Nebula - 13
Hacking For Ramen
> Objective
There is a security check that prevents the program from continuing execution if the user invoking it does not match a specific user id.
To do this level, log in as the level13 account with the password level13. Files for this level can be found in /home/flag13.
> Source code
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <sys/types.h>
#include <string.h>
#define FAKEUID 1000
int main(int argc, char **argv, char **envp)
{
int c;
char token[256];
if(getuid() != FAKEUID) {
printf("Security failure detected. UID %d started us, we expect %d\n", getuid(), FAKEUID);
printf("The system administrators will be notified of this violation\n");
exit(EXIT_FAILURE);
}
// snip, sorry :)
printf("your token is %s\n", token);
}
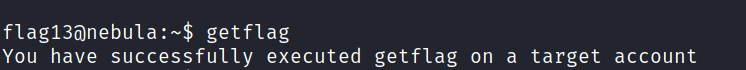
> Getting the flag
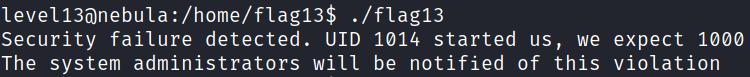
The binary in this level will compare your UID with 1000. It seems to be the only way to get the flag for this level - get yourself a UID 1000. Or make the binary think so.
As we have the full control of binary, why not to debug it?
We do have gdb installed on the Nebula VM, so let's use it.
First thing first, we need to reach the main function:
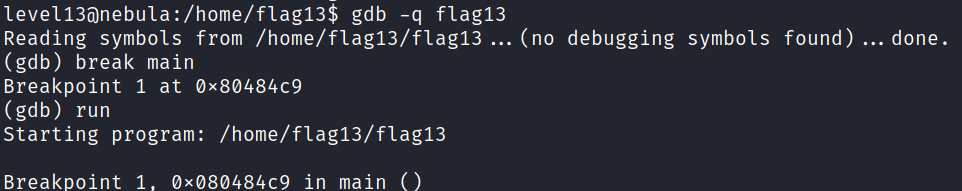
Let's view the first 30 instructions of main
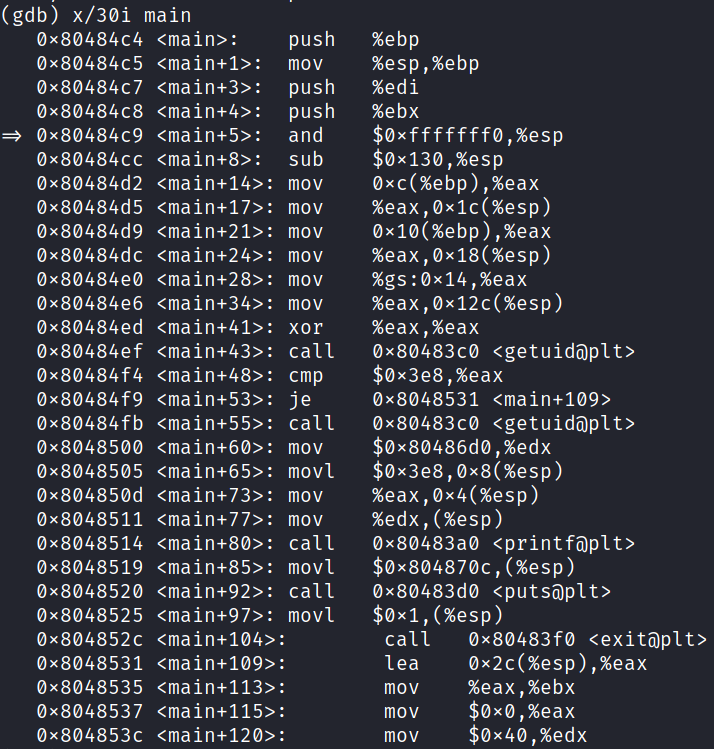
Not sure about you, but my eyes starting to bleed when I look at AT&T syntax. Let's fix that for the sake of my sanity:
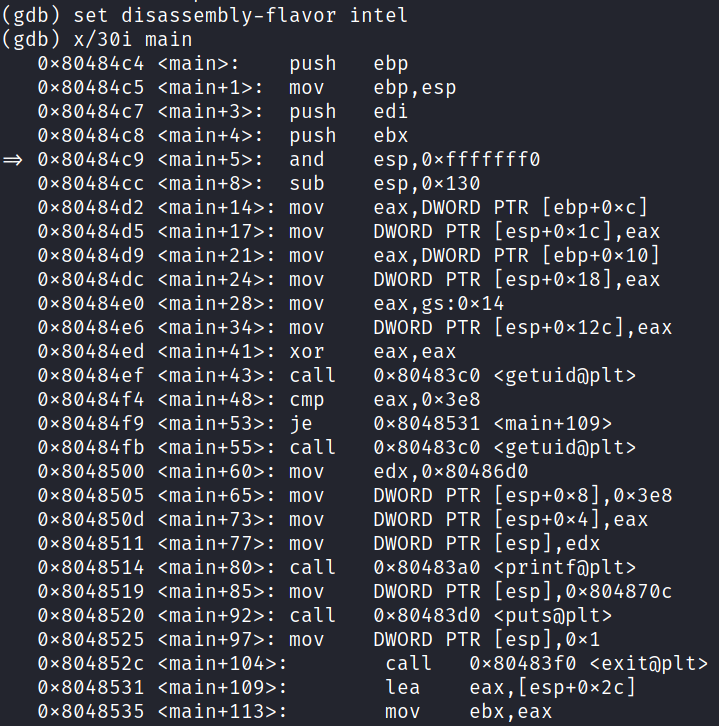
Ah, way better now.
Take a look at <main+48> closely:
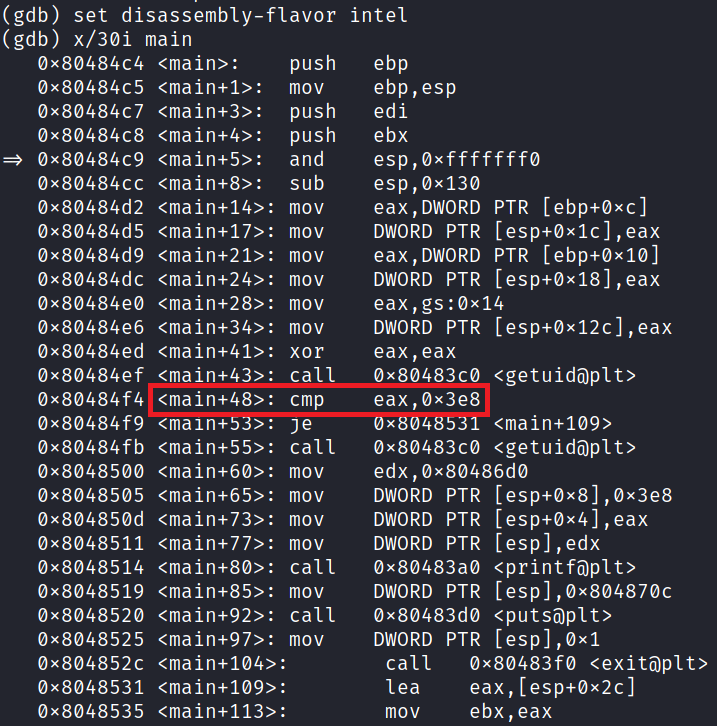
The program is comparing the 0x3e8 (decimal 1000 in HEX) with the EAX.
Let's set another breakpoint there:
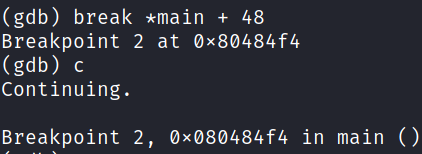
We can check the current value of the EAX register with print command. We can also set our own value of it!
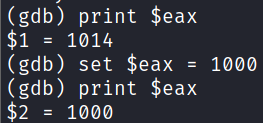
Let's try to trick the IF statement by replacing our current UID (1014) with the expected 1000:
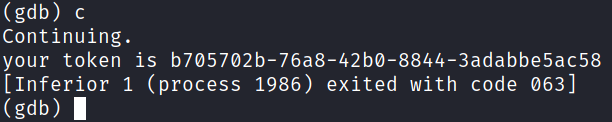
We successfully exfiltrated the token! Let's use it to get the flag: