Data transmission using luma modulation🪄
Hello my Mary Ann. We are deeper into the looking glass🪞🎀
This is a small unscheduled post on an interesting topic.
As you can probably see from my channel, I really love the topic of offline hacks.
In this post I want to talk about: data transmission using brightness modulation, and how it works.
So, Neo, don't forget to take your pills to find out " how deep is the rabbit hole " 💊

Introduction
There are many methods that allow you to transfer information through the air gap . In case standard wired and wireless communication methods are not available, there are many non-standard one-way (simplex) transmission channels:
acoustic, magnetic, visible optical and thermal.
Since these channels are usually unidirectional, they are used to transfer sensitive data. In particular, to transfer passwords, for example, to open a wireless communication channel.
One very interesting method is to transmit data using modulation of the brightness of the computer screen.
The screen may or may not be directly visible.
In this case, visibility is achieved by reflection from the walls and equipment in the room. The use of common screen protection methods, such as glass tarnishing, does not diminish the usefulness of this method.
Moreover, it allows the signal to be transmitted over very long distances, since the use of a telescope with sufficient aperture and focal length makes it possible to observe the modulation of the screen.
This method does not require special permissions and can be implemented, for example, in Linux from the user level, since changing the display brightness is available even at this level. In addition, this method can be implemented in various ways: by changing the content of the screen or its backlight.
What kind of screen brightness modulation
Air-gap transmission using modulated computer screen light is difficult when there are many light sources, such as indoors.
In extreme cases, the light from the monitor is not available directly, but only as a reflection from the wall or objects.
This means that the recorded video sequence contains a mixture of several light sources.
As you understand, processing such a " porridge " is a very difficult task.
Image segmentation, based on the frequency characteristics of rapidly changing brightness waveforms of light sources, allows you to identify areas with similar characteristics, and at the next stage, detect transmissions in them.
By defining regions, you can improve the SNR (Signal to Noise Ratio) to reduce transmission error rates.
methods
transmittance modulation . It, in turn, can also be implemented in two ways: by changing the pixel values of the image, or by changing the settings related to the brightness and contrast of the controller.
The second method uses screen backlight brightness modulation . It can be used for compact fluorescent lamp (CFL) backlighting (old monitors) and LED backlighting (currently used).
Both types of backlight use Pulse Width Modulation (PWM) controlled converters. The fill factor value affects the brightness of the backlight and therefore the monitor screen.
Luminance modulation in both cases can use different methods:
The simplest is FSK , which requires a relatively large number of frames allocated per transmitted bit. Its advantage is high resistance to interference. The main disadvantage is very slow transmission, eg 0.1 bps.
In the case of PAM modulation, two 2-PAM brightness levels can be used, while a small number of image frames are allocated per bit, so the bit rate can even be several bits per second.
This transmission is more susceptible to various interferences, but it allows you to transfer much more information, so more often than not, attackers use this method.
Examples

Here are two example scenarios:
The first is based on the line of sight of the screen of the transmitting computer.
It doesn't have to be high quality footage.
The image may be blurred due to insufficient sharpness or the use of a special matting film on the glass of the room to protect the monitors from viewing the contents of the screen.
An approximate image of a computer with software installed, transmitted by modulating the brightness of the backlight.
The second test scenario concerns the visibility of the transmission only due to the reflection of light from the wall. The screen of the transmitting computer is not visible to the camera.
In addition, a second computer was installed, the screen of which is not visible to the cameras. This means that there is a strong source of interference for the camera.
For this test scenario, two cases were:
investigating the basic algorithm to change the average brightness of the entire image frame, and using the proposed segmentation algorithm to selectively average the transmitted signal.
An example image of a computer with software installed, transmitting a signal by modulating the brightness of the backlight.
The communication channel can be of two types:
The first type is the easiest, and assumes that the image frame is converted to one pixel .
In this case, image averaging is used.
This approach is very simple and takes the idea that the acquisition conditions are very good.
This case is the ideal scenario.
In more realistic cases, there are several sources of interference:
Camera sensor noise (which can be reduced by cooling the sensor), screen activity that changes image brightness, and room lighting with various types of lamps - incandescent, fluorescent, gas discharge or LED, controlled by various DC-DC or AC converters . constant (AC-DC).
The screens also glow unevenly because they are controlled by DC converters.
Other computer screens are also a serious source of interference. The screen orientation of the transmitting computer can also be
unfavorable.
For example, it can be turned away from the camera. Despite this unfavorable orientation, reflection transmission from the environment (walls, objects and even stationary people) can be observed.
Receiving data in the case of multiple sources interfering with transmission requires filtering.
In case of interference from lighting lamps, you can use band pass filters for 100 Hz or 120 Hz for 50 Hz and 60 Hz networks respectively.
This means that the received signal consists of components that must be separated from each other.
In addition, the air gap transmission signal is very weak, and in the case of reflection, it is further attenuated.
Unfortunately, in many cases this is a very difficult task.
It is possible to use a known training sequence to further split the signal, but this is not the best approach. The fundamental mistake is to use an operation that results in the loss of spatial information about the signal.
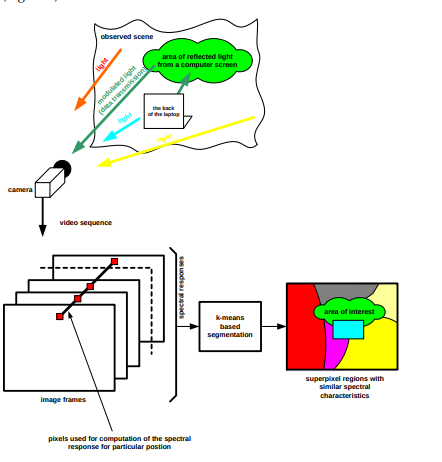
A more efficient segmentation method uses spatiotemporal clustering to recover the transmitted information.
Each pixel of the image recorded by the camera contains information about light sources in the environment, both lamps and monitor backlights.
Some light sources can be continuous light sources (DC component only), which is possible with some types of lamps and daylight.
Most lighting comes from artificial sources that are controlled by frequency or duty cycle change (PWM).
This means that most light sources have their own specific frequency responses associated with turning them on and off quickly to achieve a certain brightness.
In the case of lamps: usually pulsed light sources are used, which are powered in such a way that electricity is supplied for short periods of time and not for other periods.
This makes it possible to simplify power supply systems for light sources, which are often low voltage receivers (eg LED) and the power supply is high voltage (eg 110 or 230 V).
In the case of computer monitors: This is due to the screen refresh rate and backlight brightness control.
Depending on the location of the light sources and the environment, we get an image of the scene in which individual pixels are the result of mixing signals, which are very fast temporal changes in the brightness of the pixels from the light sources.
In the case of some light sources: their flashing frequency is of the order of several tens of kHz, since in this case the transducer systems often generate sounds (coils or transformer) that are inaudible to humans.
Using a very fast camera, one can directly measure these changes for each pixel, according to the sampling theorem. The brightness value for each pixel then contains the component sum of all variable brightnesses of the light sources.
It is also possible to use fast cameras that do not satisfy the requirements of the sampling theorem , resulting in aliasing .
Despite the violation of the sampling theorem, the use of these types of signals is possible , since the goal is not to recover the rapidly changing signal from each light source, but to control the slowly changing transmission signals.
Since each pixel contains a mixture of signals from all light sources, it is necessary to combine pixels into groups with similar frequency responses.
Otherwise, more light sources are mixed and the transmission quality deteriorations.
In an extreme case, only one pixel can contain data transmission , but due to the noise level in the image sensor and the lights themselves, this results in a degradation of SNR (Signal to Noise Ratio).
The second extreme case is when the entire image is considered as a data transfer source.
In this case, an attempt is made to reconstruct the transmission from the overall brightness of the image recorded by the camera.
This is not quite the right solution, because the image may contain many more pixels that are not related to the actual transmission, and reflections from other light sources, which also degrades the SNR.
To solve the SNR problem, we proposed an adaptive approach in which the algorithm tries to find the optimal area of the image that gives a high SNR.
The basis for this is the spatial relationships between pixels.
There is a high probability that nearby pixels have similar signals.
This process uses signal clustering with the k-means algorithm .
The k-means algorithm allows you to group pixels with a similar spectrum for the evaluation area, creating superpixels.
The main steps of the k-means algorithm are:
1) Choose the number of clusters you want to find which is k
2) Randomly assign data points |Wf | to any of k clusters
3) Then calculate the center of the clusters
4) Calculate the distance of data points |Wf | from the centers of each of the clusters
5) Depending on the distance of each data point from the cluster, reassign the data points to the nearest clusters
6) Calculate the new cluster center again
7) Repeat steps 4, 5 and 6 until data points change clusters
In the case of an intruder, this is extremely important, since the absence of an appropriate signal may indicate the need to quickly change position in relation to, for example, the room with the transmitting computer.
The method also has a very low computational cost because the implementation of the FFT is very efficient and this operation is performed only once, at the beginning of the observation. Further operations are related to simple averaging/accumulation, which is very efficient in modern processors with SIMD (single instruction, multiple data) architecture.
Conclusion

And that's all. As you understand, this is a fairly simple implementation, which gives the relative effectiveness of the attack.
This makes it a very good option for attackers.
Be vigilant and keep your Air-Gap in a room where there are no windows or where intruders can film.
A more detailed description will be in the article below💥.
Thank you for reading ❤️
I hope my brief description was helpful to you
And remember, even if you mix the pixels of Alice and the rabbit, we can still return them back, even if Alice wears antennae, and the rabbit has a bow.
🐰🎀🔮