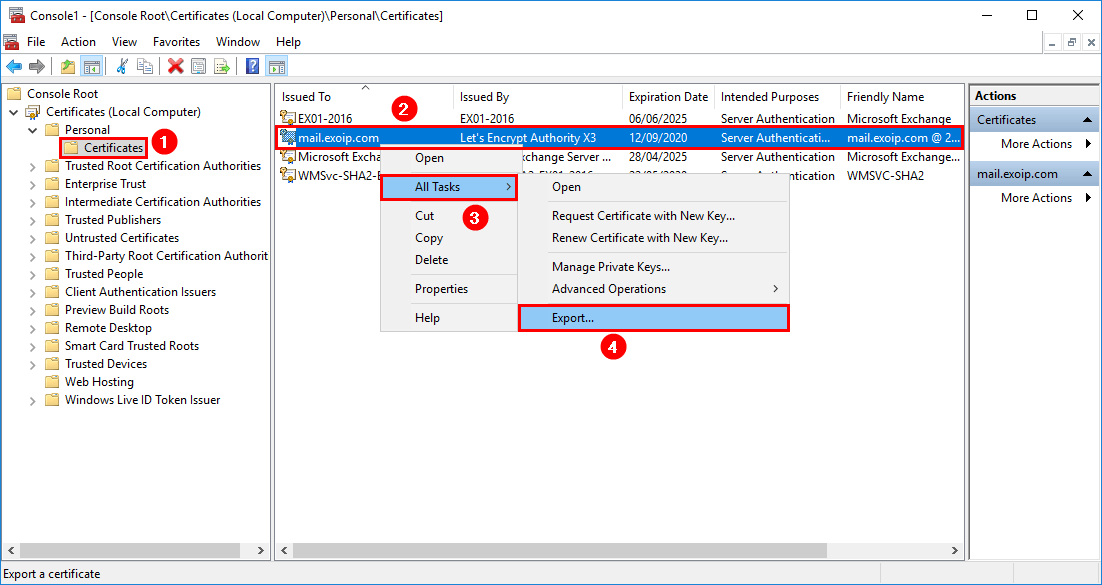
Export Not Exportable Private Key

👉🏻👉🏻👉🏻 ALL INFORMATION CLICK HERE 👈🏻👈🏻👈🏻
Sign up or log in to view your list.
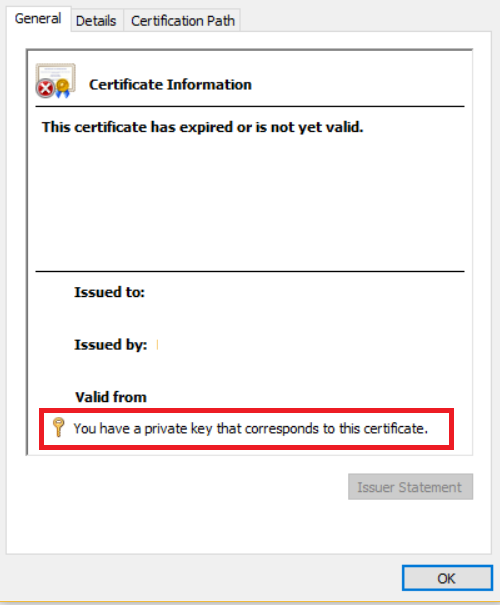
I need to export private key from Windows store. What should I do if the key is marked as non-exportable? I know that it is possible, program jailbreak can export this key.
To export key I use Org.BouncyCastle.Security.DotNetUtilities.GetKeyPair() that exports key from (RSACryptoServiceProvider)cryptoProv.ExportParameters(true). Exported key I use in Org.BouncyCastle.Cms.CmsSignedDataGenerator for CMS signature.
I need solution for .Net, but any solution will be useful. Thank you.
Gorf
Gorf 705●11 gold badge●77 silver badges●1212 bronze badges
xav
4,886●77 gold badges●4242 silver badges●5555 bronze badges
FindPrivateKey.exe util (analog to CspKeyContainerInfo.UniqueKeyContainerName) can get private key file name in "Microsoft\Crypto\RSA\" folder. Are those files really contain private key and how can I decrypt key from this file? – Gorf Oct 13 '10 at 8:48
You're right, no API at all that I'm aware to export PrivateKey marked as non-exportable. But if you patch (in memory) normal APIs, you can use the normal way to export :)
There is a new version of mimikatz that also support CNG Export (Windows Vista / 7 / 2008 ...)
Run it and enter the following commands in its prompt:
The exported .pfx files are password protected with the password "mimikatz"
Gentil Kiwi
Gentil Kiwi 661●66 silver badges●44 bronze badges
Dan Lenski
68.7k●1111 gold badges●6464 silver badges●117117 bronze badges
Thank you. As I understand, this utility only exports all keys from the store, if the store contains too many certificates it takes a lot of time. Maybe I have not figured out, but can you export specific pfx certificate with this util? And how can I decode *.pvk file in my program? I solved my problem by integrating RSACryptoServiceProvider into CmsSignedDataGenerator. – Gorf Oct 20 '10 at 13:47
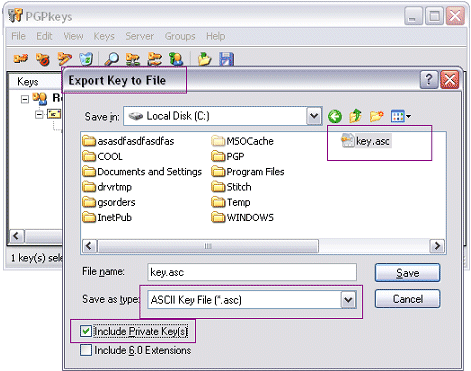
This tool export all key AND individual PFX of certificate/key. Maybe can I adapt the code to select only a specified certificate (it is a forensic tool not an utility ;)) For the PVK format, OpenSSL 1.x convert it without any problem :) openssl rsa -inform pvk -in fichier.pvk -outform pem -out fichier.pem – Gentil Kiwi Oct 20 '10 at 22:52
The commands in crypto module has changed: crypto::cng or crypto::capi or crypto::keys /export – hewigovens May 6 '14 at 13:46
Use crypto::certificates /export /systemstore:CERT_SYSTEM_STORE_LOCAL_MACHINE for Computer Store (github.com/gentilkiwi/mimikatz/blob/master/README.md#crypto) – Matej Feb 5 '16 at 14:47
@NickG / Ville, this is incorrect. The official mimikatz releases do not contain malware, at all. The tool has unfortunately been mislabeled as malware by anti-virus software because it's commonly used in exploits… like any tool that can be used to extract passwords and private keys, it's susceptible to illegitimate uses. – Dan Lenski Oct 30 '20 at 6:59
Gentil Kiwi's answer is correct. He developed this mimikatz tool that is able to retrieve non-exportable private keys.
However, his instructions are outdated. You need:
Run the cmd with admin rights in the same machine where the certificate was requested
Change to the mimikatz bin directory (Win32 or x64 version)
Follow the wiki instructions and the .pfx file (protected with password mimikatz) will be placed in the same folder of the mimikatz bin
mimikatz # crypto::capi
Local CryptoAPI patched
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # crypto::cng
"KeyIso" service patched
mimikatz # crypto::certificates /systemstore:local_machine /store:my /export
* System Store : 'local_machine' (0x00020000)
* Store : 'my'
Zanon
Zanon 23.6k●2020 gold badges●105105 silver badges●113113 bronze badges
all store locations see msdn.microsoft.com/en-us/library/windows/desktop/aa388136.aspx and in addition, please mention the password for all exported pfx is "mimikatz" – Bernhard Oct 13 '16 at 8:28
@Bernhard, I've edited to add the info about the password. Thank you. – Zanon Oct 13 '16 at 12:19
This should definitely be upvoted. It just saved my backside when I ordered a certificate and when creating the request in Windows failed to mark the key as exportable... :| – Shaamaan Feb 28 '18 at 13:06
When I run privilege::debug I get ERROR kuhl_m_privilege_simple ; RtlAdjustPrivilege (20) c0000061. I was using mimikatz 2.2.0 (x64) in Windows 10.0.18363.1016. – U. Windl Sep 9 '20 at 7:14
i wanted to mention Jailbreak specifically (GitHub):
Jailbreak is a tool for exporting certificates marked as non-exportable from the Windows certificate store. This can help when you need to extract certificates for backup or testing. You must have full access to the private key on the filesystem in order for jailbreak to work.
Ian Boyd
Ian Boyd 224k●230230 gold badges●814814 silver badges●11311131 bronze badges
Worked for me, Windows 10 Pro 1703. – RedShift Nov 7 '17 at 10:07
It works on 64-bit systems (like Windows 7 x64), but will not work for Local Machine store on W2k12R2. – StanTastic Apr 18 '18 at 7:23
The first link results in "404". – U. Windl Sep 8 '20 at 14:06
This answer definitely needs more work: What is the actual procedure? Trying it (both, 32 and 64 bit) in Windows 10 64-bit ([Version 10.0.18363.1016]) I only got CreateProces failed with error code = 740. – U. Windl Sep 9 '20 at 6:22
The other thing is: If I run the command without jailbreak, I can only see the user certificates of the administrative user, not the user I'm interested in. – U. Windl Sep 9 '20 at 6:28
There is code and binaries available here for a console app that can export private keys marked as non-exportable, and it won't trigger antivirus apps like mimikatz will.
The code is based on a paper by the NCC Group. will need to run the tool with the local system account, as it works by writing directly to memory used by Windows' lsass process, in order to temporarily mark keys as exportable. This can be done using PsExec from SysInternals' PsTools:
Cocowalla
Cocowalla 12.1k●55 gold badges●5858 silver badges●9595 bronze badges
This appears to work. It prompts me for a password for each file, then says it successfully exported to "4.pfx" -- but I can't find that file. Where does it export to? – Judah Gabriel Himango Aug 13 '19 at 16:32
I found it: it exported to c:\windows\syswow64 on my 64 bit machine. – Judah Gabriel Himango Aug 13 '19 at 16:33
By far the cleanest and easiest solution. A note about the -s option passed to PSexec - check what it does as this will affect what certificate stores are visible to exportrsa. Not needed for personal store. – petkov.np Aug 27 '19 at 10:13
This is a great solution. I'm finally able to work on my mac, although my admins say it's not possible :D – Denis V Jun 11 '20 at 15:40
Worth mentioning that program mentioned here worked for me without PsExec64, so in some cases cmd from under Admin account is enough. But I was exporting certificate from UserStore, not from a system one. – Yura Sep 8 '20 at 8:48
Unfortunately, the tool mentioned above is blocked by several antivirus vendors. If this is the case for you then take a look at the following.
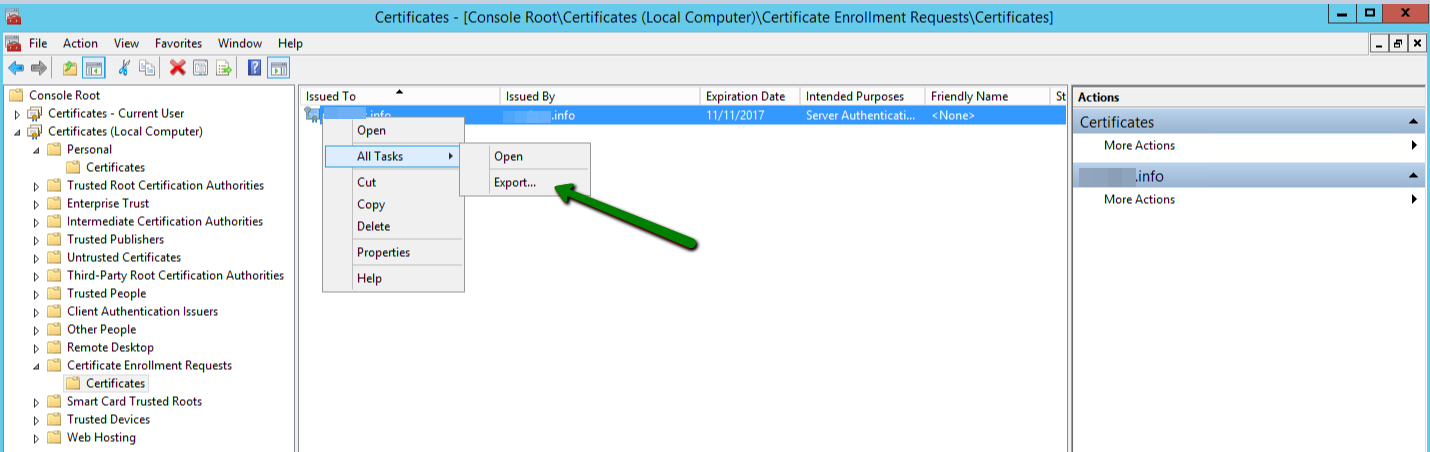
Open the non-exportable cert in the cert store and locate the Thumbprint value.
Next, open regedit to the path below and locate the registry key matching the thumbprint value.
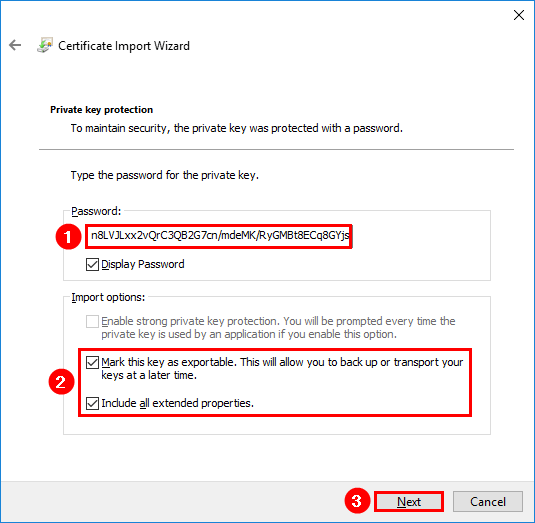
An export of the registry key will contain the complete certificate including the private key. Once exported, copy the export to the other server and import it into the registry.
The cert will appear in the certificate manager with the private key included.
Machine Store: HKLM\SOFTWARE\Microsoft\SystemCertificates\MY\Certificates User Store: HKCU\SOFTWARE\Microsoft\SystemCertificates\MY\Certificates
In a pinch, you could save the export as a backup of the certificate.
Ernest Correale
Ernest Correale 343●22 silver badges●55 bronze badges
Just checked it, and private key is not there - just pointer to some SID, probably file on disk (that's encrypted). So I don't think this approach will work. – StanTastic Apr 18 '18 at 7:22
It's in %APPDATA%\Microsoft\Crypto\RSA\$YOURSID ... I intentionally used the invalid from $YOURSID as a placeholder as you need to figure out your own SID. Probably easiest to do with regedit under HKEY_USERS ... on a single-user machine it would in all likelihood be the SID ending in the RID -1000 ... there should be a corresponding _Classes key. You can also use HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList to figure out which SID corresponds to your username. Last but not least psgetsid %USERDOMAIN%\%USERNAME% from Microsoft/Sysinternals. – 0xC0000022L May 31 at 19:38
You might need to uninstall antivirus (in my case I had to get rid of Avast).
This makes sure that crypto::cng command will work. Otherwise it was giving me errors:
Windows Defender is another program blocking the program to work, so you will need also to disable it for the time of using program at least.
Daniel Kmak
Daniel Kmak 16.5k●77 gold badges●6565 silver badges●8585 bronze badges
I'm not sure I'd call Windows Defender "spyware"?! – Cocowalla May 29 '19 at 12:06
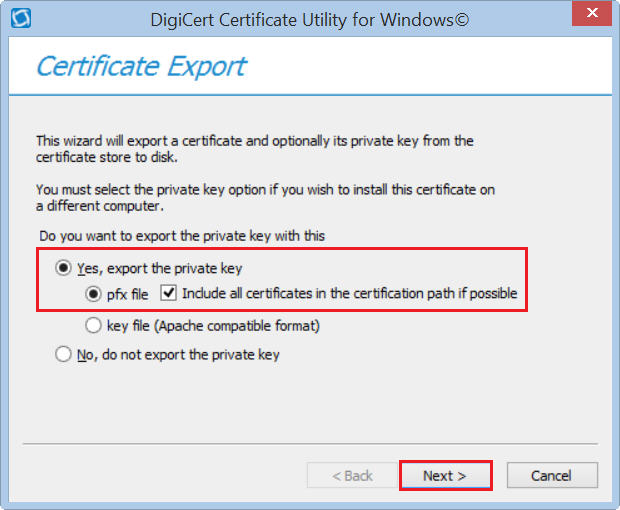
If it's issued by digicert You can use the DigiCert Certificate Utility for Windows. Do the 'Repair' on the server it was created on. Then you can export it to like c:\temp as .pfx. This worked for me with a real ssl cert.
MTMDev
MTMDev 81●11 silver badge●55 bronze badges
This worked for me on Windows Server 2012 - I needed to export a non-exportable certificate to setup another ADFS server and this did the trick. Remember to use the jailbreak instructions above i.e.:
crypto::certificates /export /systemstore:CERT_SYSTEM_STORE_LOCAL_MACHINE
miker2069
miker2069 39●33 bronze badges
What kind of answer is this: You confirm that another answer worked? – U. Windl Sep 9 '20 at 6:50
Highly active question. Earn 10 reputation (not counting the association bonus) in order to answer this question. The reputation requirement helps protect this question from spam and non-answer activity.
2021 Stack Exchange, Inc. user contributions under cc by-sa
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Accept all cookies Customize settings
Sign up or log in to view your list.
I need to export private key from Windows store. What should I do if the key is marked as non-exportable? I know that it is possible, program jailbreak can export this key.
To export key I use Org.BouncyCastle.Security.DotNetUtilities.GetKeyPair() that exports key from (RSACryptoServiceProvider)cryptoProv.ExportParameters(true). Exported key I use in Org.BouncyCastle.Cms.CmsSignedDataGenerator for CMS signature.
I need solution for .Net, but any solution will be useful. Thank you.
Gorf
Gorf 705●11 gold badge●77 silver badges●1212 bronze badges
xav
4,886●77 gold badges●4242 silver badges●5555 bronze badges
FindPrivateKey.exe util (analog to CspKeyContainerInfo.UniqueKeyContainerName) can get private key file name in "Microsoft\Crypto\RSA\" folder. Are those files really contain private key and how can I decrypt key from this file? – Gorf Oct 13 '10 at 8:48
You're right, no API at all that I'm aware to export PrivateKey marked as non-exportable. But if you patch (in memory) normal APIs, you can use the normal way to export :)
There is a new version of mimikatz that also support CNG Export (Windows Vista / 7 / 2008 ...)
Run it and enter the following commands in its prompt:
The exported .pfx files are password protected with the password "mimikatz"
Gentil Kiwi
Gentil Kiwi 661●66 silver badges●44 bronze badges
Dan Lenski
68.7k●1111 gold badges●6464 silver badges●117117 bronze badges
Thank you. As I understand, this utility only exports all keys from the store, if the store contains too many certificates it takes a lot of time. Maybe I have not figured out, but can you export specific pfx certificate with this util? And how can I decode *.pvk file in my program? I solved my problem by integrating RSACryptoServiceProvider into CmsSignedDataGenerator. – Gorf Oct 20 '10 at 13:47
This tool export all key AND individual PFX of certificate/key. Maybe can I adapt the code to select only a specified certificate (it is a forensic tool not an utility ;)) For the PVK format, OpenSSL 1.x convert it without any problem :) openssl rsa -inform pvk -in fichier.pvk -outform pem -out fichier.pem – Gentil Kiwi Oct 20 '10 at 22:52
The commands in crypto module has changed: crypto::cng or crypto::capi or crypto::keys /export – hewigovens May 6 '14 at 13:46
Use crypto::certificates /export /systemstore:CERT_SYSTEM_STORE_LOCAL_MACHINE for Computer Store (github.com/gentilkiwi/mimikatz/blob/master/README.md#crypto) – Matej Feb 5 '16 at 14:47
@NickG / Ville, this is incorrect. The official mimikatz releases do not contain malware, at all. The tool has unfortunately been mislabeled as malware by anti-virus software because it's commonly used in exploits… like any tool that can be used to extract passwords and private keys, it's susceptible to illegitimate uses. – Dan Lenski Oct 30 '20 at 6:59
Gentil Kiwi's answer is correct. He developed this mimikatz tool that is able to retrieve non-exportable private keys.
However, his instructions are outdated. You need:
Run the cmd with admin rights in the same machine where the certificate was requested
Change to the mimikatz bin directory (Win32 or x64 version)
Follow the wiki instructions and the .pfx file (protected with password mimikatz) will be placed in the same folder of the mimikatz bin
mimikatz # crypto::capi
Local CryptoAPI patched
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # crypto::cng
"KeyIso" service patched
mimikatz # crypto::certificates /systemstore:local_machine /store:my /export
* System Store : 'local_machine' (0x00020000)
* Store : 'my'
Zanon
Zanon 23.6k●2020 gold badges●105105 silver badges●113113 bronze badges
all store locations see msdn.microsoft.com/en-us/library/windows/desktop/aa388136.aspx and in addition, please mention the password for all exported pfx is "mimikatz" – Bernhard Oct 13 '16 at 8:28
@Bernhard, I've edited to add the info about the password. Thank you. – Zanon Oct 13 '16 at 12:19
This should definitely be upvoted. It just saved my backside when I ordered a certificate and when creating the request in Windows failed to mark the key as exportable... :| – Shaamaan Feb 28 '18 at 13:06
When I run privilege::debug I get ERROR kuhl_m_privilege_simple ; RtlAdjustPrivilege (20) c0000061. I was using mimikatz 2.2.0 (x64) in Windows 10.0.18363.1016. – U. Windl Sep 9 '20 at 7:14
i wanted to mention Jailbreak specifically (GitHub):
Jailbreak is a tool for exporting certificates marked as non-exportable from the Windows certificate store. This can help when you need to extract certificates for backup or testing. You must have full access to the private key on the filesystem in order for jailbreak to work.
Ian Boyd
Ian Boyd 224k●230230 gold badges●814814 silver badges●11311131 bronze badges
Worked for me, Windows 10 Pro 1703. – RedShift Nov 7 '17 at 10:07
It works on 64-bit systems (like Windows 7 x64), but will not work for Local Machine store on W2k12R2. – StanTastic Apr 18 '18 at 7:23
The first link results in "404". – U. Windl Sep 8 '20 at 14:06
This answer definitely needs more work: What is the actual procedure? Trying it (both, 32 and 64 bit) in Windows 10 64-bit ([Version 10.0.18363.1016]) I only got CreateProces failed with error code = 740. – U. Windl Sep 9 '20 at 6:22
The other thing is: If I run the command without jailbreak, I can only see the user certificates of the administrative user, not the user I'm interested in. – U. Windl Sep 9 '20 at 6:28
There is code and binaries available here for a console app that can export private keys marked as non-exportable, and it won't trigger antivirus apps like mimikatz will.
The code is based on a paper by the NCC Group. will need to run the tool with the local system account, as it works by writing directly to memory used by Windows' lsass process, in order to temporarily mark keys as exportable. This can be done using PsExec from SysInternals' PsTools:
Cocowalla
Cocowalla 12.1k●55 gold badges●5858 silver badges●9595 bronze badges
This appears to work. It prompts me for a password for each file, then says it successfully exported to "4.pfx" -- but I can't find that file. Where does it export to? – Judah Gabriel Himango Aug 13 '19 at 16:32
I found it: it exported to c:\windows\syswow64 on my 64 bit machine. – Judah Gabriel Himango Aug 13 '19 at 16:33
By far the cleanest and easiest solution. A note about the -s option passed to PSexec - check what it does as this will affect what certificate stores are visible to exportrsa. Not needed for personal store. – petkov.np Aug 27 '19 at 10:13
This is a great solution. I'm finally able to work on my mac, although my admins say it's not possible :D – Denis V Jun 11 '20 at 15:40
Worth mentioning that program mentioned here worked for me without PsExec64, so in some cases cmd from under Admin account is enough. But I was exporting certificate from UserStore, not from a system one. – Yura Sep 8 '20 at 8:48
Unfortunately, the tool mentioned above is blocked by several antivirus vendors. If this is the case for you then take a look at the following.
Open the non-exportable cert in the cert store and locate the Thumbprint value.
Next, open regedit to the path below and locate the registry key matching the thumbprint value.
An export of the registry key will contain the complete certificate including the private key. Once exported, copy the export to the other server and import it into the registry.
The cert will appear in the certificate manager with the private key included.
Machine Store: HKLM\SOFTWARE\Microsoft\SystemCertificates\MY\Certificates User Store: HKCU\SOFTWARE\Microsoft\SystemCertificates\MY\Certificates
In a pinch, you could save the export as a backup of the certificate.
Ernest Correale
Ernest Correale 343●22 silver badges●55 bronze badges
Just checked it, and private key is not there - just pointer to some SID, probably file on disk (that's encrypted). So I don't think this approach will work. – StanTastic Apr 18 '18 at 7:22
It's in %APPDATA%\Microsoft\Crypto\RSA\$YOURSID ... I intentionally used the invalid from $YOURSID as a placeholder as you need to figure out your own SID. Probably easiest to do with regedit under HKEY_USERS ... on a single-user machine it would in all likelihood be the SID ending in the RID -1000 ... there should be a corresponding _Classes key. You can also use HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList to figure out which SID corresponds to your username. Last but not least psgetsid %USERDOMAIN%\%USERNAME% from Microsoft/Sysinternals. – 0xC0000022L May 31 at 19:38
You might need to uninstall antivirus (in my case I had to get rid of Avast).
This makes sure
Child Girl Nudist
Peeing Pants Vk
Good Best To Make With Your Wife
Mature Cams Top Casting
Www Mom And Boy Com
Recovering a certificate where the private key is marked ...
SSL: How to Export Non-Exportable Private Keys – ballbl…
[3 Steps] Exporting a Certificate not Marked as Exportable ...
The option: "Yes, export the private key" is greyed out
jailbreak for Windows 10: Export unexportable private key ...
export certificate with private key - Microsoft Q&A
How to export non-exportable private key from store ...
[SOLVED] Export Private Key help - Windows Forum - Spice…
Export Not Exportable Private Key