GSM SNIFFING 2022
⭕🔱🇰🇦🇱🇮™🔱⭕Before starting let us clear some basic points about GSM SNIFFING !
What is GSM (Global System for Mobile communication)
GSM or Global System for Mobile Communications is the most popular wireless cellular communication technique, used for public communication. The GSM standard was developed for setting protocols for second generation (2G) digital cellular networks.
It initially started as a circuit switching network, but later packet switching was implemented after integration General Packet Radio Service (GPRS) technology as well. The widely-used GSM frequency bands are 900 MHz and 1800 MHz.
In the Europe and Asia, the GSM operates in 900 to 1800 MHz frequency range, whereas in United States and other American countries, it operates in the 850 to 1900 MHz frequency range. It uses the digital air interface wherein the analog signals are converted to digital signals before transmission. The transmission speed is 270 Kbps.
In GSM cellular networks, an absolute radio-frequency channel number (ARFCN) is a code that specifies a pair of physical radio carriers used for transmission and reception in a land mobile radio system, one for the uplink signal and one for the downlink signal.
❤️🔥Course Link : GSM SNIFFING
What is SDR?
Software Defined Radio is a radio broadcast communication technology, which is based on a software-defined wireless communication protocol instead of being implemented through hard-wires. SDR allows easy signal processing and experimentation with more complex radio frequency builds.
WHAT IS RTL-SDR
RTL-SDR (RTL2832U) and software defined radio news and projects. Also featuring Airspy, HackRF, FCD, SDRplay and more.
What are some RTL-SDR Radio Scanner Applications?
The RTL-SDR can be used as a wide band radio scanner. Applications include:
- Use as a police radio scanner.
- Listening to EMS/Ambulance/Fire communications.
- Listening to aircraft traffic control conversations.
- Tracking aircraft positions like a radar with ADSB decoding.
- Decoding aircraft ACARS short messages.
- Scanning trunking radio conversations.
- Decoding unencrypted digital voice transmissions such as P25/DMR/D-STAR.
- Tracking maritime boat positions like a radar with AIS decoding.
- Decoding POCSAG/FLEX pager traffic.
- Scanning for cordless phones and baby monitors.
- Tracking and receiving meteorological agency launched weather balloon data.
- Tracking your own self launched high altitude balloon for payload recovery.
- Receiving wireless temperature sensors and wireless power meter sensors.
- Listening to VHF amateur radio.
- Decoding ham radio APRS packets.
- Watching analogue broadcast TV.
- Sniffing GSM signals.
- Using rtl-sdr on your Android device as a portable radio scanner.
- Receiving GPS signals and decoding them.
- Using rtl-sdr as a spectrum analyzer.
- Receiving NOAA weather satellite images.
- Listening to satellites and the ISS.
- Radio astronomy.
- Monitoring meteor scatter.
- Listening to FM radio, and decoding RDS information.
- Listening to DAB broadcast radio.
- Listening to and decoding HD-Radio (NRSC5).
- Use rtl-sdr as a panadapter for your traditional hardware radio.
- Decoding taxi mobile data terminal signals.
- Use rtl-sdr as a high quality entropy source for random number generation.
- Use rtl-sdr as a noise figure indicator.
- Reverse engineering unknown protocols.
- Triangulating the source of a signal.
- Searching for RF noise sources.
- Characterizing RF filters and measuring antenna SWR.
- Decoding Inmarsat STD-C EGC geosynchronous satellites.
- Listening to the ISS (International Space Station).
Furthermore, with an upconverter or V3 RTL-SDR dongle to receive HF signals the applications are expanded to:
- Listening to amateur radio hams on SSB with LSB/USB modulation.
- Decoding digital amateur radio ham communications such as CW/PSK/RTTY/SSTV.
- Receiving HF weatherfax.
- Receiving digital radio mondiale shortwave radio(DRM).
- Listening to international shortwave radio.
- Looking for RADAR signals like over the horizon (OTH) radar, and HAARP signals.
Note that not all the applications listed may be legal in your country. Please be responsible.

Requirement For Sniffing.
You can use any one of them :
- RTL-SDR
- Hackrf
- USRP
- Blade-RF
Software used:
GSM Sniffing Tools
apt-get install gqrx
apt-get install kalibrate-rtl
apt-get install gr-gsm
https://github.com/Oros42/IMSI-catcher
What Is an International Mobile Subscriber Identity (IMSI)?
IMSI numbers are usually 15 digits, and they have three distinct parts:
- The first set of digits is the Mobile Country Code (MCC), which defines the country a subscriber primarily operates within. This is always either two or three digits.
- The second set of digits is the Mobile Network Code (MNC), which identifies the specific MNO a subscriber is associated with. This is between one and three digits.
- The final set of digits is the Mobile Subscription Identification Number, which is unique to the subscriber. (This is typically nine or ten digits.)
For example, here’s what you can learn from the IMSI number 310410123456789:
Mobile Country Code
310
United States
Mobile Network Code
410
AT&T
Mobile Subscription Identification Number
123456789
What Is an ICCID Number?
ICCID stands for Integrated Circuit Card Identification Number. It’s a unique 18-22 digit code that includes a SIM card’s country, home network, and identification number. You’ll usually find an ICCID printed on the back of a SIM card, but sometimes it’s included in the packaging materials instead.
What is IMSI ?
IMSI stands for "International Mobile Subscriber Identity." It’s a mobile subscriber’s unique identification number. Like an ICCID, an IMSI is saved on the SIM card. Most SIM cards only store a single IMSI, which is associated with a list of networks the subscriber is authorized to access. EMnify’s SIMs, however, are Multi-IMSI, meaning they store multiple subscriber identities. This allows the SIM to change identities to access more networks and select the one with the best coverage.
An IMSI is not the same as a telephone number. The IMSI number has up to 15 digits and consists of three parts:
The first three digits are the Mobile Country Code (MCC). This can be used to determine the home country of the operator that issued the SIM card. The IMSI of European countries always starts with the number 2.
The following two or three digits are the Mobile Network Code, which represents the network the user is active in. For example, the number 01 represents Deutsche Telekom.
All subsequent numbers are specifically assigned to the user, and no two users share the same IMSI number.
What is IMEI ?
The International Mobile Station Equipment Identity, or IMEI for short, is one unique 15-digit serial number that can be used to uniquely identify each mobile radio terminal (your device). It includes four parts:
The first two digits indicate the reporting body identifier showing Type Allocation Code (TAC) by GSMA approval group.
The next six digits are the TAC.
The six digits after that uniquely identify the individual device.
The final number is the check digit, which helps prevent errors in equipment databases.
There are also “software versions” of IMEIs, referred to as IMEISVs. In an IMEISV, there is no check digit, and the last two digits represent the Software Version Number (SVN).
How to Build an IMSI Catcher :
What is IMSI CATCHER ?
IMSI Catchers are indiscriminate surveillance tools that could be used to track who attends a political demonstration or a public event like a football match. They can even be used to monitor your calls and edit your messages – and you wouldn't even know it was happening.
How IMSI Catcher works?
IMSI Catchers are devices that act like fake cell towers, which trick a target’s device to connect to them and then relay the communication to an actual cell tower of the network carrier. The target’s communications in the form of calls, text messages, internet traffic etc. go through the IMSI Catcher, which can read messages, listen to the calls and so on. At the same time victim will have no knowledge that this is happening as everything will seemingly work as normal. This is referred to as Man-In-Middle attacks in security fields.
This is possible because of a loophole in GSM protocol. Mobile phones are always looking for the mobile tower with the strongest signal to provide the best commutation. This is usually the nearest one. At the same time, when a device connects to a cell tower, it authenticates to it via an IMSI number. However, the tower doesn’t have to authenticate back. This is why every time someone places a device that acts as a cell tower near your phone, it would connect to it and give away its IMSI.

How does an IMSI Catcher find out my identity?
IMSI is a number unique to your SIM card. Once your phone is tricked into connecting to an IMSI catcher, it reveals this unique number. Once the police have your IMSI, they can easily determine your identity.
How does an IMSI Catcher find out my location?
Once your phone has been tricked into revealing its IMSI, the IMSI catcher can determine your phone’s general location by measuring the strength of the signal from the phone. Measuring the strength of the signal from different locations permits an ever-more precise determination of the phone’s location.
Can an IMSI Catcher snoop on my calls and text messages?
Yes. Some IMSI Catchers can ‘intercept’ your text messages, calls and Internet traffic. This means others can read or listen to your personal communications. IMSI Catchers can even re-route or edit communications and data sent to and from your phone. IMSI Catchers can also block service so you can no longer use your phone to make or receive calls and text messages – even for emergency calls.
Hardware and Installation of tools
Hardware
Any of the hardware below can be used for practical purposes.
- RTL-SDR
- Hackrf
- USRP
- Blade-RF
Software
The following software tools are required for practical purposes.
- GR-GSM - A python module, which is used for receiving information transmitted by GSM.
- Wireshark - Capturing the wireless traffic.
- IMSI-Catcher - This program shows the IMSI number, country, brand and operator of cellphones.
- GQRX – Software defined radio receiver.
- RTL-SDR Tools – Get the information of the RTL SDR dongle.
- Kailbrate – Determine the signal strength.
Installation of Wireshark, GQRX, GR-GSM, rtl-sdr
sudo apt-get update
sudo apt-get install gnuradio gnuradio-dev git cmake autoconf libtool pkg-config g++ gcc make libc6 libc6-dev libcppunit-1.14-0 libcppunit-dev swig doxygen liblog4cpp5v5 liblog4cpp5-dev python3-scipy gr-osmosdr libosmocore libosmocore-dev rtl-sdr osmo-sdr libosmosdr-dev libboost-all-dev libgmp-dev liborc-dev libboost-regex-dev python3-docutils build-essential automake librtlsdr-dev libfftw3-dev gqrx wireshark tshark
git clone -b maint-3.8 https://github.com/velichkov/gr-gsm.git
cd gr-gsm
mkdir build
cd build
cmake ..
make
sudo make install
sudo ldconfig
export PYTHONPATH=/usr/local/lib/python3/dist-packages/:$PYTHONPATH

Installation of Kalibrate
sudo apt-get update
git clone https://github.com/steve-m/kalibrate-rtl
cd kalibrate-rtl
./bootstrap && CXXFLAGS='-W -Wall -O3'
./configure
make
sudo make install
Installation of IMSI Catcher
sudo apt install python-numpy python-scipy python-scapy
git clone https://github.com/Oros42/IMSI-catcher.git

Capturing the GSM traffic
For this practical, the RTL-SDR dongle was used. Once the tools installation process is complete, plugin the RTL-SDR USB dongle to your system.
Open the terminal and run the below command to check the dongle has been plugged in successfully.

In India Mobile GSM networks work on 900MHz and 1800MHz frequency bands (Uplink and Downlink).
The help guide of the “grgsm scanner” tool.
Search for nearby GSM base stations using “Kalibrate” or “grgsm_scanner” tools.

Three base stations were found. The signal mentioned above was relatively strong with a frequency of 945.4MHz and 945.6MHz.
In the above manner, we obtained some parameter information of the base station, such as: center frequency, channel, ARFCN value, LAC, MCC, MNC value, etc.
With the above details, we want to sniff the base station frequency. For that the program called “grgsm_livemon” will be used.
The help guide of the “grgsm_livemon” tool.


Run the “Wireshark” before running the “grgsm_livemon” tool to capture the packets. Select any interface to capture all the data.

Once the sniffing of the frequency starts, a popup window appears, as shown in the screenshot below.

The frequency button needs to be moved in order to capture the frequency. Once data capture starts it will look like the screenshot below.

Now we need to capture the IMSI details with the help of an “IMSI Catcher” tool.

To capture the IMSI and other details like TMSI, Country, Brand, Operator, MCC, MNC, LAC, Cell-ID etc., run the “IMSI Catcher” tool.

In Wireshark, the captured data of base station’s MNC, MCC, LAI and other information can be seen.

HOW TO DETECT IMSI CATCHER :
There are different applications available, which help to find the IMSI Catcher in your location. Once it is installed in mobile, it will automatically detect the IMSI Catcher. Applications contain a database of all the cell towers of mobile carriers in different countries and regularly update this list.
Every time it detects a cell tower, it checks the list to see if it exists. If it exists, then it is a legitimate one, and there is no danger. However, if the tower is not on the list, there is something suspicious going on – and there is a high probability that this is an IMSI Catcher.
In this case, the best you can do is to turn off your phone and turn it on again, once you reach a safe location.
Below are some of the IMSI Catcher detector applications:
- Osmocom – used to detect and fingerprint certain network characteristics
- Android IMSI-Catcher Detector
- SnoopSnitch
- Cell Spy Catcher
- GSM Spy Finder
What is Harris Stingray ?
Stingrays, also known as "cell site simulators" or "IMSI catchers," are invasive cell phone surveillance devices that mimic cell phone towers and send out signals to trick cell phones in the area into transmitting their locations and identifying information. When used to track a suspect's cell phone, they also gather information about the phones of countless bystanders who happen to be nearby. It only works on 2G networks.
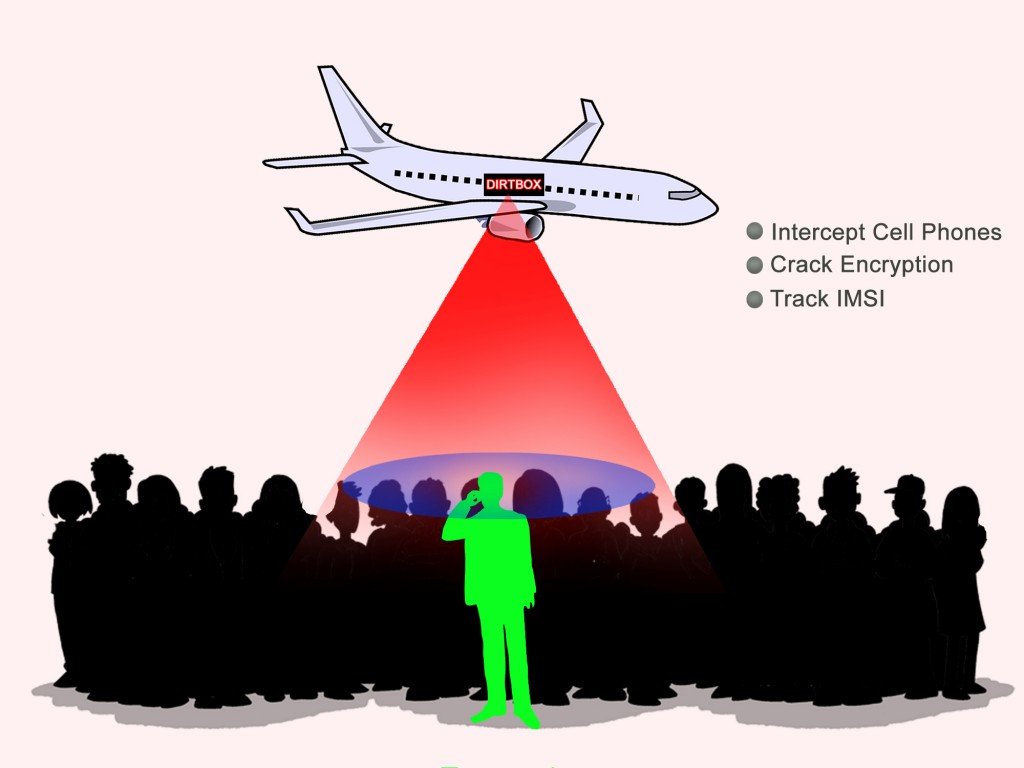
What Is A Dirtbox ?
A dirtbox (or DRT box) is a cell site simulator, a phone device mimicking a cell phone tower, that creates a signal strong enough to cause nearby dormant mobile phones to switch to it. ... It can also be used to jam phones. The device's name comes from the company that developed it, Digital Receiver Technology, Inc.
What Does the Dirtbox Do?
Dirtboxes basically operate as fake mobile phone towers, forcing all the (targeted) mobile phones within its range to use their signal for communication purposes. In other words, a dirtbox functions as a cell tower simulator. Also, as the information passes through the cell tower simulator, the dirtbox simultaneously breaks the encryption on the voice and data transmissions of dozens of mobile phones. If you put dirtboxes on an airplane or even a drone, you’ll potentially elicit all sorts of information about hundreds of people. This information shockingly includes recorded telephone conversations, identification of callers and receivers, and even SMS shared between them.
What does dirtbox can do ?
According to Digital Receiver Technology ,DRT is capable of cracking the encryption on communications from over 200 mobile phones at the same time. This is done across state-of-the-art 4G LTE frequencies used for fast voice and data communication. In 2008, Boeing took over the Digital Receiver Technology company. Boeing describes this device’s purpose as “jamming, managed access and detection”.
Thank You , This tutorial is just for educational purpose ! I m not responsible if you're in jail !!
I hope you get it !!