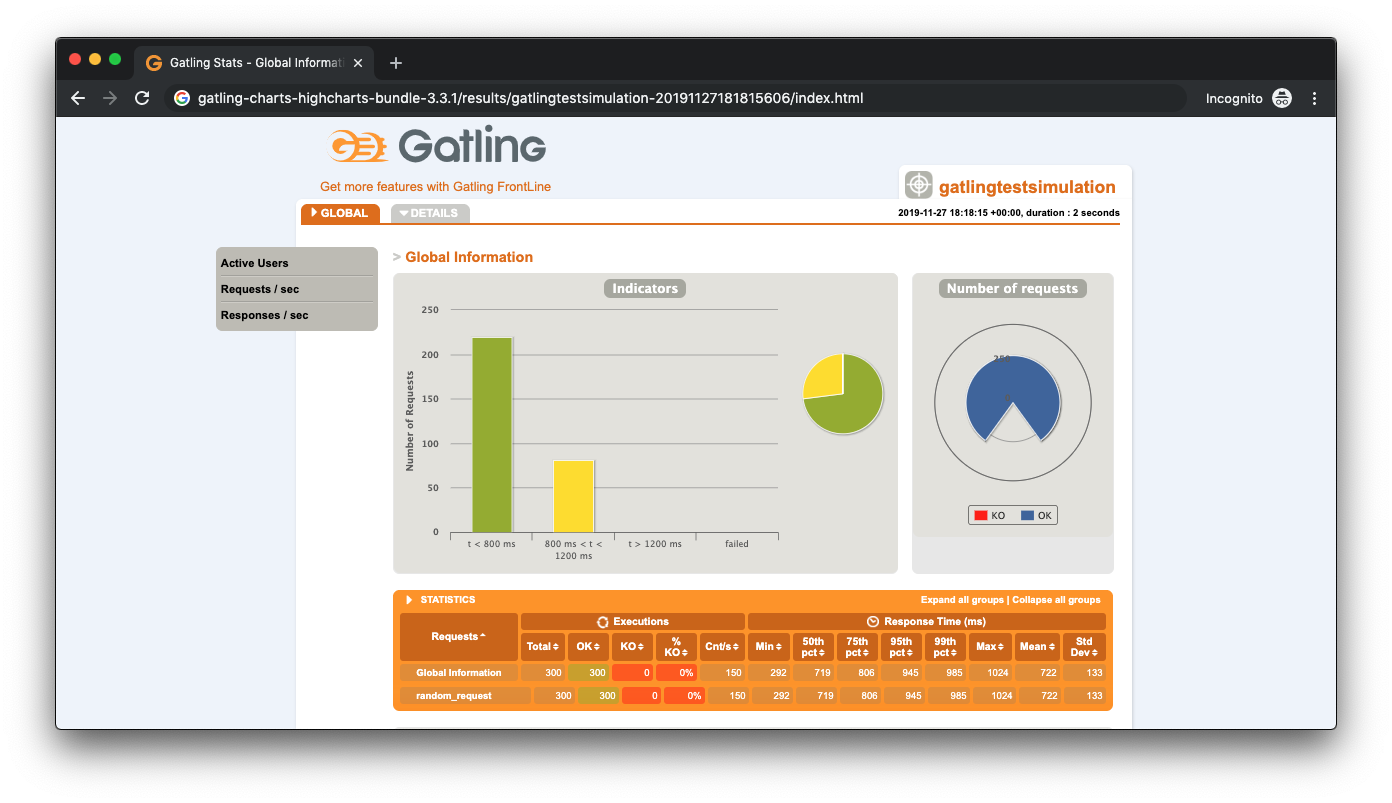
Integer Underflow Private Testing

⚡ 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE 👈🏻👈🏻👈🏻
Sign up or log in to view your list.
I'm currently working on a safe integer library for C++. I've come across some issues when implementing subtraction.
I first attempted to write operator-= like this:
but obviously this will fail with input of -0x80000000 on a two's complement system.
I then attempted to do it like this:
But this doesn't work for anything less than 0 (e.x. -1 - -0x80000000 should be 0x7fffffff but instead reports overflow).
But now even though it correctly catches a case where overflow would occur, it itself causes overflow in a valid case (e.x. -1 - -0x80000000, where - -0x80000000 overflows).
At this point I believe that there's no way to reuse code from the addition while catching all of the corner cases. Therefore, I should probably write different code for the subtraction.
How can I correctly check that integer overflow will not happen before subtraction?
Assume no particular size of integer. Do not rely on undefined behavior.
S.S. Anne
S.S. Anne 14k●77 gold badges●3131 silver badges●6363 bronze badges
there are special instructions (addition, subtraction, multiplication) that inform about overflow - but I doubt that there are any portable ones. you can try to look for them. – ALX23z Jan 29 '20 at 17:51
@ALX23z As you can tell I'm not using assembly nor am I adding before I check for overflow. I intend this to be entirely portable. – S.S. Anne Jan 29 '20 at 17:52
@Tarc I don't use Boost. It's a pain to install and brings in a huge library to something that would otherwise be simple. – S.S. Anne Jan 29 '20 at 18:53
Yeah, but at least it is curated and, I think, Safe Numerics is intended to be portable. Maybe it is worth reading to see the techniques the author made use of. – Tarc Jan 29 '20 at 19:07
note that the two functions are basically asking the same question. First we ask "what direction will rhs move our result from lhs". Then we check if lhs is "far enough away" from the min or max in that direction.
you'll need to change this code if not using it on integral types. On floating point types, there are more complications.
After you check that the operation is valid, simply do it. Don't call another function.
Yakk - Adam Nevraumont
Yakk - Adam Nevraumont 241k●2525 gold badges●289289 silver badges●475475 bronze badges
The first is underflow and the second is overflow, correct? – S.S. Anne Jan 29 '20 at 19:00
@S.S.Anne I have 4 different bounds checks in the above code, I'm not certain what you mean by first or second. Passing max is overflow, passing min is underflow, in a sense. – Yakk - Adam Nevraumont Jan 29 '20 at 19:16
I meant the second function, that checks subtraction. – S.S. Anne Jan 29 '20 at 19:25
@S.S.Anne Then no. Passing max is overflow, not underflow. Rearrange lhs > max + rhs to be lhs - rhs > max to see the (unsafe, but mathematically equivalent) version of the test. – Yakk - Adam Nevraumont Jan 29 '20 at 19:28
Click here to upload your image (max 2 MiB)
You can also provide a link from the web.
By clicking “Post Your Answer”, you agree to our terms of service, privacy policy and cookie policy
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Update: Thanks to Mihai Rusu who discovered that my “correct” functions had a bug in them; I have updated them to fix the bug.
Update2: Thanks to Kevin Bailey who discovered that my final functions had a redundant comparison in them. I have updated them to remove it.
Update2: Thanks to Ami Fischman who pointed me to this code in the Chromium tree that has implemented this functionality in a way that appears to avoid all of the compiler warnings I was getting: src/base/safe_numerics.h.
Integer overflow (and underflow – I’ll lump them together) is one of those pesky things that creeps up in the real world and makes low-level software a little less clean and elegant than what you might see in an algorithms textbook. Checking for overflow is one of those things that distinguishes production-quality software from toy code. If you program in C or C++, it’s something you should always be aware of, especially since it can be a security issue.
If you’re written much low-level software that deals with buffers or offsets, you’ve probably already come across this pattern for testing if an addition will overflow:
If you compile the first example in optimized mode and look at its output, you will see that the function has been optimized to simply return 0 without looking at its arguments at all. Our attempt to check for overflow has been completely defeated. But the second version works as intended. Here the overflow had an easy fix.
The fix is not so easy if we want to test whether a given value can be directly converted to a given data type without overflow. In fact this problem is surprisingly hard. But let’s start with a problem statement. I’ll write it in C++ because templates are convenient, but the issue applies equally to C:
You already know the naive solution isn’t going to work, so let’s just get it out of the way:
The theory here is that if we can round-trip to the destination type and back, then the destination type can represent our target value. But alas, our test program fails!
What happened? Well it turns out that on my platform, -1 can round-trip to unsigned just fine. I’m on a two’s complement system and converting the integer -1 to unsigned yields 0xFFFFFFFF (also known as UINT_MAX), which becomes -1 when converted back to int. But just because the value could round-trip to my destination type doesn’t mean it has the correct value in my destination type. So our first attempt is unsuccessful.
(Note that although this example uses C++ and templates, the lesson equally applies to an attempt in C to test (int)(unsigned)x == x).
If round-tripping isn’t a good test, perhaps we can explicitly test that our value is inside the range of our destination type.
But this does no better; it fails on exactly the same assertion, but this time for a different reason. In our failure case the comparisons are mixed-type comparisons, meaning that the operands are of different types (in this case int and unsigned). How does C++ handle mixed-type comparisons? The hardware can only really compare two values of the same type, so which type do both operands get converted to before the comparison happens?
This is decided by what the C and C++ standards call the usual arithmetic conversions. The usual arithmetic conversions are more complicated than I want to inaccurately summarize here, but in this case they say that -1 is converted to unsigned before being compared in the unsigned domain. So naturally the resulting value will be in range for the unsigned data type.
The “usual arithmetic conversions” are confounding our attempts to ask questions about the original value. So we need to avoid them by ensuring that both sides of our comparison are the same type. But there is no numeric type in C or C++ that can represent all integral values (no type can represent both LLONG_MIN and ULLONG_MAX), so what domain can we use for our range comparisons?
You might be tempted to reach for two’s complement tricks like testing the sign bit of signed types, but resist the urge: the standard does not guarantee two’s complement arithmetic, and besides, the real solution is more principled anyway:
The types intmax_t and uintmax_t are defined in C99 and C++11 as types capable of representing any value of any signed/unsigned integer type, respectively. So if we do our comparisons using those types, we should be able to avoid getting overflow before the comparison is even performed. By casting both sides of the expression to the same type, we avoid the usual arithmetic conversions. But we still have to handle the case where we are converting a signed type to an unsigned one or vice-versa. If we are converting int x to an unsigned type, we need to check whether x < 0 first, before doing our uintmax_t conversions, because once we convert a negative number to uintmax_t it will become a large signed number and appear in range.
So finally we have a solution that works and passes our initial test cases. But the implementation still has one small wart; it throws warnings like the following:
This check exists for when we are converting from a signed type; we want and expect it to be a no-op when converting from an unsigned type. But clang doesn’t know we know this so it warns us anyway. How can we make this warning go away? The warning is thrown even if the comparison is unreachable, so changing the expression to explicitly check whether the type is signed first does not help:
It seems that the only solution to this is to use template partial specialization to ensure that that the val < 0 comparison is only generated for signed types. And functions cannot be partially specialized (only classes) so we need to use a functor. Getting around this warning unfortunately bloats the code significantly, but the solution below does work and avoids the warning.
Parsing, performance, and low-level programming.
Two Sexy Girls Fisting Each Other
Tranny Fucking Guy
Yogscast Diggy Diggy Hole
Xnxx Lolita Maria Russian
Big Wet Ass 2
CWE - CWE-191: Integer Underflow (Wrap or Wraparound) (4.5)
Testing for Integer Overflow in C and C++
Java | int and float overflow and underflow with examples ...
Arithmetic Overflow and Underflow — Blog
Correct the intermittent integer underflow in the angle ...
Integer Underflow Archives - Kali Linux Tutorials
Arithmetic underflow - Wikipedia
Chapter 3: Overflow/underflow, constants, and combined ...
Integer Underflow Private Testing