Online Penetration Test

🛑 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Online Penetration Test
=>> Contact us to suggest a listing here.
=>> Contact us to suggest a listing here.
Helping our community since 2006!
Most popular portal for Software professionals with 100 million+ visits and 300,000+ followers! You will absolutely love our tutorials on QA Testing, Development, Software Tools and Services Reviews and more!
List and Comparison of the Top Penetration Testing Tools (Security Testing Tools) used by the professionals. Research Done for you!
Wouldn’t it be fun if a company hired you to hack its website/network/Server? Well, yeah!
Penetration Testing, commonly known as Pen-Testing, is on a roll in the testing circle nowadays. The reason is not too hard to guess – with the change in the way computer systems are used and built, security takes center stage.
Even though companies realize that they can’t make every system 100% secure, they are extremely interested to know exactly what kind of security issues they are dealing with.
That’s where Pen-testing comes handy with its use of ethical hacking techniques.
For more details about Penetration Testing, you can check these guides:
It is a method of testing in which the areas of weakness in the software systems in terms of security are put to test to determine if a “weak-point” is indeed one that can be broken into or not.
Performed for : Websites/Servers/Networks
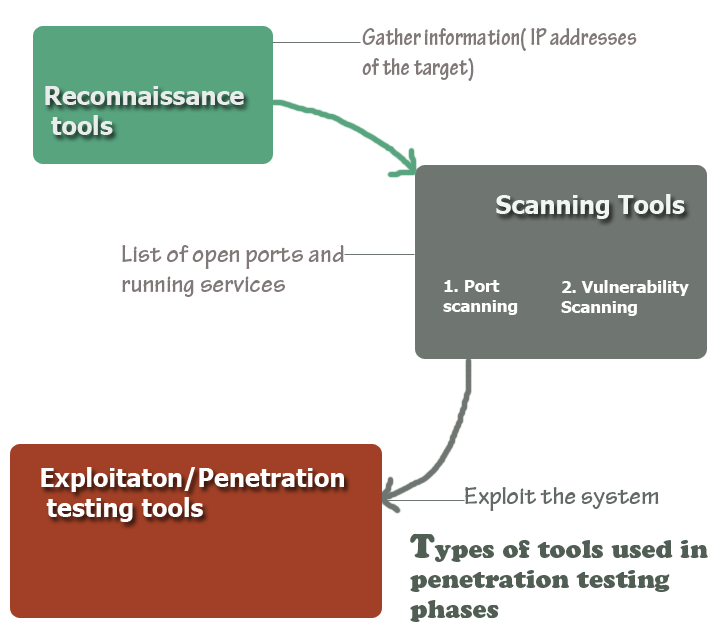
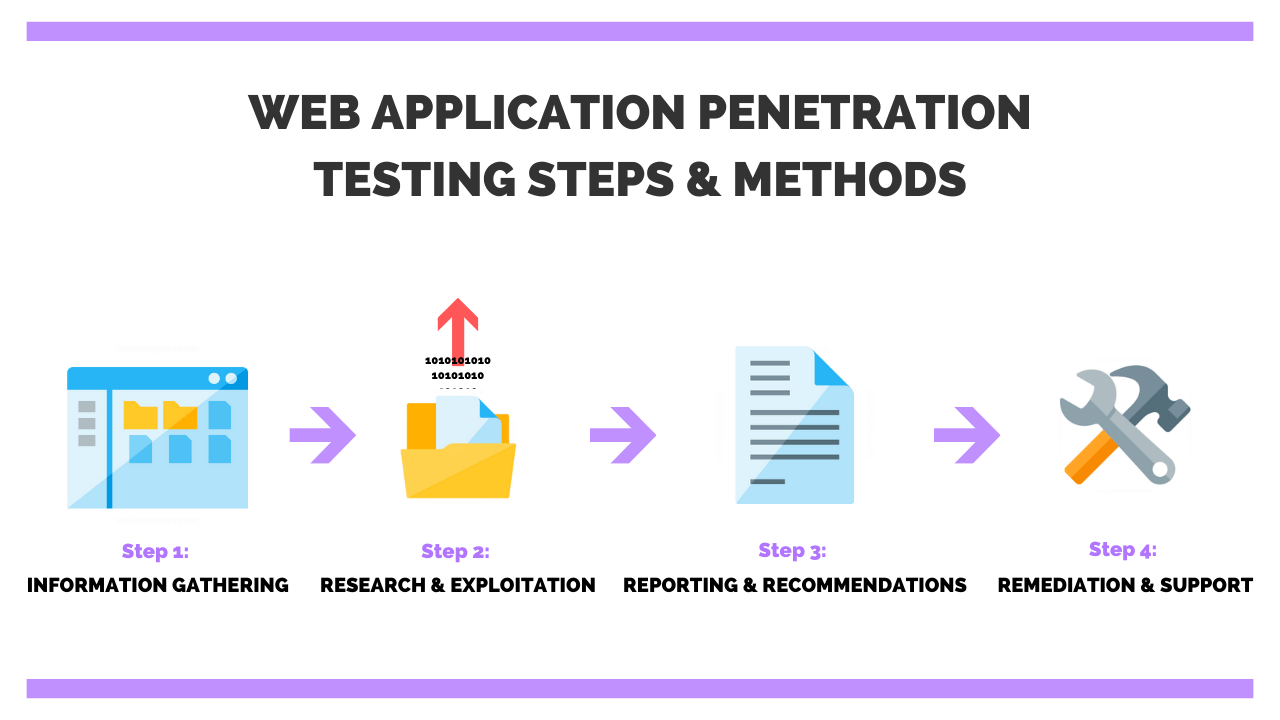
Step #1. It starts with a list of vulnerabilities/potential problem areas that could cause a security breach for the system.
Step #2. If possible, this list of items is ranked in order of priority/criticality
Step #3. Device penetration tests that would work (attack your system) from both within the network and outside (externally) are done to determine if you can access data/network/server/website unauthorized.
Step #4. If unauthorized access is possible, then the system has to be corrected and a series of steps need to be re-run until the problem area is fixed.
Testers/ Network specialists/ Security Consultants perform Pen-Testing.
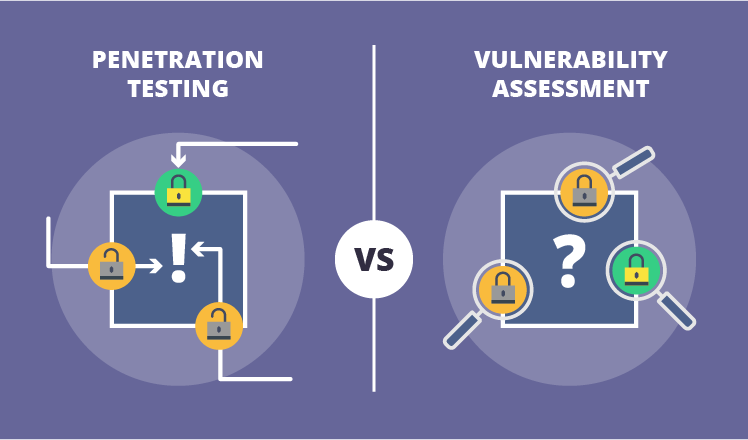
Note: It is important to note that Pen-Testing is not the same as Vulnerability Testing. The intention of Vulnerability Testing is just to identify the potential problems, whereas Pen-Testing is to attack those problems.
The good news is, you do not have to start the process by yourself – you have a number of tools already available in the market. Wondering, why tools?
Before we look into the details of the tools, what they do, where you can get them, etc. , I would like to point out that the tools you use for Pen-Testing can be classified into two kinds – In simple words, they are scanners and attackers.
This is because; by definition, Pen-Testing is exploiting the weak spots. So there are some software/tools that will show you the weak spots, & some that show, and attack. Literally speaking, the ‘show-ers’ are not Pen-Testing tools but they are inevitable for its success.
A comprehensive list of the best Penetration or Security Testing tools used by Penetration testers:
List of the best Security Pentesting Tools that every Security Tester should know about:
Netsparker is a dead accurate automated scanner that will identify vulnerabilities such as SQL Injection and Cross-site Scripting in web applications and web APIs. Netsparker uniquely verifies the identified vulnerabilities, proving they are real and not false positives.
Therefore, you do not have to waste hours manually verifying the identified vulnerabilities once a scan is finished.
It is available as a Windows software and an online service.
Acunetix is a fully automated web vulnerability scanner that detects and reports on over 4500 web application vulnerabilities including all variants of SQL Injection and XSS.
It complements the role of a penetration tester by automating tasks that can take hours to test manually, delivering accurate results with no false positives at top speed.
Acunetix fully supports HTML5, JavaScript and Single-page applications as well as CMS systems. It includes advanced manual tools for penetration testers and integrates with popular Issue Trackers and WAFs.
Core impact: With over 20 years in the market, Core Impact claims the largest range of exploits available in the market, they also let you run the free Metasploit exploits within their framework if they are missing one. They automate a lot of processes with wizards, have a complete audit trail including PowerShell commands, and can re-test a client simply by re-playing the audit trail.
Core write their own ‘Commercial Grade’ exploits to guarantee quality and offer technical support around both those exploits and their platform.
They claim to be the market leader and used to have a price tag to match. More recently the price has come down and they have models appropriate for both corporate and security consultancies.
Hackerone is one of the top security testing platforms. It can find and fix critical vulnerabilities. More and more Fortune 500 and Forbes Global 1000 companies choose HackerOne as it provides fast on-demand delivery. You can get started in just 7 days and get results in 4 weeks.
With this hacker-powered security platform, you will not have to wait for the report to find the vulnerabilities, it will alert you when the vulnerability will be found. It will let you communicate directly with your team by using tools like Slack. It provides integration with products like GitHub and Jira and you will be able to collaborate with dev teams.
With HackerOne, you will be able to achieve compliance standards like SOC2, ISO, PCI, HITRUST, etc. There will not be any additional cost for retesting.
The partners of HackerOne include the U.S. Department of Defense, Google, CERT Coordination Center, etc. and found over 120,000 vulnerabilities and awarded over $80M in bug bounties.
Intruder is a powerful vulnerability scanner that finds cybersecurity weaknesses in your digital estate, and explains the risks & helps with their remediation before a breach can occur. It is the perfect tool to help automate your penetration testing efforts.
With over 9,000 security checks available, Intruder makes enterprise-grade vulnerability scanning accessible to companies of all sizes. Its security checks include identifying misconfigurations, missing patches, and common web application issues such as SQL injection & cross-site scripting.
Built by experienced security professionals, Intruder takes care of much of the hassle of vulnerability management, and thereby you can focus on what truly matters. It saves you time by prioritizing results based on their context as well as proactively scans your systems for the latest vulnerabilities so that you don’t need to stress about it.
Intruder also integrates with major cloud providers as well as Slack & Jira.
Indusface WAS provides both manual penetration testing bundled with its own automated web application vulnerability scanner that detects and reports vulnerabilities based on OWASP top 10 and also includes a website reputation check of links, malware and defacement checks of the website in every scan.
Every customer who gets a Manual PT done automatically gets an automated scanner and they can use on-demand for the whole year.
The company is headquartered in India with offices in Bengaluru, Vadodara, Mumbai, Delhi, and San Francisco, and their services are used by 1100+ customers across 25+ countries globally.
Product Name: RATA Web Application Vulnerability Scanner
RATA (Reliable Attack Testing Automation) Web Application Vulnerability Scanner is the industry’s first Artificial Intelligence, Cloud and Human Hacker powered automated web vulnerability scanner.
RATA Web is an online vulnerability scanner for websites and requires no security expertise, hardware, or software installation. With just a few clicks you can launch scans for vulnerabilities and get a report on the findings that include recommendations for potential solutions.
This is the most advanced and popular Framework that can be used for pen-testing. It is based on the concept of “exploit,” which is a code that can surpass the security measures and enter a certain system. If entered, it runs a ‘payload’, a code that performs operations on a target machine, thus creating a perfect framework for penetration testing.
It can be used on web applications, networks, servers, etc. It has a command-line and the GUI clickable interface works on Linux, Apple Mac OS X, and Microsoft Windows. Although there might be few free limited trials available, this is a commercial product.
This is basically a network protocol analyzer –popular for providing the minutest details about your network protocols, packet information, decryption, etc. It can be used on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many other systems.
The information that is retrieved via this tool can be viewed through a GUI or the TTY-mode TShark utility. You can get your own free version of the tool from the link below.
W3af is a Web Application Attack and Audit Framework. Some of its features include fast HTTP requests, integration of web and proxy servers into the code, injecting payloads into various kinds of HTTP requests, etc.
It has a command-line interface and works on Linux, Apple Mac OS X, and Microsoft Windows. All versions are free of charge to download.
Kali Linux is an open-source project that is maintained by Offensive Security. A few prime features of Kali Linux include Accessibility, Full customization of Kali ISOs, Live USB with Multiple Persistence Stores, Full Disk Encryption, Running on Android, Disk Encryption on Raspberry Pi 2, etc.
Tools Listings, Metapackages, and version Tracking are some of the Penetration Testing tools present in Kali Linux. For more information and in order to download, visit the below page.
Nessus is also a scanner and needs to be watched out for. It is one of the most robust vulnerability identifier tools available. It specializes in compliance checks, sensitive data searches, IPs scans, website scanning, etc. and aids in finding the “weak-spots”.
It works best in most of the environments. For more information and in order to download, visit the below page.
Burp Suite is also essentially a scanner (with a limited “intruder” tool for attacks), although many security testing specialists swear that pen-testing without this tool is unimaginable. The tool is not free, but very cost-effective.
Take a look at it on the below download page. It mainly works wonders with intercepting proxy, crawling content and functionality, web application scanning, etc. You can use this on Windows, Mac OS X, and Linux environments.
If cracking encrypted passwords or network keys is what you need, then Cain & Abel is the perfect tool for you.
It uses network sniffing, Dictionary, Brute-Force & Cryptanalysis attacks, cache uncovering, and routing protocol analysis methods to achieve this. This is exclusively for Microsoft operating systems.
ZAP is completely free to use, scanner and security vulnerability finder for web applications. ZAP includes Proxy intercepting aspects, a variety of scanners, spiders, etc.
It works best on most platforms. For more information and in order to download, visit the below page.
Another password cracker in line is John the Ripper. This tool works in most environments, although it’s primarily for UNIX systems. It is considered one of the fastest tools in this genre.
Password hash code and strength-checking code are also made available to be integrated into your own software/code which I think is very unique. This tool comes in a pro and free form. Check out their site to obtain the software on this page.
As opposed to a certain application or a server, Retina targets the entire environment at a particular company/firm. It comes as a package called Retina Community.
It is a commercial product and is a sort of a vulnerability management tool more than a Pen-Testing tool. It works on having scheduled assessments and presenting results. Check out more about this package on the page below.
Sqlmap is again a good open-source Pen-Testing tool. This tool is mainly used for detecting and exploiting SQL injection issues in an application and hacking over database servers.
It comes with a command-line interface. Platform: Linux, Apple Mac OS X, and Microsoft Windows are its supported platforms. All versions of this tool are free for download. Check out the page below for details.
Immunity’s CANVAS is a widely used tool that contains more than 400 exploits and multiple payload options. It renders useful for web applications, wireless systems, networks, etc.
It has a command-line and GUI interface, works best on Linux, Apple Mac OS X, and Microsoft Windows. It is not free of charge and more information can be found on the page below.
The Social-Engineer Toolkit (SET) is a unique tool in terms that the attacks are targeted at the human element rather than on the system element. It has features that let you send emails, java applets, etc. containing the attack code. It goes without saying that this tool is to be used very carefully and only for white-hat reasons.
It has a command-line interface, works on Linux, Apple Mac OS X, and Microsoft Windows. It is open source and can be found on the page below.
Sqlninja, as the name indicates, is all about taking over the DB server using SQL injection in any environment. This product by itself claims not to be so stable. Its popularity indicates how robust it is already with the DB related vulnerability exploitation.
It has a command-line interface, works best on Linux, Apple Mac OS X and not on Microsoft Windows. It is open-source and can be found on the page below.
“Network Mapper” though not necessarily a Pen-Testing tool, it is a must-have tool for ethical hackers. This is a very popular hacking tool that predominantly aids in understanding the characteristics of any target network.
The characteristics include host, services, OS, packet filters/firewalls, etc. It works in most environments and is open-sourced.
BeEF stands for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser which means, it takes advantage of the fact that an open web-browser is the window(or crack) into a target system and designs its attacks to go on from this point.
It has a GUI interface, works on Linux, Apple Mac OS X, and Microsoft Windows. It is open-source and can be found on the below page.
Dradis is an open-source framework (a web application) that helps with maintaining the information that can be shared among the participants of a pen-test. The information collected helps to understand what is done and what needs to be done.
It achieves this purpose by means of plugins to read and collect data from network scanning tools like Nmap, w3af, Nessus, Burp Suite, Nikto and much more. It has a GUI interface, works on Linux, Apple Mac OS X, and Microsoft Windows. It is open-source and can be found on the page below.
Probely scan your web applications to find vulnerabilities or security issues and provide guidance on how to fix them, having developers in mind.
Probely not only features a sleek and intuitive interface but also follows an API-First development approach, providing all features through an API. This allows Probely to be integrated into Continuous Integration pipelines in order to Automate Security Testing.
Probely covers OWASP TOP10 and thousands more vulnerabilities. It can also be used to check specific PCI-DSS, ISO27001, HIPAA, and GDPR requirements.
We hope this piques your interest in the Pen-Testing field and provides you with the necessary information to get started. A word of caution: remember to wear your ‘White-hat’ because with great power comes great responsibility- and we don’t want to be the ones to misuse it.
Spyse is a search engine that collects, processes, and provides structured information about network elements using an OSINT mechanic. Spyse search engines have everything that pen testers might need to perform complete web reconnaissance.
All users have the ability to perform a detailed search on the following elements of a network:
This is just part of the things that Spyse’s search engine can do.
The above given is a huge list of Penetration tools but that is not the end. There are a few more tools and software that are gaining momentum in recent times.
#27) Ettercap: A network and host analysis tool that provides sniffing and protocol dissection among other things. Website .
#28) Veracode : Works with the code development process to ensure security and minimize vulnerabilities at the source level. Website .
#29) Aircrack-ng : Captures data packets and uses the same for recovery of 802.11 WEP and WPA-PSK keys. Website
#30) Arachni : This is a Ruby framework that helps in analyzing web application security. It performs a meta-analysis on the HTTP responses it receives during an audit process and presents various insights into how secure the application is. Website
Have you performed pen-testing before? If yes, please share your experiences. What Security and Penetration testing tool do you use? If we have missed any important tools in this list please let us know in the comments below.
Agree with this list, covers essential tools required for any pentester doing basic web and infrastructure testing. I also use AttackForge.com to manage pentesting projects and for automated reporting.
It would be helpful to have two lists: one for commercial products and one for open source products.
Network Security Toolkit has an advanced Web User Interface for system/network administration, navigation, automation, network monitoring & analysis and configuration of many applications found in Network Security Toolkit distro.
Netsparker is legendary. The ease of use and noob friendliness makes it way better than the rest. I must also add that its very powerful too and gives very accurate results.
CMSEEK is a tool to detect almost 150+ cms
These are some of the go to tools for pentesting, we just started using another tool which helps manage pentesting and automate reporting although we don’t have to do that anymore as the platform also provides a login profile to our internal teams (our customers), they login see the projects and push findings to tickets.
I see now they also have a sort of freemium version, also a lot of the tools above can be imported in to the tool itself.
hi can anyone help me? Let say there is a website that have sql injection security, is there other issue related? Especially for login page or website with authorization?
Please I need your reply
Do you know any penetrating tools Facebook use to improve it’s security, can you tell me
About us | Contact us | Advertise | Testing Services
All articles are copyrighted and can not be reproduced without permission.
© Copyright SoftwareTestingHelp 2021 — Read our Copyright Policy | Privacy Policy | Terms | Cookie Policy | Affiliate Disclaimer | Link to Us
40 Best Penetration Testing (Pen Test ) Vapt Tools in 2021
19 Powerful Penetration Testing Tools Used By Pros in 2021
24 Essential Penetration Testing Tools in 2020 | Varonis
11 Best Tools for Penetration Testing - Reviews & Links (Paid & Free)
PentestTools - Penetration Testing Tools.
“This really opened my eyes to AD security in a way defensive work never did.”
Get a highly customized data risk assessment run by engineers who are obsessed with data security.
Live Cyber Attack Lab 🎯 Watch our IR team detect & respond to a rogue insider trying to steal data! Choose a Session
Inside Out Security Blog » IT Pros » 24 Essential Penetration Testing Tools
Penetration testing has become an essential part of the security verification process. While it’s great that there are many penetration testing tools to choose from, with so many that perform similar functions it can become confusing which tools provide you the best value for your time.
We are going to review some of the best pentesting tools available to pentesters today and organize them by category.
While pentesting tools are usually used in the context of a larger security assessment of a network or service, there’s nothing holding back sysadmin’s or developers from deploying the exact same tools to validate the strength of their own work.
Below is a list of the best pentesting tools to tackle different penetration testing tasks. We also included what each tool is best used for and which platforms they’re supported on.
The PowerShell-suite is a collection of PowerShell scripts that extract information about the handles, processes, DLLs, and many other aspects of Windows machines. By scripting together specific tasks, you can quickly navigate and check which systems on a network are vulnerable to exploit.
Zmap is a lightweight network scanner that is capable of scanning everything from a home network to the entire Internet. This free network scanner is best used to gather baseline details about a network. If you only have an IP range to go off of, use to get a lay of the land quickly.
Xray is an excellent network mapping tool that uses the OSINT framework to help guide its tactics. Xray uses wordlists, DNS requests , and any API keys to help identify open ports on a network from the outside looking in.
SimplyEmail is an email recon tool used to help gather associated information found on the internet based on someone’s email address. SimplyEmail is based on the harvester solution and works to search the internet for any data that can help provide intelligence around any given email address.
Wireshark is likely the most widely used network protocol analyzer across the world. Network traffic captured via Wireshark can show what protocols and systems are live, what accounts are most active, and allow attackers to intercept sensitive data.
Hashcat is one of the fastest password recovery tools to date. By downloading the Suite version, you have access to the password recovery tool, a word generator, and a password cracking element. Dictionary, combination, brute-force, rule-based, toggle-case, and Hybrid password attacks are all fully supported. Best of all is hashcat has a great online community to help support the tool with patching, a WiKi page, and walkthroughs.
John the Ripper is the original password cracking tool. Its sole purpose is to find weak passwords on a given system and expose them. John the Ripper is a pentesting tool that can be used for both a security and a compliance perspective. John is famous for its ability to expose weak passwords within a short timeframe quickly.
Hydra is another password cracking tool but with a twist. Hydra is the only password pentesting tool that supports multiple protocols and parallel connections at once. This feature allows a penetration tester to attempt to crack numerous passwords on different systems at the same time without losing connection if unbeaten.
Aircrack-ng is a wireless network security tool that is an all in one package for penetration testing. Aircrack-ng has four primary functions that make it the ultimate standout in its class; It does monitoring of network packets, attacking via packet injection, testing of WiFi capabilities , and finally, password cracking.
For pentesting web applications, Burp Suite is your go-to tool. Incorporating not only vulnerability scanning but Fully Proxy capturing and command injection services as well. Burps UI is fully optimized for the working professional with built-in profiles to allow you to save your configurations on a per-job basis.
Comparable to Burp Suite, Metasploit started as an open-source solution and has gained some traction over the years. Some of the tasks that can be accomplished in Metasploit from a pentesting perspective include vulnerability scanning, listening, exploiting known vulnerabilities, evidence collection, and project reporting.
Nikto is a loud and proud web application scanning solution. It is open-source and contains features like a web server scanner, a pre-packaged list of potentially dangerous files, and a misconfiguration checker as well. Nikto is not stealthy, nor does it try to be; it doesn’t try to hide its presence, but it will get the job done.
Fuzzdb is a special kind of penetration testing tool as it contains pre-built attack payloads to run against web applications to discover if vulnerabilities are genuinely exploitable. On top of being able to simulate attack patterns, Fuzzd b can run discovery scans and perform analysis on the responses received from these scans to narrow better the focus of where vulnerabilities exist.
NMAP is a pentesters best friend. This network security mapping tool gives you a quick look at the open ports on any given network. NMAP commands allow you to dig into the feasibility of specific network-level vulnerabilities. NMAP also has a friendly GUI interface called ZenMap that is easy to use for any skill level. NMAP also comes with a debugging tool, a comparison tool for comparing scan results, and a packet generation tool as well.
Sqlmap is an open-source penetration tool that helps bring validity to possible SQL injection flaws that may affect your database servers. This automated testing tool comes with a slew of detailed features, including DB fingerprinting, remote commands , and its detection engine.
For mobile platform vulnerability discovery, MobSF is your tool. This hacking tool is an all in one platform for pen-testing and vulnerability discovery via static and dynamic application analysis. MobSF also has built-in REST APIs to provide an integrated experience into your development pipeline. ModSF is ultimately a vulnerability scanner for mobile applications.
Linux-Exploit-Suggester is an excellent tool for on the fly security testing of Linux systems without dealing with the overhead of a beefy vulnerability scanner. LES was created for system admins to get a quick sense of the. Based on its lightweight compatibility, LES is a great vulnerability catalog for pentesters looking to get a quick overview of a systems configuration, without creating too much noise via resource consumption.
Apktool is for those Pentesters or security researchers that are attempting to reverse engineer malware to determine a way to better protect against it. Apktool only supports 3rd party, android applications. Apktool’s feature set includes being able to disassemble and reassemble to original form, debugging and help to automate repetitive tasks.
Resource Hacker is a windows specific file editor that allows anyone to decompile a windows file and recompile it at a later time. The great thing about this reverse engineering tool is that it comes with a GUI interface that makes it easy for novice pentesters to learn and use.
IDA is the Kleenex of disassembler tools as it is widely supported and used in commercial validation testing. IDA is interactive as a disassembler as well as a debugger, thus providing you with a whole solution as a professional. Best of all, it supports all major OS system types.
Lastly, we have Radare , which is one of the most widely accepted and versatile disassembly tools available. Some of its features include multiple OS and mobile OS support, file system forensics, data carving capabilities, and visualizing data structures.
If it is available to you, the best way to send out compromised data is through the account you compromised in the first place. Most of the time you will have the ability to use the user’s account to send ether emails out or you could try to use the installed enterprise chat solution in place to accomplish the same outcome. For pentesters trying to remain anonymous, this is a great technique as long as you limit the size of the emails so that it isn’t detected as an anomaly by any DLP solution that might be watching.
Srm stands for Secure remove, and it takes the hassle out, ensuring a file is entirely removed from a system. As a pentester, Srm is great for removing temporary files created while accessing a system, If your intent is to cover up your tracks, Srm is the tool required to remove any rootkit files that may have been used during the exploit process. Srm removes and rewrites over the data location to ensure all traces of the data are thoroughly wiped from the system. Best of all, it is a command-line program that is quick to set up and use.
Catfish is a pentesting tool that is used by many to quickly search for specific files that tend to contain sensitive data or can provide them with additional access (like a password file). Catfish allows the end-user to explore a system for any files containing a particular string within its name. It is simple but highly effective at what it does.
Performing penetration tests is an essential part of verifying that systems are secure. Using the right penetration testing tools saves time and helps to improve your overall security posture.
Jeff has been working on computers since his Dad brought home an IBM PC 8086 with dual disk drives. Researching and writing about data security is his dream job.
© 2021 Inside Out Security | Policies | Certifications
This site uses cookies to provide you with a better browsing experience. Further information may be found in the Varonis Site Privacy Policy
Accept
Lingerie Black Girl
Women Lingerie Porn
Ass Fucked Com
Best Hardcore Free Porn
Xxx Homemade Hairy Bbw