because this affects the security of your server.
This means you can store your private key in your home directory in .ssh. Another possibility is to tell ssh via the -i parameter switch to use a special identity file. Also from man ssh:
This is for the private key. Now you need to introduce your public key on Server 2. Again a quote from man ssh:
The easiest way to achive that is to copy the file to Server 2 and append it to the authorized_keys file:
Authorisation via public key must be allowed for the ssh daemon, see man ssh_config. Usually this can be done by adding the following statement to the config file:
echox
echox 16.2k●66 gold badges●4646 silver badges●5454 bronze badges
Kusalananda♦
250k●3131 gold badges●472472 silver badges●754754 bronze badges
Hi thank you for the effort but I only need this. ssh -i keyfile thanks! – Aivan Monceller Oct 25 '11 at 20:59
After generating the key, the easiest and recommended way to install it on the server is with ssh-copy-id: ssh-copy-id -i ~/.ssh/foo.id_rsa remote.example.com. – Gilles 'SO- stop being evil' Oct 26 '11 at 7:09
It's interesting how everyone forgets to mention that u need to run ssh-add after creating a key on the computer you are connecting from. that is what causes a headache to most people. – Luka Sep 19 '17 at 21:49
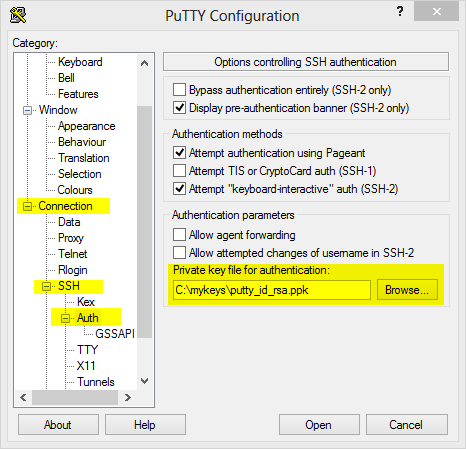
IMPORTANT NOTE: The client can have many private keys and select based on an arbitrary name in their private ~/.ssh/config file where Host= gives the arbitrary name, HostName gives either a name or IP address, Port= the target port, User is destination username, and ItentityFile= points to the private key file. This feature set is often overlooked and is THE solution to many configuration issues, such as having multiple key-pairs that otherwise collide in name-space. – Richard T Aug 25 '18 at 22:46
When I try and connect with SSH using $ ssh -i ~/.ssh/id_rsa myuser@ssh.myhost.com I get the error myuser@ssh.myhost.com: Permission denied (publickey). I have the key created, added locally using ssh-add, and added as an authorized key on the remote server. – Aaron Franke Sep 22 '19 at 20:08
I used ssh with -i option to add your key here.
If you want to pass arg1,arg2 with .sh file, just pass it after .sh file and use a use space to separate it.
ssh -i home/avr/new.pem ar@231.221.54.8 "/var/www/beta/betatolive.sh mmin 30"
Avinash Raut
Avinash Raut 413●55 silver badges●55 bronze badges
Jeff Schaller♦
60.1k●3232 gold badges●9494 silver badges●210210 bronze badges
Don't forget to set the right permissions: chmod 600 home/avr/new.pem – Brian Cannard Jun 22 '17 at 3:34
The first thing you’ll need to do is make sure you’ve run the keygen command to generate the keys:
Then use this command to push the key to the remote server, modifying it to match your server name.
Anubhav Singh
Anubhav Singh 319●22 silver badges●22 bronze badges
Mat
47.4k●1010 gold badges●145145 silver badges●138138 bronze badges
let's call ssh-copy-id user@hostname instead – andrej Nov 12 '18 at 17:14
@andrej Note that ssh-copy-id is not part of the official OpenSSH distribution, so it may not be available on all Unices (it seems to be a Linux thing though). – Kusalananda♦ Dec 16 '19 at 8:18
@Kusalananda good point, thanks. However, this issue requirements are for two CentOS 5.6 machines so they have ssh-copy-id for sure. – andrej Dec 16 '19 at 12:28
Append the public key (id_[rd]sa.pub) for your source machine (where you're sshing from) to the ~/.ssh/authorized_keys file of the destination server for the username you want to ssh into. If you've lost the public key, you'll want to create a new one with ssh-keygen. Using the default arguments for that should be ok for most purposes. If you need more detailed instructions, there are thousands of tutorials you can google.
Kevin
Kevin 36k●1414 gold badges●8282 silver badges●111111 bronze badges
ssh-copy-id -- use locally available keys to authorise logins on a remote machine
Use ssh-copy-id on Server 1, assuming you have the key pair (generated with ssh-keygen):
Now you should be able to ssh into Server 2 with ssh using the private key
Indeed, if you check cat ~/.ssh/authorized_keys on Server 2, you'll see the public key is appended for you.
Sida Zhou
Sida Zhou 203●22 silver badges●55 bronze badges
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Let Me See Your Ass
Japanese Women Ass
Erotic Lesbi Photo
Squirting Webcam Lesbian
Bring Mom In Free
OpenSSH key management for Windows | Microsoft Docs
The OpenSSH Private Key Format - coolaj86
Windows 10 OpenSSH – Creating a new private/public key ...
OpenSSH ssh-agent Shielded Private Key Extraction (x86_64 ...
ssh - How to name openssh public and private key pairs ...
How to Generate SSH Key in Windows 10 {OpenSSH or PuTTY}
openssl - ssh-keygen does not create RSA private key ...
Openssh Private Key