How does blockchain prevent tampering?
ANT QUSNT CAPITAL LIMITED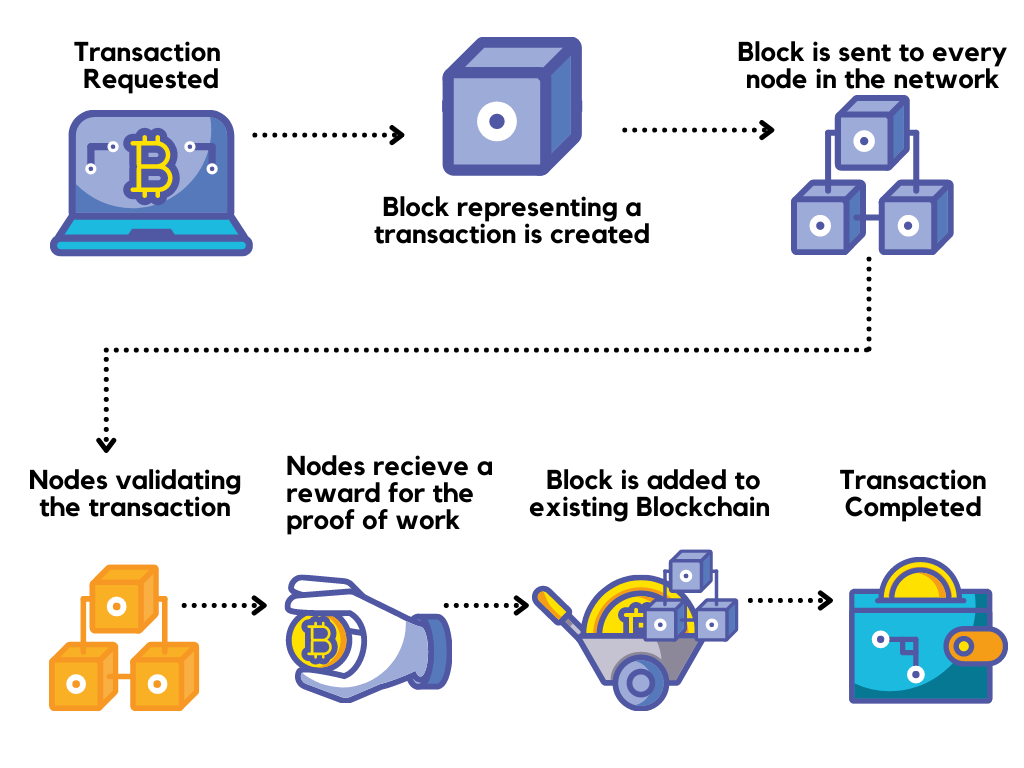
Compared with the centralized currency system, one of the advantages of the blockchain is security - the account itself is anonymous, and inflation will not be caused by excessive issuance of currency. In the article "How does Bitcoin avoid the double payment problem?" ", we discussed how time stamps and the longest chain principle can avoid the double-spending problem. In today's article, we will deeply analyze why transactions on the blockchain are almost impossible to tamper with.
Simply put, the blockchain network itself is a super large distributed ledger. That is to say, there is a ledger that records all transactions generated on the entire blockchain network. This ledger is owned by the owner, and the data is updated in real time. Next, let's analyze how the blockchain implements this distributed ledger from a technical point of view, which involves the specific structure of the blockchain.
The blockchain is composed of blocks linked in chronological order. And each block can be divided into two parts: block header and block body. The block body is relatively simple and can be imagined as a small ledger, which records the transactions that occurred within 10 minutes of generating the block. The block header contains the following parts:
1. Version number: used to identify the transaction version and the referenced rules;
2. Previous block hash value: the value obtained by hashing the block header data of the previous block. Therefore, except that the genesis block has no previous blocks, there is a logical order between any two connected blocks. Tampering the data of a block alone will cause it to be inaccessible to subsequent blocks. , the two blocks are disconnected.
According to the longest chain principle (for details, see the article "How does Bitcoin avoid the double payment problem?"), if I want to tamper with the data of a certain block, the only way is to build a block after the previous block of this block. New malicious blocks that contain tampered data, and ensure that the newly generated blocks in real time are connected to my malicious block, until this chain is longer than the original and becomes the only valid main chain. Can.
In reality, if you want to ensure that all future blocks are generated after my block, you need at least 51% of the computing power to be hopeful. Note that it is only "hopeful", not "100% successful" . Although this kind of 51% attack is possible for some very, very unpopular small currencies, the market price of unpopular digital currencies determines that it is completely unnecessary to do so from the perspective of input-output ratio . For a very influential digital currency like Bitcoin, achieving such a goal requires a huge economic cost, which will make counterfeiters lose more than they gain.
3. Merkle root: On the block body, all the transaction information of the block within 10 minutes is dug out, arranged in a Merkle tree structure, the leaf nodes are hashed in pairs, and the upper layer nodes are generated, and the upper layer nodes are hashed again , to generate the upper layer, until finally a tree root is generated, which is called the Merkle tree root, and this hash value is placed on the block header.
Therefore, any change in a transaction in the block body will cause a change in the Merkle root data of the block header, making this block inconsistent with its next block data, and then returning to what we mentioned in the previous paragraph Condition.
4. Timestamp: Record the time when the block was generated. We wrote in the article "How does Bitcoin avoid the double payment problem?" "Introduced, timestamp can effectively avoid the double spend problem.
5. Difficulty value: The difficulty target for digging out the block. Every 2016 blocks are generated, the difficulty of data block calculation will be adjusted once.
6. Random number: It is the "answer" that the miners are looking for during the mining process. Only by obtaining the random number can they obtain the right to package the block.