Eavesdropping smartphones with a built-in accelerometer.
Introduction.🔑
Good afternoon, my birds go dodo, I propose again in the world of wonderland, but without risking Alice's finger.🦤🎀
I recently discovered an interesting side-channel attack (these are non-invasive attacks, they cover vulnerabilities in the practical implementation of cryptosystems, not analysis of statistical or mathematical weaknesses), unfortunately, it is not directed to some article with a predisposition to the air gap, and I solved post limitation.🧩
The essence of detecting errors in speech recognition from phones, while using their motion sensors. 🎛
Attack.💥
Introduction.
Motion sensors on modern smartphones are used to control sound, due to their sensitivity to sensation. 🎚
This threat is not considered dangerous due to two generally recognized limitations:
1) The ability to transmit sound.
It is believed that, unlike microphones, motion sensors can pick up river signals lying on any excitations (table, chair, shelf) due to vibration. Formerly gyroscopes for smartphones to detect eavesdropping attacks.
2) Injury frequency.
It also assumes that these sensors only capture a narrow band (85–100 Hz) of the river signal due to the 200 Hz sampling limit. When a person speaks in a slightly larger amount, as will be discussed below.
Here I want to touch on the topic of why such sensors are not all protected, as well as talk about relatively new attacks on the side channel of AccelEve.
This attack uses the smartphone's accelerometer to eavesdrop on the speaker. 📱
In the attack, the researchers use a system based on deep machine learning that will recognize and recover speech information from spectrogram representations of signals.
The researchers' assessment shows that the AccelEve attack is effective and very accurate in various scenarios, for example, it can work even with external noise (on the street, in a car, in the subway).🚟
The original study is attached below.
How is the attack going?
1) An attacker trains a machine learning model to recognize speech.
2) An attacker collects vibration data from motion sensors using an application running in the background.
3) The attacker runs the recorded data through his trained model and obtains information about the person's conversations.
Smartphones have penetrated into everyday life as an important interface for communication with the rest of the world.
Among all the different ways of communication communication, voice communication is always the main one in communication.
Due to the importance of voice communication, the microphone uses the highest privilege level by default on most operating systems ( Android ).
At the same time, motion sensors, due to the general opinion of the safety of their use, do not need such privileges.
By analyzing the readings of motion sensors on the same smartphone, it is possible to identify and reconstruct the speech signal of the smartphone's speaker without hacking the operating system and without gaining access to the ad manager. 🫠
Reasons for the attack.
This attack can be caused by the following reasons:
1) Access rights. 🔓
Because accelerometers and gyroscopes are considered of little danger, they are usually configured as zero-resolution sensors and can be accessed without warning to smartphone users.
2) Response to vibrations. 🗝
Motion sensors can respond to external vibrations, allowing them to pick up certain audio signals.
In addition, there is an overlap between the fundamental frequency of human speech and the sample rate of smartphone sensors.
Therefore, it is possible to capture voice signals by a motion sensor with zero privileges.
Since most of the speech information in the high band is the fundamental harmonic, the reconstruction module can convert the acceleration signal into a speech signal with an upsampled frequency (1500 Hz).
According to experimental results, the reconstruction module is able to restore almost all speech exactly (although there are interruptions with muffled sounds due to the height of their frequencies.🗣
Attack details.
Modern smartphones are usually equipped with a three-axis accelerometer and a three-axis gyroscope. 🎛
These sensors are very sensitive to the movement of the device and are widely used to determine orientation, vibration, shock, etc., it is their vibrations that an attacker will intercept.
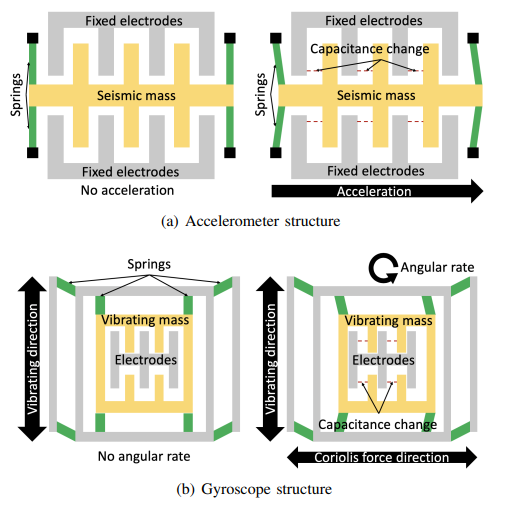
In fact, the information recorded by the motion sensor depends not only on its sensitivity to the environment, but also on the sampling rate.
On Android smartphones, motion sensors can be accessed using four delay options.
Each option determines the interval at which sensor readings are sent to the application.
For example, if an application selects SENSOR_DELAY_FASTEST , sensor measurements will be sent to the application as soon as possible, and the actual sample rate will be determined mainly by the performance of the smartphone. 📱
The fundamental frequencies of human speech signals carry important information.
It is defined as the frequency of vibration of the vocal cords and varies depending on many factors of the person himself. Usually the frequencies are in the range of 85-255 Hz , respectively.
What systems are affected?
The attack mainly targets the Android system due to its popularity.
Note that since the maximum sample rate of the accelerometer in iOS also depends on the maximum sample rate supported by the hardware, this method can be extended to attack iOS.
The sampling rate of the accelerometer and gyroscope in an Android smartphone should not exceed 200 Hz, respectively, orbital sensors can only pick up human speech at a very short distance.
However, if the Android spy app selects SENSOR_DELAY_FASTEST, the sensor measurements will be sent to the app as soon as possible.
This means that the fastest sampling rate of the latest smartphones can exceed 200Hz.
Table with details in different systems from the original article.
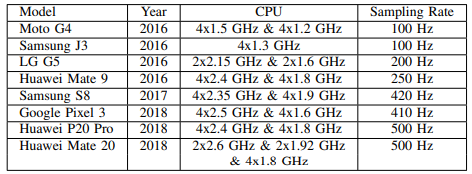
How dangerous is it?
Let's say the victim uses a smartphone during important negotiations, holding it close to him. Private information contained in voice signals. ъ\
Spy apps continuously collect accelerometer readings in the background and try to extract voice information when an audio signal is played through the smartphone's speaker (for example, an important conversation with someone).
A spy app could potentially masquerade as any app, or even worse, legitimate apps could use this to pick up ads since no privileges are required to access the accelerometer.
Here are some examples of threats:
1) Voice notes 🗣, a person can record important information for himself in audio format (for example, flogged or phone numbers). A human-targeted attacker could intercept this to attack the services used by the victim, or worse, if an unsophisticated user wrote down the password of the service of the company it works for, the attacker could get inside the company's infrastructure.
2) Location information 🌍, many apps support voice navigation, people often enable this feature, especially in cars, because spy apps can track the user's location.
3) Music and video preferences 🎼 (this is the most harmless in my opinion), but do not forget that the information received can be analyzed by an attacker to establish the habits of the victim.
4) Audio calls and messages 🎬 . People often listen to audio messages loudly enough or turn on calls on the speakerphone, so such an attack can intercept key information from them.
I'll give an example:
An important journalist told by phone or in an audio message some important information that he had not yet published, but the malicious application overheard his speech using motion sensors, and the attackers, having learned this information, managed to use it for their own purposes.
Outcome.
Well, my birds, summing up:
This attack clearly shows how motion sensors without special rights in the system can play sound at close range.
The worst thing is that the speech signal from the speaker of a smartphone will always have a significant impact on the readings of the accelerometer of the same smartphone, and accelerometers, in turn, can cover almost the entire range of the main frequencies of adult speech .
But how to protect yourself, you ask? Here is a set of my recommendations:
1) For example, you can not use a smartphone🙃.
2) alternatively, you can try cutting out motion sensors.
3) Add vibration absorbing material around the phone's speakers.
4) Try to restrict application permissions.
5) Disable motion sensors at the system level.
6) When talking on the phone, or listening to information, you can use headphones, and for important conversations, keep the phones away from you.
And on this, our small but interesting article comes to an end, I hope you were interested, and you were able to draw some usefulness for yourself.
The original research material will be listed below, where you can learn more about the technical details of the attack. 📚
Thanks for reading. ❤️
And remember:
If a lot of amazing things happen around Alice, then nothing is impossible. Therefore, be careful plunging into the wonderland. 🎀🔮