Google Private Key

🛑 👉🏻👉🏻👉🏻 INFORMATION AVAILABLE CLICK HERE👈🏻👈🏻👈🏻
Language
Language
English
Deutsch
Español – América Latina
Français
Português – Brasil
中文 – 简体
日本語
한국어
This page explains how to create and manage service account keys using the Google Cloud Console, the gcloud command-line tool, the Identity and Access Management API, or one of the Google Cloud Client Libraries.
To allow a user to manage service account keys, grant the Service Account Key Admin role (roles/iam.serviceAccountKeyAdmin). For more information, see Service Accounts roles.
IAM basic roles also contain permissions to manage service account keys. You should not grant basic roles in a production environment, but you can grant them in a development or test environment.
To use a service account from outside of Google Cloud, such as on other platforms or on-premises, you must first establish the identity of the service account. Public/private key pairs provide a secure way of accomplishing this goal. When you create a service account key, the public portion is stored on Google Cloud, while the private portion is available only to you. For more information about public/private key pairs, see Service account keys.
You can create a service account key using the Cloud Console, the gcloud tool, the serviceAccounts.keys.create() method, or one of the client libraries. A service account can have up to 10 keys.
In the examples below, sa-name is the name of your service account, and project-id is the ID of your Google Cloud project. You can retrieve the sa-name@project-id.iam.gserviceaccount.com string from the Service Accounts page in the Cloud Console.
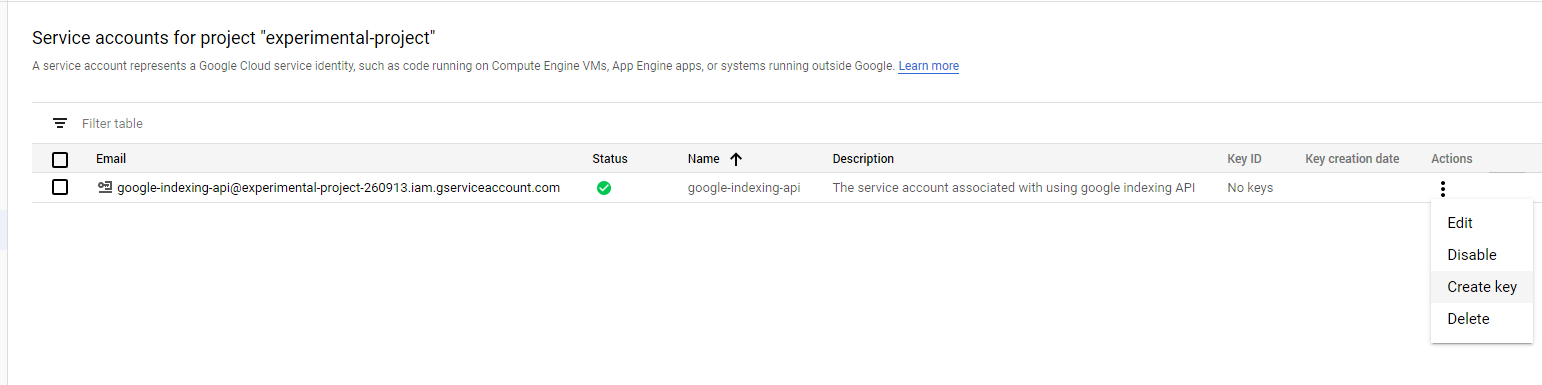
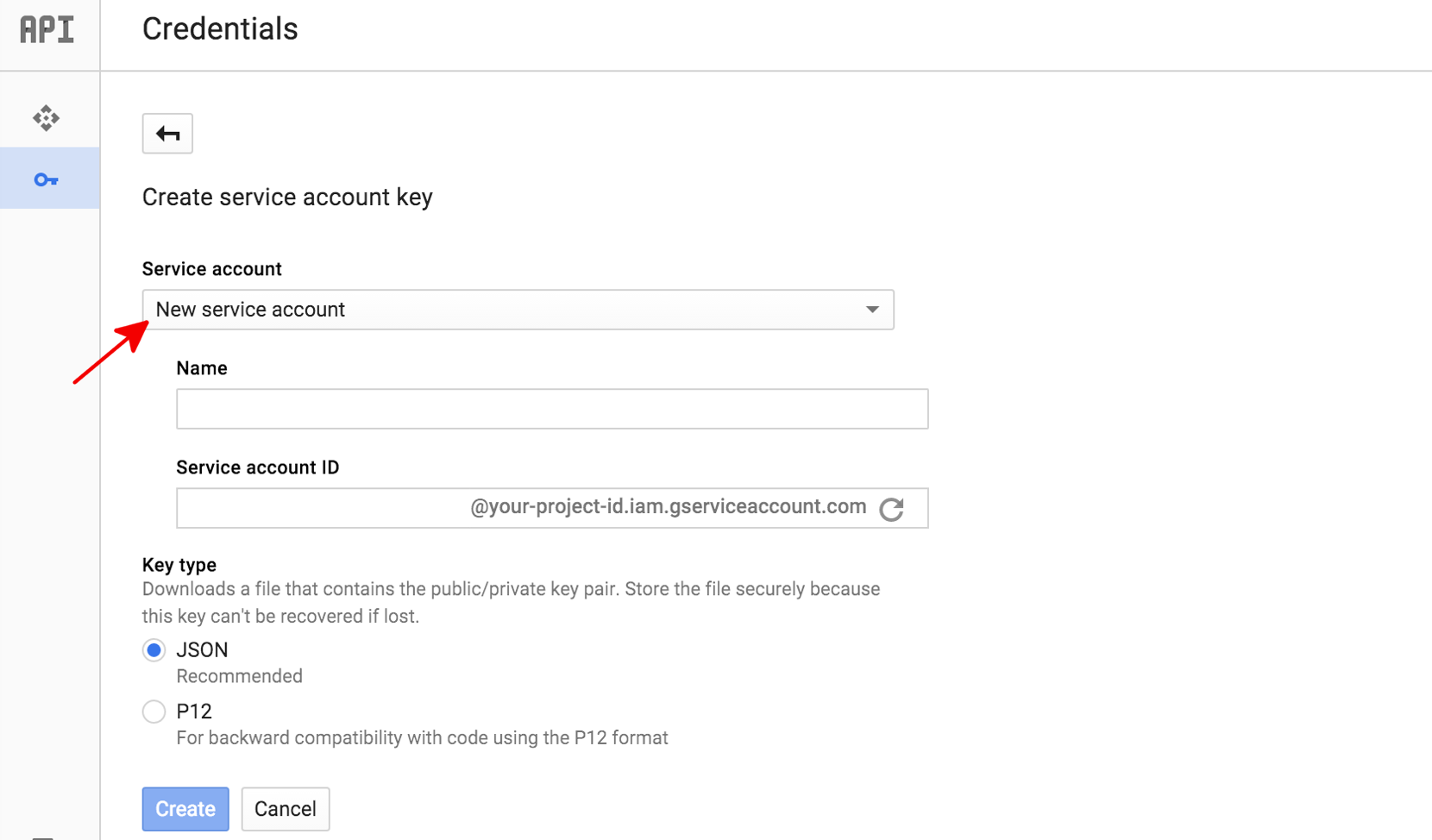
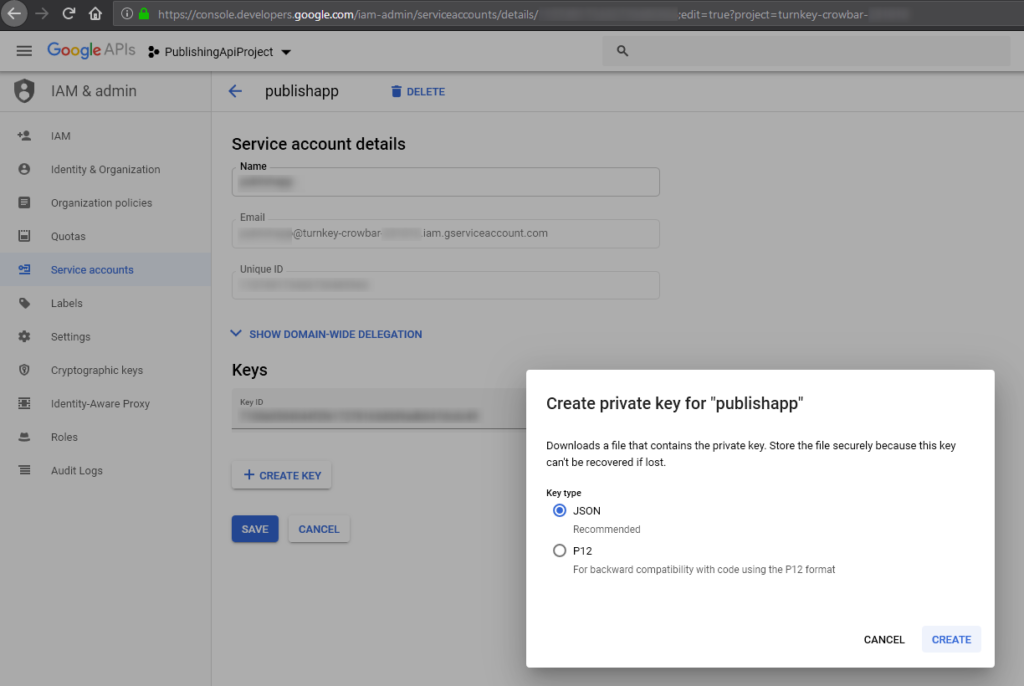
In the Cloud Console, go to the Service Accounts page.
Click the email address of the service account that you want to create a key for.
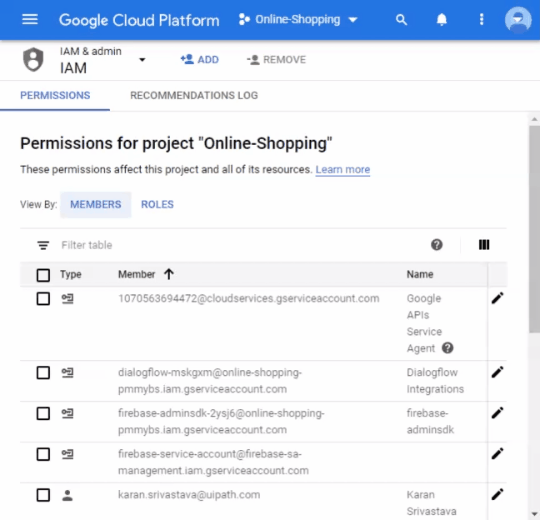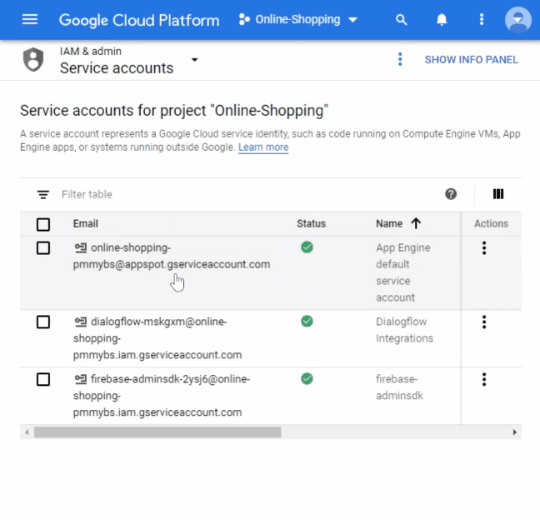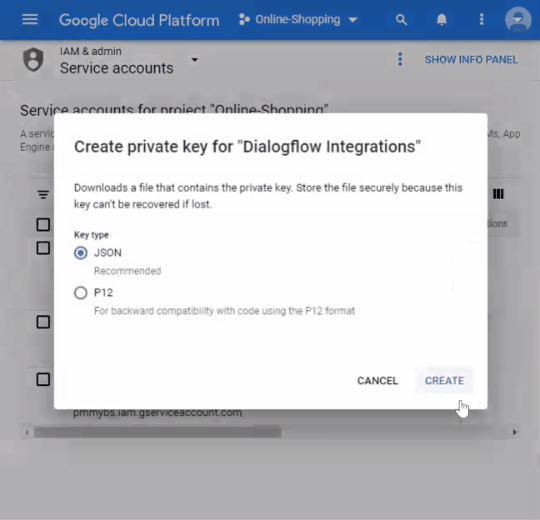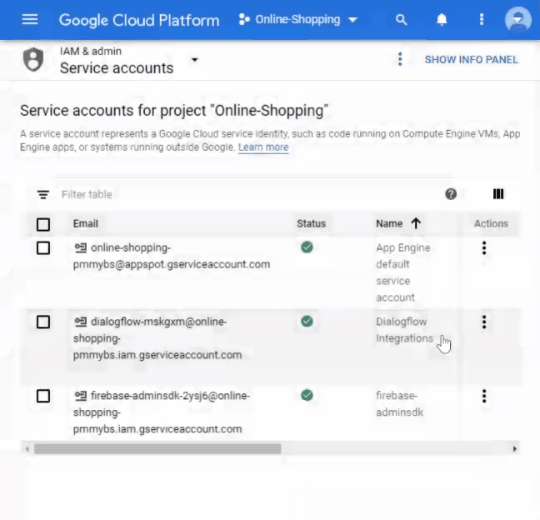
Click the Add key drop-down menu, then select Create new key.
Select JSON as the Key type and click Create.
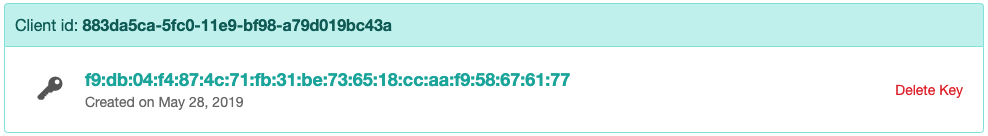
Clicking Create downloads a service account key file. After you download the key file, you cannot download it again.
The downloaded key has the following format, where private-key is the private portion of the public/private key pair:
Make sure to store the key file securely, because it can be used to authenticate as your service account. You can move and rename this file however you would like.
Execute the gcloud iam service-accounts keys create command to create service account keys.
The service account key file is now downloaded to your machine. After you download the key file, you cannot download it again.
The downloaded key has the following format, where private-key is the private portion of the public/private key pair:
Make sure to store the key file securely, because it can be used to authenticate as your service account. You can move and rename this file however you would like.
The projects.serviceAccounts.keys.create method creates a key for a service account.
Before using any of the request data below, make the following replacements:
To send your request, expand one of these options:
Save the request body in a file called request.json, and execute the following command:
Save the request body in a file called request.json, and execute the following command:
Copy the request body and open the method reference page. The API Explorer panel opens on the right side of the page. You can interact with this tool to send requests. Paste the request body in this tool, complete any other required fields, and click Execute.
The response contains a key for your service account. The returned key has the following format, where ENCODED_PRIVATE_KEY is the private portion of the public/private key pair, encoded in base64.
To create a key file that you can use to authenticate as the service account, decode the private key data and save it in a file:
Replace PATH with the path of the file that you want to save the key to. Use the .json file extension.
Replace PATH with the path of the file that you want to save the key to. Use the .json file extension.
Save the encoded private key data (ENCODED_PRIVATE_KEY) in a file.
Make sure to store the key data securely, because it can be used to authenticate as your service account.
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM C++ API reference documentation.
namespace iam = google::cloud::iam;
return [](std::string const& name) {
iam::IAMClient client(iam::MakeIAMConnection());
auto response = client.CreateServiceAccountKey(
name,
google::iam::admin::v1::ServiceAccountPrivateKeyType::
TYPE_GOOGLE_CREDENTIALS_FILE,
google::iam::admin::v1::ServiceAccountKeyAlgorithm::KEY_ALG_RSA_2048);
if (!response) throw std::runtime_error(response.status().message());
std::cout << "ServiceAccountKey successfully created: "
<< response->DebugString() << "\n";
return response->name();
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM C# API reference documentation.
using System;
using Google.Apis.Auth.OAuth2;
using Google.Apis.Iam.v1;
using Google.Apis.Iam.v1.Data;
public partial class ServiceAccountKeys
{
public static ServiceAccountKey CreateKey(string serviceAccountEmail)
{
var credential = GoogleCredential.GetApplicationDefault()
.CreateScoped(IamService.Scope.CloudPlatform);
var service = new IamService(new IamService.Initializer
{
HttpClientInitializer = credential
});
var key = service.Projects.ServiceAccounts.Keys.Create(
new CreateServiceAccountKeyRequest(),
"projects/-/serviceAccounts/" + serviceAccountEmail)
.Execute();
Console.WriteLine("Created key: " + key.Name);
return key;
}
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Go API reference documentation.
import (
"context"
"fmt"
"io"
iam "google.golang.org/api/iam/v1"
)
// createKey creates a service account key.
func createKey(w io.Writer, serviceAccountEmail string) (*iam.ServiceAccountKey, error) {
ctx := context.Background()
service, err := iam.NewService(ctx)
if err != nil {
return nil, fmt.Errorf("iam.NewService: %v", err)
}
resource := "projects/-/serviceAccounts/" + serviceAccountEmail
request := &iam.CreateServiceAccountKeyRequest{}
key, err := service.Projects.ServiceAccounts.Keys.Create(resource, request).Do()
if err != nil {
return nil, fmt.Errorf("Projects.ServiceAccounts.Keys.Create: %v", err)
}
fmt.Fprintf(w, "Created key: %v", key.Name)
return key, nil
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Java API reference documentation.
import com.google.api.client.googleapis.javanet.GoogleNetHttpTransport;
import com.google.api.client.json.jackson2.JacksonFactory;
import com.google.api.services.iam.v1.Iam;
import com.google.api.services.iam.v1.IamScopes;
import com.google.api.services.iam.v1.model.CreateServiceAccountKeyRequest;
import com.google.api.services.iam.v1.model.ServiceAccountKey;
import com.google.auth.http.HttpCredentialsAdapter;
import com.google.auth.oauth2.GoogleCredentials;
import java.io.IOException;
import java.security.GeneralSecurityException;
import java.util.Collections;
public class CreateServiceAccountKey {
// Creates a key for a service account.
public static void createKey(String projectId, String serviceAccountName) {
// String projectId = "my-project-id";
// String serviceAccountName = "my-service-account-name";
Iam service = null;
try {
service = initService();
} catch (IOException | GeneralSecurityException e) {
System.out.println("Unable to initialize service: \n" + e.toString());
return;
}
String serviceAccountEmail = serviceAccountName + "@" + projectId + ".iam.gserviceaccount.com";
try {
ServiceAccountKey key =
service
.projects()
.serviceAccounts()
.keys()
.create(
"projects/-/serviceAccounts/" + serviceAccountEmail,
new CreateServiceAccountKeyRequest())
.execute();
System.out.println("Created key: " + key.getName());
} catch (IOException e) {
System.out.println("Unable to create service account key: \n" + e.toString());
}
}
private static Iam initService() throws GeneralSecurityException, IOException {
// Use the Application Default Credentials strategy for authentication. For more info, see:
// https://cloud.google.com/docs/authentication/production#finding_credentials_automatically
GoogleCredentials credential =
GoogleCredentials.getApplicationDefault()
.createScoped(Collections.singleton(IamScopes.CLOUD_PLATFORM));
// Initialize the IAM service, which can be used to send requests to the IAM API.
Iam service =
new Iam.Builder(
GoogleNetHttpTransport.newTrustedTransport(),
JacksonFactory.getDefaultInstance(),
new HttpCredentialsAdapter(credential))
.setApplicationName("service-account-keys")
.build();
return service;
}
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Python API reference documentation.
import os
from google.oauth2 import service_account
import googleapiclient.discovery
def create_key(service_account_email):
"""Creates a key for a service account."""
credentials = service_account.Credentials.from_service_account_file(
filename=os.environ['GOOGLE_APPLICATION_CREDENTIALS'],
scopes=['https://www.googleapis.com/auth/cloud-platform'])
service = googleapiclient.discovery.build(
'iam', 'v1', credentials=credentials)
key = service.projects().serviceAccounts().keys().create(
name='projects/-/serviceAccounts/' + service_account_email, body={}
).execute()
print('Created key: ' + key['name'])
Google ensures that all public keys for all service accounts are publicly accessible by anyone and available to verify signatures that are created with the private key. The public key is publicly accessible at the following URLs:
You can list the service account keys for a service account using the Cloud Console, the gcloud tool, the serviceAccount.keys.list() method, or one of the client libraries.
The serviceAccount.keys.list() method is commonly used to audit service accounts and keys, or to build custom tooling for managing service accounts.
To find out which project your key belongs to, you can download the key as a JSON file and look at that file.
You might see keys listed that you did not create. These are Google Cloud-managed keys used by Google Cloud services such as App Engine and Compute Engine. For more information on the difference between user and Google Cloud-managed keys, see Understanding service accounts.
In the Cloud Console, go to the Service Accounts page.
Select a project. The Cloud Console lists all of the project's service accounts and their corresponding keys.
Execute the gcloud iam service-accounts keys list command to list service account keys.
8e6e3936d7024646f8ceb39792006c07f4a9760c
937c98f870f5c8db970af527aa3c12fd88b1c20a
The projects.serviceAccounts.keys.list method lists all of the service account keys for a service account.
Before using any of the request data below, make the following replacements:
To send your request, expand one of these options:
Open the method reference page. The API Explorer panel opens on the right side of the page. You can interact with this tool to send requests. Complete any required fields and click Execute.
You should receive a JSON response similar to the following:
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM C++ API reference documentation.
namespace iam = google::cloud::iam;
[](std::string const& service_account_name,
std::vector const& key_type_labels) {
iam::IAMClient client(iam::MakeIAMConnection());
std::vector
key_types;
for (auto const& type : key_type_labels) {
if (type == "USER_MANAGED") {
key_types.push_back(google::iam::admin::v1::
ListServiceAccountKeysRequest::USER_MANAGED);
} else if (type == "SYSTEM_MANAGED") {
key_types.push_back(google::iam::admin::v1::
ListServiceAccountKeysRequest::SYSTEM_MANAGED);
}
}
auto response =
client.ListServiceAccountKeys(service_account_name, key_types);
if (!response) throw std::runtime_error(response.status().message());
std::cout << "ServiceAccountKeys successfully retrieved: "
<< response->DebugString() << "\n";
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM C# API reference documentation.
using System;
using System.Collections.Generic;
using Google.Apis.Auth.OAuth2;
using Google.Apis.Iam.v1;
using Google.Apis.Iam.v1.Data;
public partial class ServiceAccountKeys
{
public static IList ListKeys(string serviceAccountEmail)
{
var credential = GoogleCredential.GetApplicationDefault()
.CreateScoped(IamService.Scope.CloudPlatform);
var service = new IamService(new IamService.Initializer
{
HttpClientInitializer = credential
});
var response = service.Projects.ServiceAccounts.Keys
.List($"projects/-/serviceAccounts/{serviceAccountEmail}")
.Execute();
foreach (ServiceAccountKey key in response.Keys)
{
Console.WriteLine("Key: " + key.Name);
}
return response.Keys;
}
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Go API reference documentation.
import (
"context"
"fmt"
"io"
iam "google.golang.org/api/iam/v1"
)
// listKey lists a service account's keys.
func listKeys(w io.Writer, serviceAccountEmail string) ([]*iam.ServiceAccountKey, error) {
ctx := context.Background()
service, err := iam.NewService(ctx)
if err != nil {
return nil, fmt.Errorf("iam.NewService: %v", err)
}
resource := "projects/-/serviceAccounts/" + serviceAccountEmail
response, err := service.Projects.ServiceAccounts.Keys.List(resource).Do()
if err != nil {
return nil, fmt.Errorf("Projects.ServiceAccounts.Keys.List: %v", err)
}
for _, key := range response.Keys {
fmt.Fprintf(w, "Listing key: %v", key.Name)
}
return response.Keys, nil
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Java API reference documentation.
import com.google.api.client.googleapis.javanet.GoogleNetHttpTransport;
import com.google.api.client.json.jackson2.JacksonFactory;
import com.google.api.services.iam.v1.Iam;
import com.google.api.services.iam.v1.IamScopes;
import com.google.api.services.iam.v1.model.ServiceAccountKey;
import com.google.auth.http.HttpCredentialsAdapter;
import com.google.auth.oauth2.GoogleCredentials;
import java.io.IOException;
import java.security.GeneralSecurityException;
import java.util.Collections;
import java.util.List;
public class ListServiceAccountKeys {
// Lists all keys for a service account.
public static void listKeys(String projectId, String serviceAccountName) {
// String projectId = "my-project-id";
// String serviceAccountName = "my-service-account-name";
Iam service = null;
try {
service = initService();
} catch (IOException | GeneralSecurityException e) {
System.out.println("Unable to initialize service: \n" + e.toString());
return;
}
String serviceAccountEmail = serviceAccountName + "@" + projectId + ".iam.gserviceaccount.com";
try {
List keys =
service
.projects()
.serviceAccounts()
.keys()
.list("projects/-/serviceAccounts/" + serviceAccountEmail)
.execute()
.getKeys();
for (ServiceAccountKey key : keys) {
System.out.println("Key: " + key.getName());
}
} catch (IOException e) {
System.out.println("Unable to list service account keys: \n" + e.toString());
}
}
private static Iam initService() throws GeneralSecurityException, IOException {
// Use the Application Default Credentials strategy for authentication. For more info, see:
// https://cloud.google.com/docs/authentication/production#finding_credentials_automatically
GoogleCredentials credential =
GoogleCredentials.getApplicationDefault()
.createScoped(Collections.singleton(IamScopes.CLOUD_PLATFORM));
// Initialize the IAM service, which can be used to send requests to the IAM API.
Iam service =
new Iam.Builder(
GoogleNetHttpTransport.newTrustedTransport(),
JacksonFactory.getDefaultInstance(),
new HttpCredentialsAdapter(credential))
.setApplicationName("service-account-keys")
.build();
return service;
}
}
To learn how to install and use the client library for IAM, see IAM client libraries. For more information, see the IAM Python API reference documentation.
import os
from google.oauth2 import service_account
import googleapiclient.discovery
def list_keys(service_account_email):
"""Lists all keys for a service account."""
credentials = service_account.Credentials.from_service_account_file(
filename=os.environ['GOOGLE_APPLICATION_CREDENTIALS'],
scopes=['https://www.googleapis.com/auth/cloud-platform'])
service = googleapiclient.discovery.build(
'iam', 'v1', credentials=credentials)
keys = service.projects().serviceAccounts().keys().list(
name='projects/-/serviceAccounts/' + service_account_email).execute()
for key in keys['keys']:
print('Key: ' + key['name'])
You can only get the private key data for a service account key when the key is first created.
You can get basic information about a key such as its ID, algorithm, and public key data with the projects.serviceAccounts.keys.get() REST API method. Using the Cloud Console or the gcloud command-line tool is not supported.
You can upload the public key portion of a user-managed key pair to a service account. After you upload the public key, it is permanently associated w
Milf Big Tits Hd 2021
Lena Paul Xxx Torrent
Dick Whittington And His Cat
Muscle Girl Dp Porno Xvideo
Turkish Big Cock
Creating and managing service account keys | Cloud IAM ...
Cloud Key Management | Google Cloud
Generate a Google Translate API Key For Your Site
How to generate an access & secret key in Google Cloud ...
Using API Keys | Directions API | Google Developers
Google
Cloud Storage authentication | Google Cloud
How can I find my certificate’s Private Key? – HelpDesk ...
Google Private Key
































/GettyImages-157504374-5b6c5719c9e77c0050710197.jpg)